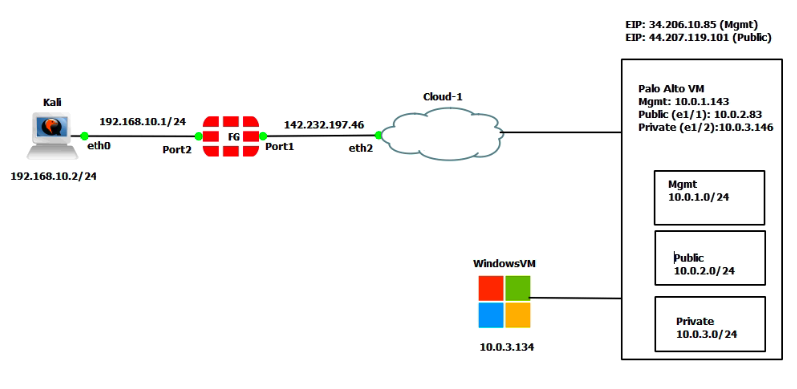
This is a diagram that I have used for this lab.
Understanding on deploying Palo Alto instance in AWS is necessary for this lab (https://tungle.ca/?p=3979).
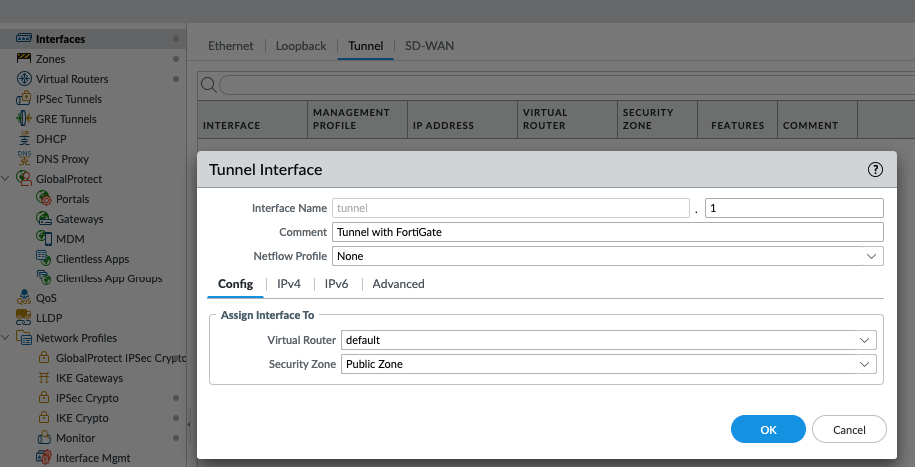
On PA, Configure a tunnel.
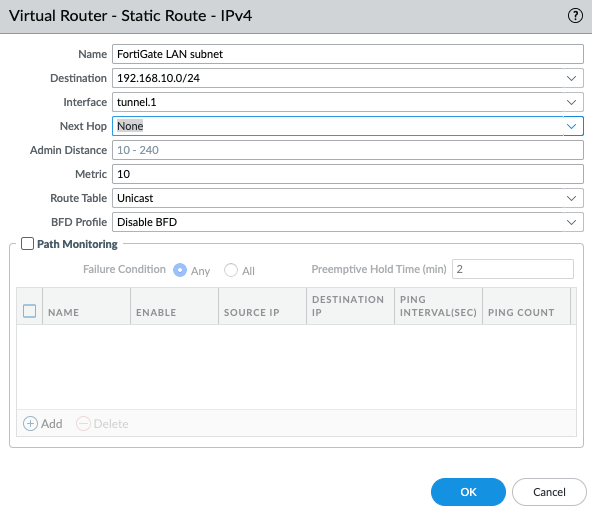
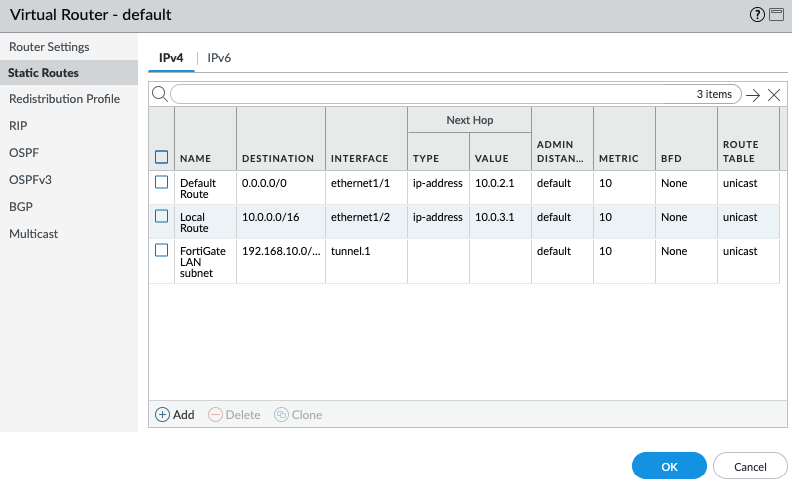
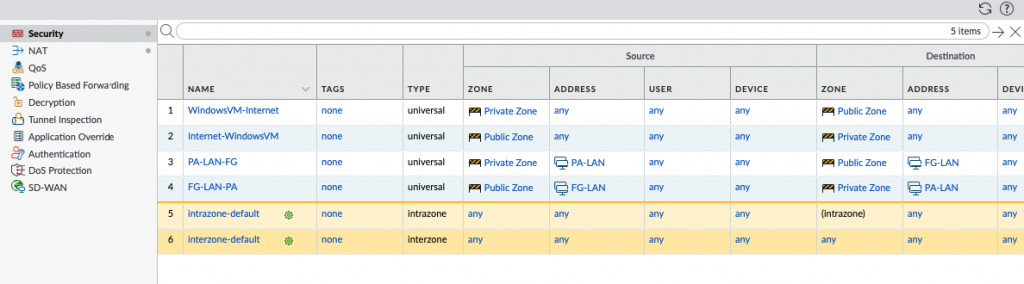
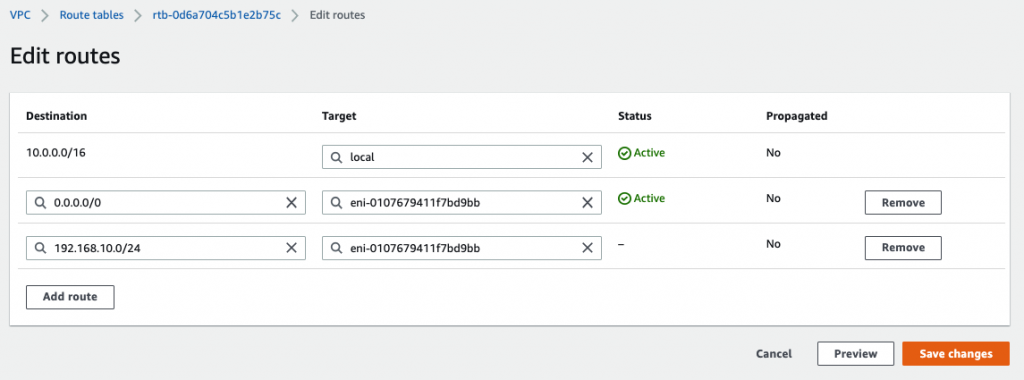
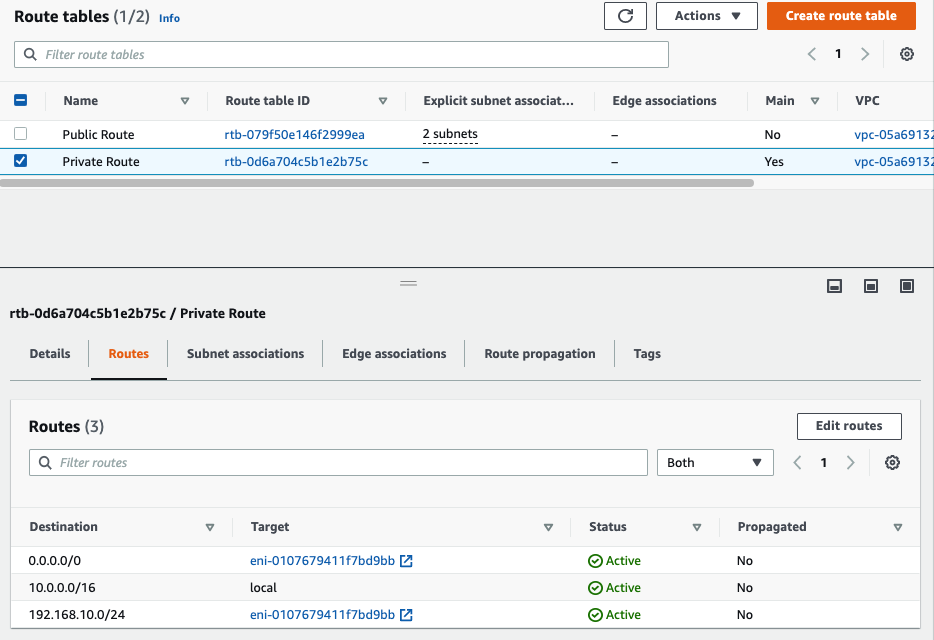
Add a new static route into PA Virtual Route to allow traffic from the Private subnet to a LAN subnet in FortiGate.
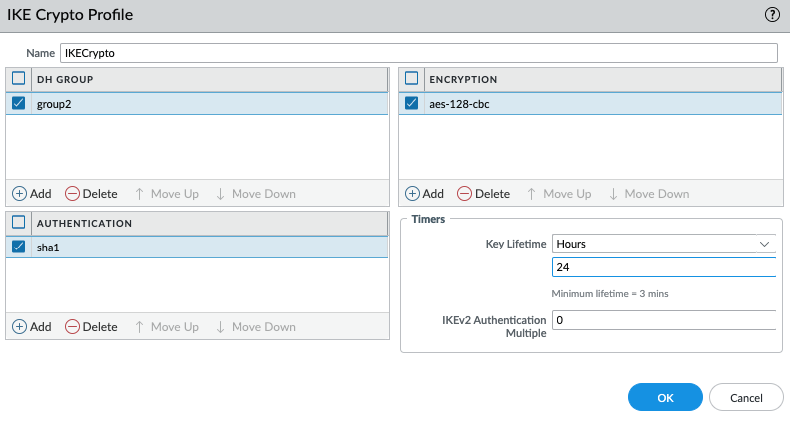
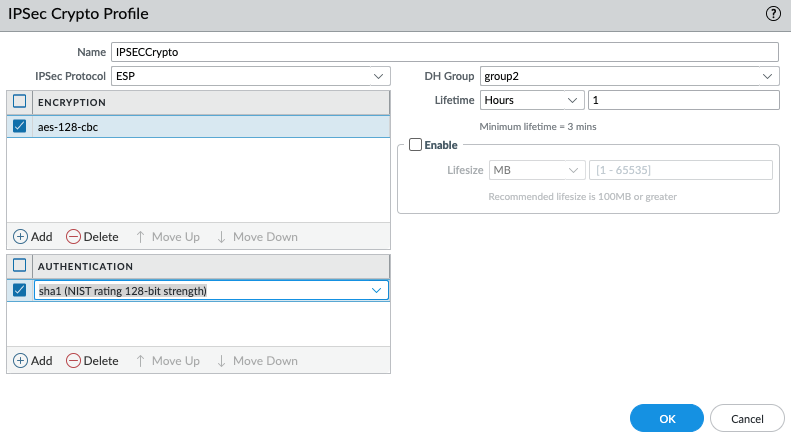
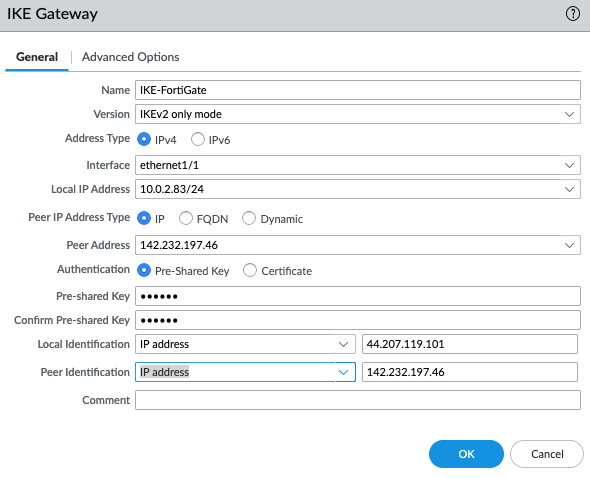
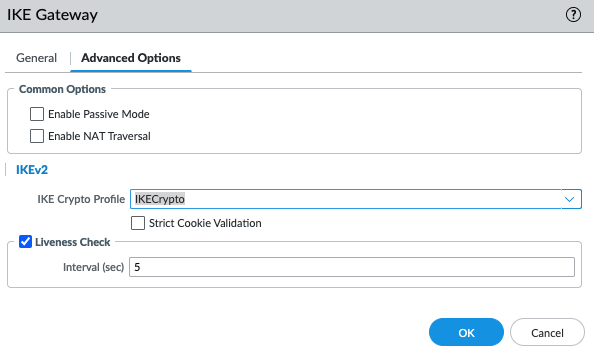
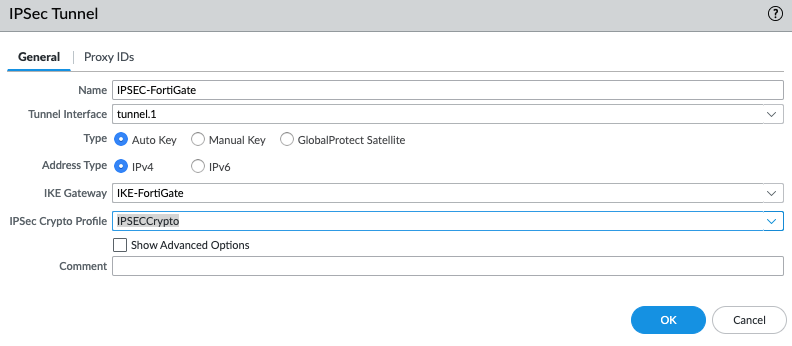
Create an IPSEC tunnel.
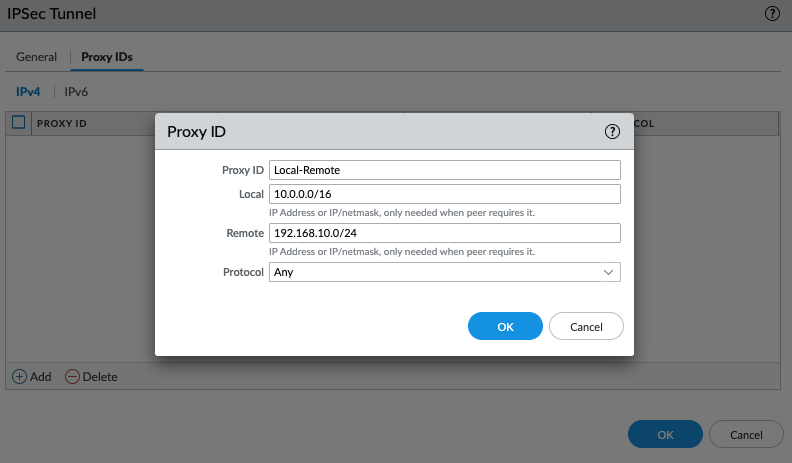
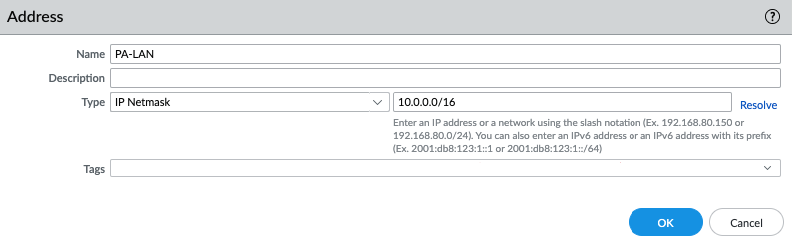
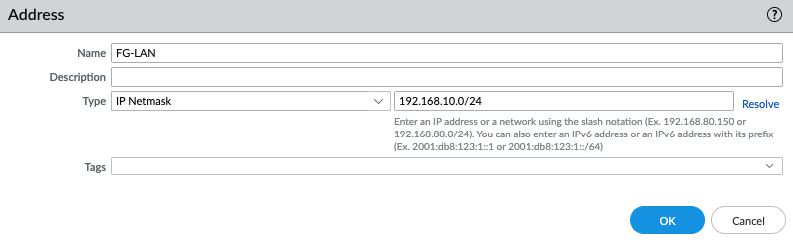
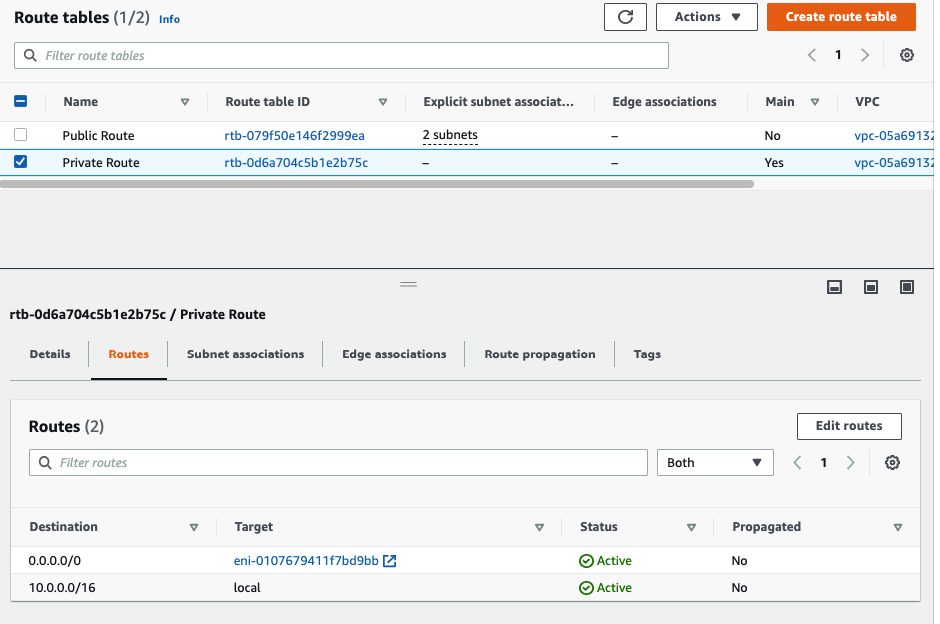
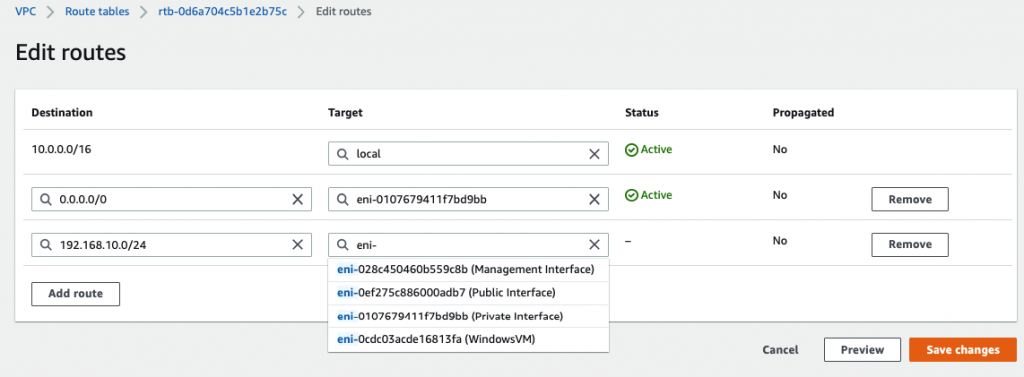
Add 192.168.10.0/24 into the routes and select “Private Interface” on the target.
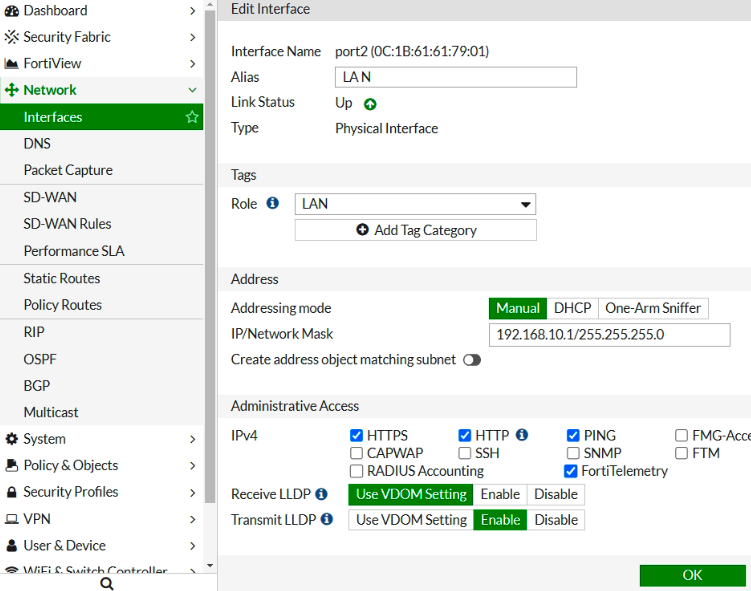
Configure interfaces.
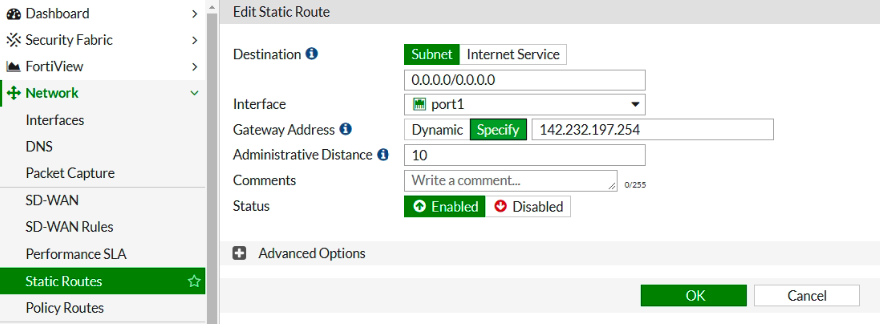
Configure default routes on FG.
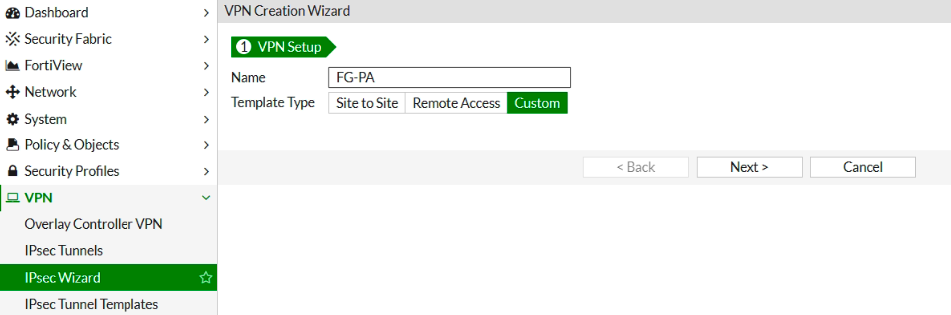
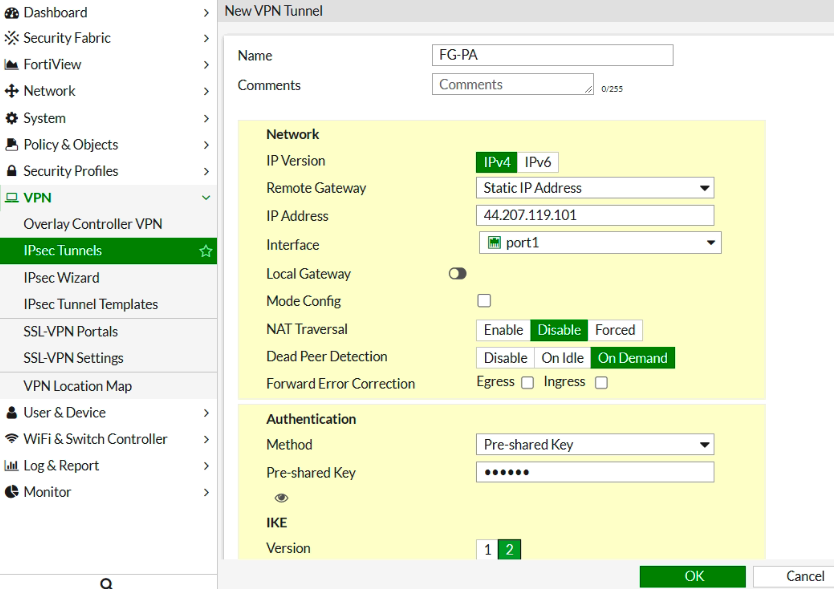
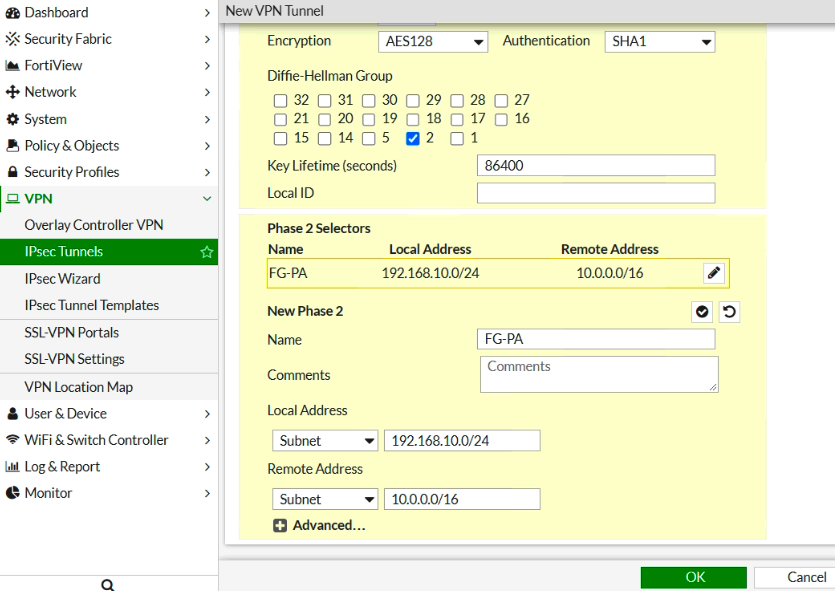
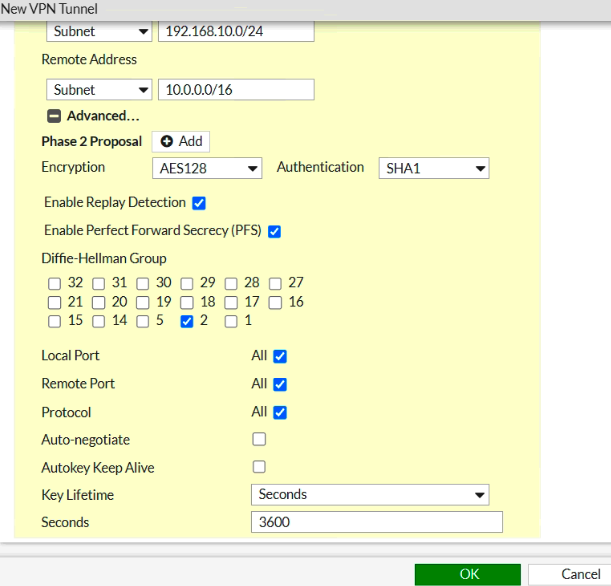
Configure IPSEC VPN on FG.
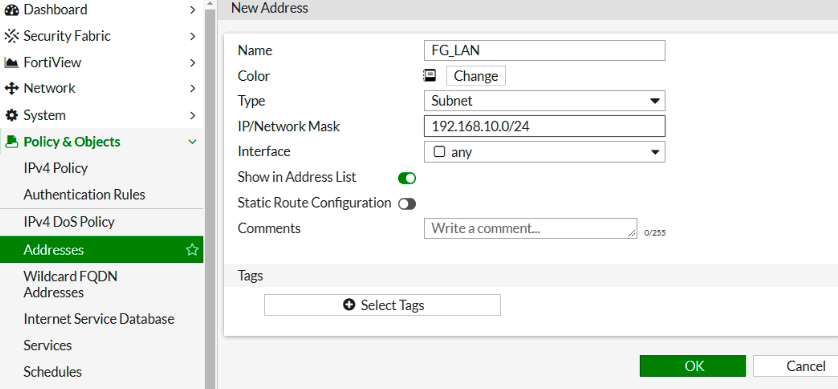
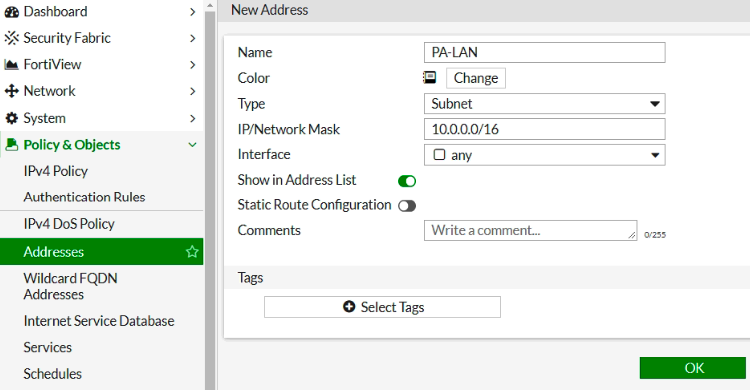
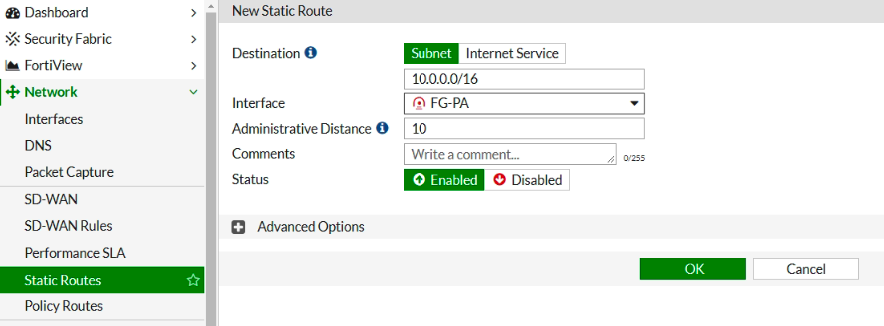
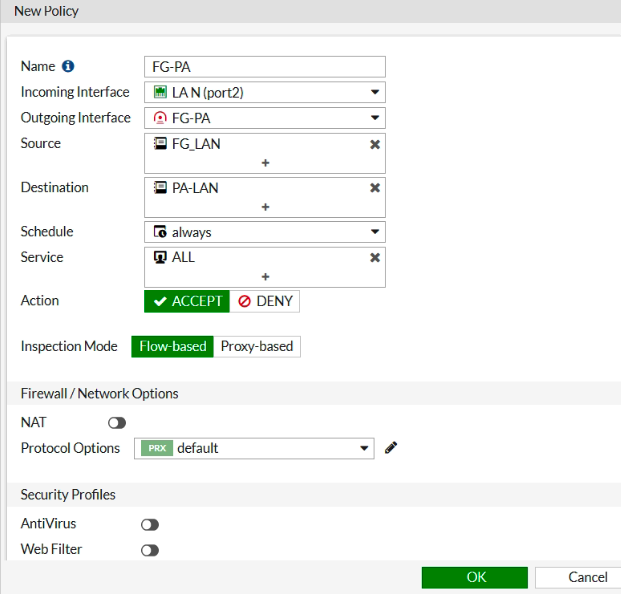
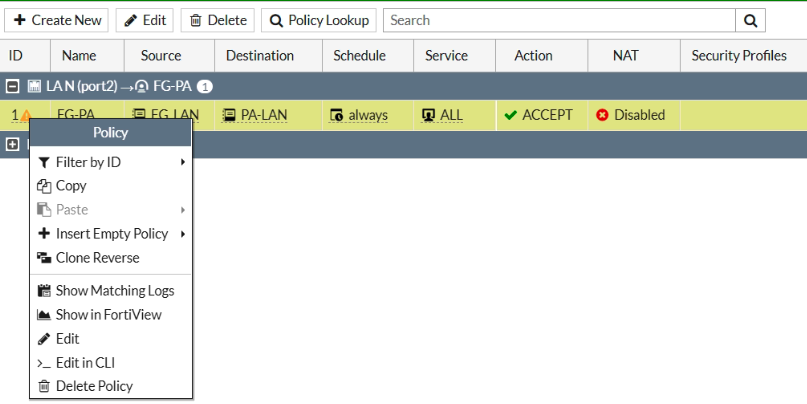
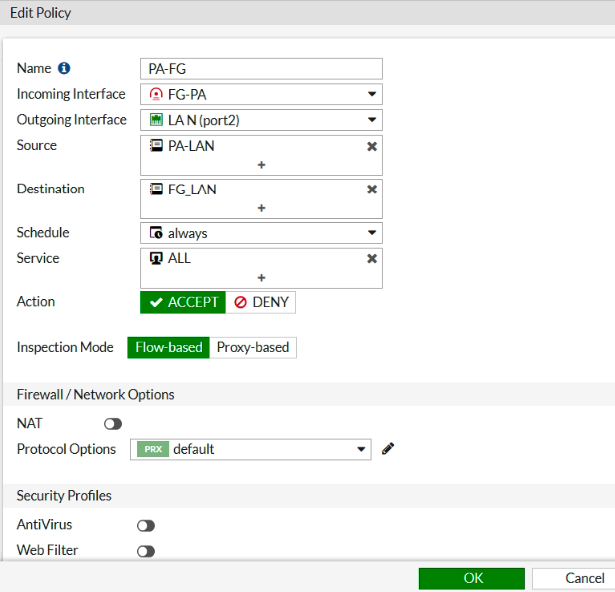
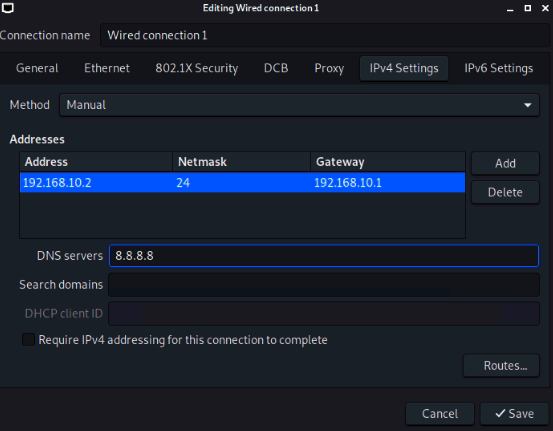
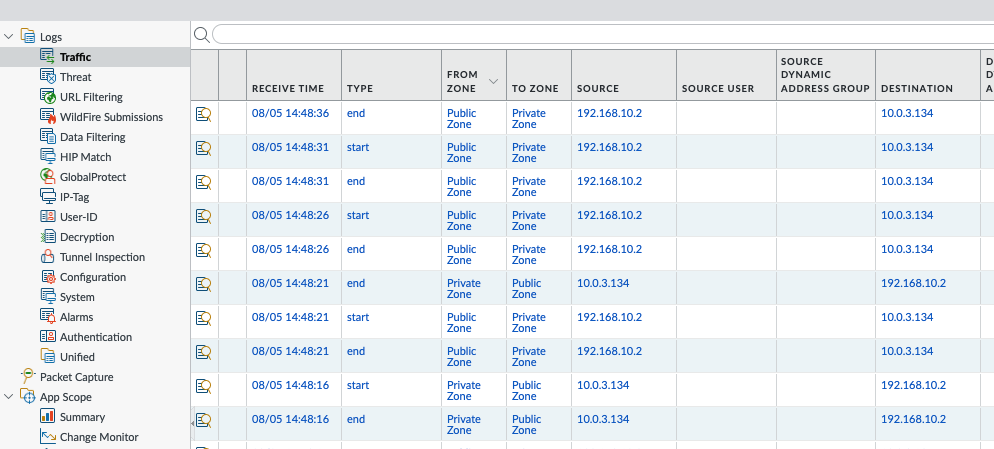
Ping from Kali machine to Windows instance (10.0.3.134).
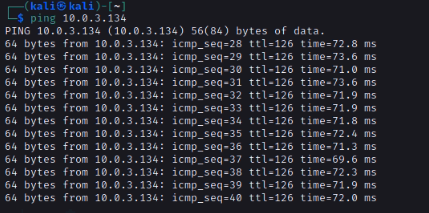
Ping from Windows instance to Kali machine (192.168.10.2).
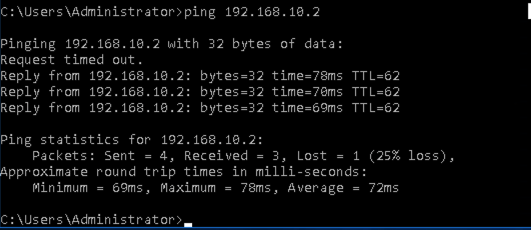
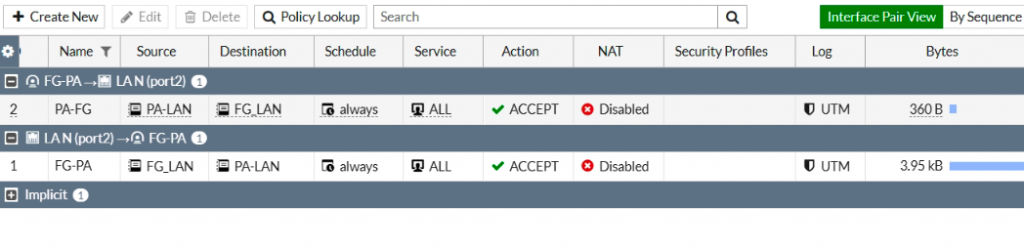
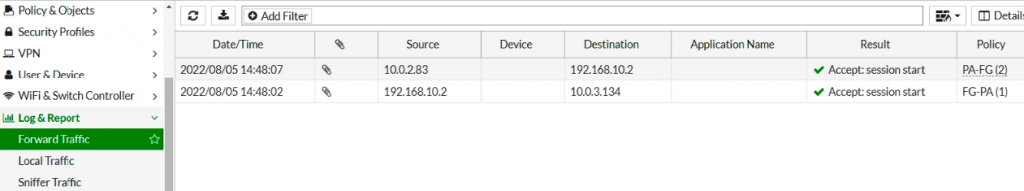
Back to Palo Alto in AWS. We can see the traffic from PA-LAN to FG-LAN and vice versa.
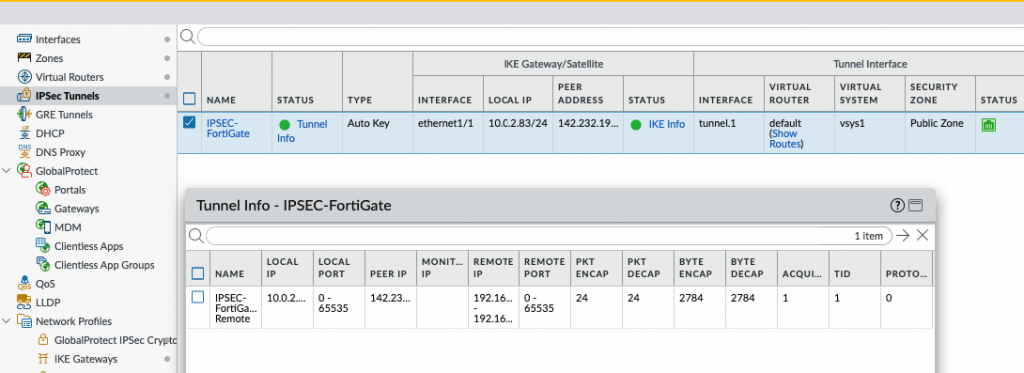
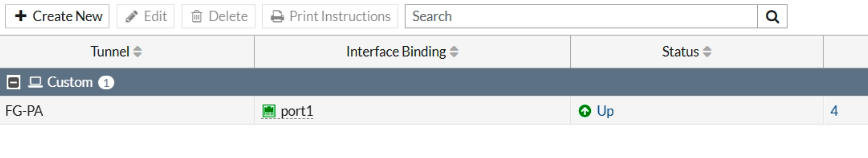
The Palo Alto IPSEC tunnel is UP.