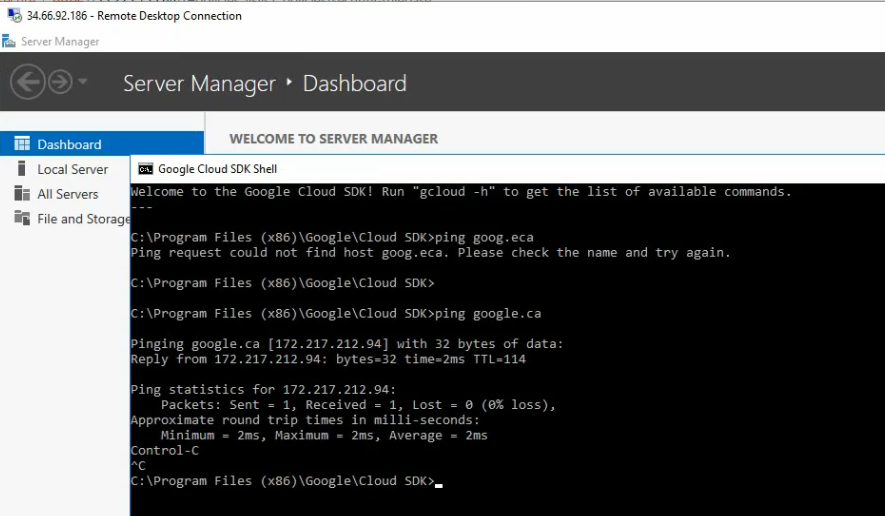
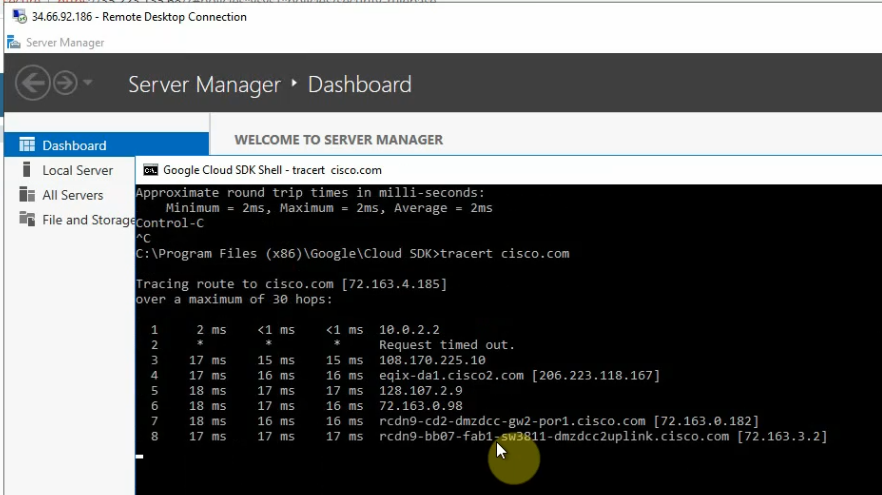
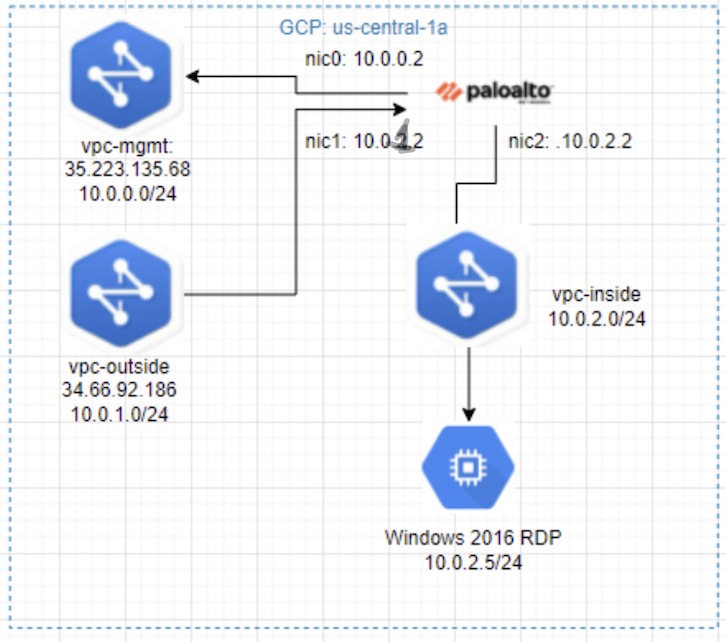
This is a diagram that I have used in this lab.
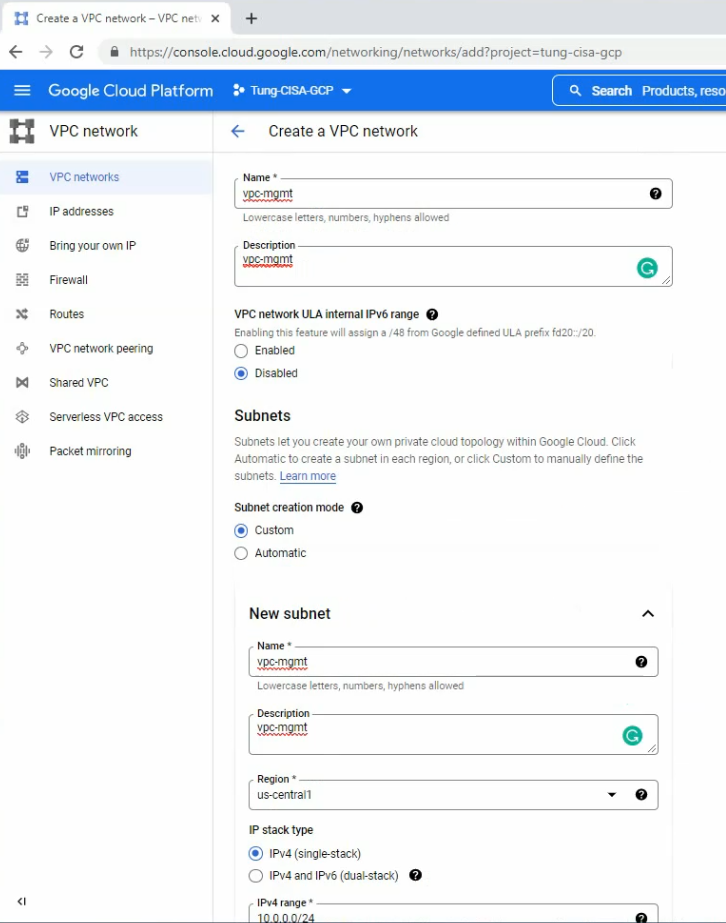
Below are several main steps in this lab:
- Create 3 vpc networks: vpc-mgmt (10.0.0.0/24), vpc-outside (10.0.1.0/24), and vpc-inside (10.0.2.0/24) on GCP.
- Create ingress/egress Firewall rules on the vpc networks.
- Launch Palo Alto instance on GCP.
- Launch Windows 2016 instance on the inside network.
- Create a default route, security rules, SNAT, and DNAT for RDP traffic from the Internet to Windows 2016 instance via Palo Alto.
- Modify the default route for the inside network to use the Palo Alto instance.
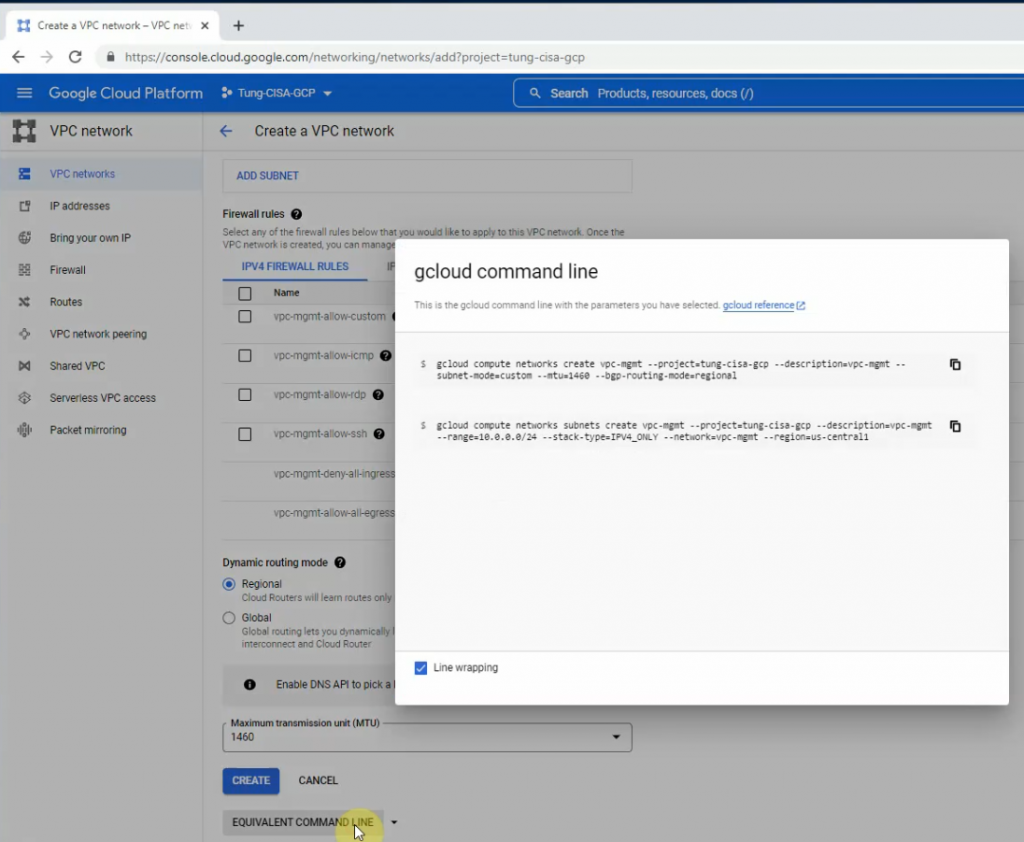
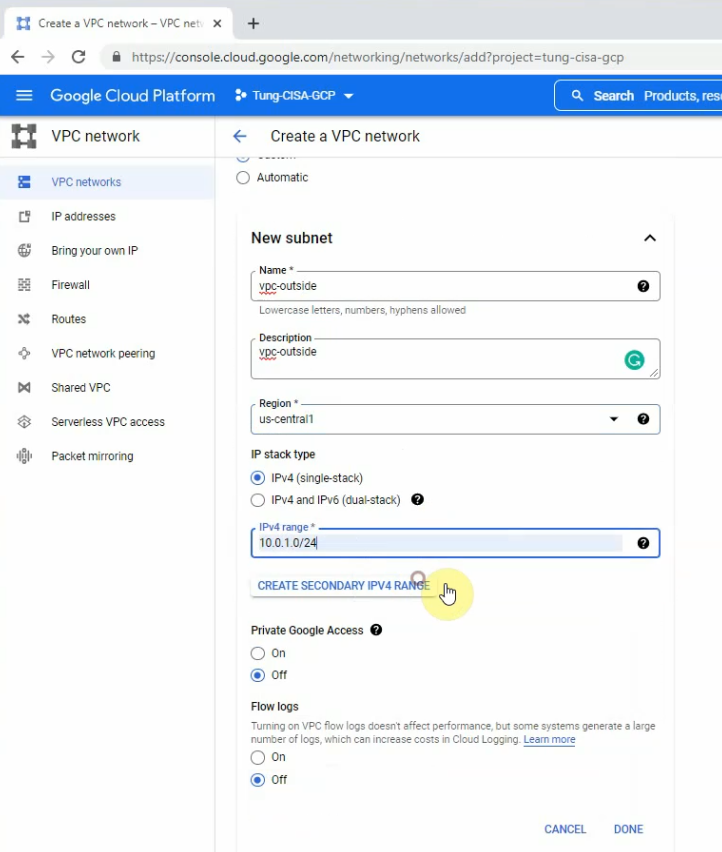
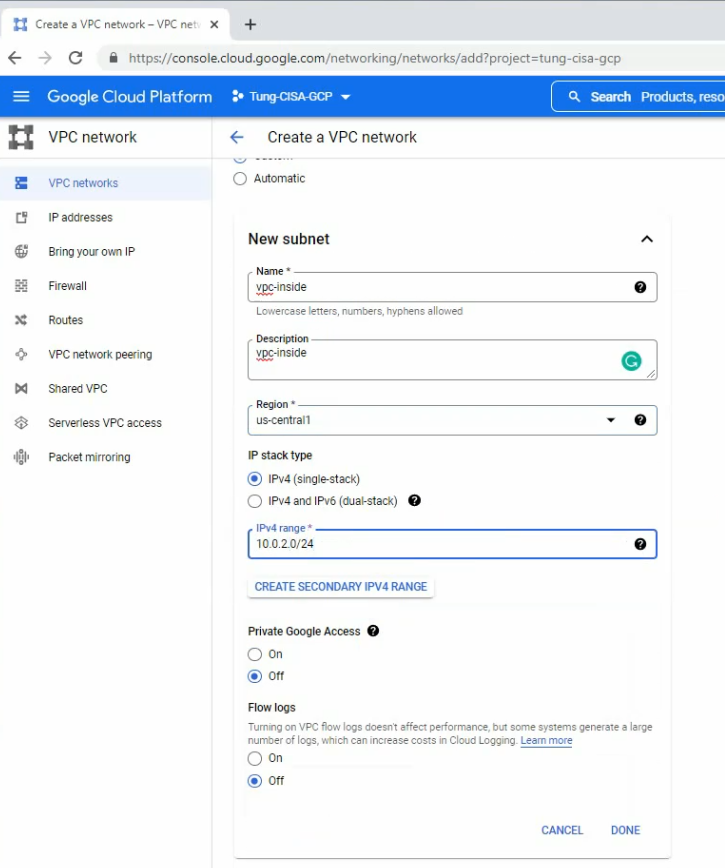
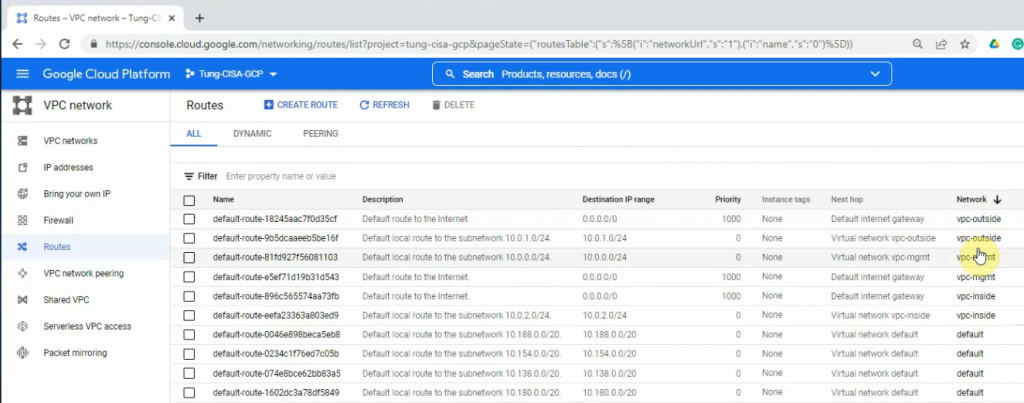
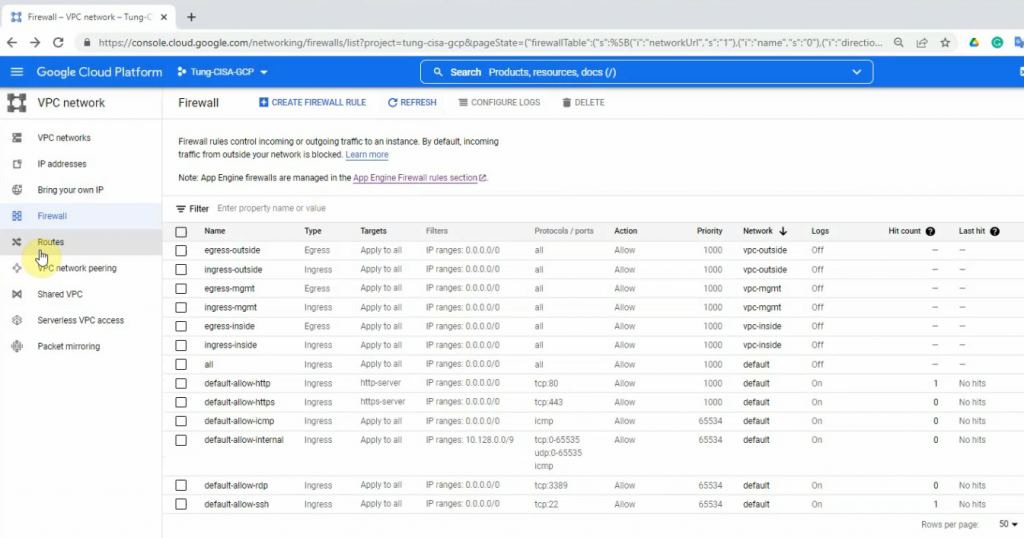
VPC Network – Route tables.
Go to VPC network – Firewall – Create a firewall rule for ingress/egress traffic from and to the network 0.0.0.0/0.
The ingress-mgmt rule.
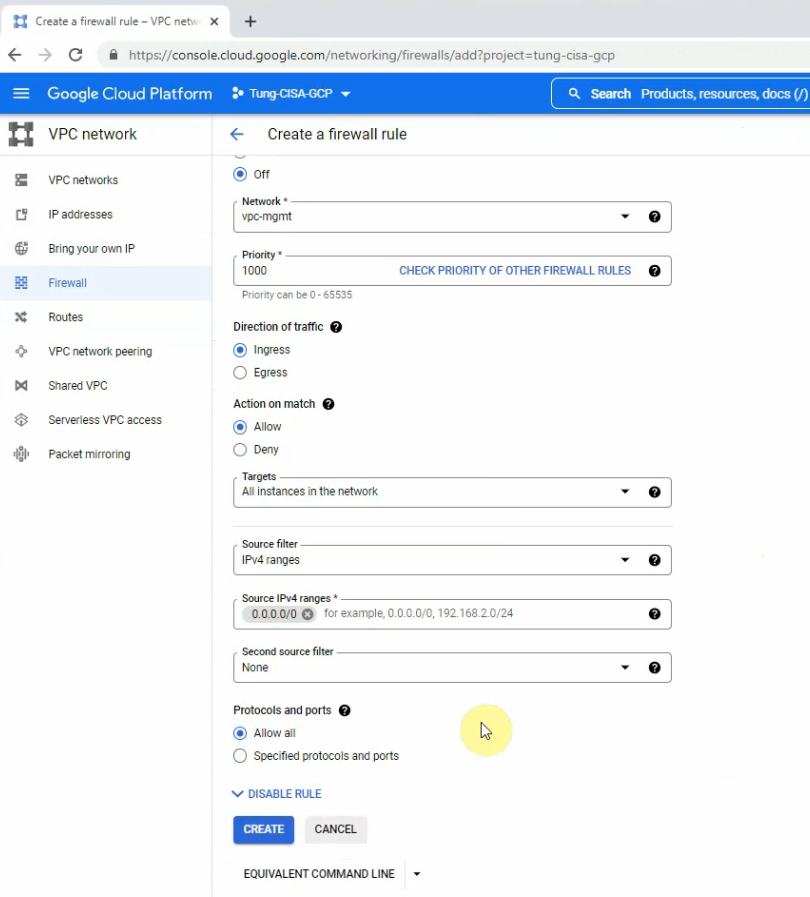
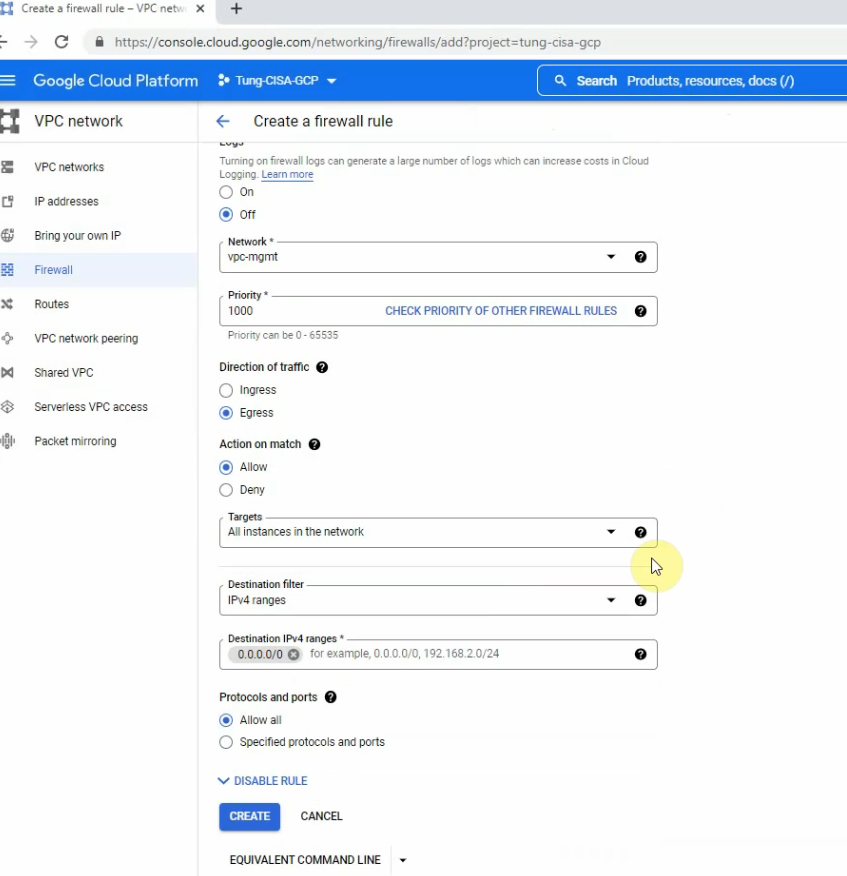
The egress-mgmt rule.
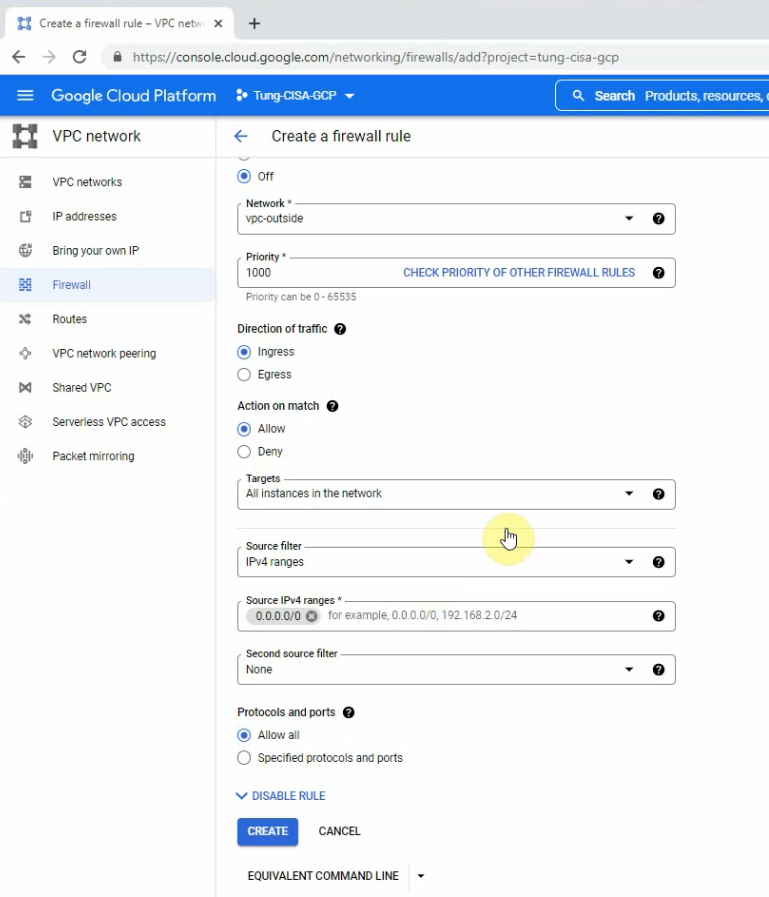
The ingress-outside rule.
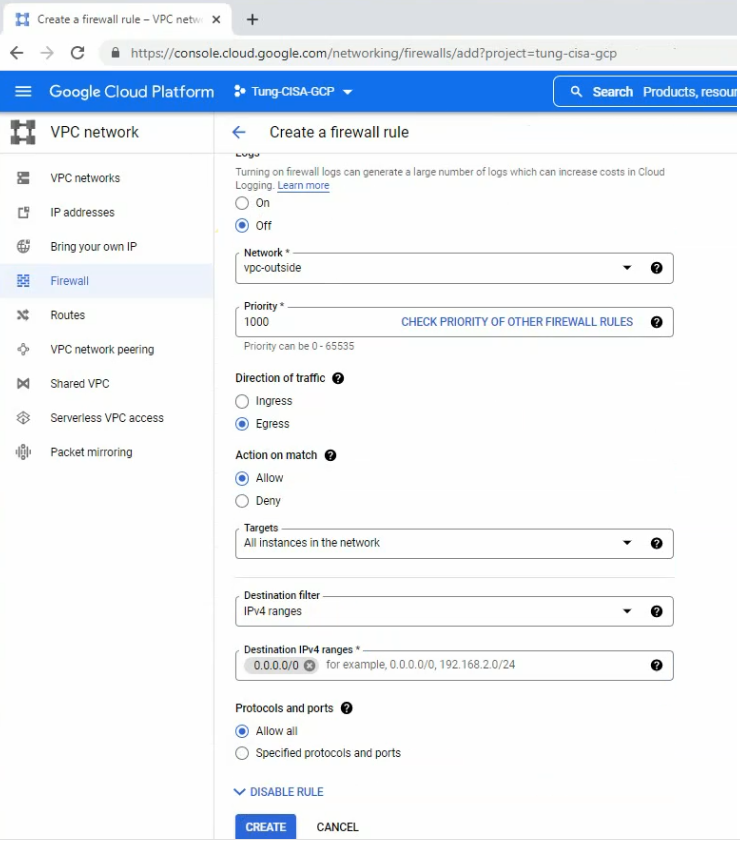
The egress-outside rule.
The ingress-inside rule.
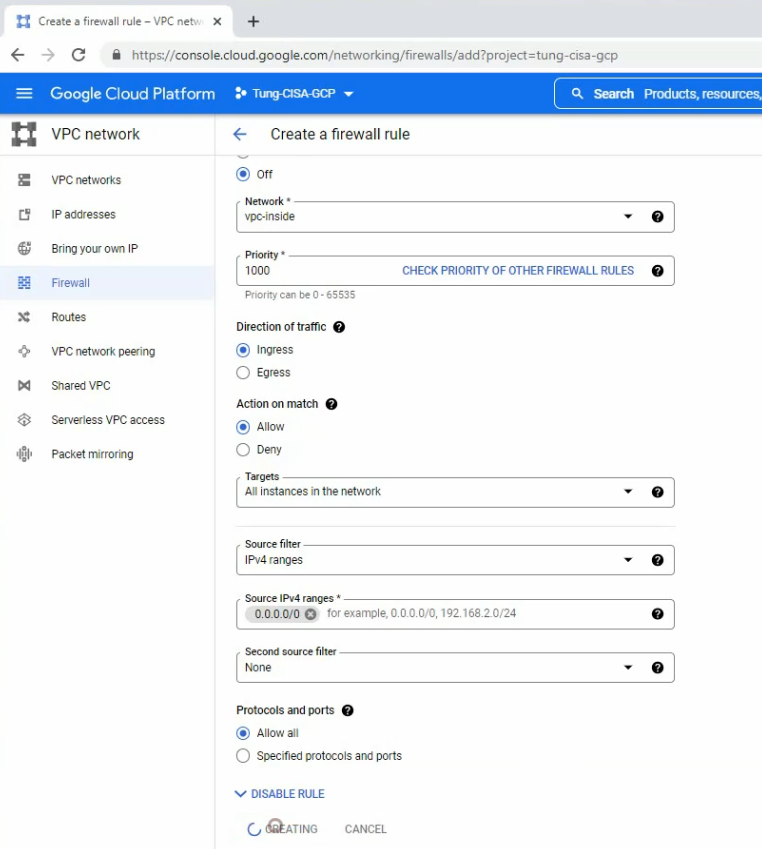
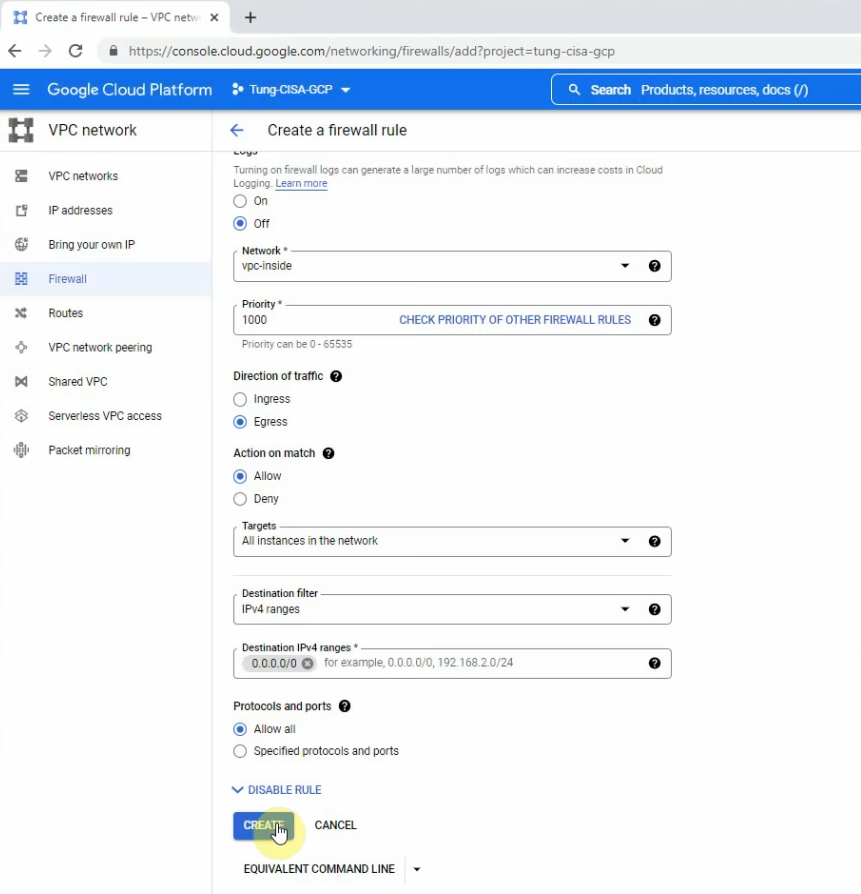
The egress-inside rule.
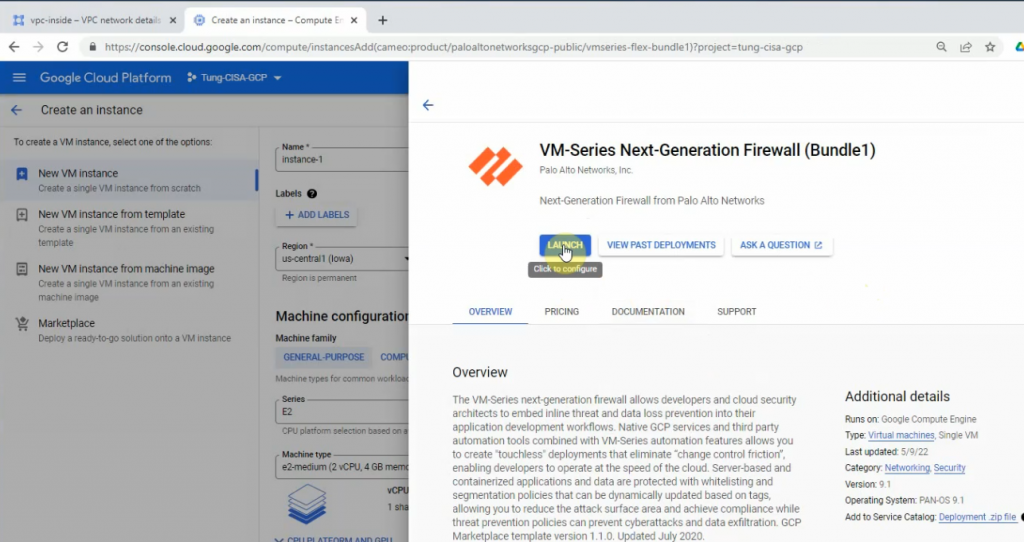
Go to Compute Engine – Create an instance – Marketplace – enter “Palo Alto” – select “VM-series Next-Generation Firewall (Bundle 1)” – click launch.
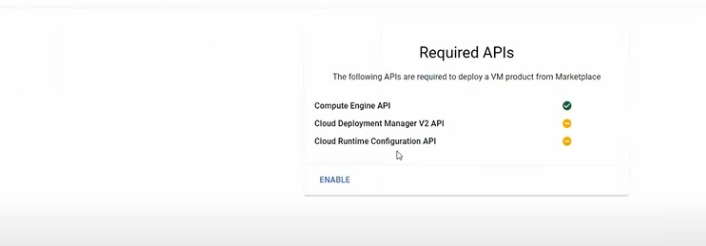
Click Enable on the Required APIs.
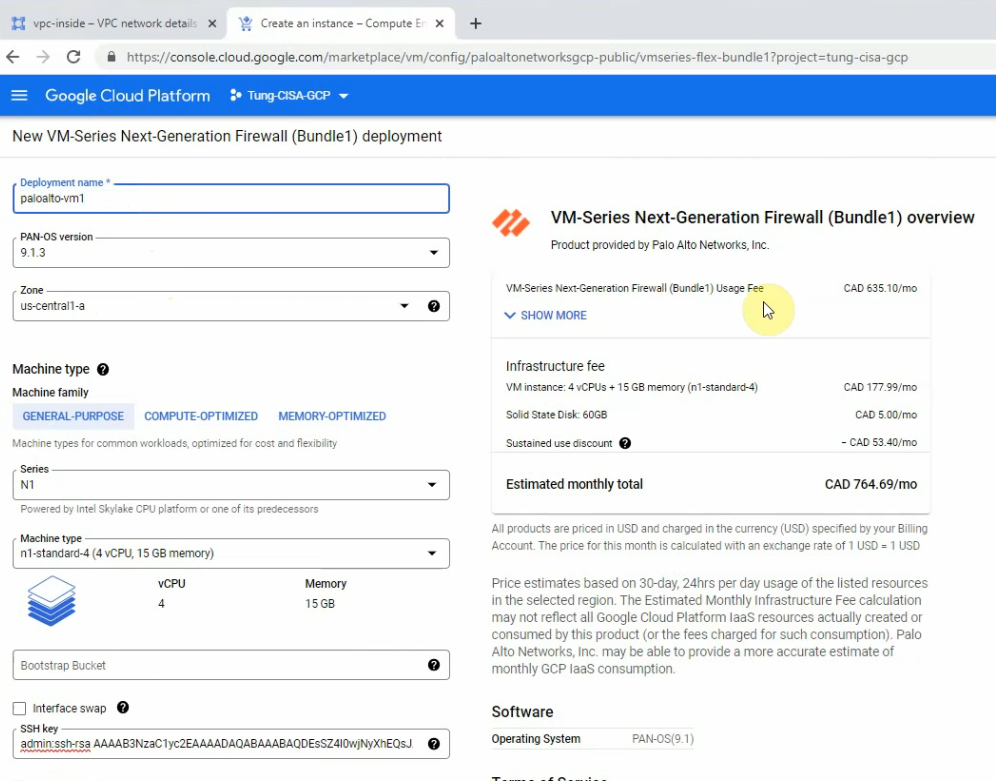
Back to create Palo Alto VM.
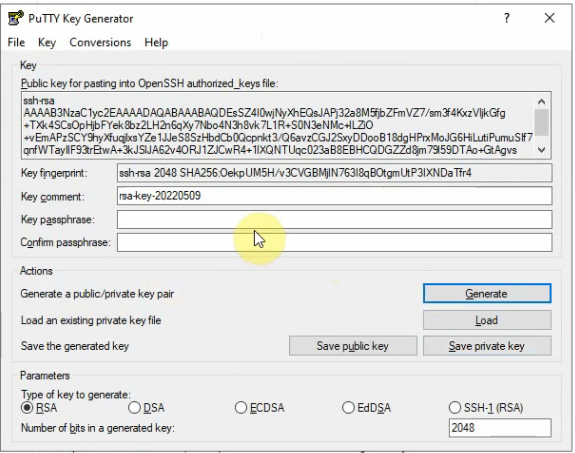
Using the puttygen to generate an SSH key pair. Click to save the public and private keys.
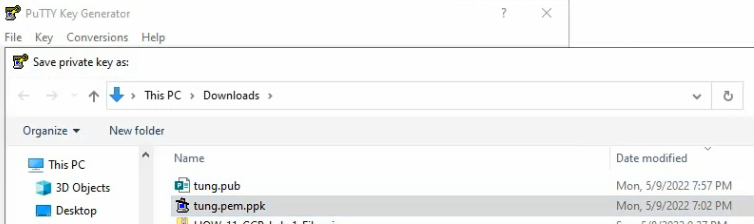
This is a public key that you need to submit when creating the Palo Alto VM on GCP.
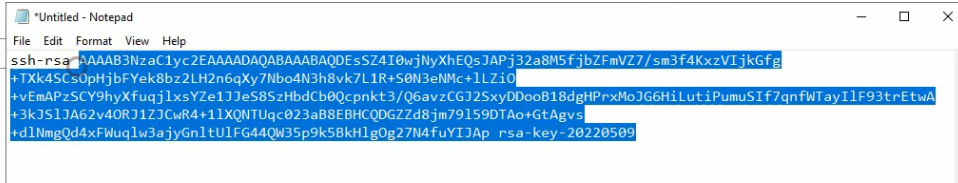
Copy the key and pass it into the SSH key.
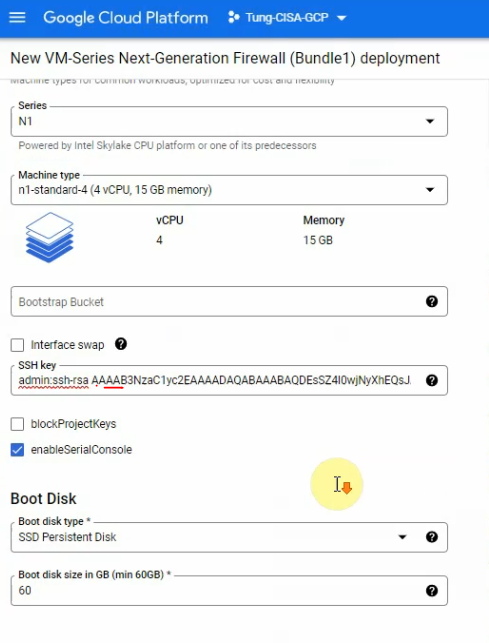
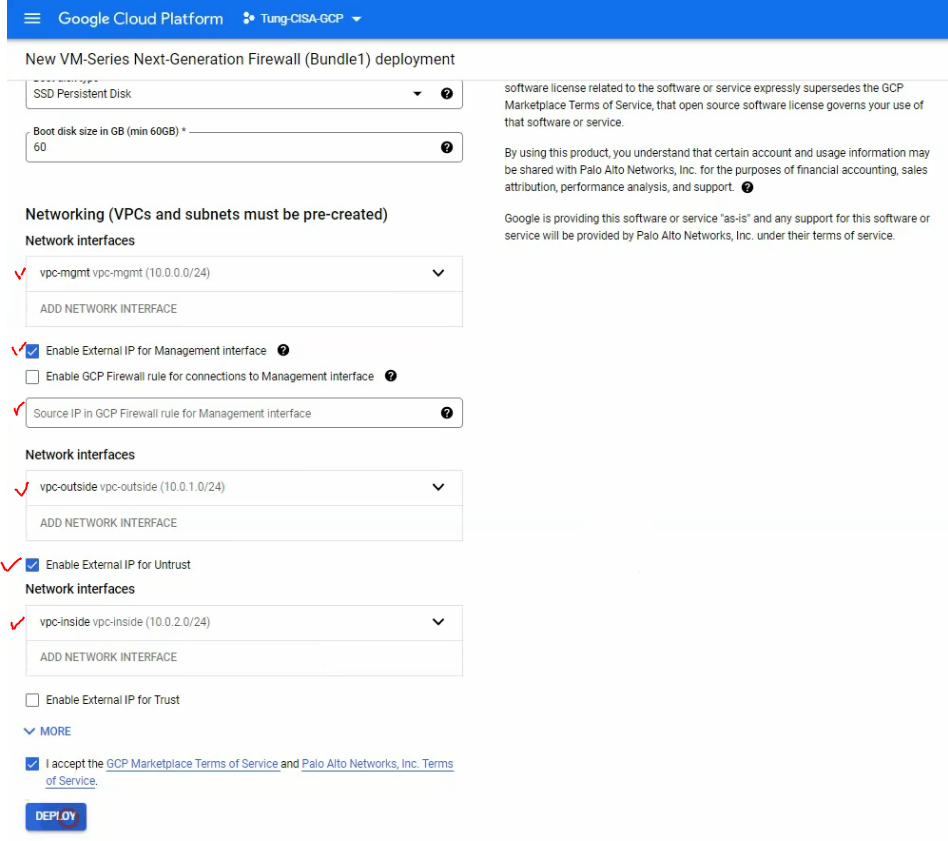
Select the interfaces like the following screenshot. Then, click “Deploy”.
Wait a couple of minutes to see the “Palo Alto has been deployed” notification.
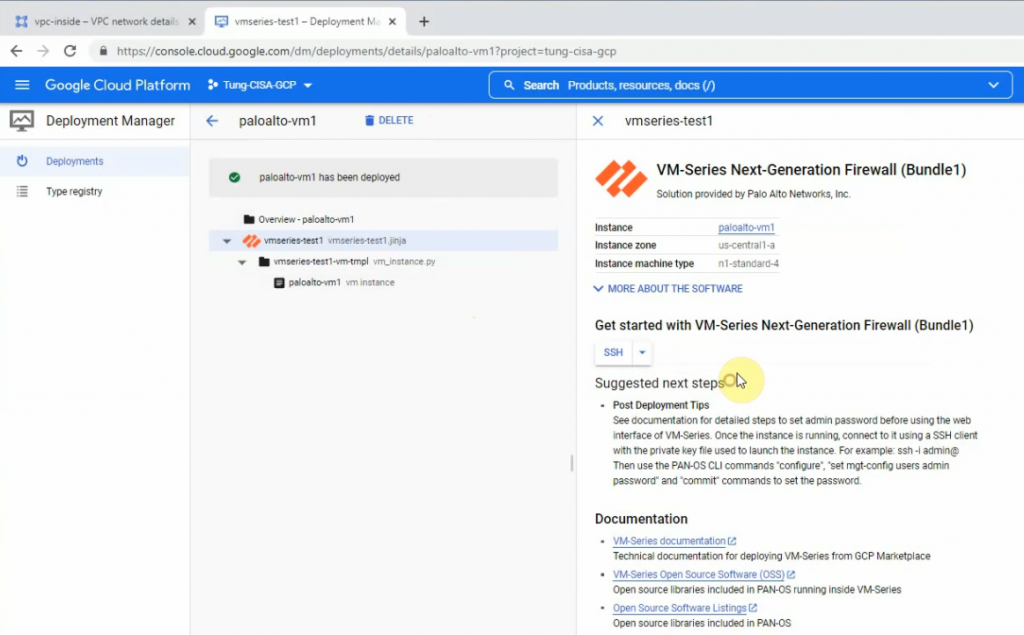
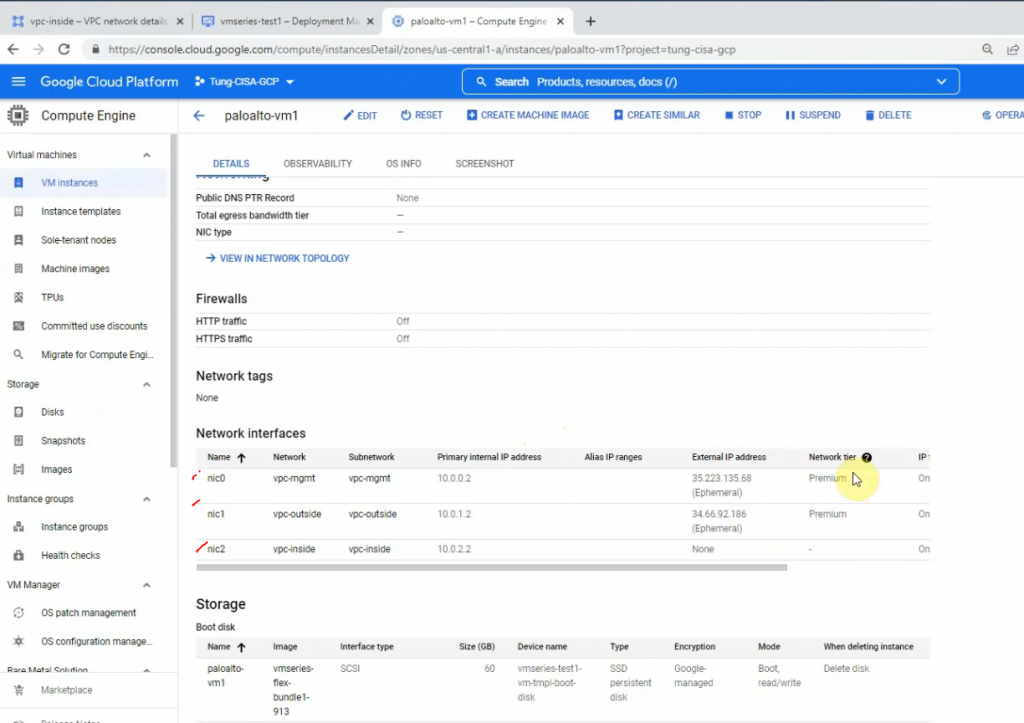
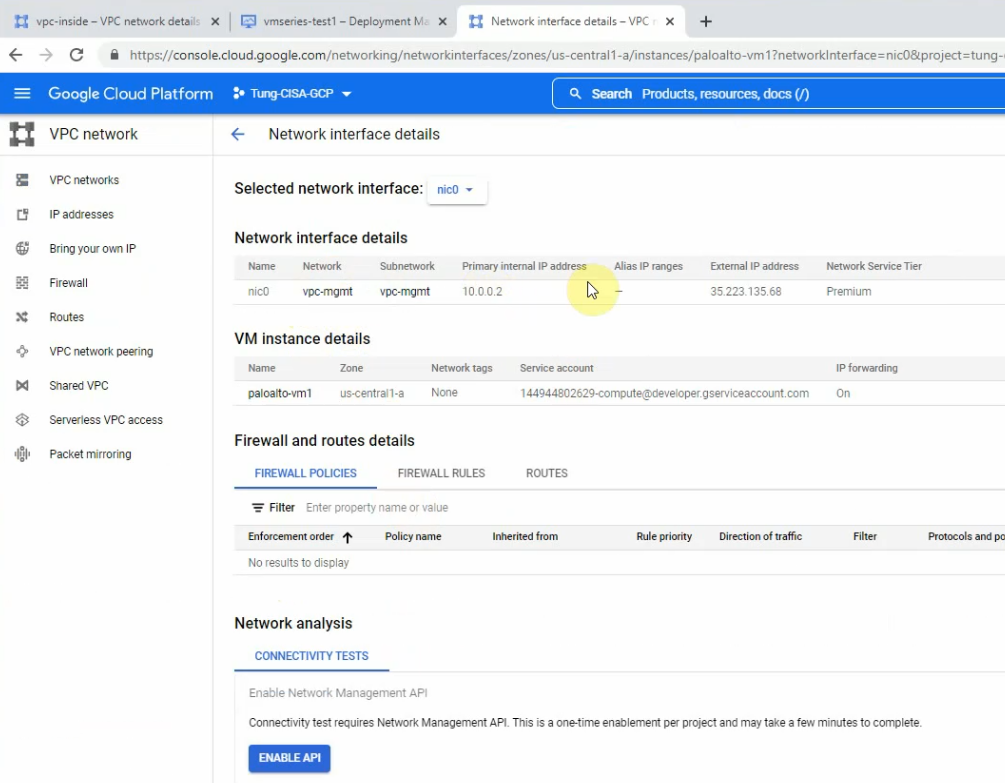
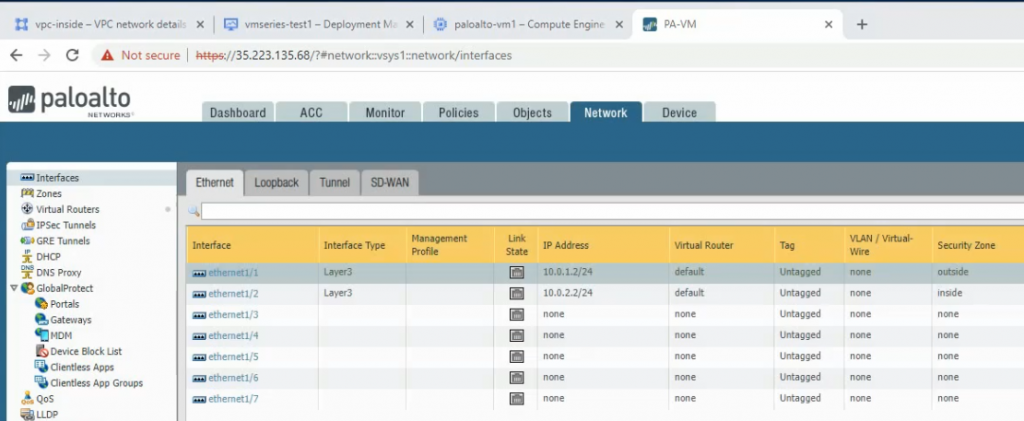
Get the external IP address of mgmt and outside interfaces.
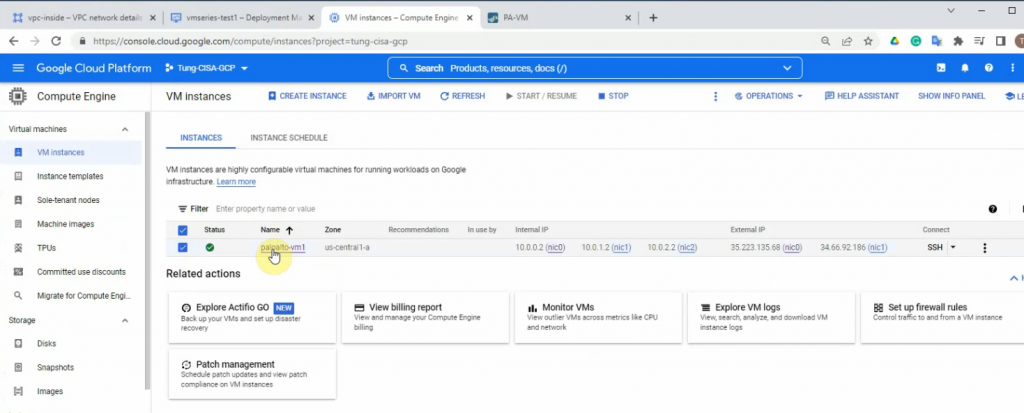
Compute Engine – VM instances – paloalto-vm1.
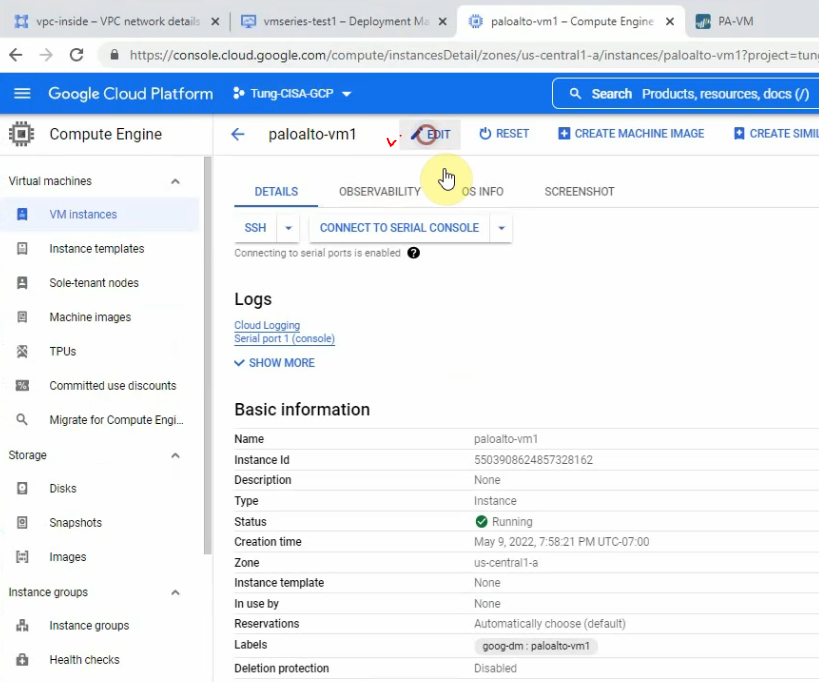
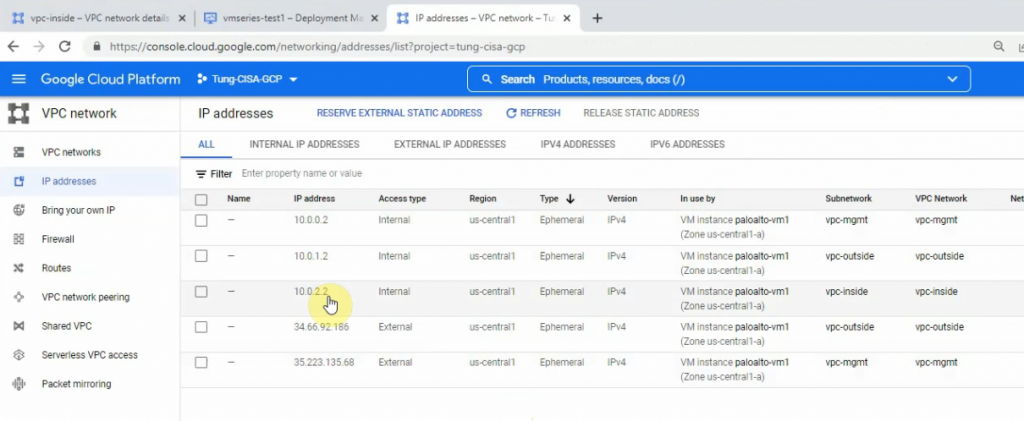
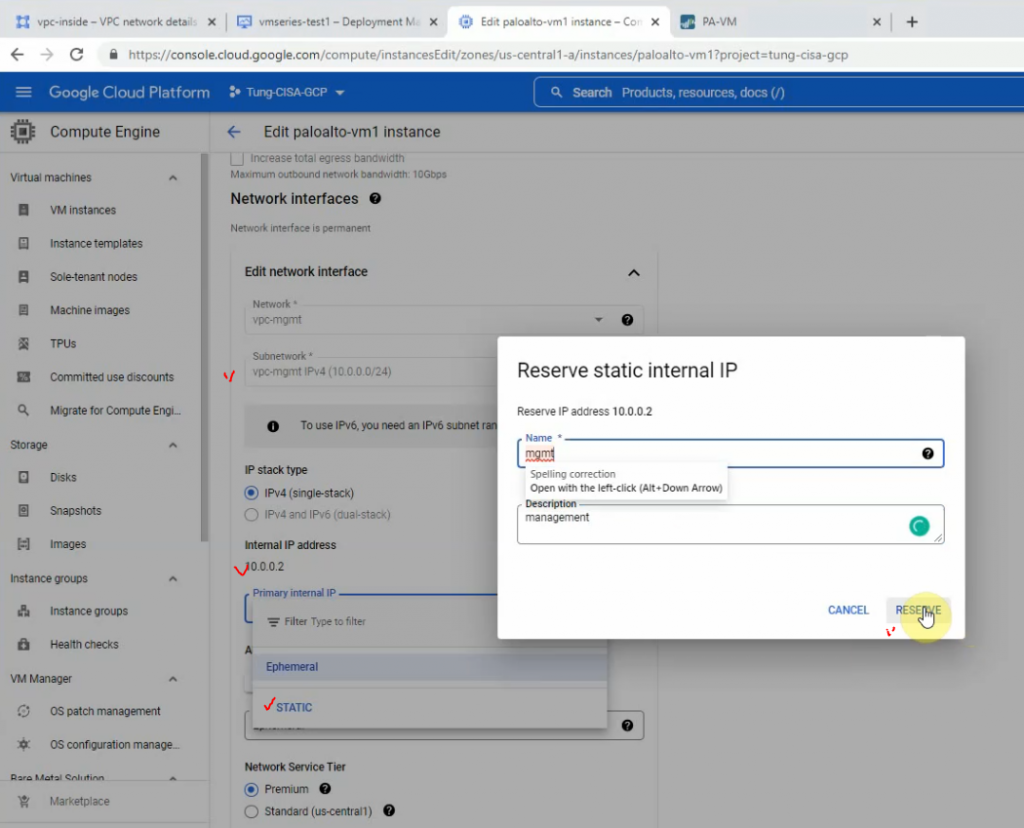
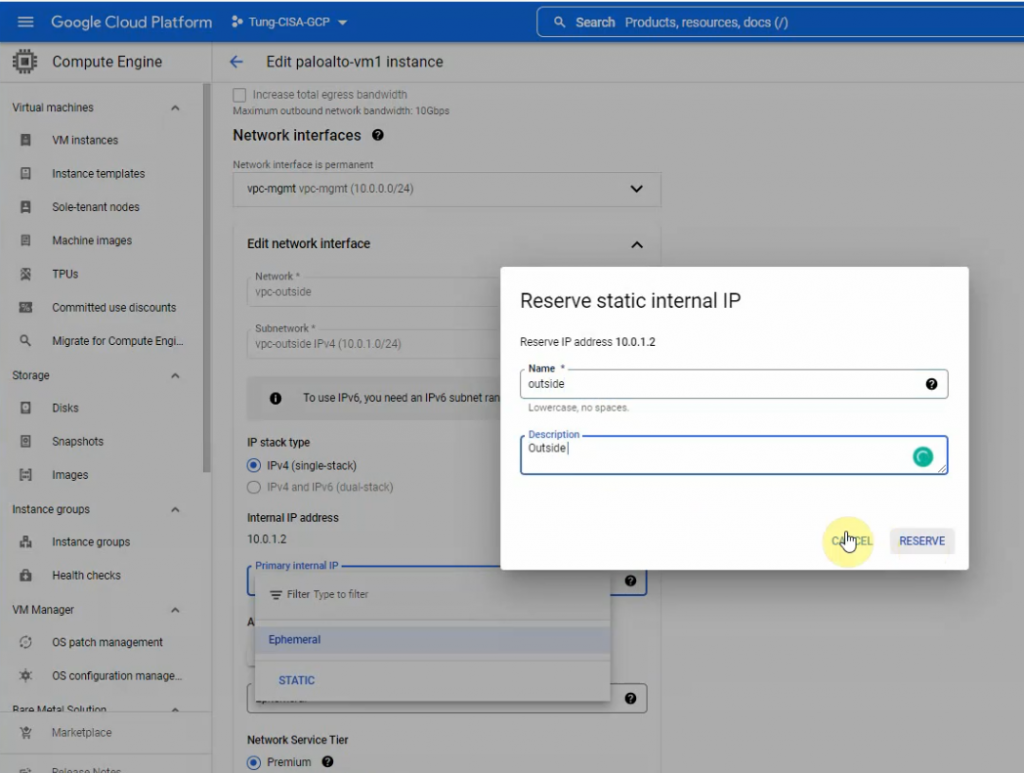
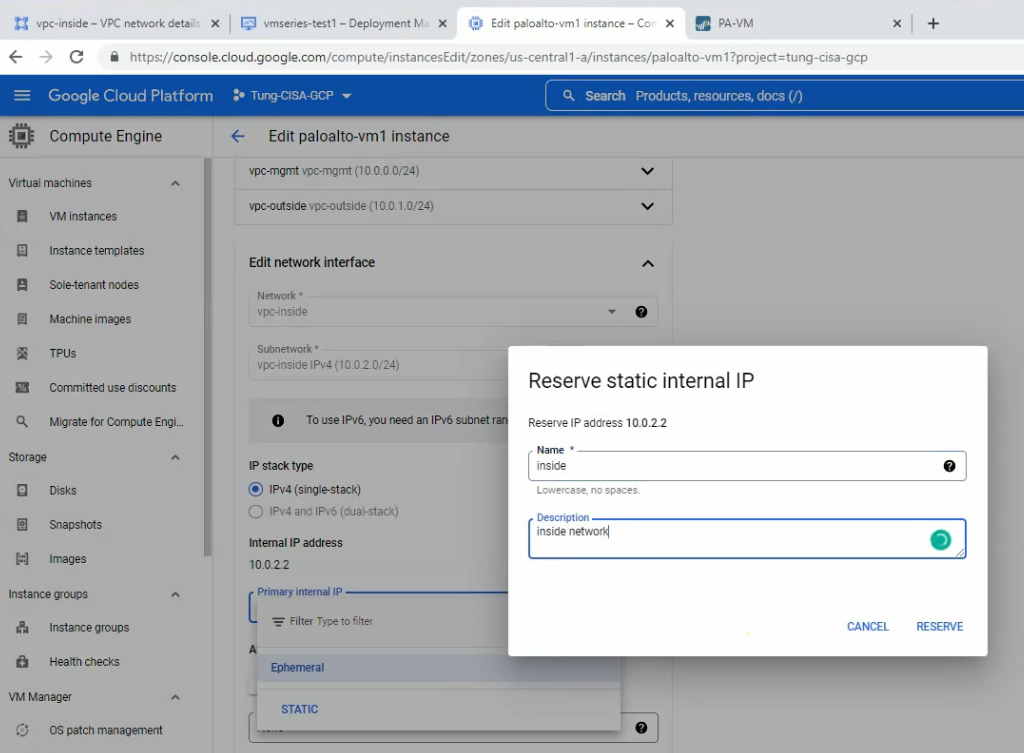
Reserve the static IP address 10.0.0.2, 10.0.1.2 and 10.0.2.2 for mgmt, outside and inside network on Palo Alto.
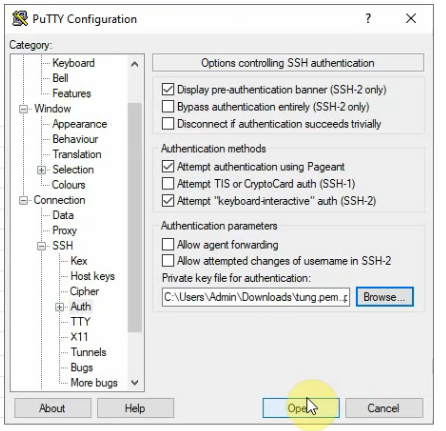
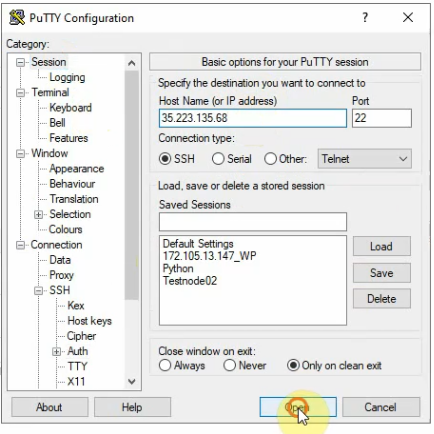
Open Putty and load the private key that you have saved in the previous step.
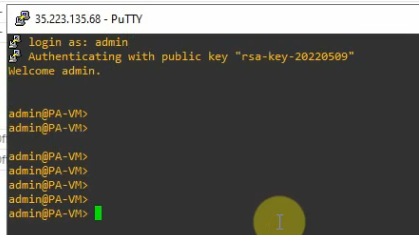
configure
set mgt-config users admin password
commit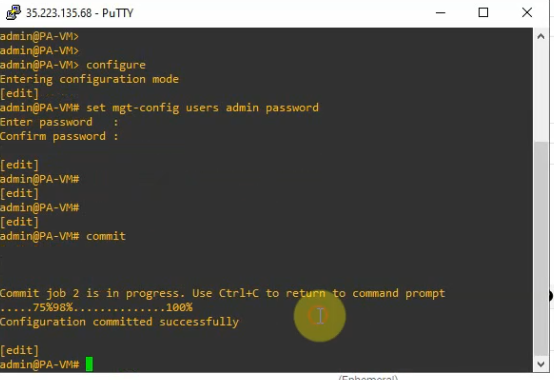
Open your web browser and enter https://35.223.135.68.
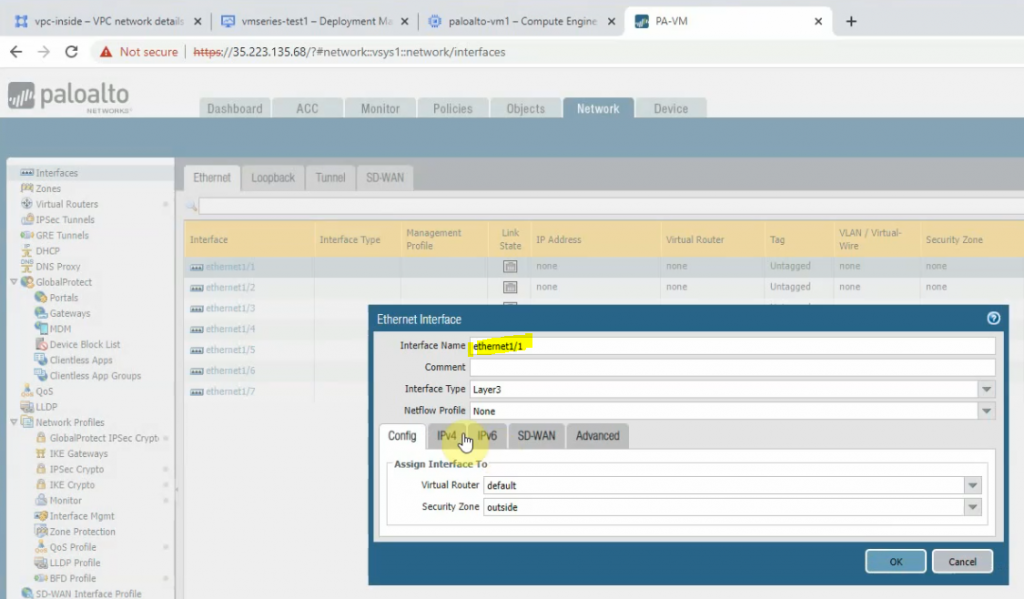
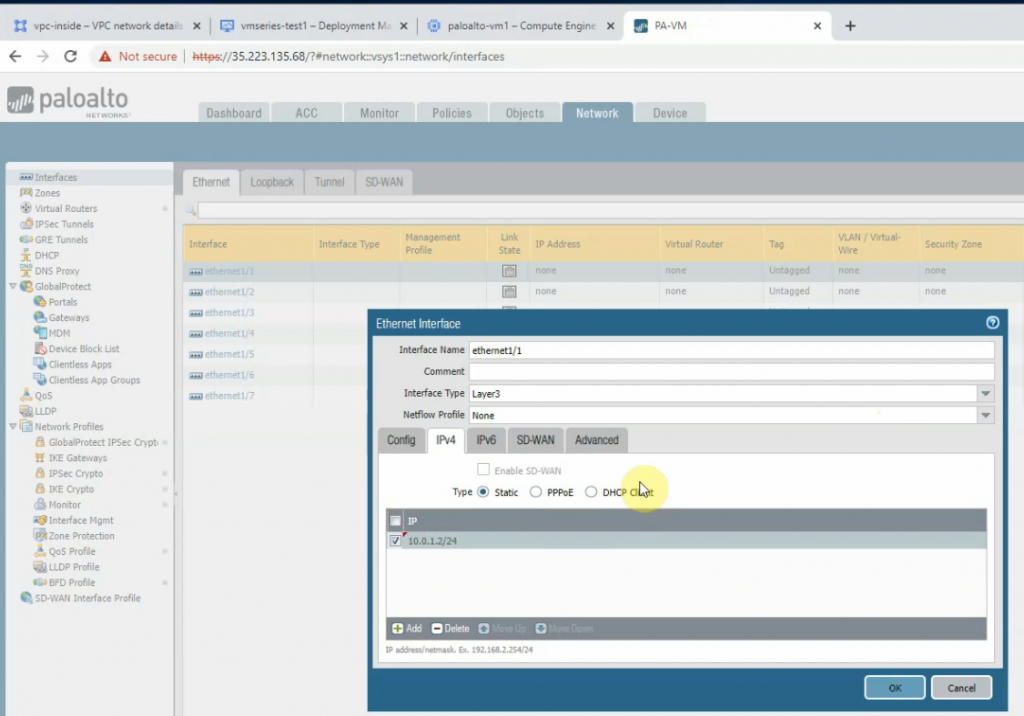
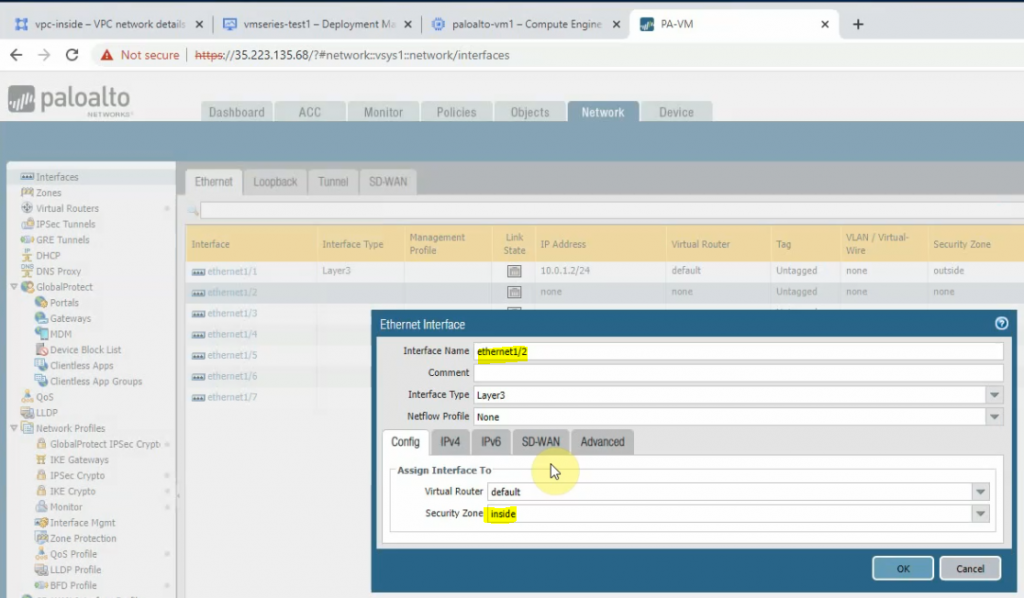
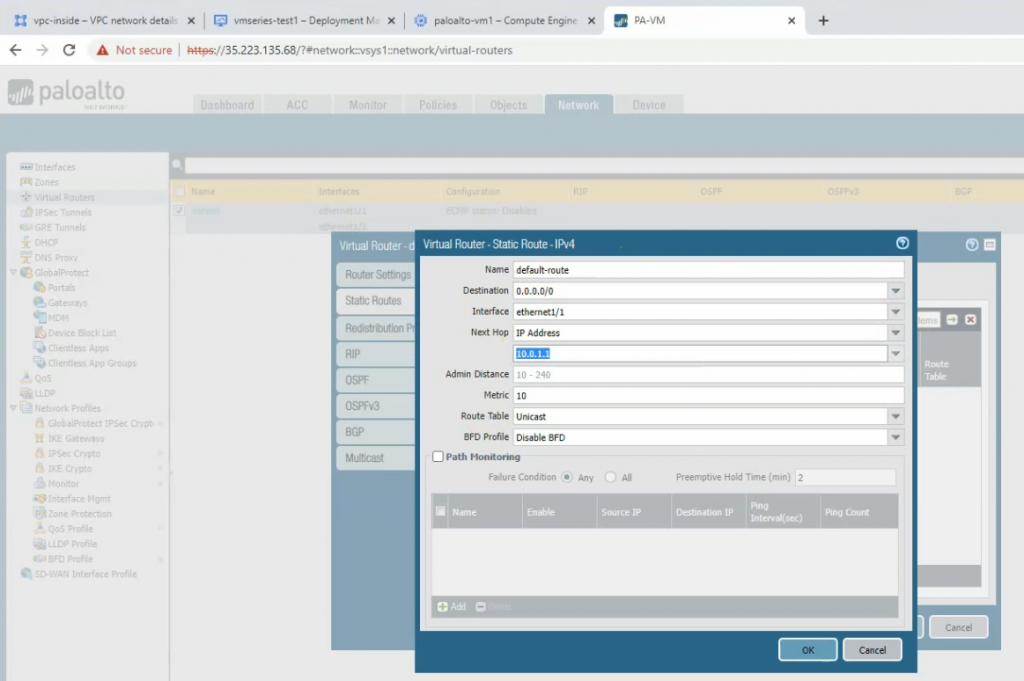
Create a default route on Palo Alto.
Go to Compute Engine – Create a new Windows 2016 VM.
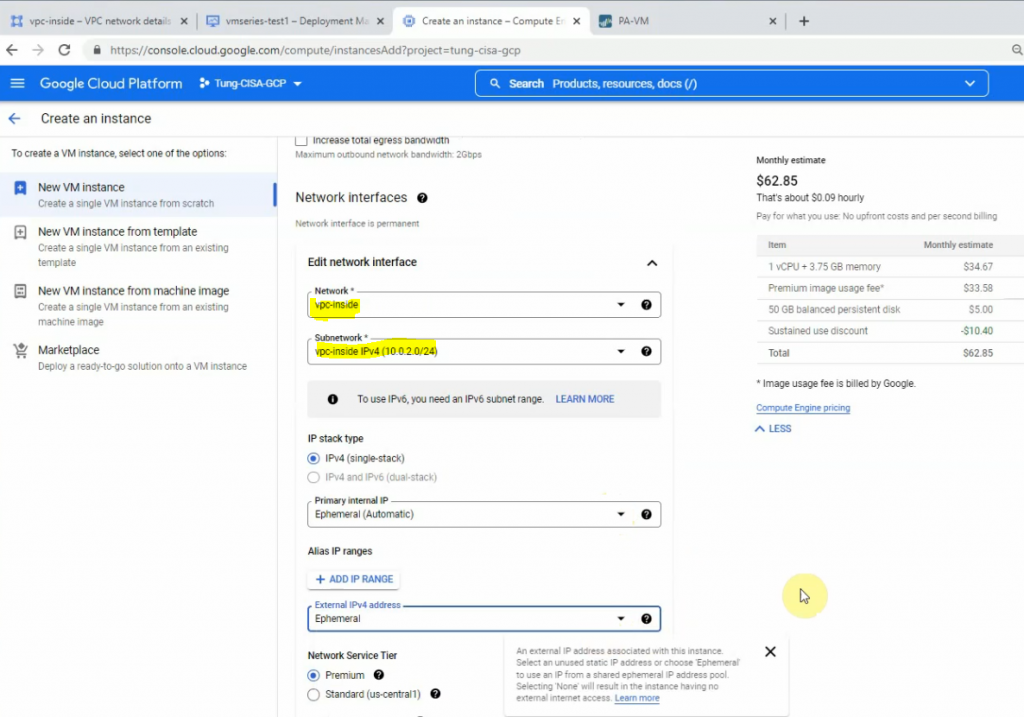
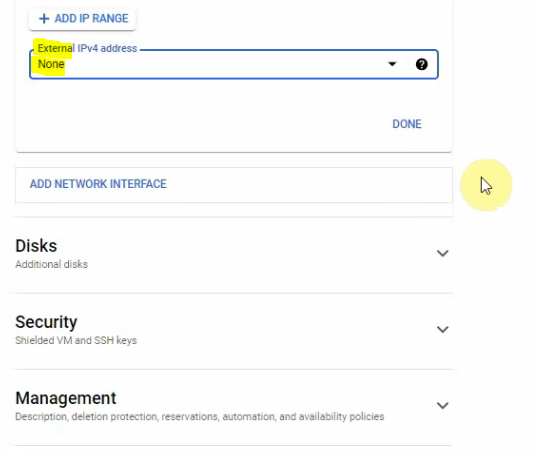
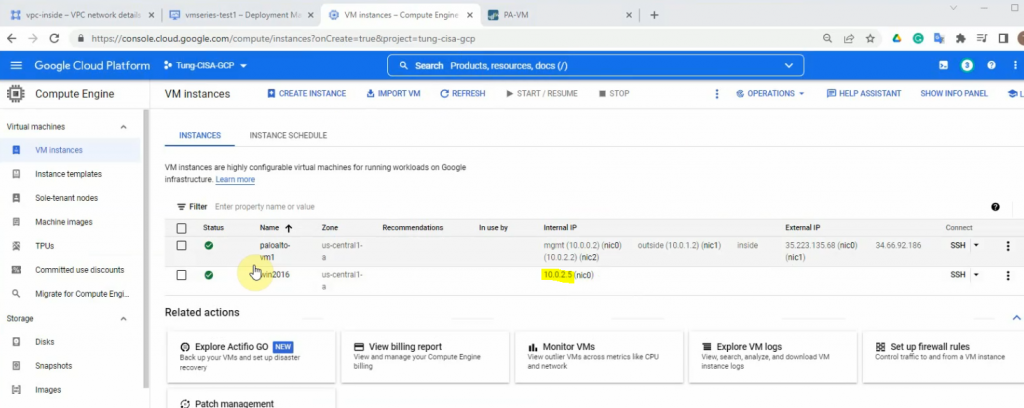
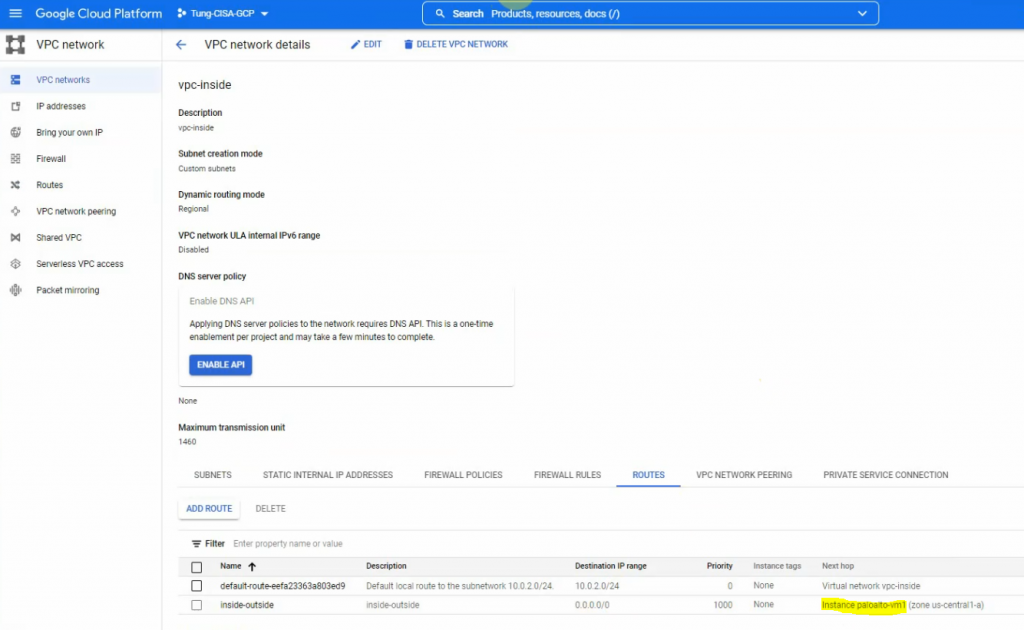
Back to the VPC network – Routes to change the default route of the inside network to the Palo Alto instance. Delete the highlighted route as the screenshot below.
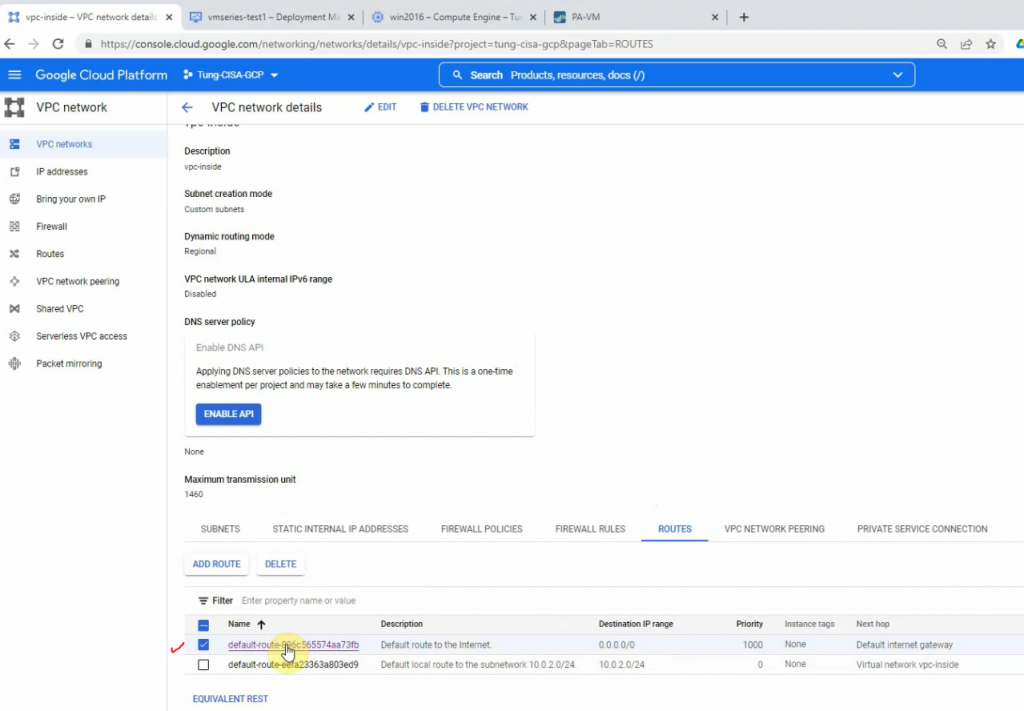
Create a new default route, and change the next hop instance from the internet gateway to use the Palo Alto instance.
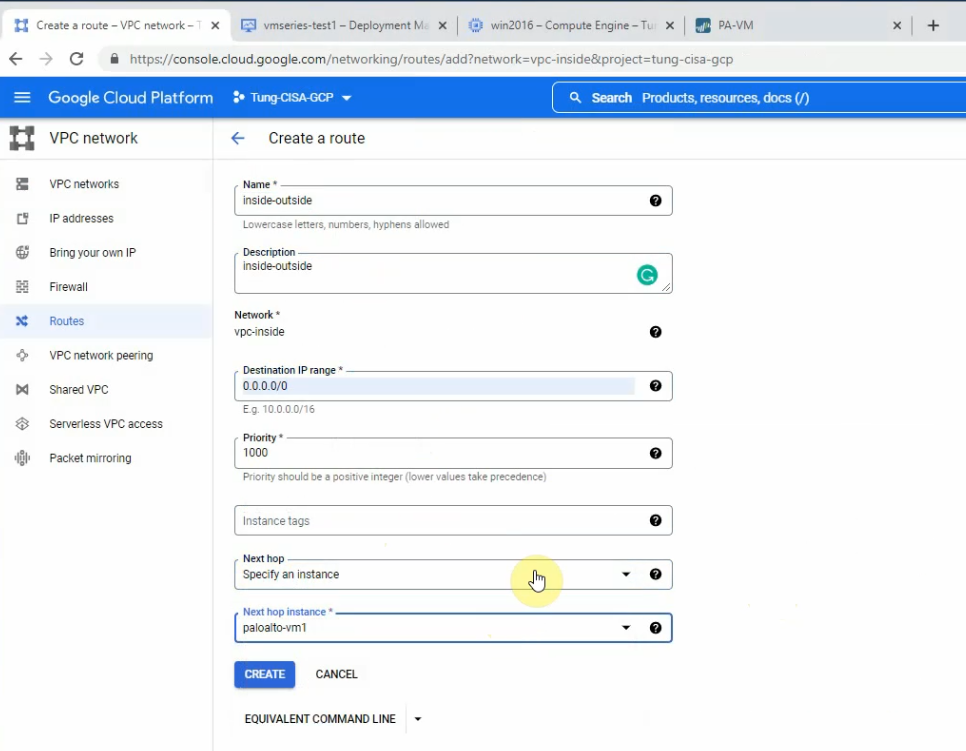
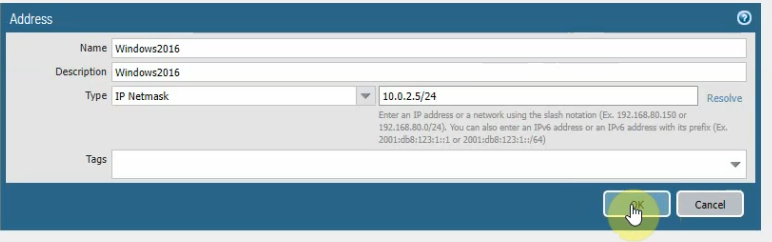
Create a new Windows 2016 instance object on Palo Alto.
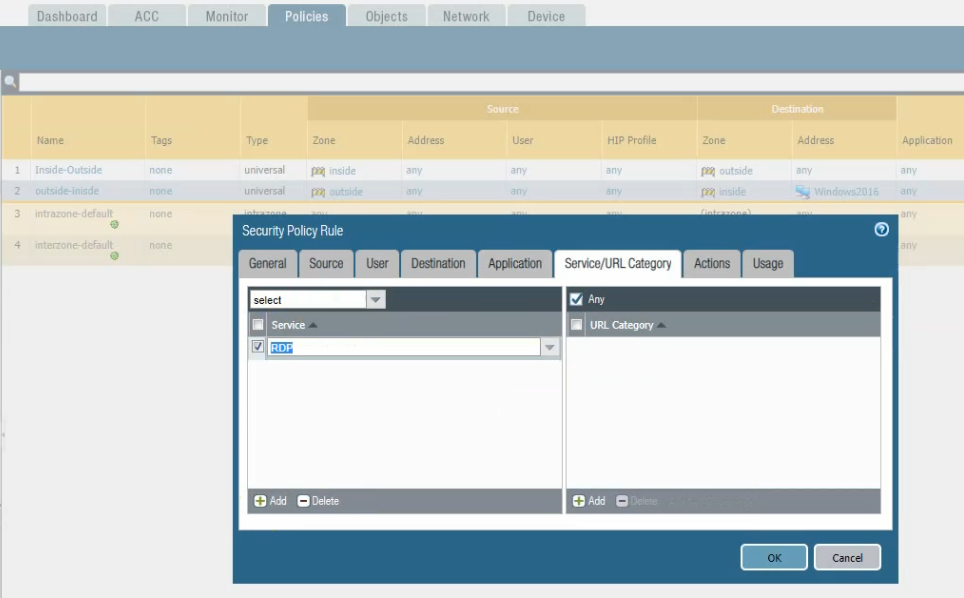
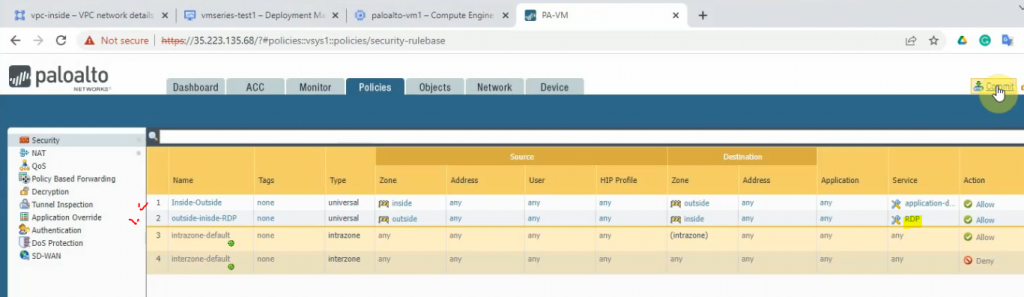
Create both access rules to allow traffic from the inside network to the outside, and from the Internet to the Windows 2016 VM.
The outside network to RDP service on the inside network.
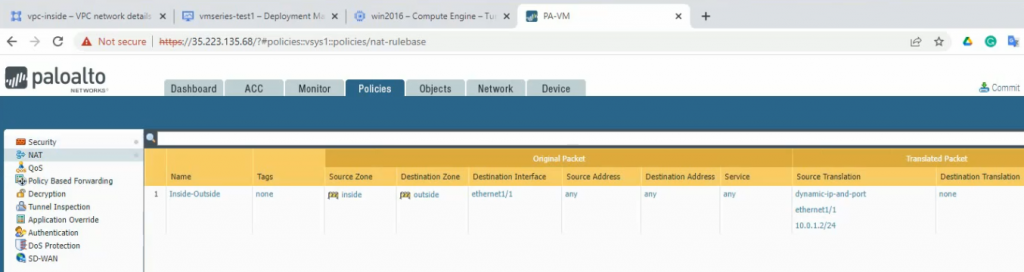
Create SNAT to allow traffic from the inside network to the outside network via the Palo Alto.
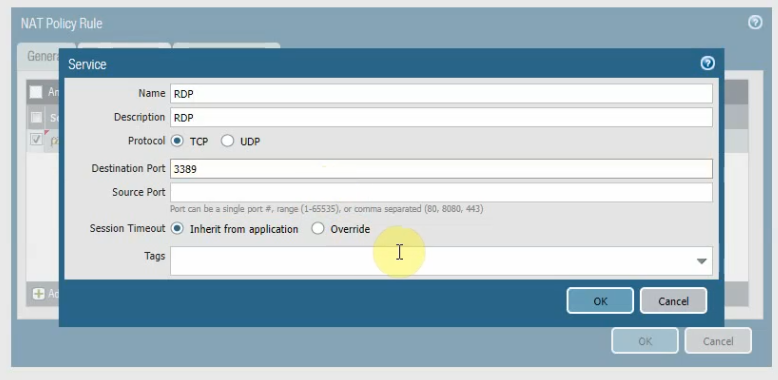
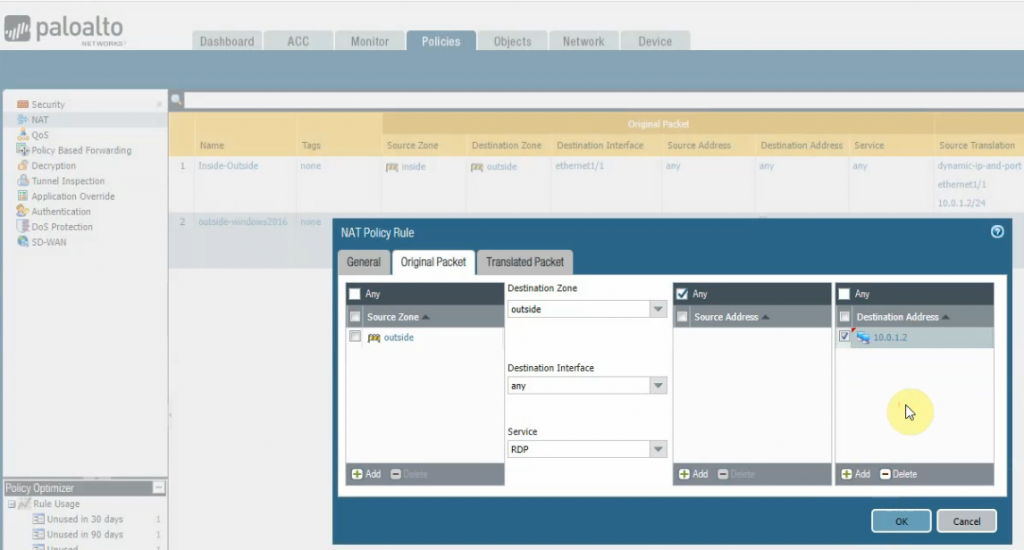
Create a DNAT rule to allow RDP traffic from the Internet to Palo Alto and DNAT to Windows 2016 instance.
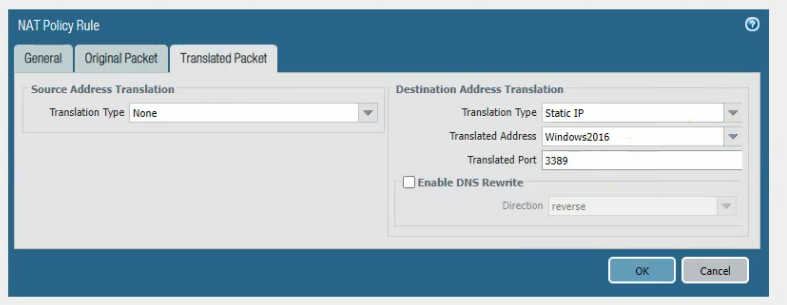
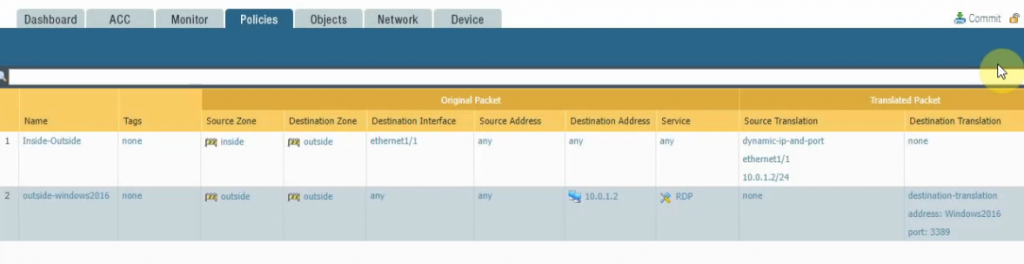
Click commit.
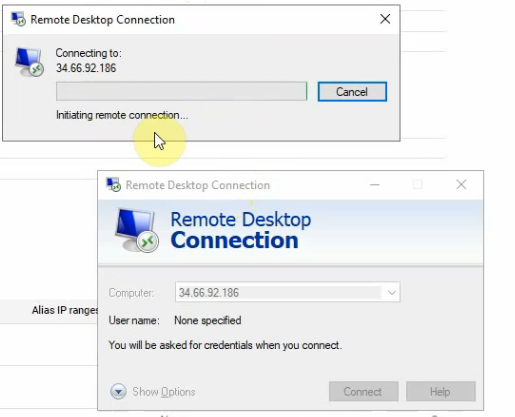
Open RDP on a Windows machine and enter the public IP address of the vpc-outside network on Palo Alto.
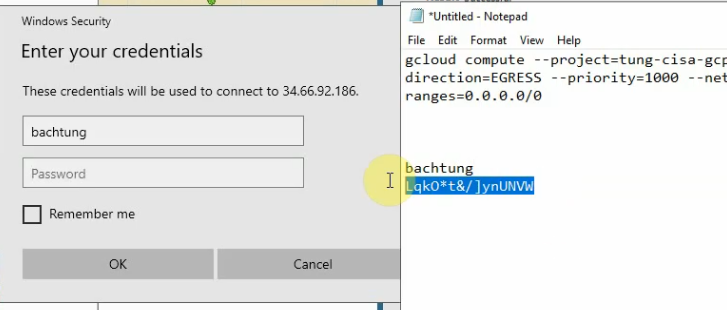
Enter your username and password.
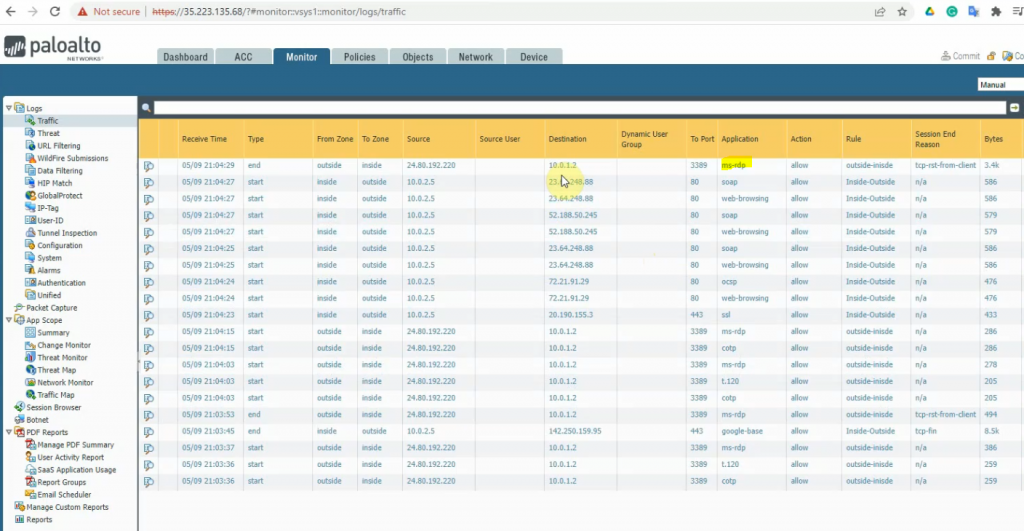
The Windows instance is able to access the Internet via Palo Alto.