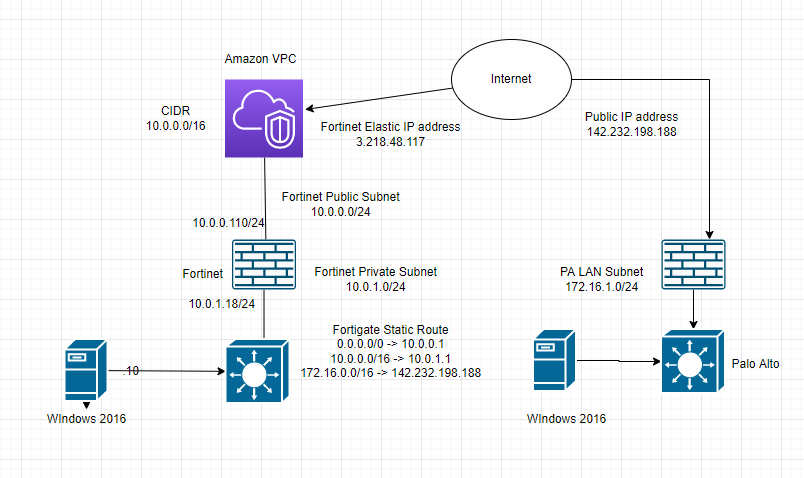
This is a diagram to show how to create a VPN site to site connection from PA on-prem and FG on AWS.
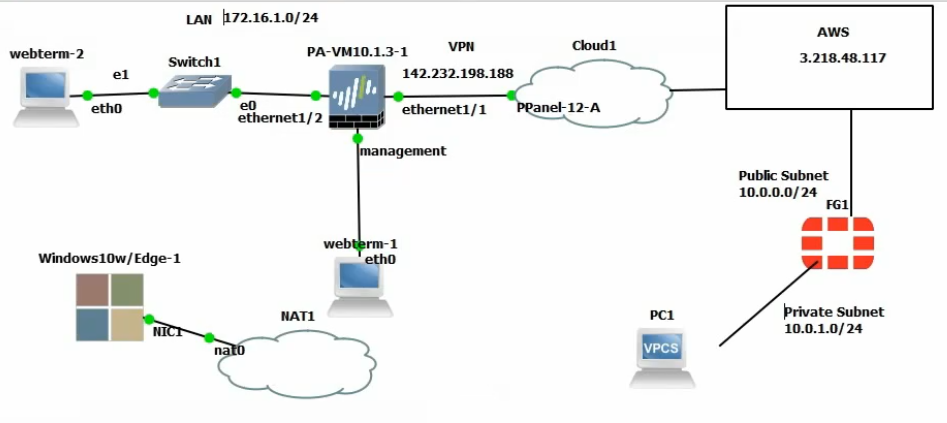
In this lab:
- Create a VPC, subnets, Internet gateway, route tables.
- Create a FortiGate VM and Windows 2016 instance on AWS
- Configure Palo Alto
- Create VPN site to site between both sites PA and FortiGate
- Allow Windows 2016 instance to access the Internet via FortiGate. Also, allow RDP to this machine via the Internet by using FortiGate.
- Test ping traffic between both sites.
- Allow a machine on the PA LAN subnet to access the Internet and the Windows 2016 instance on AWS.
- Create a new SSLVPN portal on AWS and test to access the portal via SSLVPN.
+ Below are a couple of steps to deploy FortiGate on AWS.
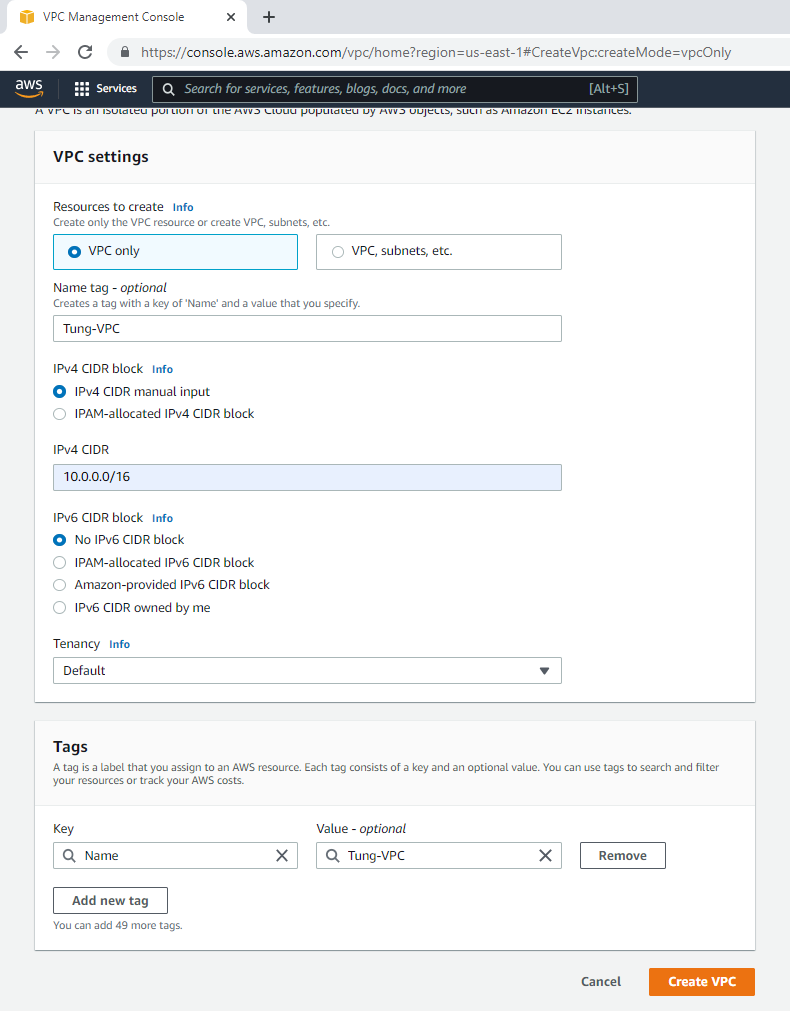
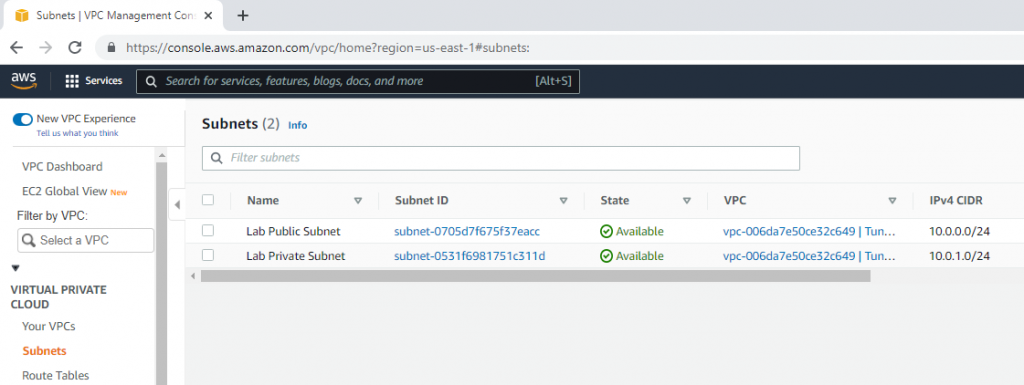
Create a new VPC.
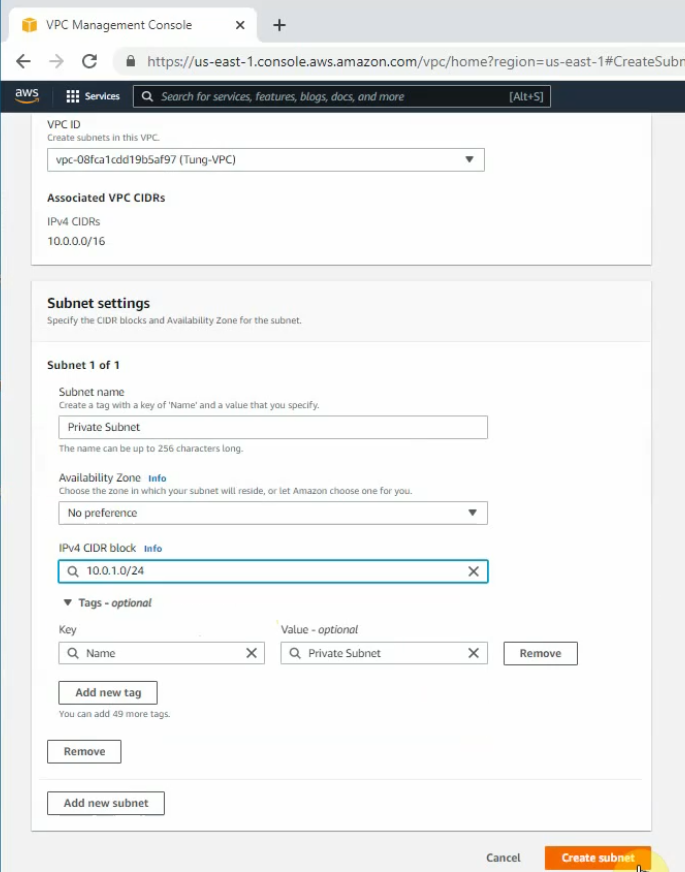
Create a public subnet.
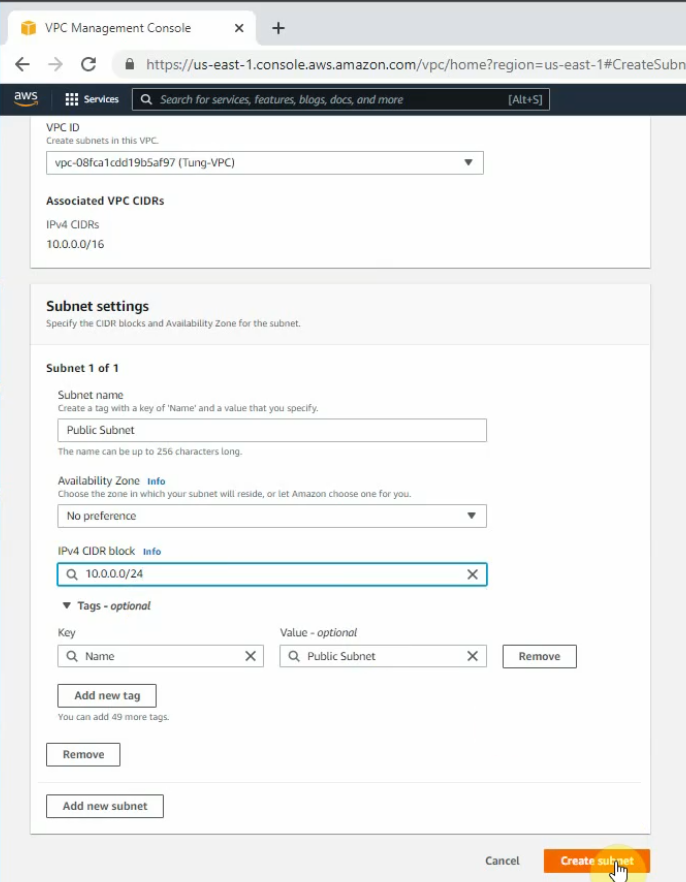
Create a private subnet.
Create an Internet gateway.
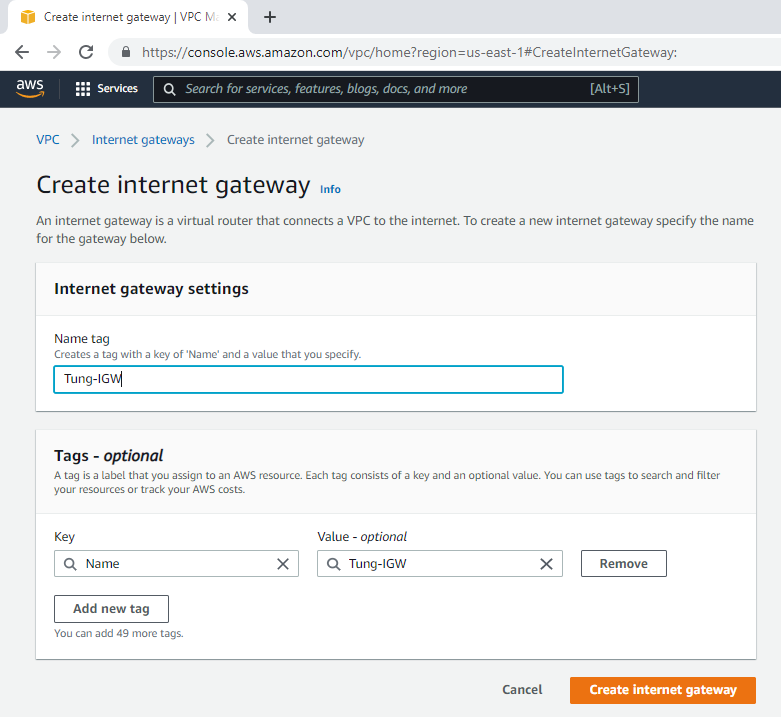
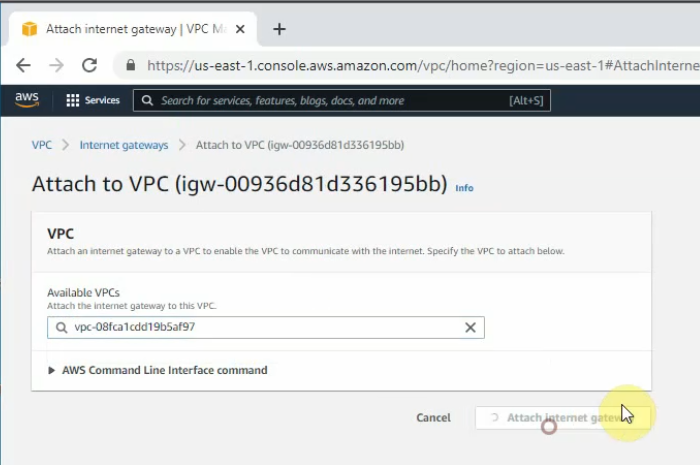
Attach the gateway to your VPC.
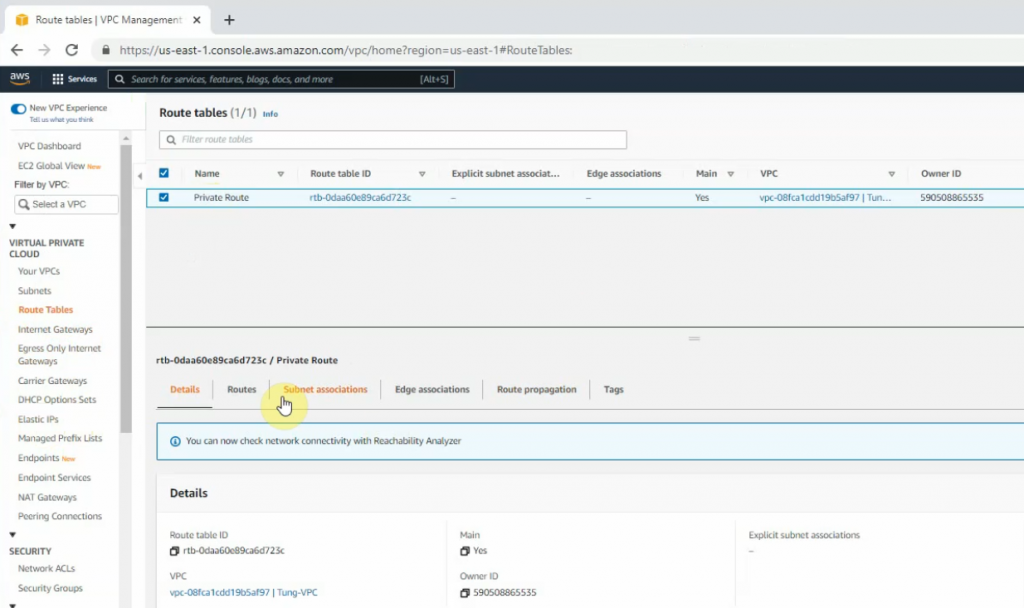
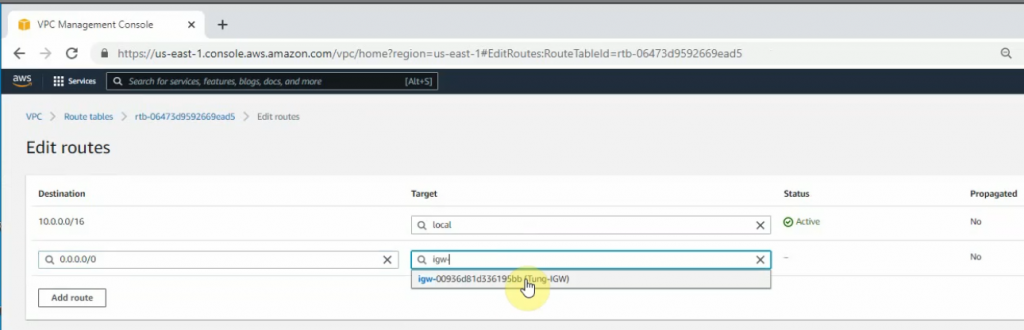
Edit Route table, change default Route table to Private Route.
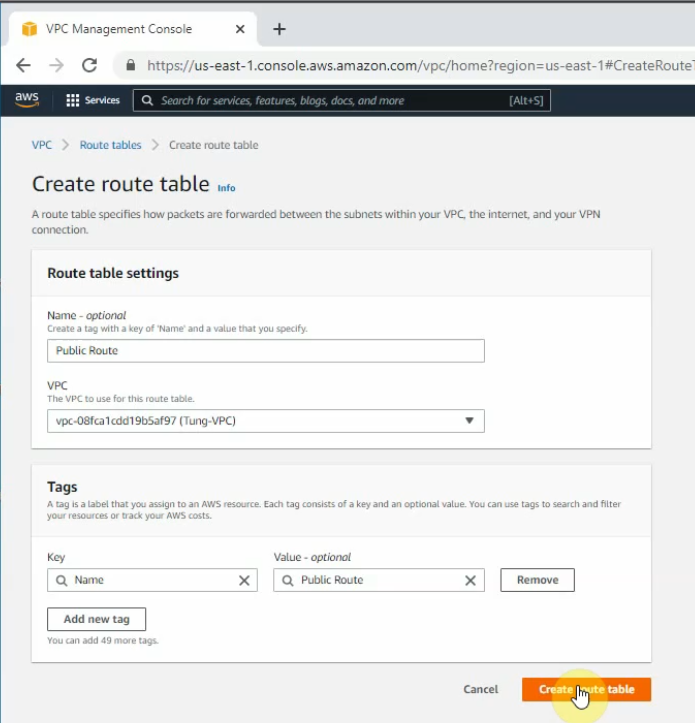
Create a Public Route Table.
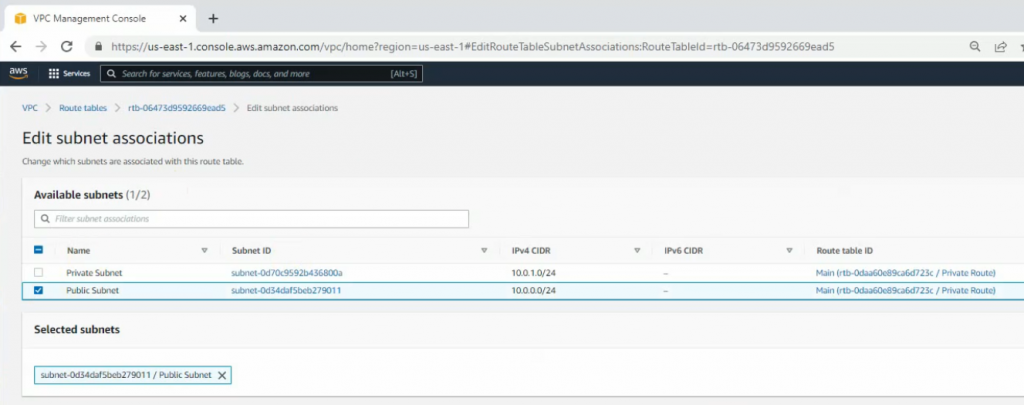
Link the Public Subnet to the Public Route.
Add a new route 0.0.0.0/0 to your Internet gateway.
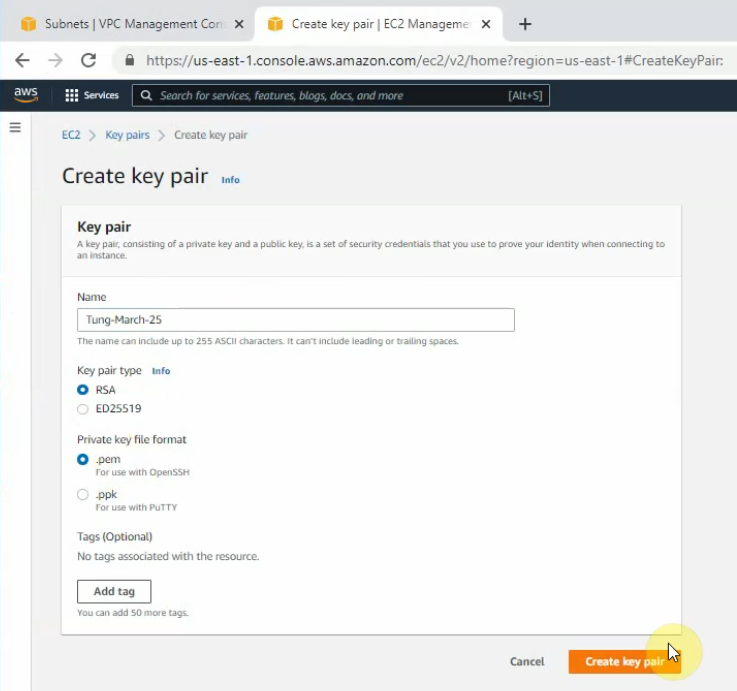
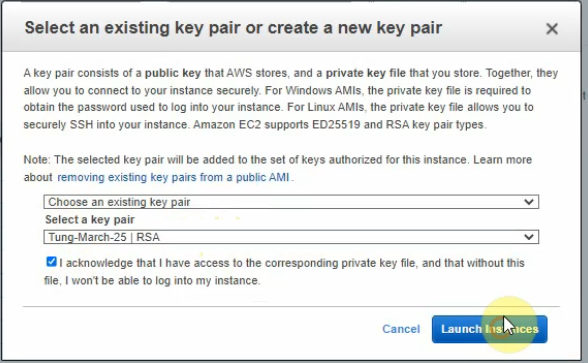
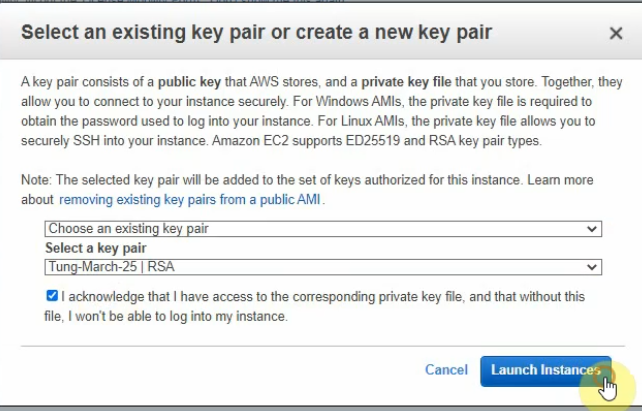
Create a new key pair.
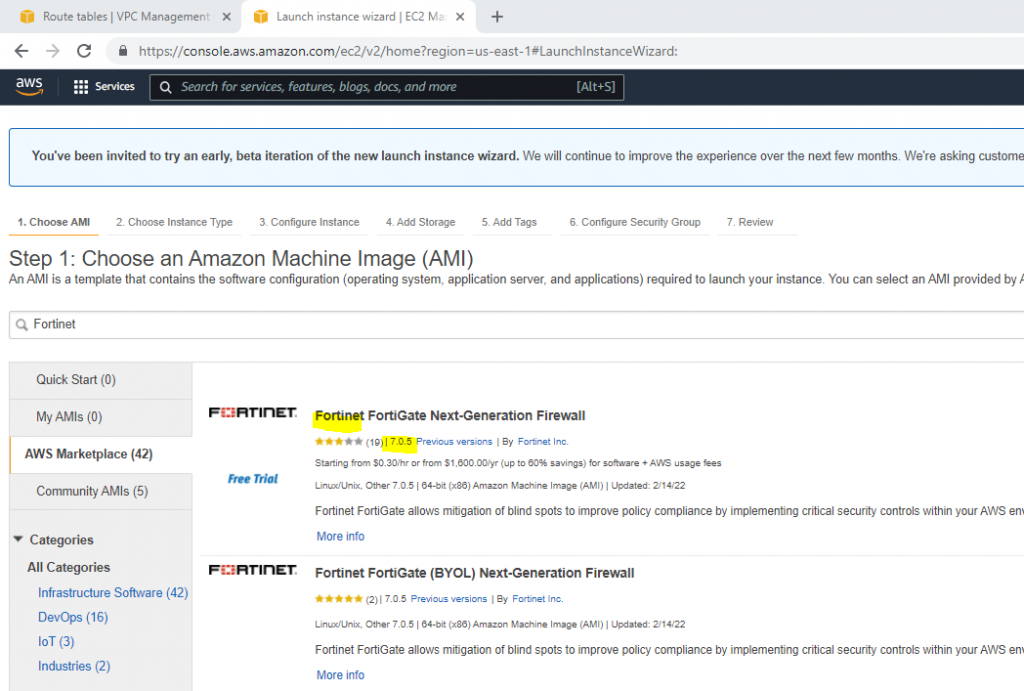
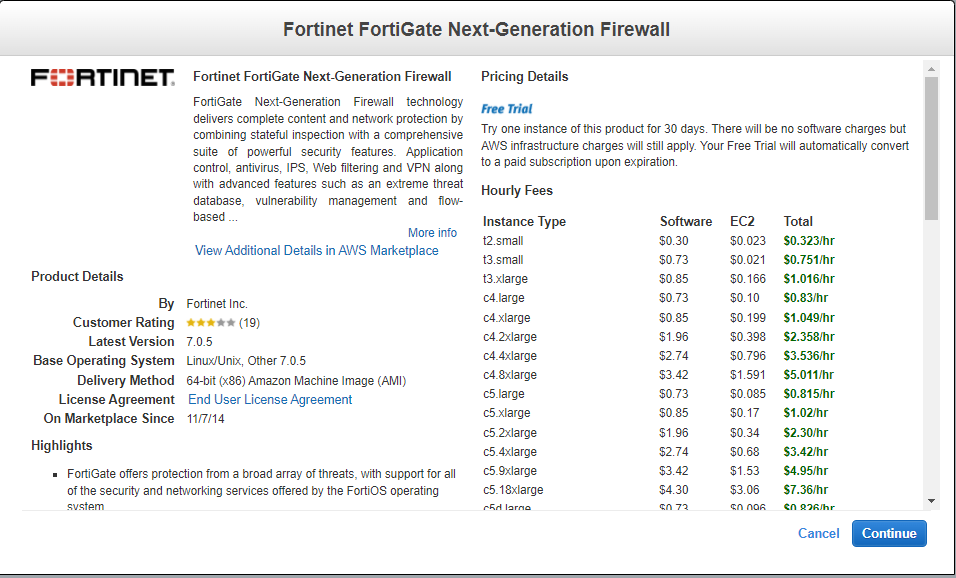
+ Go to EC2, and deploy Fortinet on AWS.
Select your VPC, the subnet belongs to Lab Public Subnet. Also, changing the Auto-assign Public IP is Enable.
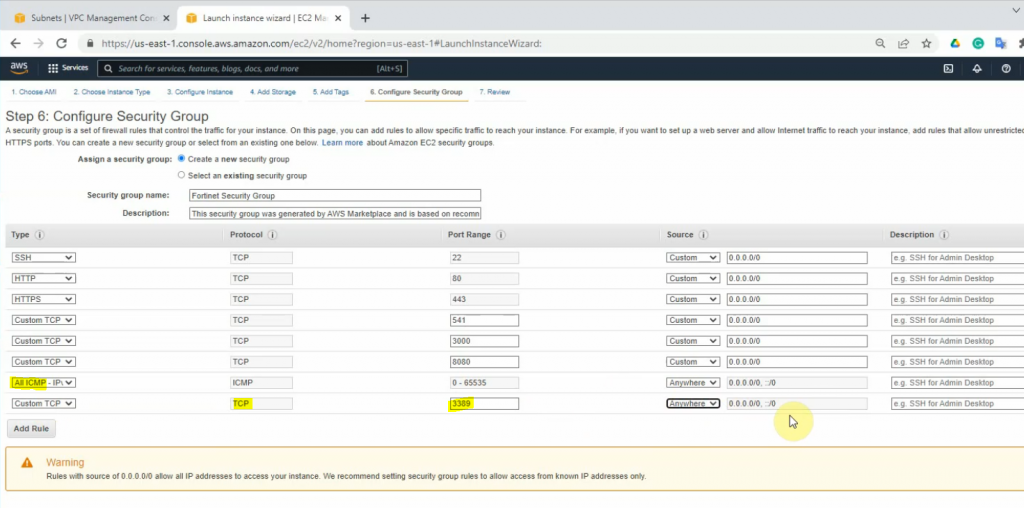
On the Security Group tab, add new two lines at the end of Security Group as a screenshot below. This allows to ping and RDP to the Windows 2016 machine on a private subnet later on.
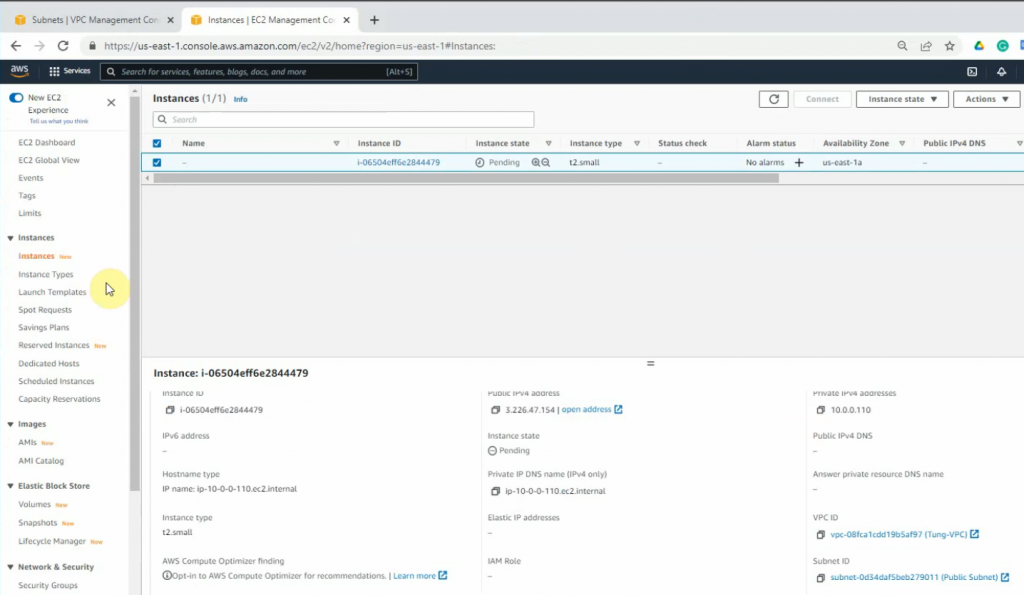
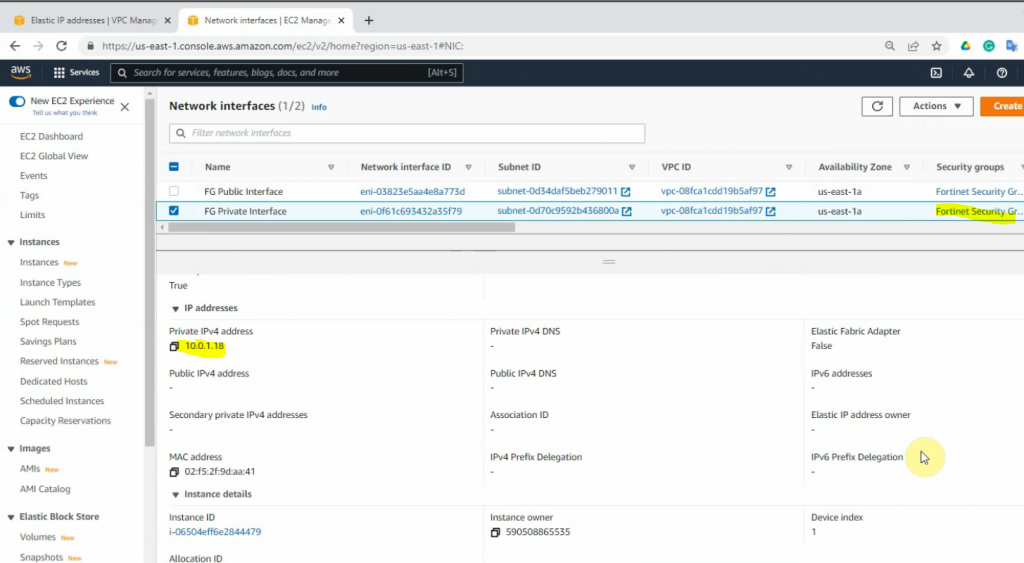
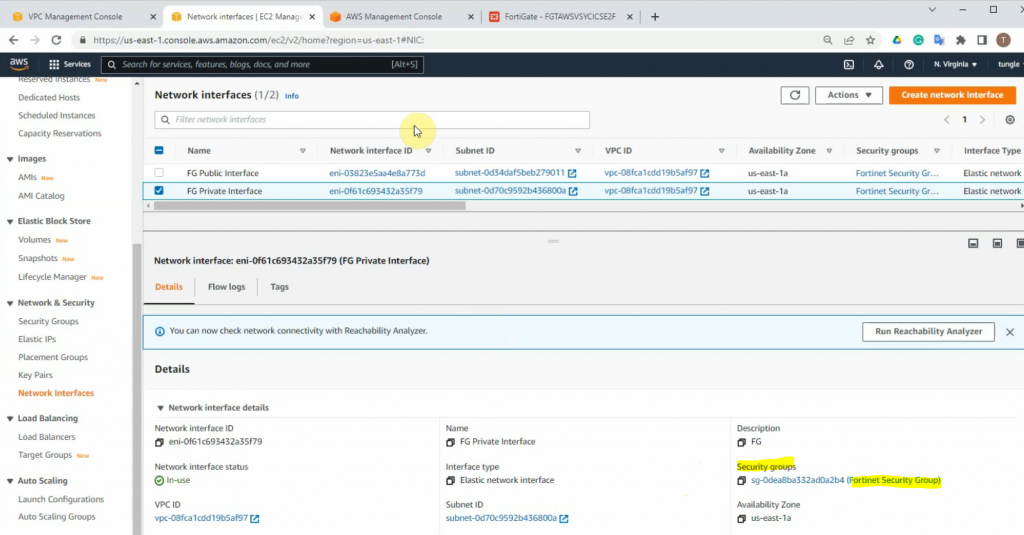
Go to Network interfaces, change the interface to FG Public Interface.
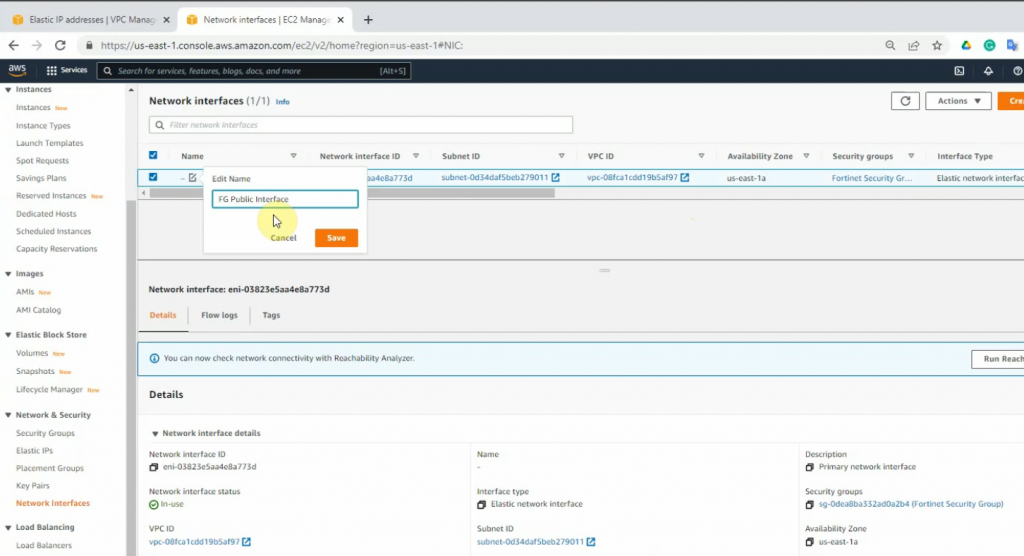
Create a new FG Private interface. Links to the private subnet and FortiGate Security Group.
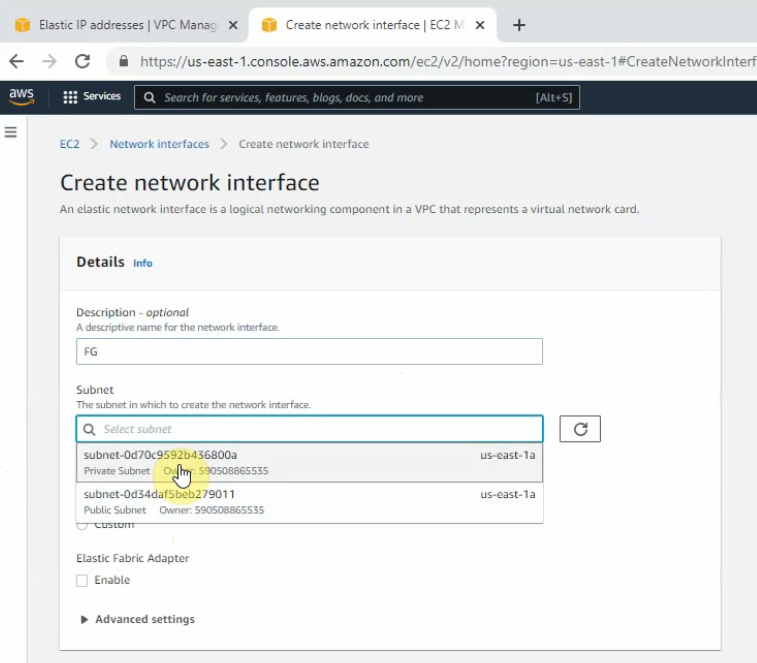
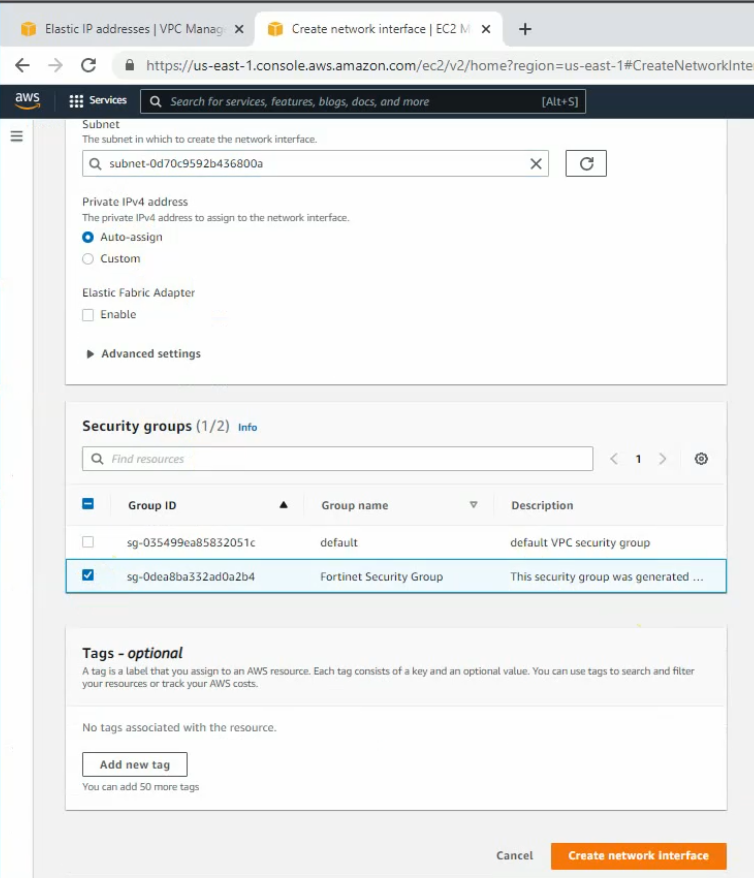
Change to FG Private Interface.
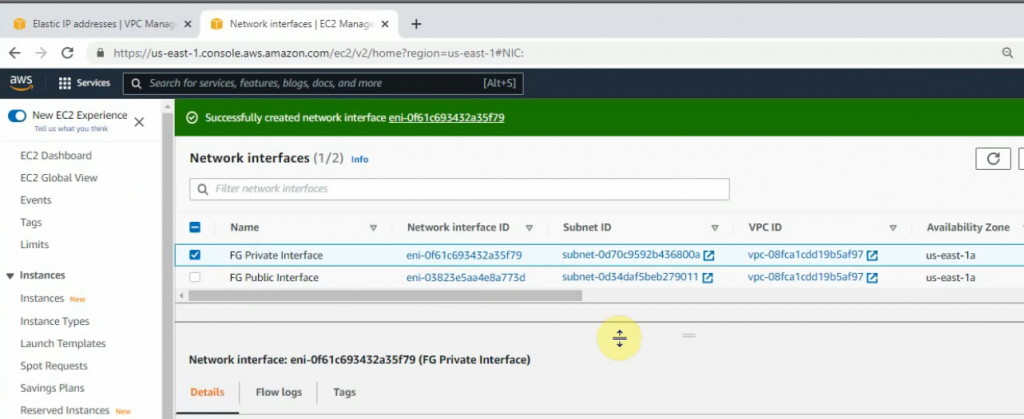
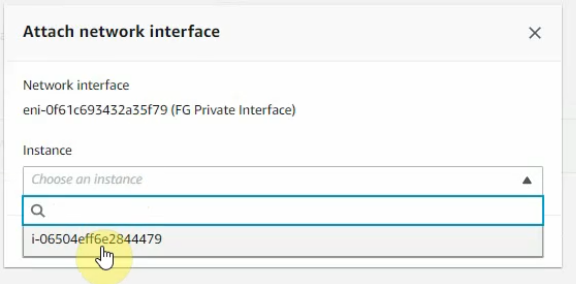
Select the FG private interface, choose Action on the top right-hand side and Attach this network interface to Fortinet EC2.
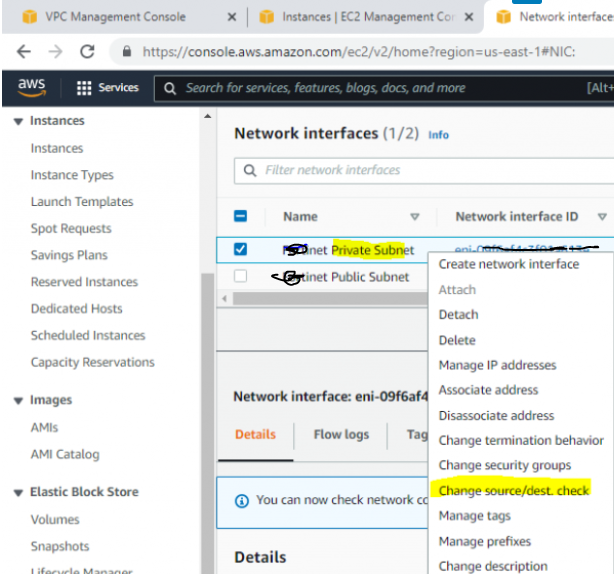
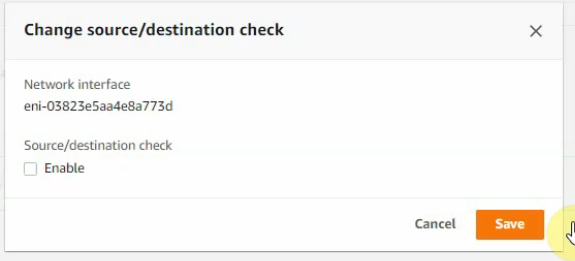
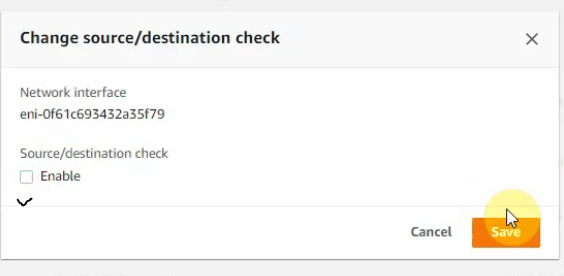
Right-click on both FG Public and Private interfaces, and disable “Change source/dest check” on both interfaces to allow NAT traffic on these interfaces.
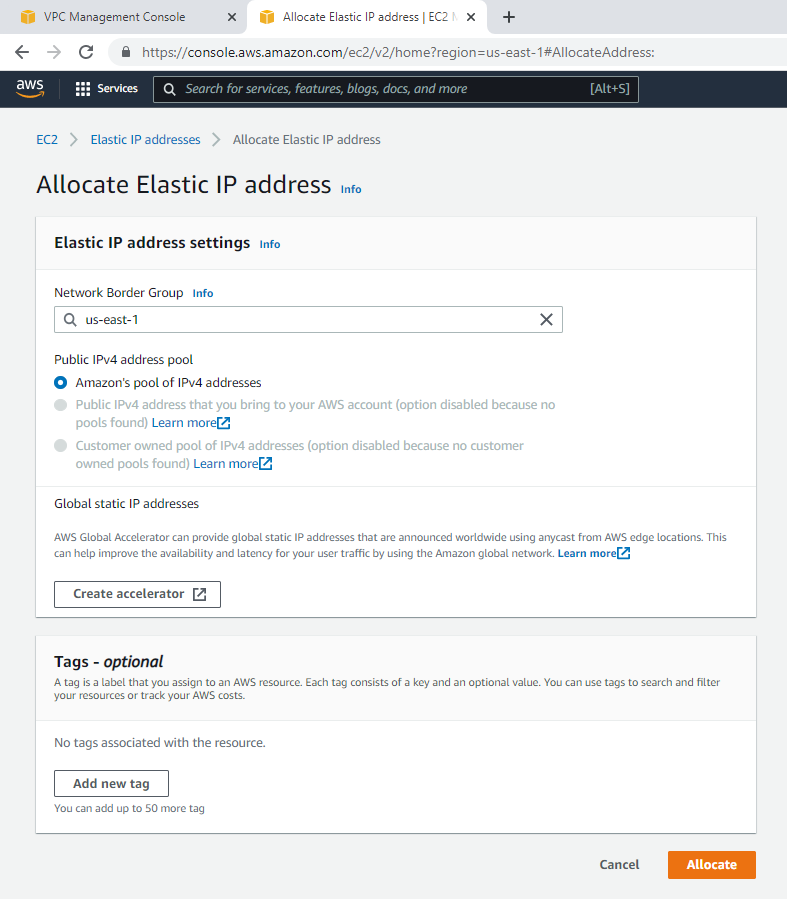
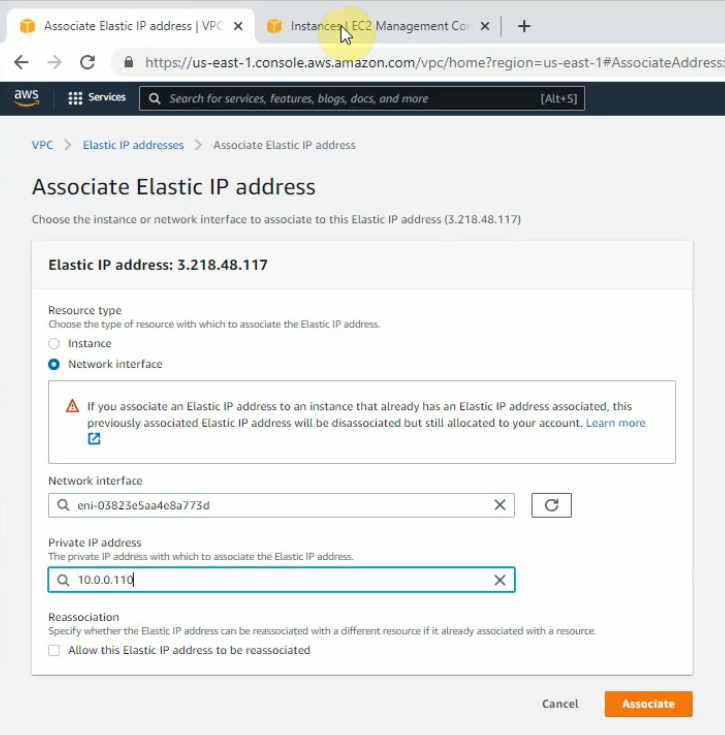
Create a new Elastic IP address.
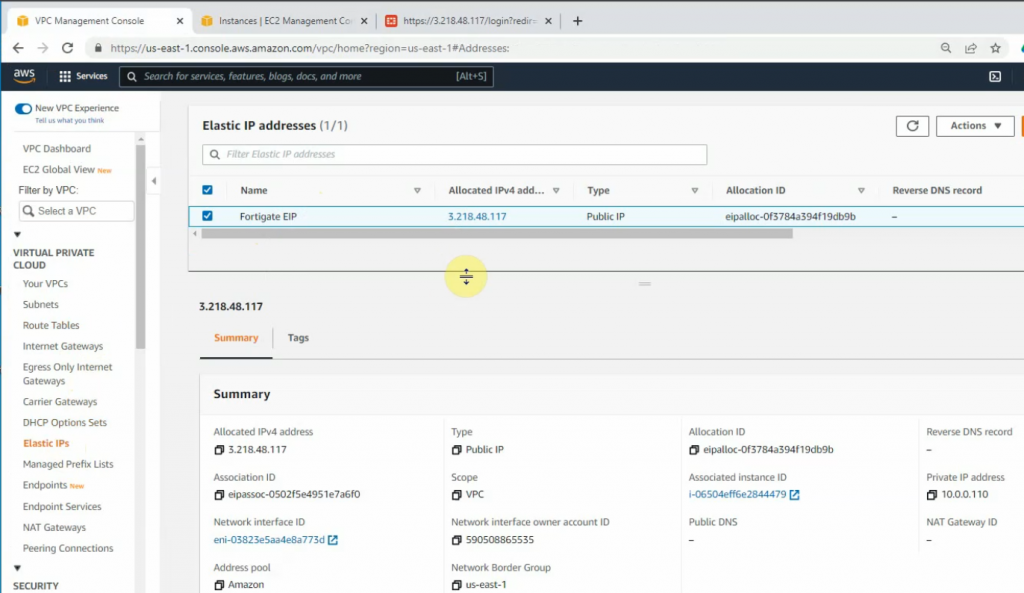
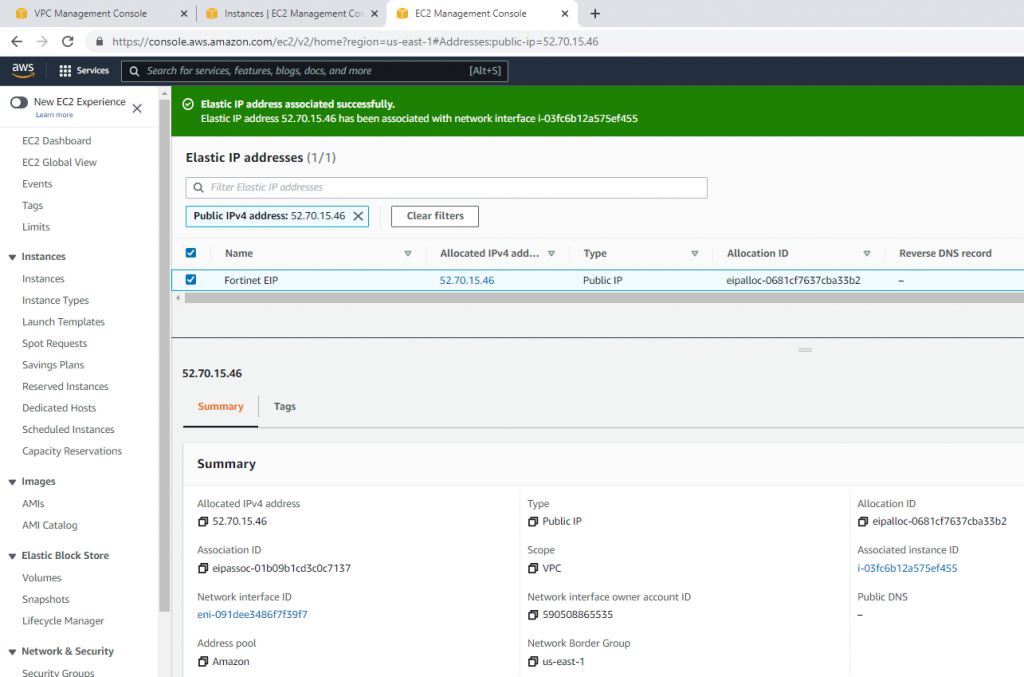
Associate this Elastic IP address to Fortinet EC2.
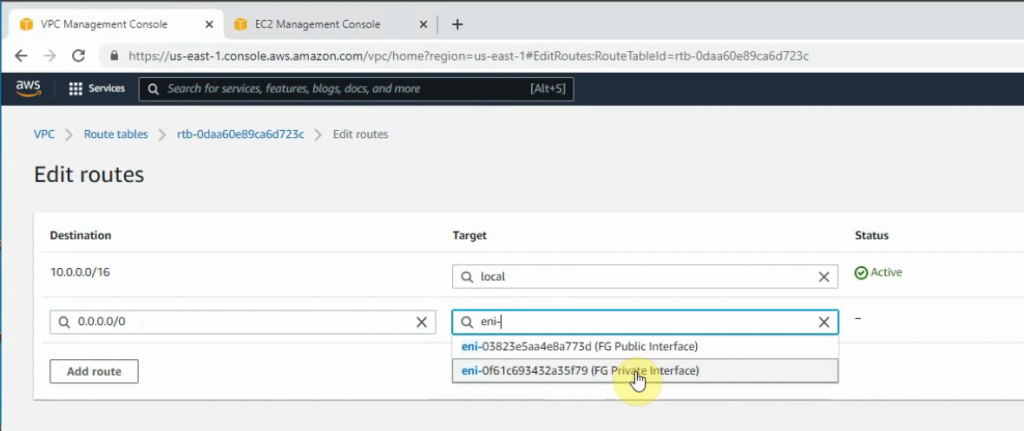
Back to Route tables, add a new route 0.0.0.0/0 to FG private interface.
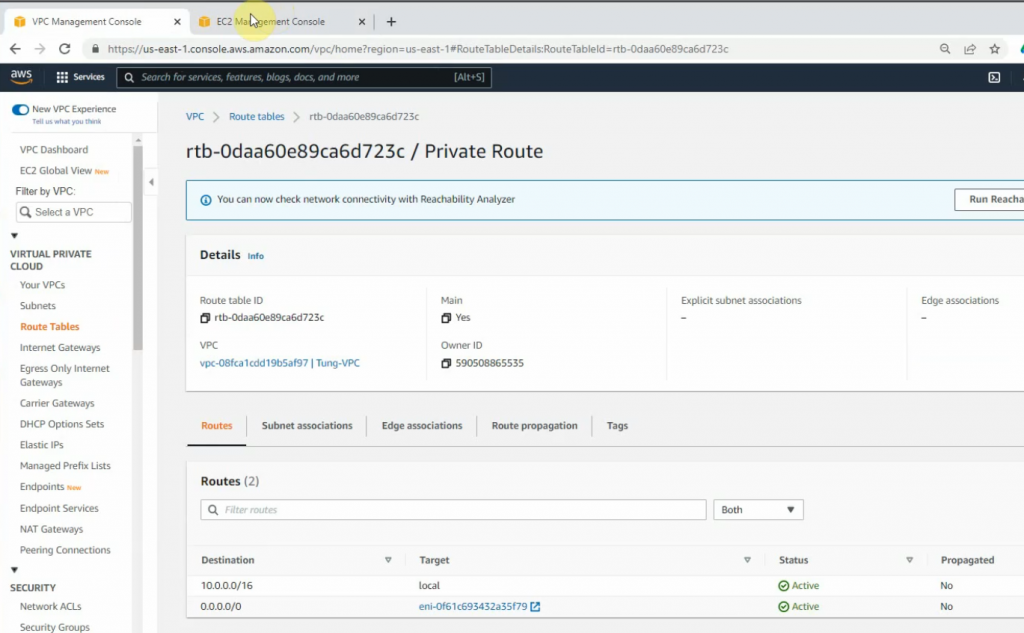
Now, Fortinet has two interfaces. One is Private, and another one is Public.
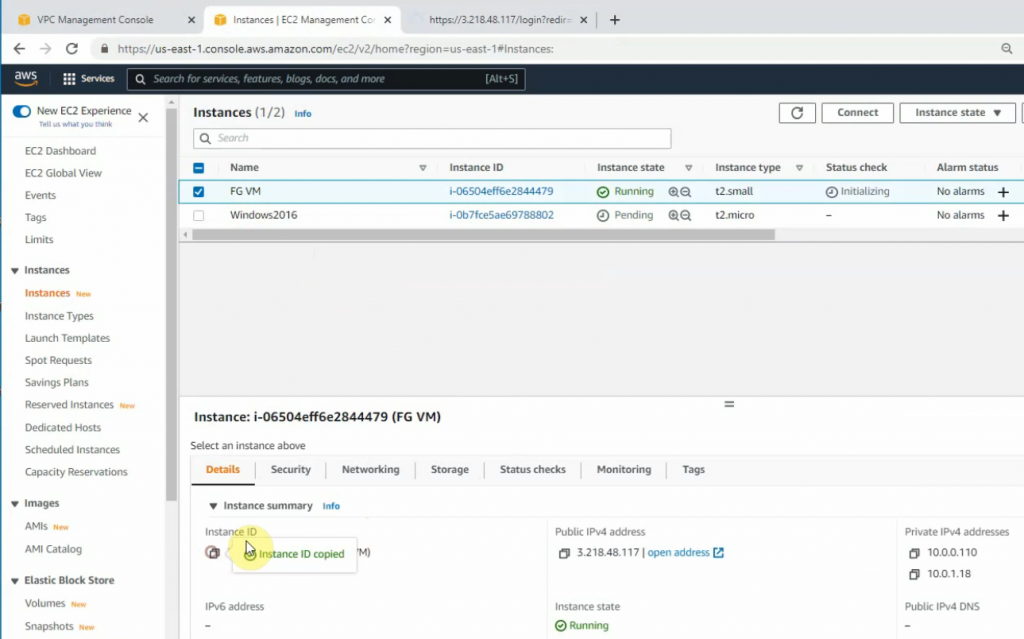
Copy the Elastic IP address and paste it to your web browser to access the FortiGate management interface.
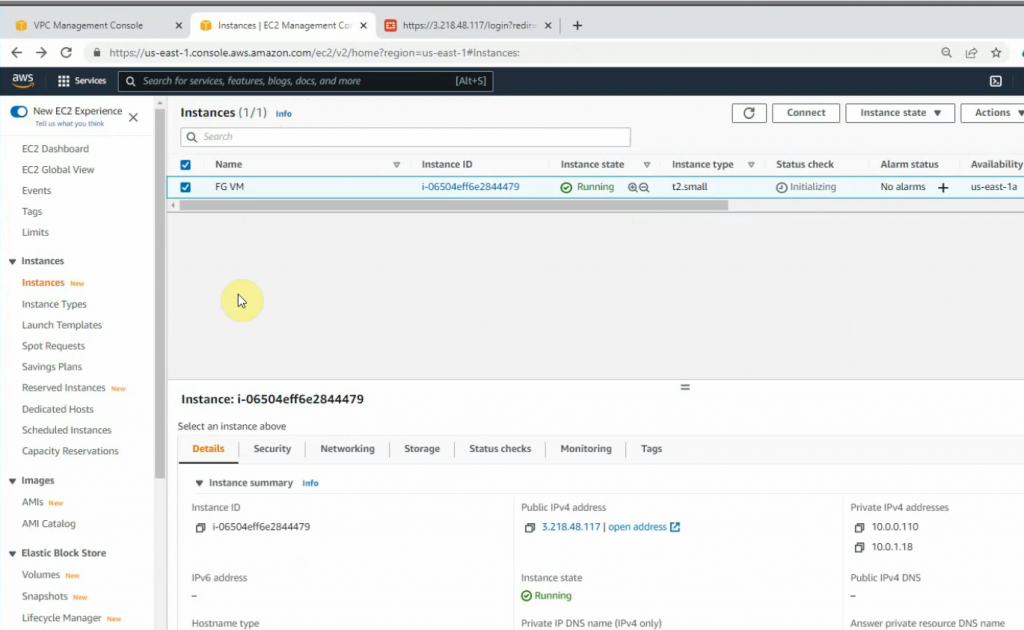
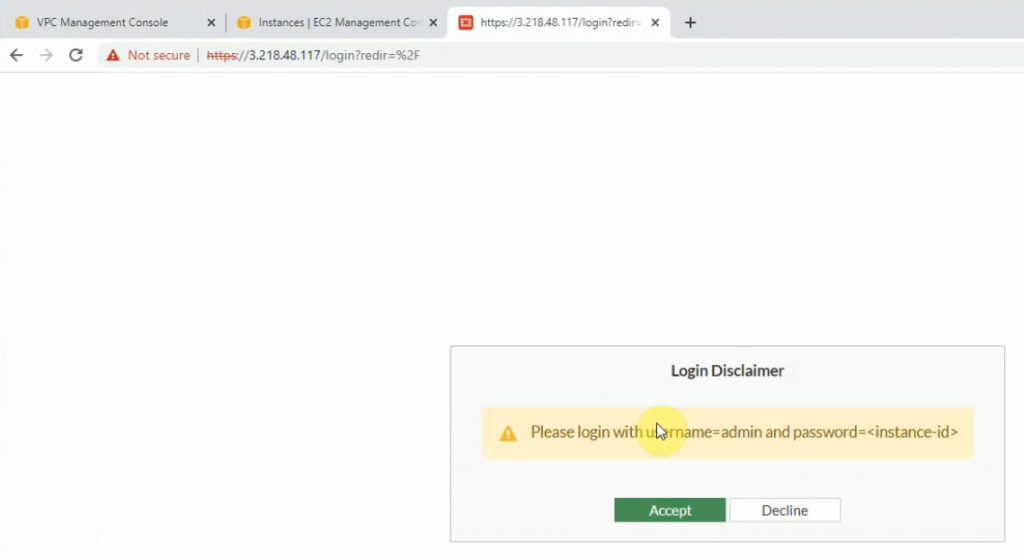
Access Fortinet via the Internet.
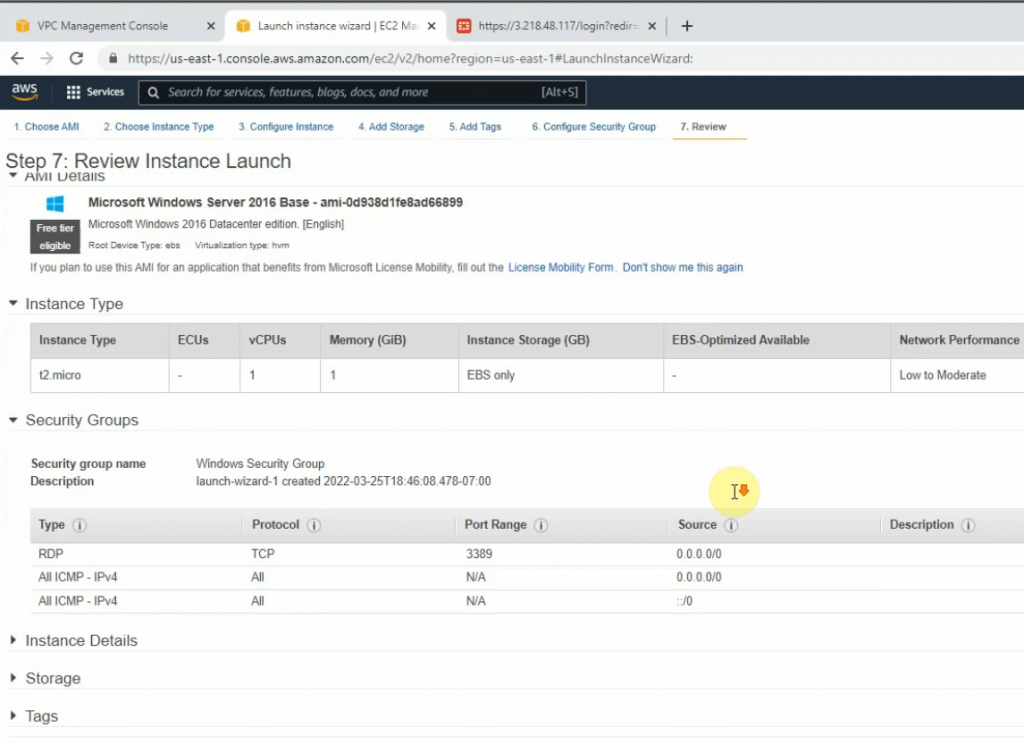
+ Launch a new Windows VM EC2 instance on your VPC.
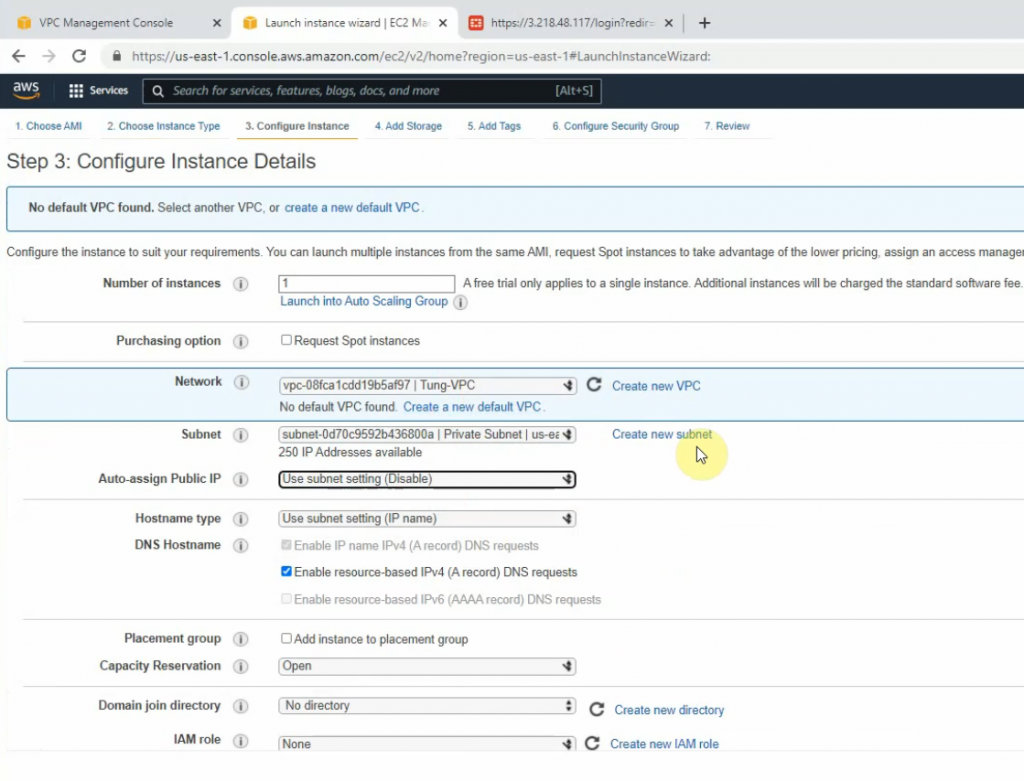
Network: Your VPC
Subnet: Private subnet
Auto-assign Public IP: Disabled. We will access RDP to the machine via DNAT on FortiGate.
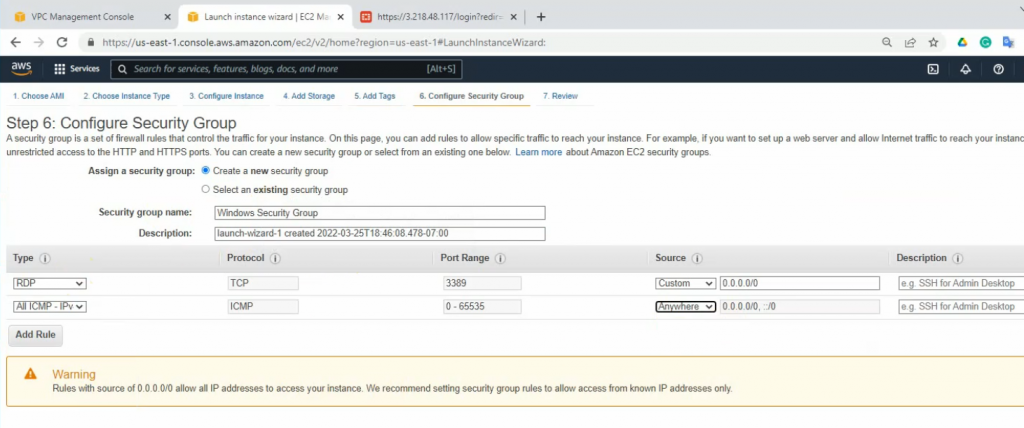
On the Security Group setting, add two lines to allow RDP and ICMP traffic to the machine.
+ Login to Fortinet.
Copy the FG instance and paste it to password login.
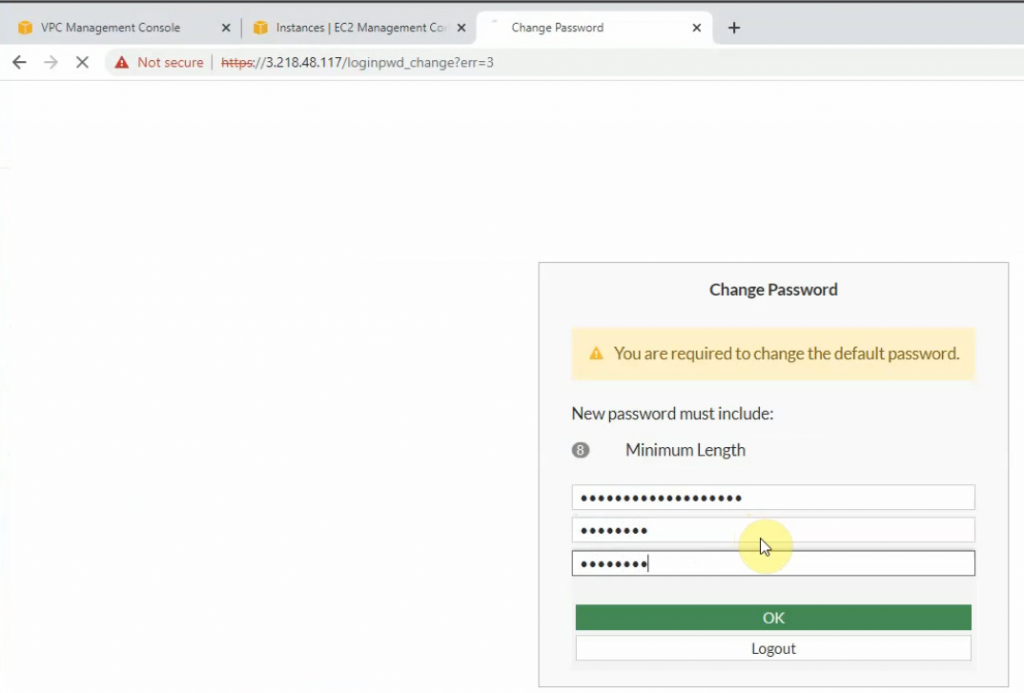
Change the password to login to Fortinet.
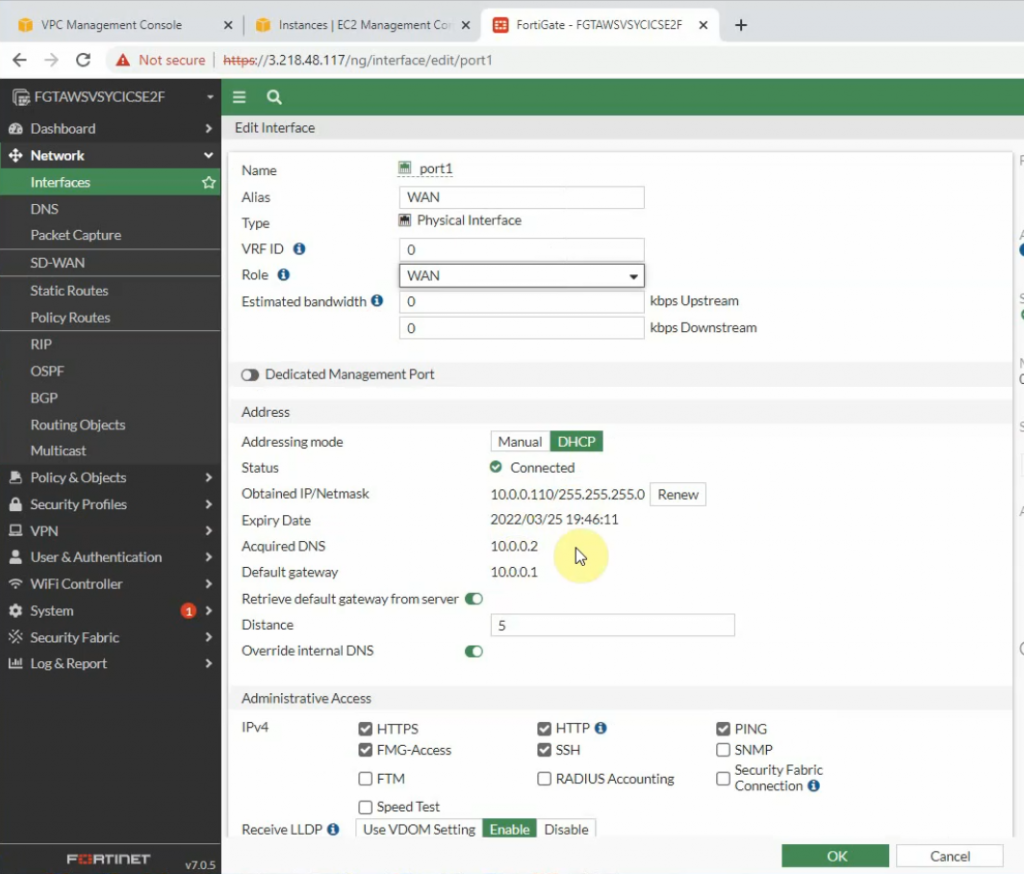
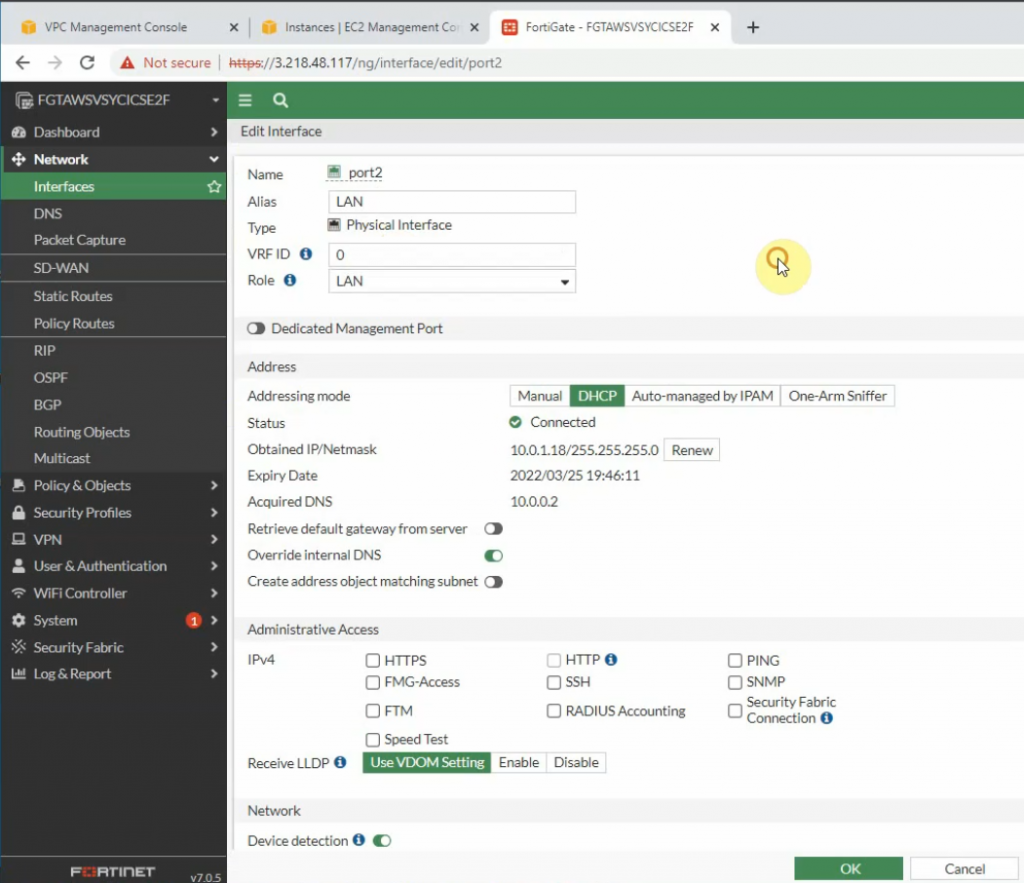
Edit WAN and LAN interface setting.
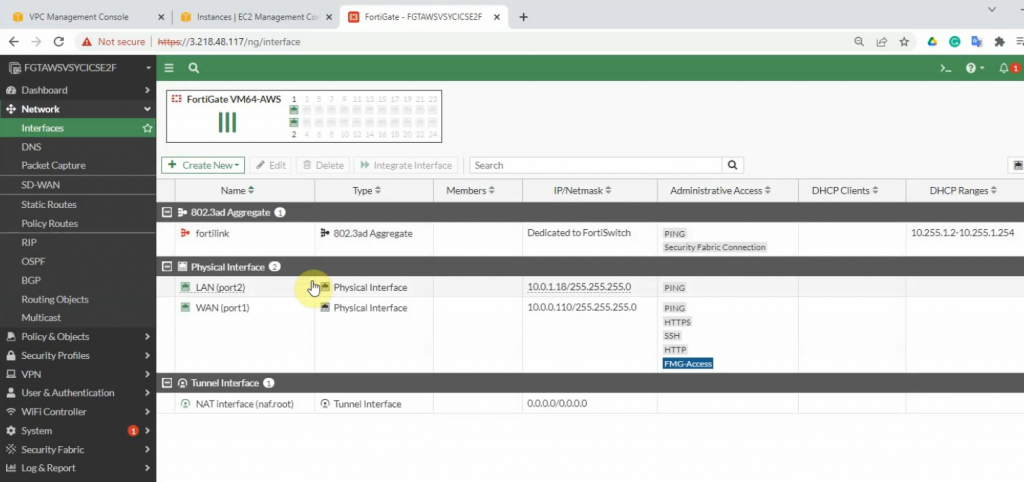
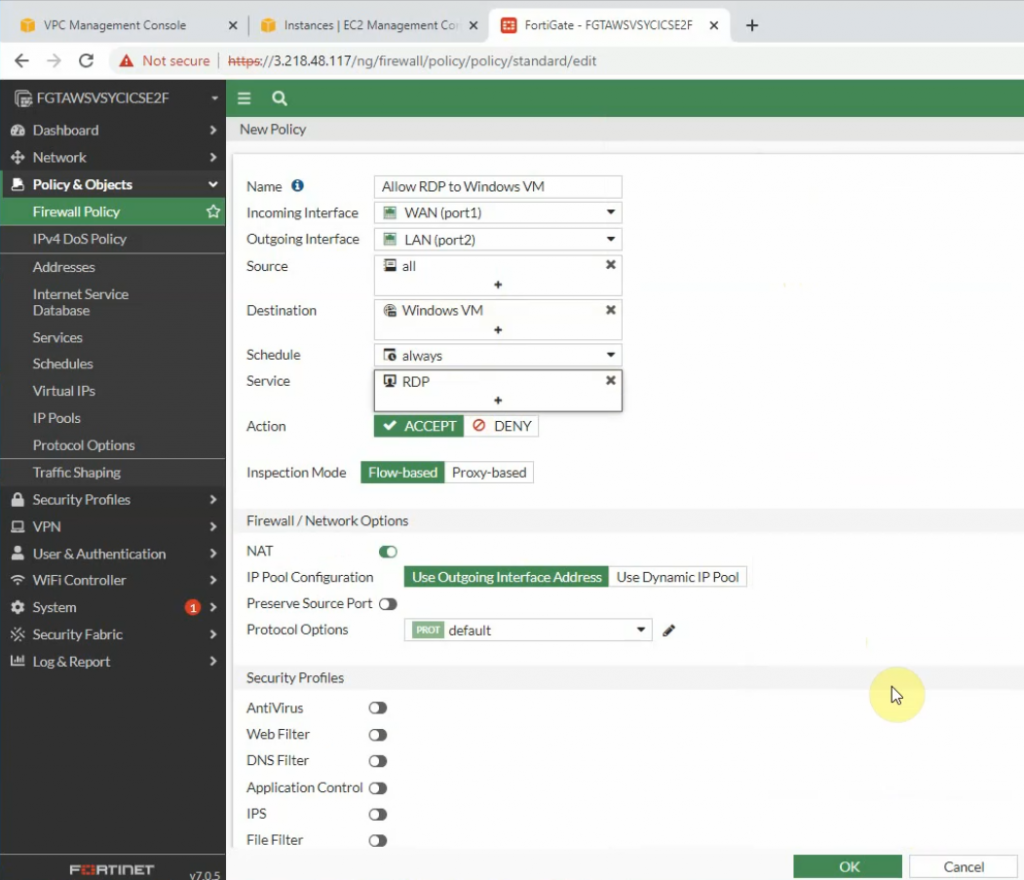
Back to Fortinet to configure Firewall Policy to allow RDP traffic from the Internet to the Windows VM machine.
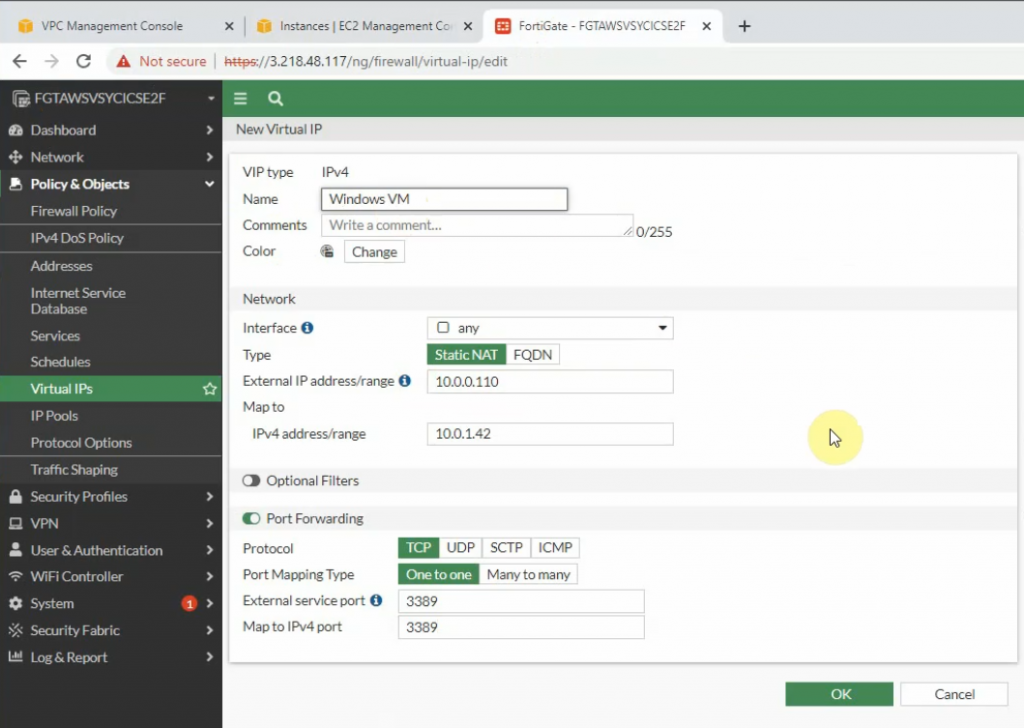
Configure port forwarding to allow traffic from the Internet to Windows 2016 VM instance on AWS.
External IP address: IP address of FG on the public subnet
Map to IPv4 address on the private subnet is IP address of Windows VM computer.
The external service port and map to IPv4 port is 3389.
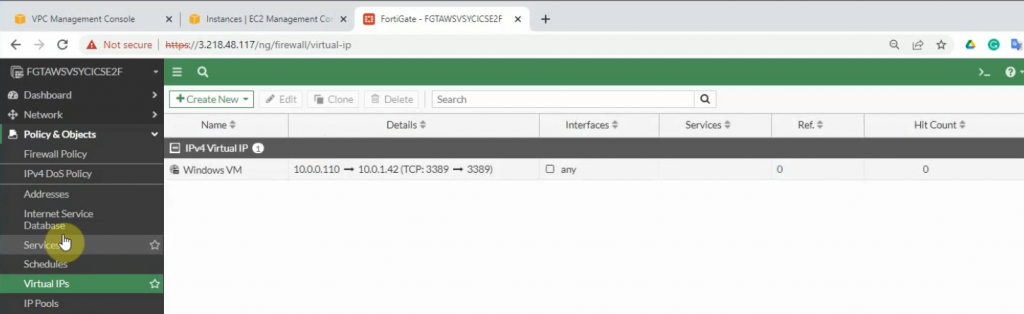
Allow inbound traffic from WAN to this machine.
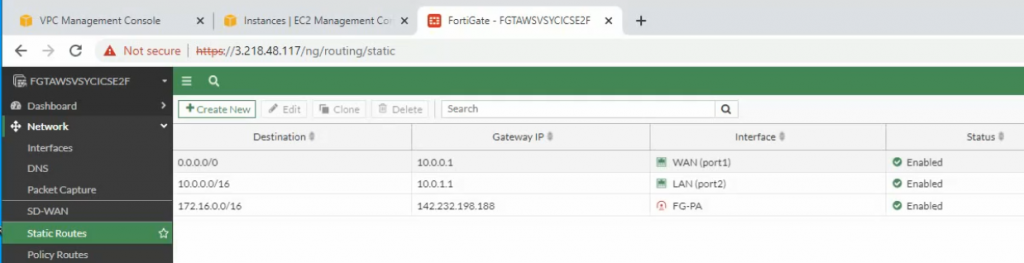
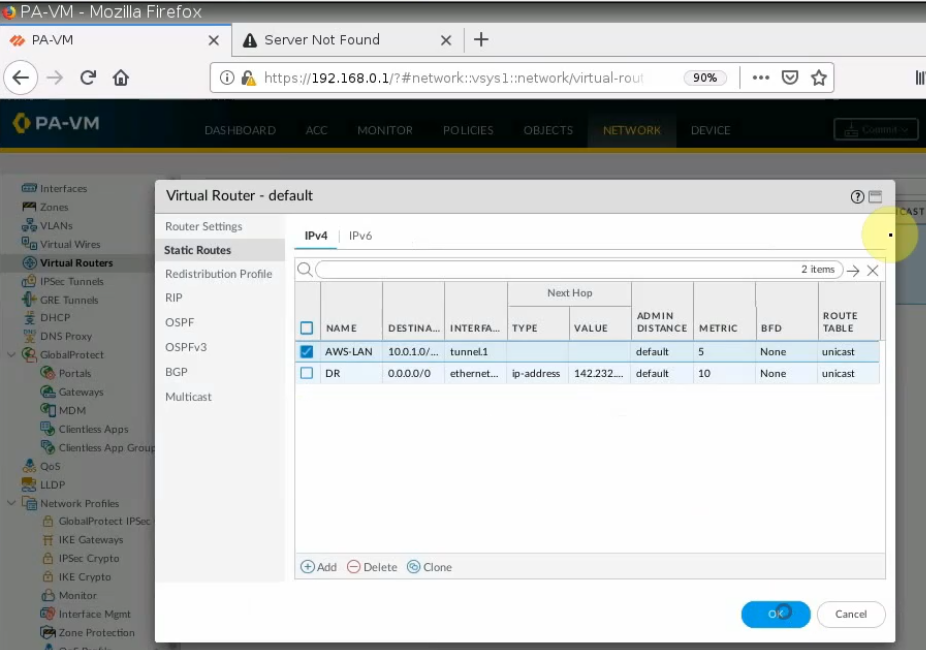
Create both static routes to allow a private subnet to access outside.
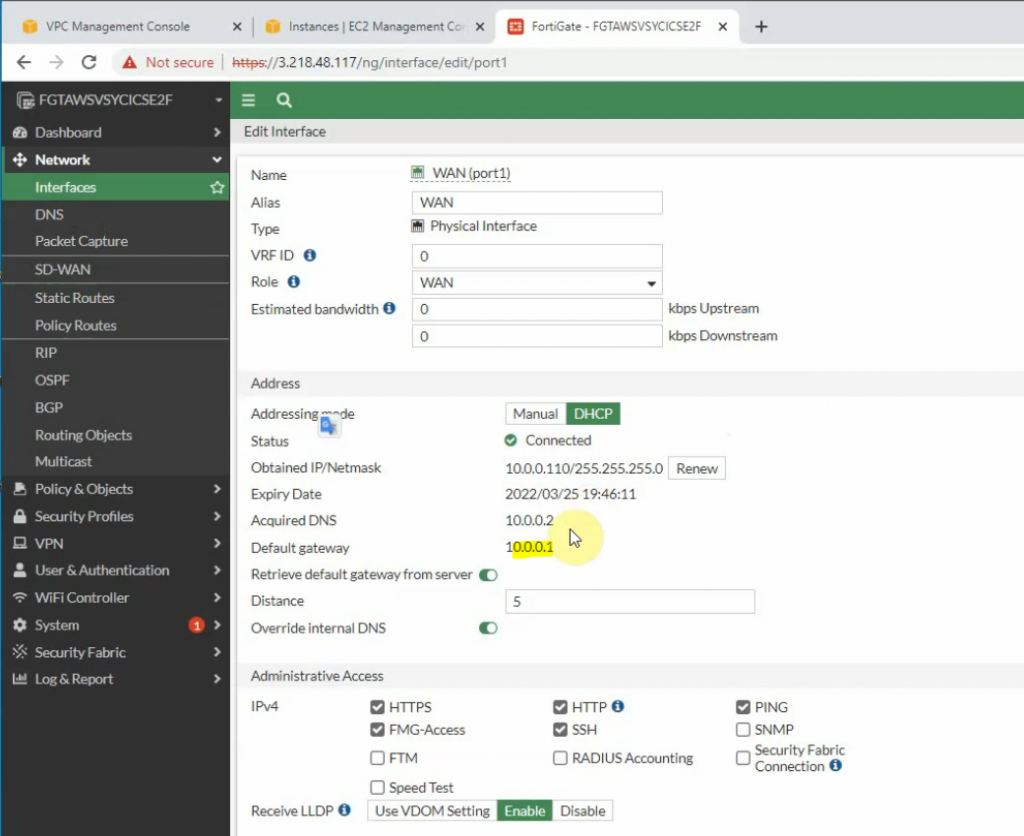
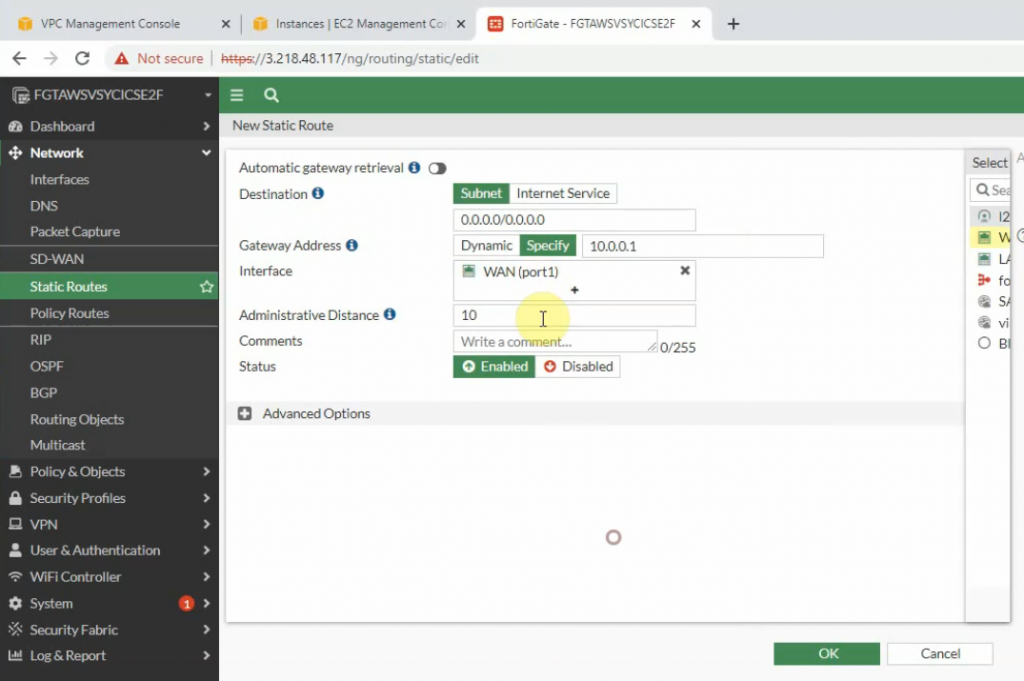
Creating new static routes for the private subnet from 10.0.0.0/16 to 10.0.1.1 that is the default gateway on the private subnet.
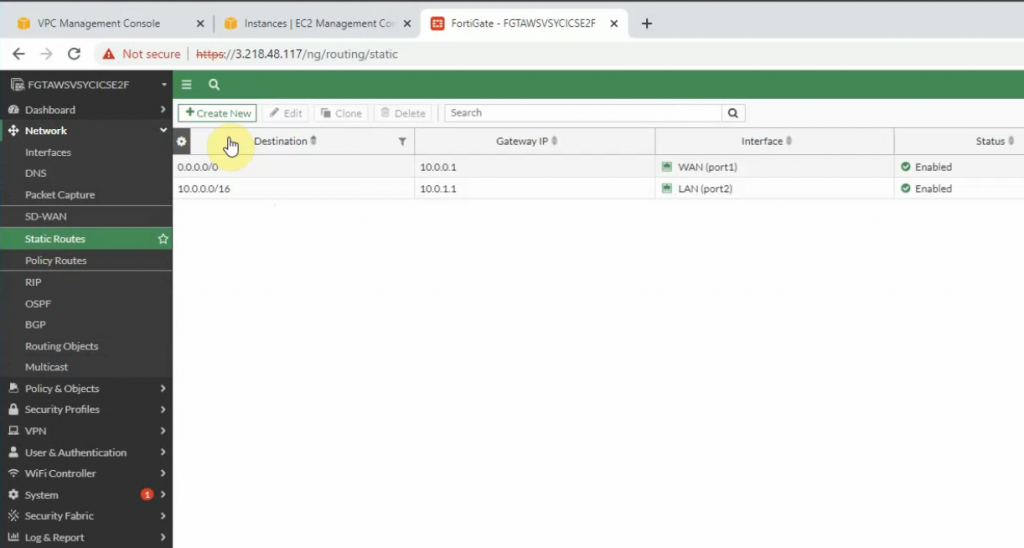
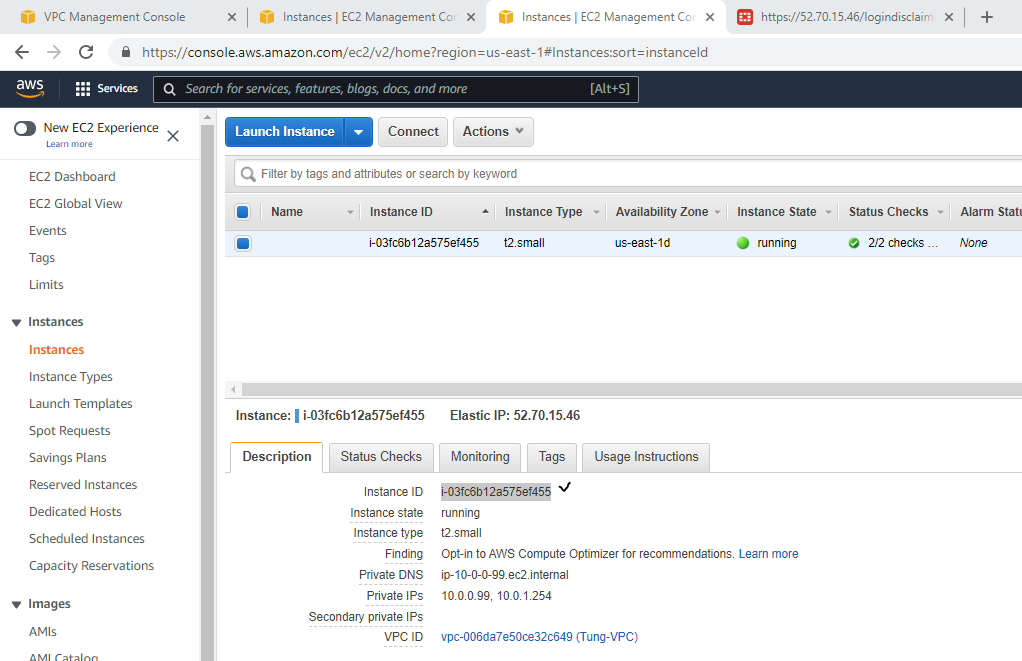
Try to access the machine.
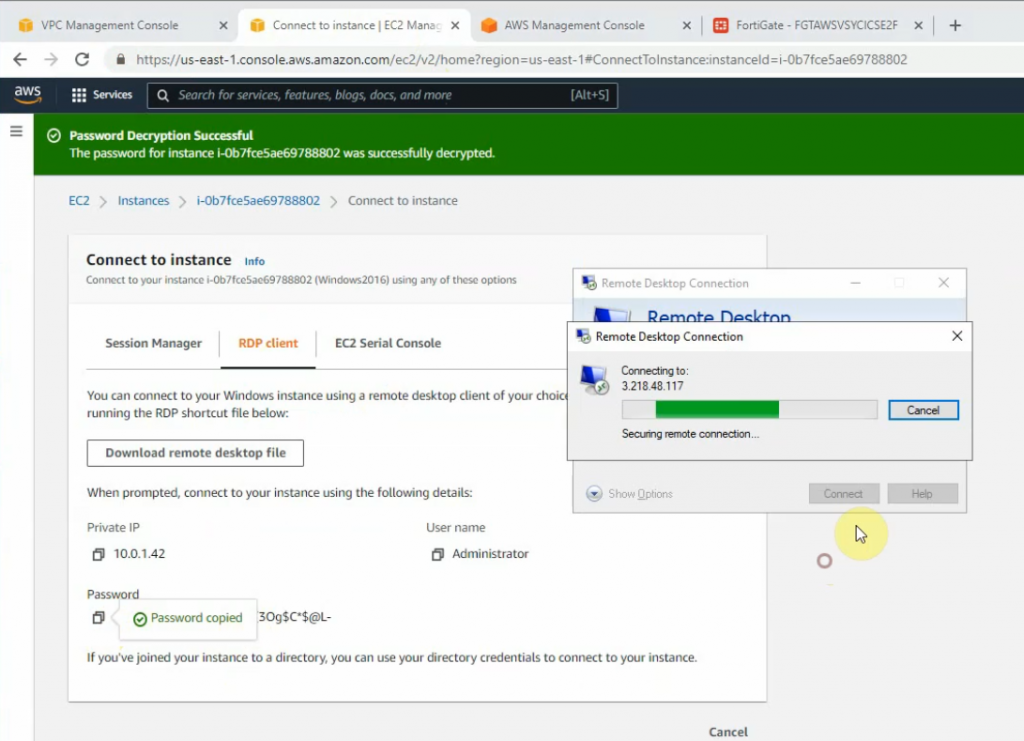
Load private key to decrypt Windows password.
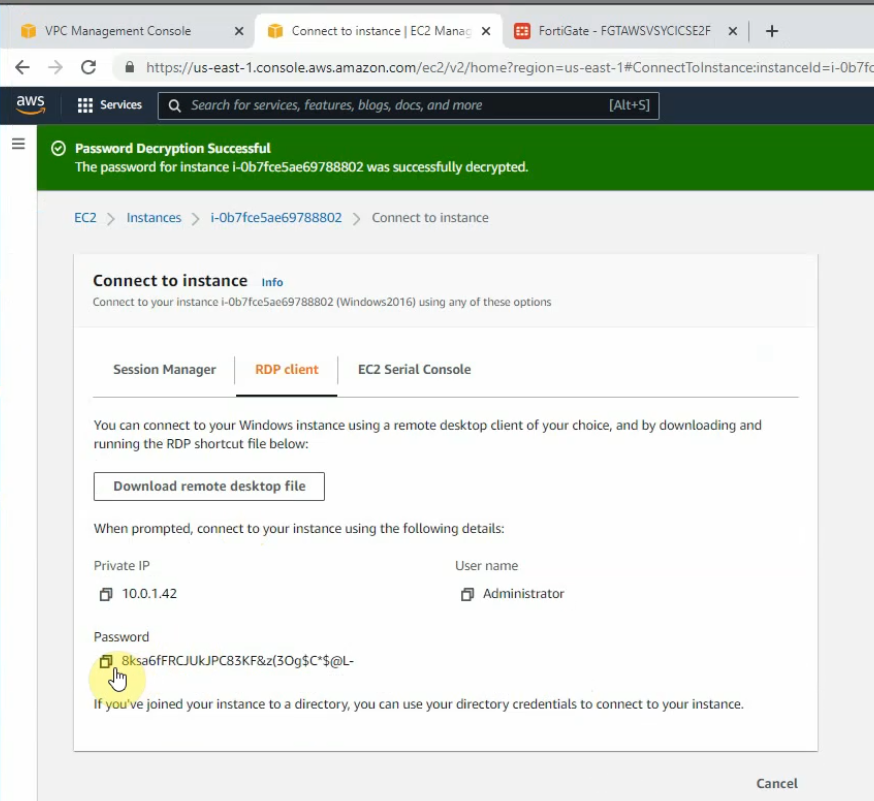
Access RDP to Windows 2016 instance on AWS.
Now we can see the RDP traffic via Fortinet.
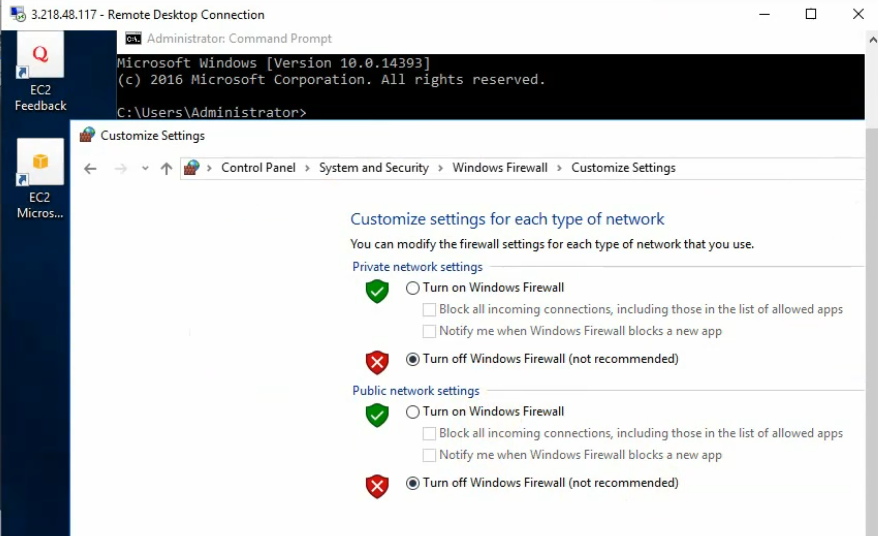
Disable Windows Firewall to allow ICMP traffic to that machine on Palo Alto private subnet.
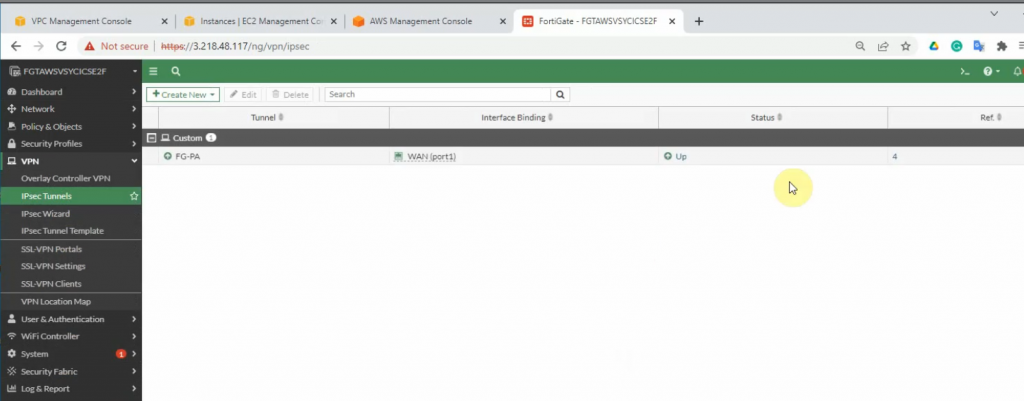
Configure IPSEC site to site wizard. Choose Custom.
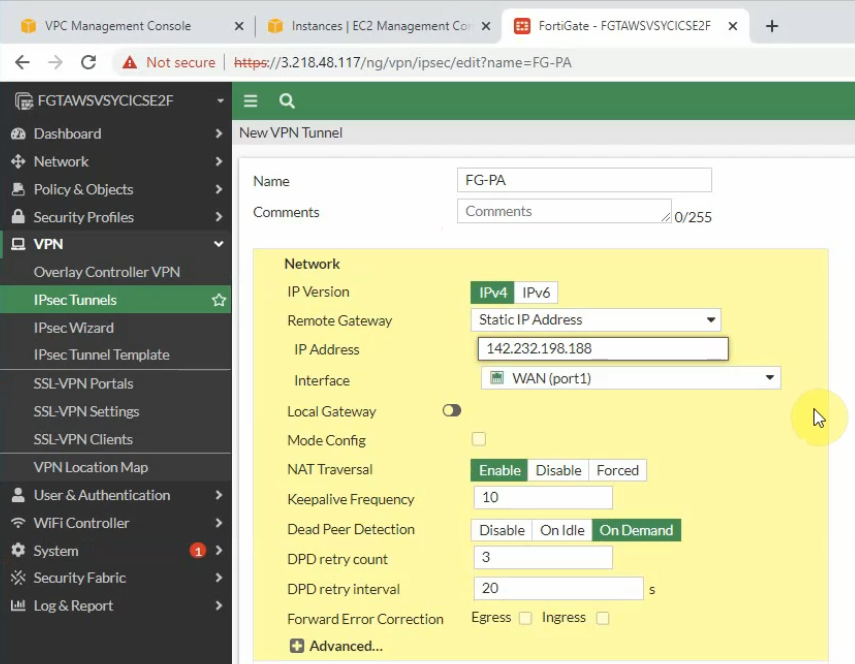
Enter IP address of public interface of PA. Disable NAT traversal, enter the pre-shared key and choose the IKE v2.
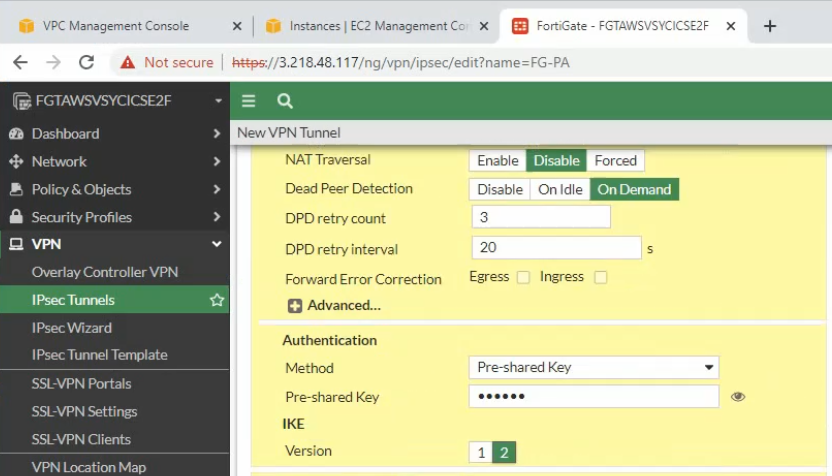
Phase 1 and Phase 2 settings need to match with the Palo Alto setting.
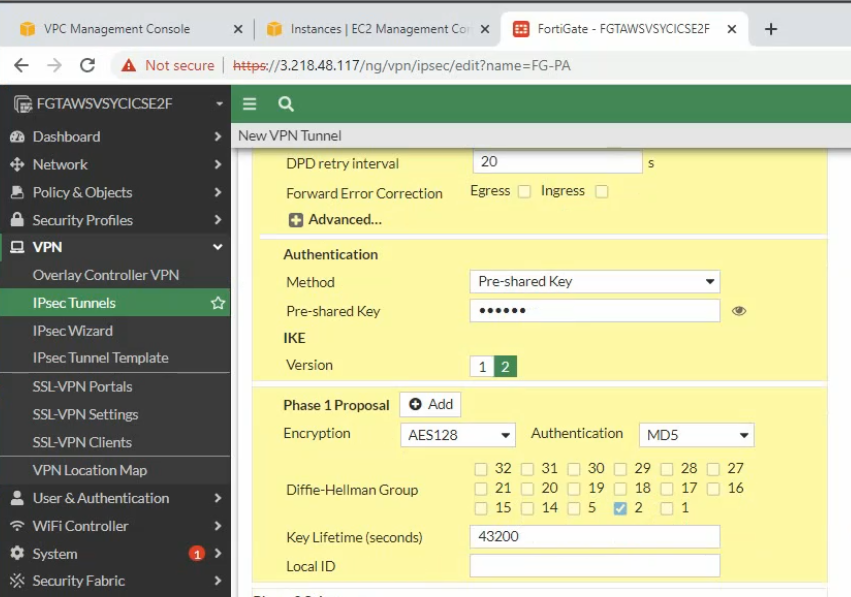
Local Address: the private subnet of FG: 10.0.1.0/24
Remote Address: PA LAN subnets: 172.16.0.0/16
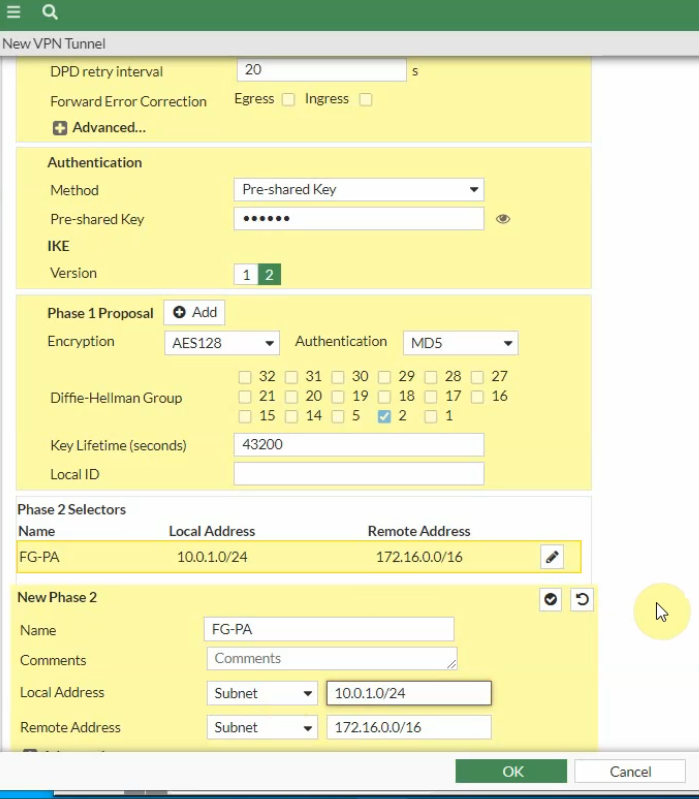
Click the Advanced tab. Change the setting to match with PA Phase 2 setting
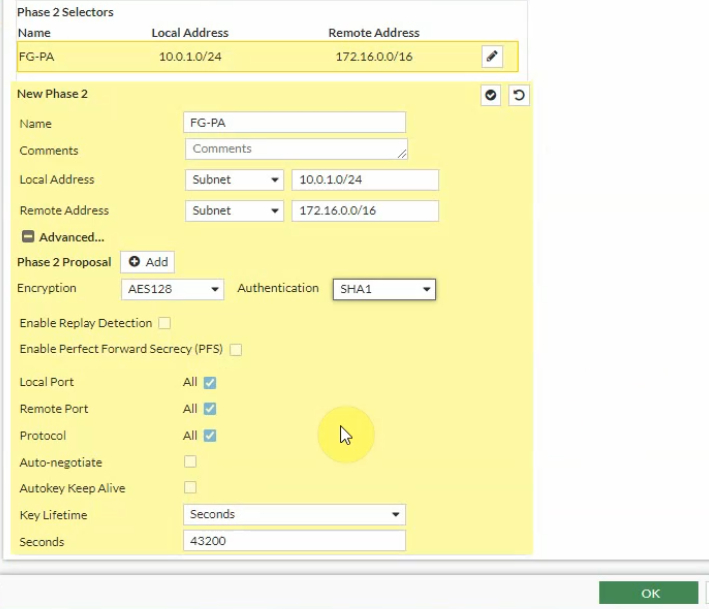
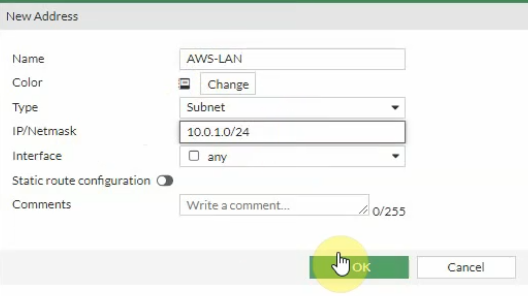
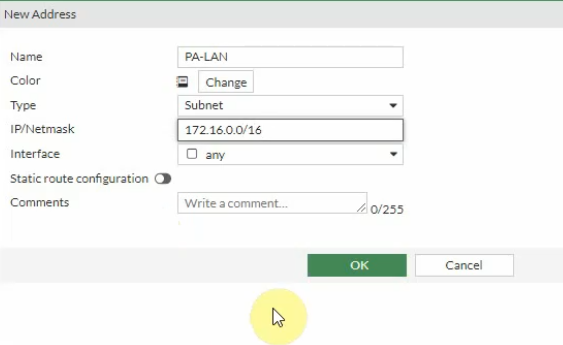
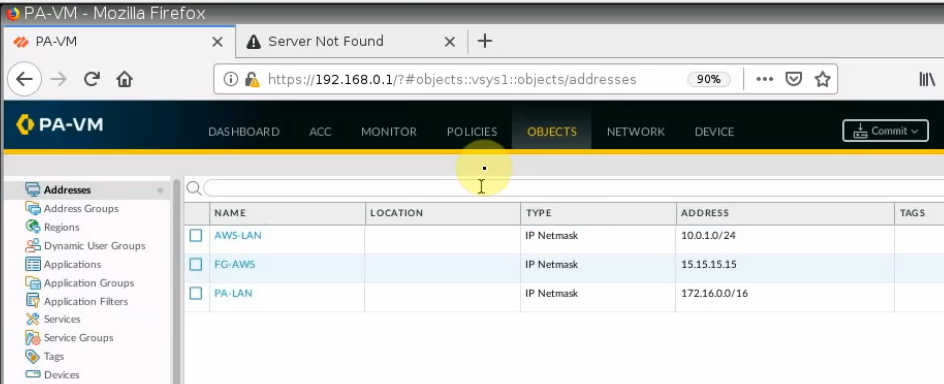
Create Fortinet LAN and PA LAN subnet network addresses.
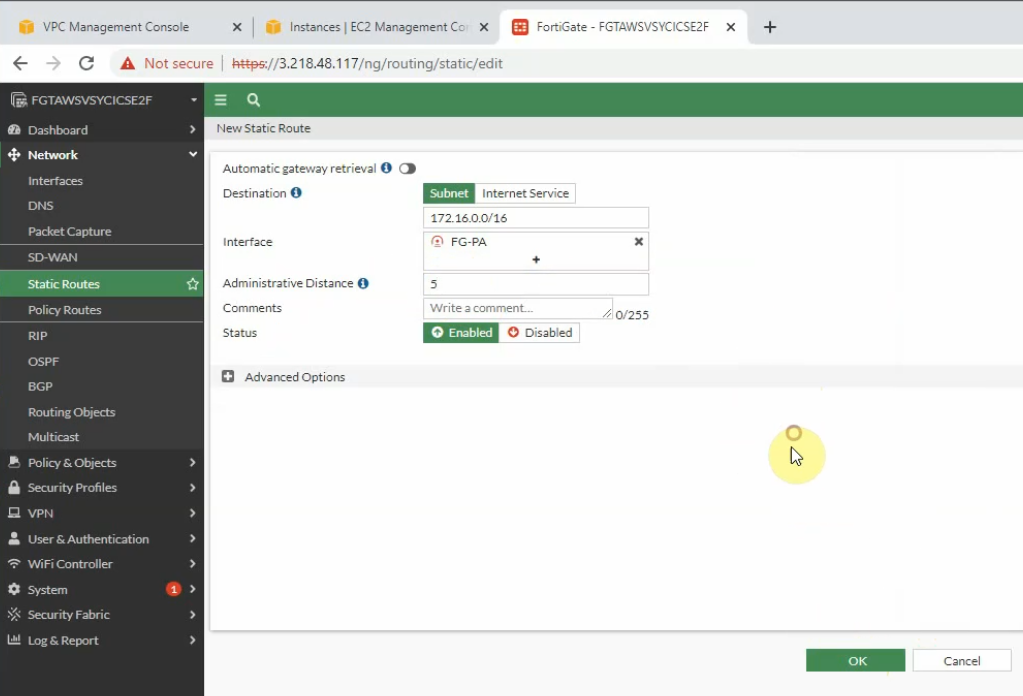
Create a static route on Fortinet to allow private subnet traffic to the Palo Alto LAN subnet.
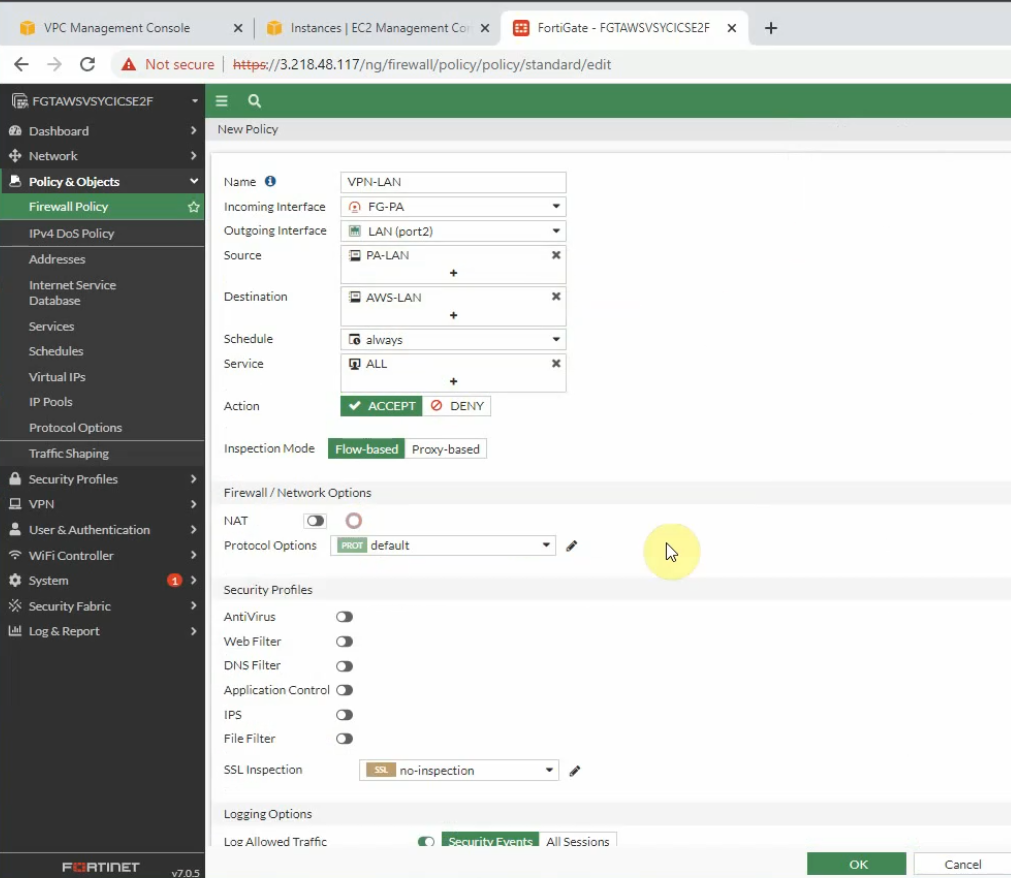
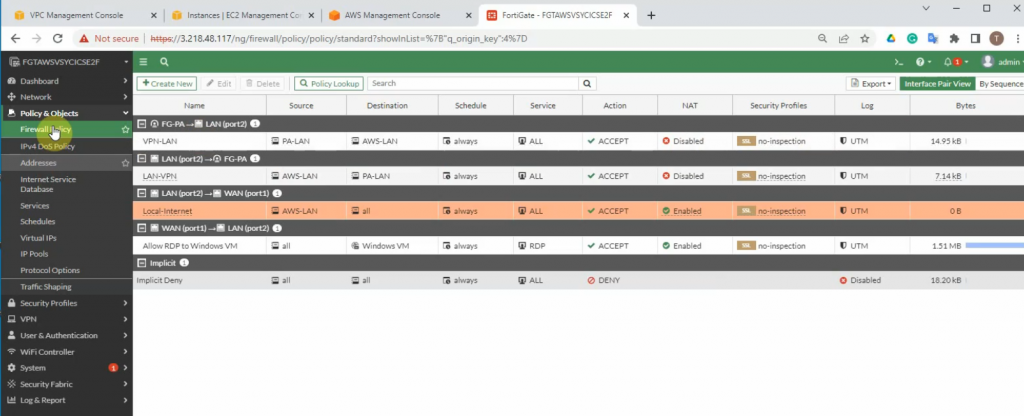
Create a Security Policy to allow traffic from the Fortinet LAN subnet to the PA LAN subnet. Remember to uncheck NAT setting on access rules from AWS LAN to PA LAN and vice versa.
PA LAN subnet to AWS LAN subnet.
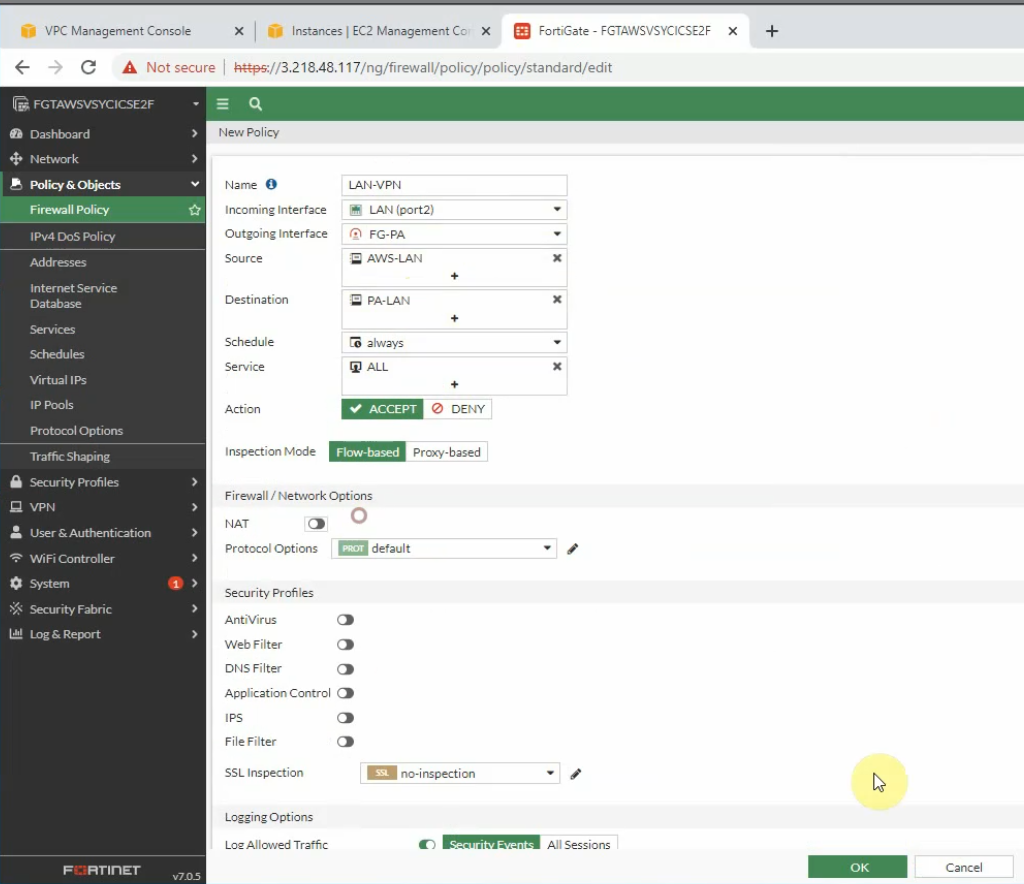
AWS LAN subnet to PA LAN subnet.
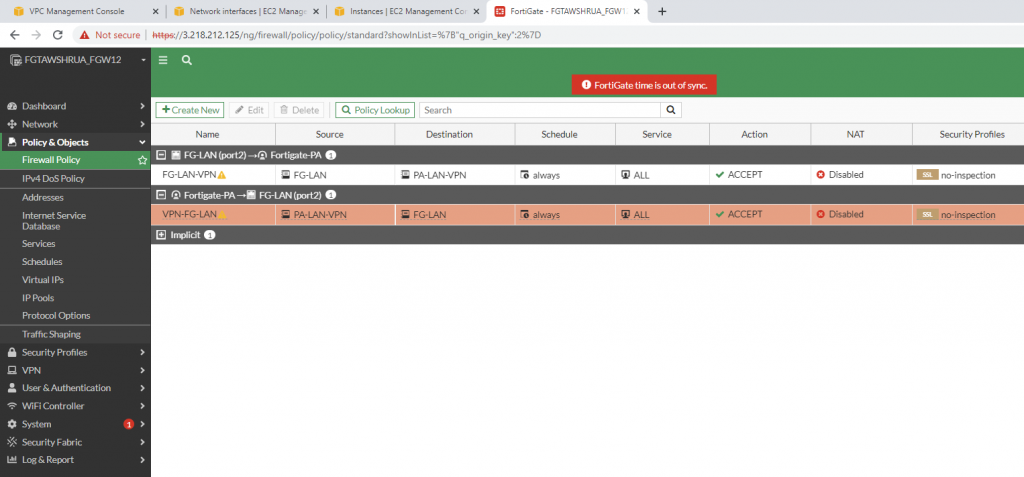
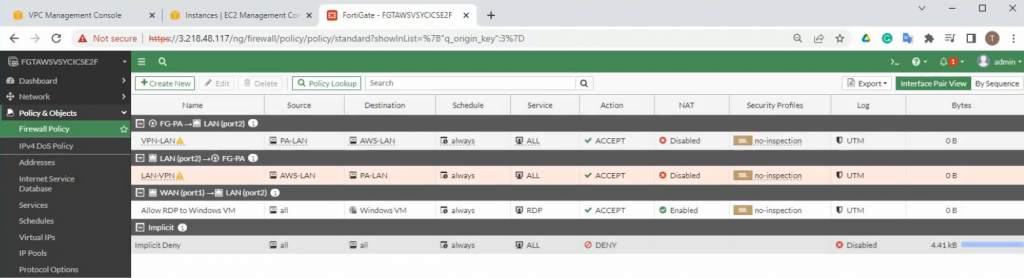
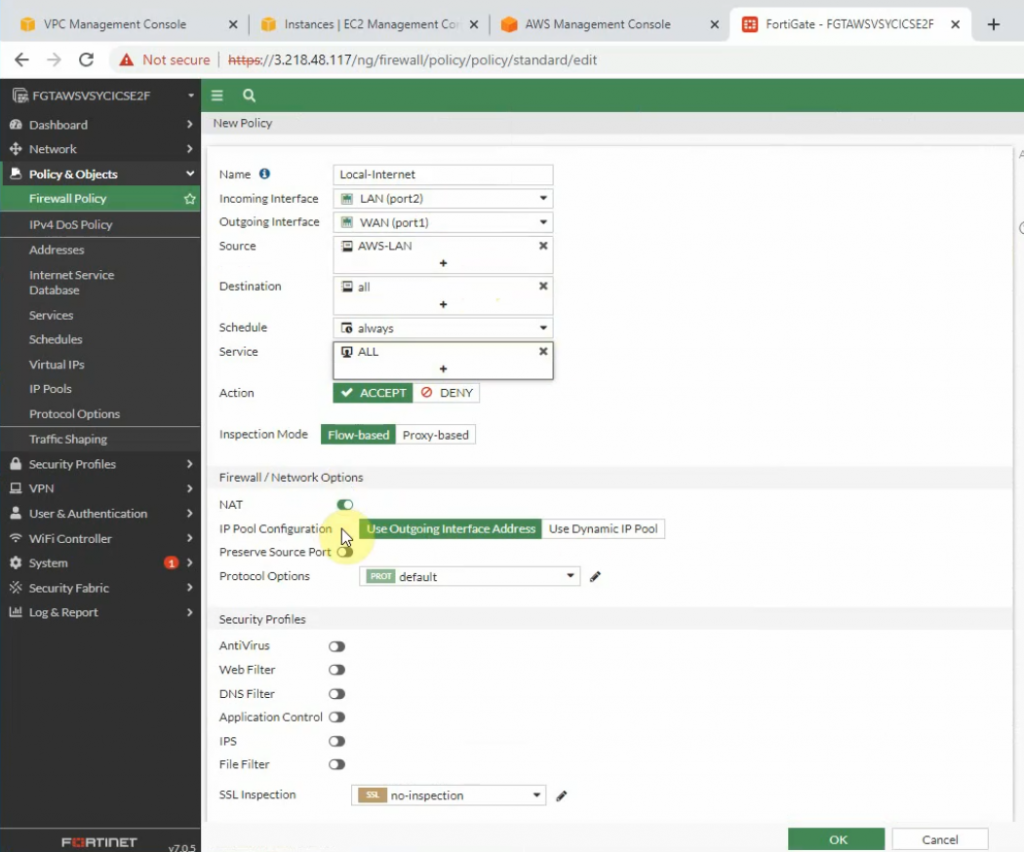
Create a new access rule to allow the FG LAN subnet to access the Internet.
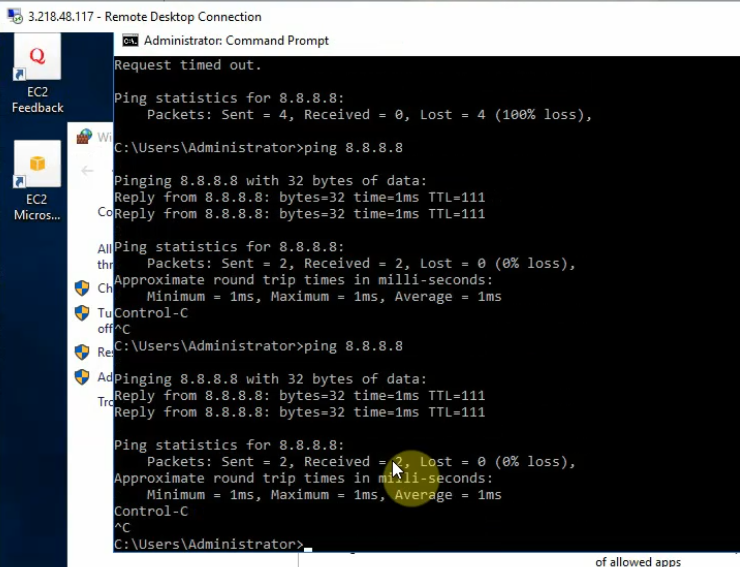
Ping 8.8.8.8 from Windows 2016 VM instance.
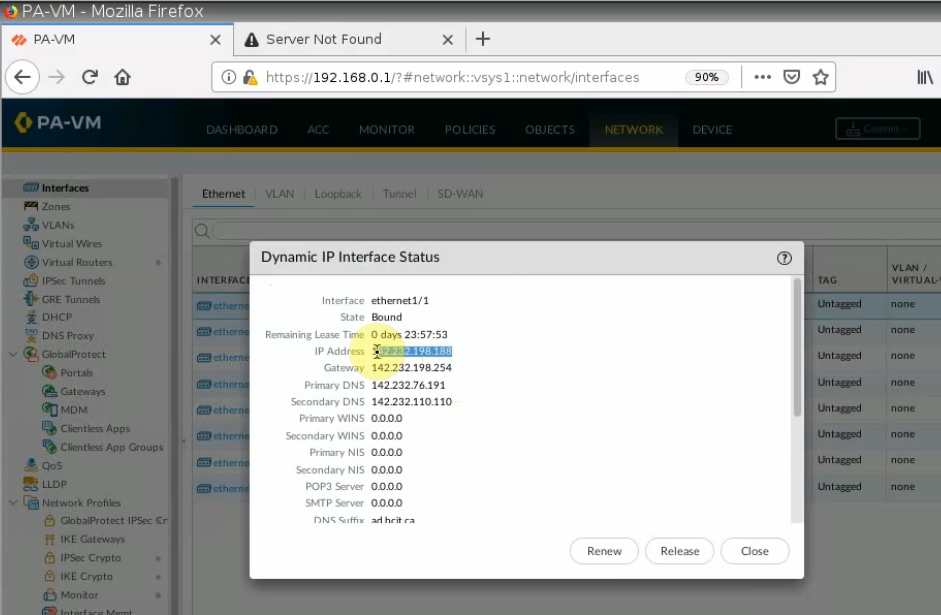
+ Configure PA.
Setting the IP address for e1/1 is DHCP, and assign an IP address for e1/2 is 172.16.1.254/24
Create a tunnel interface: tunnel 1.
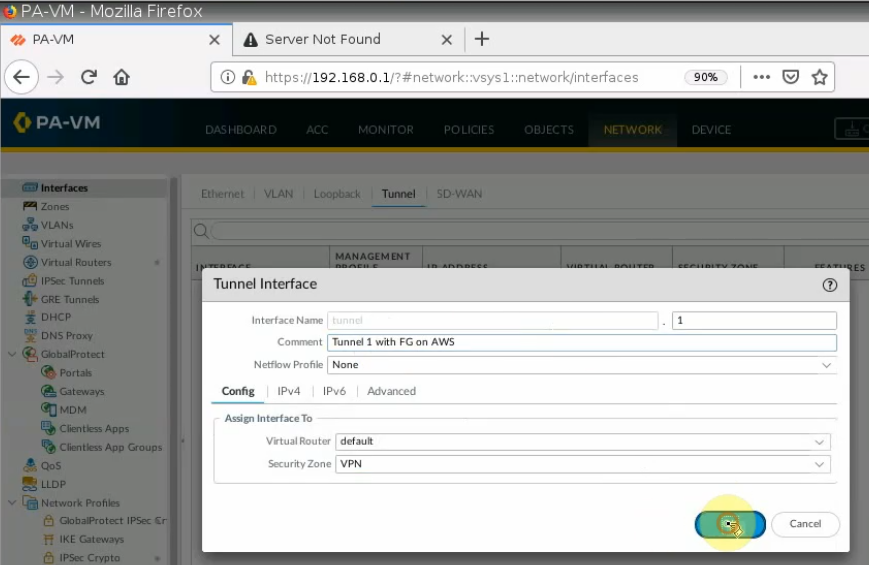
Create network objects for FortiGate, PA LAN, and AWS LAN.
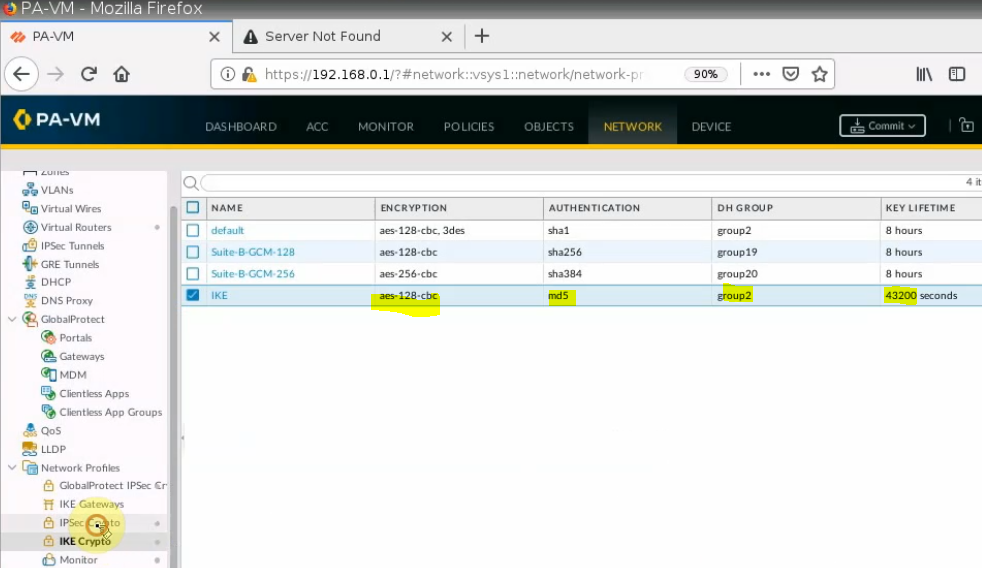
Create IKEC Crypto.
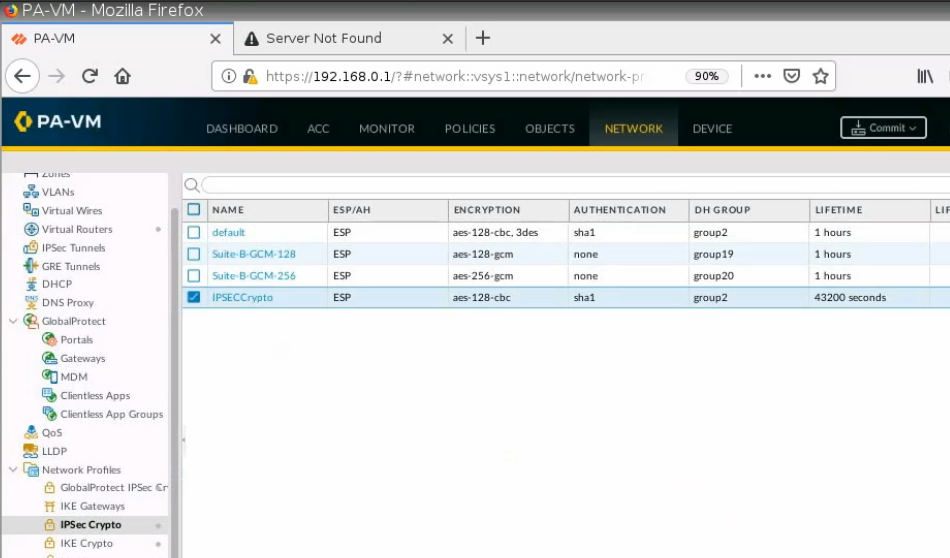
Create an IPSEC Crypto.
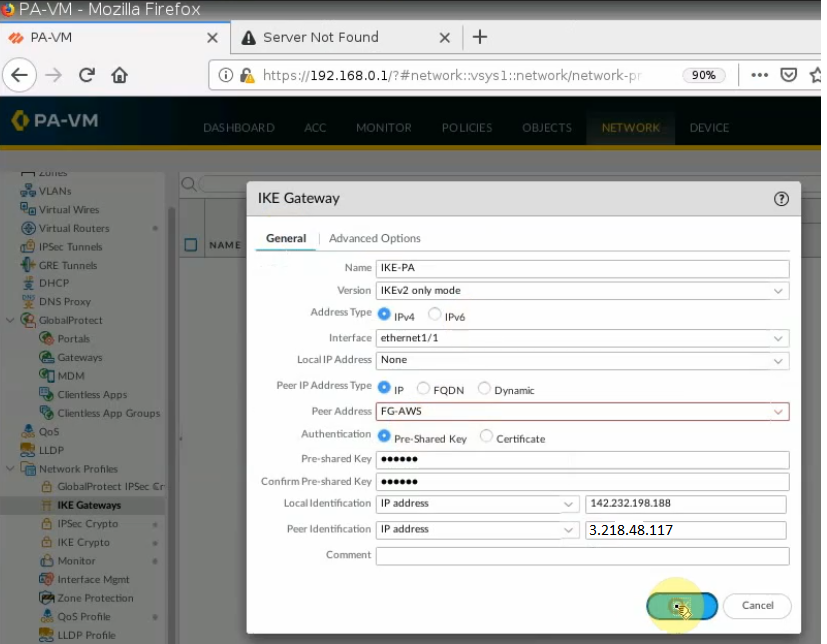
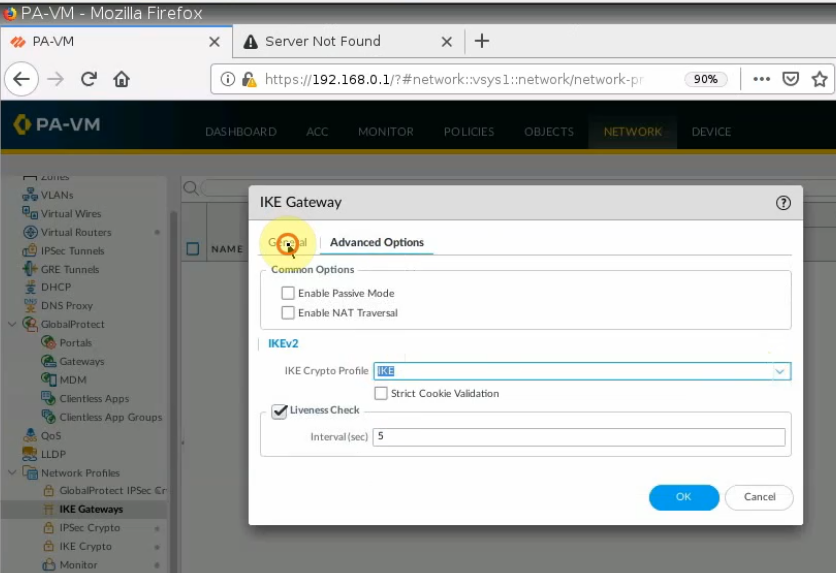
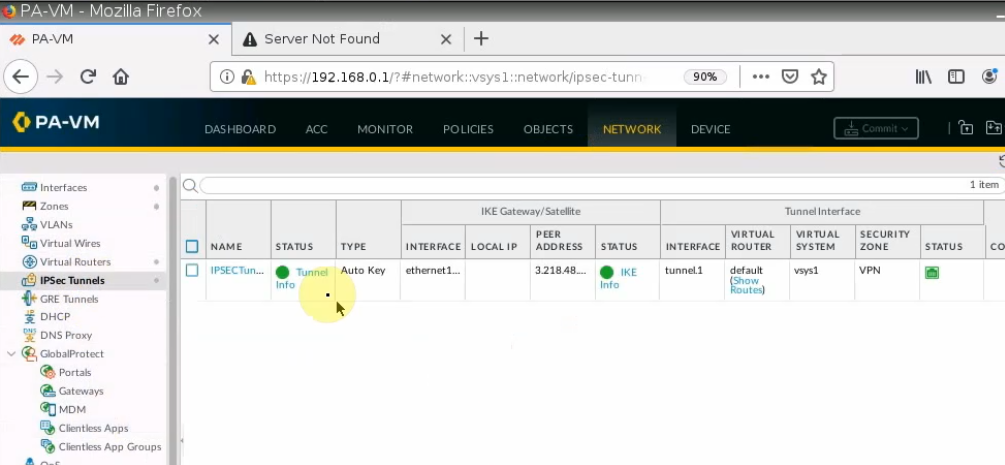
IKE Gateway.
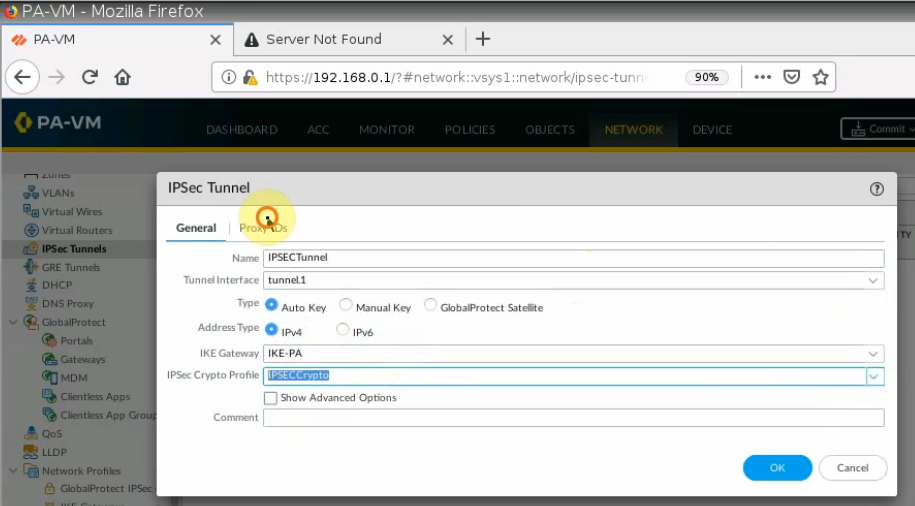
IPSEC tunnel.
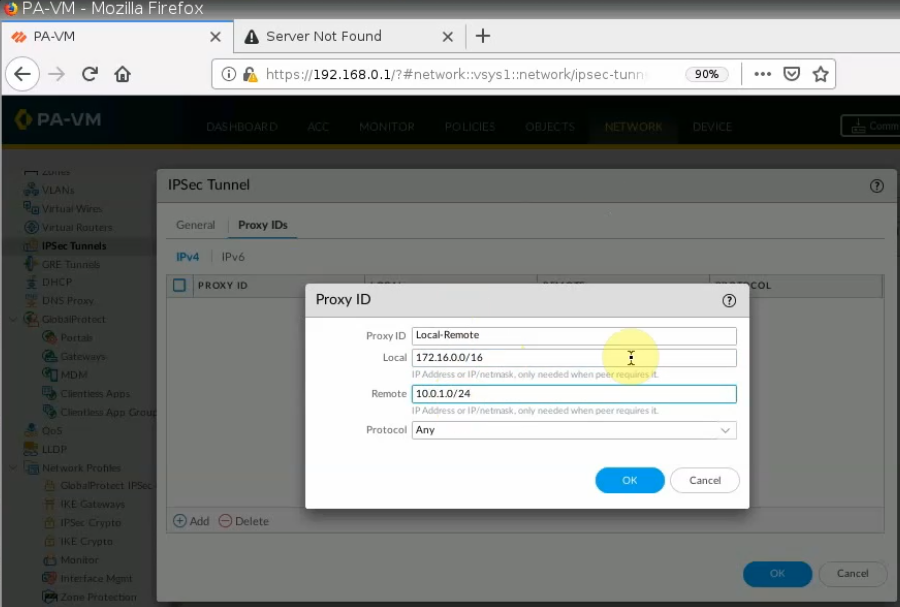
On Proxy ID tab.
Local: PA LAN subnets.
Remote: AWS LAN subnet.
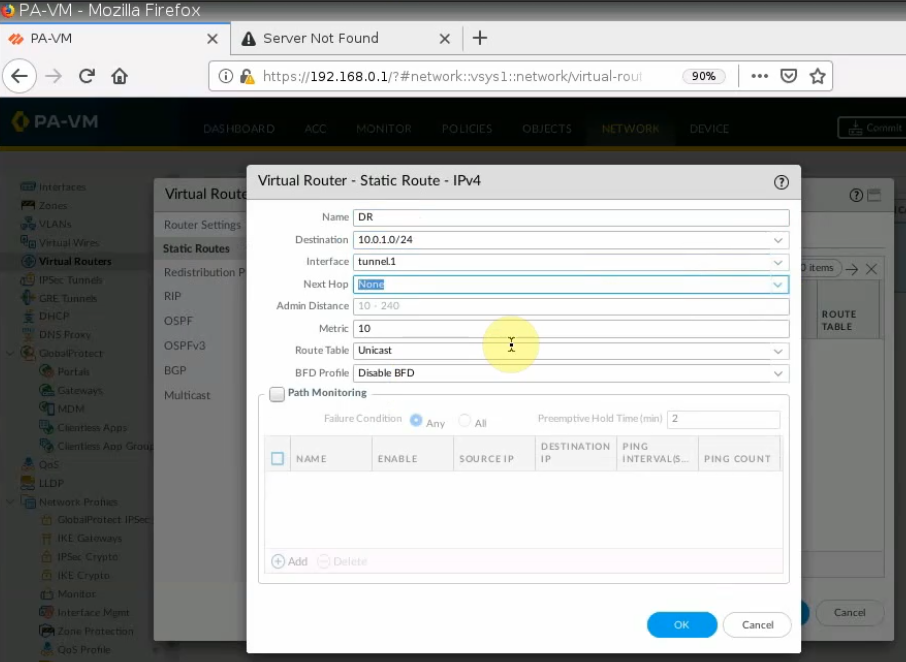
Create a Static Route from PA LAN to Fortinet LAN on AWS.
Create both Security Policies to allow traffic from PA LAN subnet to AWS LAN subnet.
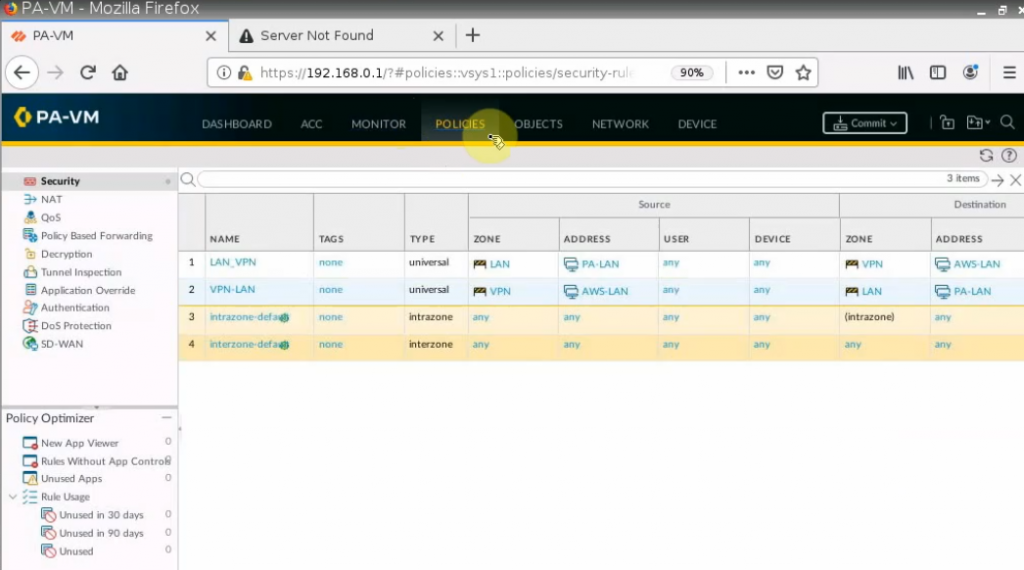
Remember to click “Commit” button to apply the new settings on PA.
From Windows 2016 VM instance, pings a machine on PA LAN subnet.
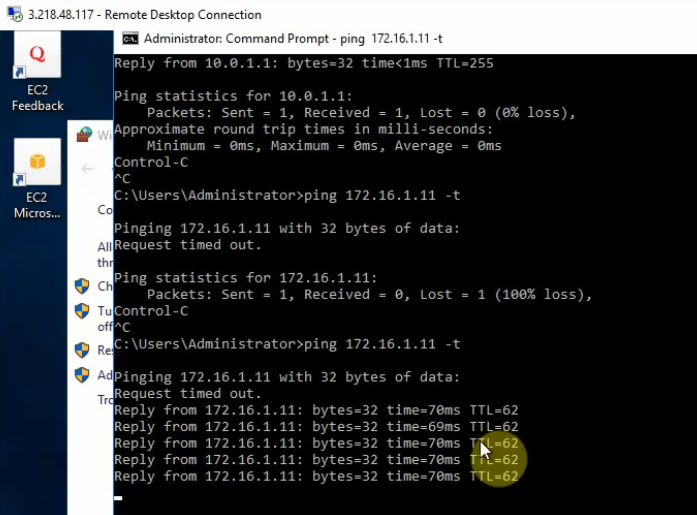
+ Pings from PA LAN subnet to AWS LAN subnet.
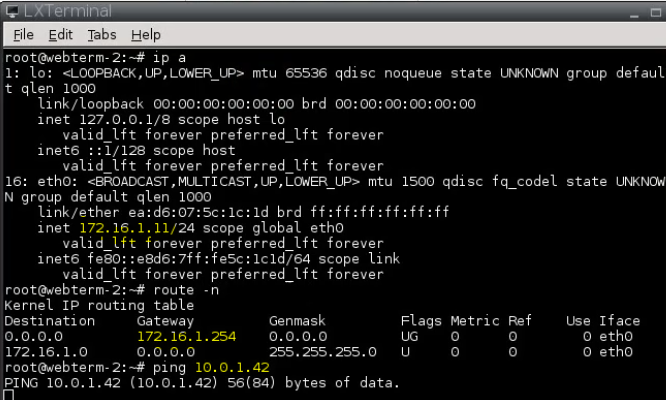
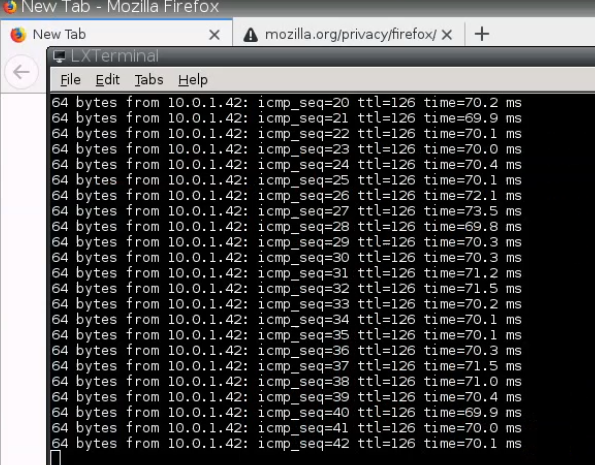
On PA, a tunnel is up.
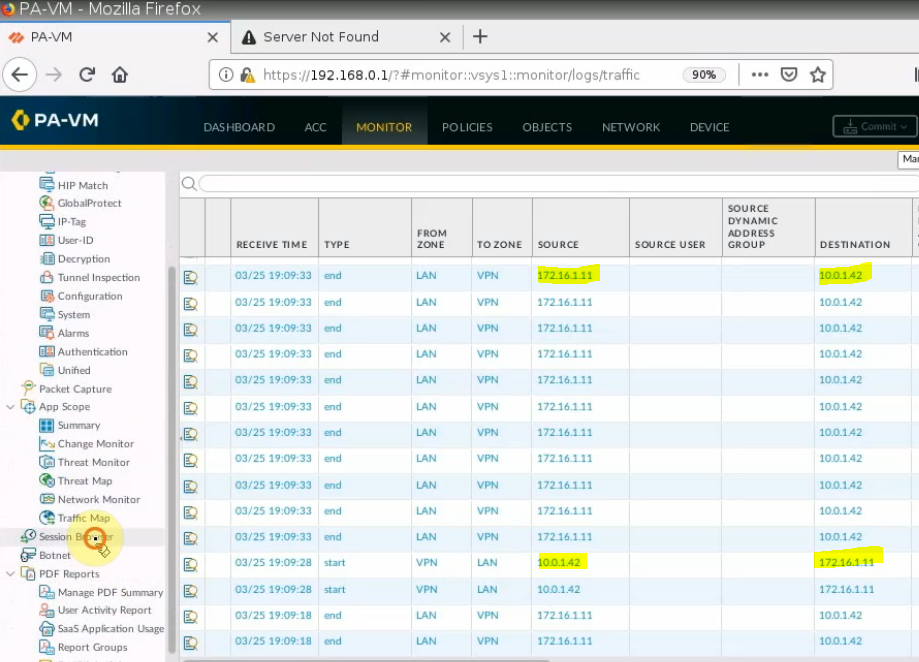
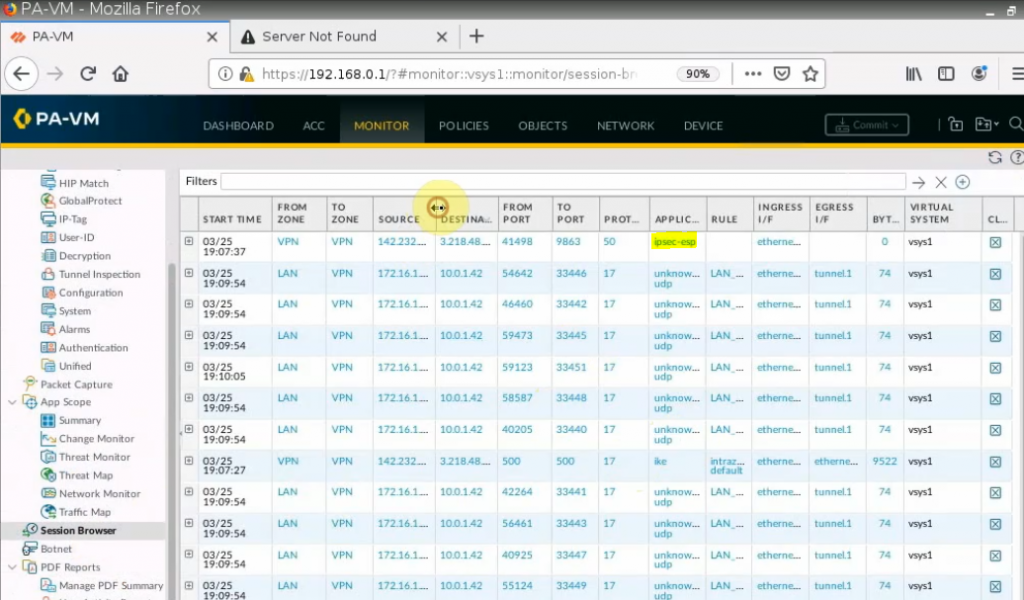
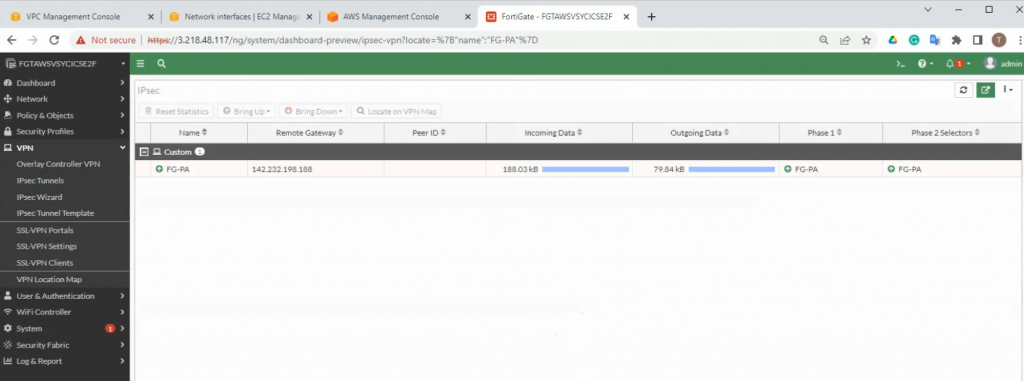
Monitoring to see the traffic on both sites.
On FortiGate.
An IPSEC VPN site-to-site tunnel is up.
diagnose vpn tunnel list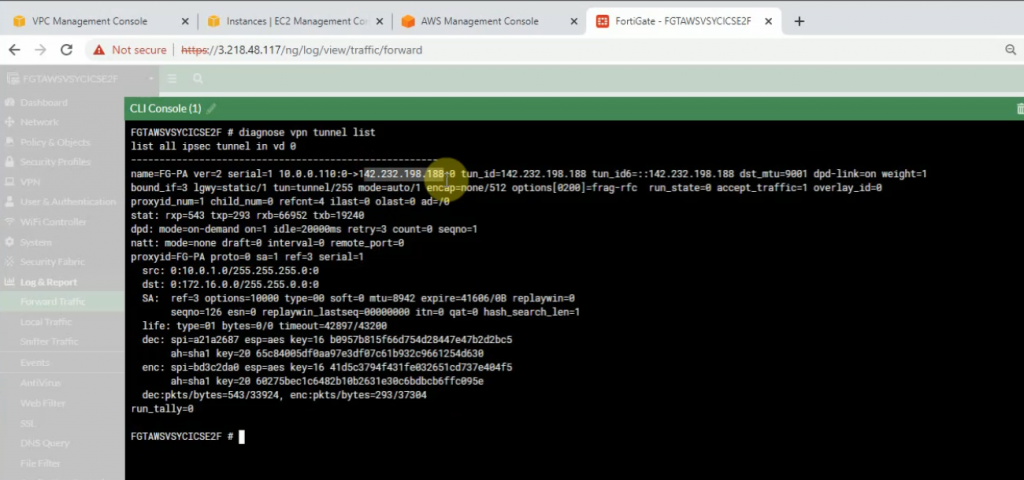
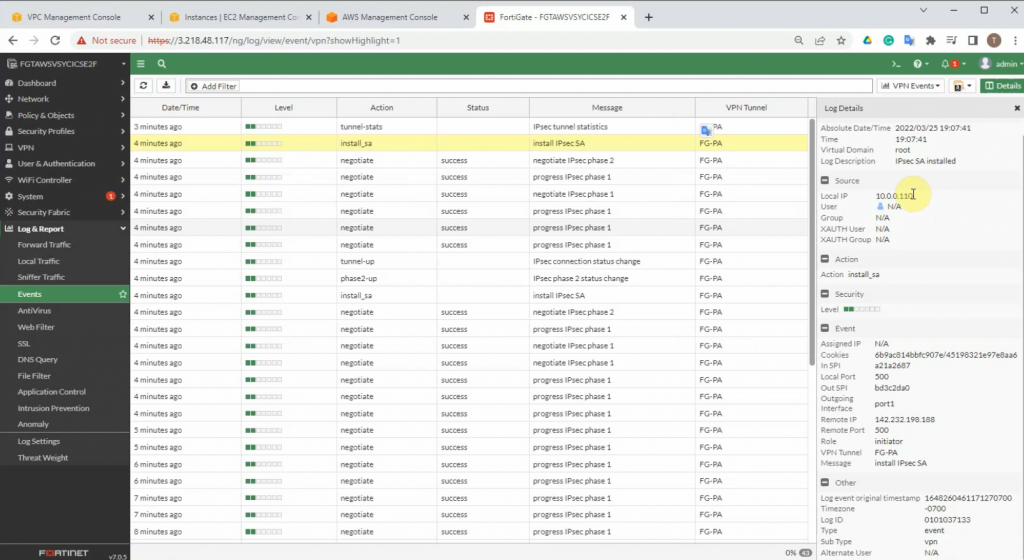
Click on the log and Report to see events that are related to VPN.
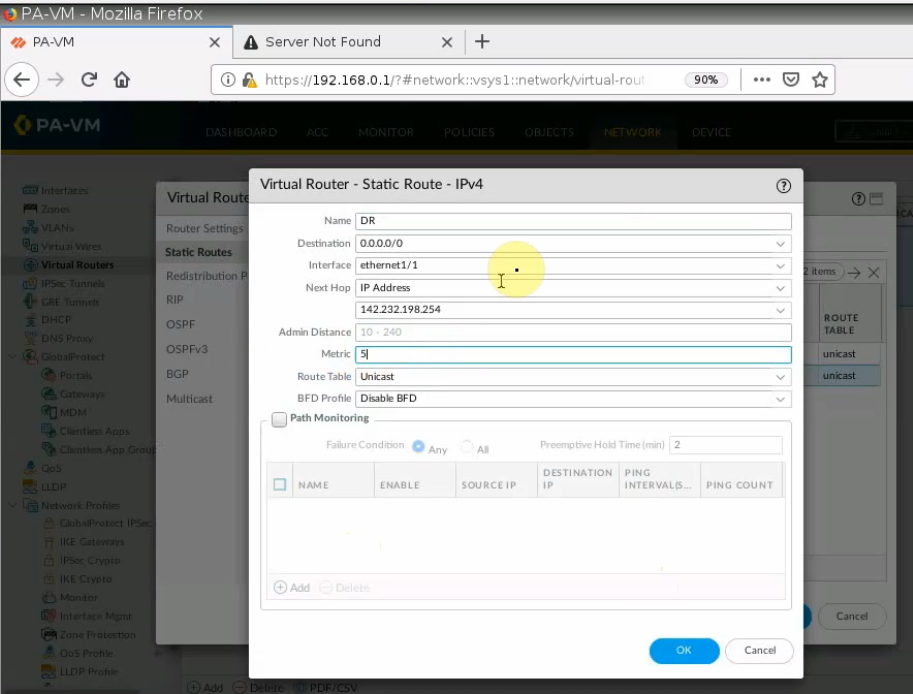
+ Back to PA to create another static route to allow the PA LAN subnet to access the Internet.
A next hop is the default gateway of the PA public subnet.
Create a SNAT policy to allow traffic from the PA LAN subnet to the Internet.
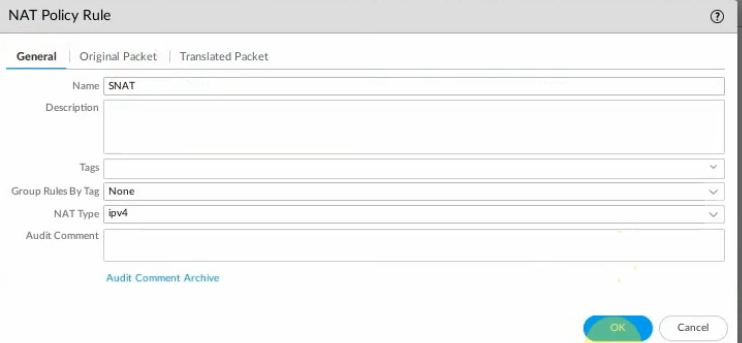
On the Destination interface, should choose e1/1. This is because VPN site-to-site traffic does not use NAT.
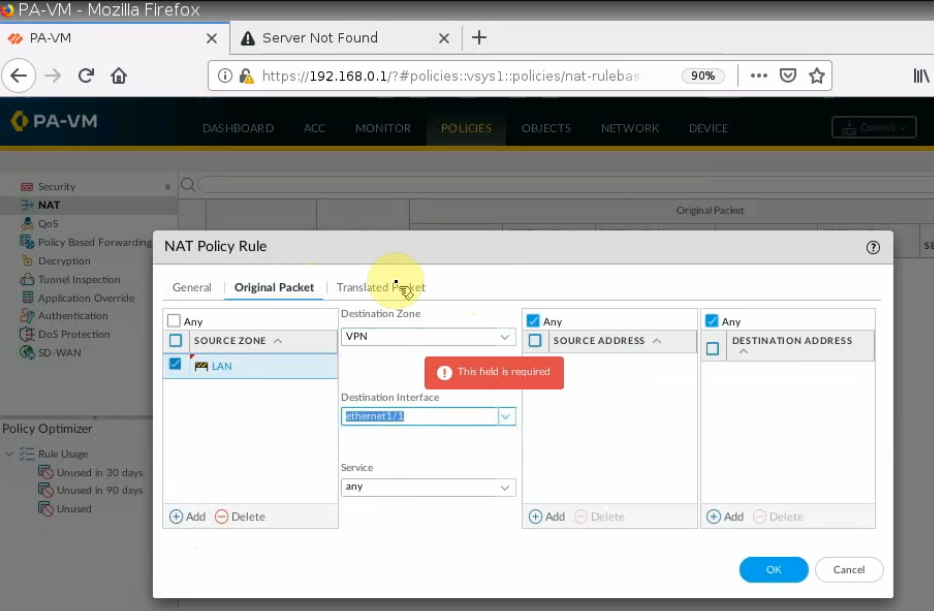
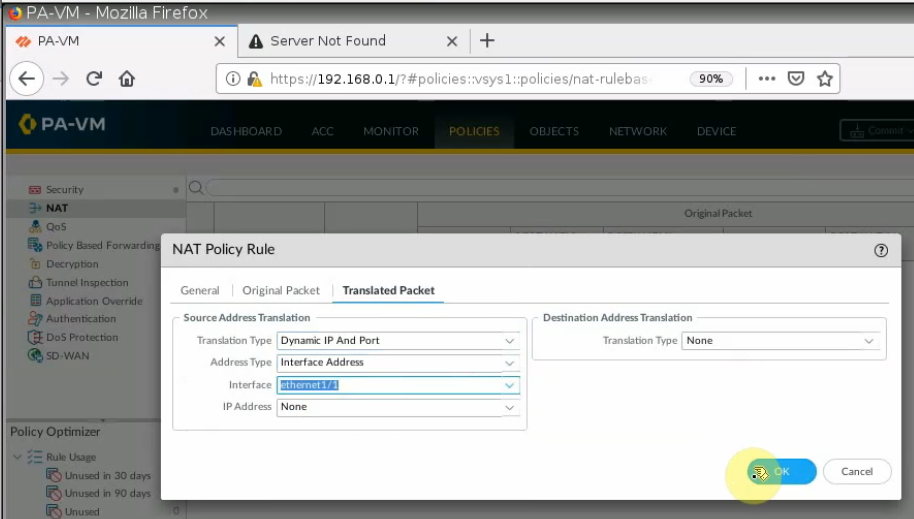
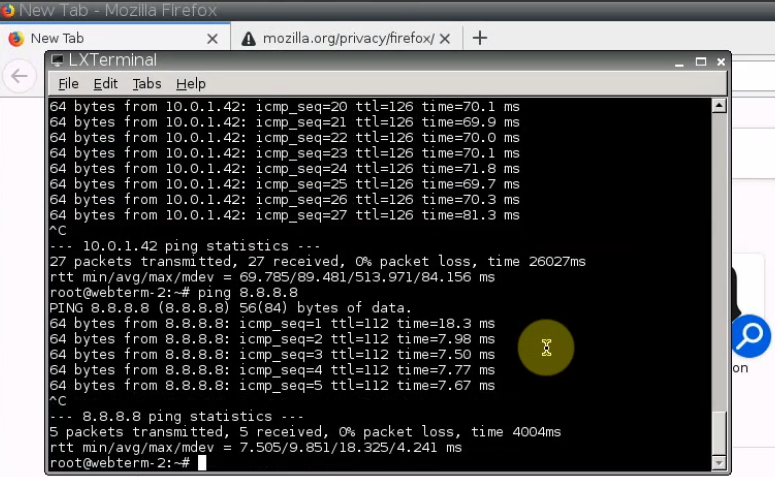
Ping 8.8.8.8 from PA LAN subnet.
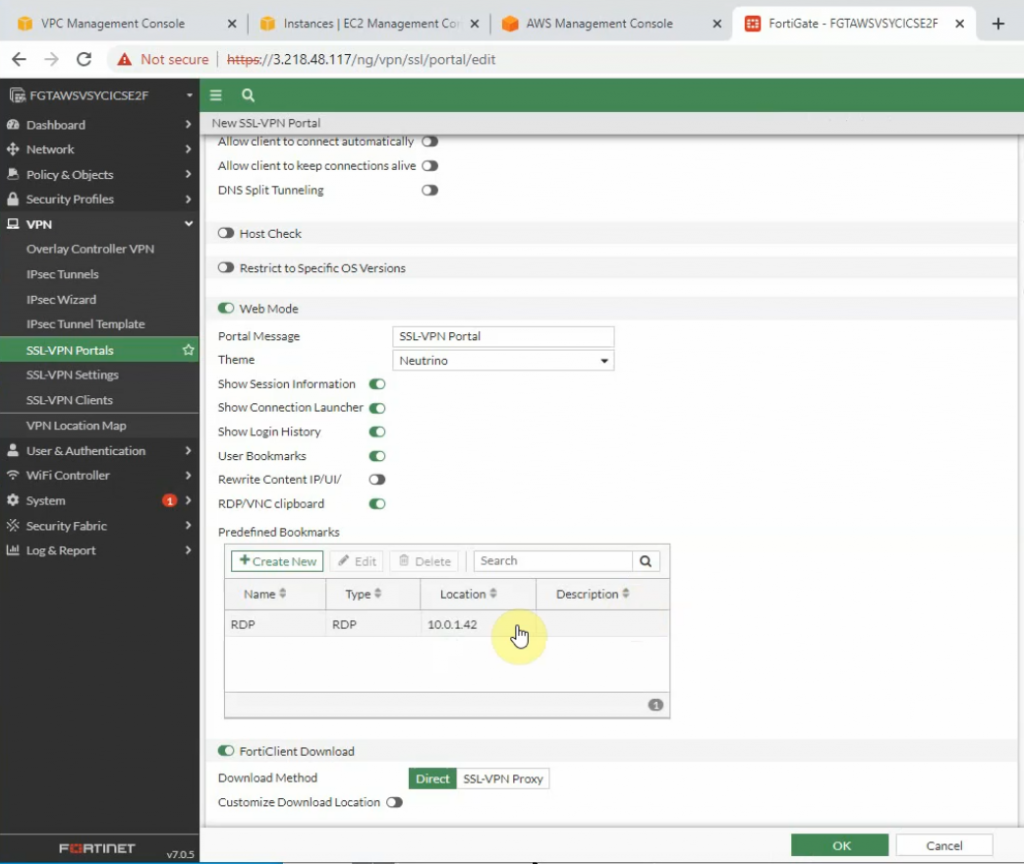
+ Create an SSLVPN portal on FortiGate to allow to access FG private subnet on the SSLVPN zone.
RDP to Windows 2016 instance private subnet on AWS is 10.0.1.42
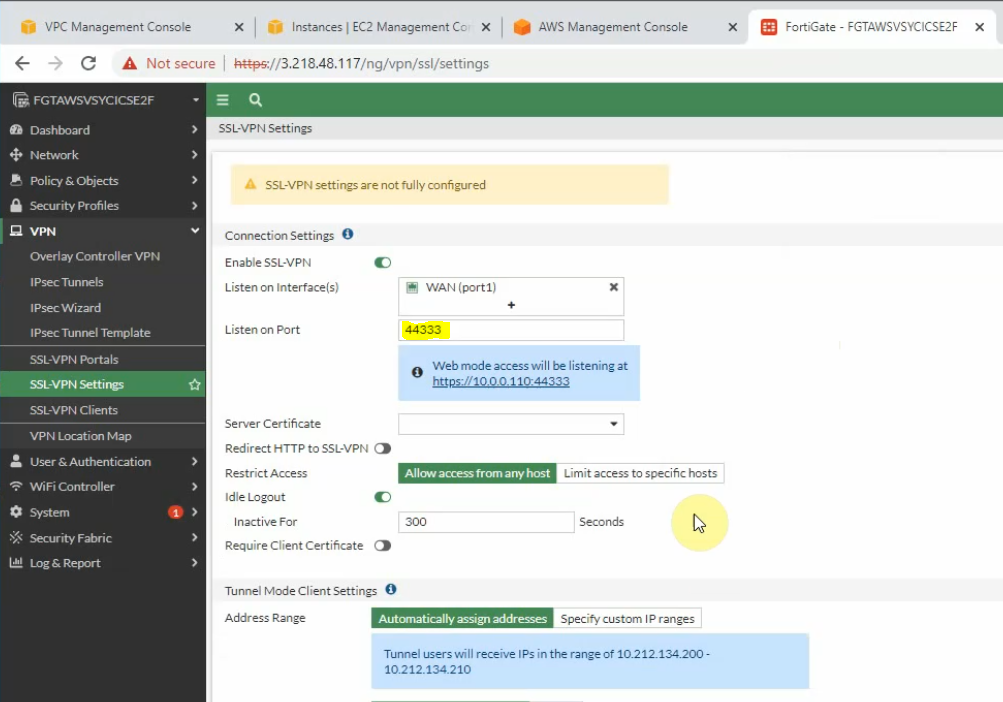
On SSLVPN setting, enable SSLVPN via 44333 port.
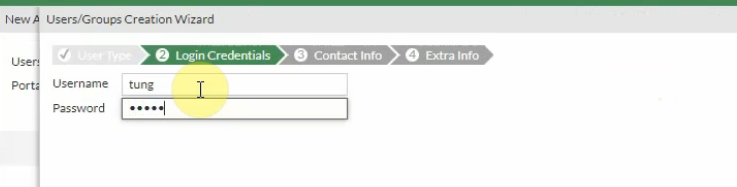
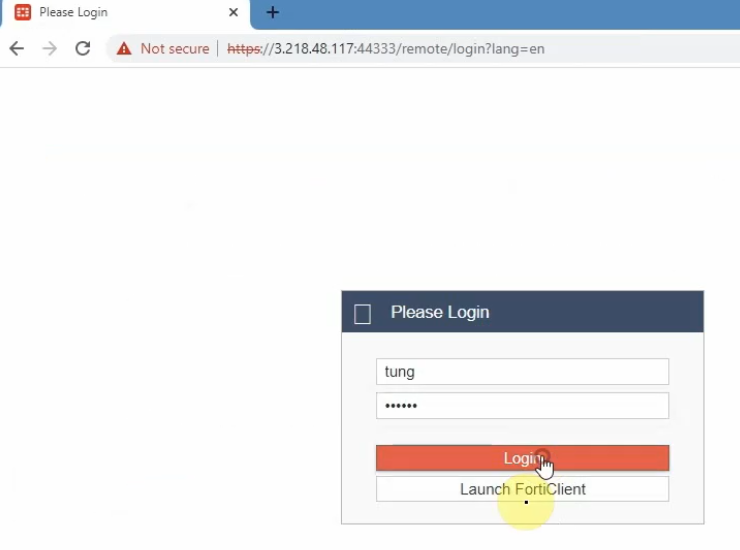
Create a new username and password to access SSLVPN.
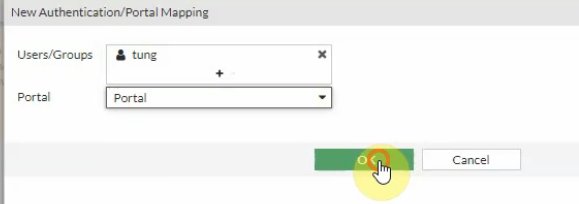
Then assign this user to the portal that we have created on previous step.
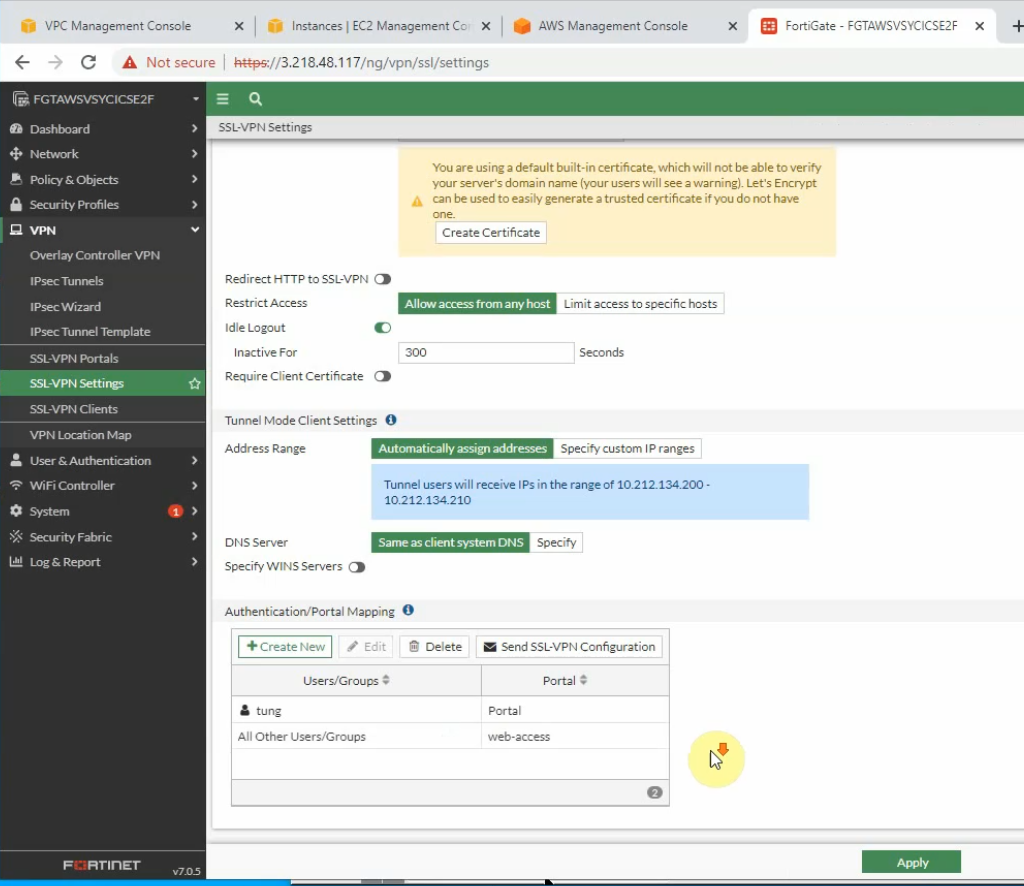
Edit the Security Group to allow Internet traffic to SSLVPN port is 44333.
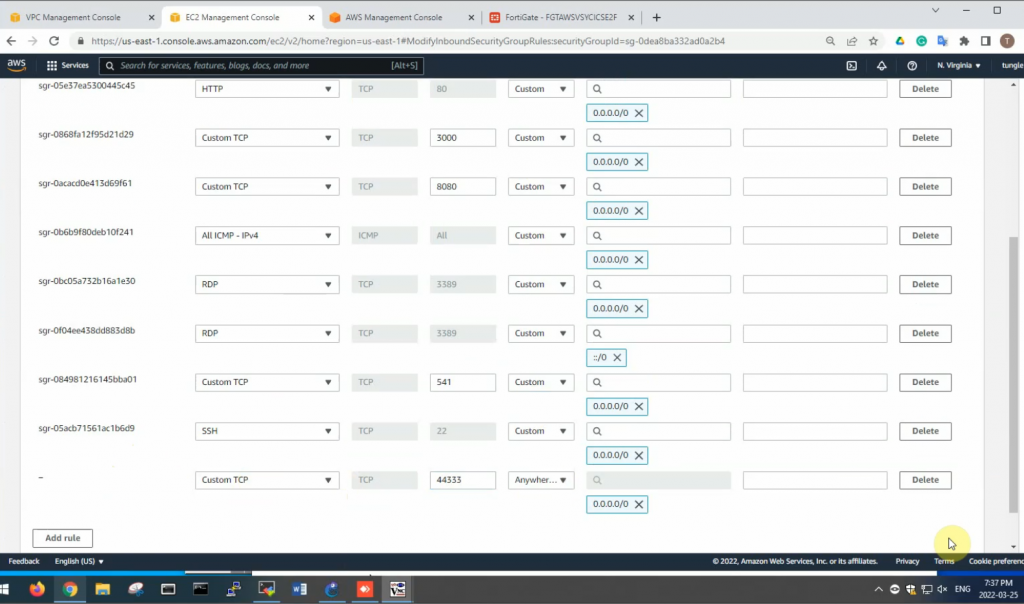
From a Windows machine, access SSLVPN portal on FG.
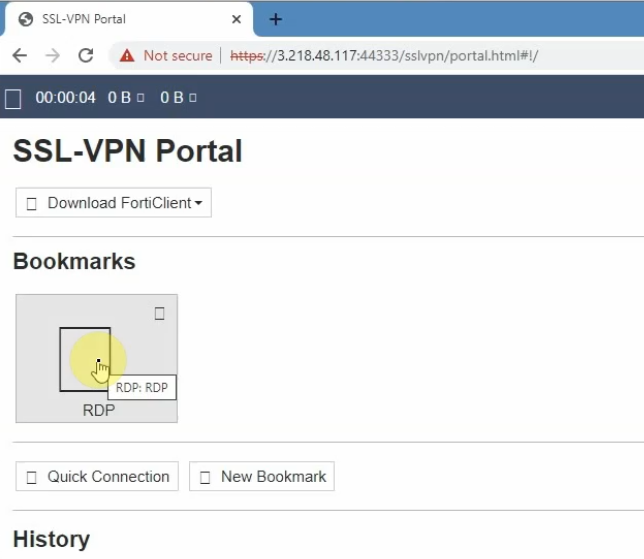
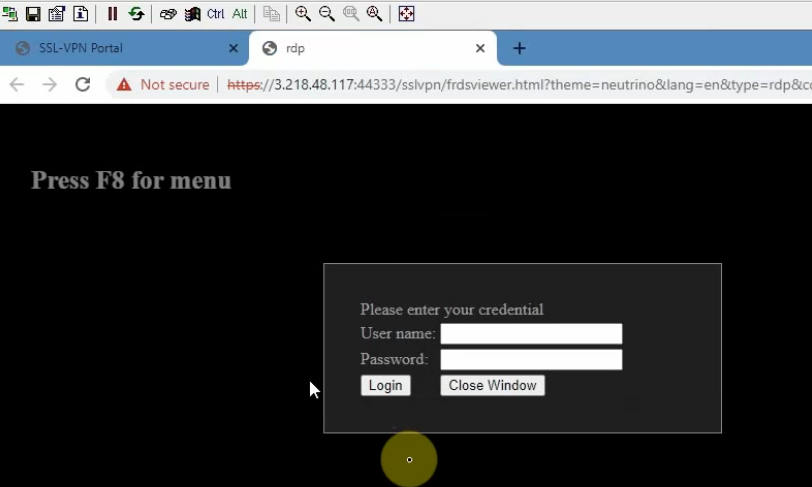
Also, we can use Forticlient to access if we have a license.