This is a diagram that I have used for this lab.
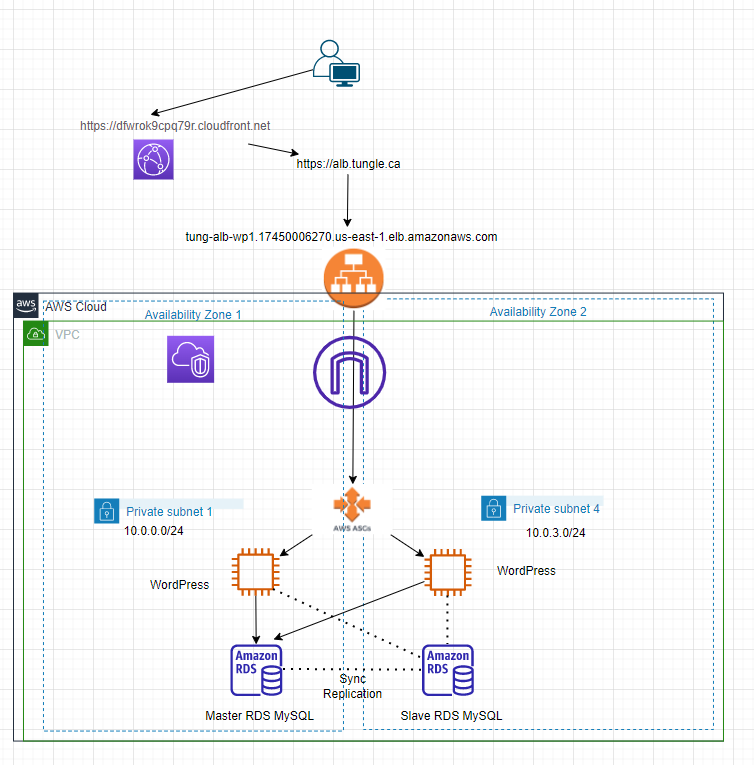
There are several main steps that I have used in the lab.
- Create four private subnets on four AZs.
- Create a WordPress instance on the first AZ.
- Create a new MySQL instance on Multi-AZs deployment.
- Create an AMI image for the WordPress instance.
- Create a Launch configuration.
- Set up an Auto Scaling Group with your launch configuration.
- Request ALB certificate via AWS Certificate Manager.
- Configure HTTPS listener on ALB.
- Configure the HTTP listener and redirect the HTTP traffic to HTTPS.
- Create a CNAME record on your DNS zone for the Amazon domain name.
- Test an Application Load Balancer for WordPress on multiple AZs with MySQL instance on Multi-AZ deployments.
- Configure Amazon CloudFront.
- Test an Application Load Balancer for WordPress on your cloudfront.net domain.
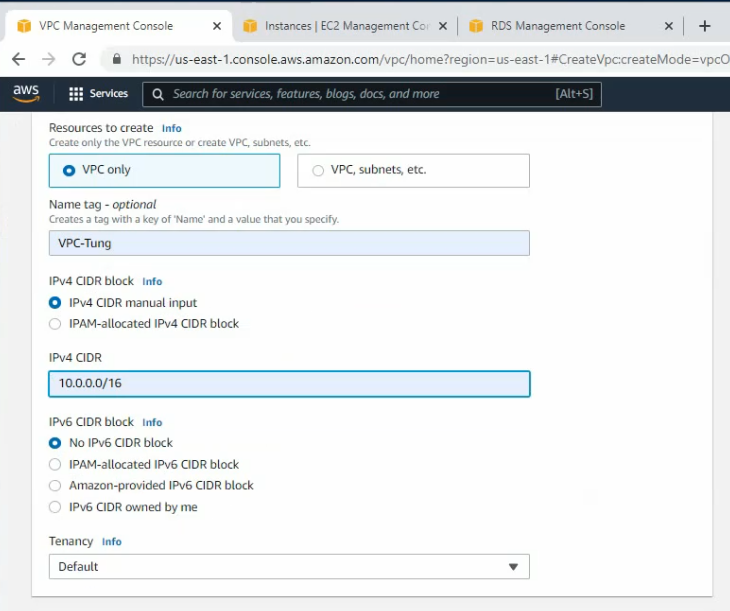
Create a new VPC.
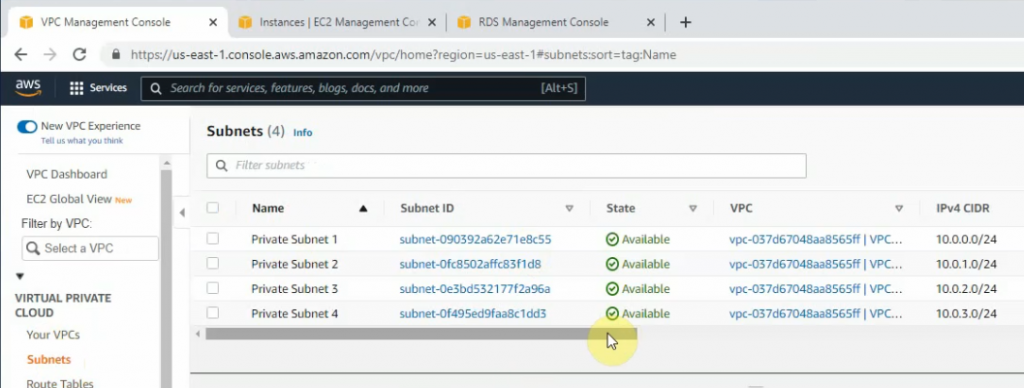
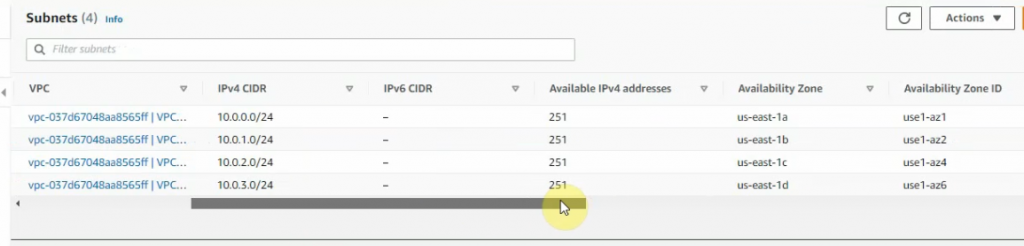
Create 4 private subnets on 4 Availability zones.
Create and attach a new Internet Gateway to your VPC.
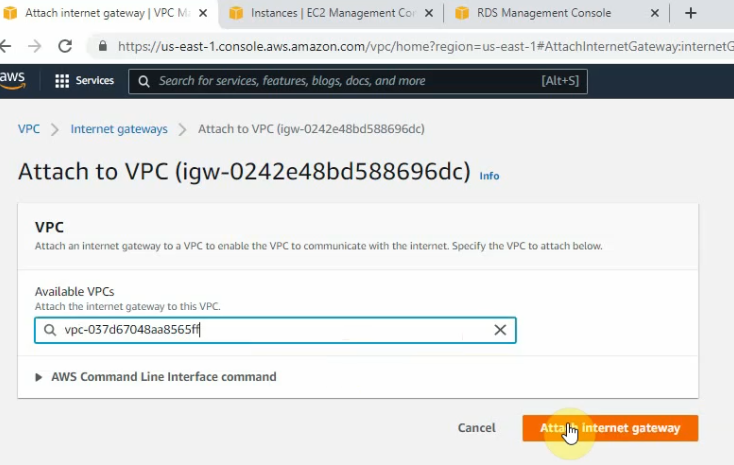
Create a static route 0.0.0.0/0 on your VPC.
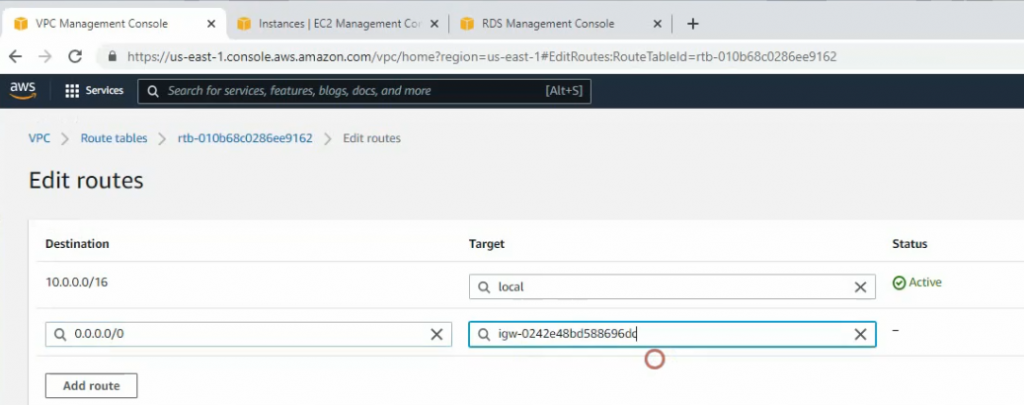
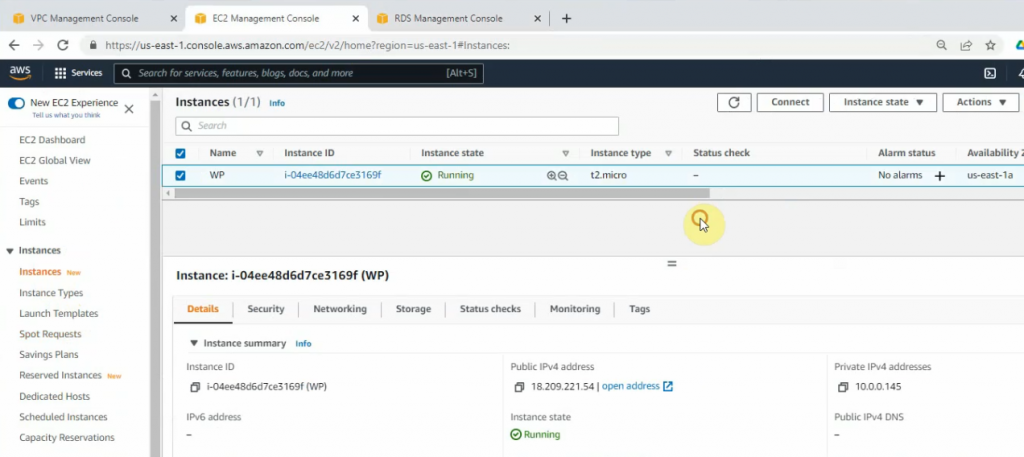
Create a Linux instance.
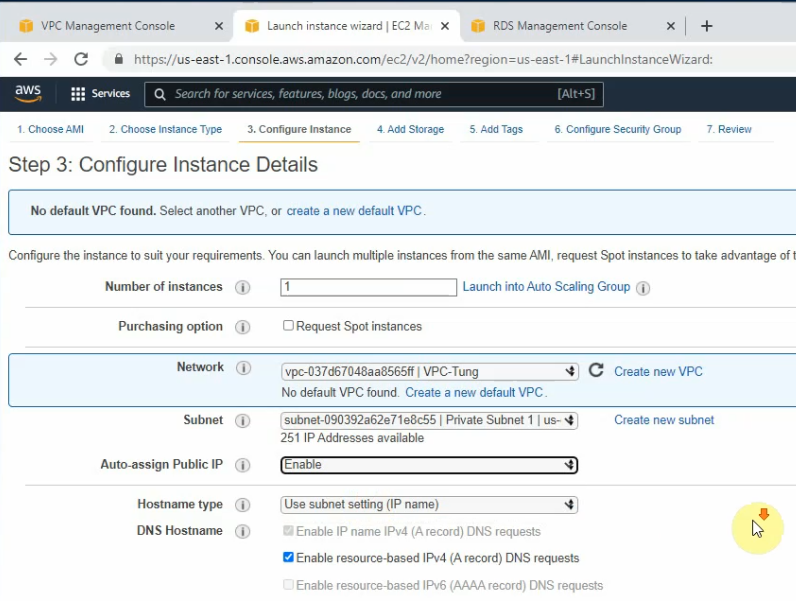
Copy it into the User data setting.
#!/bin/bash
yum update -y
# Install Apache web service
yum install httpd -y
# Download WordPress
wget https://wordpress.org/latest.tar.gz
tar -zxf latest.tar.gz
# Install php7.4
amazon-linux-extras install php7.4 -yCreate a WordPress-SG.
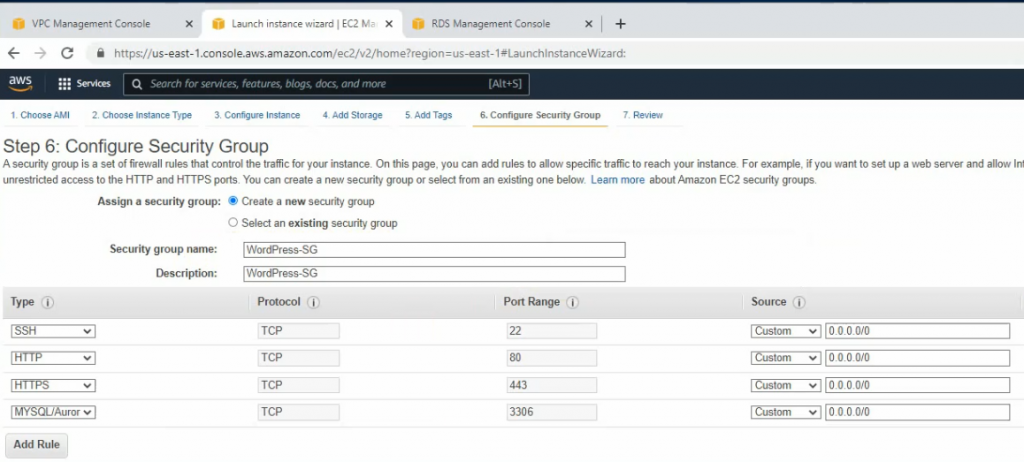
Create a new Security Group is WordPress-ALB-AutoScaling for ALB AutoScaling.
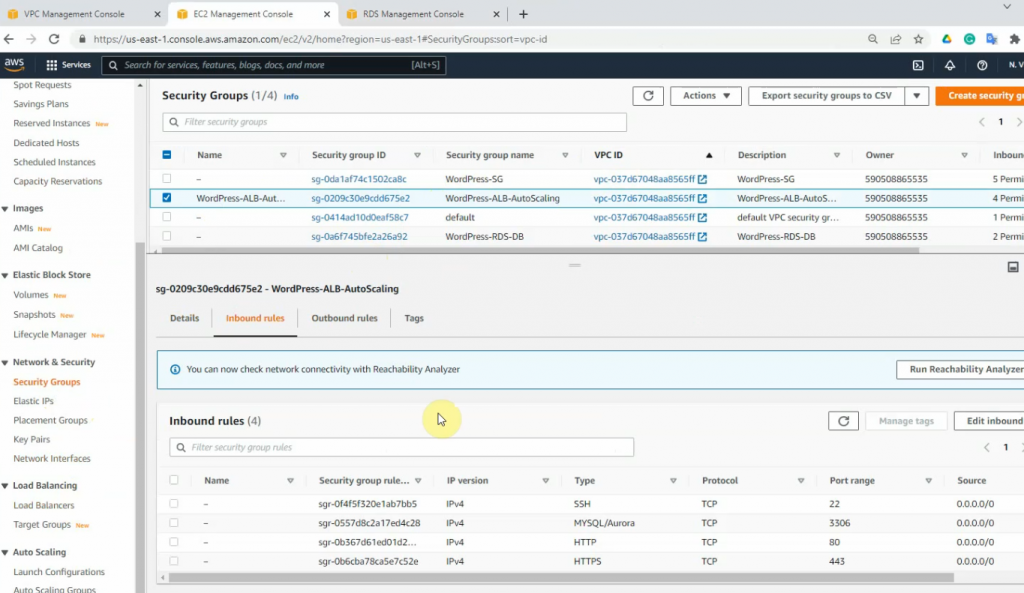
SSH to the Linux instance, and check httpd, php is installed on the machine.
rpm -qa | grep httpd
rpm -qa | grep php
sudo yum install php -y
sudo systemctl start httpd
sudo systemctl enable httpd
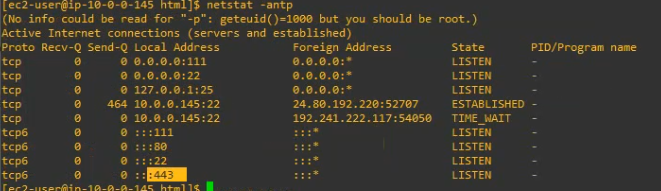
netstat -antpCopy all files on WordPress directory to /var/www/html.
cd wordpress
sudo cp -r * /var/www/html
cd /var/www/htmlCreate an ip.php file on /var/www/html directory.
#sudo nano ip.php
<?php
echo "Local IP address: "; echo $_SERVER['SERVER_ADDR'];
echo "<br>";
echo "Public IP address: "; echo $_SERVER['SERVER_NAME']
?>Install mod_ssl on the Linux instance.
sudo yum install mod_sslCreate a TLS certificate for the Linux instance.
sudo openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/pki/tls/private/localhost.key -out /etc/pki/tls/certs/localhost.crt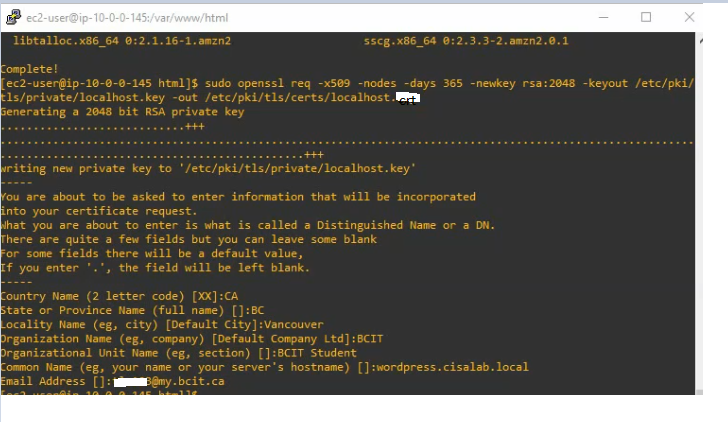
Restart apache web service.
sudo systemctl stop httpd
sudo systemctl start httpdCheck https is running on the Linux instance.
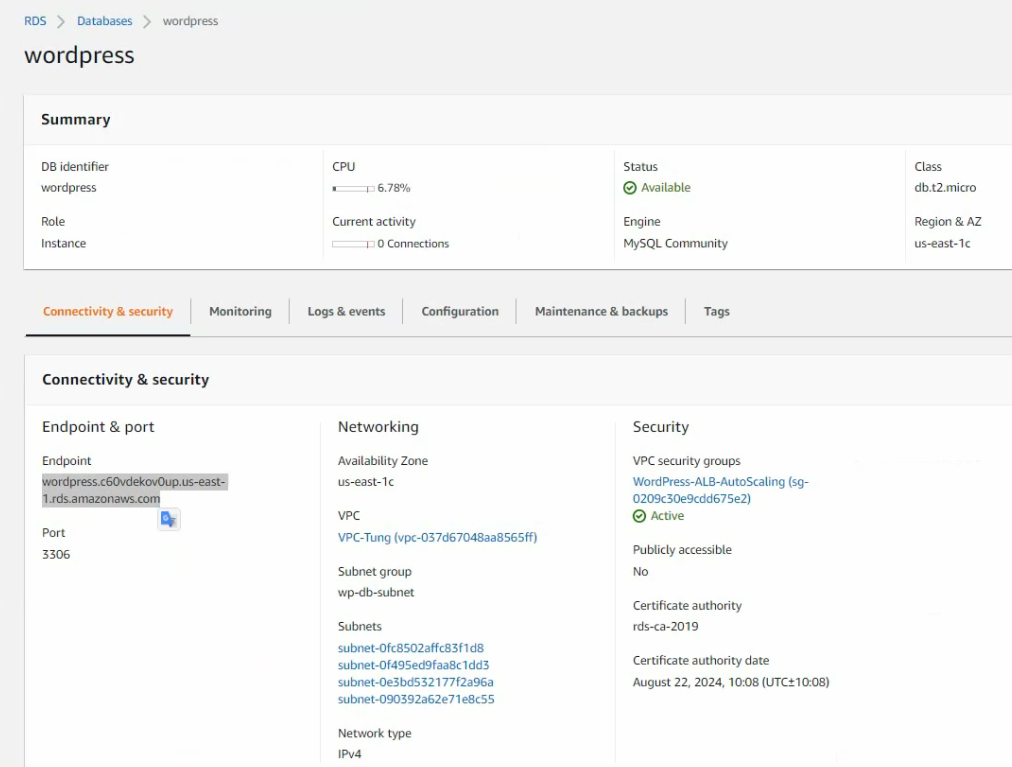
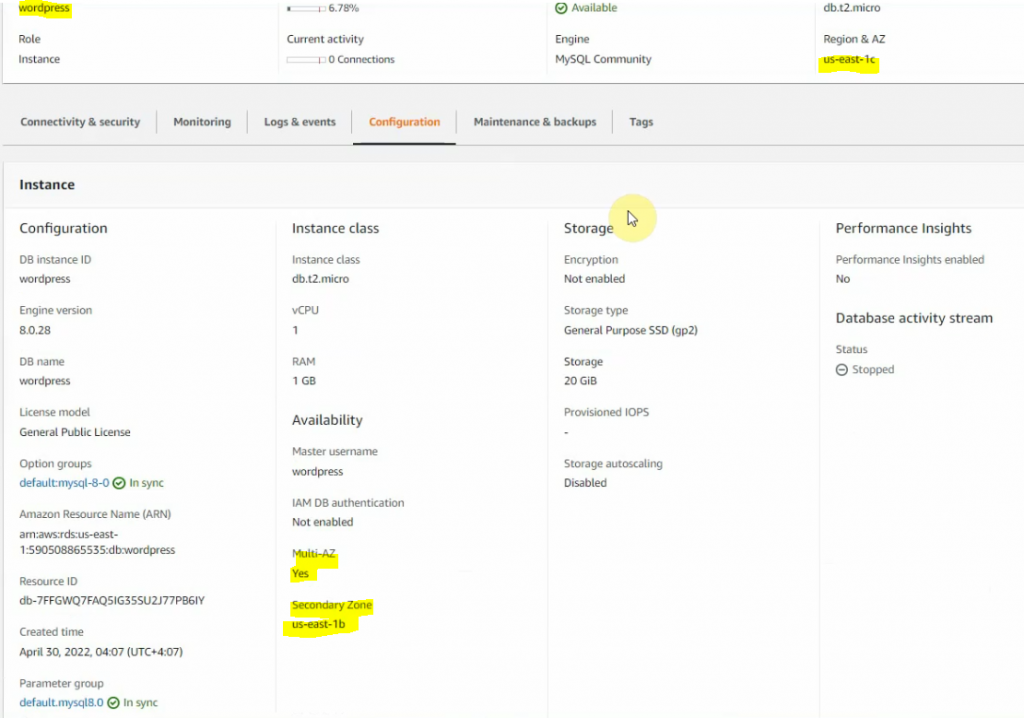
Go to RDS, and create a new database subnet.
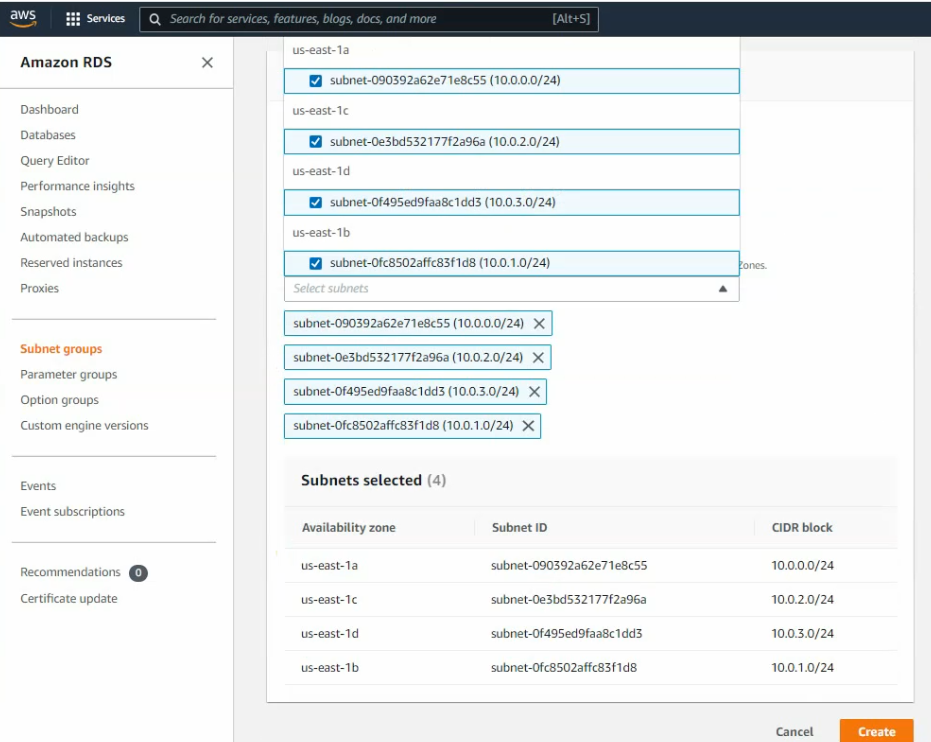
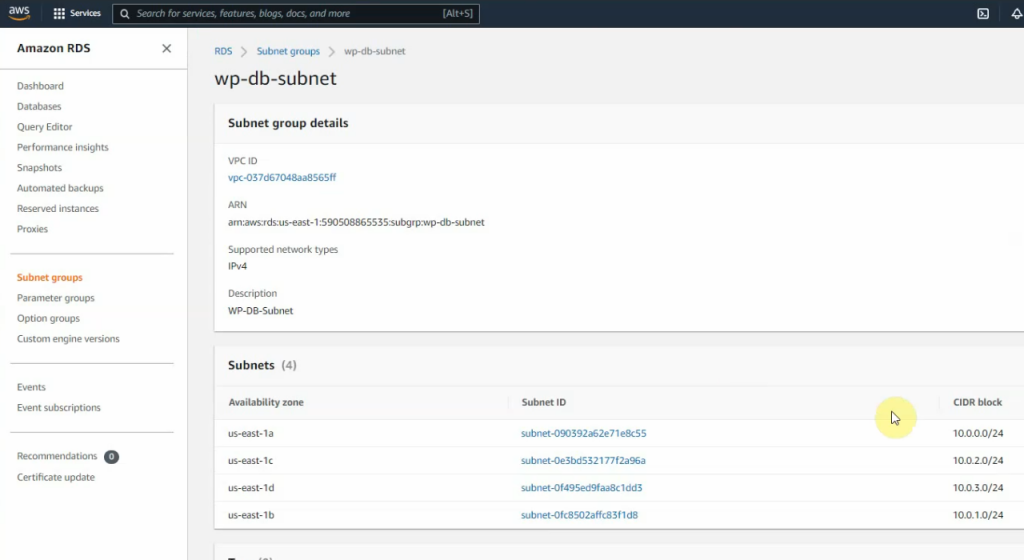
Create a new database instance on AWS.
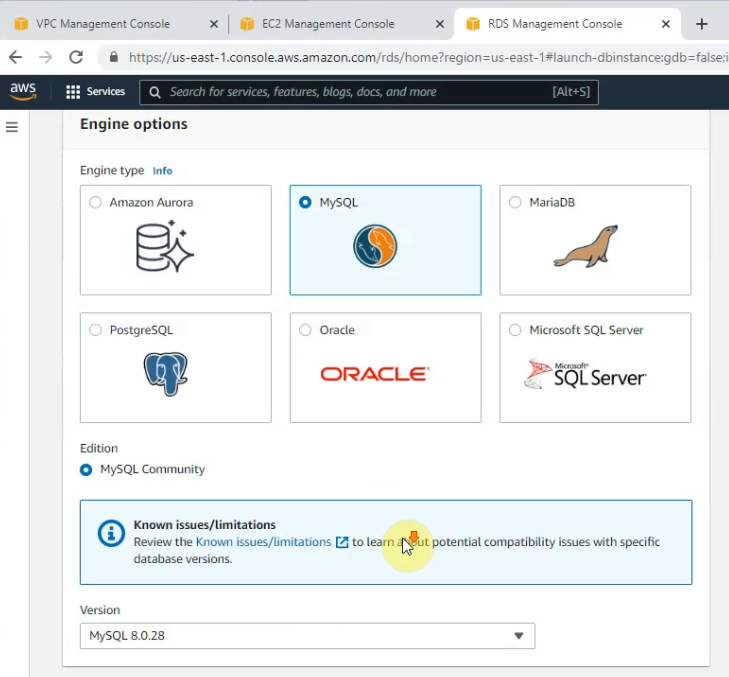
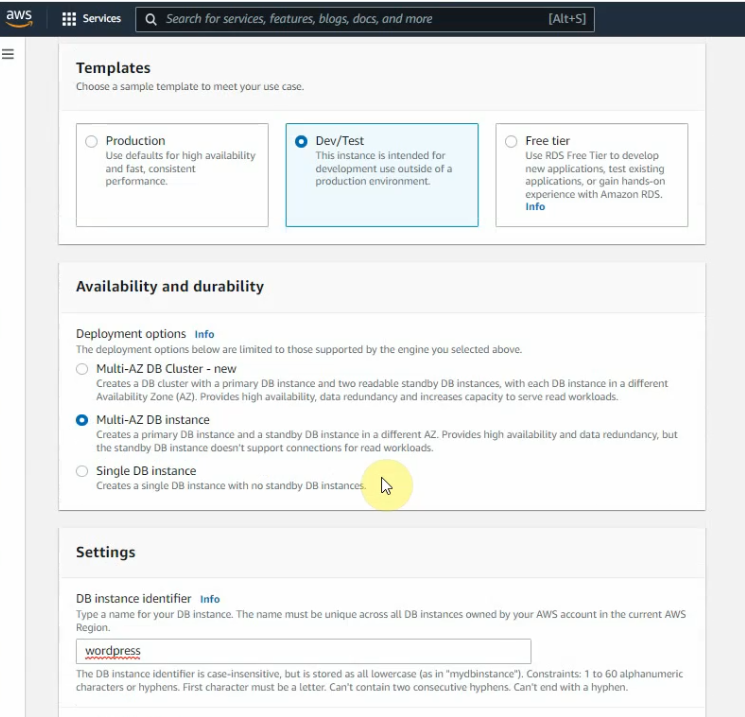
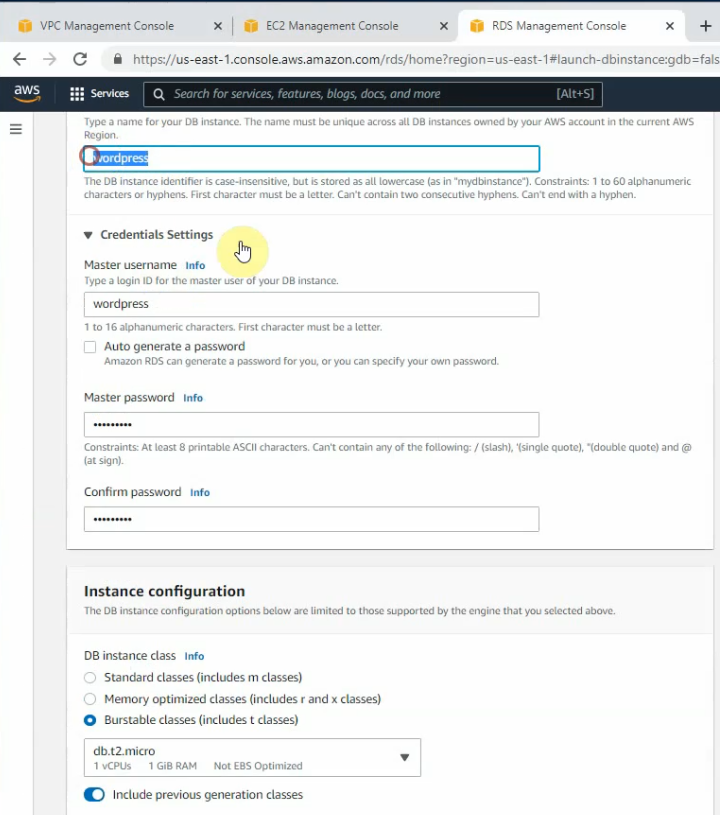
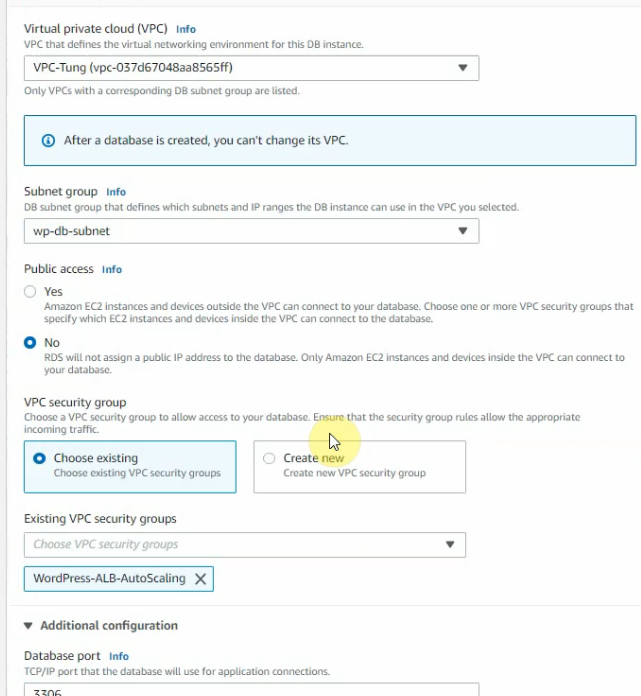
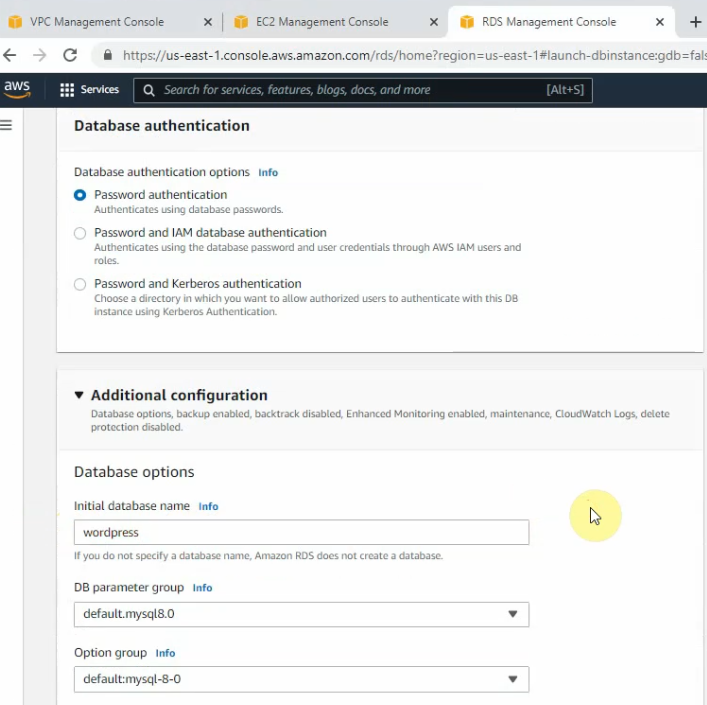
Create a database.
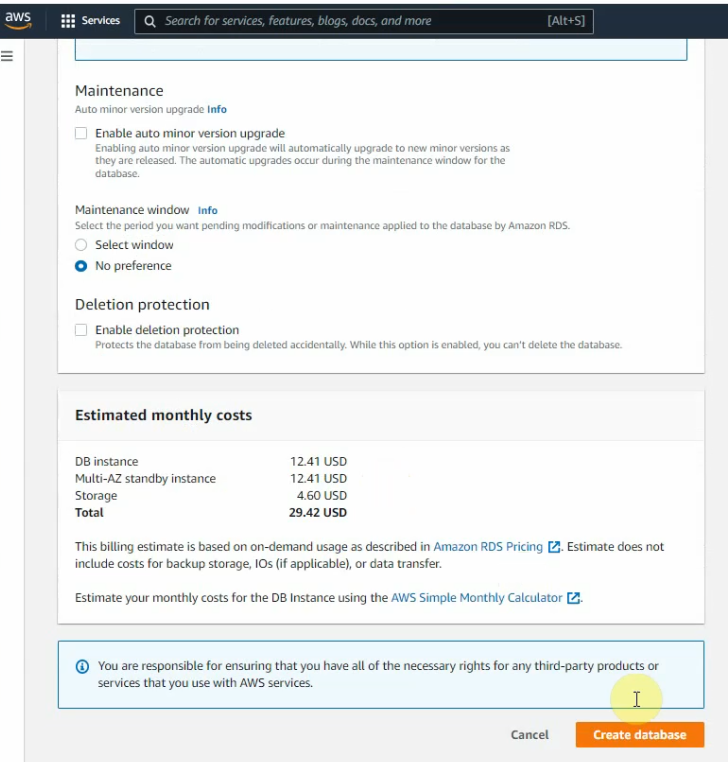
Open https://18.209.221.54 on your web browser to set up WordPress.
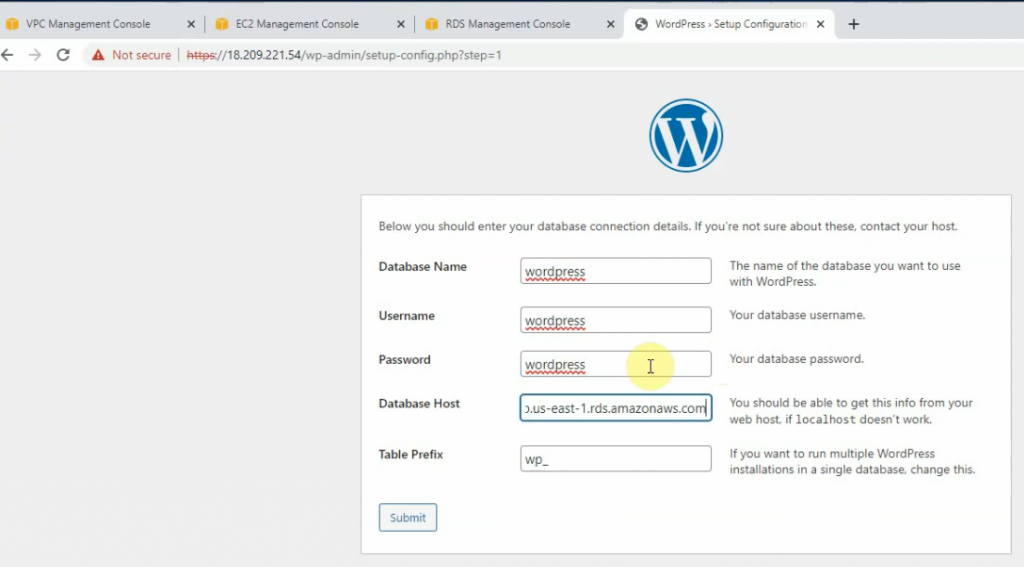
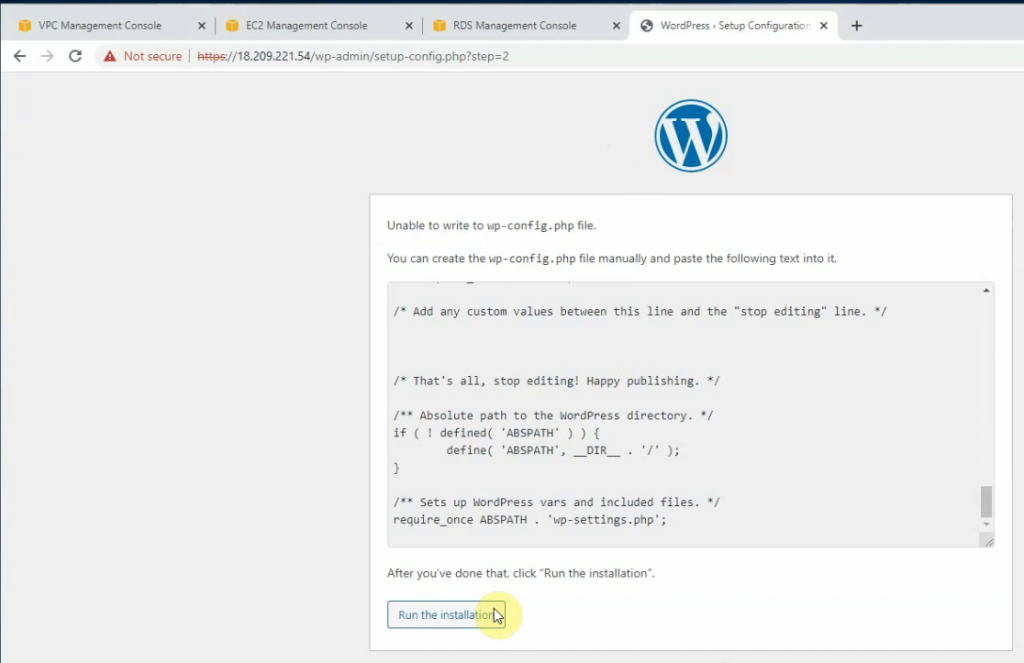
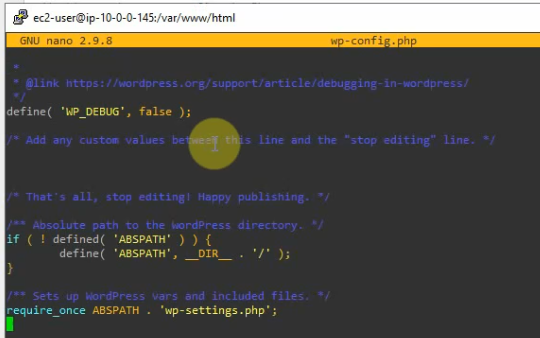
Create a new wp-config.php under /var/www/html directory, and paste the information on the screen to this file. Click “Run the installation”
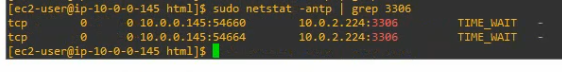
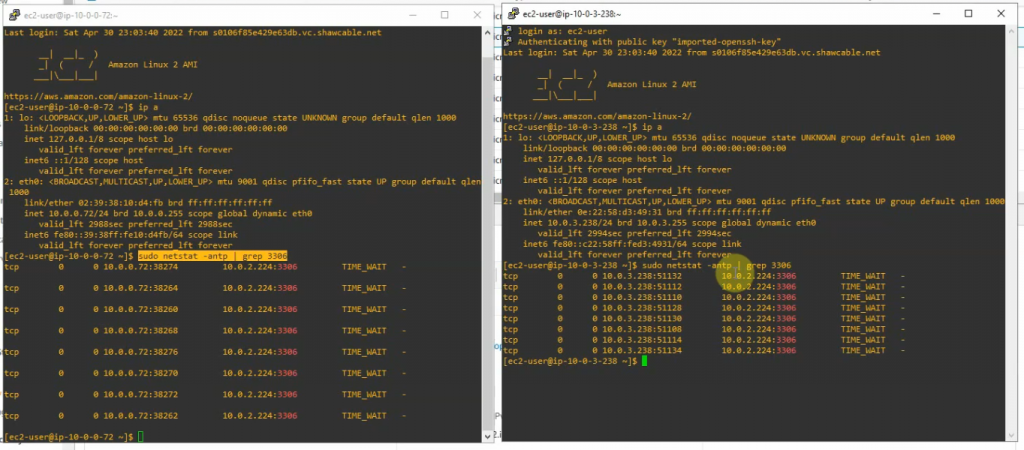
Check the connection from WP to RDS instance via the port 3306.
Create an image for the WP instance.
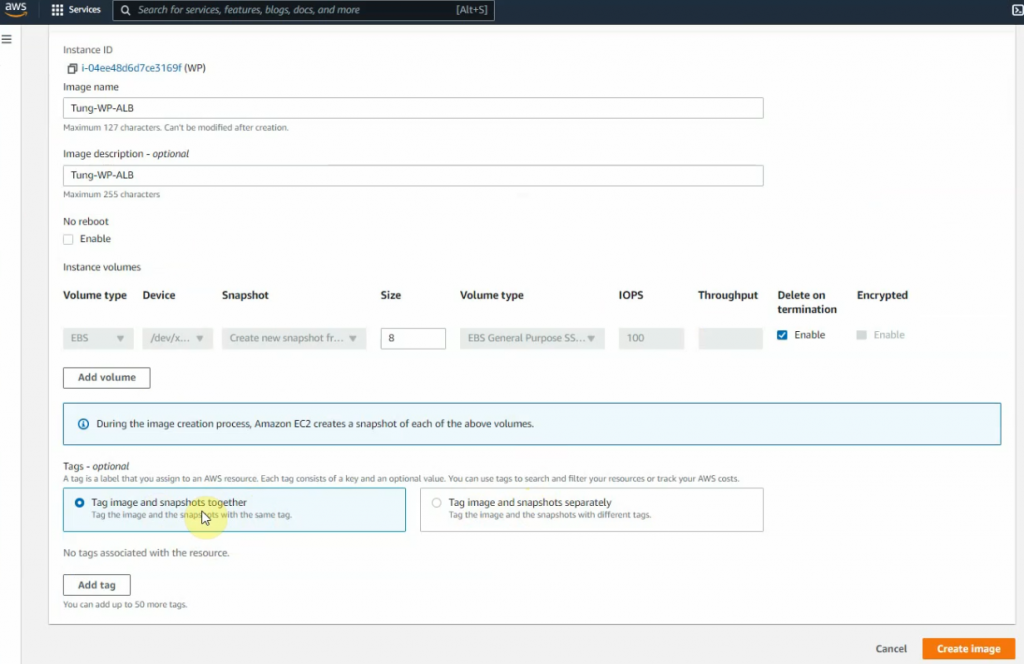
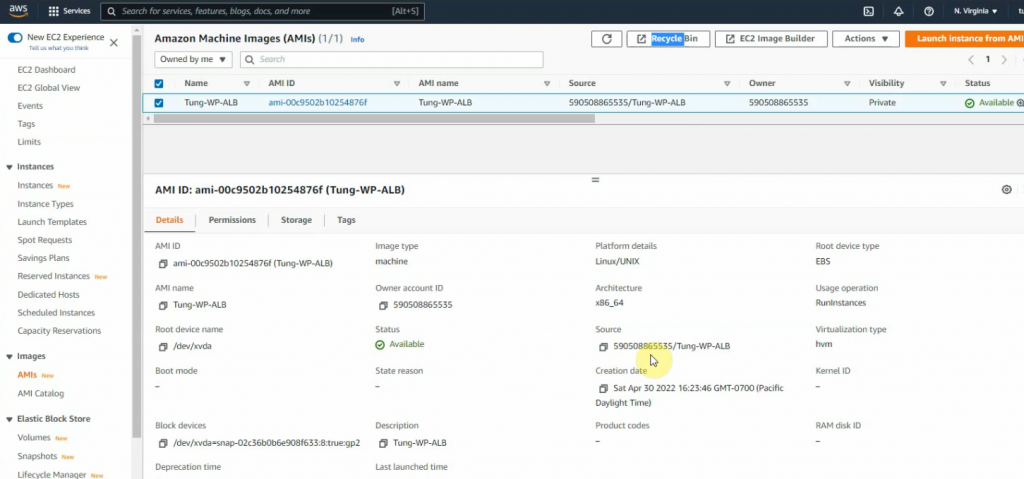
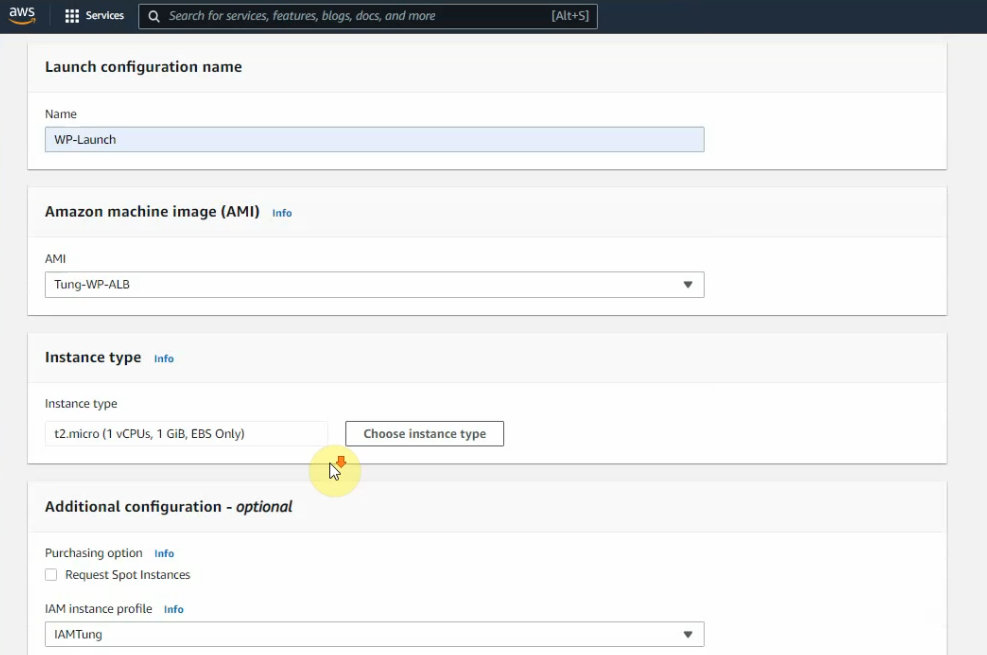
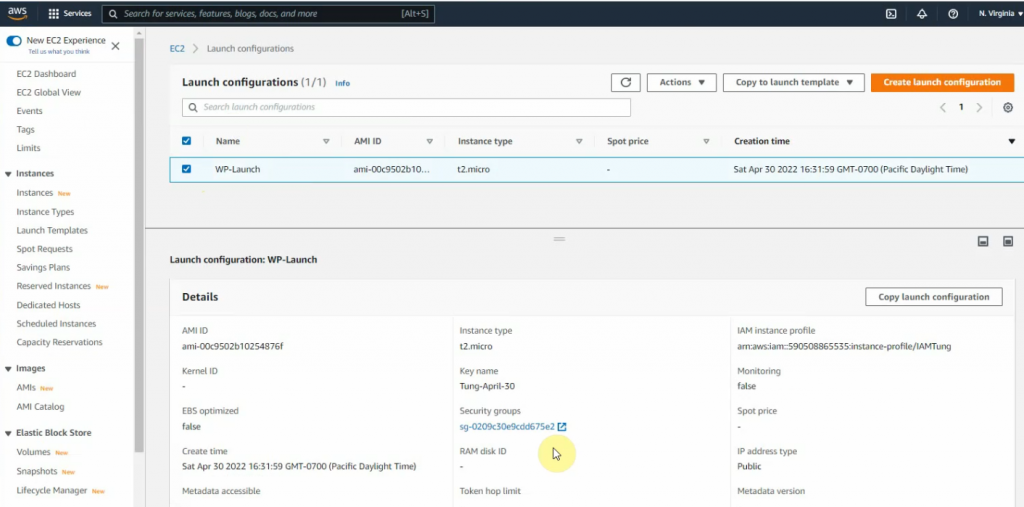
Go to launch configuration and create a launch configuration.
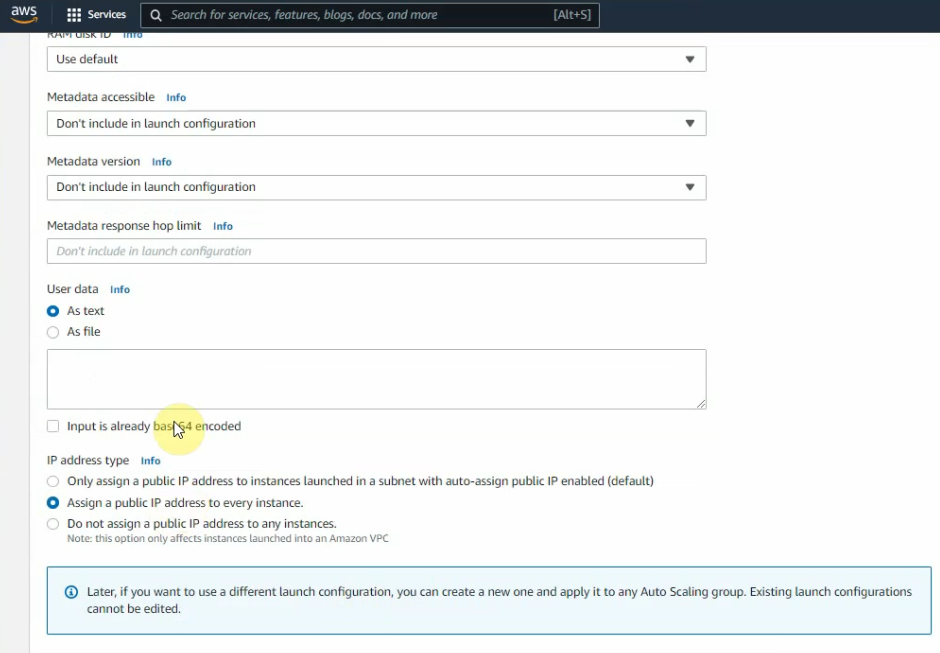
On Advanced configuration – advanced details – Select “Assign a pubic IP address to any instances”
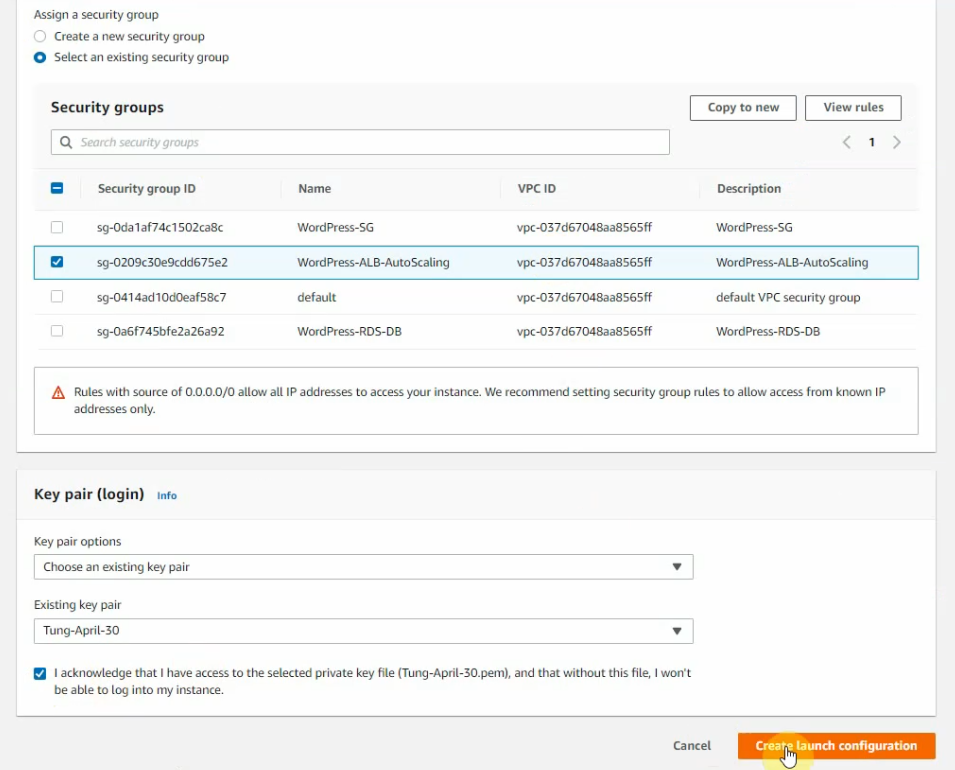
Select an existing security group. Click create a launch configuration.
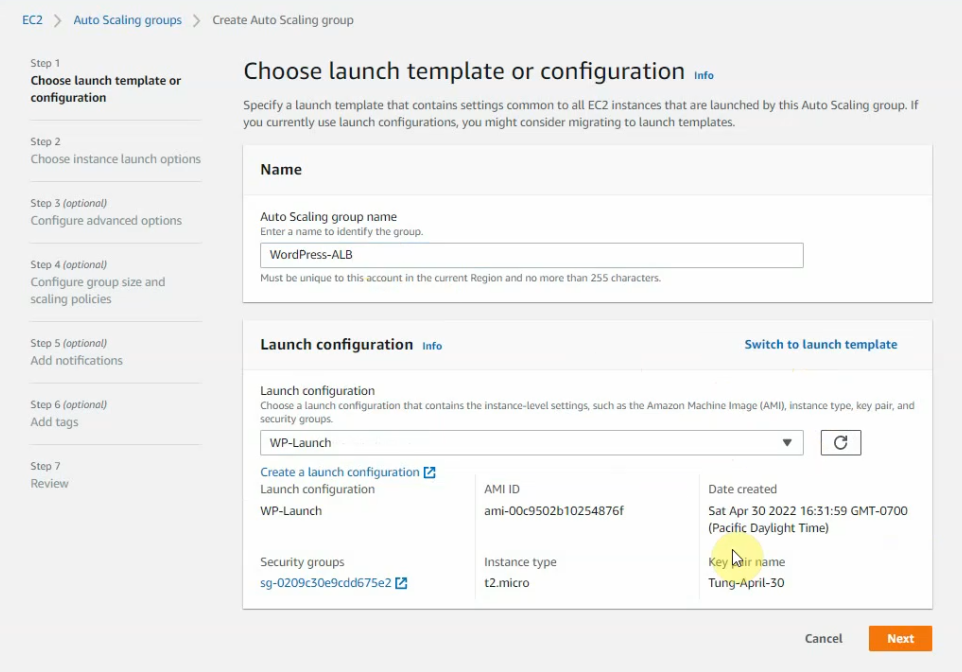
Go to Auto Scaling Group and create a new one.
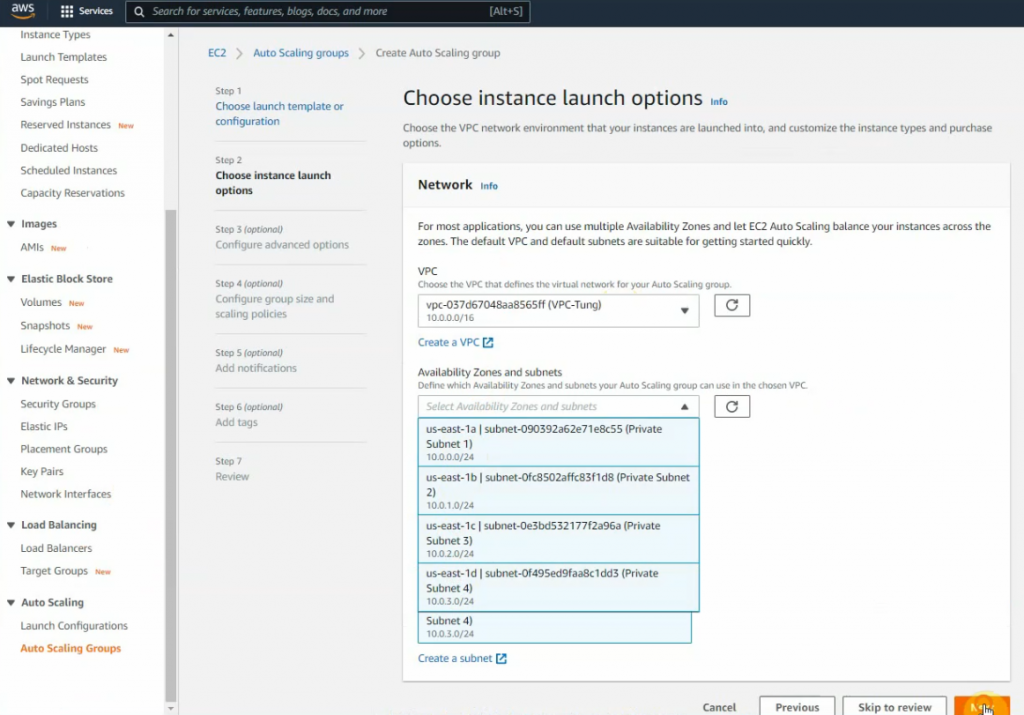
Enable “Internet-facing” on load balancing scheme.
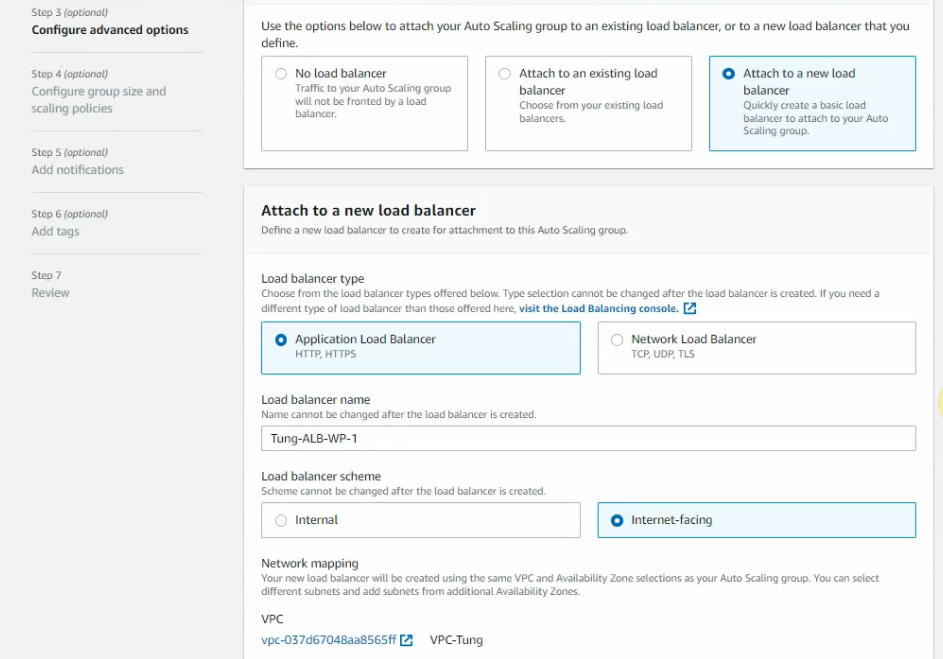
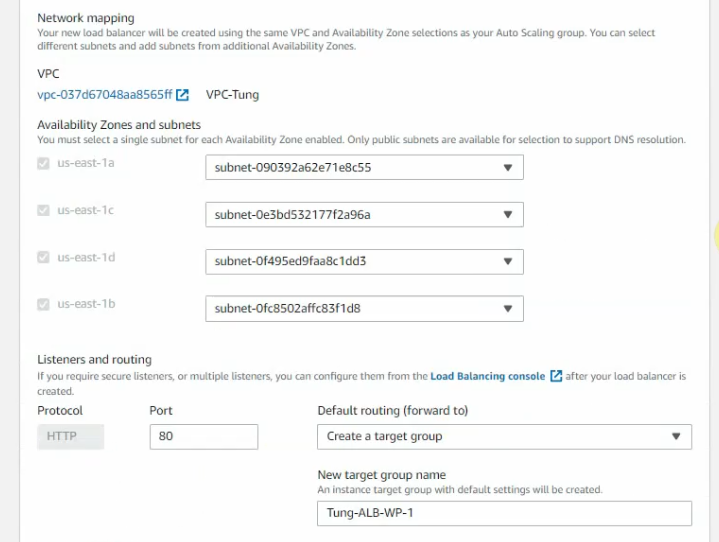
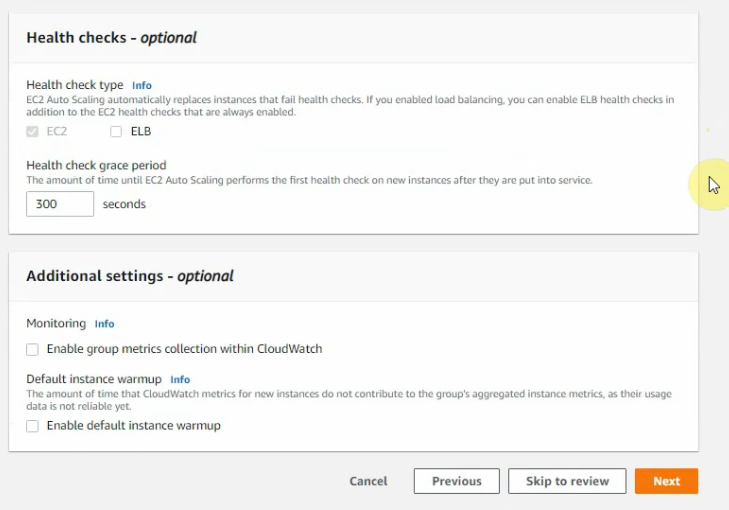
On “Configure group size and scaling policies”.
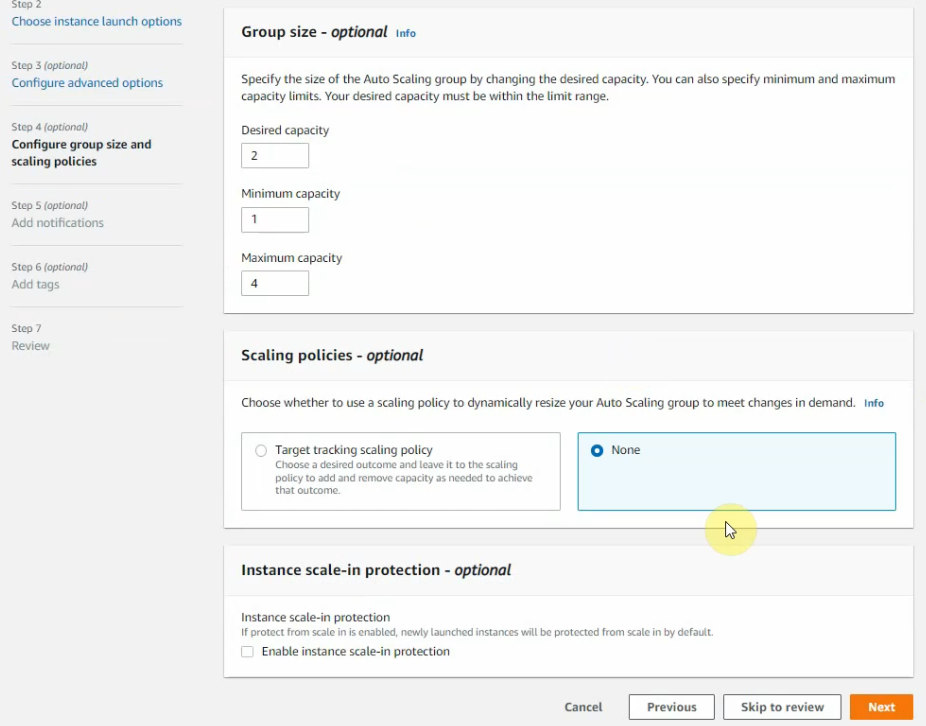
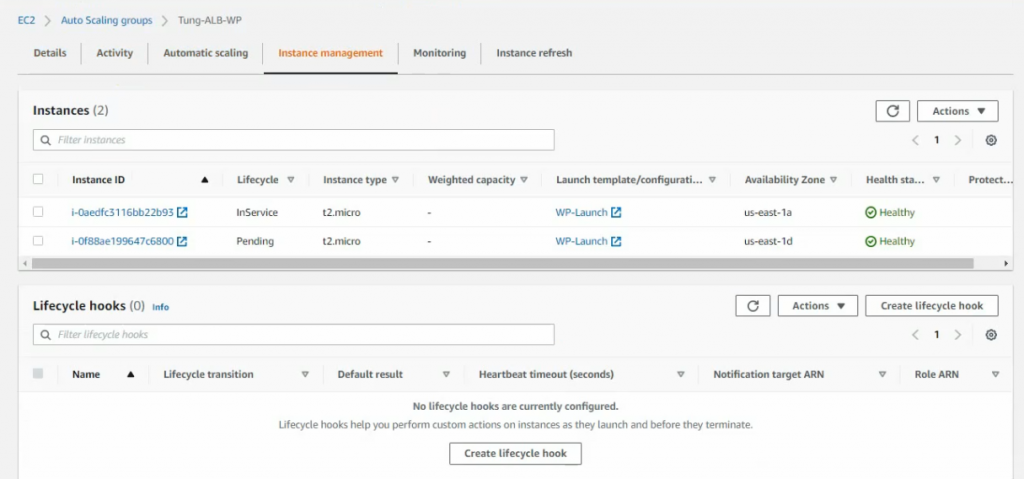
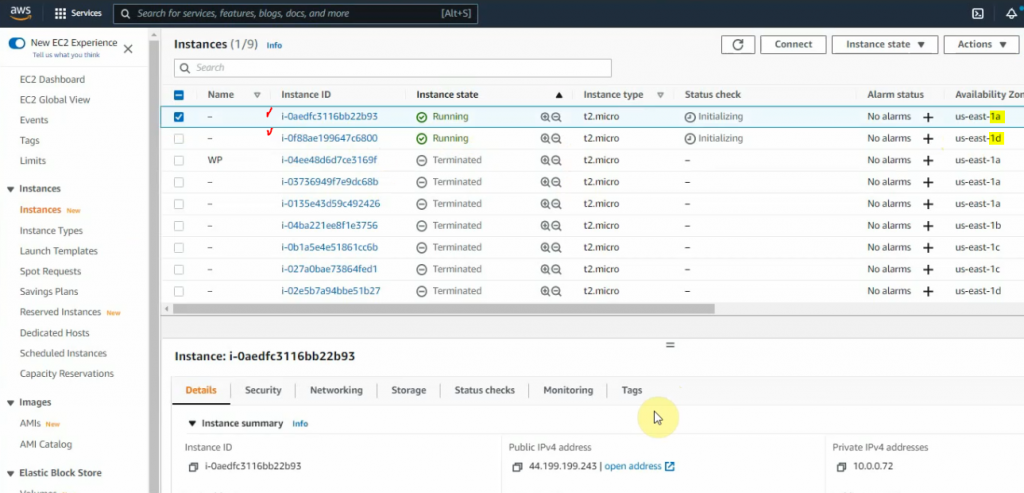
Both WP instances have been automatically created via the AutoScaling group.
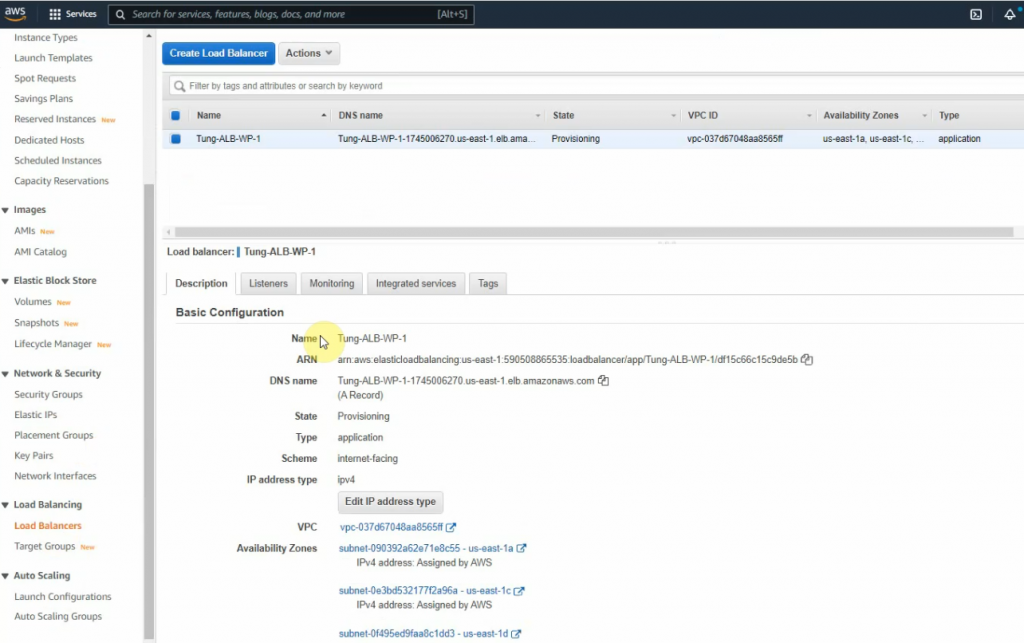
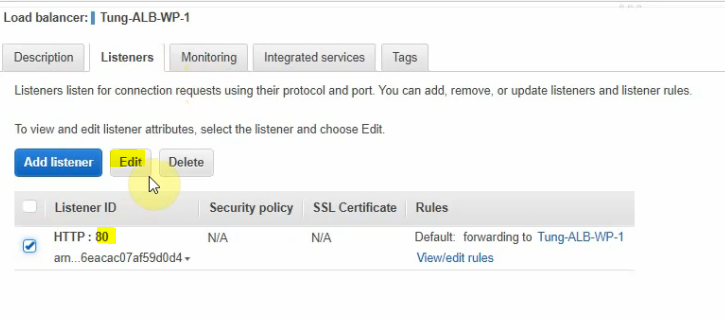
Go to the load balancer.
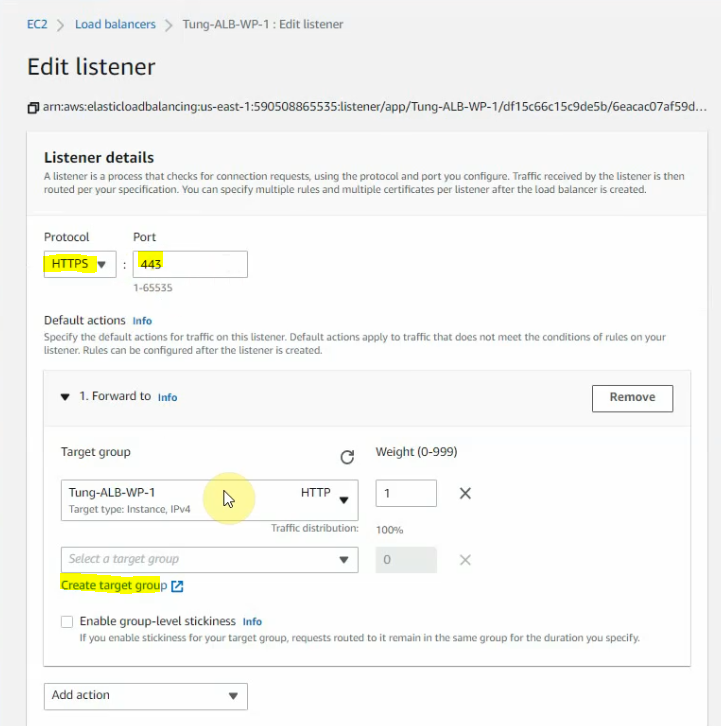
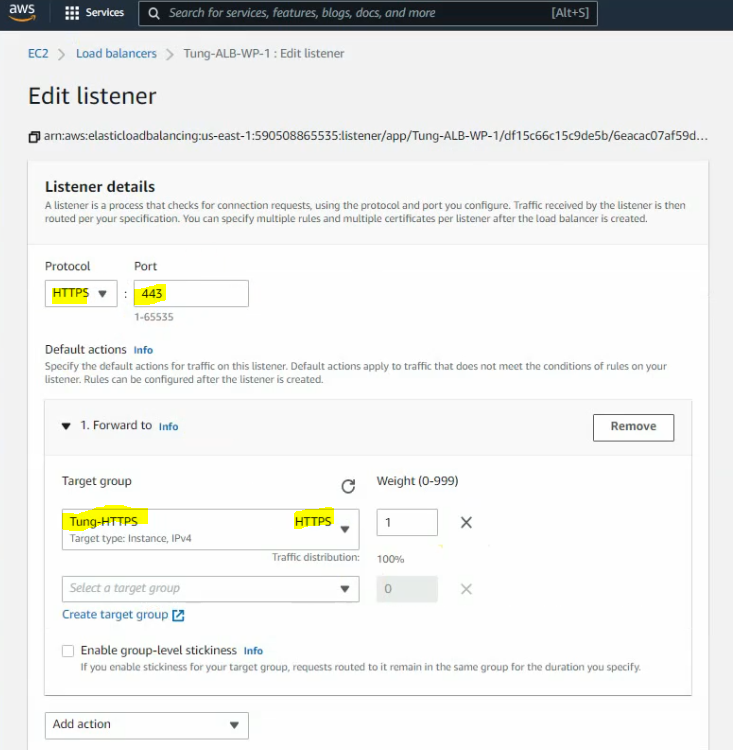
Click edit to create a new listener for port 443.
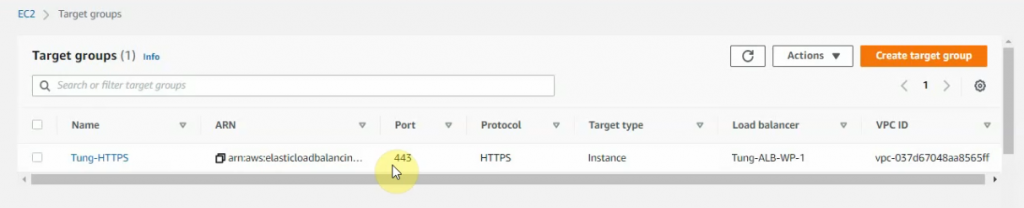
Create a new target group for HTTPS.
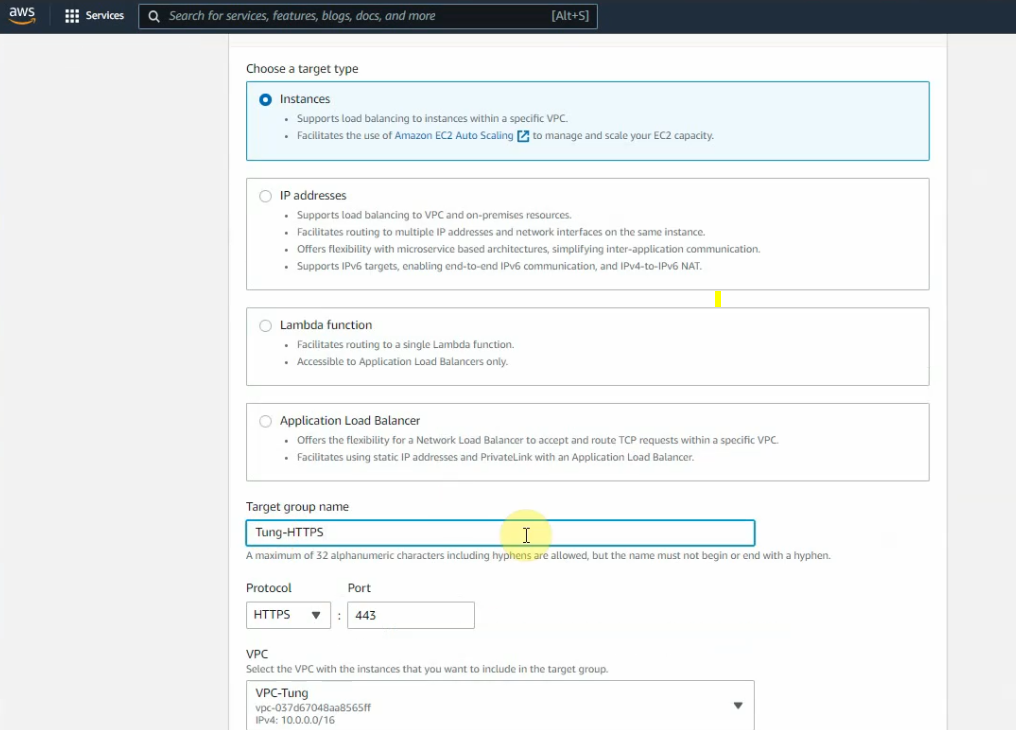
Click Next.
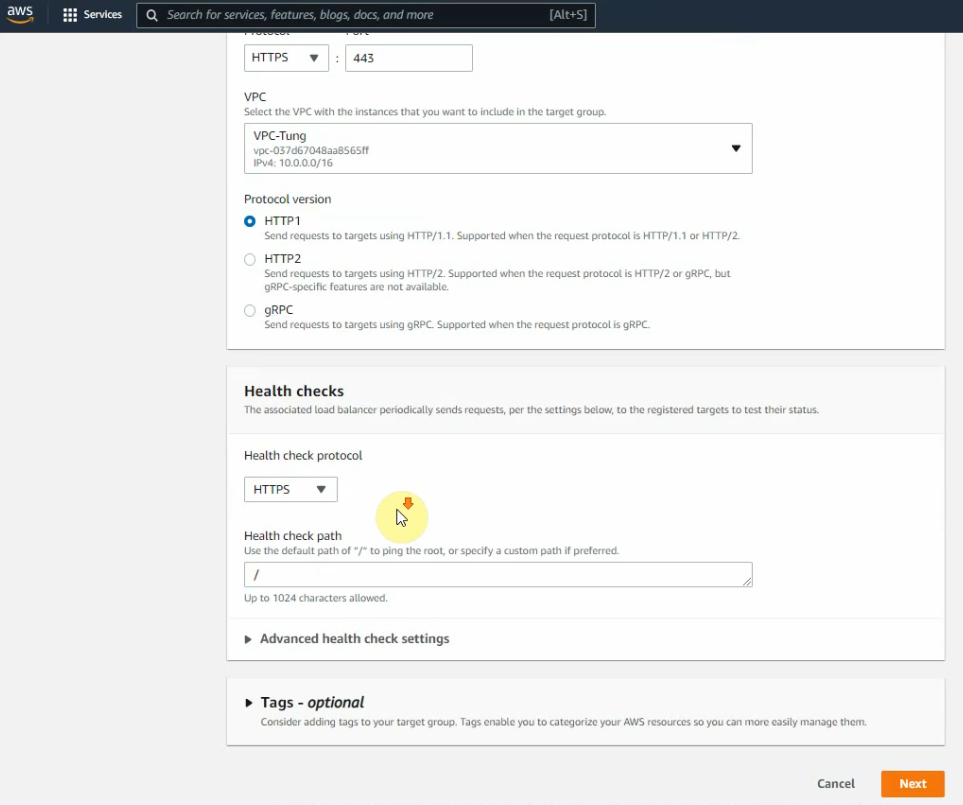
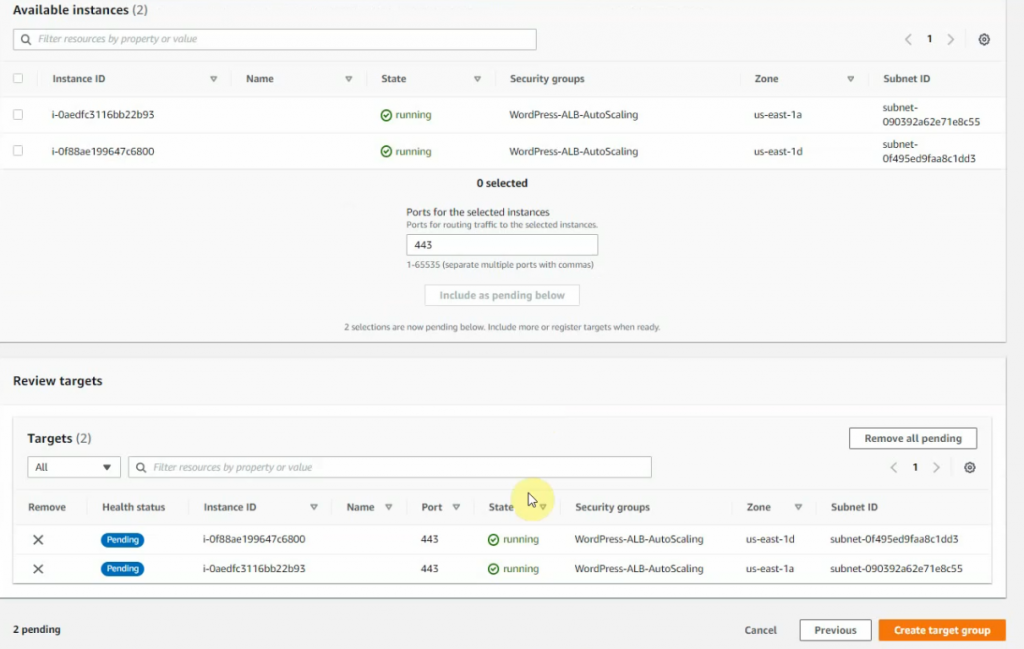
Select both instances, and select “include as pending below”. Then, click “create target group”.
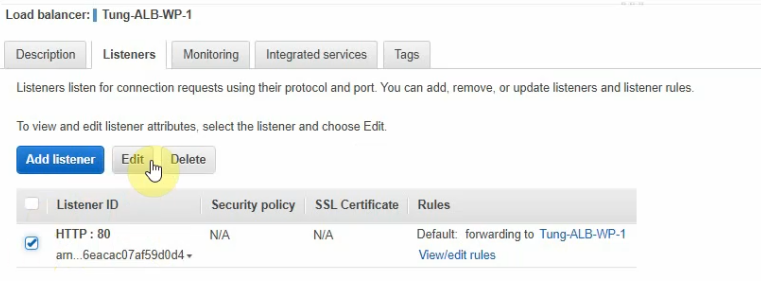
Go back and change the listener.
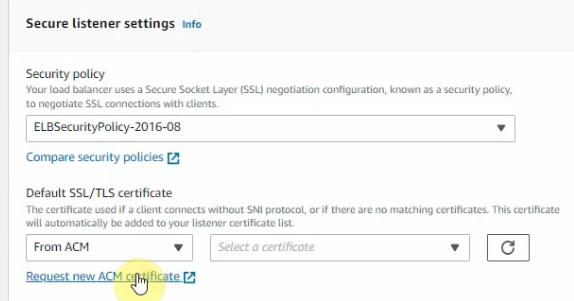
Select “Request new ACM certificate” for ALB instance.
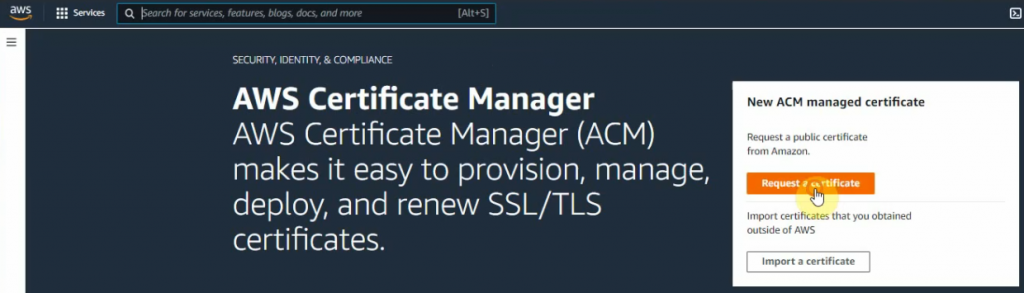
Click “Request a certificate”.
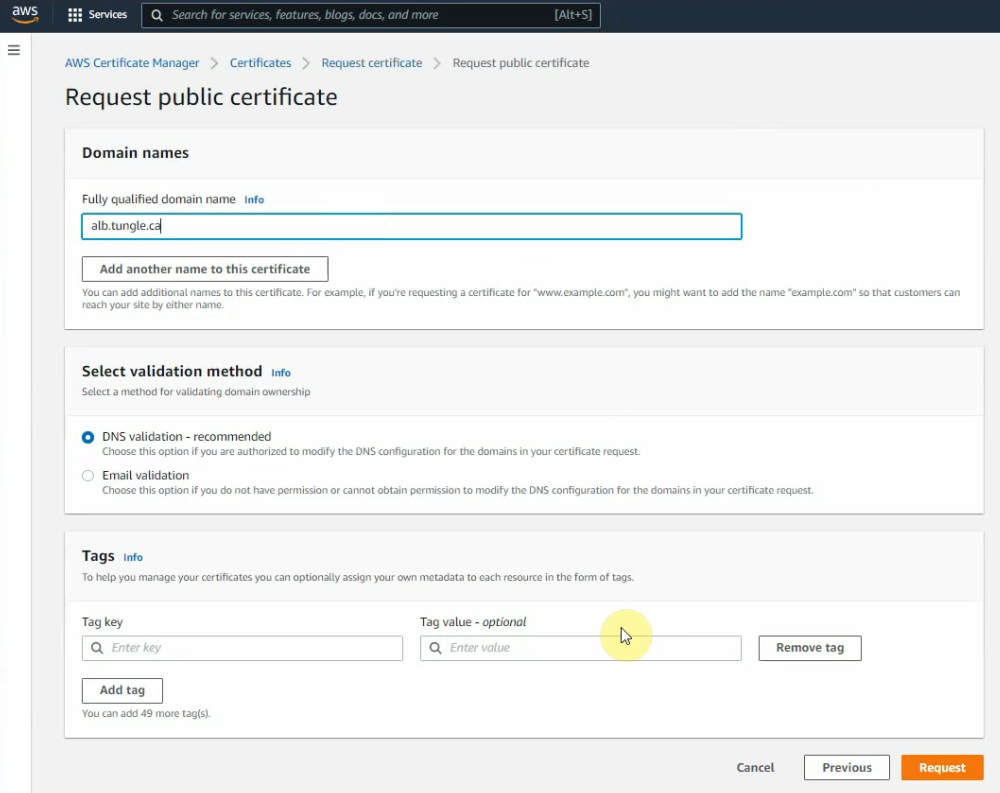
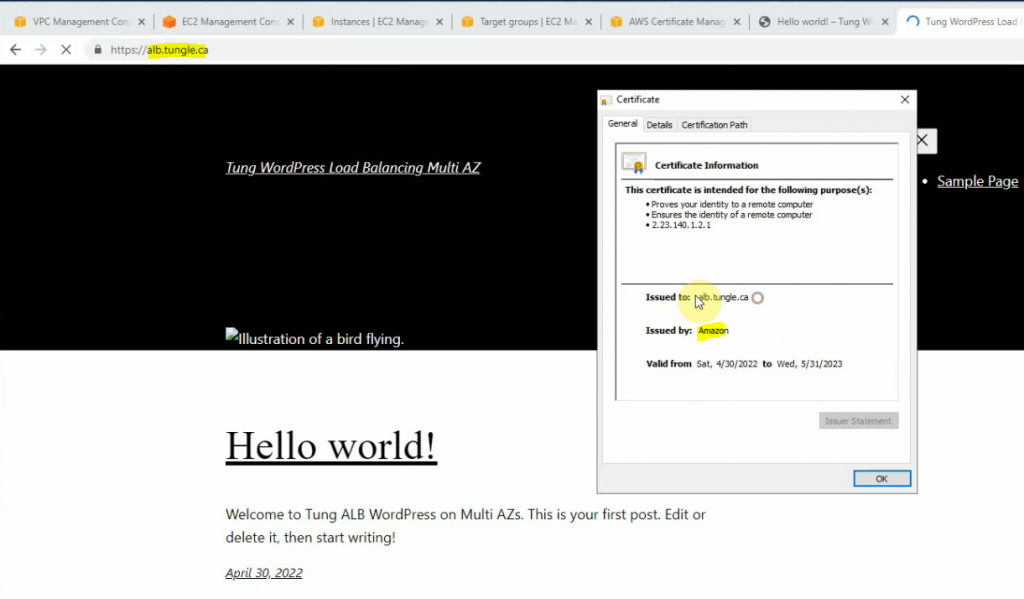
Enter your domain: alb.tungle.ca.
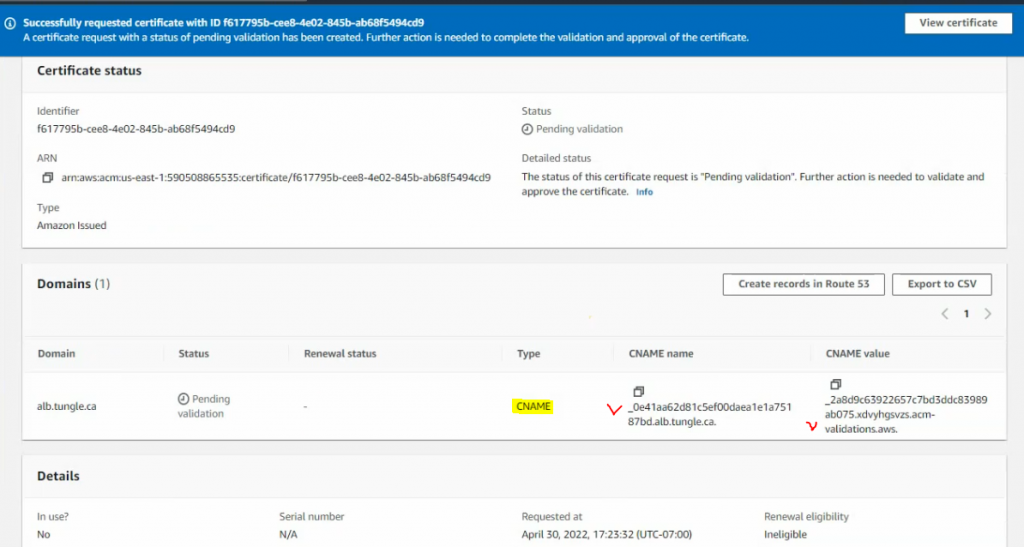
Go to your hosting DNS domain name.
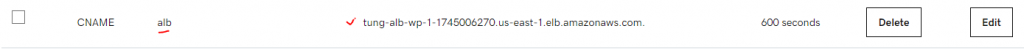
Create a CNAME record is alb with Amazon ALB domain name as a screenshot below.
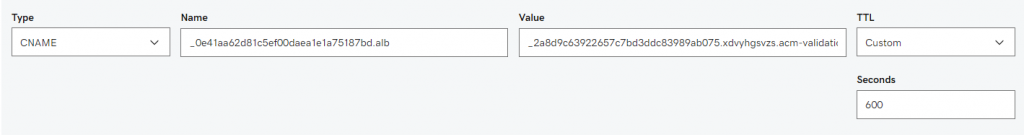
Copy and paste information on the Amazon certificate into your CNAME record.
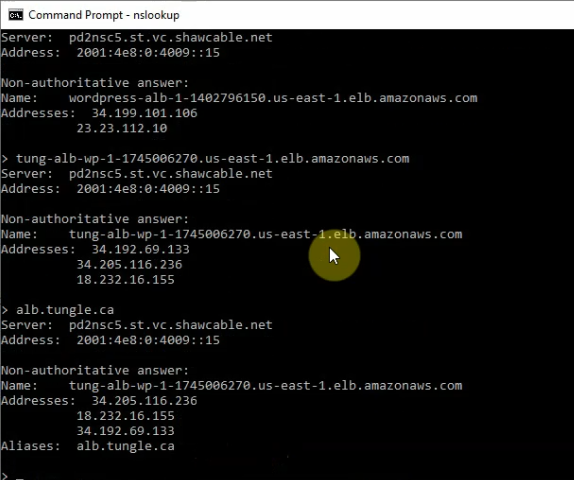
Checking domain via nslookup command.
Back to configure listener setting, and choose the certificate that has been issued from AWS.
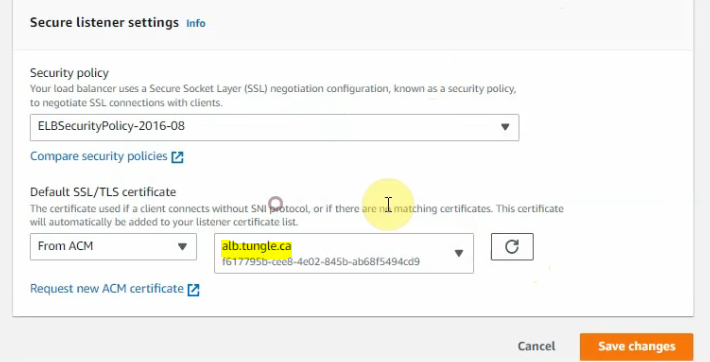
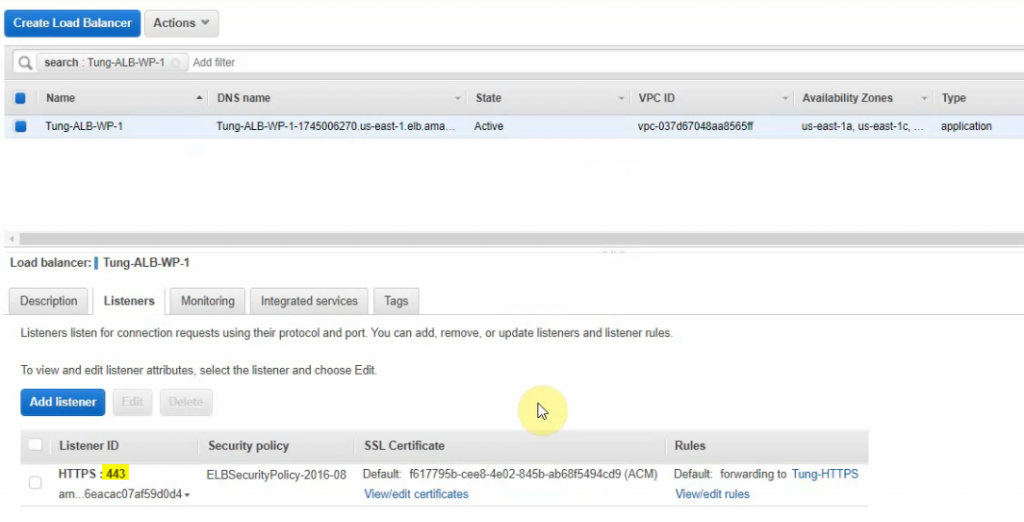
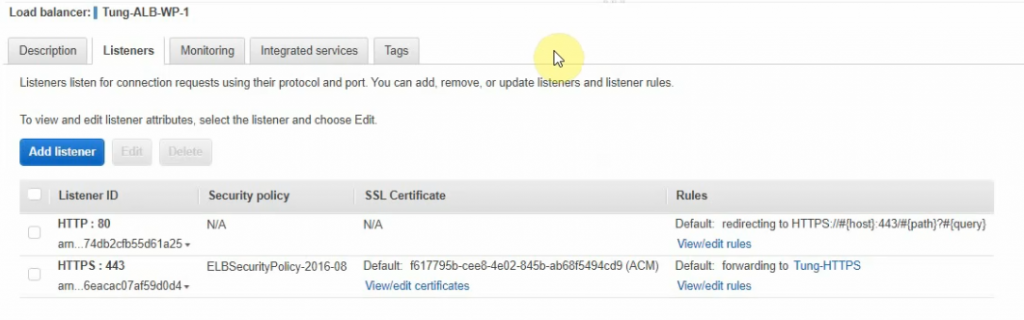
Delete the unnecessary HTTP listener.
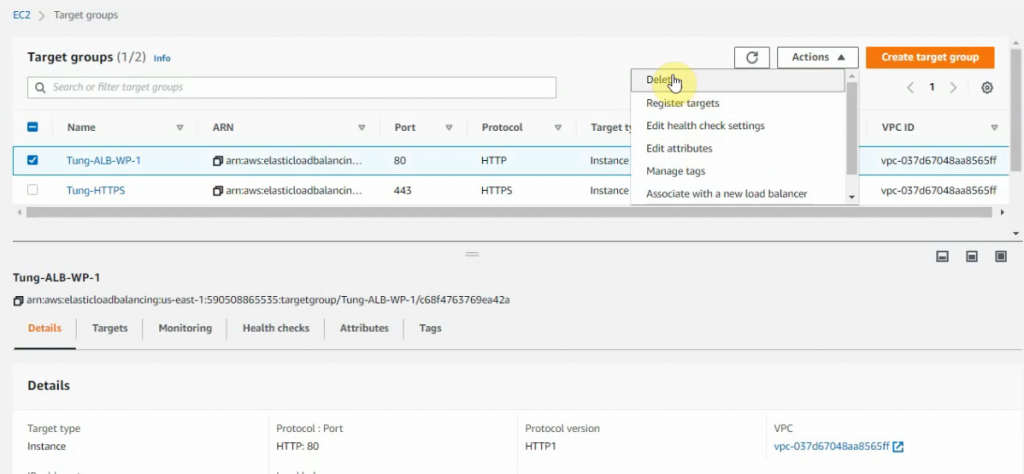
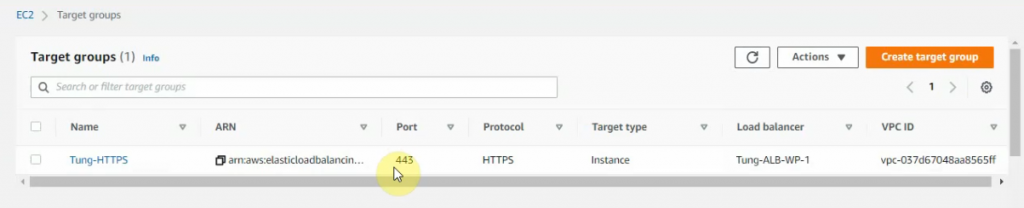
Add the new listener on ALB to redirect port 80 to port 443.
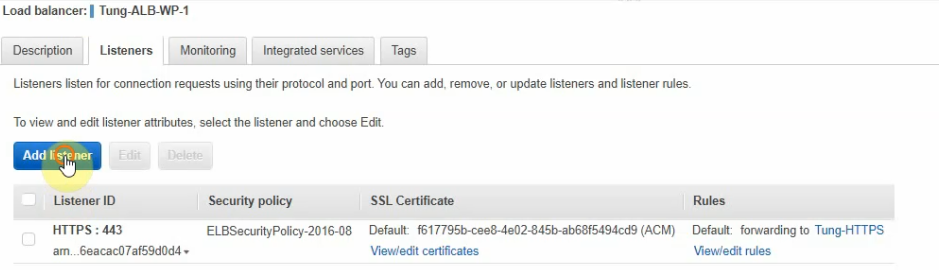
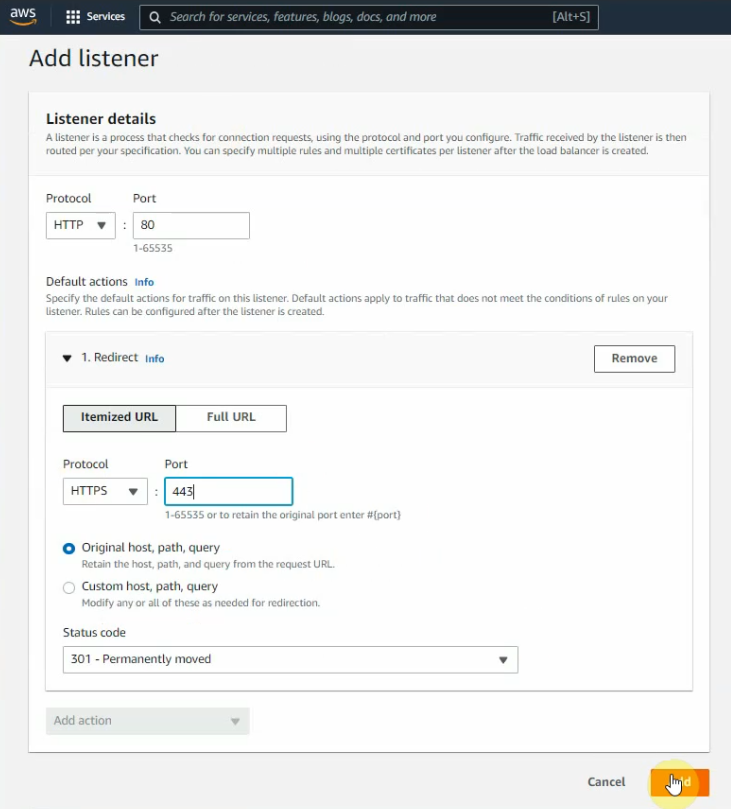
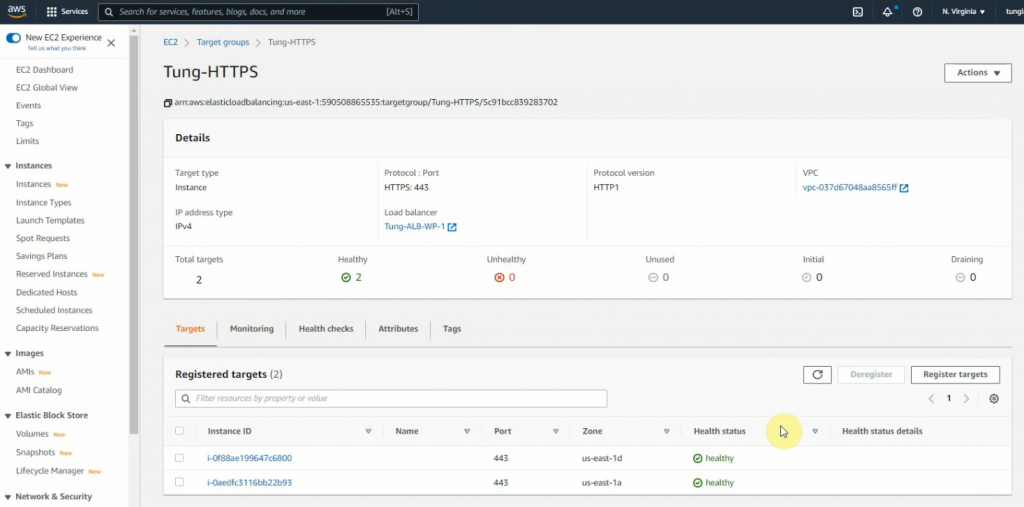
Check target groups and verify both instances have healthy status on registered targets.
Access the ALB web link on your web browser.
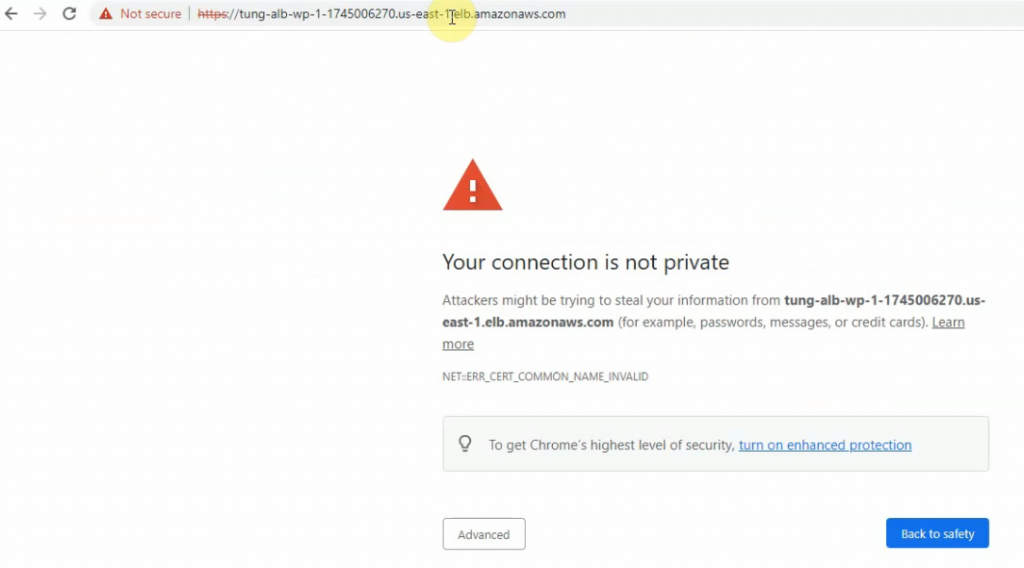
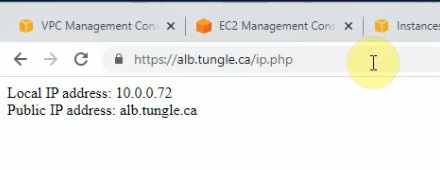
Check load balancing on both WPs.
Refresh the web link.
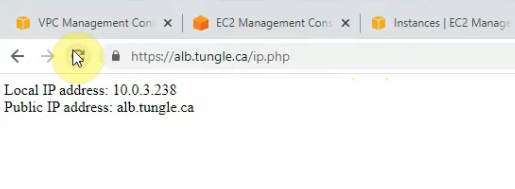
Both WPS have accessed the same RDS instance (the master) on the IP address 10.0.2.224.
Go to Amazon CloudFront to create CloudFront distribution.
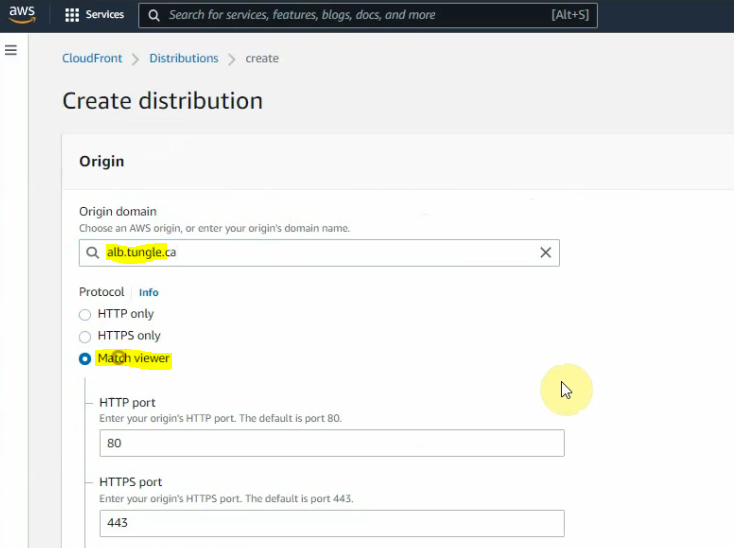
Enter your domain on the origin domain.
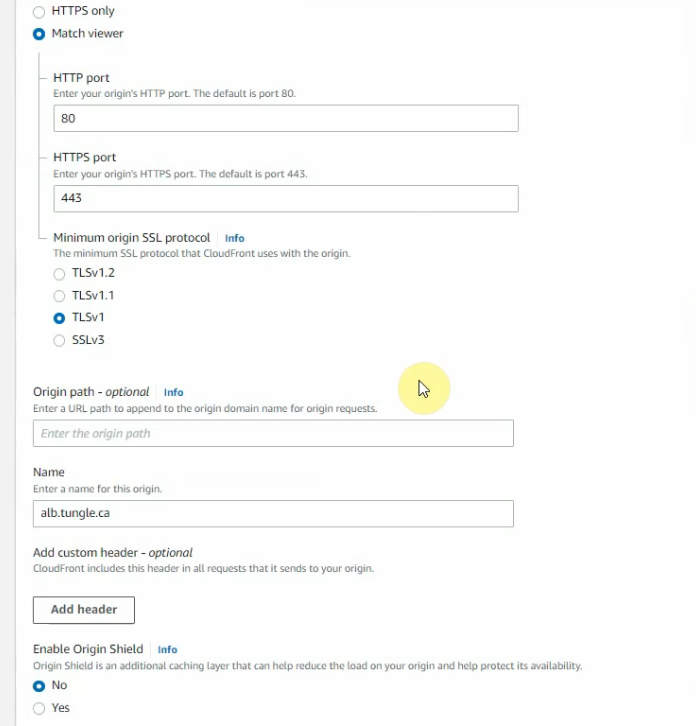
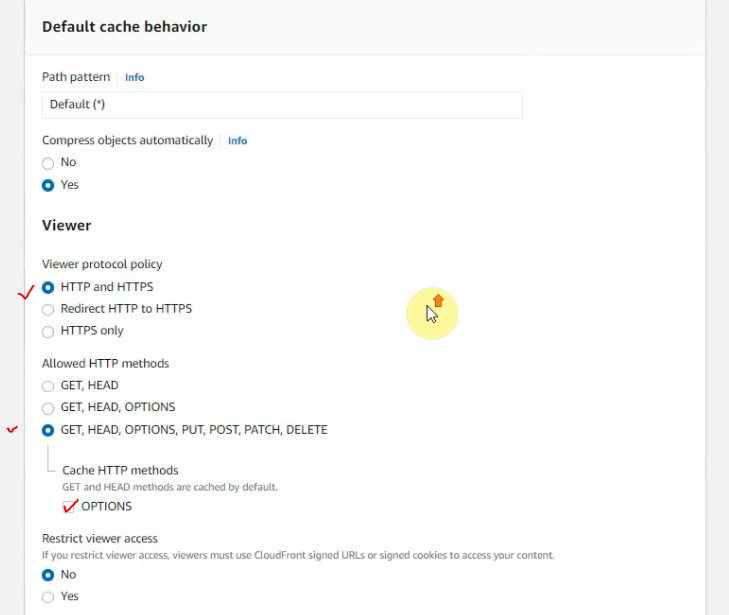
Select your certificate on “the custom SSL certificate”.
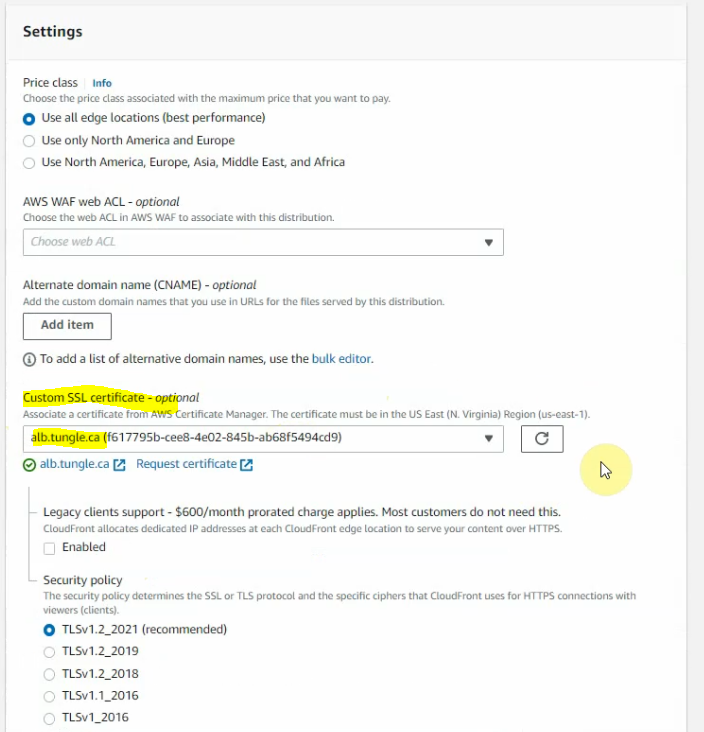
Leave the other settings default, then click Create distribution.
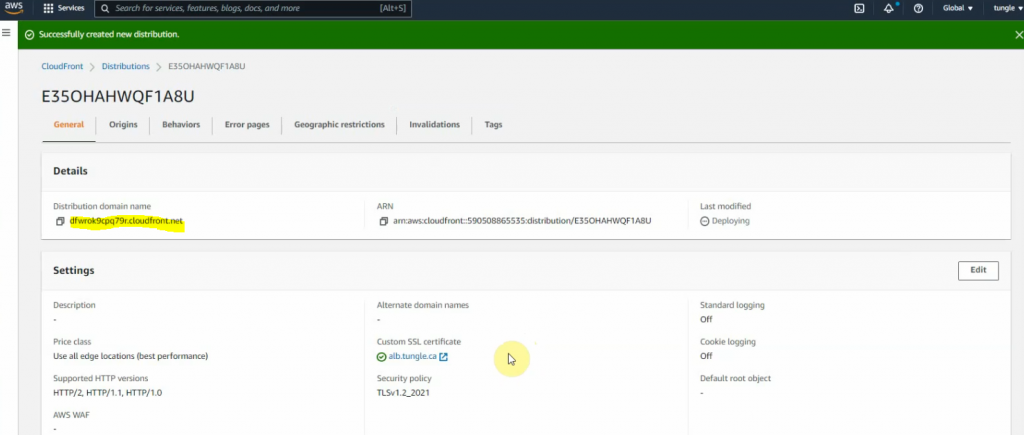

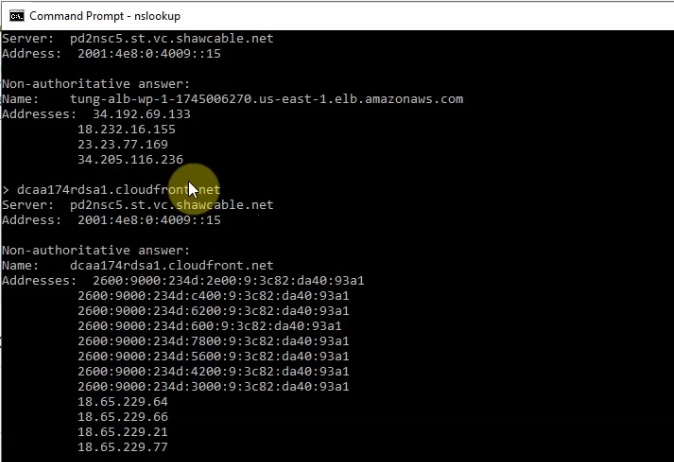
Access your CloudFront domain.


