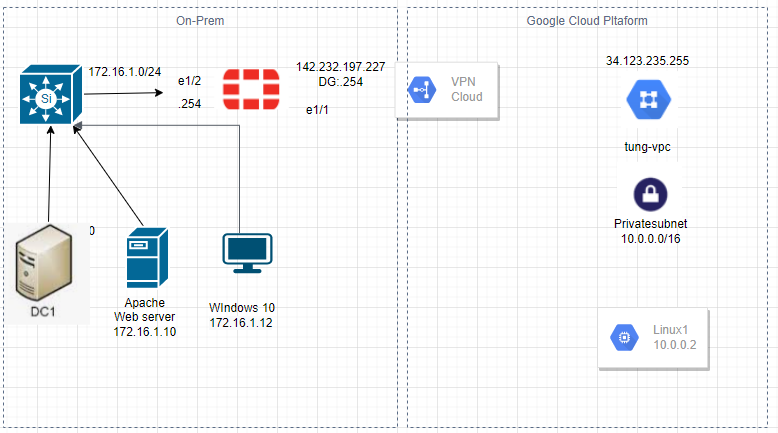
This is a diagram that I have used for the lab.
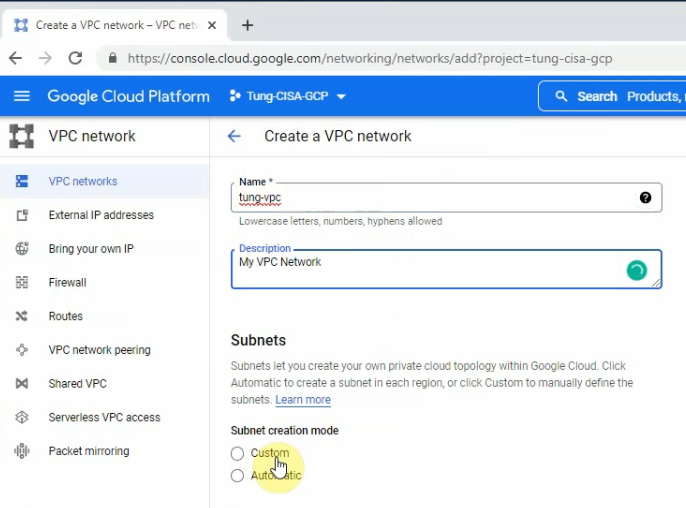
Create a new VPC network on GCP.
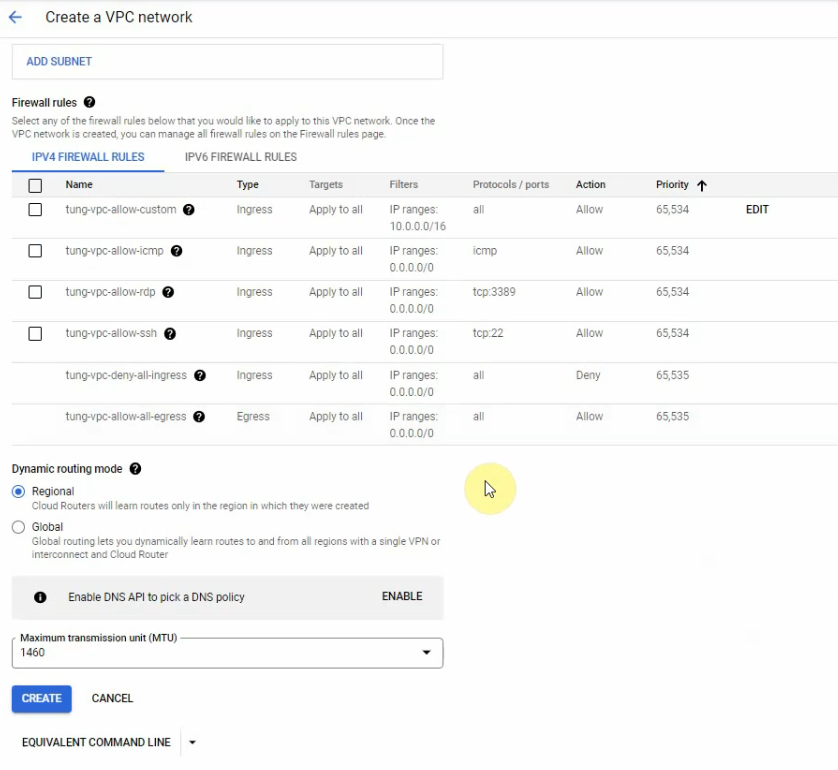
Search VPN keyword on the search function.
Click “Create VPN connection”.
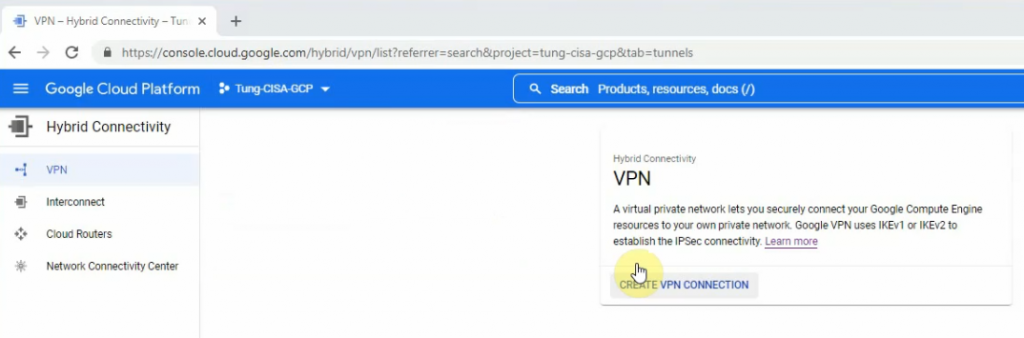
Select Classic VPN.
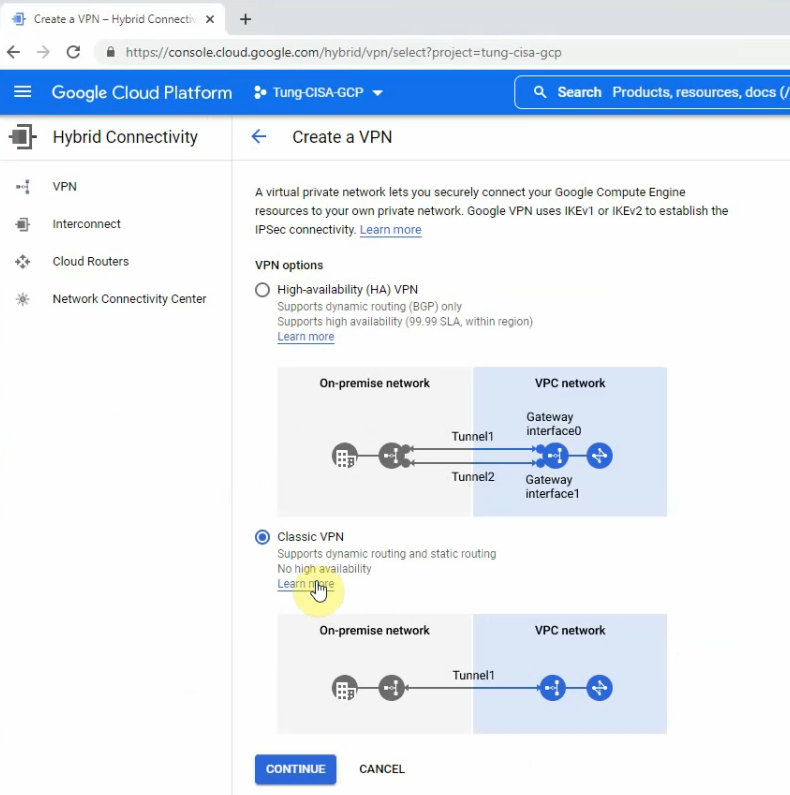
Select tung-vpc on the network setting.
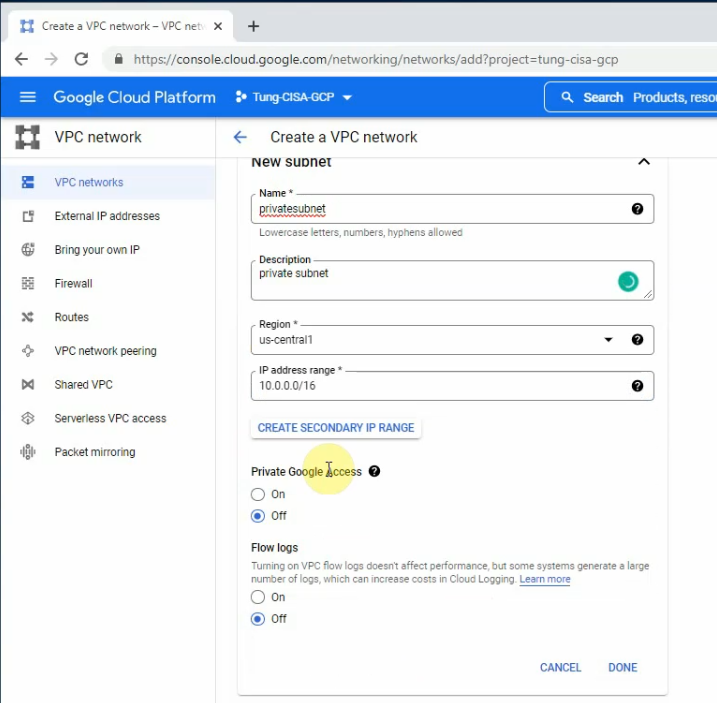
Create a new static IP address for your VPC.
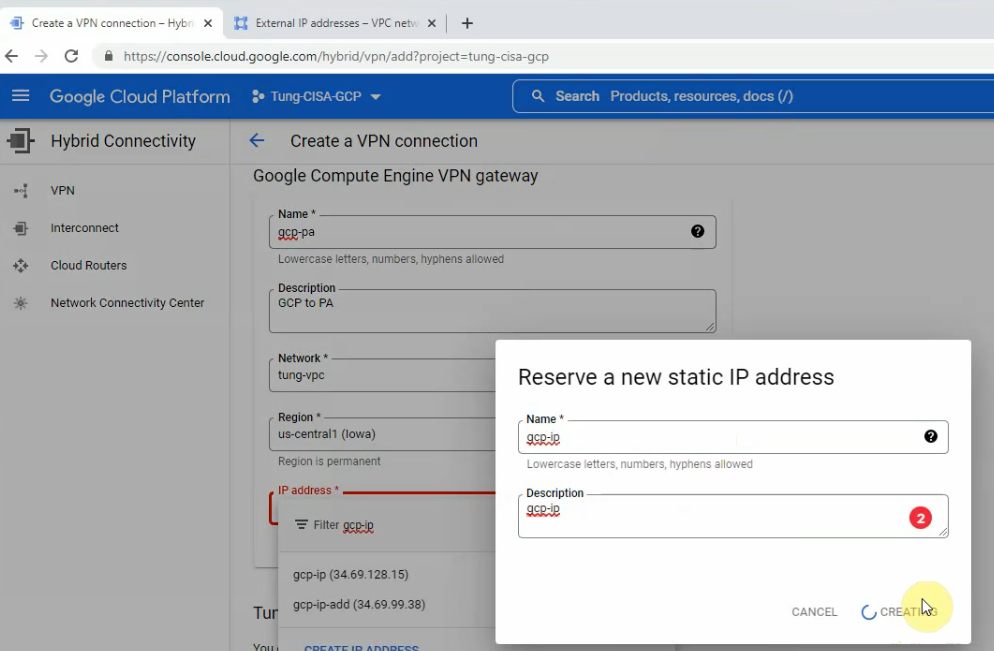
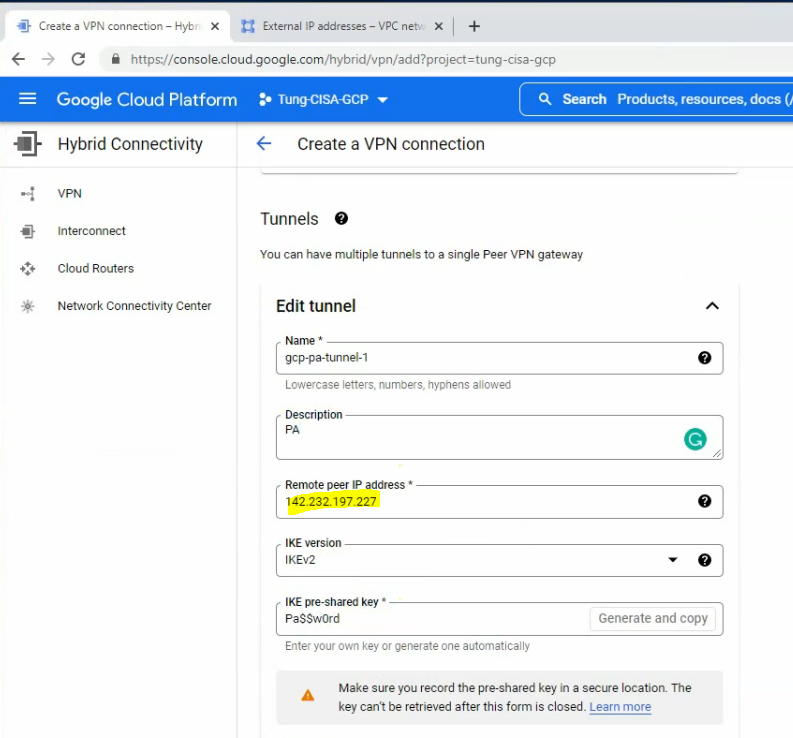
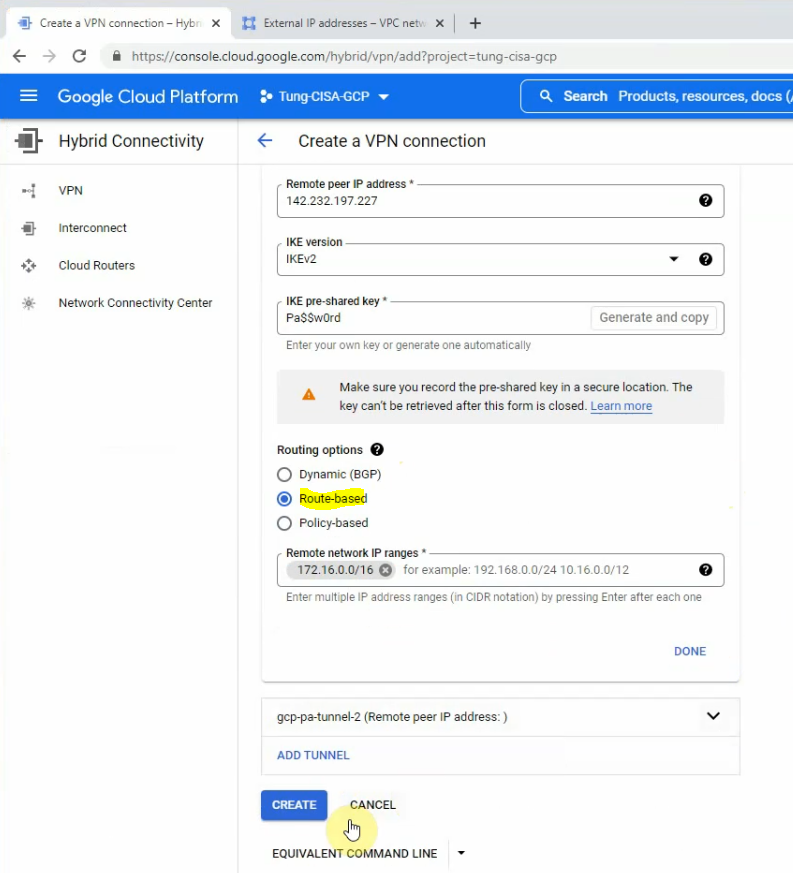
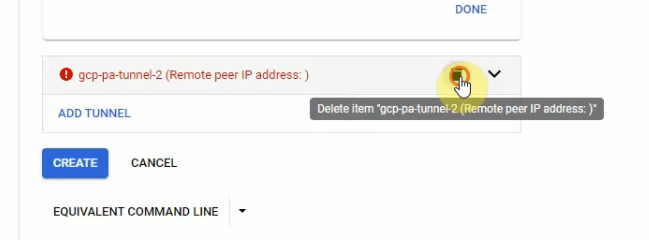
Delete tunnel 2 because I have only used tunnel 1 in this lab. Then click Create.
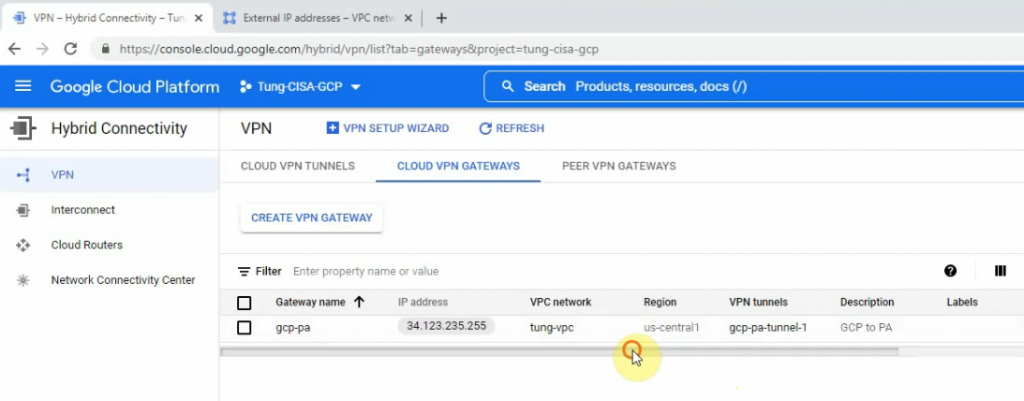
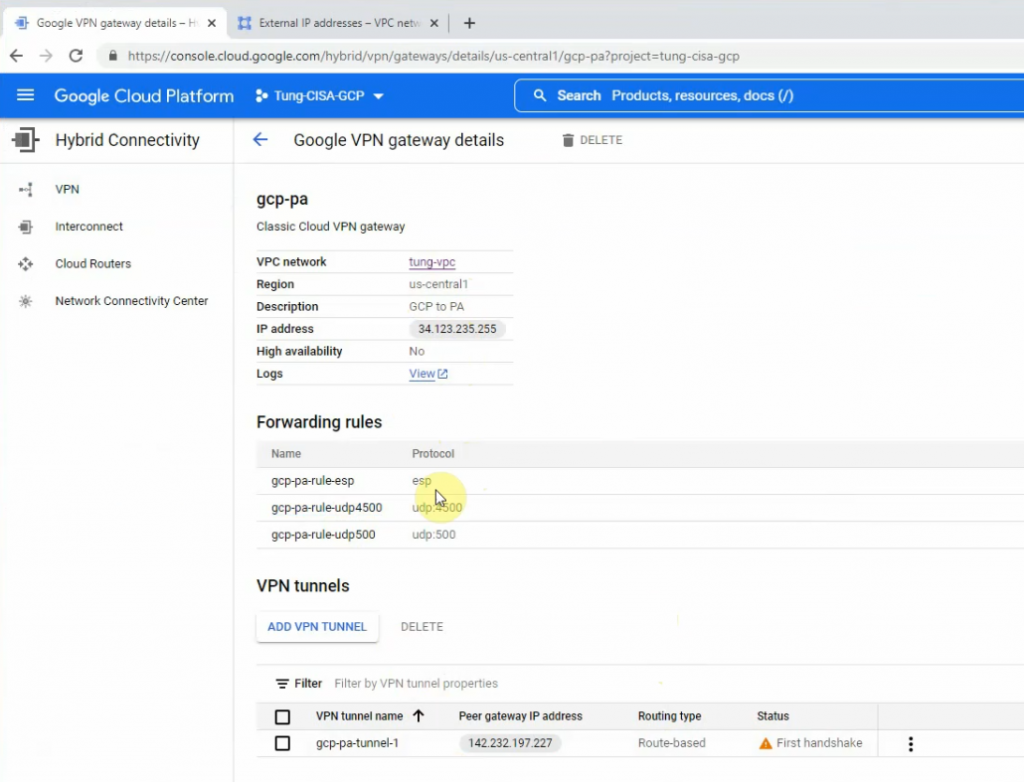
Click gpc-pa-tunnel-1.
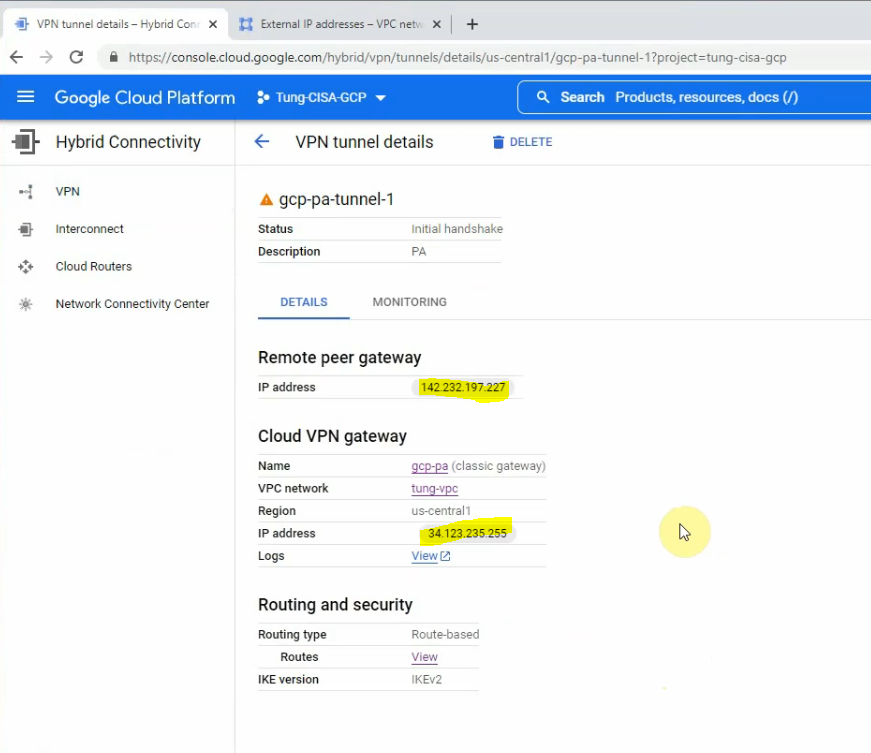
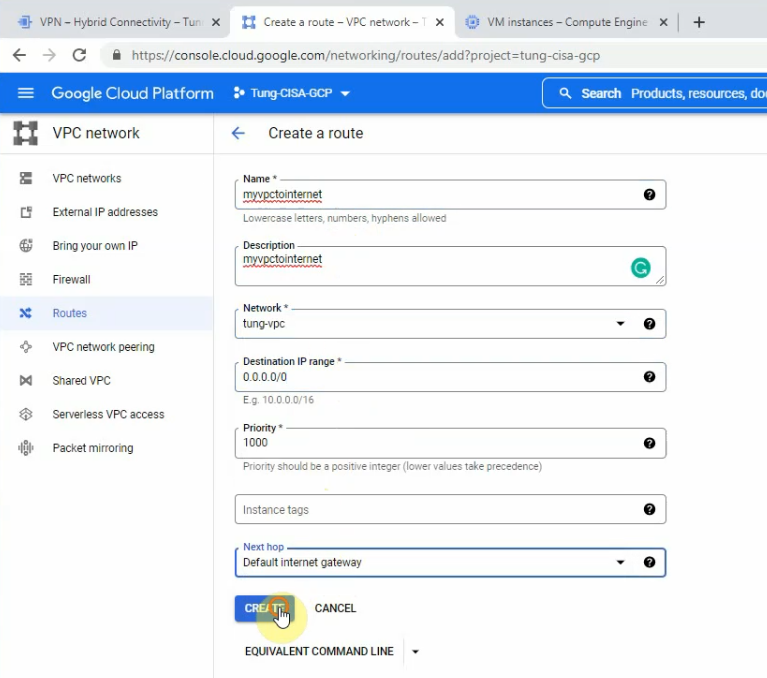
Edit the Routes to allow traffic from my tung-vpc network to the Internet via the Default Internet gateway.
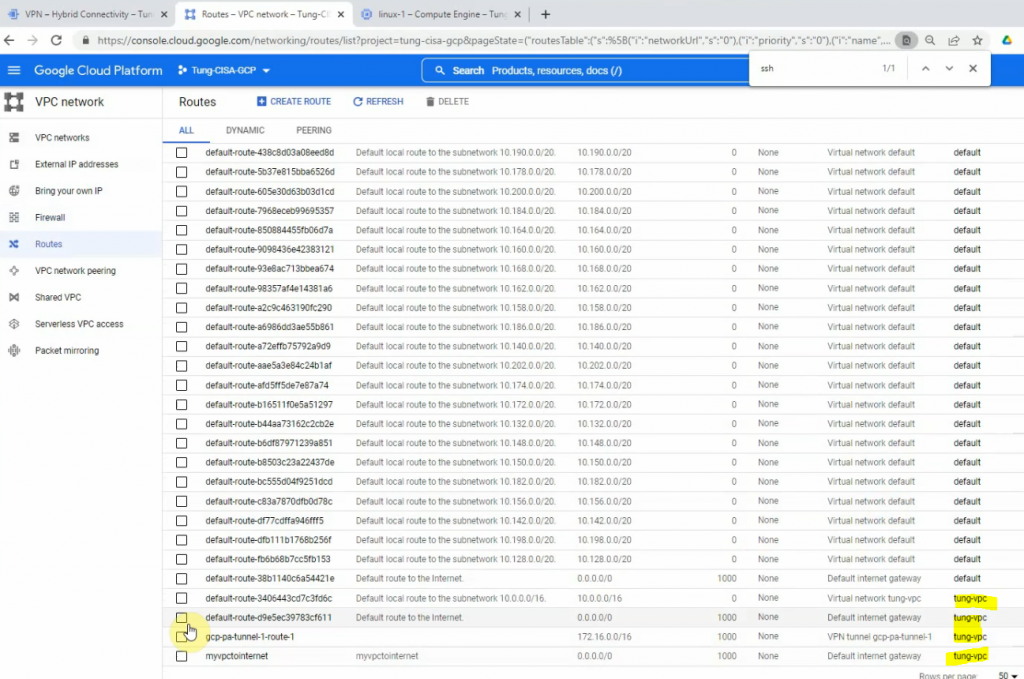
We can see the static route from privatesubnet on GCP to the LAN subnets on Palo Alto has been created on the Routes section.
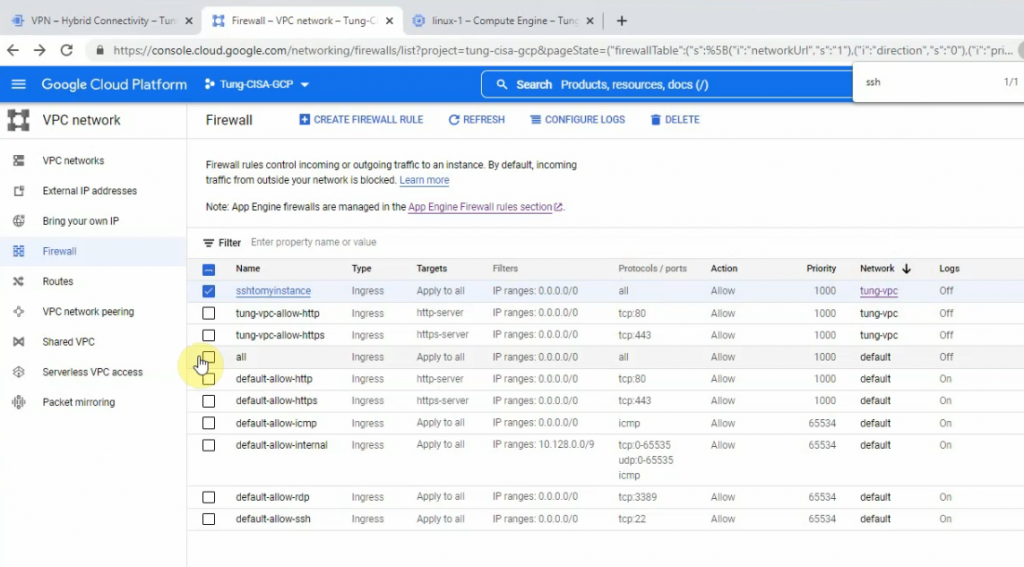
Check the Firewall and allow SSH from the Internet to Linux instance on the “privatesubnet”.
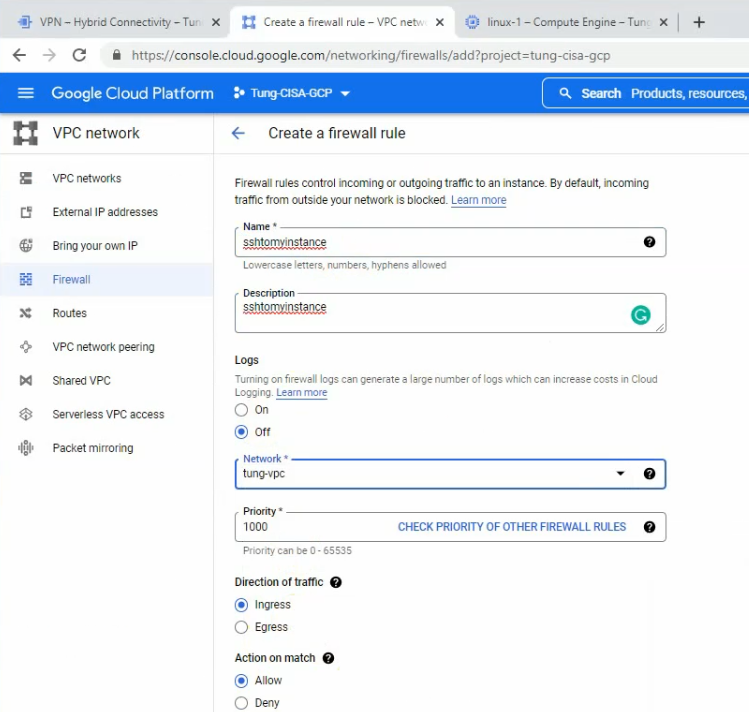
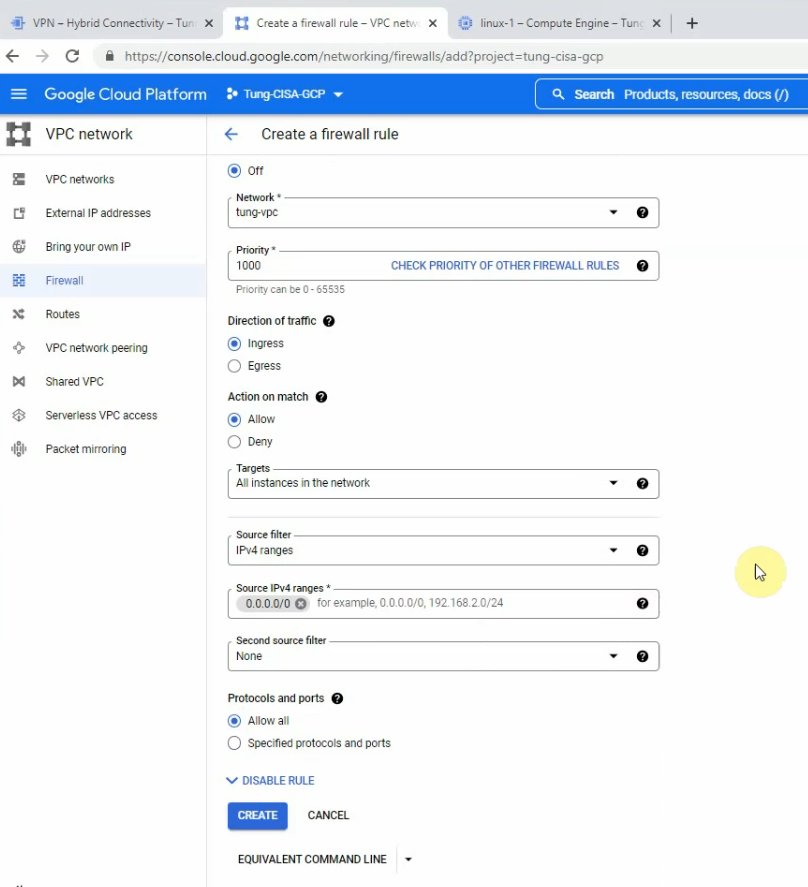
I have used “Allow all” to allow SSH from the Internet to Linux instance, We are able to change to only allow SSH protocol or port 22. Click Create.
Search “compute engine”, and click create an instance.
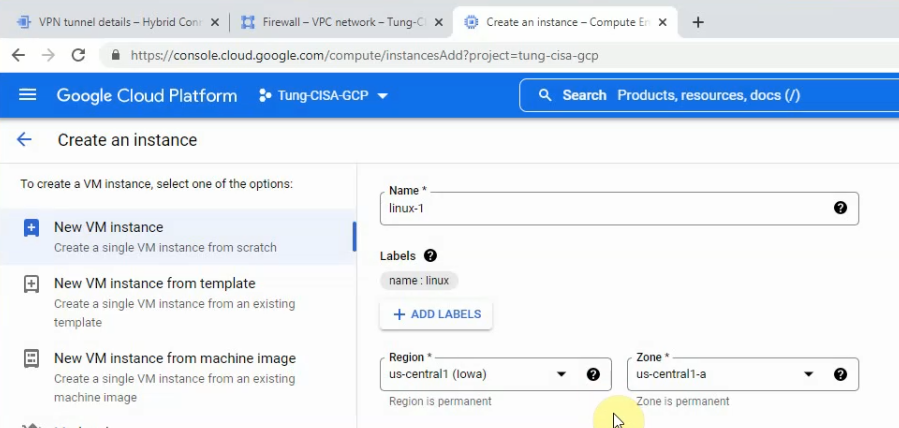
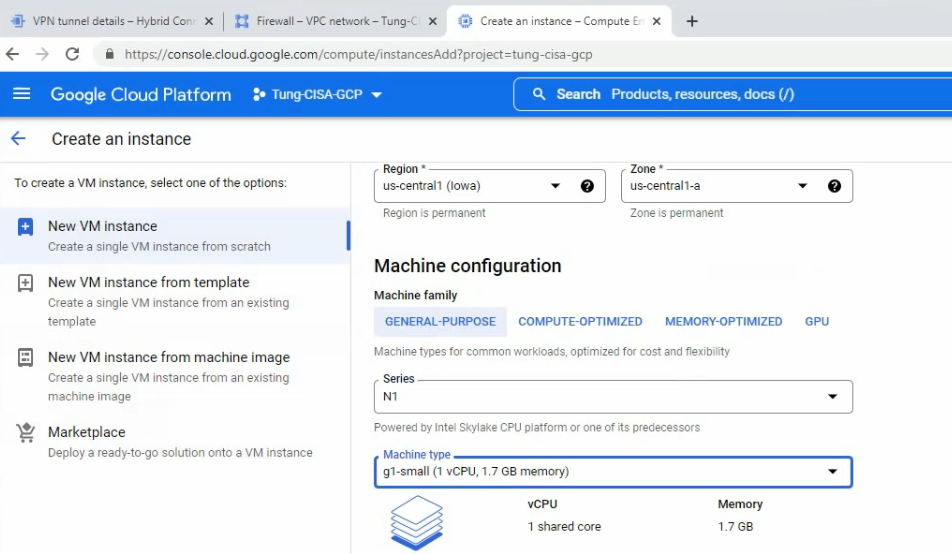
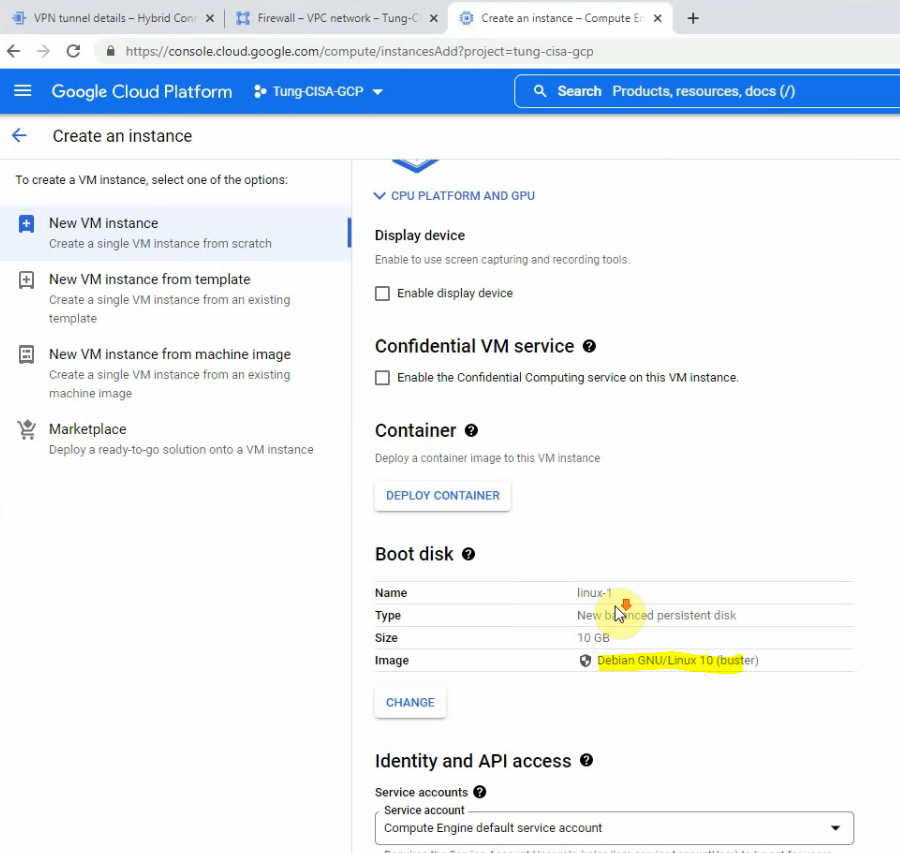
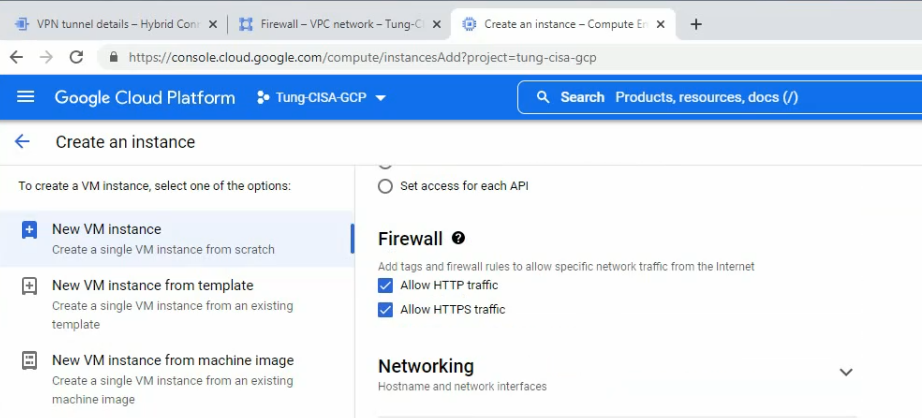
On network interfaces.
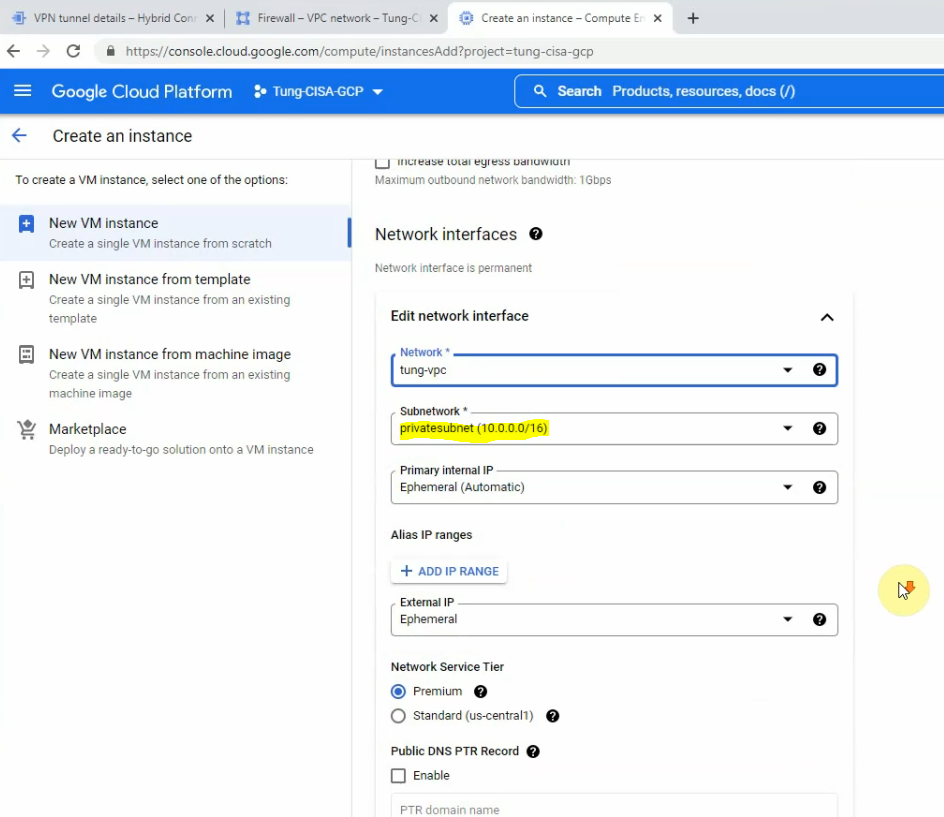
Click create.
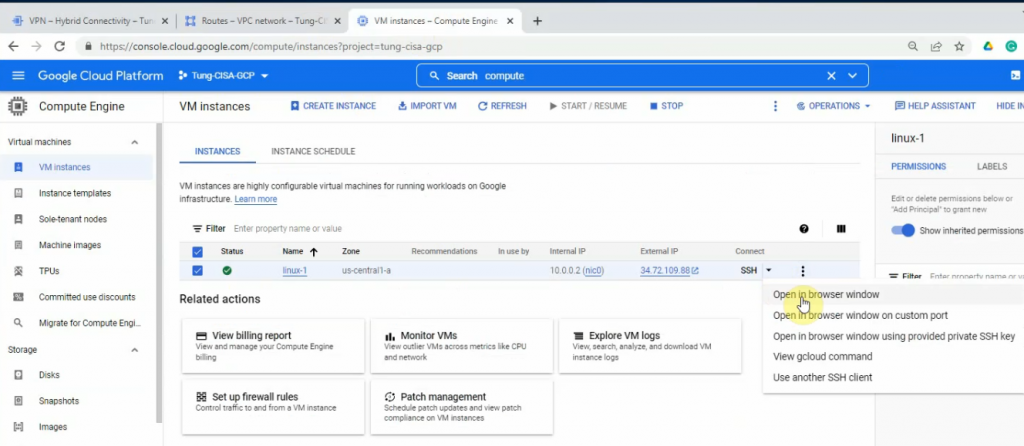
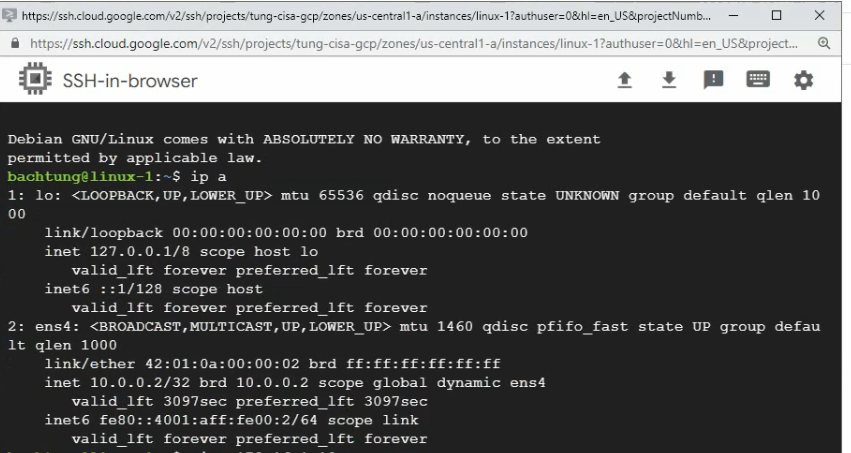
Open SSH in browser windows on the Linux instance.
Go to FortiGate.
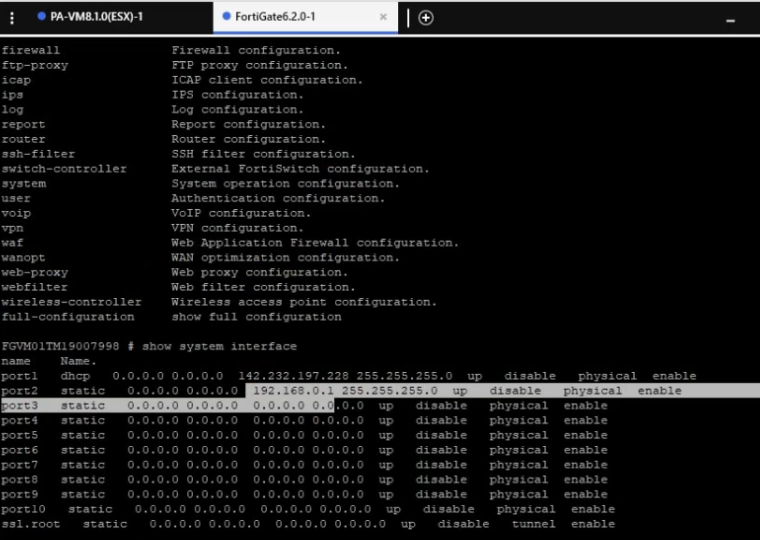
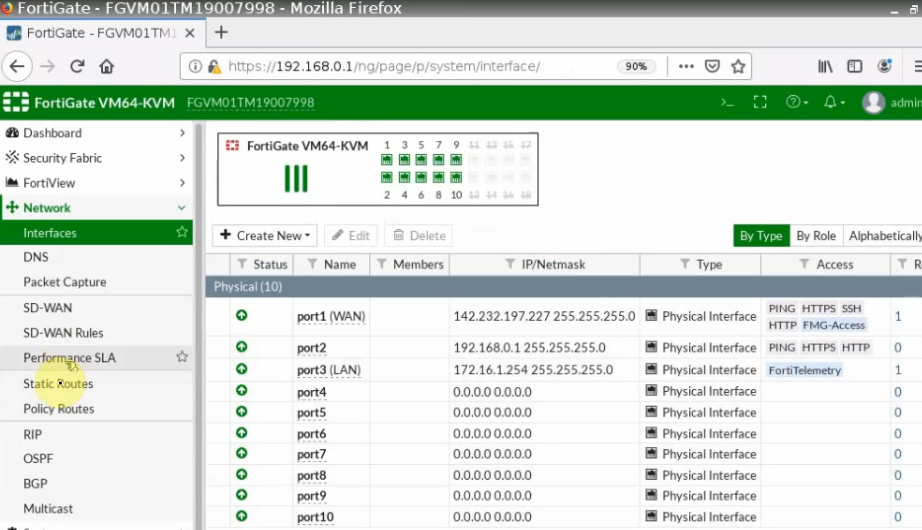
Create IP tunnel.
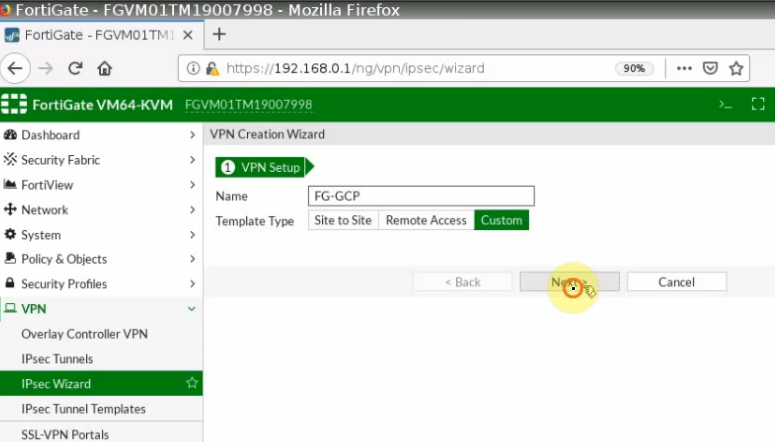
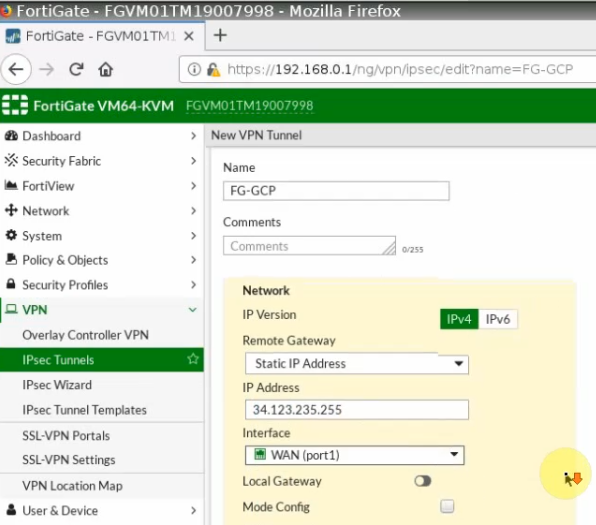
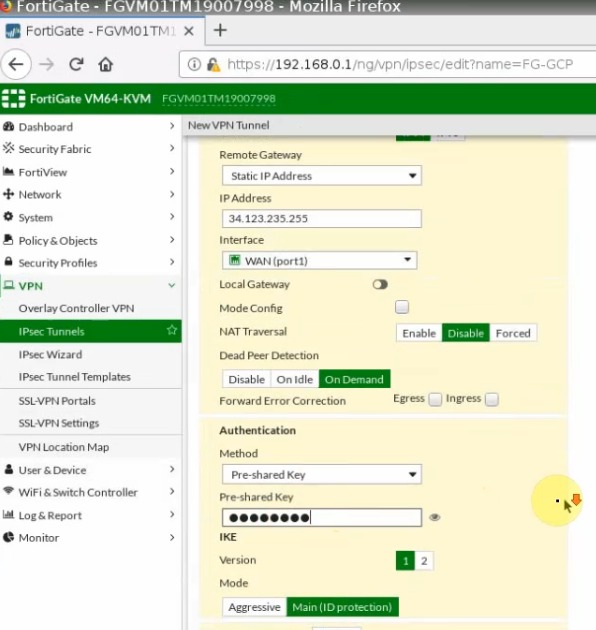
Phase 1.
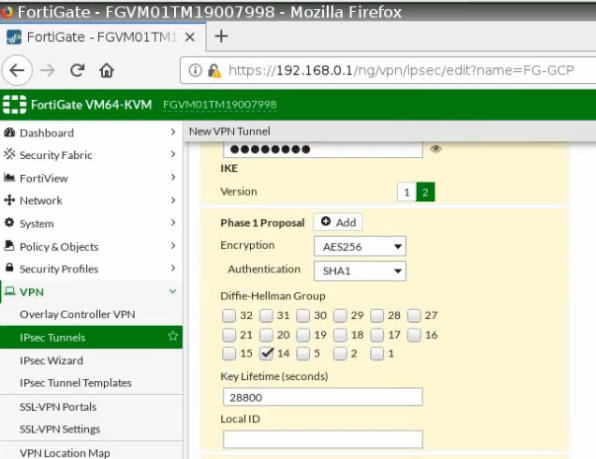
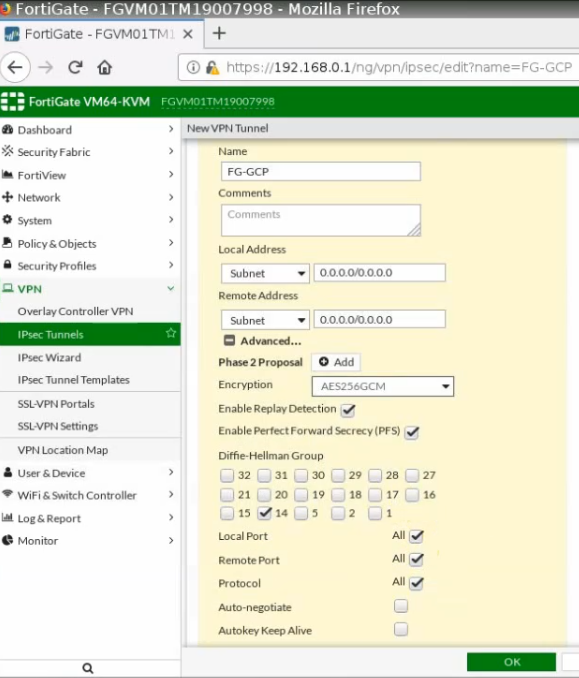
Phase 2.
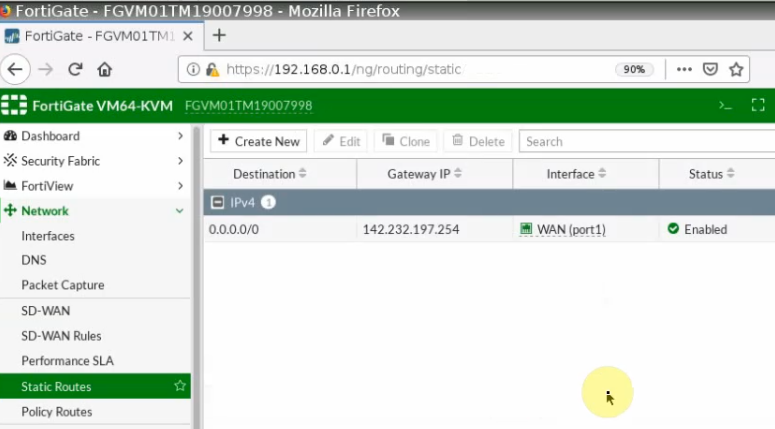
Create a static route to allow traffic from FortiGate LAN subnet to GCP privatesubnet.
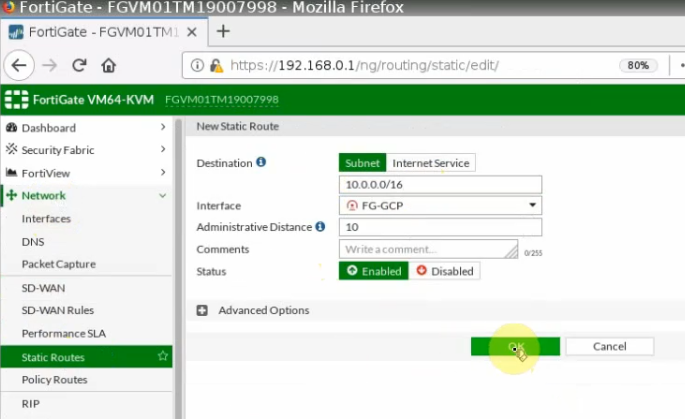
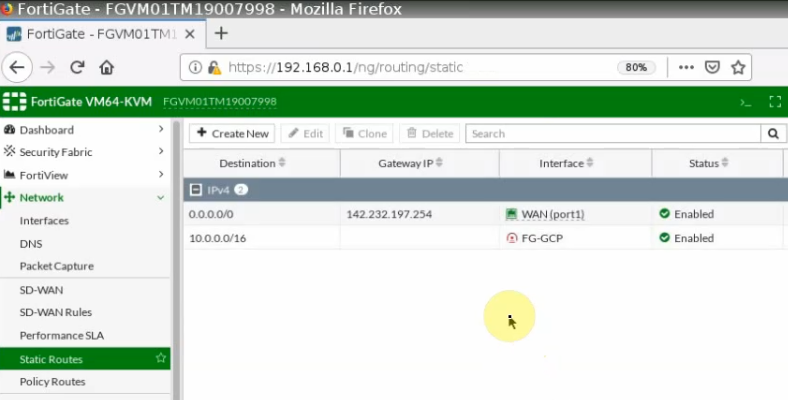
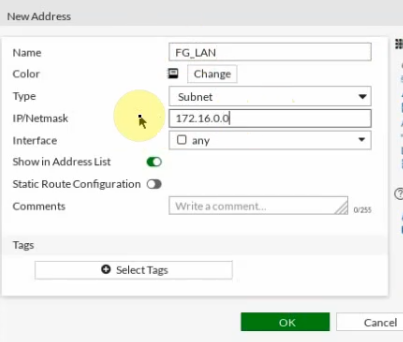
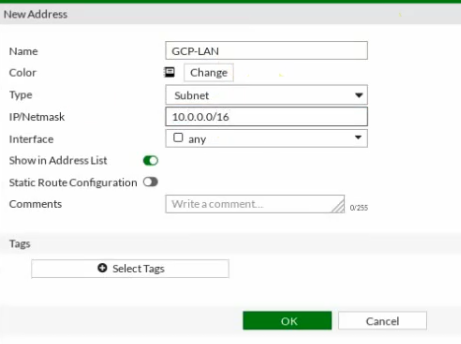
Create both FG-LAN and GCP-LAN subnet.
Create both access rules to allow traffic from the FortiGate LAN subnet to the GCP private subnet and vice versa.
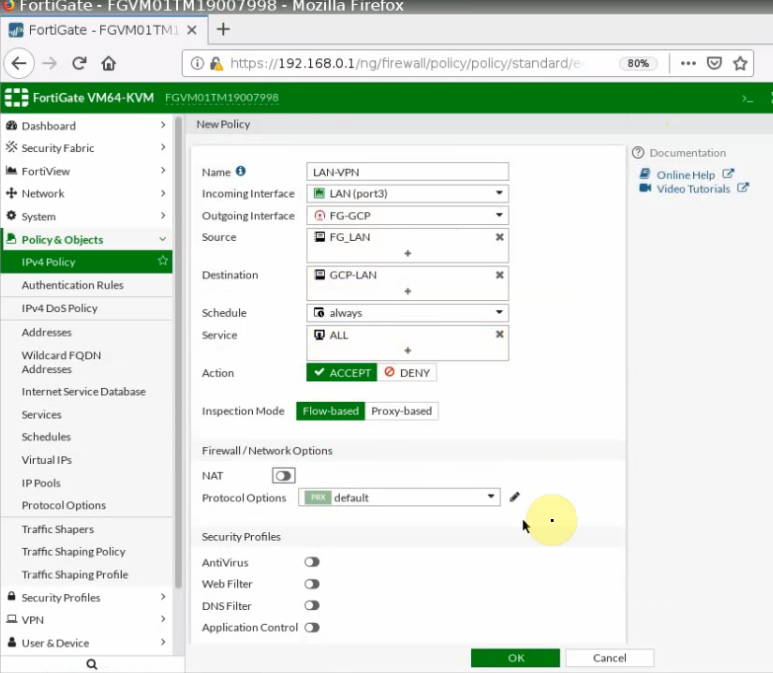
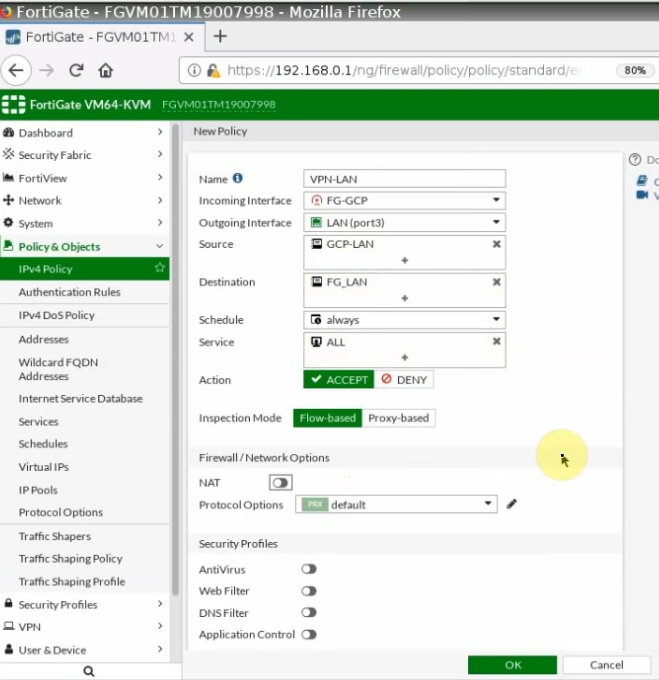
Ping from Kali machine to the Linux instance on GCP.
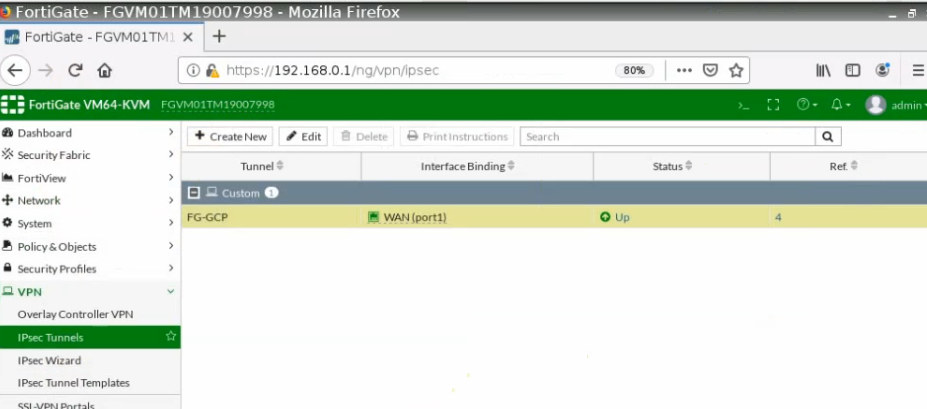
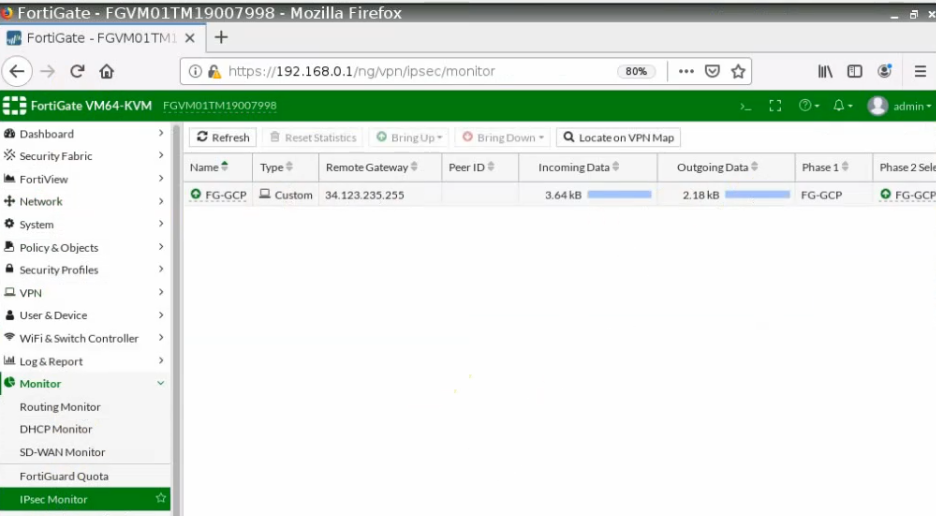
The tunnel is up on FortiGate.
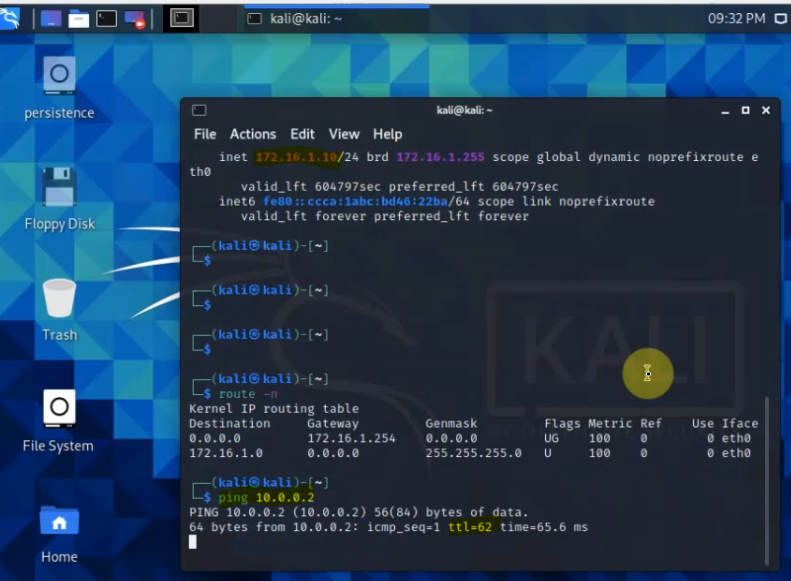
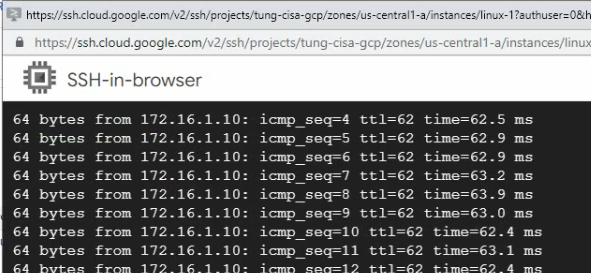
Ping from Linux instance on GCP to Kali machine on FortiGate LAN subnet.
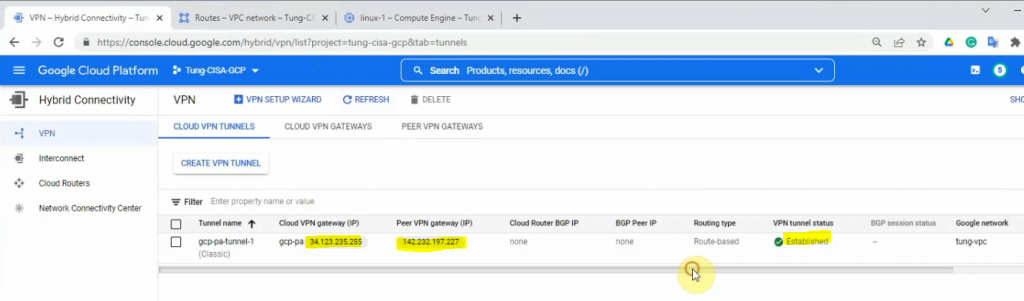
The tunnel is up on GCP as well.