This is a diagram that I have used for this lab.
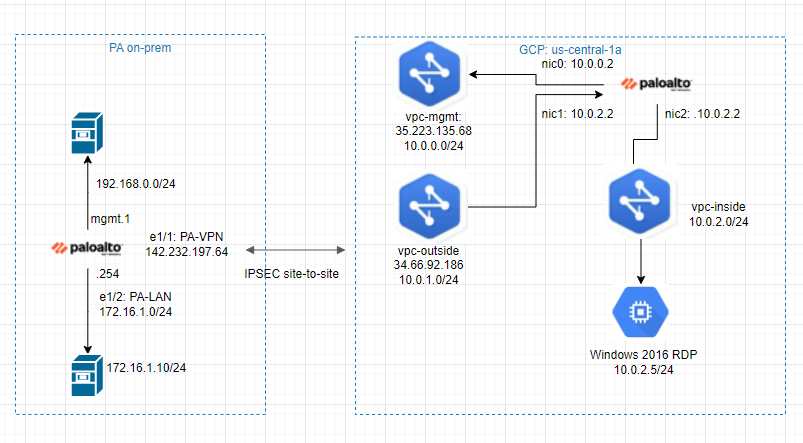
I have set up the first part for Palo Alto on GCP (https://tungle.ca/?p=3760). Now, I go to set up the VPN site-to-site between Palo Alto on-prem and Palo Alto on GCP.
On Palo Alto on-prem.
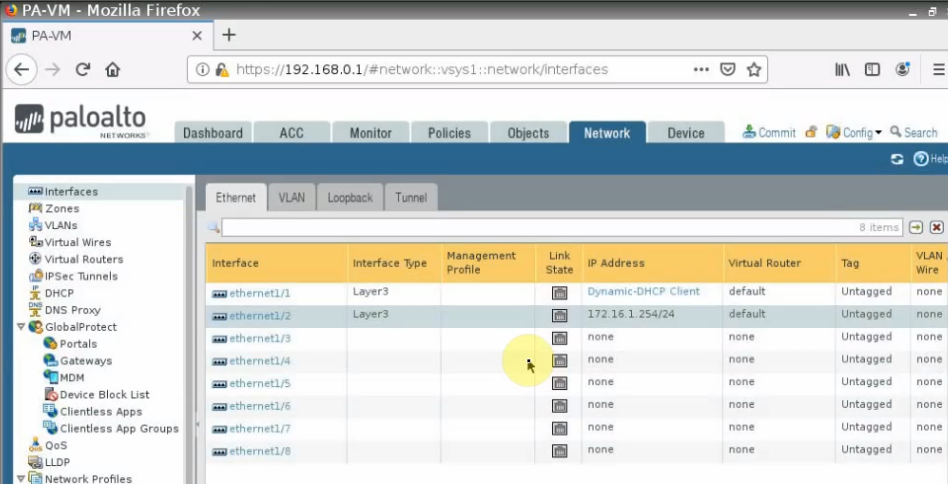
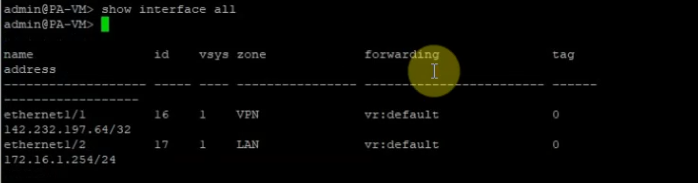
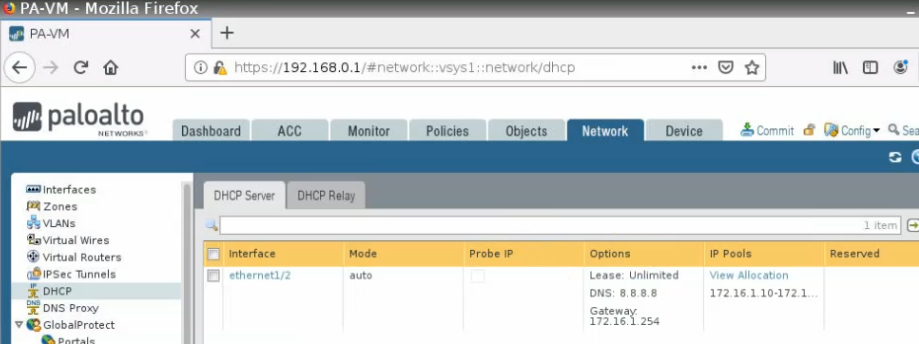
Setup DHCP service on the e1/2 interface.
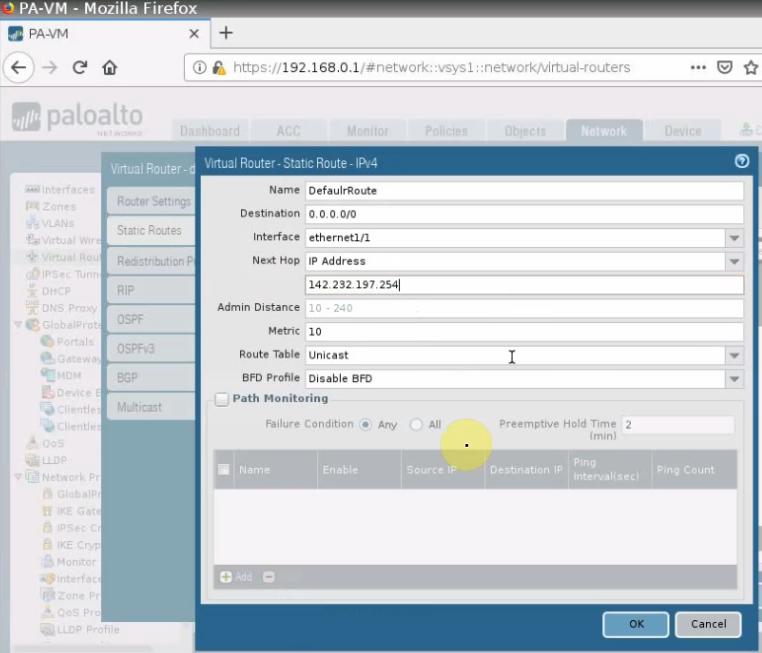
Set the default route on Palo Alto.
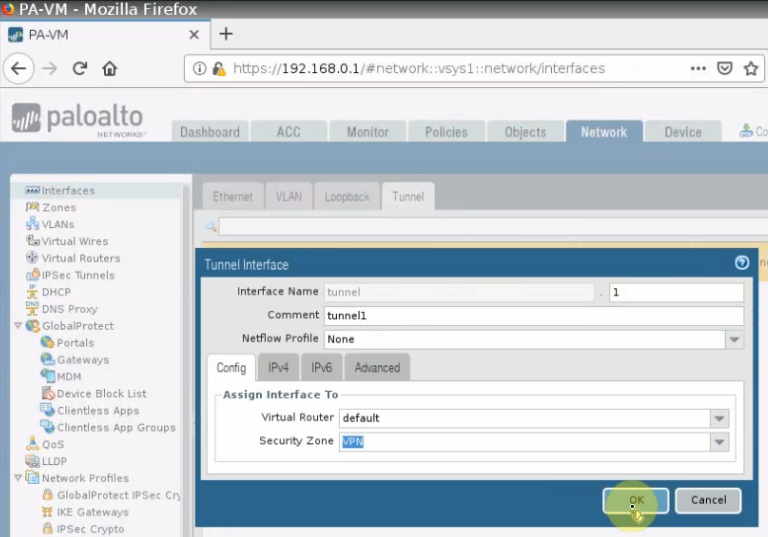
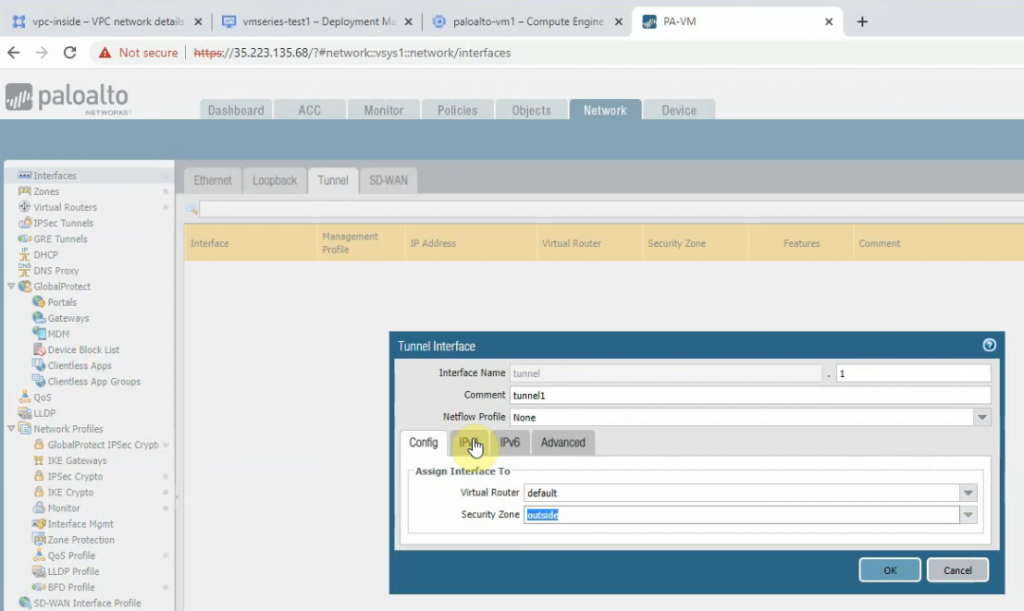
Create a tunnel 1 on Palo Alto.
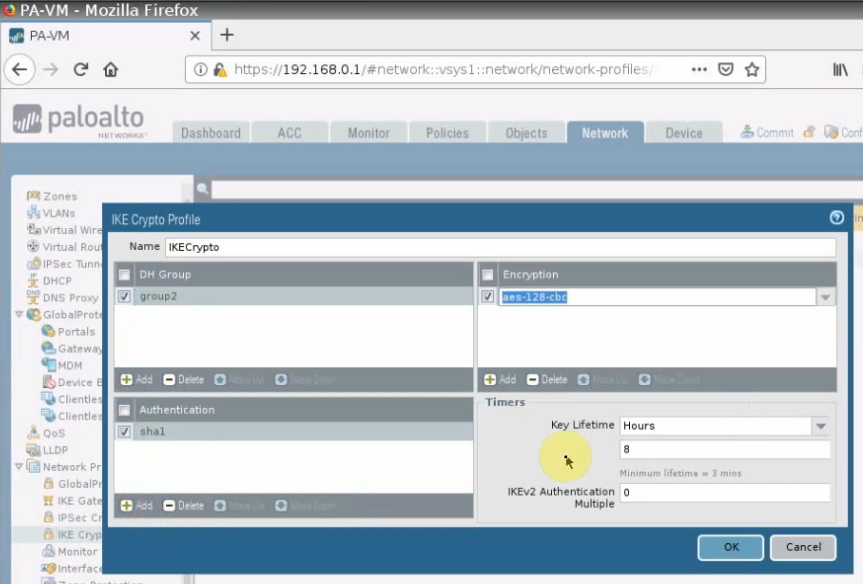
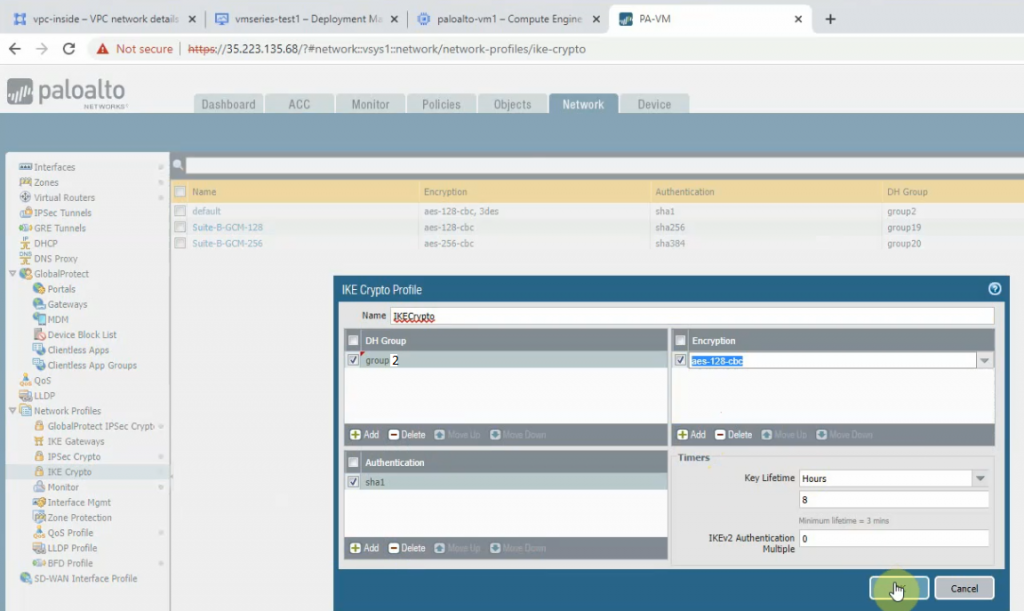
Create an IKECrypto.
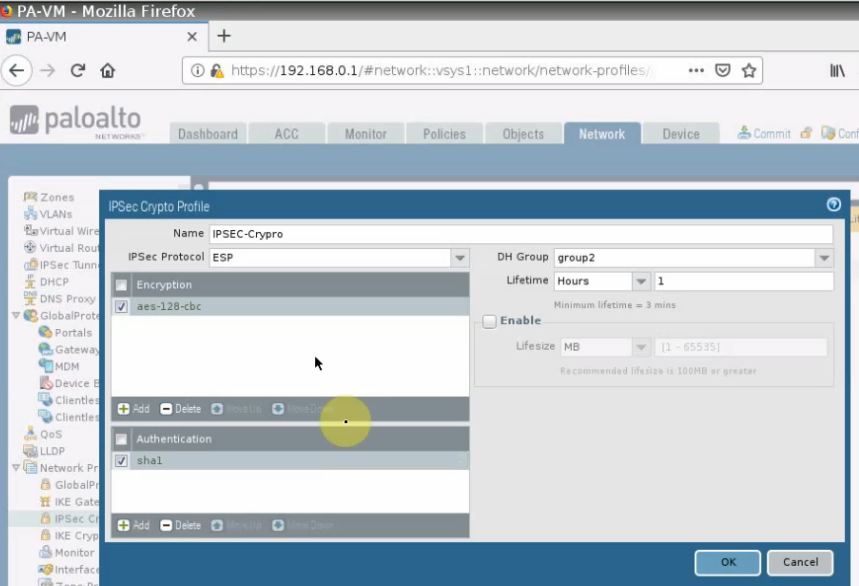
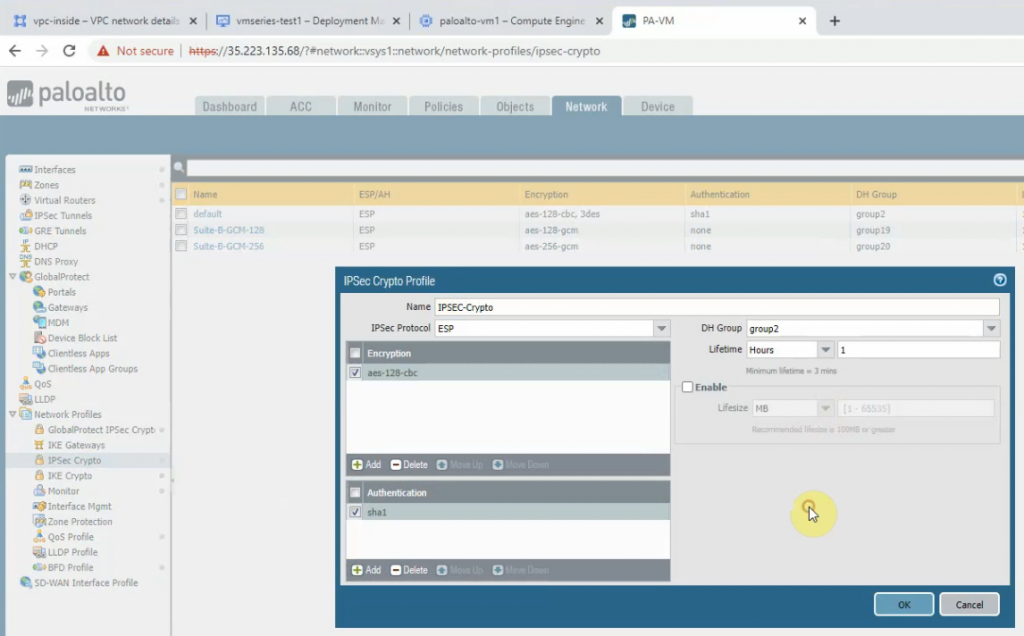
Create an IPSECCrypto.
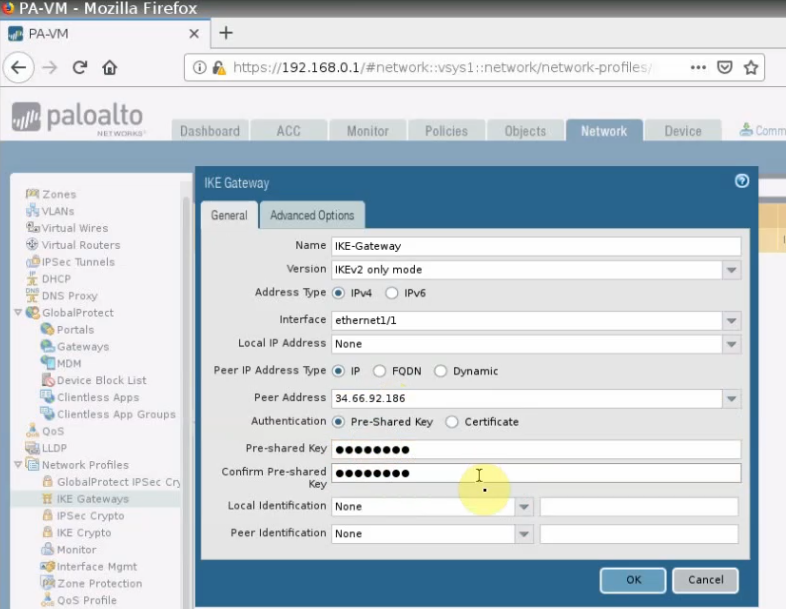
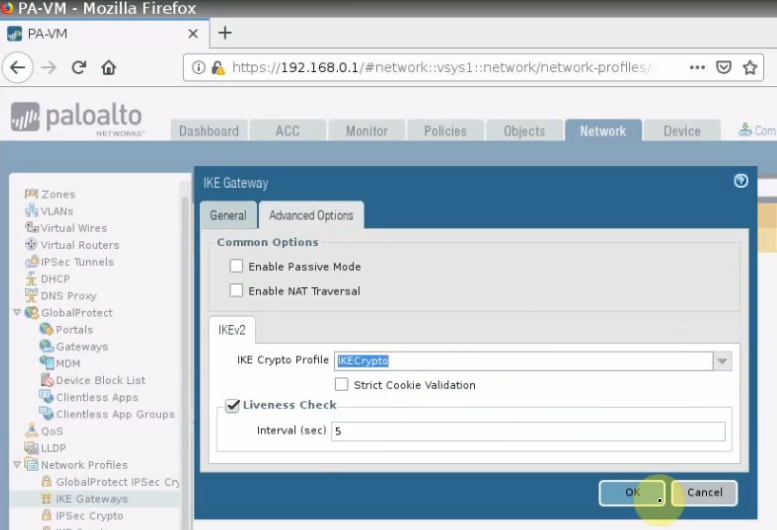
Create an IKEGateway.
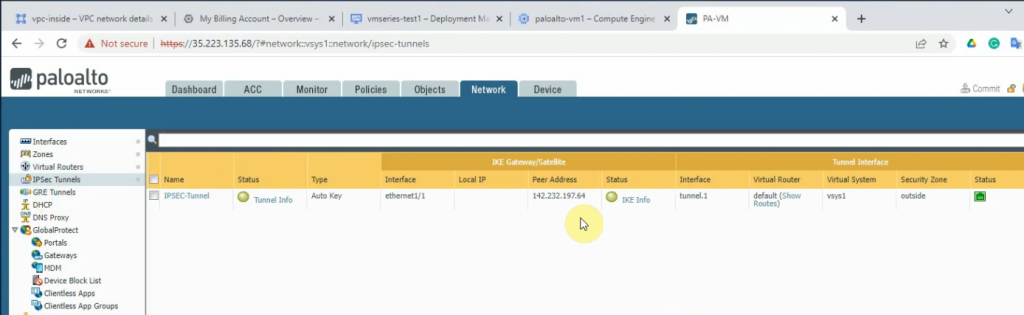
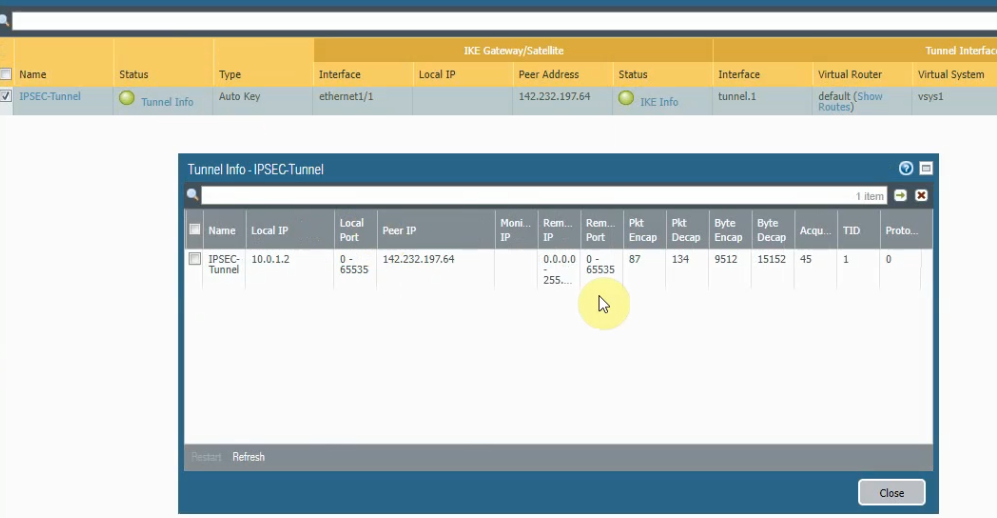
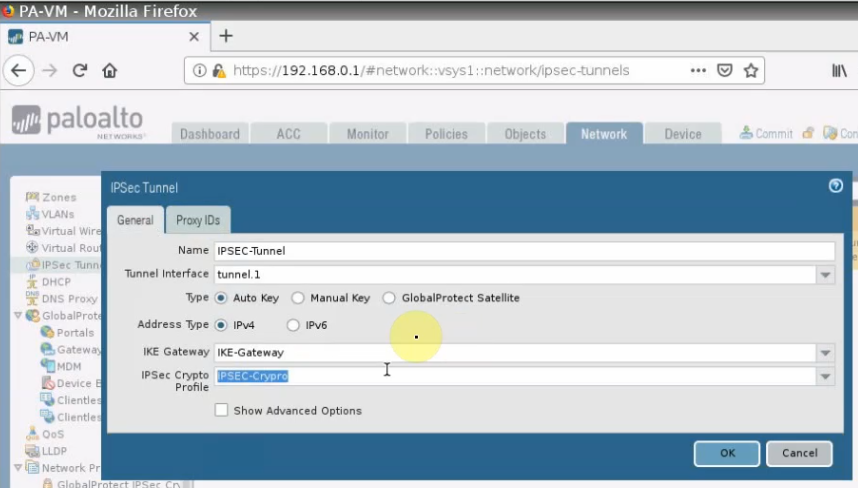
Create an IPSECTunnel.
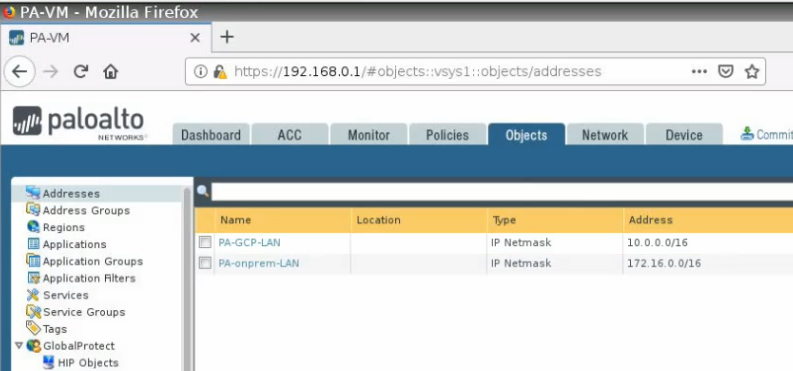
Create network objects for LAN subnets of Palo Alto on-prem and on GCP.
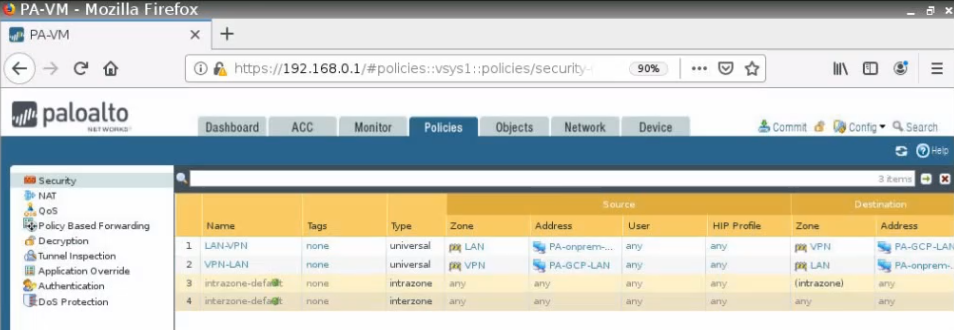
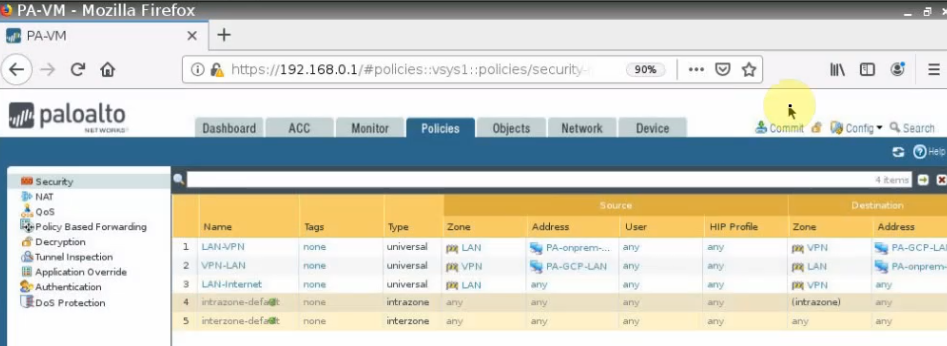
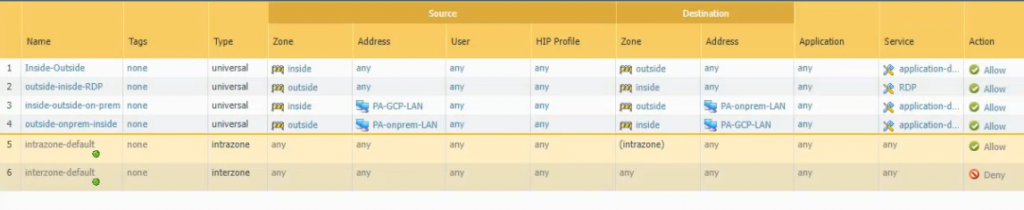
Create both security policies to allow traffic from LAN subnets on Palo Alto – GCP to LAN subnets on Palo Alto on-prem and vice versa.
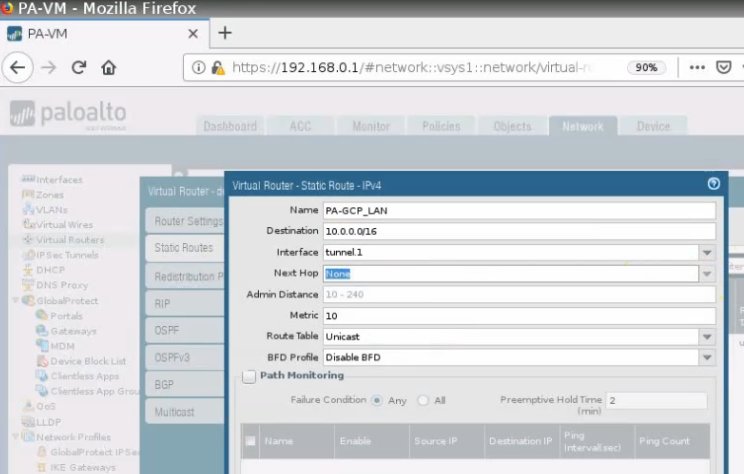
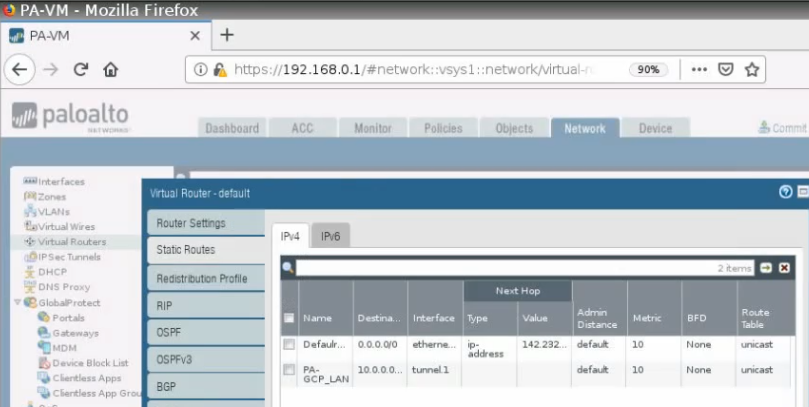
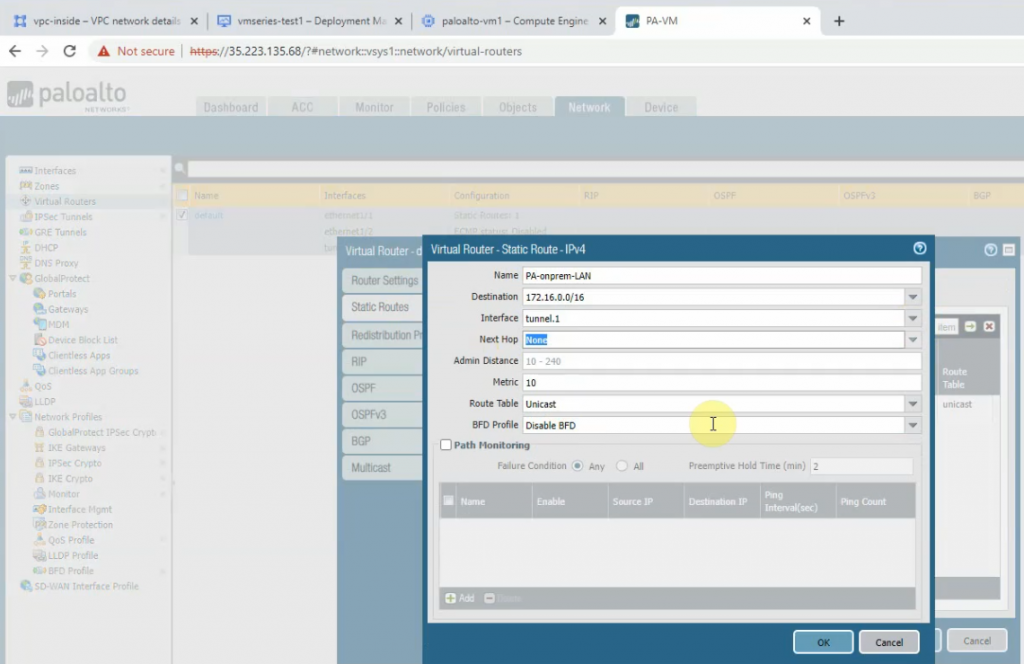
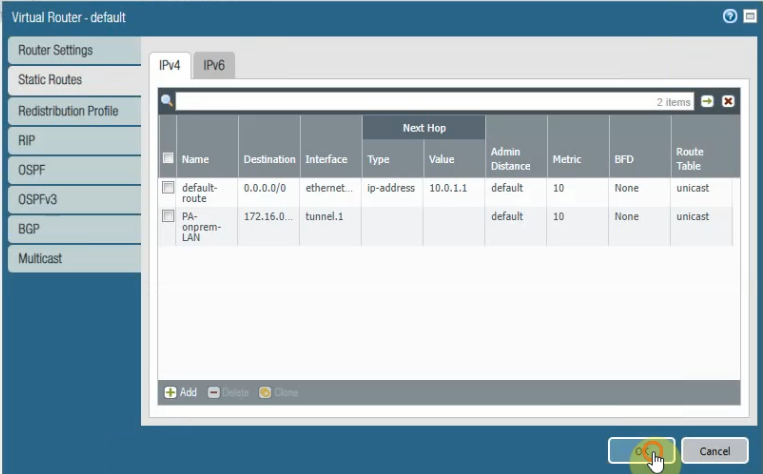
Create a static route to allow traffic from LAN subnets of Palo Alto on-prem to LAN subnets of Palo Alto on the cloud.
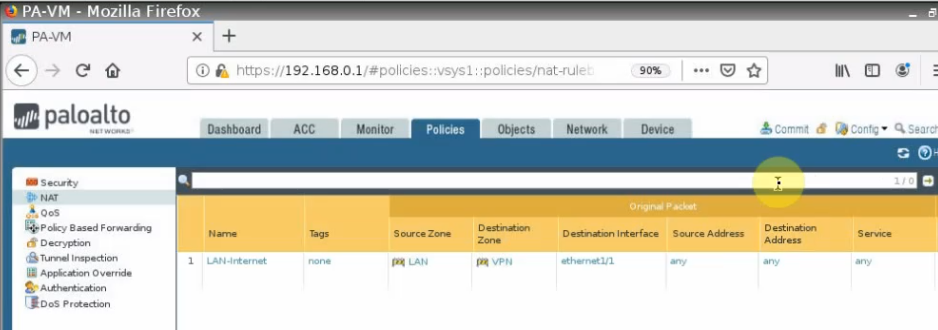
Create SNAT to allow the local network to access the Internet.
Create another access rule to allow traffic from the LAN network to access the Internet.
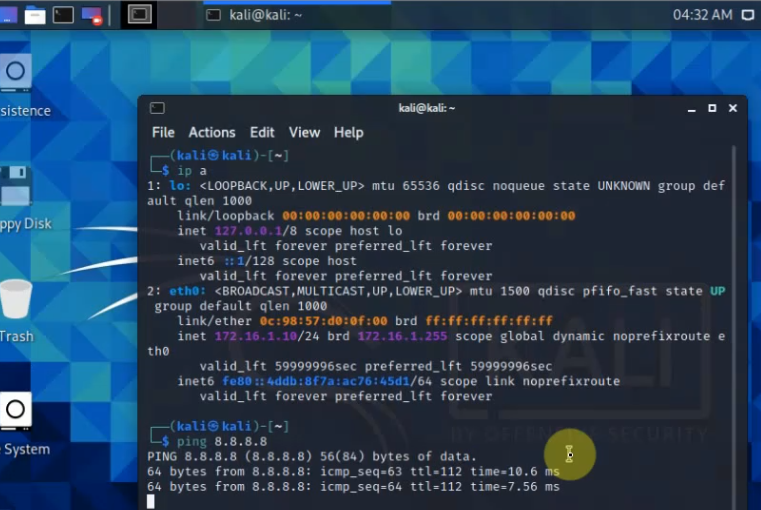
The Kali machine on the LAN network is able to access the Internet.
Back to Palo Alto on GCP.
Create a tunnel 1 on Palo Alto.
Create an IKECrypto.
Create an IPSECCrypto.
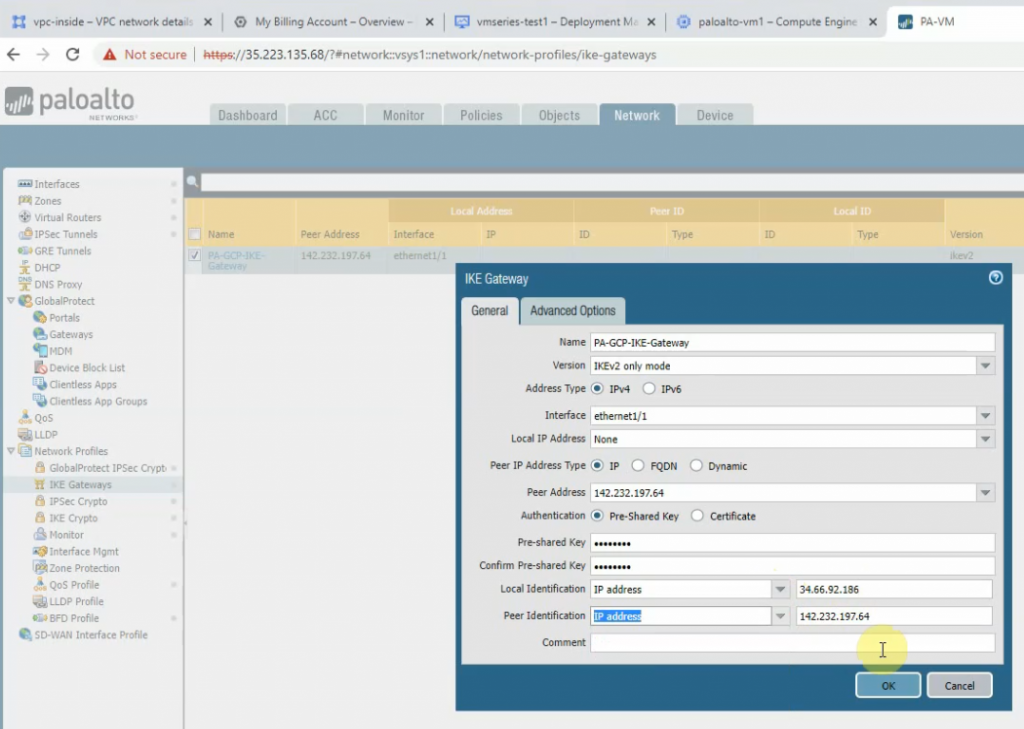
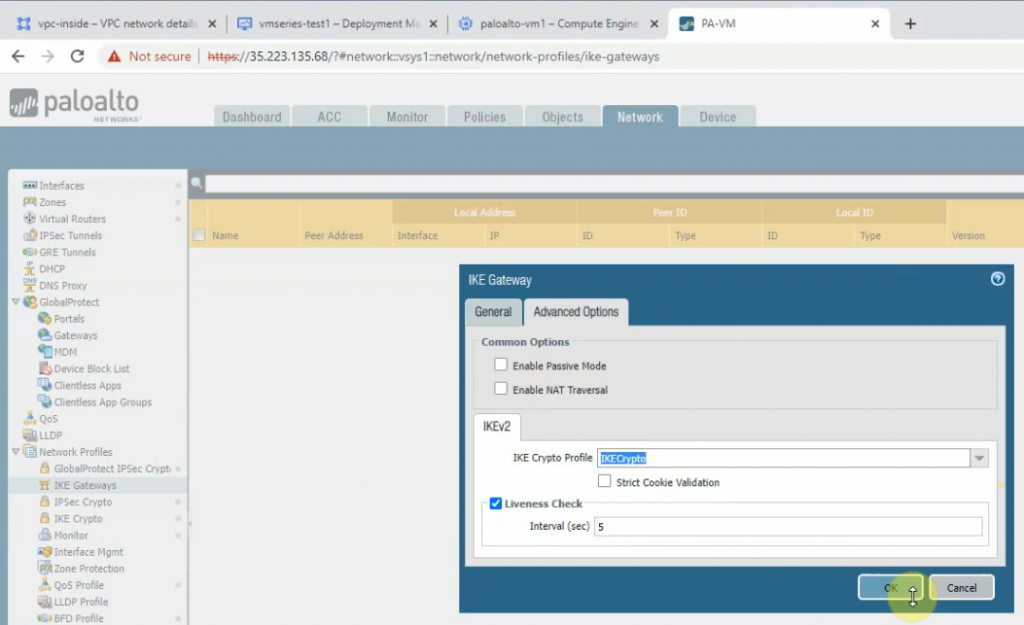
Create an IKEGateway.
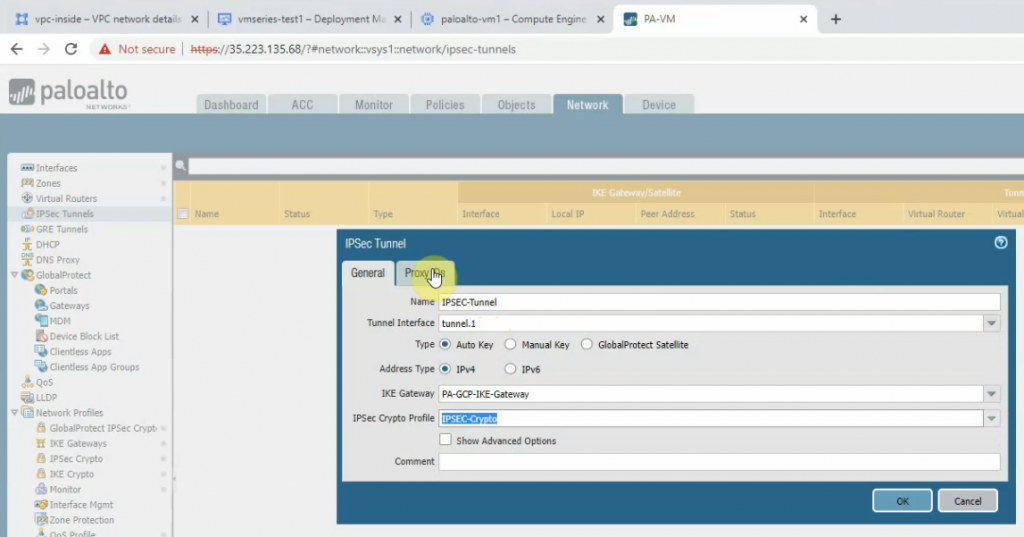
Create an IPSEC tunnel.
Create network objects for LAN subnets for Palo Alto on-prem and on the cloud.
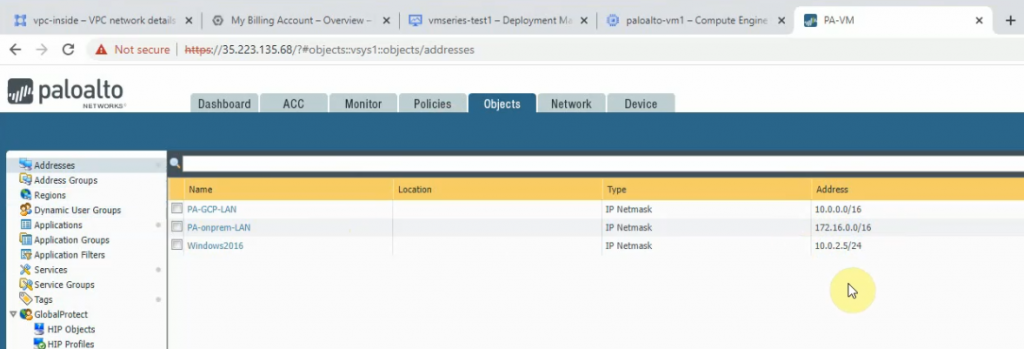
Create both security policies to allow traffic from LAN subnets on Palo Alto on GCP to LAN subnets on Palo Alto on-prem and vice versa.
Create a static route to allow traffic from LAN subnets of Palo Alto on the cloud to LAN subnets of Palo Alto on-prem.
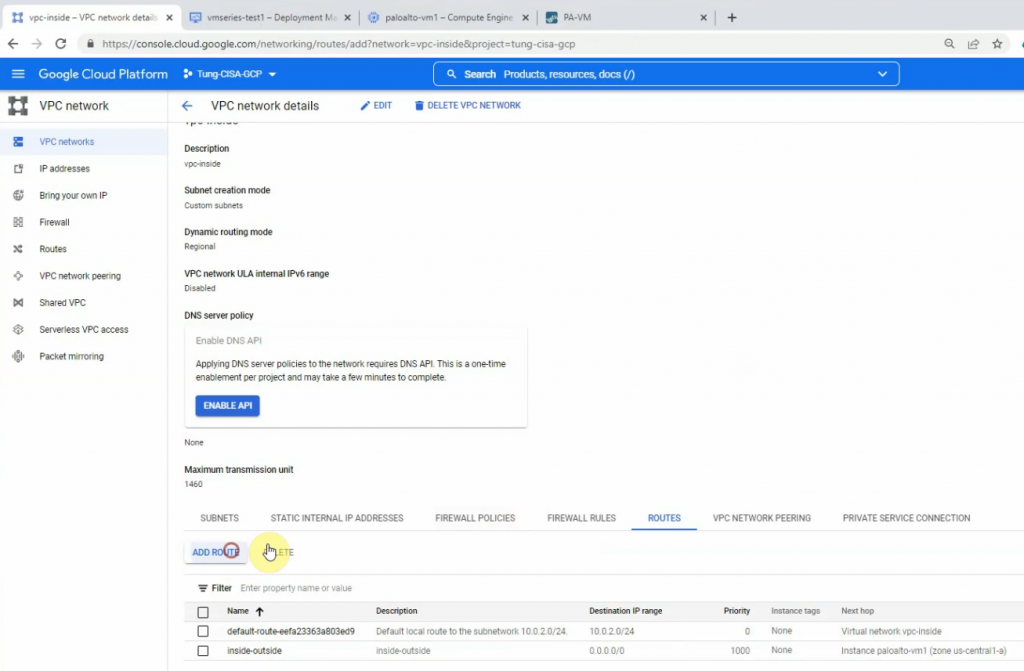
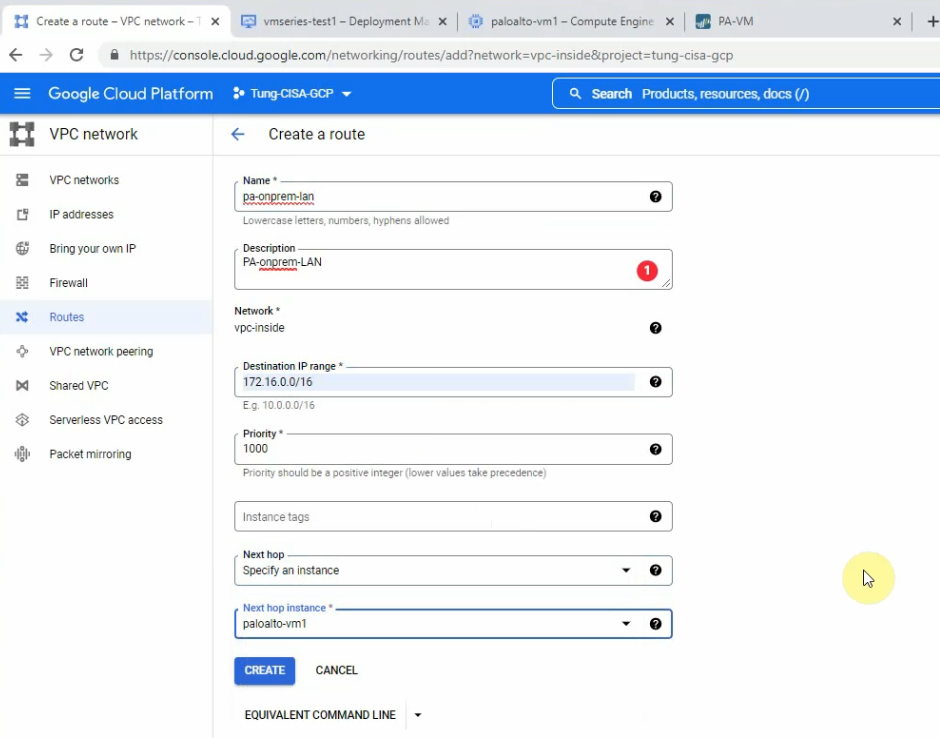
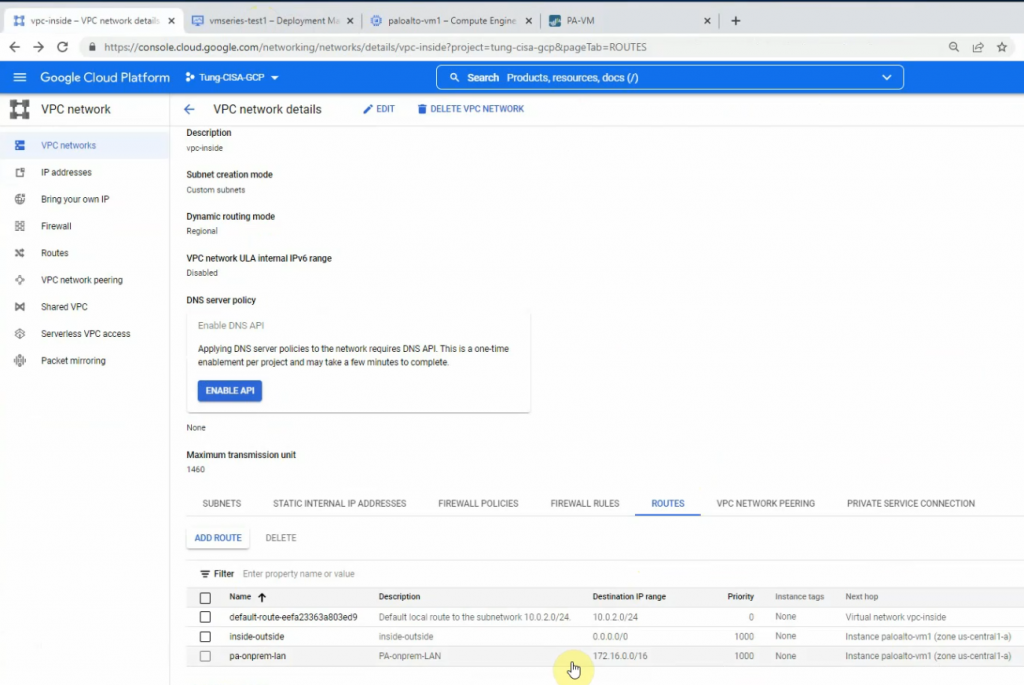
Go to the vpc-inside network, and create “Add route” to add a new route to LAN subnets of Palo Alto on-prem.
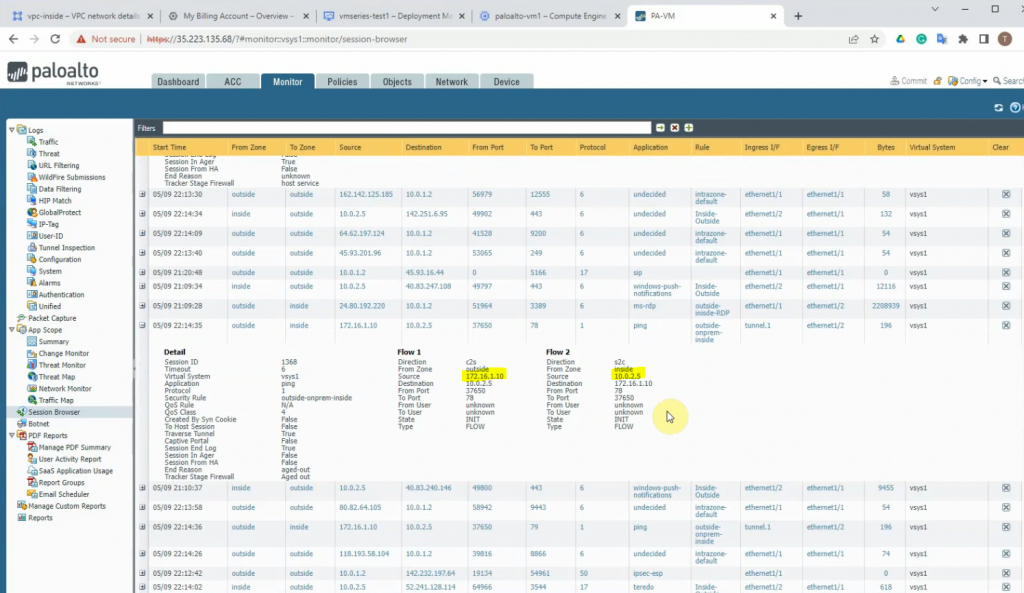
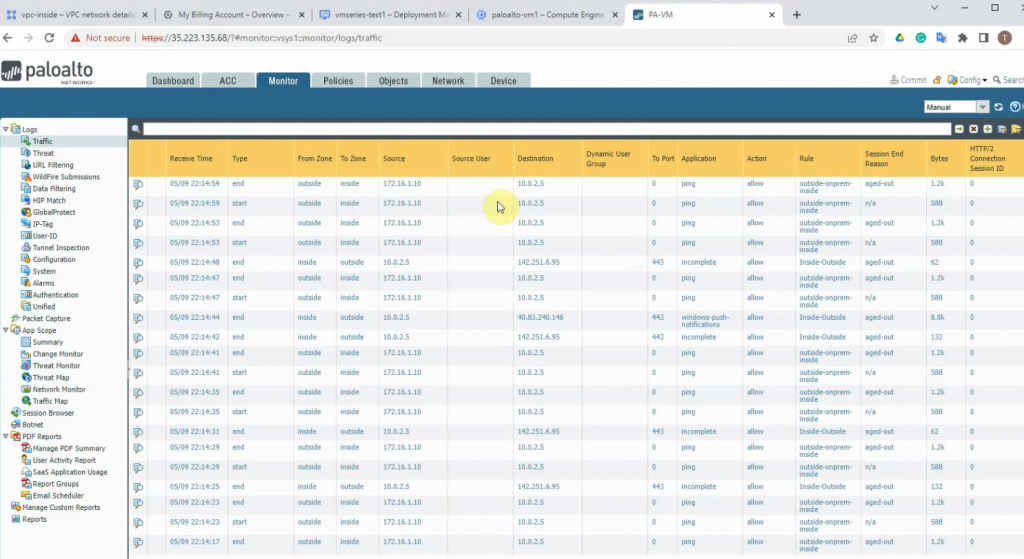
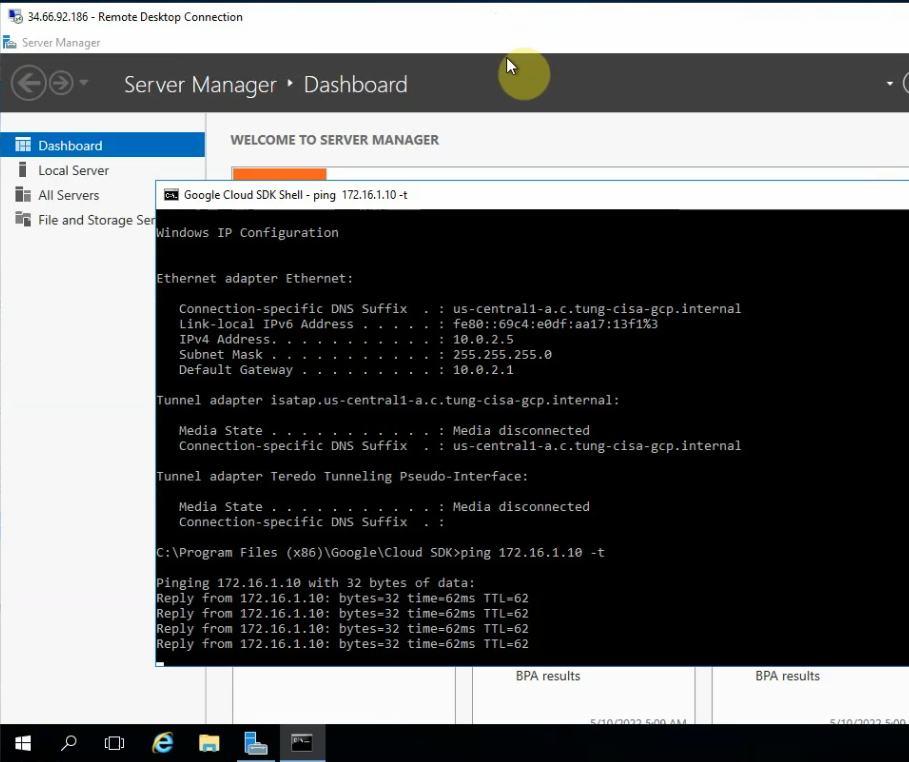
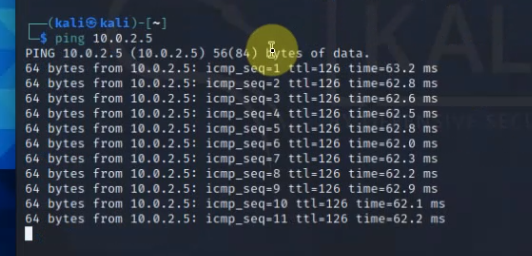
Ping Kali’s machine from Windows 2016 VM on GCP.
Ping the Windows 2016 VM on Kali’s machine.
The IPSEC tunnel is up on Palo Alto on-prem.
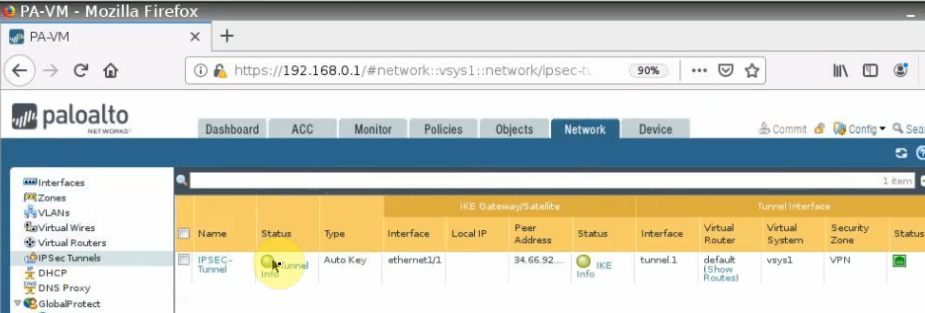
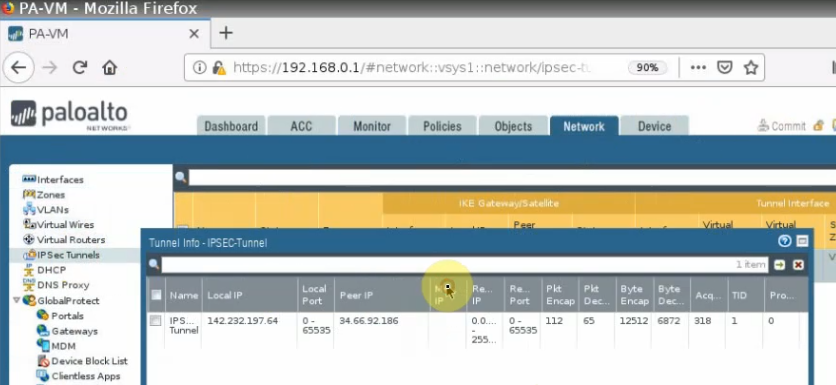
The IPSEC tunnel is up in Palo Alto on GCP.