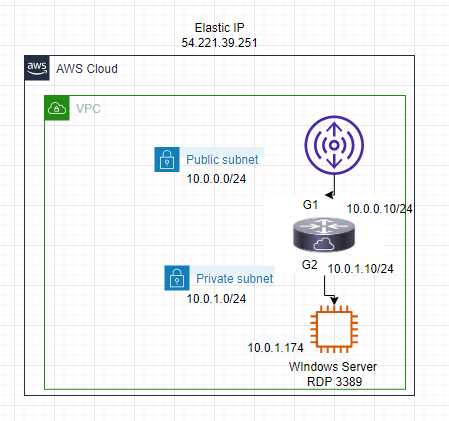
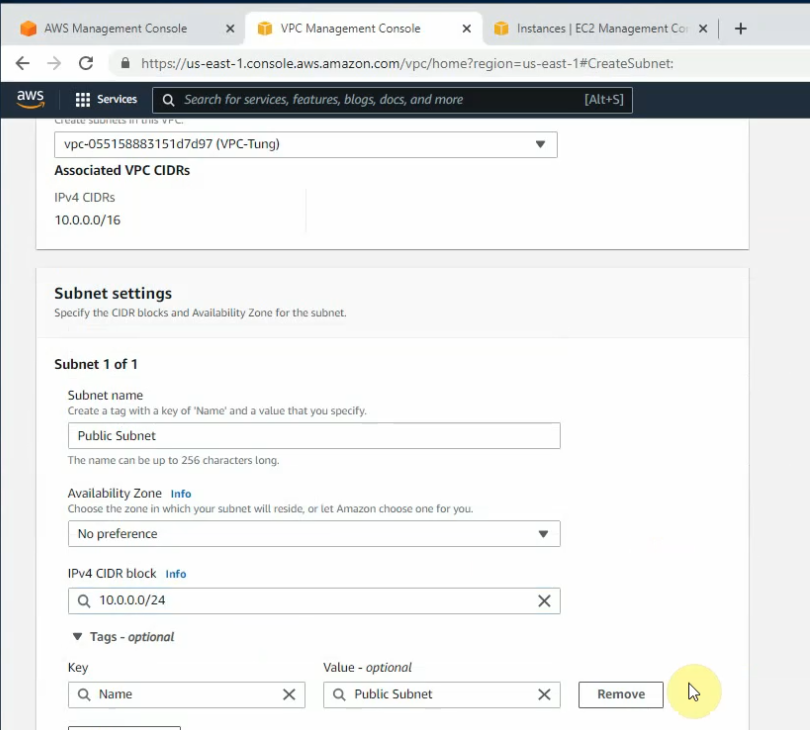
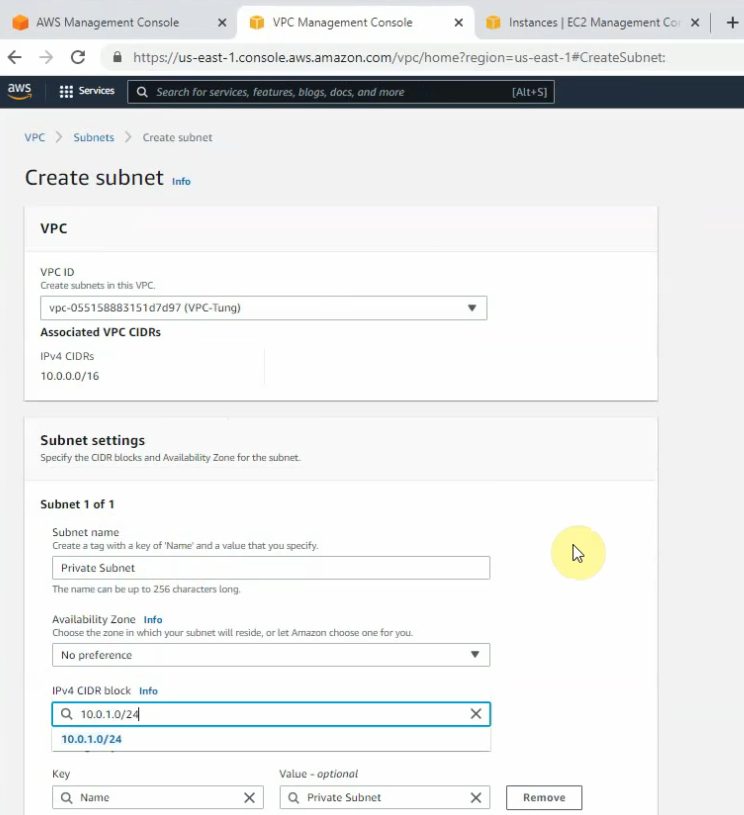
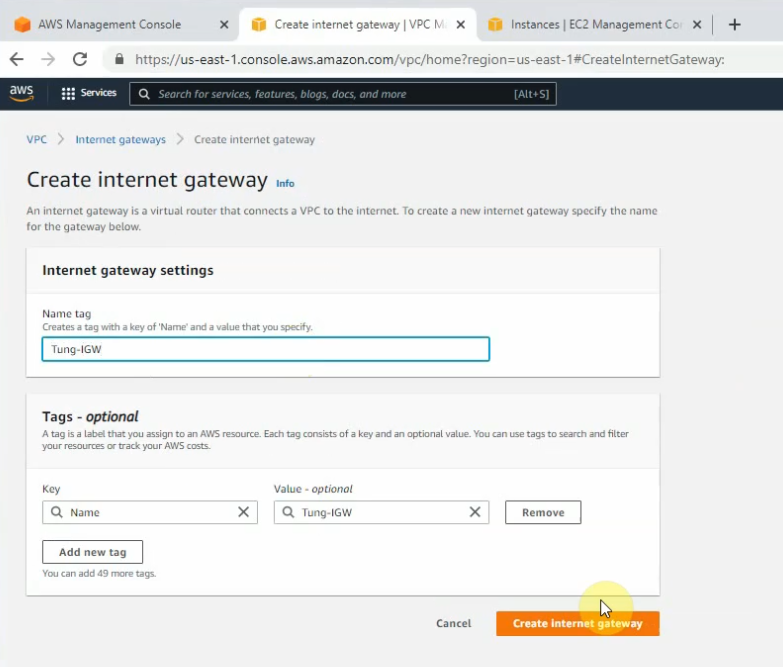
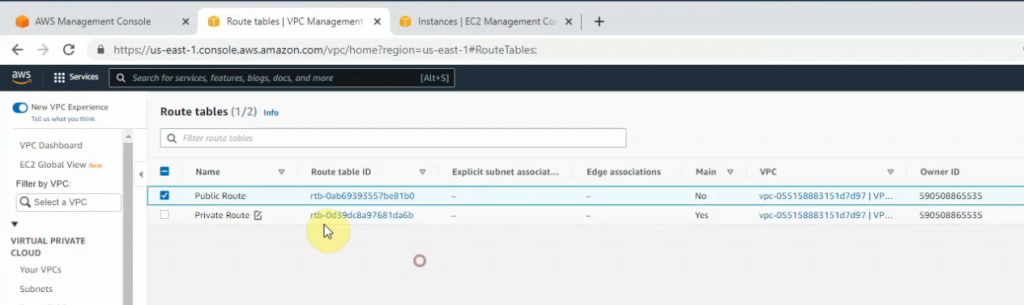
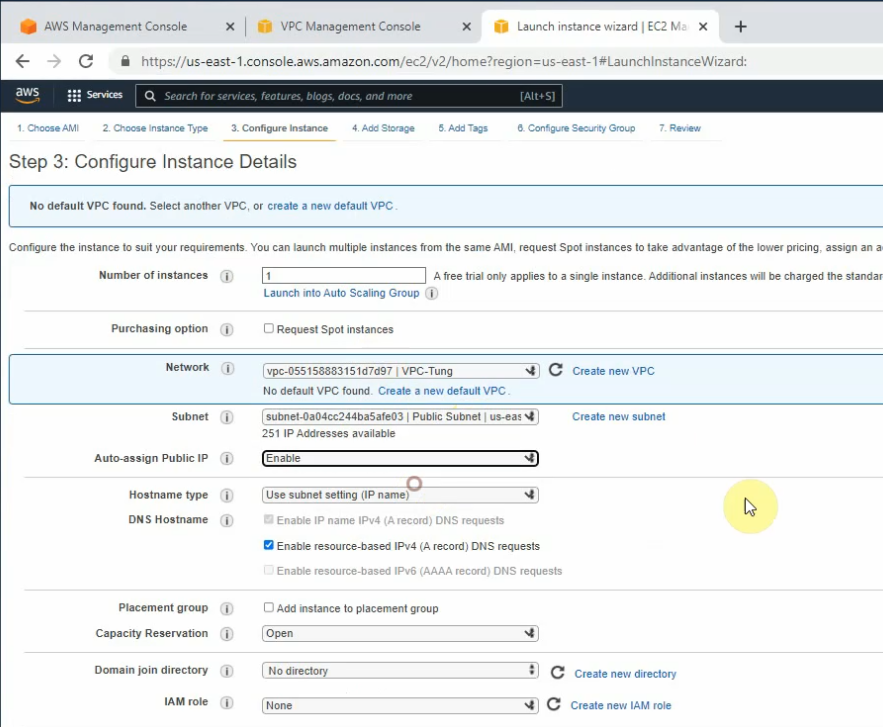
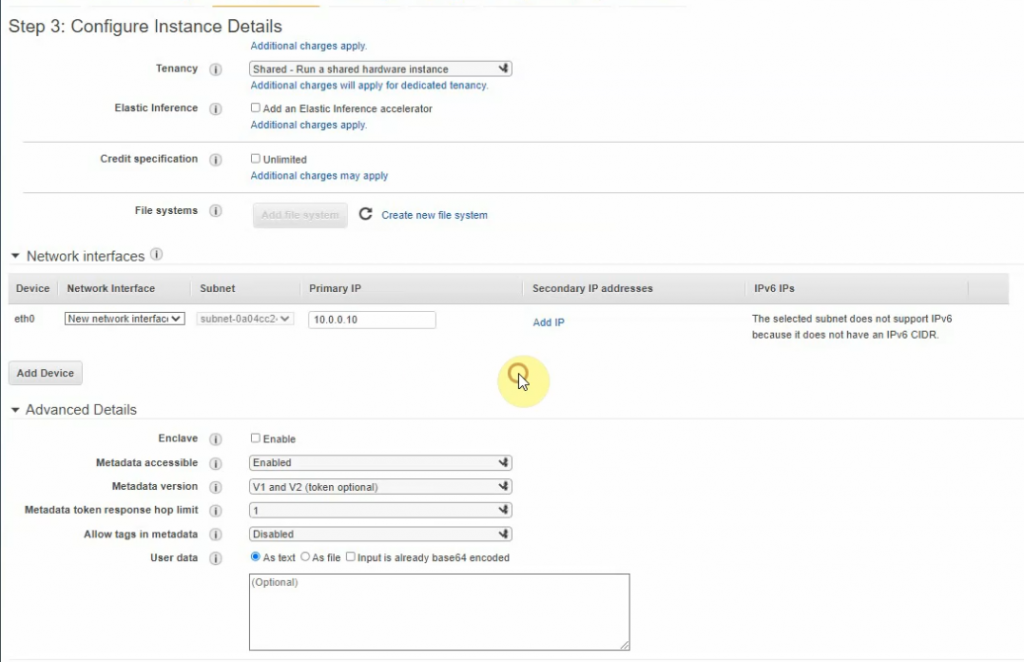
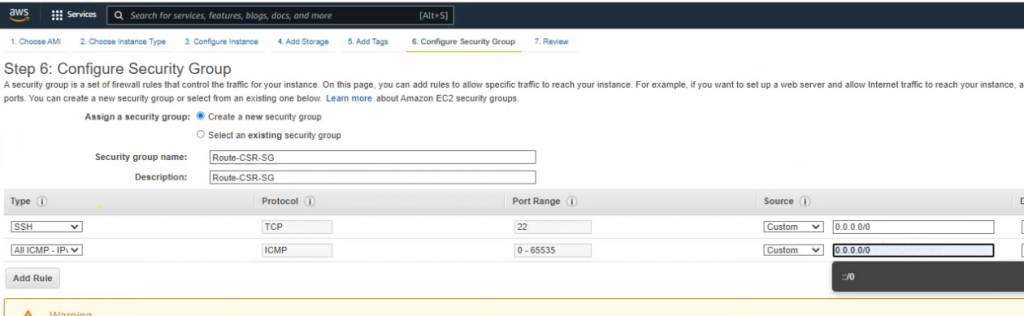
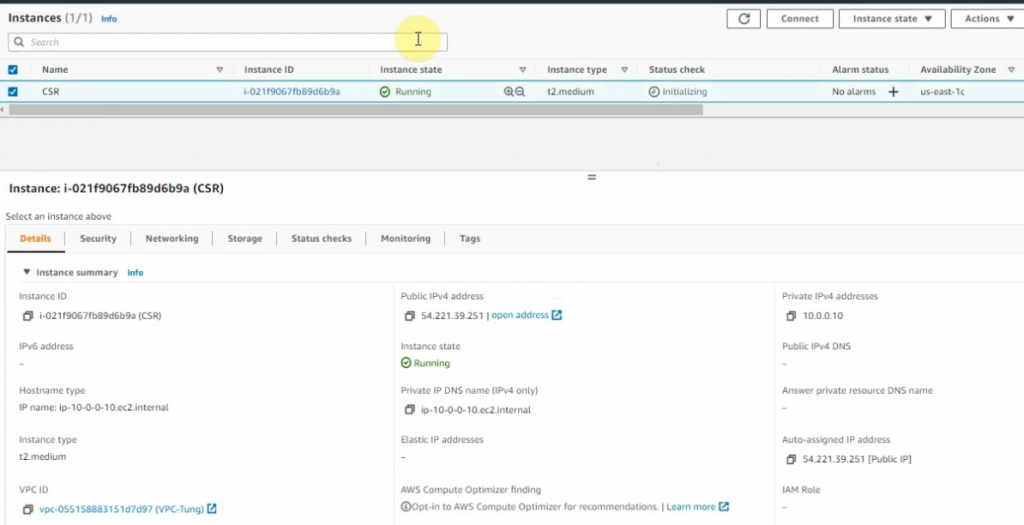
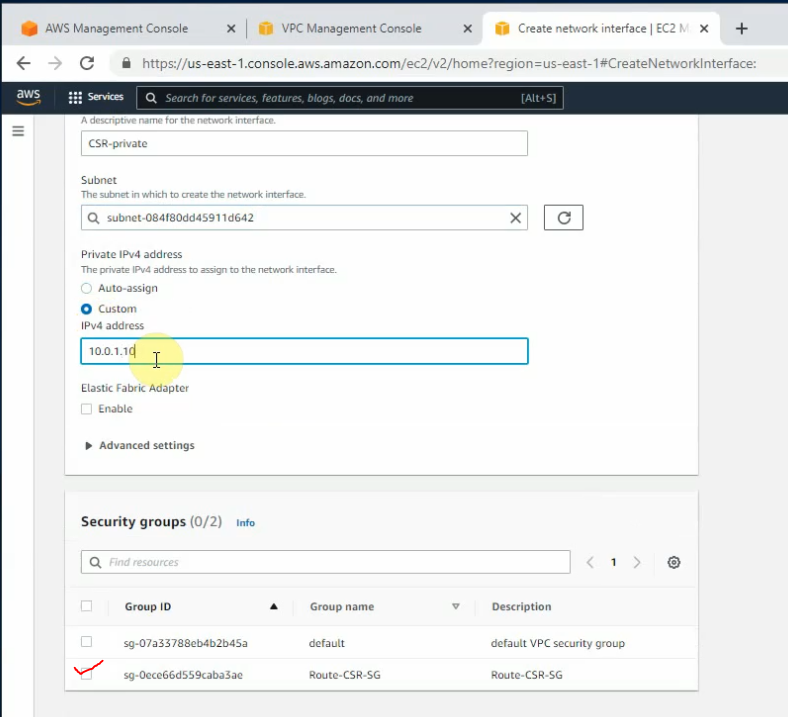
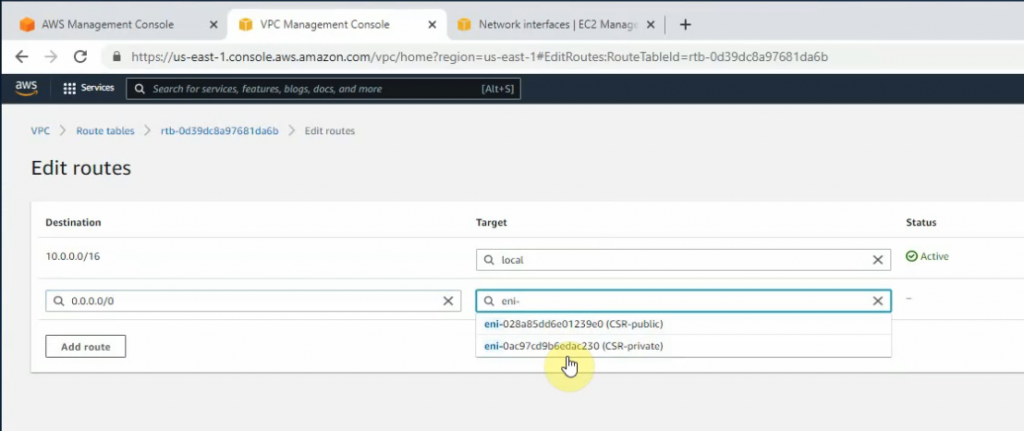
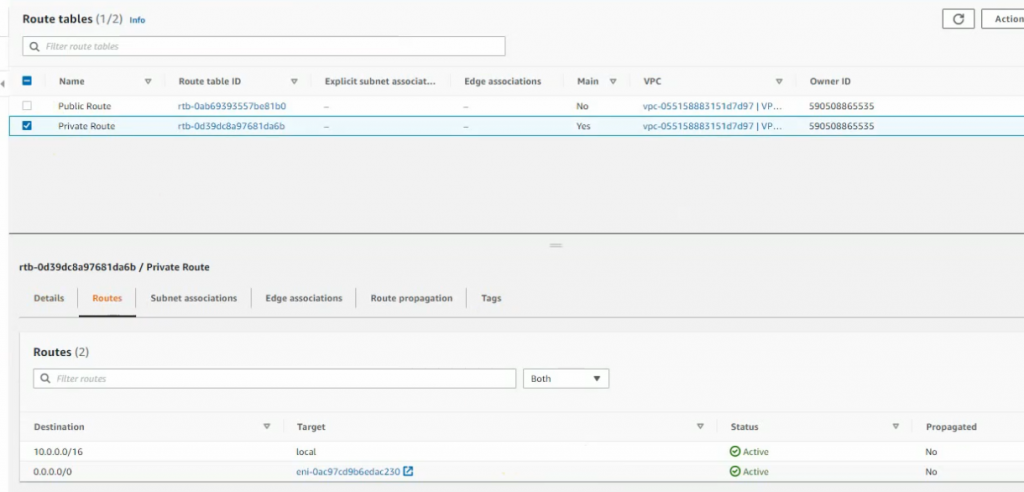
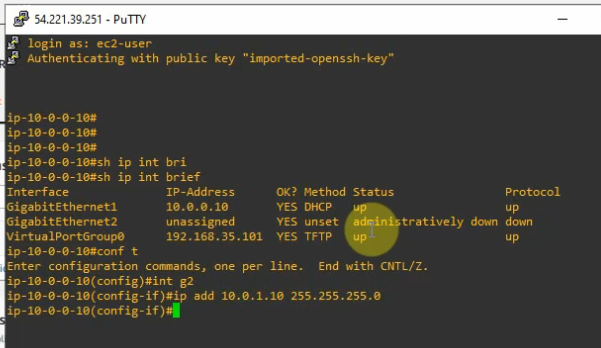
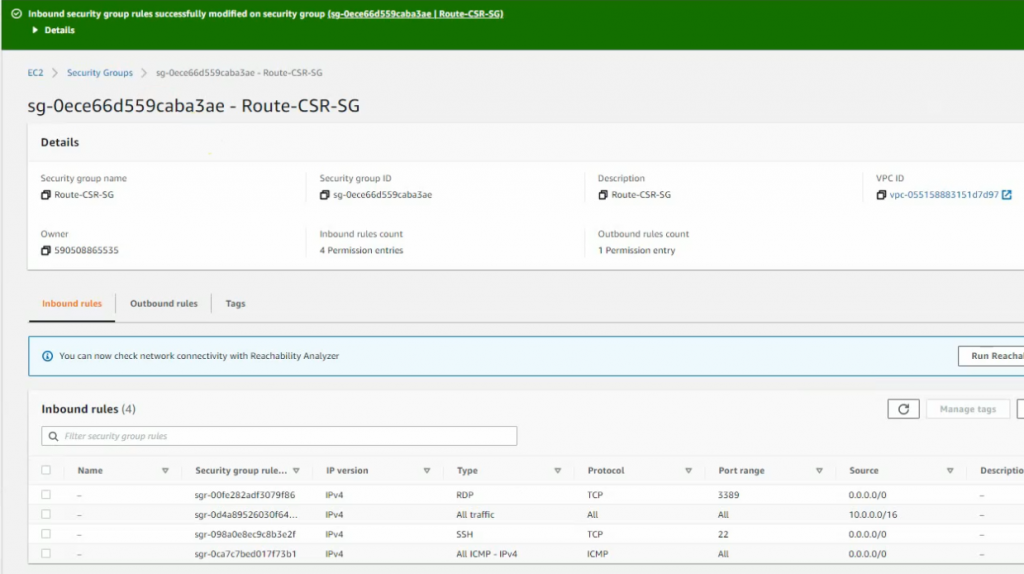
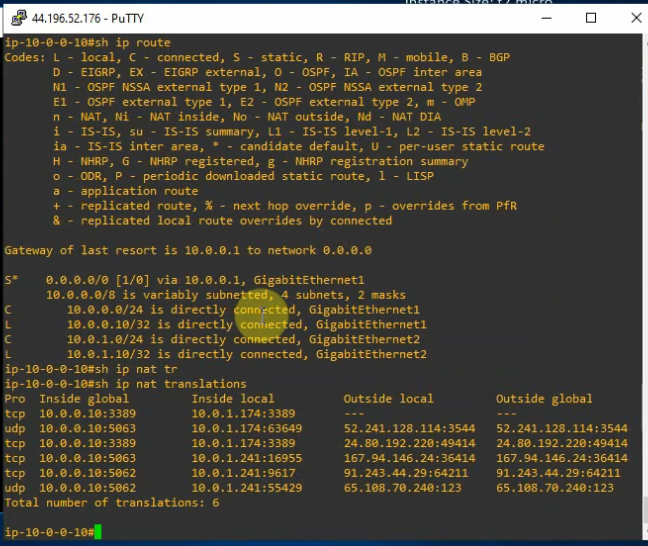
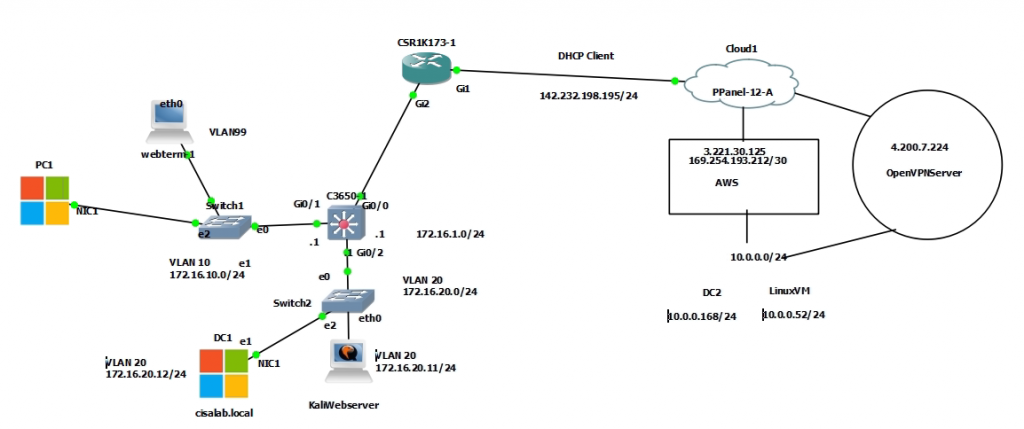
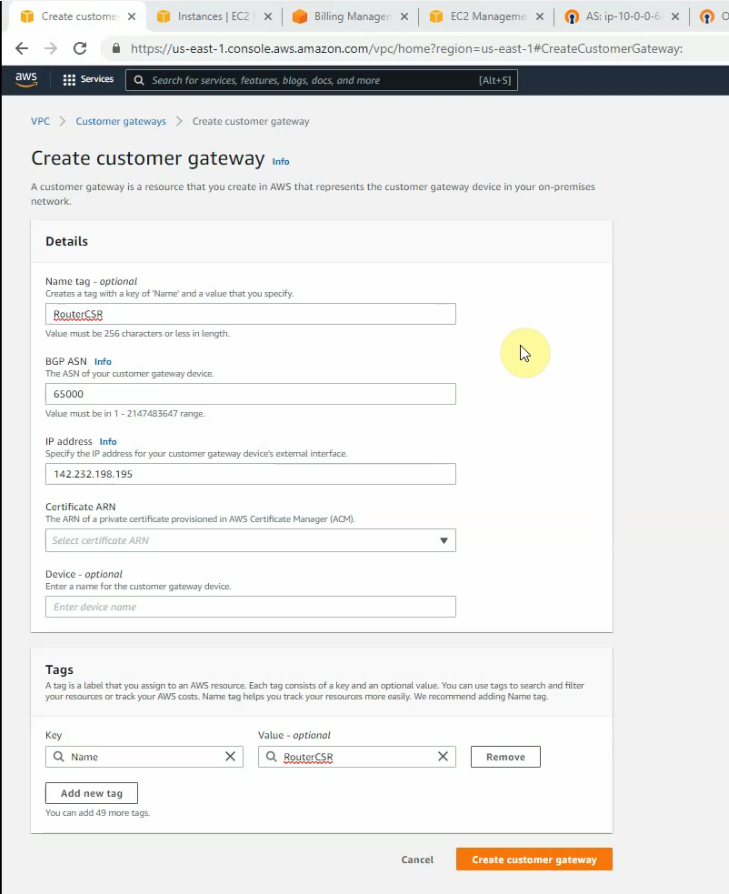
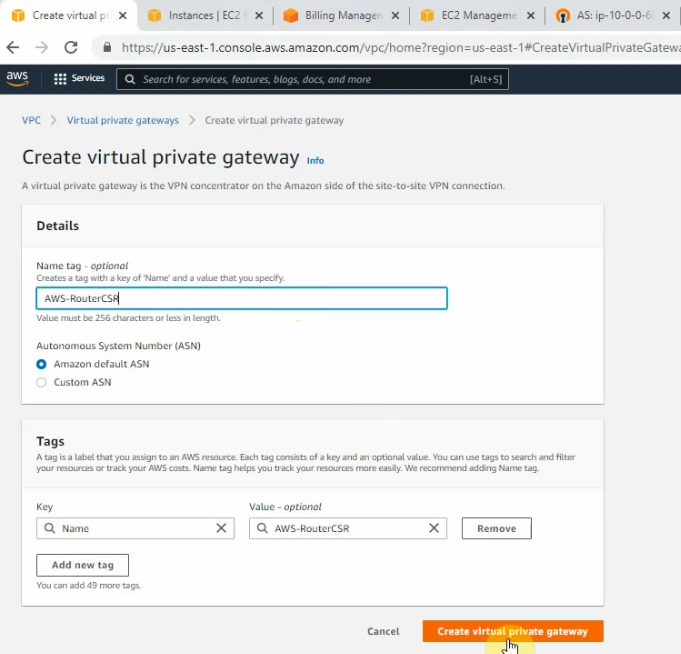
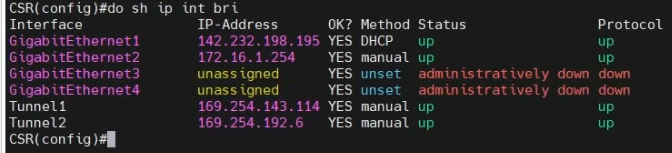
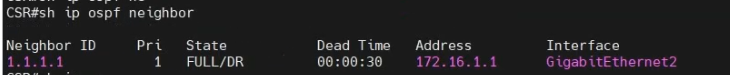
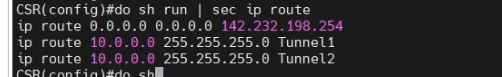
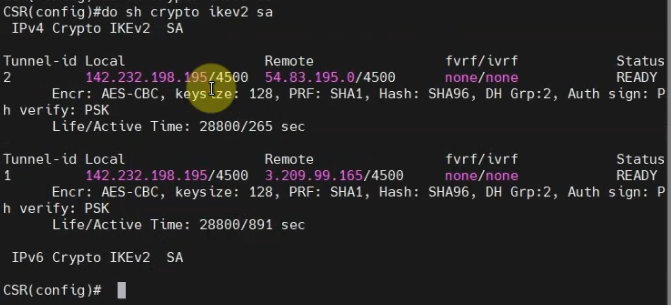
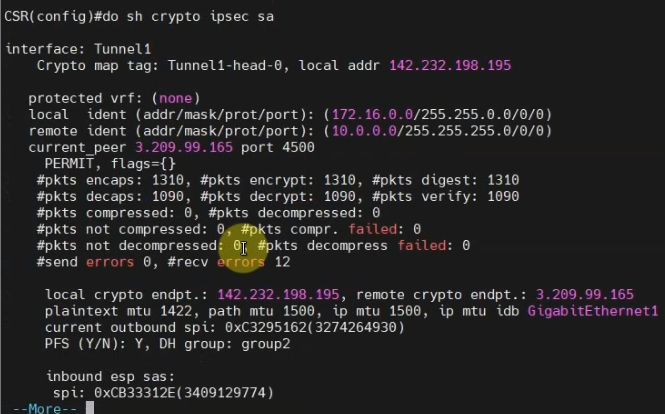
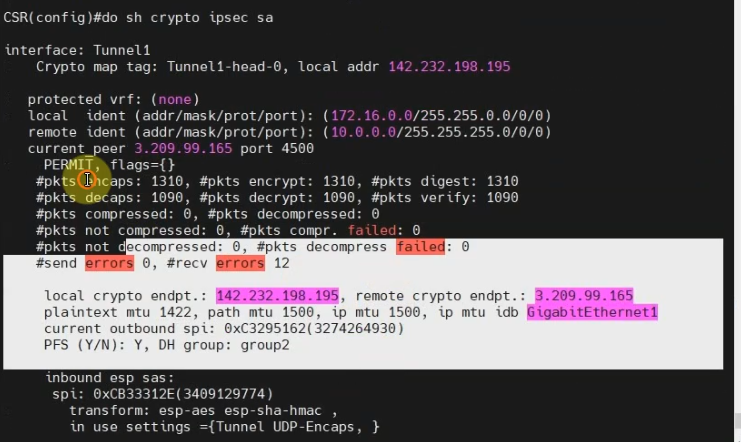
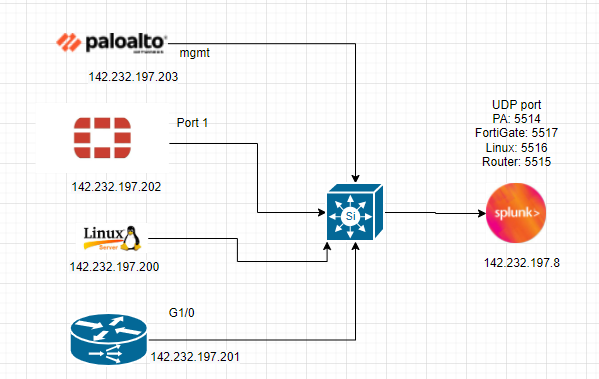
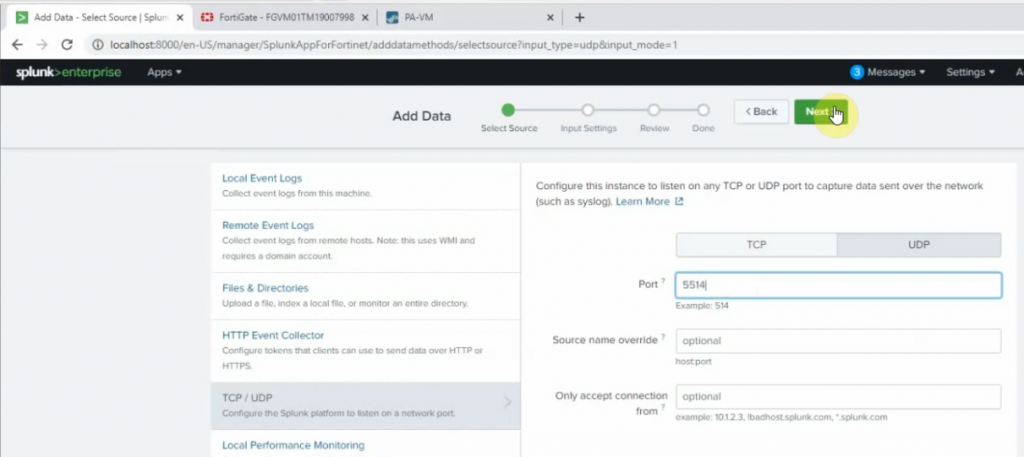
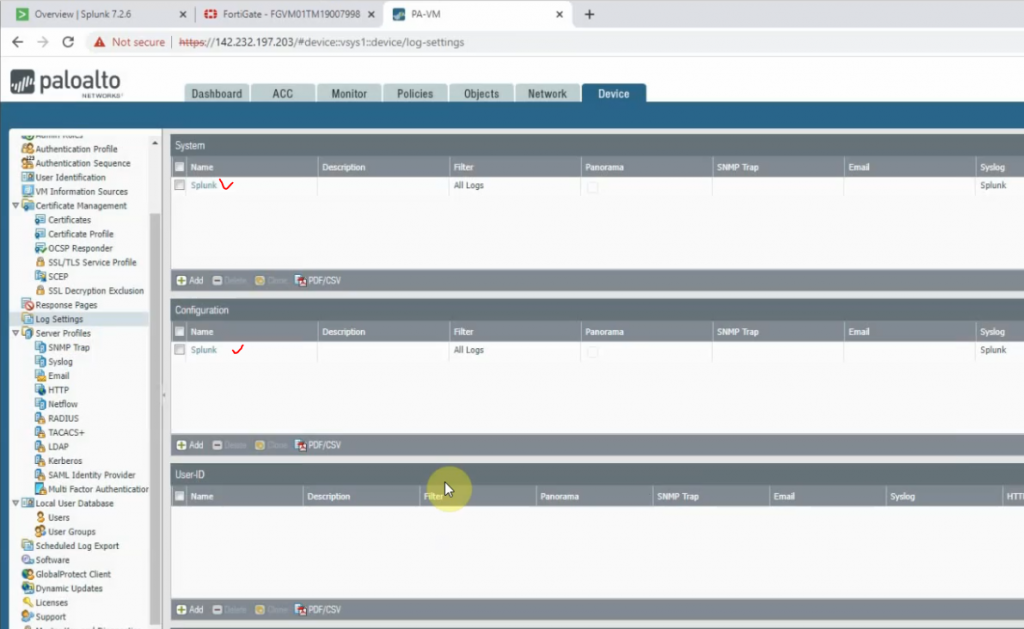
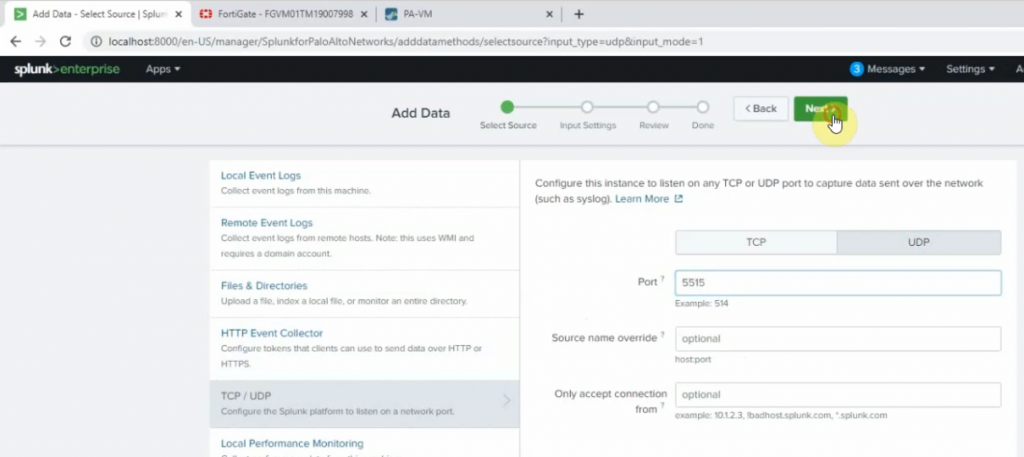
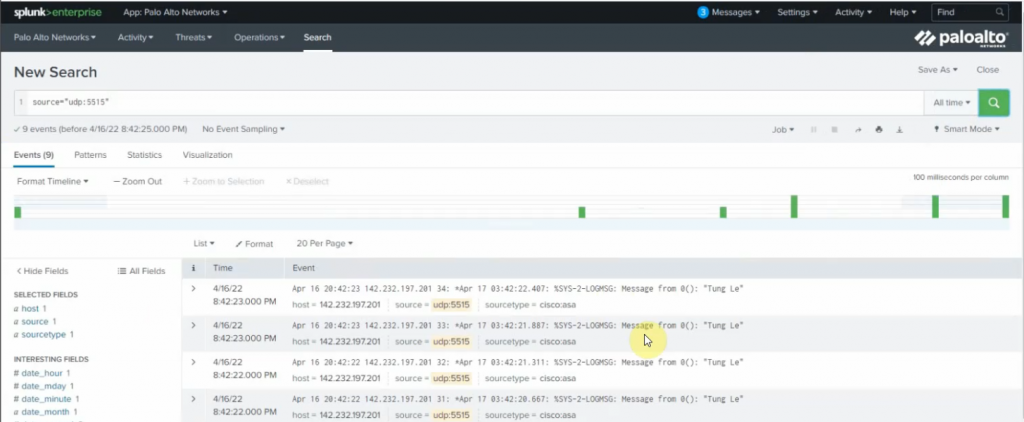
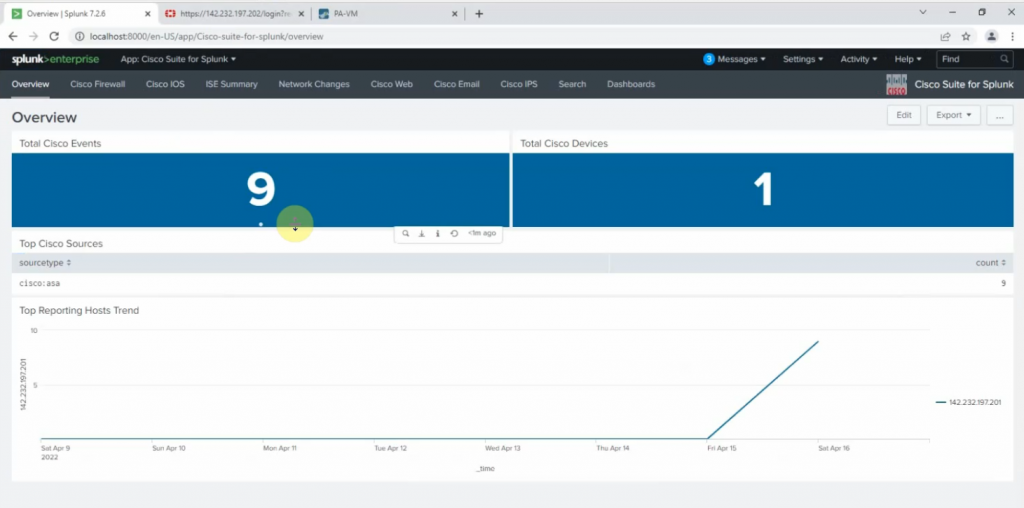
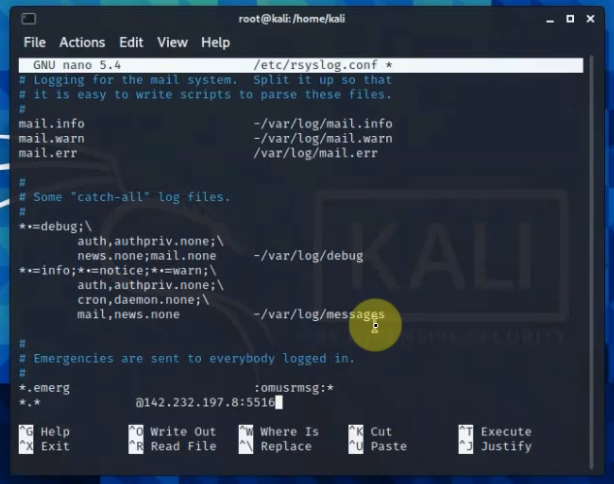
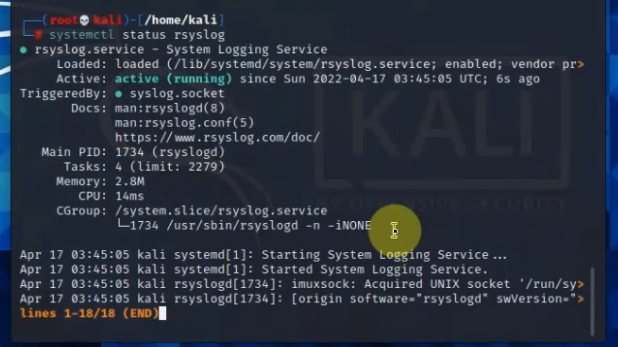
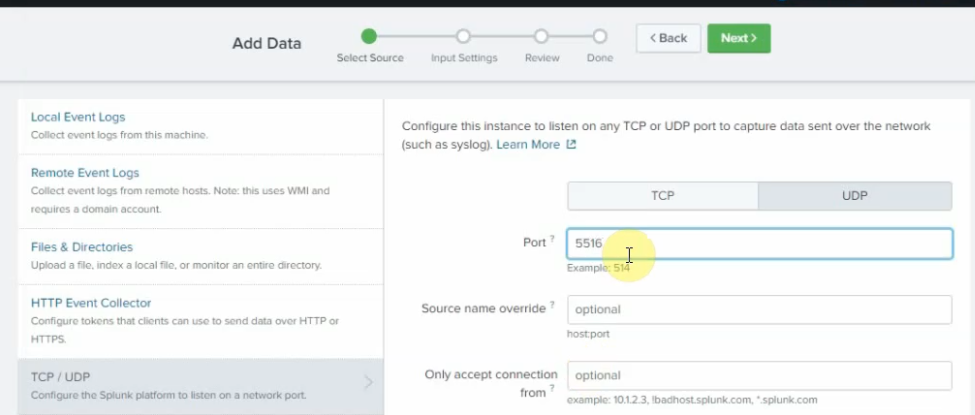
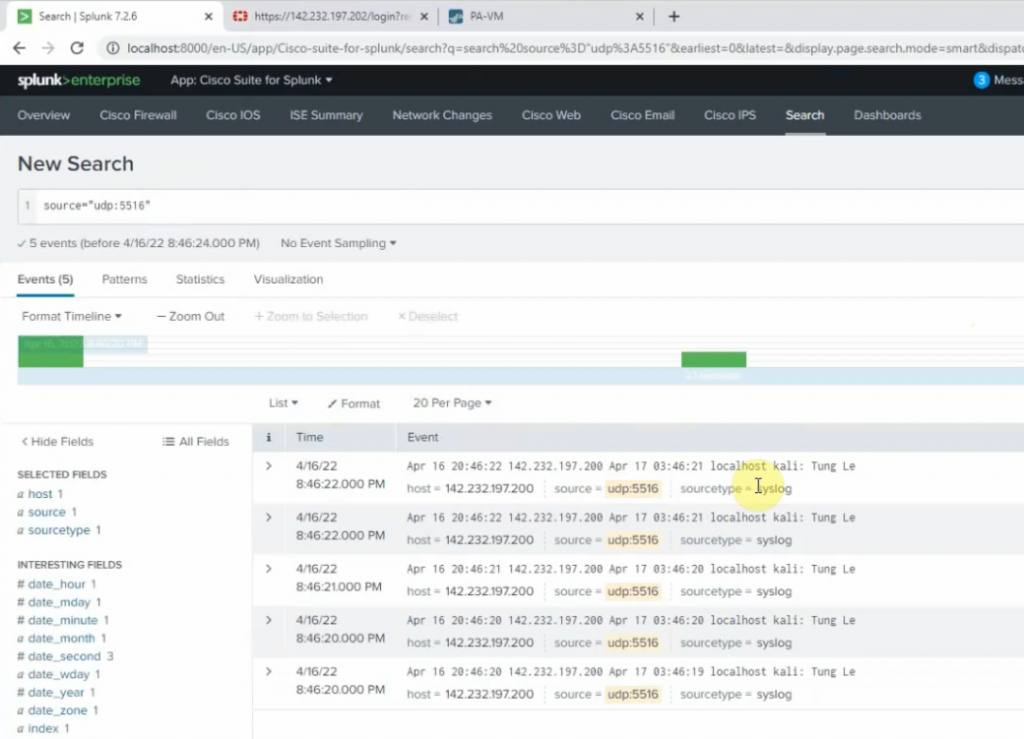
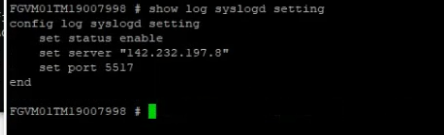
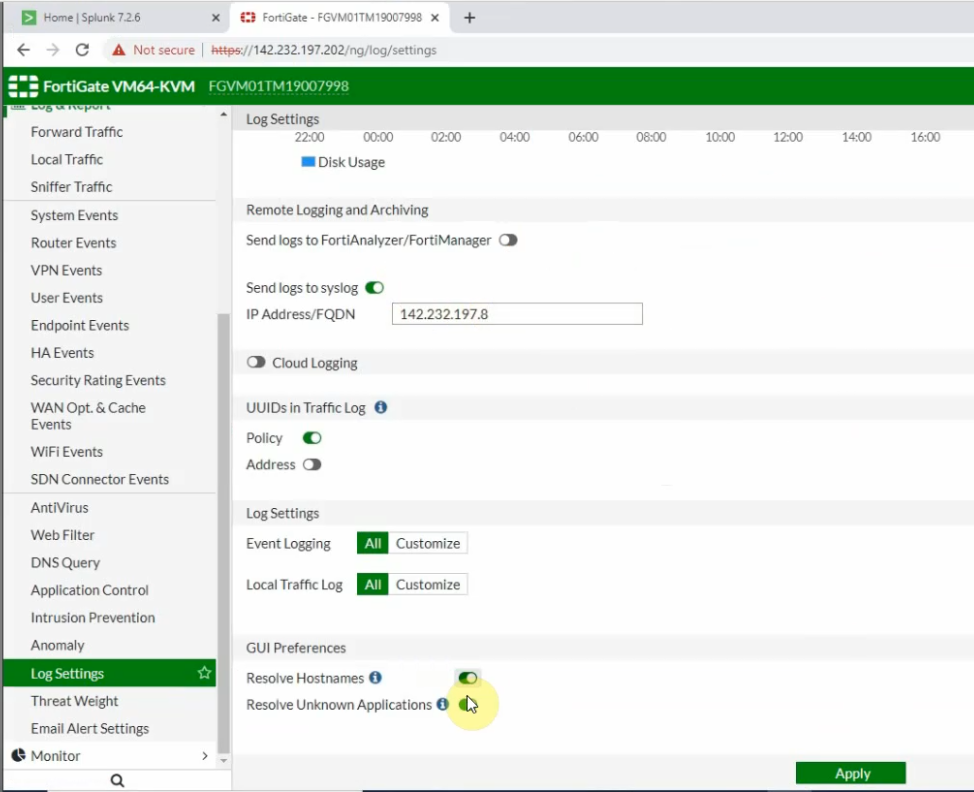
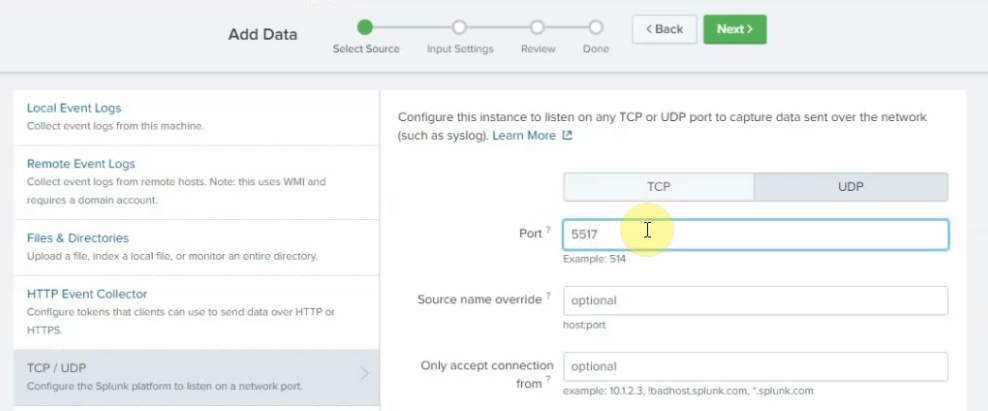
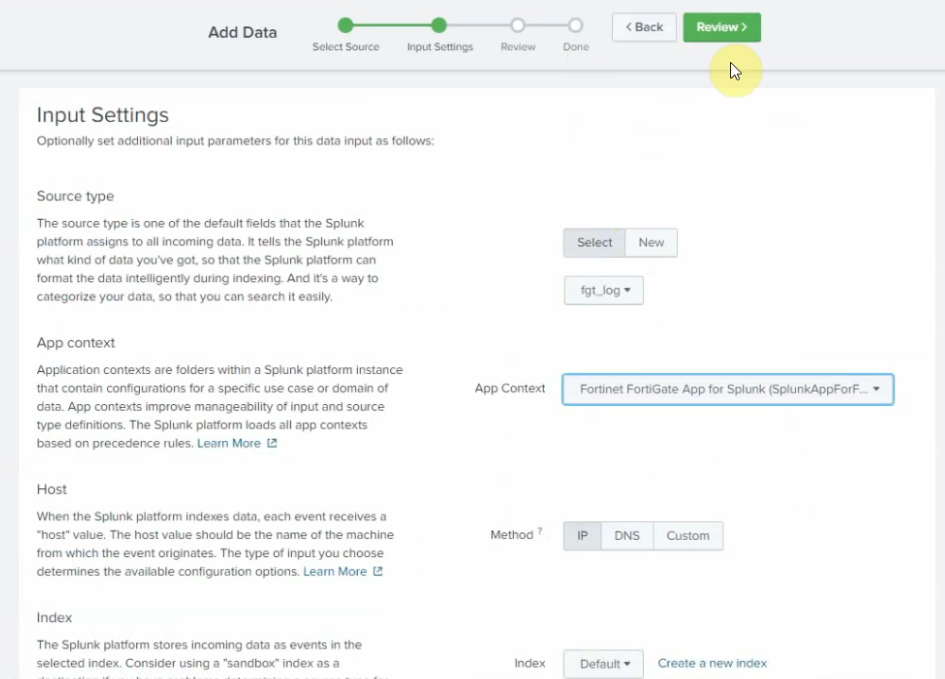
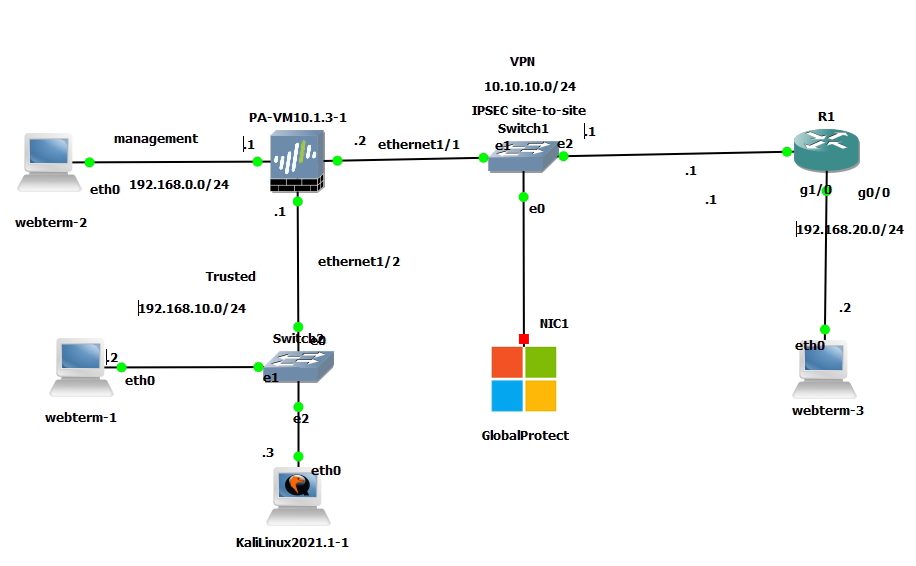
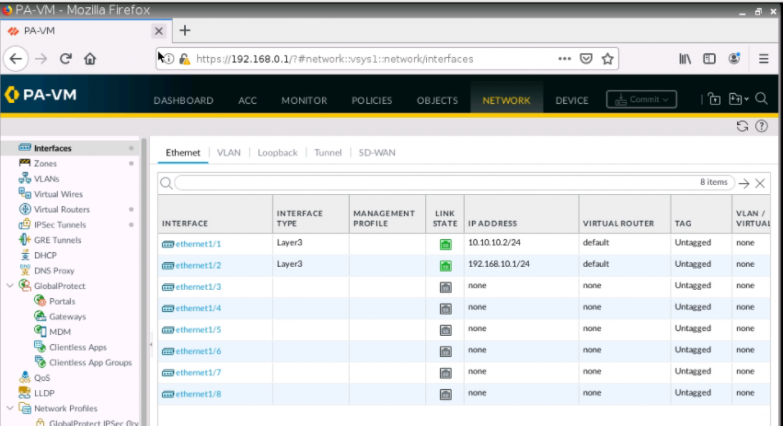
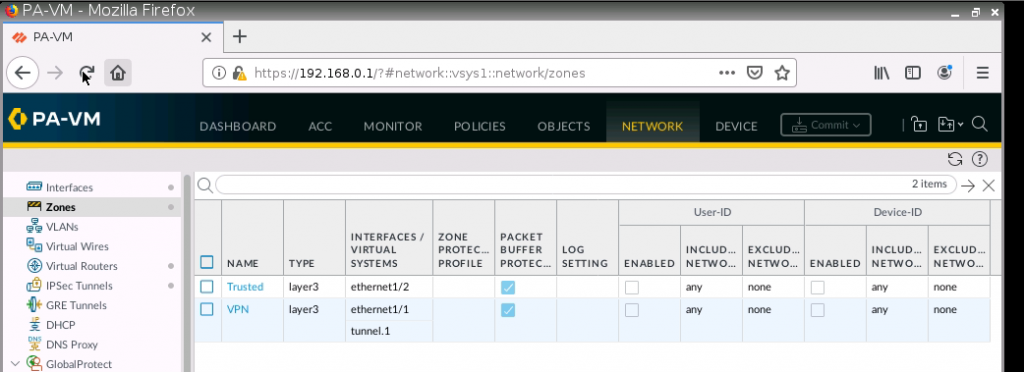
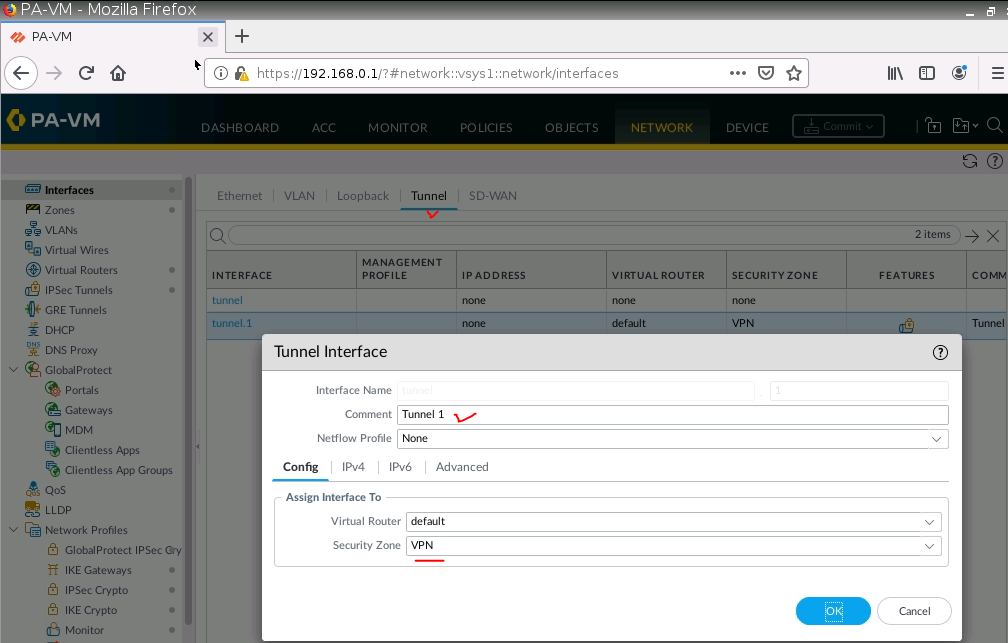
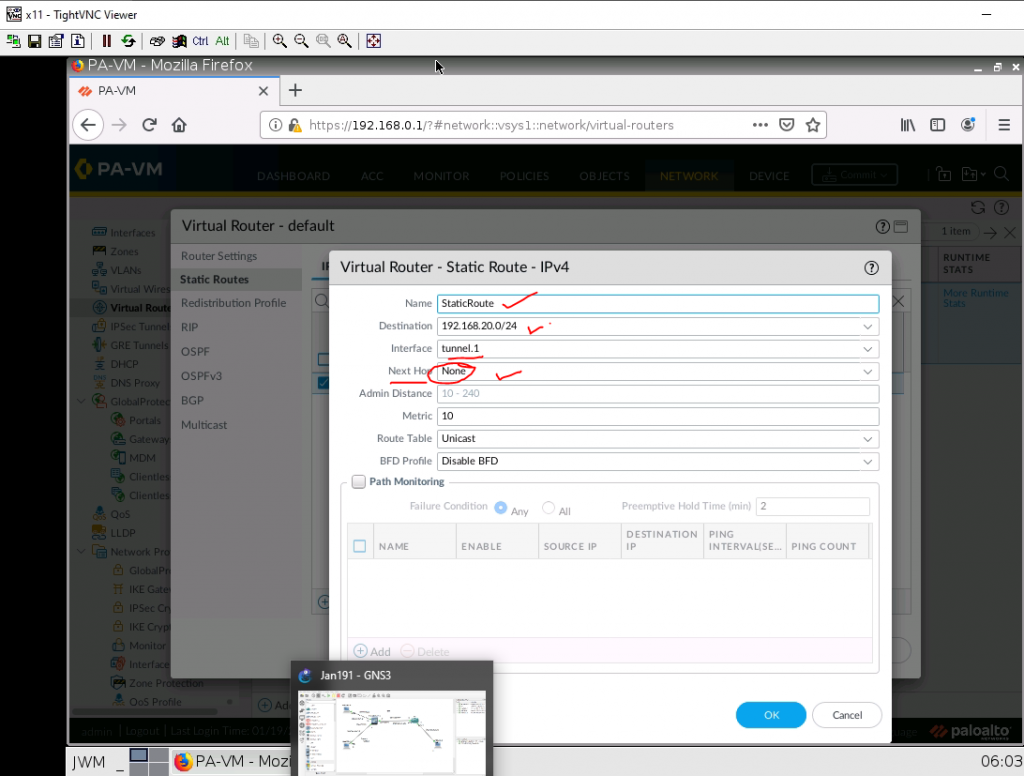
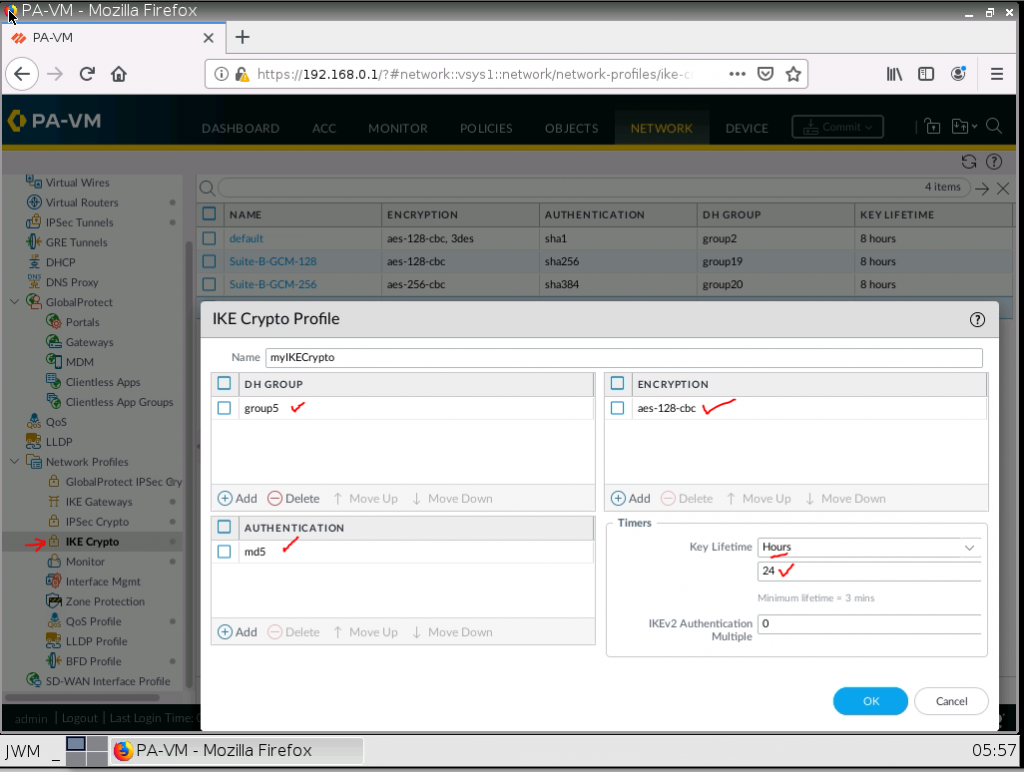
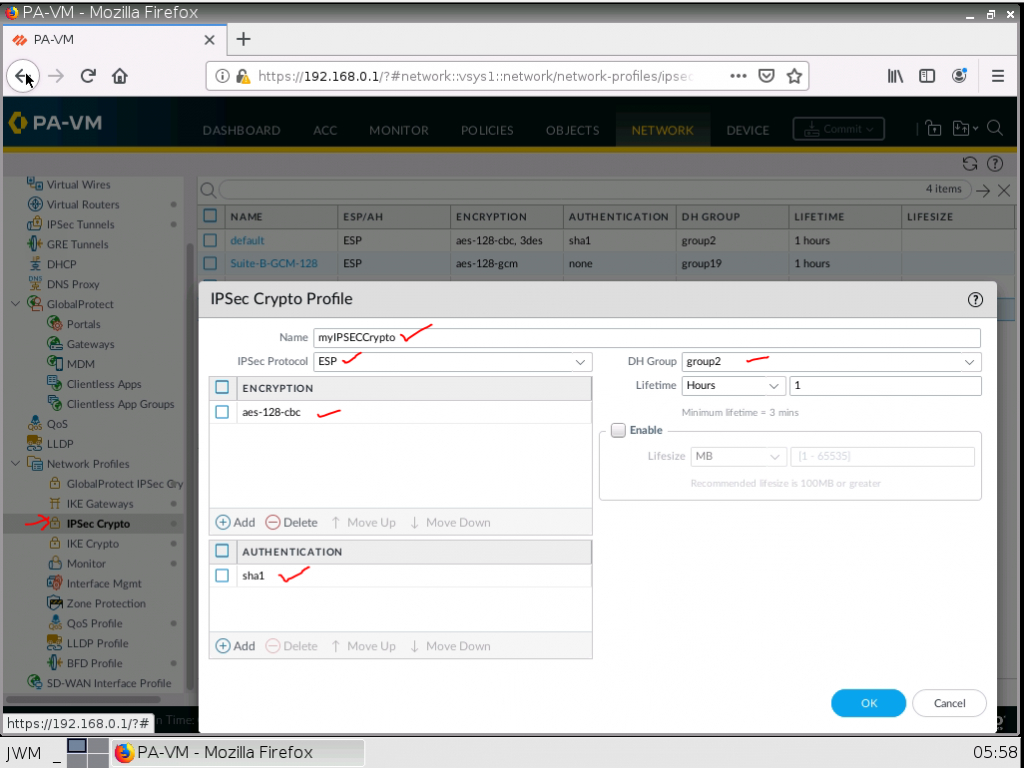
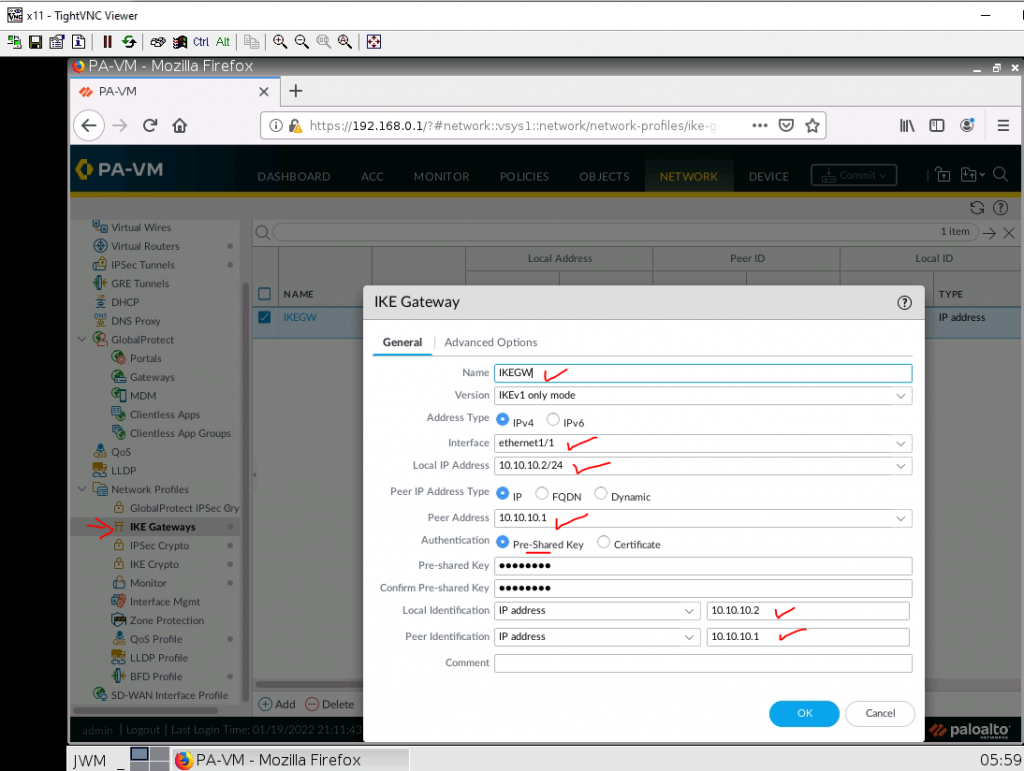
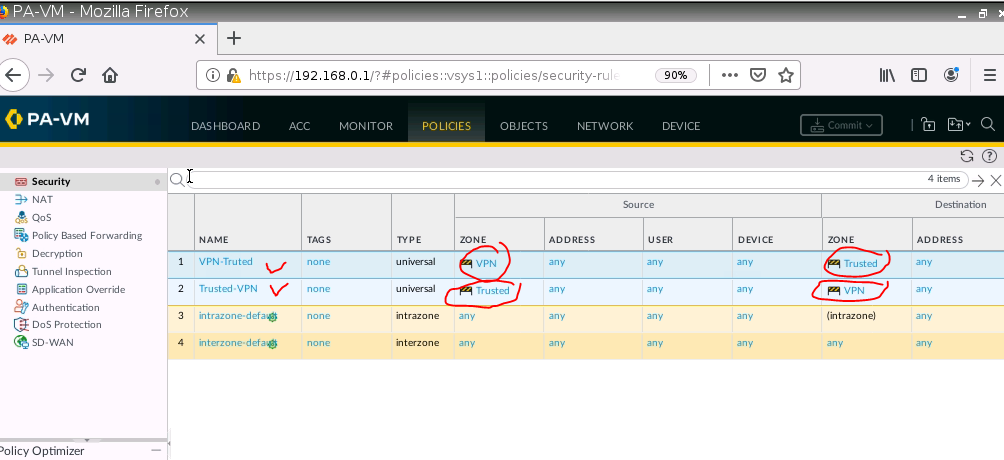
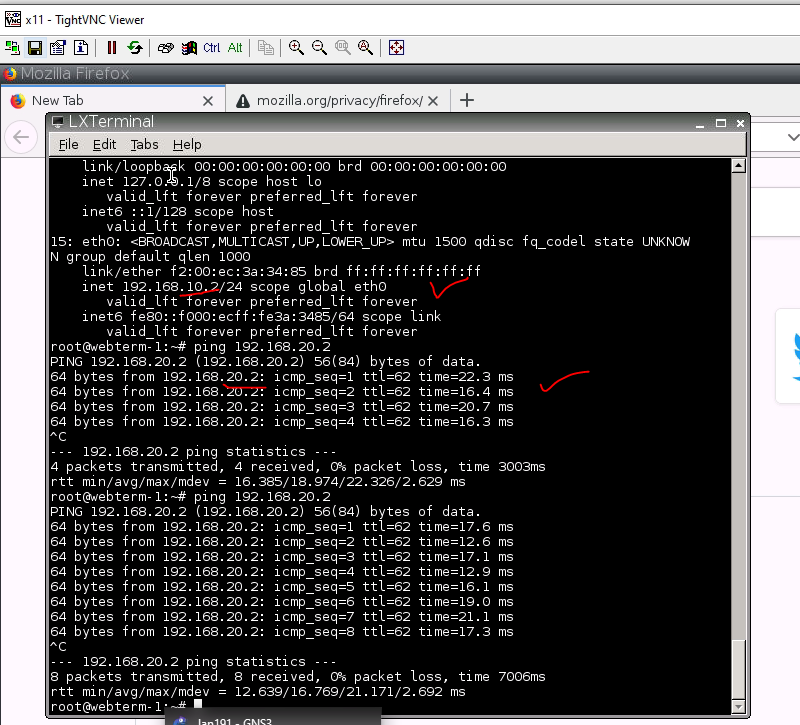
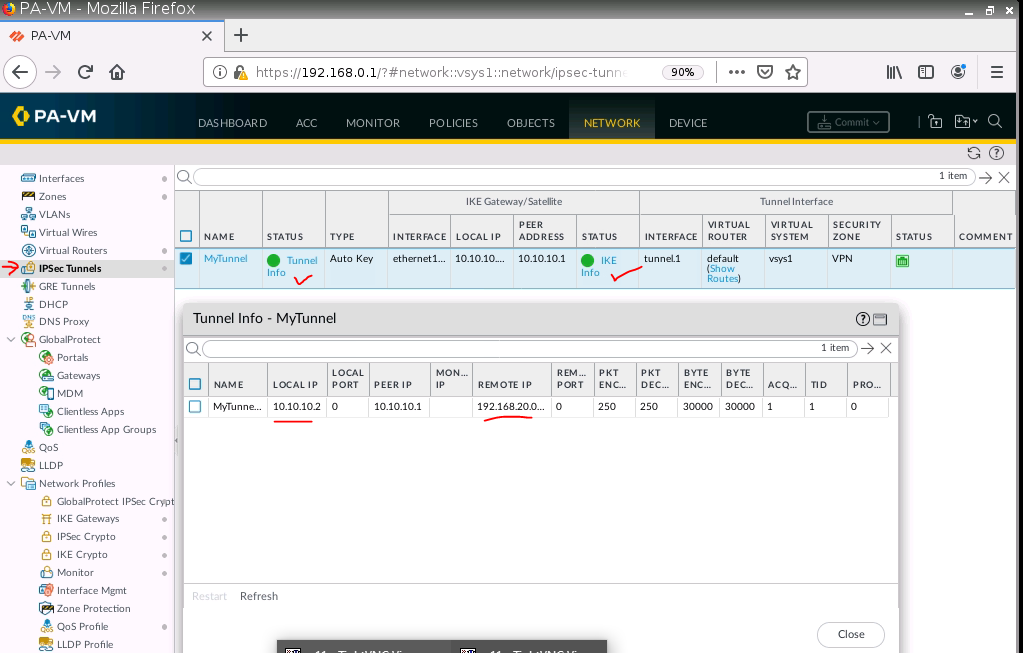
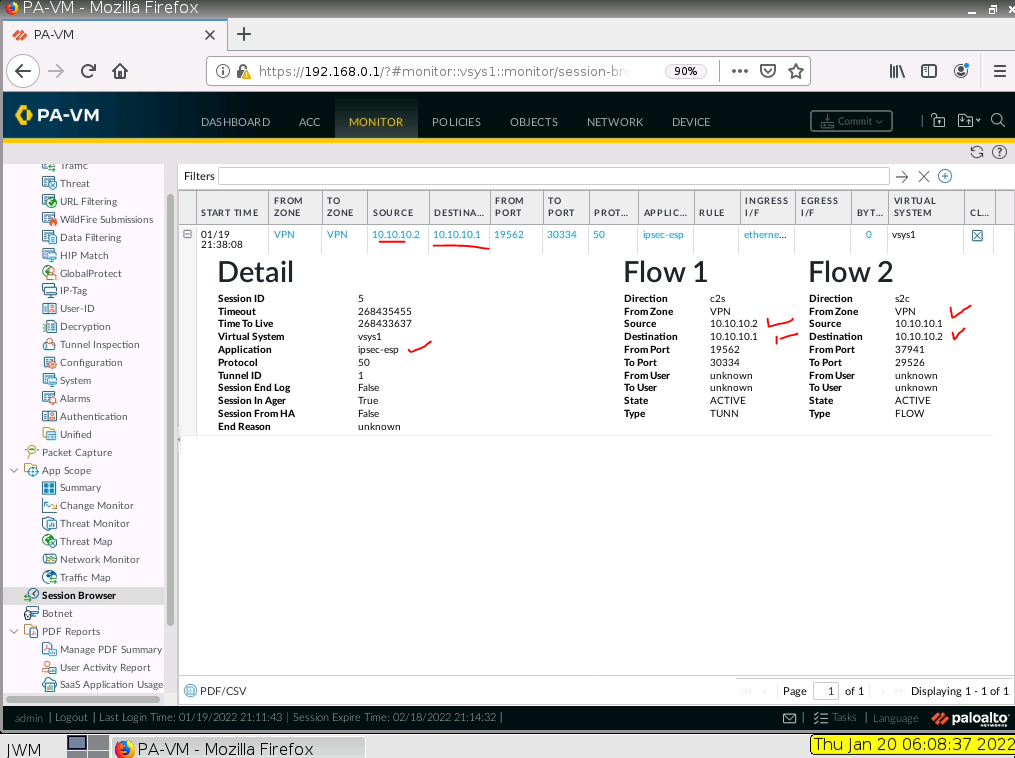
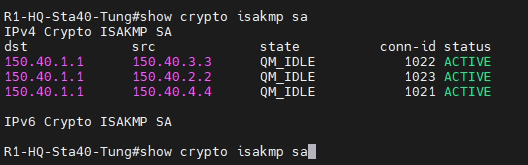
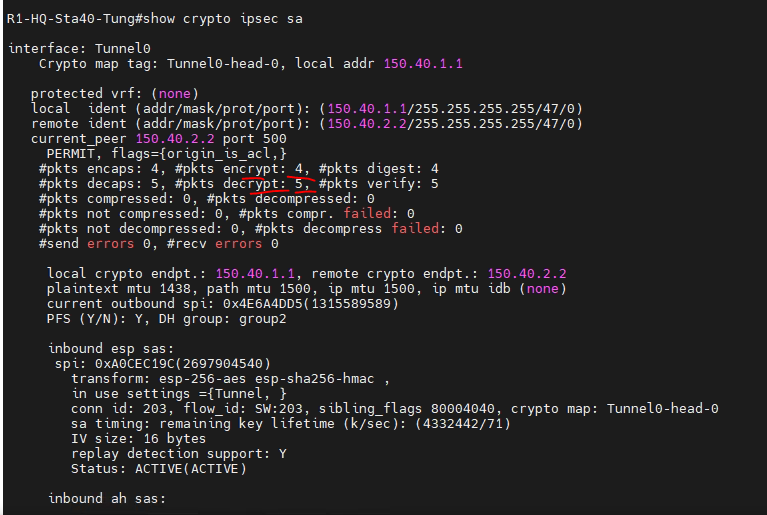
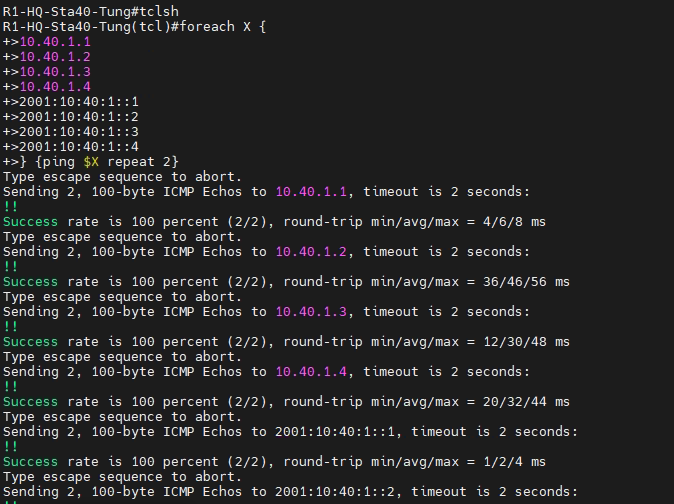
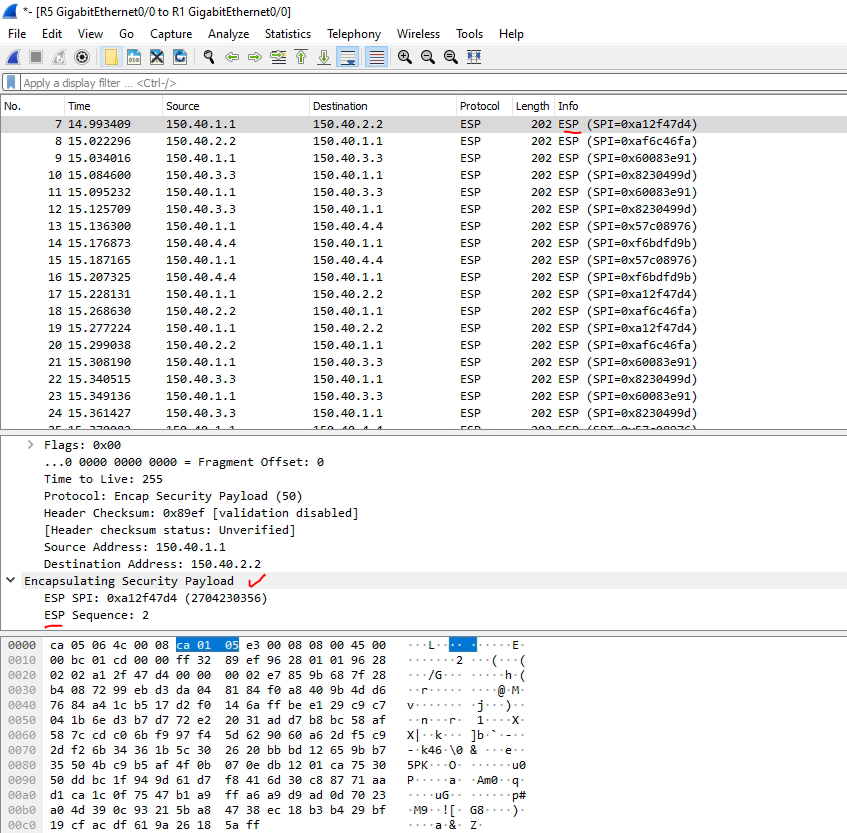
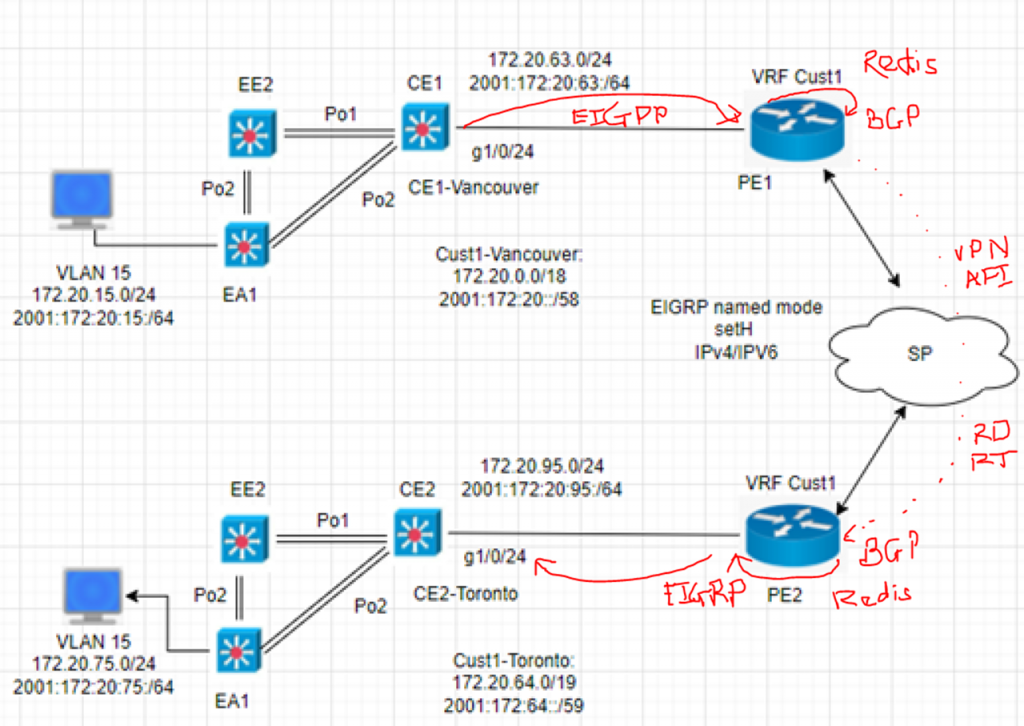
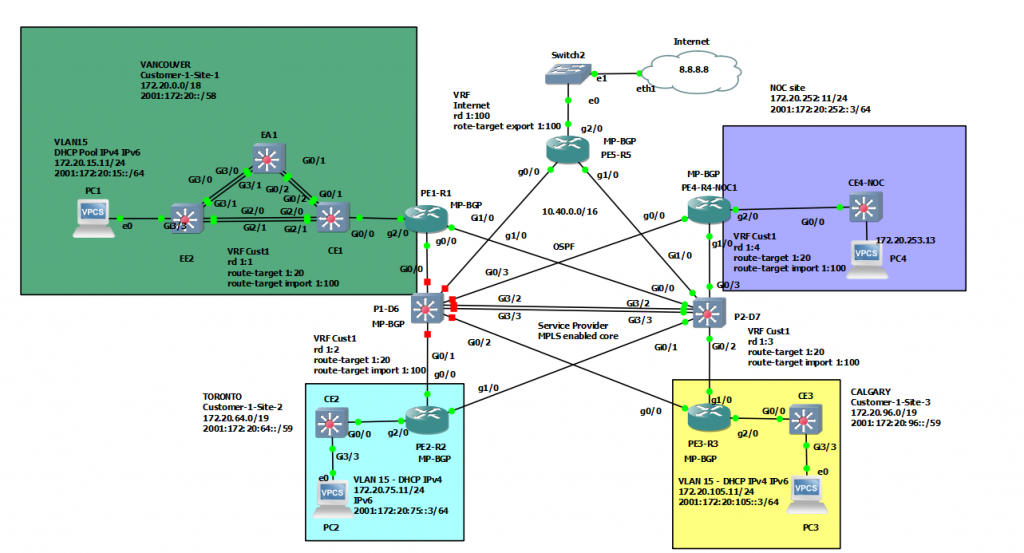
This is a diagram that I have used to implement the project.
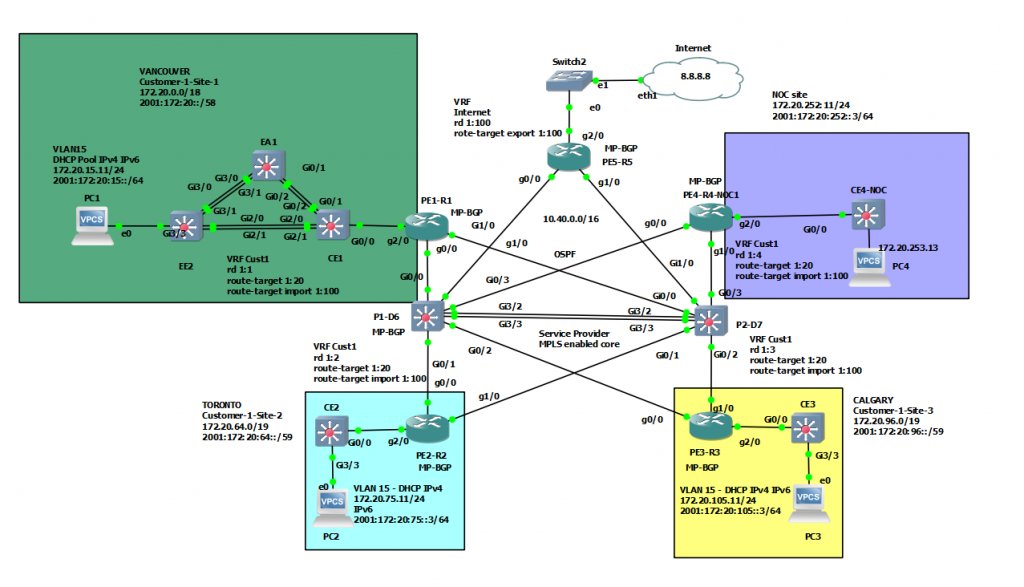
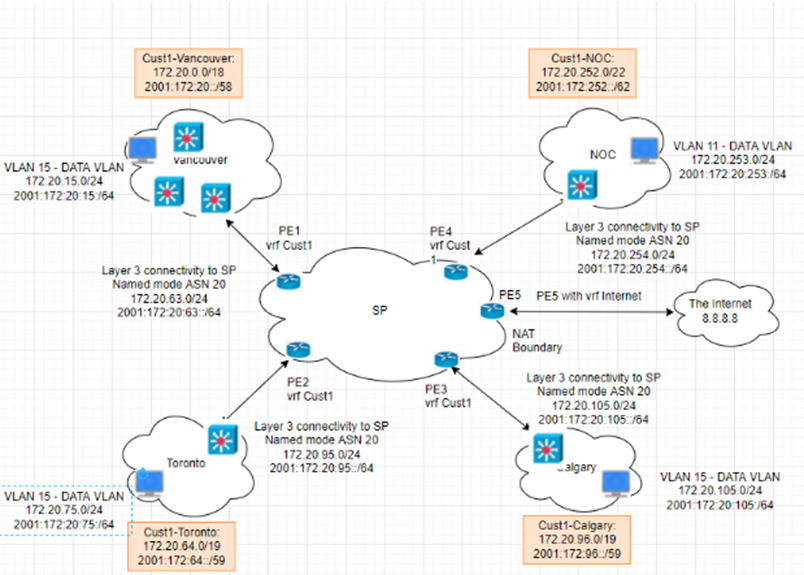
This topology is used to set up for a small national service provider to provide connectivity for customers located in Vancouver, Toronto, and Calgary. The Service Provider has a location for shared services location to act as NOC by all clients. All sites have centralized Internet access via an MPLS-enabled core network in Vancouver head quarter. The design must meet the following requirements:
- Connectivity, Security and traffic separation, Reliability
- Access to the shared services
- Secure Internet Access
- Use Layer 2 technologies: VLANs/VTP/Trunks/Etherchannel/STP
- User Layer 3 technologies: Dynamic routing/MP-BGP/NAT/VPNs/MPLS/VRF/6VPE/PE-CE routing/ Route redistribution/RADIUS/TACACS
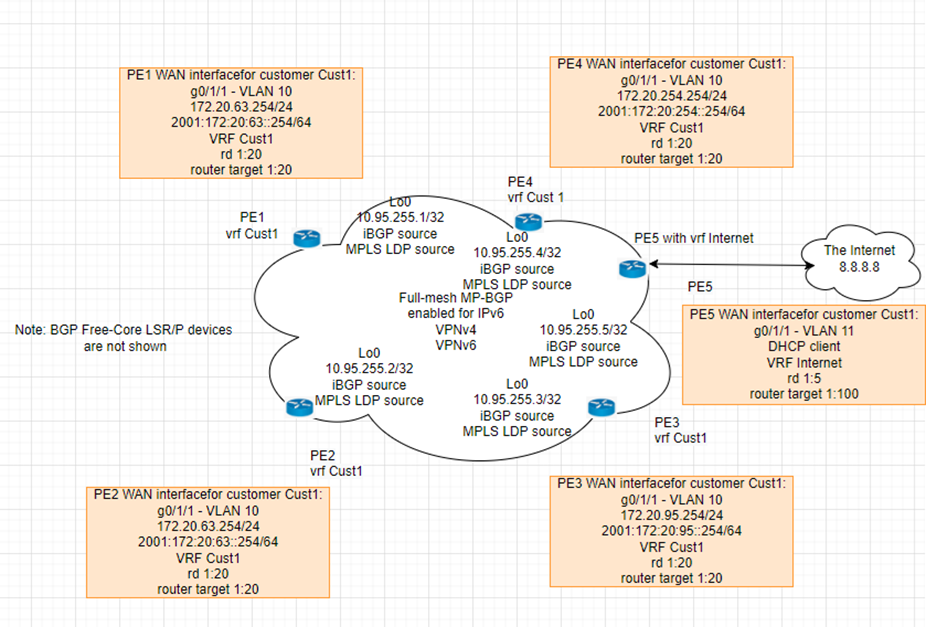
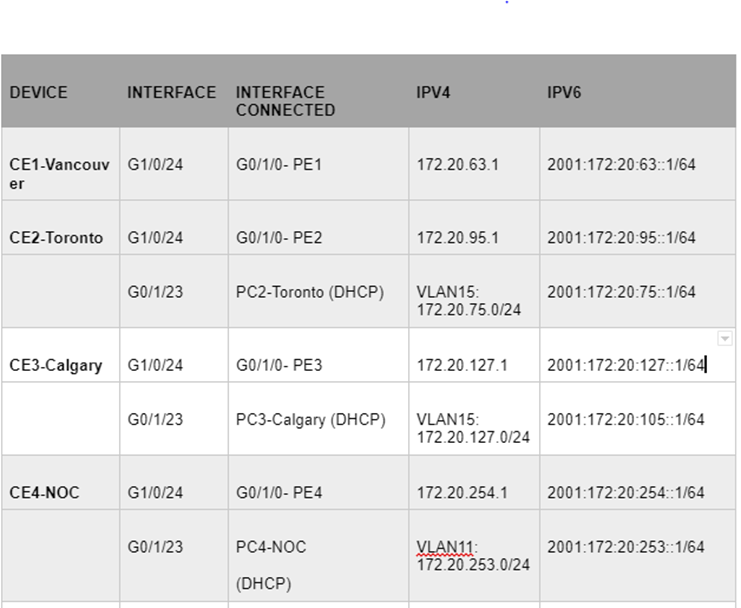
| PE1-R1 | Gig 1/0 | G1/0/1-P3D7-P2 | 10.40.71.1 | |
| Gig 0/0 | Gig 1/0/1-P3D6-P1 | 10.40.61.1 | ||
| Gig 2/0 VLAN10 | G0/0-CE1-Vancouver | 172.20.63.254 | 2001:172:20:63::254/64 | |
| lo0 | 10.40.255.1 | |||
| PE2-R2 | Gig 1/0 | G1/0/2-P3D7-P2 | 10.40.72.2 | |
| Gig 0/0 | Gig 1/0/1-P3D6-P1 | 10.40.62.2 | ||
| Gig 2/0 | G0/0-CE2-Toronto | 172.20.40.254 | 2001:172:20:40::254/64 | |
| lo0 | 10.40.255.2 | |||
| PE3-R3 | Gig 1/0 | G1/0/3-P3D7-P2 | 10.40.73.3 | |
| Gig 0/0 | Gig 1/0/3- P3D6-P1 | 10.40.63.3 | ||
| Gig 2/0 | G0/0-CE3-Calgary | 172.20.127.254 | 2001:172:20:127::254/64 | |
| lo0 | 10.40.255.3 | |||
| PE4-R4 | Gig 1/0 | G1/0/4-P3D7-P2 | 10.40.74.4 | |
| Gig 0/0 | Gig 1/0/4- P3D6-P1 | 10.40.64.4 | ||
| Gig 2/0 | G0/0-CE3-NOC | 172.20.254.254 | 2001:172:20:254::254/64 | |
| lo0 | 10.40.255.4 | |||
| PE5-R5 | Gig 0/0/0 | Gig 0/1/1-P3D6-P1 | 10.40.65.5 | |
| Gig 0/0/1 | Gig0/1/1-P3D7-P2 | 10.40.75.5 | ||
| vlan1 | VRF internet | DHCP (10.0.0.x) | ||
| lo0 | 10.40.255.5 | |||
| P1-D6 | Gig 1/0/5 | Gig 0/0/0-B2R3-PE5 | 10.40.65.6 | |
| Gig 1/0/3 | Gig 0/0/0-P4R1-PE3 | 10.40.63.6 | ||
| Gig 1/0/4 | Gig 0/0/0-P4R2-PE4 | 10.40.64.6 | ||
| Gig 1/0/1 | Gig 0/0/0-P3R1-PE1 | 10.40.61.6 | ||
| Gig 1/0/2 | Gig 0/0/0-P3R2-PE2 | 10.40.62.6 | ||
| Gig 3/2-3 | Gig 3/2-3-P3D7-P2 | 10.40.67.6 Po1 |
| Gig 1/0/23 | Gig 1/0/23-P3D7-P2 | 10.40.67.6 Po1 | |
| P2-D7 | Gig 1/0/5 | Gig 0/0/1-B2R3-PE5 | 10.40.75.7 |
| Gig 1/0/3 | Gig 0/0/1-P4R1-PE3 | 10.40.73.7 | |
| Gig 1/0/4 | Gig 0/0/1-P4R2-PE4 | 10.40.74.7 | |
| Gig 1/0/1 | Gig 0/0/1-P3R1-PE1 | 10.40.71.7 | |
| Gig 1/0/2 | Gig 0/0/1-P3R2-PE2 | 10.40.72.7 | |
| Gig 3/2 | Gig 3/2-P3D7-P2 | 10.40.67.7 Po1 | |
| Gig 3/3 | Gig 3/3-P3D7-P2 | 10.40.67.7 Po1 |
On P1-D6:
hostname P1-D6-Tung
no ip domain lookup
ip domain name labs.bcit
vtp domain cisalab.local
vtp mode transparent
vlan 666
name ParkingLot
interface Loopback0
ip address 10.40.255.6 255.255.255.255
interface Port-channel1
no switchport
ip address 10.40.67.6 255.255.255.0
interface GigabitEthernet0/0
no switchport
ip address 10.40.61.6 255.255.255.0
!
interface GigabitEthernet0/1
no switchport
ip address 10.40.62.6 255.255.255.0
!
interface GigabitEthernet0/2
no switchport
ip address 10.40.63.6 255.255.255.0
!
interface GigabitEthernet0/3
no switchport
ip address 10.40.64.6 255.255.255.0
!
interface GigabitEthernet1/0
no switchport
ip address 10.40.65.6 255.255.255.0
!
vlan 666
name Parkinglot
!
interface Loopback0
ip address 10.40.255.7 255.255.255.255
!
interface Port-channel1
no switchport
ip address 10.40.67.7 255.255.255.0
!
interface GigabitEthernet0/0
no switchport
ip address 10.40.71.7 255.255.255.0
!
interface GigabitEthernet0/1
no switchport
ip address 10.40.72.7 255.255.255.0
!
interface GigabitEthernet0/2
no switchport
ip address 10.40.73.7 255.255.255.0
!
interface GigabitEthernet0/3
no switchport
ip address 10.40.74.7 255.255.255.0
!
interface GigabitEthernet1/0
no switchport
ip address 10.40.75.7 255.255.255.0
!
interface GigabitEthernet3/2
no switchport
no ip address
channel-group 1 mode active
!
interface GigabitEthernet3/3
no switchport
no ip address
channel-group 1 mode active
!
router ospf 40
network 10.40.0.0 0.0.255.255 area 40
mpls ldp sync
mpls ldp autoconfig
## No autoconfig feature on D6
int range g0/0-3
mpls ip
int range g3/2-3
mpls ip
int g1/0
mpls ipOn P2-D7.
hostname P2D7-Tung
no ip domain lookup
ip domain name labs.bcit
vtp domain cisalab.local
vtp mode transparent
vlan 666
name Parkinglot
!
interface Loopback0
ip address 10.40.255.7 255.255.255.255
!
interface Port-channel1
no switchport
ip address 10.40.67.7 255.255.255.0
!
interface GigabitEthernet0/0
no switchport
ip address 10.40.71.7 255.255.255.0
!
interface GigabitEthernet0/1
no switchport
ip address 10.40.72.7 255.255.255.0
!
interface GigabitEthernet0/2
no switchport
ip address 10.40.73.7 255.255.255.0
!
interface GigabitEthernet0/3
no switchport
ip address 10.40.74.7 255.255.255.0
!
interface GigabitEthernet1/0
no switchport
ip address 10.40.75.7 255.255.255.0
!
interface GigabitEthernet3/2
no switchport
no ip address
channel-group 1 mode active
!
interface GigabitEthernet3/3
no switchport
no ip address
channel-group 1 mode active
router ospf 40
network 10.40.0.0 0.0.255.255 area 40
mpls ldp sync
mpls ldp autoconfig
## No autoconfig on D7
int range g0/0-3
mpls ip
int range g3/2-3
mpls ip
int g1/0
mpls ipOn PE1-Tung
hostname hostname P3R1-PE1
## Create a vrf Cust1 and define a rd, export and imporrt route-target
vrf definition Cust1
rd 1:1
route-target export 1:20
route-target import 1:20
route-target import 1:100
!
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
no ip domain lookup
ip domain name labs.bcit
!
ipv6 unicast-routing
interface Loopback0
ip address 10.40.255.1 255.255.255.255
!
interface GigabitEthernet0/0
description to P1
ip address 10.40.61.1 255.255.255.0
negotiation auto
!
interface GigabitEthernet1/0
description to P2
ip address 10.40.71.1 255.255.255.0
negotiation auto
!
interface GigabitEthernet2/0
vrf forwarding Cust1
ip address 172.20.63.254 255.255.255.0
ipv6 address 2001:172:20:63::254/64
no shut
!
# Enable EIGRP named mode and redistribute bgp to EIGRP
router eigrp TungLe
!
address-family ipv4 unicast vrf Cust1 autonomous-system 20
!
topology base
default-metric 2000 100 255 1 1500
redistribute bgp 40
exit-af-topology
network 172.20.0.0
exit-address-family
!
address-family ipv6 unicast vrf Cust1 autonomous-system 20
!
topology base
default-metric 2000 100 255 1 1500
redistribute bgp 40
exit-af-topology
exit-address-family
!
# Enable OSPF and MPLS enabled-core
router ospf 40
network 10.40.0.0 0.0.255.255 area 40
mpls ldp sync
mpls ldp autoconfig
# Enable MP-BGP with AS 40, activate vpnv4 and vpnv6 to support IPv4 and Ipv6 via BGP network
router bgp 40
bgp log-neighbor-changes
neighbor STA40 peer-group
neighbor STA40 remote-as 40
neighbor STA40 update-source Loopback0
neighbor 10.40.255.2 peer-group STA40
neighbor 10.40.255.3 peer-group STA40
neighbor 10.40.255.4 peer-group STA40
neighbor 10.40.255.5 peer-group STA40
!
address-family ipv4
neighbor 10.40.255.2 activate
neighbor 10.40.255.3 activate
neighbor 10.40.255.4 activate
neighbor 10.40.255.5 activate
exit-address-family
!
address-family vpnv4
neighbor STA40 send-community extended
neighbor 10.40.255.2 activate
neighbor 10.40.255.3 activate
neighbor 10.40.255.4 activate
neighbor 10.40.255.5 activate
exit-address-family
!
address-family vpnv6
neighbor STA40 send-community extended
neighbor 10.40.255.2 activate
neighbor 10.40.255.3 activate
neighbor 10.40.255.4 activate
neighbor 10.40.255.5 activate
exit-address-family
!
# Activate BGP on vrf Cust1 for IPv4 and Ipv6. Redistribute EIGRP IPv4/IPV6 named mode to BGP
address-family ipv4 vrf Cust1
redistribute eigrp 20
exit-address-family
!
address-family ipv6 vrf Cust1
redistribute eigrp 20 include-connected
exit-address-family
!On PE2-Tung
hostname P3R2-PE2-Tung
vrf definition Cust1
rd 1:2
route-target export 1:20
route-target import 1:20
route-target import 1:100
!
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
!
no ip domain lookup
ip domain name labs.bcit
!
ipv6 unicast-routing
interface Loopback0
ip address 10.40.255.2 255.255.255.255
!
interface GigabitEthernet0/0
description to P1
ip address 10.40.62.2 255.255.255.0
negotiation auto
!
interface GigabitEthernet1/0
description to P2
ip address 10.40.72.2 255.255.255.0
negotiation auto
!
interface GigabitEthernet2/0
vrf forwarding Cust1
ip address 172.20.95.254 255.255.255.0
ipv6 address 2001:172:20:95::254/64
no shut
!
router eigrp TungLe
!
address-family ipv4 unicast vrf Cust1 autonomous-system 20
!
topology base
default-metric 2000 100 255 1 1500
redistribute bgp 40
exit-af-topology
network 172.20.0.0
exit-address-family
!
address-family ipv6 unicast vrf Cust1 autonomous-system 20
!
topology base
default-metric 2000 100 255 1 1500
redistribute bgp 40
exit-af-topology
exit-address-family
!
router ospf 40
network 10.40.0.0 0.0.255.255 area 40
mpls ldp sync
mpls ldp autoconfig
!
router bgp 40
bgp log-neighbor-changes
neighbor STA40 peer-group
neighbor STA40 remote-as 40
neighbor STA40 update-source Loopback0
neighbor 10.40.255.1 peer-group STA40
neighbor 10.40.255.3 peer-group STA40
neighbor 10.40.255.4 peer-group STA40
neighbor 10.40.255.5 peer-group STA40
!
address-family ipv4
neighbor 10.40.255.1 activate
neighbor 10.40.255.3 activate
neighbor 10.40.255.4 activate
neighbor 10.40.255.5 activate
exit-address-family
!
address-family vpnv4
neighbor STA40 send-community extended
neighbor 10.40.255.1 activate
neighbor 10.40.255.3 activate
neighbor 10.40.255.4 activate
neighbor 10.40.255.5 activate
exit-address-family
!
address-family vpnv6
neighbor STA40 send-community extended
neighbor 10.40.255.1 activate
neighbor 10.40.255.3 activate
neighbor 10.40.255.4 activate
neighbor 10.40.255.5 activate
exit-address-family
!
address-family ipv4 vrf Cust1
redistribute eigrp 20
exit-address-family
!
address-family ipv6 vrf Cust1
redistribute eigrp 20 include-connected
exit-address-family
!+ On PE3-Tung
hostname P4R1-PE3-Tung
!
vrf definition Cust1
rd 1:3
route-target export 1:20
route-target import 1:20
route-target import 1:100
!
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
no ip domain lookup
ip domain name labs.bcit
!
ipv6 unicast-routing
interface Loopback0
ip address 10.40.255.3 255.255.255.255
!
interface GigabitEthernet0/0
description to P1
ip address 10.40.63.3 255.255.255.0
negotiation auto
!
interface GigabitEthernet1/0
description to P2
ip address 10.40.73.3 255.255.255.0
negotiation auto
!
interface GigabitEthernet2/0
vrf forwarding Cust1
ip address 172.20.127.254 255.255.255.0
ipv6 address 2001:172:20:127::254/64
no shut
!
router eigrp TungLe
!
address-family ipv4 unicast vrf Cust1 autonomous-system 20
!
topology base
default-metric 2000 100 255 1 1500
redistribute bgp 40
exit-af-topology
network 172.20.0.0
exit-address-family
!
address-family ipv6 unicast vrf Cust1 autonomous-system 20
!
topology base
default-metric 2000 100 255 1 1500
redistribute bgp 40
exit-af-topology
exit-address-family
!
address-family ipv4 unicast vrf kirk autonomous-system 100
!
topology base
default-metric 1000 100 1 255 1500
redistribute bgp 40
exit-af-topology
network 172.19.0.0
exit-address-family
!
address-family ipv6 unicast vrf kirk autonomous-system 100
!
topology base
redistribute bgp 40
exit-af-topology
exit-address-family
!
router ospf 40
network 10.40.0.0 0.0.255.255 area 40
mpls ldp sync
mpls ldp autoconfig
!
router bgp 40
bgp log-neighbor-changes
neighbor STA40 peer-group
neighbor STA40 remote-as 40
neighbor STA40 update-source Loopback0
neighbor 10.40.255.1 peer-group STA40
neighbor 10.40.255.2 peer-group STA40
neighbor 10.40.255.4 peer-group STA40
neighbor 10.40.255.5 peer-group STA40
!
address-family ipv4
neighbor 10.40.255.1 activate
neighbor 10.40.255.2 activate
neighbor 10.40.255.4 activate
neighbor 10.40.255.5 activate
exit-address-family
!
address-family vpnv4
neighbor STA40 send-community extended
neighbor 10.40.255.1 activate
neighbor 10.40.255.2 activate
neighbor 10.40.255.4 activate
neighbor 10.40.255.5 activate
exit-address-family
!
address-family vpnv6
neighbor STA40 send-community extended
neighbor 10.40.255.1 activate
neighbor 10.40.255.2 activate
neighbor 10.40.255.4 activate
neighbor 10.40.255.5 activate
exit-address-family
!
address-family ipv4 vrf Cust1
redistribute eigrp 20
exit-address-family
!
address-family ipv6 vrf Cust1
redistribute eigrp 20 include-connected
exit-address-family
!+ on PE4-NOC
hostname P4R2-PE4-NOC
!
vrf definition Cust1
rd 1:4
route-target export 1:20
route-target import 1:20
route-target import 1:100
!
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
!
no ip domain lookup
ip domain name labs.bcit
ipv6 unicast-routing
interface Loopback0
ip address 10.40.255.4 255.255.255.255
!
interface GigabitEthernet0/0
description to P1
ip address 10.40.64.4 255.255.255.0
negotiation auto
!
interface GigabitEthernet1/0
description to P2
ip address 10.40.74.4 255.255.255.0
negotiation auto
!
interface GigabitEthernet2/0
vrf forwarding Cust1
ip address 172.20.254.254 255.255.255.0
ipv6 address 2001:172:20:254::254/64
no shut
!
router eigrp TungLe
!
address-family ipv4 unicast vrf Cust1 autonomous-system 20
!
topology base
default-metric 2000 100 255 1 1500
redistribute bgp 40
exit-af-topology
network 172.20.0.0
exit-address-family
!
address-family ipv6 unicast vrf Cust1 autonomous-system 20
!
topology base
default-metric 2000 100 255 1 1500
redistribute bgp 40
exit-af-topology
exit-address-family
!
router ospf 40
network 10.40.0.0 0.0.255.255 area 40
mpls ldp sync
mpls ldp autoconfig
!
router bgp 40
bgp log-neighbor-changes
neighbor STA40 peer-group
neighbor STA40 remote-as 40
neighbor STA40 update-source Loopback0
neighbor 10.40.255.1 peer-group STA40
neighbor 10.40.255.2 peer-group STA40
neighbor 10.40.255.3 peer-group STA40
neighbor 10.40.255.5 peer-group STA40
!
address-family ipv4
neighbor 10.40.255.1 activate
neighbor 10.40.255.2 activate
neighbor 10.40.255.3 activate
neighbor 10.40.255.5 activate
exit-address-family
!
address-family vpnv4
neighbor STA40 send-community extended
neighbor 10.40.255.1 activate
neighbor 10.40.255.2 activate
neighbor 10.40.255.3 activate
neighbor 10.40.255.5 activate
exit-address-family
!
address-family vpnv6
neighbor STA40 send-community extended
neighbor 10.40.255.1 activate
neighbor 10.40.255.2 activate
neighbor 10.40.255.3 activate
neighbor 10.40.255.5 activate
exit-address-family
!
address-family ipv4 vrf Cust1
redistribute eigrp 20
exit-address-family
!
address-family ipv6 vrf Cust1
redistribute eigrp 20 include-connected
exit-address-family
!+ On PE5-Tung
hostname B2R5-PE5-Tung
!
# Define vrf Internet and export route-target 1:100. Then we will import route-target 1:100 to all PE1, PE2, PE3, PE4. Import route-target 1:20 for PE1, PE2, PE3, PE4
vrf definition Internet
rd 1:100
route-target export 1:100
route-target import 1:100
route-target import 1:20
!
address-family ipv4
exit-address-family
no ip domain lookup
ip domain name labs.bcit
!
ipv6 unicast-routing
interface Loopback0
ip address 10.40.255.5 255.255.255.255
!
interface GigabitEthernet0/0
description to P1
ip address 10.40.65.5 255.255.255.0
ip nat inside
no shut
!
interface GigabitEthernet1/0
description to P2
ip address 10.40.75.5 255.255.255.0
ip nat inside
no shut
!
interface GigabitEthernet2/0
description to Internet
vrf forwarding Internet
ip address dhcp
ip nat outside
no shut
!
router ospf 40
network 10.40.0.0 0.0.255.255 area 40
mpls ldp sync
mpls ldp autoconfig
!
router bgp 40
bgp log-neighbor-changes
neighbor STA40 peer-group
neighbor STA40 remote-as 40
neighbor STA40 update-source Loopback0
neighbor 10.40.255.1 peer-group STA40
neighbor 10.40.255.2 peer-group STA40
neighbor 10.40.255.3 peer-group STA40
neighbor 10.40.255.4 peer-group STA40
!
address-family ipv4
neighbor 10.40.255.1 activate
neighbor 10.40.255.1 default-originate
neighbor 10.40.255.2 activate
neighbor 10.40.255.3 activate
neighbor 10.40.255.4 activate
exit-address-family
!
address-family vpnv4
neighbor STA40 send-community extended
neighbor 10.40.255.1 activate
neighbor 10.40.255.2 activate
neighbor 10.40.255.3 activate
neighbor 10.40.255.4 activate
exit-address-family
!
address-family vpnv6
neighbor STA40 send-community extended
neighbor 10.40.255.1 activate
neighbor 10.40.255.2 activate
neighbor 10.40.255.3 activate
neighbor 10.40.255.4 activate
exit-address-family
!
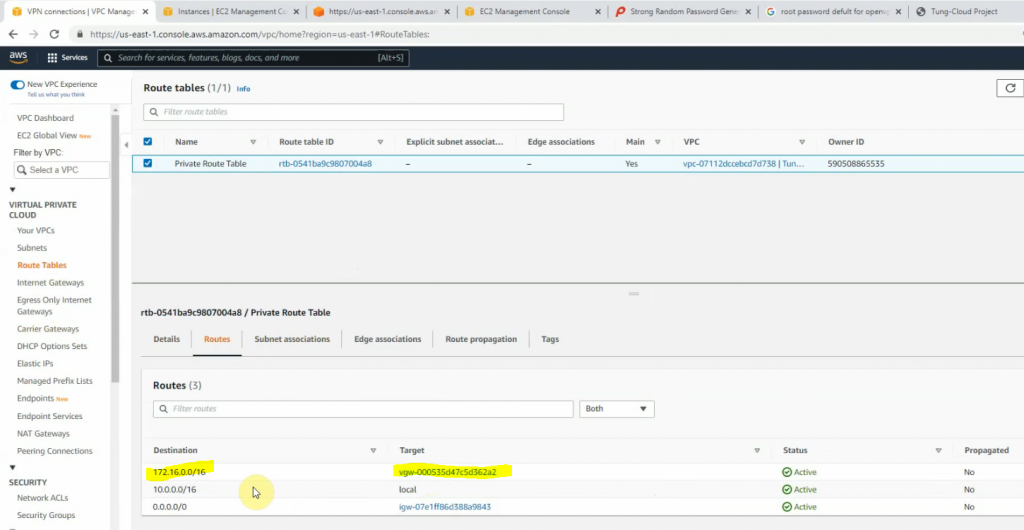
# Distribute default static route via BGP to vrf Internet
address-family ipv4 vrf Internet
network 0.0.0.0
exit-address-family
!
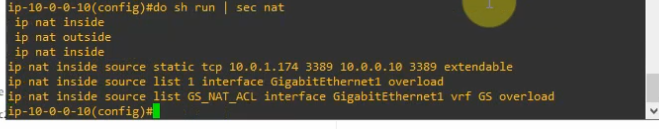
# Enable ip nat inside for vrf Internet via interface g2/0
ip nat inside source list 1 interface g2/0 vrf Internet overload
# Create a static default route for vrf Internet via 10.0.0.1 (simuate public network)
ip route vrf Internet 0.0.0.0 0.0.0.0 10.0.0.1
!
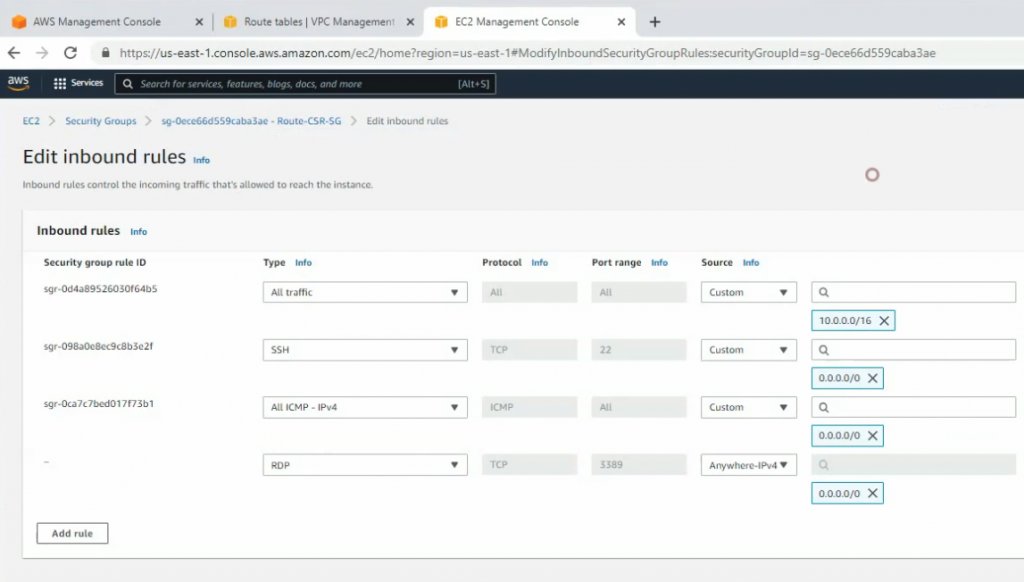
access-list 1 permit 172.20.0.0 0.0.255.255+ On CE1-Van
hostname CE1-Vancouver
ip domain-name labs.bcit
ip routing
no ip domain lookup
ip dhcp excluded-address 172.20.11.1 172.20.11.10
ip dhcp excluded-address 172.20.11.254
ip dhcp excluded-address 172.20.12.1 172.20.12.10
ip dhcp excluded-address 172.20.12.254
ip dhcp excluded-address 172.20.13.1 172.20.13.10
ip dhcp excluded-address 172.20.13.254
ip dhcp excluded-address 172.20.14.1 172.20.14.10
ip dhcp excluded-address 172.20.14.254
ip dhcp excluded-address 172.20.15.1 172.20.15.10
ip dhcp excluded-address 172.20.15.254
ip dhcp excluded-address 172.20.16.1 172.20.16.10
ip dhcp excluded-address 172.20.16.254
ip dhcp excluded-address 172.20.17.1 172.20.17.10
ip dhcp excluded-address 172.20.17.254
ip dhcp excluded-address 172.20.18.1 172.20.18.10
ip dhcp excluded-address 172.20.18.254
ip dhcp excluded-address 172.20.19.1 172.20.19.10
ip dhcp excluded-address 172.20.19.254
!
ip dhcp pool Vlan11
network 172.20.11.0 255.255.255.0
default-router 172.20.11.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan12
network 172.20.12.0 255.255.255.0
default-router 172.20.12.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan13
network 172.20.13.0 255.255.255.0
default-router 172.20.13.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan14
network 172.20.14.0 255.255.255.0
default-router 172.20.14.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan15
network 172.20.15.0 255.255.255.0
default-router 172.20.15.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan16
network 172.20.16.0 255.255.255.0
default-router 172.20.16.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan17
network 172.20.17.0 255.255.255.0
default-router 172.20.17.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan18
network 172.20.18.0 255.255.255.0
default-router 172.20.18.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan19
network 172.20.19.0 255.255.255.0
default-router 172.20.19.1
dns-server 8.8.8.8
!
ipv6 unicast-routing
ipv6 dhcp pool VLAN11
address prefix 2001:172:20:11::/64
domain-name cisalab.local
ipv6 dhcp pool VLAN12
address prefix 2001:172:20:12::/64
domain-name cisalab.local
ipv6 dhcp pool VLAN13
address prefix 2001:172:20:13::/64
domain-name cisalab.local
ipv6 dhcp pool VLAN14
address prefix 2001:172:20:14::/64
domain-name cisalab.local
ipv6 dhcp pool VLAN15
address prefix 2001:172:20:15::/64
domain-name cisalab.local
ipv6 dhcp pool VLAN16
address prefix 2001:172:20:16::/64
domain-name cisalab.local
ipv6 dhcp pool VLAN17
address prefix 2001:172:20:17::/64
domain-name cisalab.local
ipv6 dhcp pool VLAN18
address prefix 2001:172:20:18::/64
domain-name cisalab.local
ipv6 dhcp pool VLAN19
address prefix 2001:172:20:19::/64
domain-name cisalab.local
!
vtp domain Vancouver.local
vtp mode transparent
!
vlan 10
name ISP
!
vlan 11
name Servers
!
vlan 12
name Sales
!
vlan 13
name Legal
!
vlan 14
name HR
!
vlan 15
name Marketing
!
vlan 16
name IT
!
vlan 17
name VoIP
!
vlan 18
name Temp
!
vlan 19
name Mgmt
!
vlan 20
name Parkinglot
!
vlan 99
name Native
!
!
interface Loopback0
ip address 172.20.62.1 255.255.255.0
ipv6 address 2001:172:20:62::1/64
!
interface Port-channel1
switchport trunk native vlan 99
switchport mode trunk
switchport nonegotiate
!
interface Port-channel2
switchport trunk native vlan 99
switchport mode trunk
switchport nonegotiate
!
interface GigabitEthernet0/1
switchport trunk native vlan 99
switchport mode trunk
switchport nonegotiate
channel-group 1 mode active
!
interface GigabitEthernet0/2
switchport trunk native vlan 99
switchport mode trunk
switchport nonegotiate
channel-group 1 mode active
!
interface GigabitEthernet2/0
switchport trunk native vlan 99
switchport mode trunk
switchport nonegotiate
channel-group 2 mode active
!
interface GigabitEthernet2/1
switchport trunk native vlan 99
switchport mode trunk
switchport nonegotiate
channel-group 2 mode active
!
interface GigabitEthernet0/0
no switchport
ip address 172.20.63.1 255.255.255.0
ipv6 address 2001:172:20:63::1/64
!
interface Vlan11
ip address 172.20.11.1 255.255.255.0
ipv6 address 2001:172:20:11::1/64
!
interface Vlan12
ip address 172.20.12.1 255.255.255.0
ipv6 address 2001:172:20:12::1/64
!
interface Vlan13
ip address 172.20.13.1 255.255.255.0
ipv6 address 2001:172:20:13::1/64
!
interface Vlan14
ip address 172.20.14.1 255.255.255.0
ipv6 address 2001:172:20:14::1/64
!
interface Vlan15
ip address 172.20.15.1 255.255.255.0
ipv6 address 2001:172:20:15::1/64
!
interface Vlan16
ip address 172.20.16.1 255.255.255.0
ipv6 address 2001:172:20:16::1/64
!
interface Vlan17
ip address 172.20.17.1 255.255.255.0
ipv6 address 2001:172:20:17::1/64
!
interface Vlan18
ip address 172.20.18.1 255.255.255.0
ipv6 address 2001:172:20:18::1/64
!
interface Vlan19
ip address 172.20.19.1 255.255.255.0
ipv6 address 2001:172:20:19::1/64
!
# Enabe EIGRP named mode between CE1 and PE1
router eigrp TungLe
!
address-family ipv4 unicast autonomous-system 20
!
topology base
redistribute static
exit-af-topology
network 172.20.0.0
exit-address-family
!
address-family ipv6 unicast autonomous-system 20
!
topology base
exit-af-topology
exit-address-family
!+ On CE2-Toronto
hostname CE2-Toronto
ip routing
!
ip domain-name labs.bcit
username admin privilege 15 secret 5 $1$X7ux$H.3fHdZjg2hIUjOyFRUDJ.
no ip domain lookup
ip dhcp excluded-address 172.20.71.1 172.20.71.10
ip dhcp excluded-address 172.20.71.254
ip dhcp excluded-address 172.20.72.1 172.20.72.10
ip dhcp excluded-address 172.20.72.254
ip dhcp excluded-address 172.20.73.1 172.20.73.10
ip dhcp excluded-address 172.20.73.254
ip dhcp excluded-address 172.20.74.1 172.20.74.10
ip dhcp excluded-address 172.20.74.254
ip dhcp excluded-address 172.20.75.1 172.20.75.10
ip dhcp excluded-address 172.20.75.254
ip dhcp excluded-address 172.20.76.1 172.20.76.10
ip dhcp excluded-address 172.20.76.254
ip dhcp excluded-address 172.20.77.1 172.20.77.10
ip dhcp excluded-address 172.20.77.254
ip dhcp excluded-address 172.20.78.1 172.20.78.10
ip dhcp excluded-address 172.20.78.254
ip dhcp excluded-address 172.20.79.1 172.20.79.10
ip dhcp excluded-address 172.20.79.254
!
ip dhcp pool Vlan11
network 172.20.71.0 255.255.255.0
default-router 172.20.71.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan12
network 172.20.72.0 255.255.255.0
default-router 172.20.72.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan13
network 172.20.73.0 255.255.255.0
default-router 172.20.73.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan14
network 172.20.74.0 255.255.255.0
default-router 172.20.74.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan15
network 172.20.75.0 255.255.255.0
default-router 172.20.75.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan16
network 172.20.76.0 255.255.255.0
default-router 172.20.76.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan17
network 172.20.77.0 255.255.255.0
default-router 172.20.77.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan18
network 172.20.78.0 255.255.255.0
default-router 172.20.78.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan19
network 172.20.79.0 255.255.255.0
default-router 172.20.79.1
dns-server 8.8.8.8
!
ipv6 unicast-routing
ipv6 dhcp pool VLAN11
address prefix 2001:172:20:71::/64
domain-name cisalab.local
ipv6 dhcp pool VLAN12
address prefix 2001:172:20:72::/64
domain-name cisalab.local
ipv6 dhcp pool VLAN13
address prefix 2001:172:20:73::/64
domain-name cisalab.local
ipv6 dhcp pool VLAN14
address prefix 2001:172:20:74::/64
domain-name cisalab.local
ipv6 dhcp pool VLAN15
address prefix 2001:172:20:75::/64
domain-name cisalab.local
ipv6 dhcp pool VLAN16
address prefix 2001:172:20:76::/64
domain-name cisalab.local
ipv6 dhcp pool VLAN17
address prefix 2001:172:20:77::/64
domain-name cisalab.local
ipv6 dhcp pool VLAN18
address prefix 2001:172:20:78::/64
domain-name cisalab.local
ipv6 dhcp pool VLAN19
address prefix 2001:172:20:79::/64
domain-name cisalab.local
!
!
vtp domain toronto.local
vtp mode transparent
!
vlan 10
name ISP
!
vlan 11
name Servers
!
vlan 12
name Sales
!
vlan 13
name Legal
!
vlan 14
name HR
!
vlan 15
name Marketing
!
vlan 16
name IT
!
vlan 17
name VoIP
!
vlan 18
name Temp
!
vlan 19
name Mgmt
!
vlan 20
name Parkinglot
!
vlan 99
name Native
!
!
interface Loopback0
ip address 172.20.94.1 255.255.255.0
ipv6 address 2001:172:20:94::1/64
!
interface GigabitEthernet0/0
no switchport
ip address 172.20.95.1 255.255.255.0
ipv6 address 2001:172:20:95::1/64
!
interface Vlan11
ip address 172.20.71.1 255.255.255.0
ipv6 address 2001:172:20:71::1/64
!
interface Vlan12
ip address 172.20.72.1 255.255.255.0
ipv6 address 2001:172:20:72::1/64
!
interface Vlan13
ip address 172.20.73.1 255.255.255.0
ipv6 address 2001:172:20:73::1/64
!
interface Vlan14
ip address 172.20.74.1 255.255.255.0
ipv6 address 2001:172:20:74::1/64
!
interface Vlan15
ip address 172.20.75.1 255.255.255.0
ipv6 address 2001:172:20:75::1/64
!
interface Vlan16
ip address 172.20.76.1 255.255.255.0
ipv6 address 2001:172:20:76::1/64
!
interface Vlan17
ip address 172.20.77.1 255.255.255.0
ipv6 address 2001:172:20:77::1/64
!
interface Vlan18
ip address 172.20.78.1 255.255.255.0
ipv6 address 2001:172:20:78::1/64
!
interface Vlan19
ip address 172.20.79.1 255.255.255.0
ipv6 address 2001:172:200:79::1/64
!
!
router eigrp TungLe
!
address-family ipv4 unicast autonomous-system 20
!
topology base
redistribute static
exit-af-topology
network 172.20.0.0
exit-address-family
!
address-family ipv6 unicast autonomous-system 20
!
topology base
exit-af-topology
exit-address-family
!+ On CE3-Cal
hostname CE3-Calgary
ip routing
!
ip domain-name labs.bcit
no ip domain lookup
ip dhcp excluded-address 172.20.101.1 172.20.101.10
ip dhcp excluded-address 172.20.101.254
ip dhcp excluded-address 172.20.102.1 172.20.102.10
ip dhcp excluded-address 172.20.102.254
ip dhcp excluded-address 172.20.103.1 172.20.103.10
ip dhcp excluded-address 172.20.103.254
ip dhcp excluded-address 172.20.104.1 172.20.104.10
ip dhcp excluded-address 172.20.104.254
ip dhcp excluded-address 172.20.105.1 172.20.105.10
ip dhcp excluded-address 172.20.105.254
ip dhcp excluded-address 172.20.106.1 172.20.106.10
ip dhcp excluded-address 172.20.106.254
ip dhcp excluded-address 172.20.107.1 172.20.107.10
ip dhcp excluded-address 172.20.107.254
ip dhcp excluded-address 172.20.108.1 172.20.108.10
ip dhcp excluded-address 172.20.108.254
ip dhcp excluded-address 172.20.109.1 172.20.109.10
ip dhcp excluded-address 172.20.109.254
!
ip dhcp pool Vlan11
network 172.20.101.0 255.255.255.0
default-router 172.20.101.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan12
network 172.20.102.0 255.255.255.0
default-router 172.20.102.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan10
network 172.20.103.0 255.255.255.0
default-router 172.20.103.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan14
network 172.20.104.0 255.255.255.0
default-router 172.20.104.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan15
network 172.20.105.0 255.255.255.0
default-router 172.20.105.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan16
network 172.20.106.0 255.255.255.0
default-router 172.20.106.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan17
network 172.20.107.0 255.255.255.0
default-router 172.20.107.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan18
network 172.20.108.0 255.255.255.0
default-router 172.20.108.1
dns-server 8.8.8.8
!
ip dhcp pool Vlan19
network 172.20.109.0 255.255.255.0
default-router 172.20.109.1
dns-server 8.8.8.8
!
ipv6 unicast-routing
ipv6 dhcp pool VLAN15
address prefix 2001:172:20:105::/64
domain-name cisalab.local
!
ipv6 dhcp pool VLAN11
address prefix 2001:172:20:101::/64
domain-name cisalab.local
!
ipv6 dhcp pool VLAN12
address prefix 2001:172:20:102::/64
domain-name cisalab.local
!
ipv6 dhcp pool VLAN13
address prefix 2001:172:20:103::/64
domain-name cisalab.local
!
ipv6 dhcp pool VLAN14
address prefix 2001:172:20:104::/64
domain-name cisalab.local
!
ipv6 dhcp pool VLAN16
address prefix 2001:172:20:106::/64
domain-name cisalab.local
!
ipv6 dhcp pool VLAN17
address prefix 2001:172:20:107::/64
domain-name cisalab.local
!
ipv6 dhcp pool VLAN18
address prefix 2001:172:20:108::/64
domain-name cisalab.local
!
ipv6 dhcp pool VLAN19
address prefix 2001:172:20:109::/64
domain-name cisalab.local
!
!
vtp domain calgary.local
vtp mode transparent
!
vlan 10
name ISP
!
vlan 11
name Servers
!
vlan 12
name Sales
!
vlan 13
name Legal
!
vlan 14
name HR
!
vlan 15
name Marketing
!
vlan 16
name IT
!
vlan 17
name VoIP
!
vlan 18
name Temp
!
vlan 19
name Mgmt
!
vlan 20
name Parkinglot
!
vlan 51-54,61-64
!
vlan 99
name Native
!
interface GigabitEthernet0/0
no switchport
ip address 172.20.127.1 255.255.255.0
ipv6 address 2001:172:20:127::1/64
!
interface Vlan11
ip address 172.20.101.1 255.255.255.0
ipv6 address 2001:172:20:101::1/64
!
interface Vlan12
ip address 172.20.102.1 255.255.255.0
ipv6 address 2001:172:20:102::1/64
!
interface Vlan13
ip address 172.20.103.1 255.255.255.0
ipv6 address 2001:172:20:103::1/64
!
interface Vlan14
ip address 172.20.104.1 255.255.255.0
ipv6 address 2001:172:20:104::1/64
!
interface Vlan15
ip address 172.20.105.1 255.255.255.0
ipv6 address 2001:172:20:105::1/64
!
interface Vlan16
ip address 172.20.106.1 255.255.255.0
ipv6 address 2001:172:20:106::1/64
!
interface Vlan17
ip address 172.20.107.1 255.255.255.0
ipv6 address 2001:172:20:107::1/64
!
interface Vlan18
ip address 172.20.108.1 255.255.255.0
ipv6 address 2001:172:20:108::1/64
!
interface Vlan19
ip address 172.20.109.1 255.255.255.0
ipv6 address 2001:172:20:109::1/64
!
!
router eigrp TungLe
!
address-family ipv4 unicast autonomous-system 20
!
topology base
redistribute static
exit-af-topology
network 172.20.0.0
exit-address-family
!
address-family ipv6 unicast autonomous-system 20
!
topology base
exit-af-topology
exit-address-family+ On CE4-NOC
hostname CE4-NOC
ip routing
ip domain-name labs.bcit
no ip domain lookup
username admin privilege 15 secret 5 Cisco123
ip dhcp excluded-address 172.20.253.1 172.20.253.10
ip dhcp excluded-address 172.20.253.254
!
ip dhcp excluded-address 172.20.253.1 172.20.253.10
ip dhcp excluded-address 172.20.253.254
!
ip dhcp pool Vlan11
network 172.20.253.0 255.255.255.0
default-router 172.20.253.1
dns-server 8.8.8.8
!
!
no ip domain-lookup
ip domain-name labs.bcit
ip cef
ipv6 unicast-routing
ipv6 dhcp pool VLAN11
address prefix 2001:172:20:253::/64
domain-name cisalab.local
ipv6 unicast-routing
!
vtp domain noc.local
vtp mode transparent
!
vlan 11-20,99
interface GigabitEthernet0/0
vrf forwarding Mgmt-vrf
no ip address
negotiation auto
!
!
interface GigabitEthernet3/3
switchport access vlan 11
!
interface GigabitEthernet0/0
no switchport
ip address 172.20.254.1 255.255.255.0
ipv6 address 2001:172:20:254::1/64
!
interface Vlan11
ip address 172.20.253.1 255.255.255.0
ipv6 address 2001:172:20:253::1/64
!
router eigrp TungLe
!
address-family ipv4 unicast autonomous-system 20
!
topology base
redistribute static
exit-af-topology
network 172.20.0.0
exit-address-family
!
address-family ipv6 unicast autonomous-system 20
!
topology base
exit-af-topology
exit-address-family
!
tacacs server TACSRV1
address ipv4 172.20.253.12
key Cisco123
!
!
radius server RADSRV1
address ipv4 172.20.253.12 auth-port 1812 acct-port 1813
key Cisco123
!
!
control-plane
service-policy input system-cpp-policy
!
line con 0
stopbits 1
line aux 0
stopbits 1
line vty 0 4
login authentication VTY_ACCESS
line vty 5 15
endON Vancouver-EE2
hostname Vancouver-EE2
vtp domain Vancouver.local
vtp mode transparent
!
no ip domain-lookup
ip domain-name labs.bcit
vlan 10
name ISP
!
vlan 11
name Servers
!
vlan 12
name Sales
!
vlan 13
name Legal
!
vlan 14
name HR
!
vlan 15
name Marketing
!
vlan 16
name IT
!
vlan 17
name VoIP
!
vlan 18
name Temp
!
vlan 19
name Mgmt
!
vlan 20
name Parkinglot
!
vlan 99
name Native
!
!
interface Port-channel1
switchport trunk native vlan 99
switchport mode trunk
switchport nonegotiate
!
interface Port-channel2
switchport trunk native vlan 99
switchport mode trunk
switchport nonegotiate
!
interface G2/0
switchport trunk native vlan 99
switchport mode trunk
switchport nonegotiate
channel-group 1 mode active
!
interface G2/1
switchport trunk native vlan 99
switchport mode trunk
switchport nonegotiate
channel-group 1 mode active
!
interface G3/0
switchport trunk native vlan 99
switchport mode trunk
switchport nonegotiate
channel-group 2 mode active
!
interface G3/1
switchport trunk native vlan 99
switchport mode trunk
switchport nonegotiate
channel-group 2 mode active
!
interface GigabitEthernetg/3
switchport access vlan 15
!On Vancouver-EA1
hostname Vancouver-EA1
vtp domain Vancouver.local
vtp mode transparent
!
no ip domain-lookup
ip domain-name labs.bcit
vlan 10
name ISP
!
vlan 11
name Servers
!
vlan 12
name Sales
!
vlan 13
name Legal
!
vlan 14
name HR
!
vlan 15
name Marketing
!
vlan 16
name IT
!
vlan 17
name VoIP
!
vlan 18
name Temp
!
vlan 19
name Mgmt
!
vlan 20
name Parkinglot
!
vlan 99
name Native
!
interface Port-channel1
switchport trunk native vlan 99
switchport mode trunk
switchport nonegotiate
!
interface Port-channel2
switchport trunk native vlan 99
switchport mode trunk
switchport nonegotiate
!
interface G0/1
switchport trunk native vlan 99
switchport mode trunk
switchport nonegotiate
channel-group 1 mode active
!
interface G0/2
switchport trunk native vlan 99
switchport mode trunk
switchport nonegotiate
channel-group 1 mode active
!
interface G3/0
switchport trunk native vlan 99
switchport mode trunk
switchport nonegotiate
channel-group 2 mode active
!
interface G3/2
switchport trunk native vlan 99
switchport mode trunk
switchport nonegotiate
channel-group 2 mode active
!+ OSPF
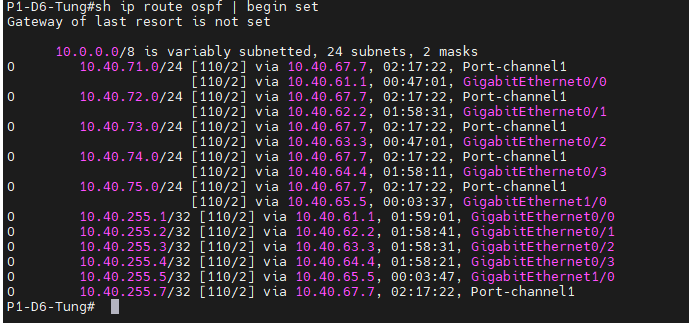
+ MPLS
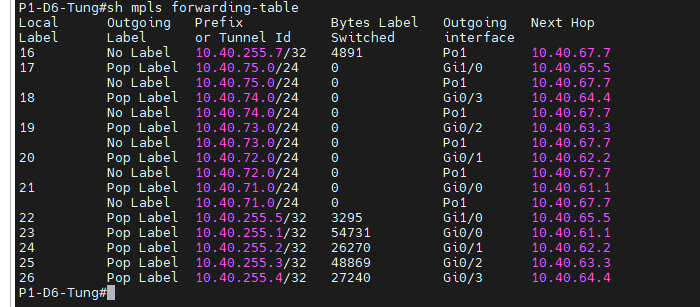
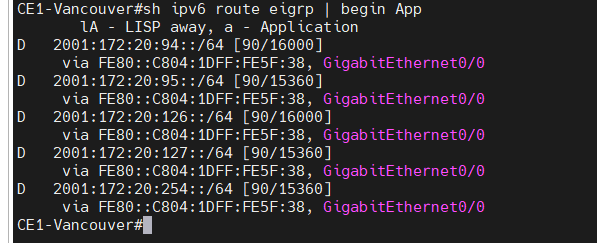
+ EIGRP named mode.
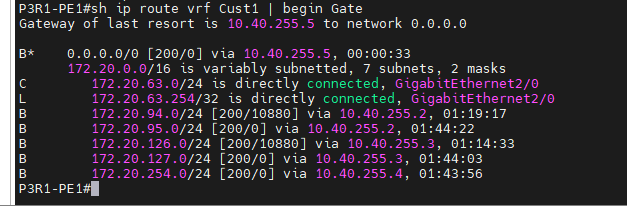
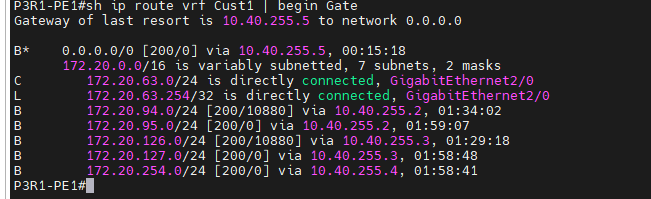
+ BGP on PE1
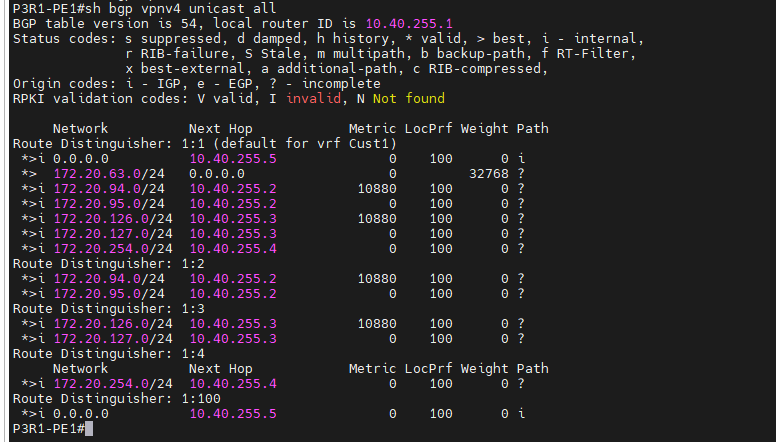
+ MP-BGP VPNv4
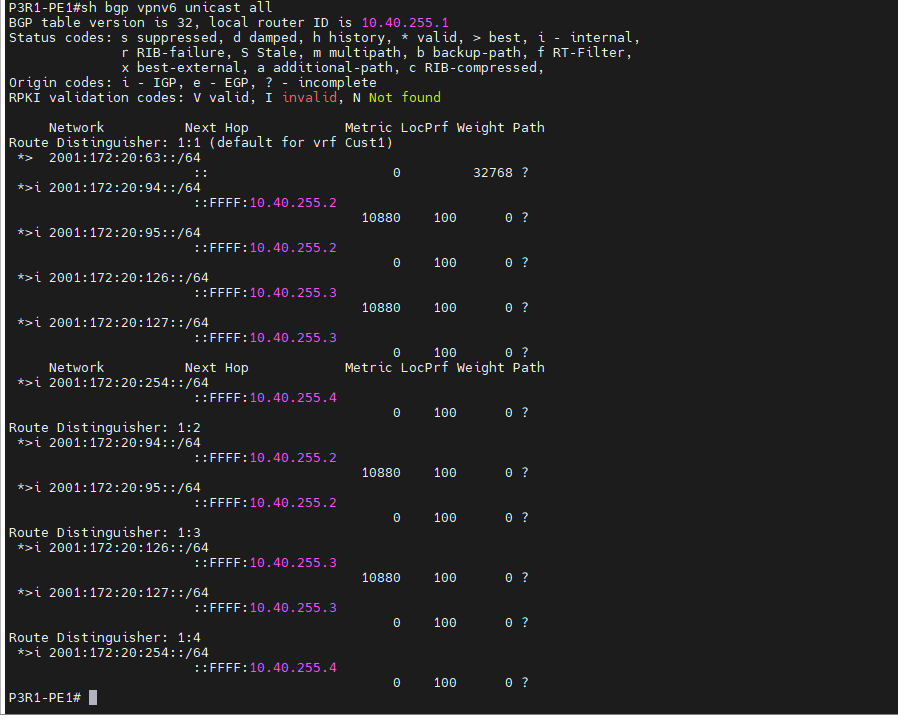
+ MP-BGP VPNv6
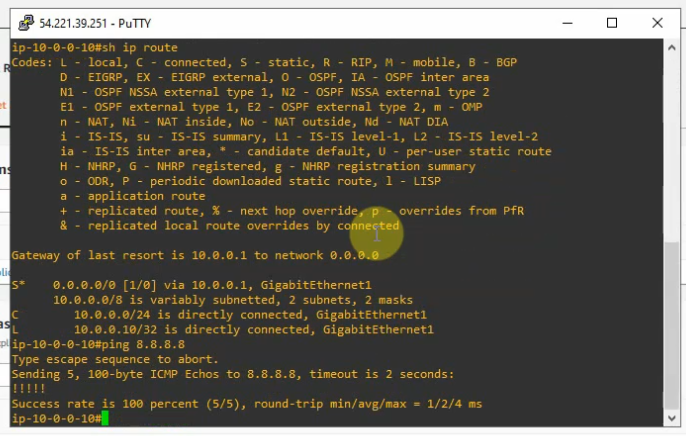
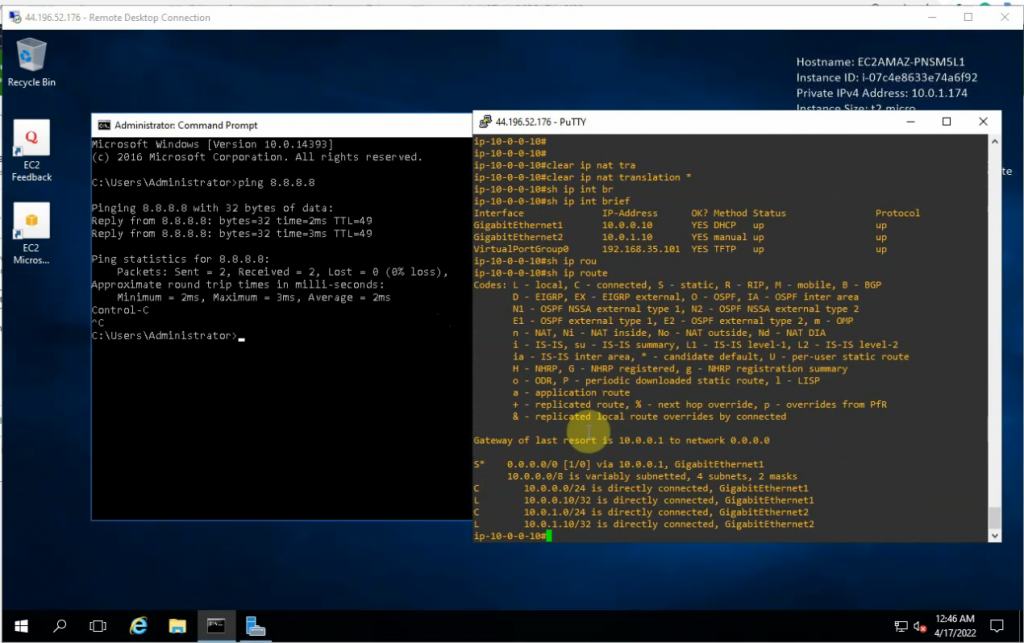
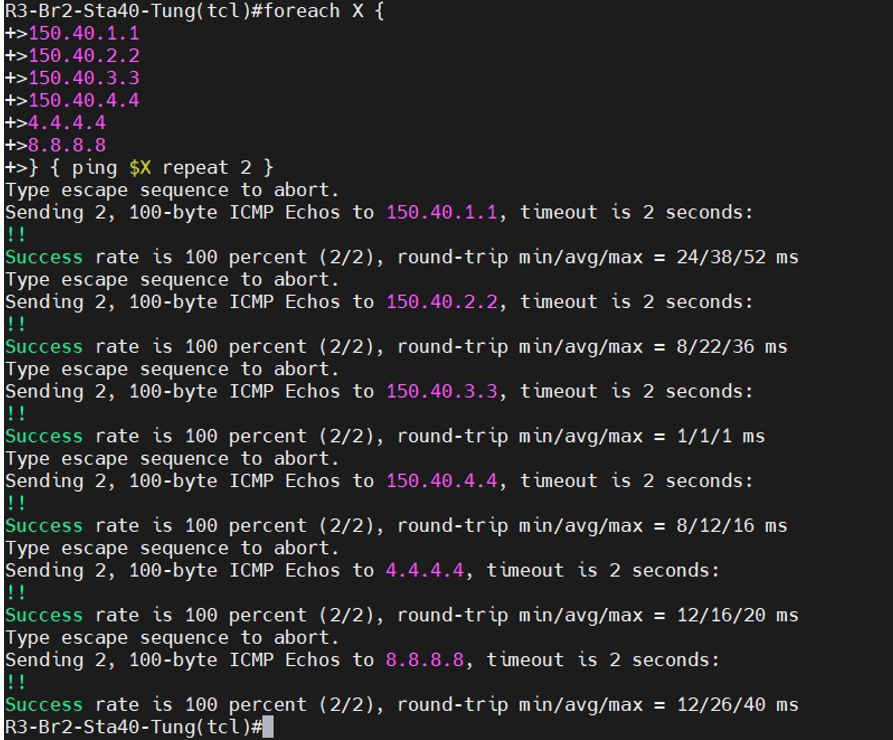
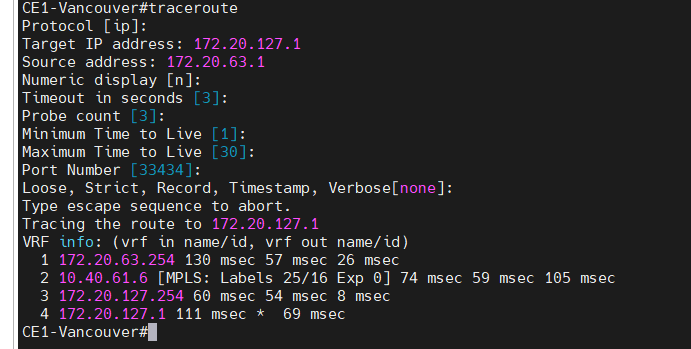
Traceroute IPv4 from Vancouver to Calgary. Traffic is passed through the MPLS enabled core network
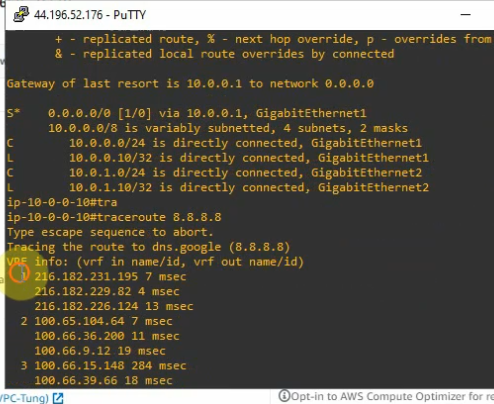
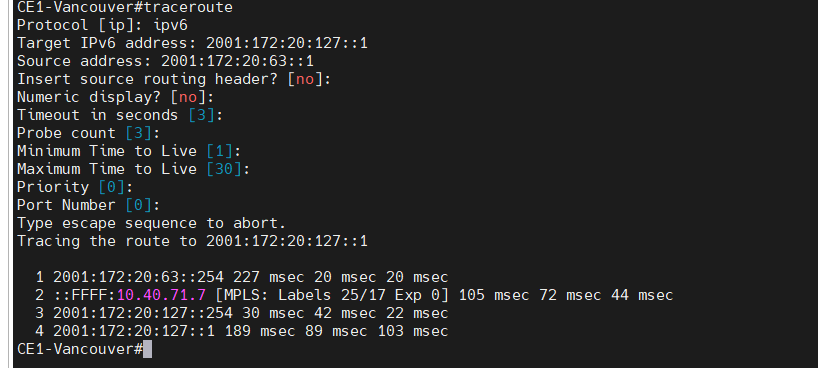
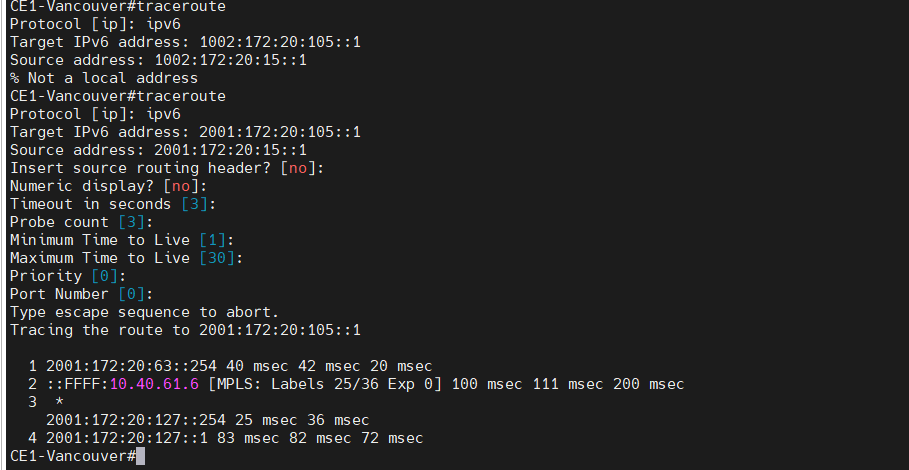
Traceroute IPv6 from Vancouver to Calgary.
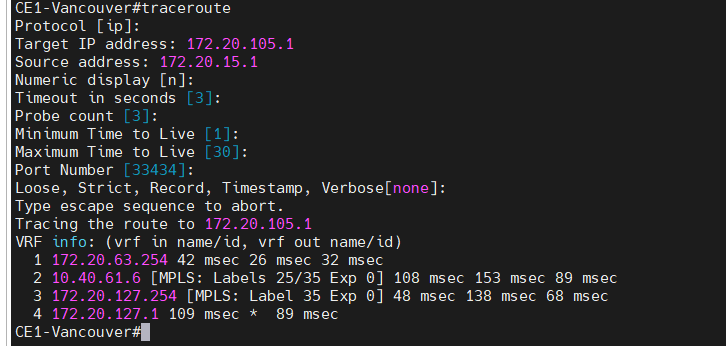
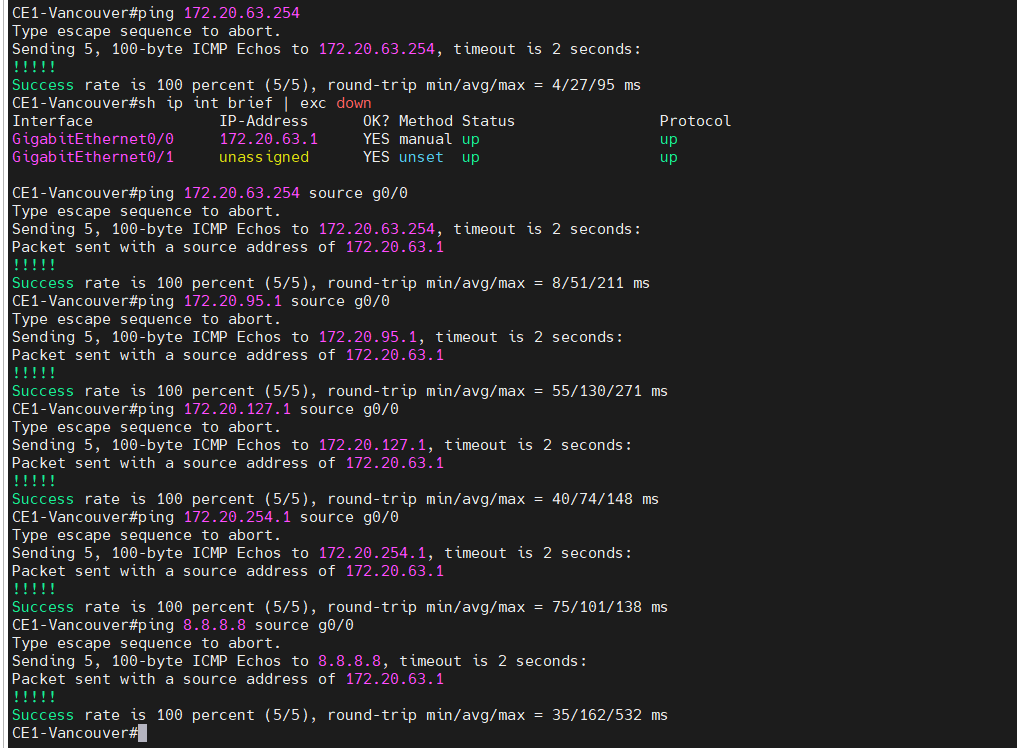
On Vancouver
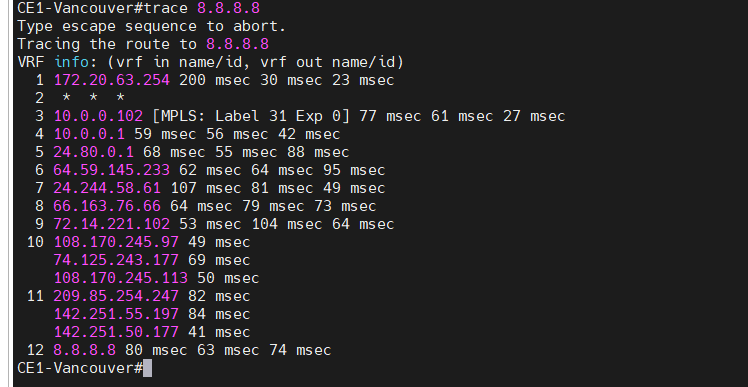
traceroute 8.8.8.8
PC1.
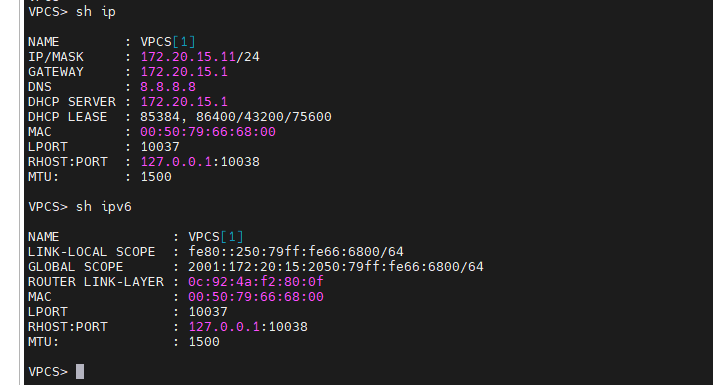
+ PC2.
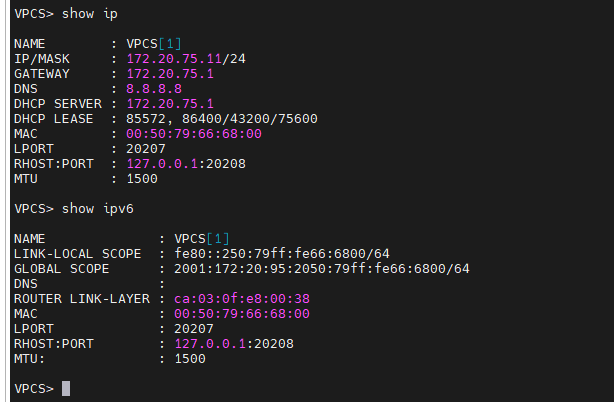
+ on PC3.
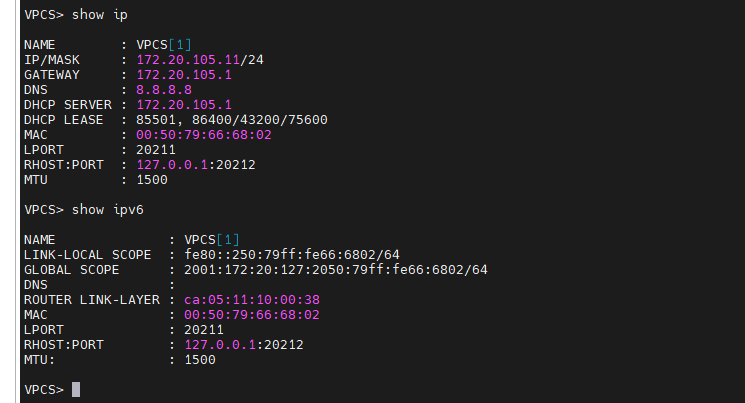
+ On PC4:
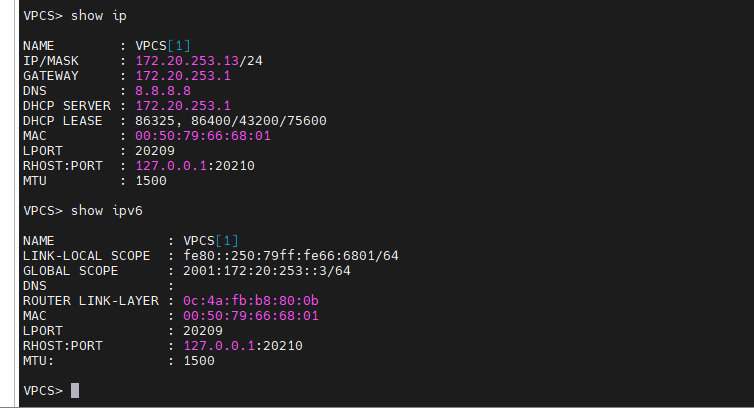
On PC1.
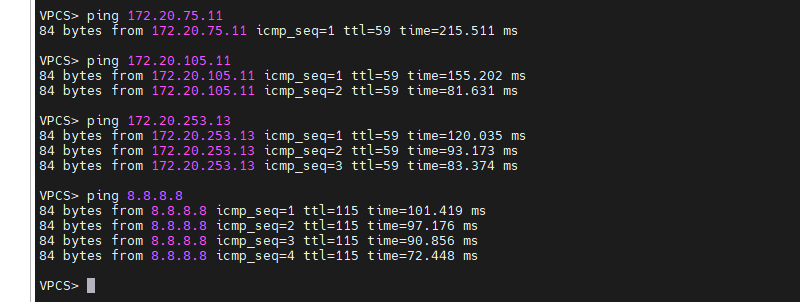
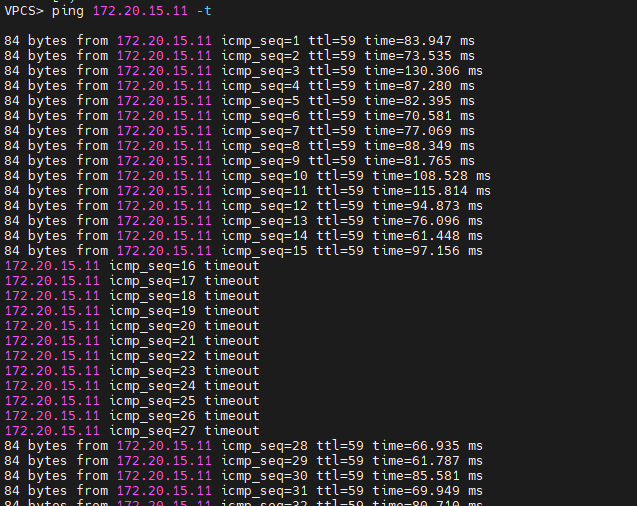
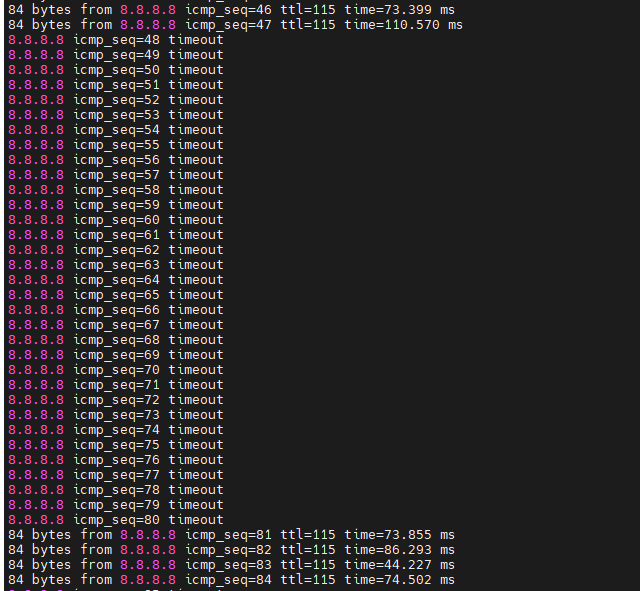
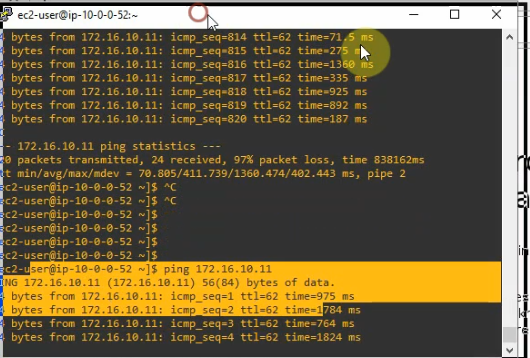
Turn P1-D6 off to test network redundancy.
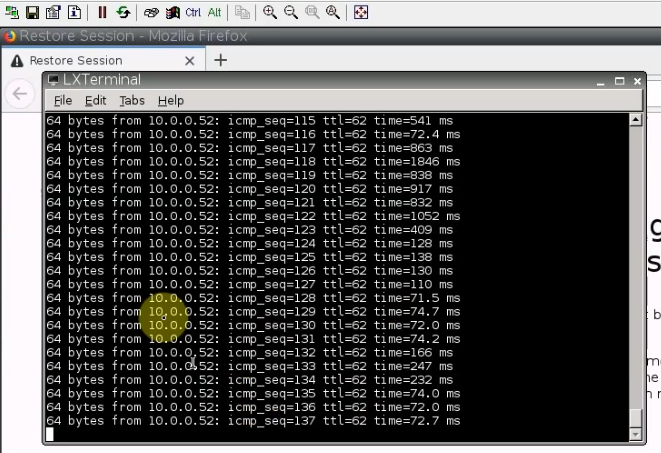
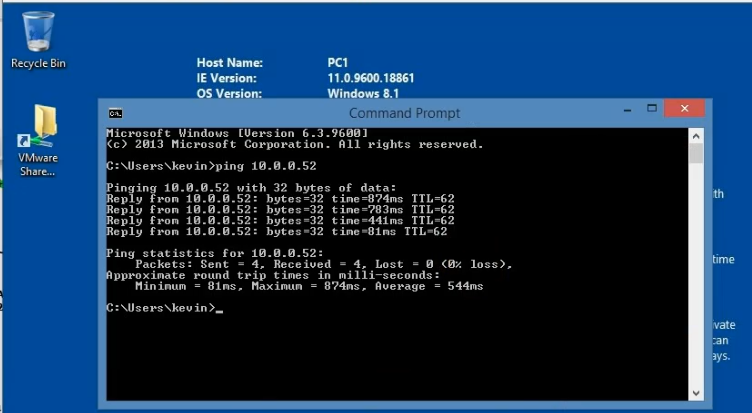
There are a couple of dropped packets when pinging PCs between different sites and Internet.