This is a lab to set up a VPN site-to-site tunnel between both devices.
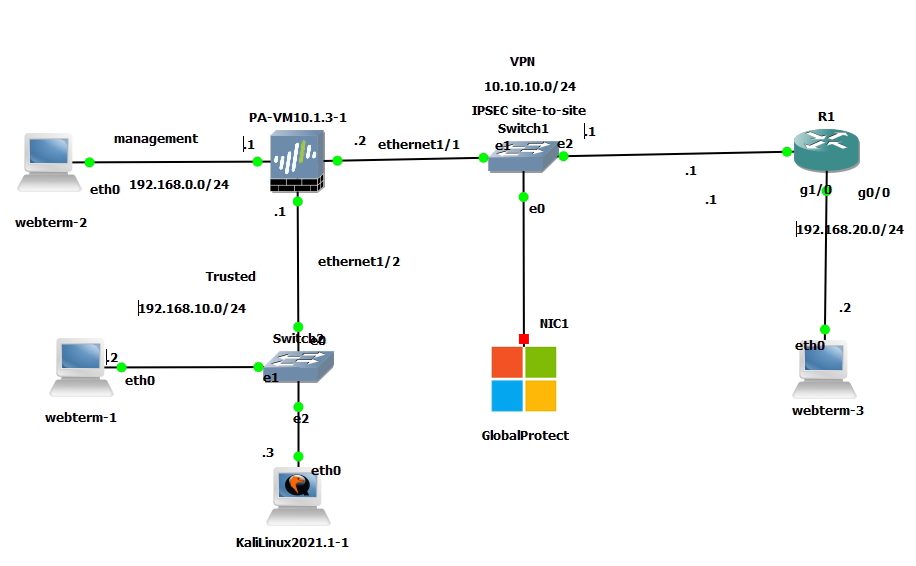
Configure interfaces and enable IPSEC VPN site to site on Cisco Router.
R1(config)#int g0/0
R1(config-if)#ip add 192.168.20.1 255.255.255.0
R1(config-if)#no shut
R1(config)#int g1/0
R1(config-if)#des "Connect to PA""
R1(config-if)#ip add 10.10.10.1 255.255.255.0
R1(config-if)#no shut
Create an ACL for VPN.
R1(config)#ip access-list extended ACL
R1(config-ext-nacl)#permit ip 192.168.20.0 0.0.0.255 192.168.10.0 0.0.0.255
Create ISAKMP phase 1 of the tunnel.
R1(config)#crypto isakmp policy 1
R1(config-isakmp)#encr aes
R1(config-isakmp)#hash md5
R1(config-isakmp)#authentication pre-share
R1(config-isakmp)#group 5
R1(config-isakmp)#lifetime 86400
# Assign authentication-key for remote peer.
R1(config)#crypto isakmp key cisco123 address 10.10.10.2
# Create IPSEC transfrom set for phase 2
R1(config)#crypto ipsec transform-set TSET esp-aes esp-sha-hmac
# Create cryoto map to apply the phase 2 settings to the interface
crypto map PA1 10 ipsec-isakmp
set peer 10.10.10.2
set transform-set TSET
match address ACL
# Applly crypto map to an interface.
R1(config-crypto-map)#int g1/0
R1(config-if)#crypto map PA1
# Create a static route to route traffic between both sites.
R1(config)#ip route 0.0.0.0 0.0.0.0 10.10.10.2
Access Palo Alto Web management.
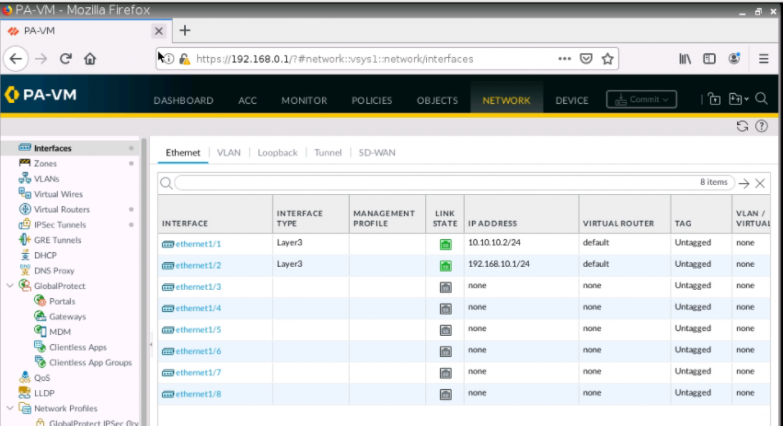
Assign an IP address for interface e1/1 and e1/2.
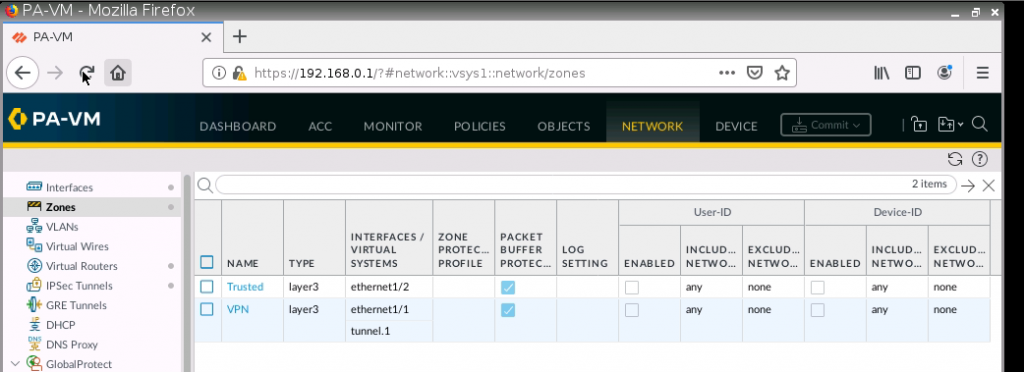
Create a new tunnel 1 on PA.
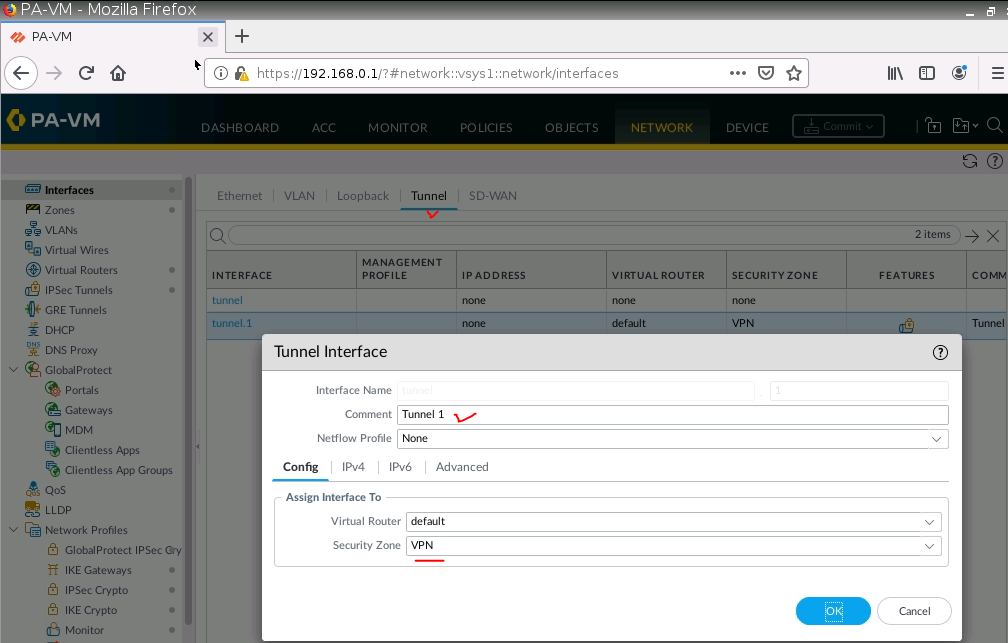
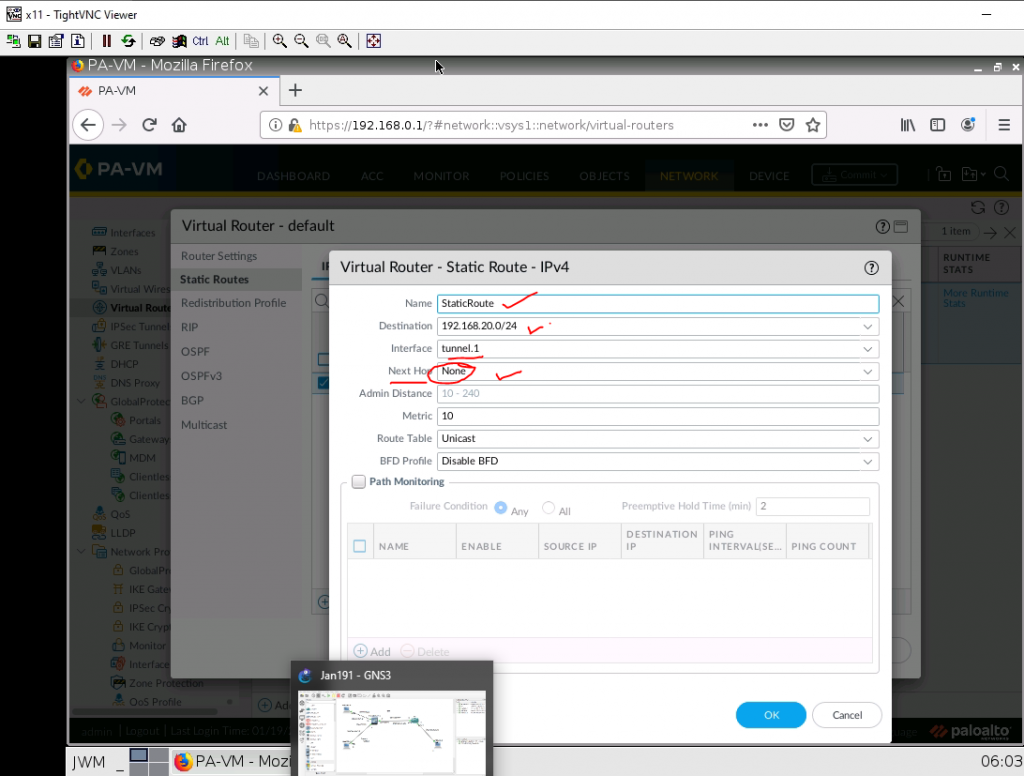
Configure a static route between PA and Cisco Router and set next hop is “None”.
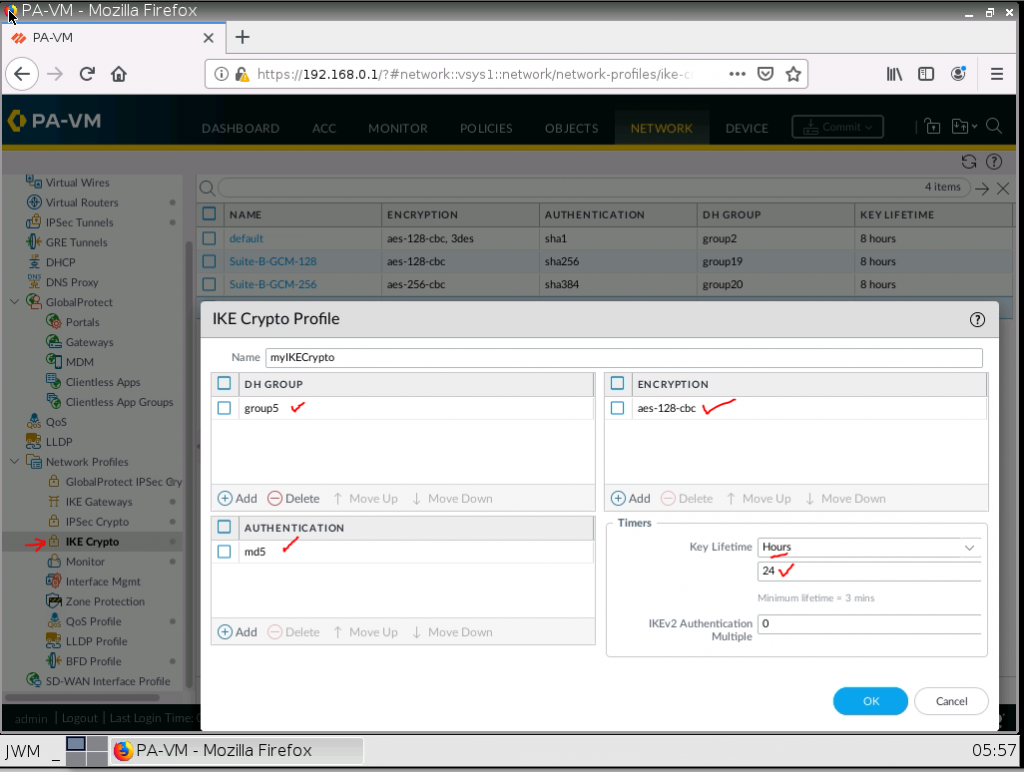
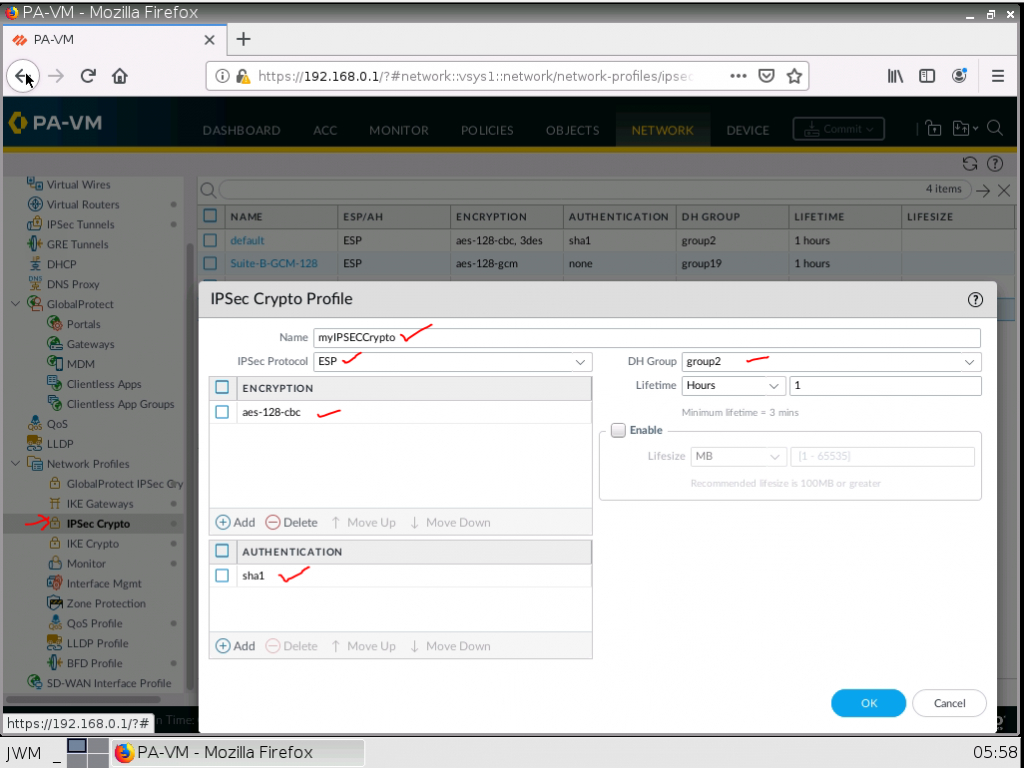
Configure IKECrypto as on Cisco Router.
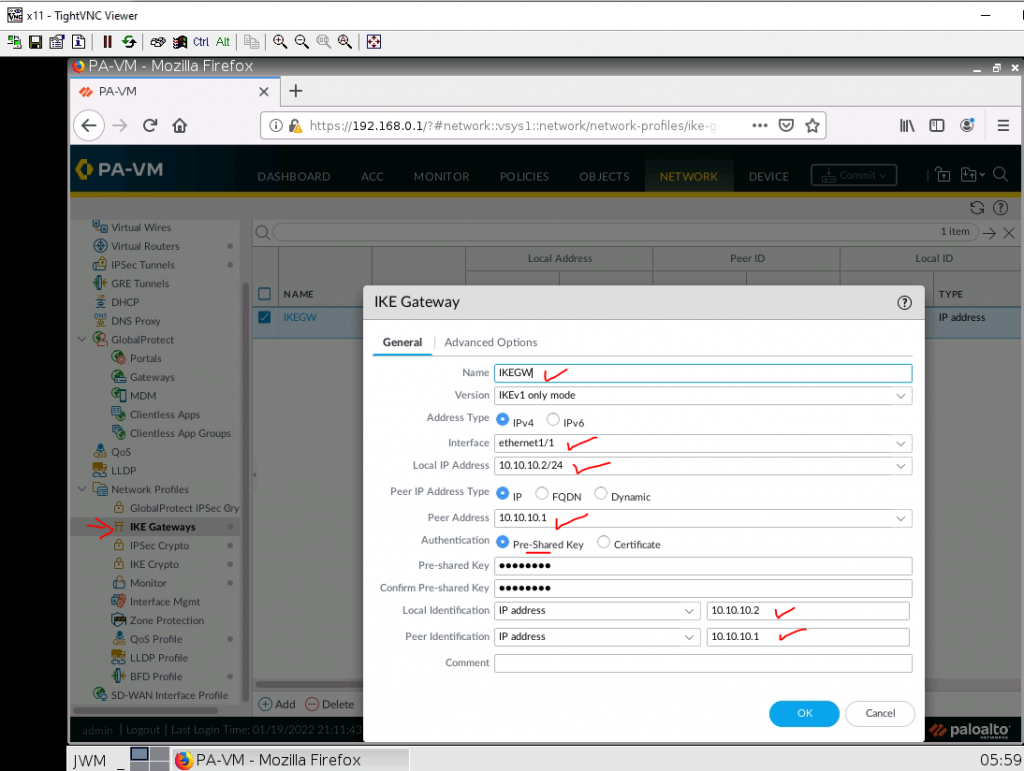
Configure IKE Gateway.
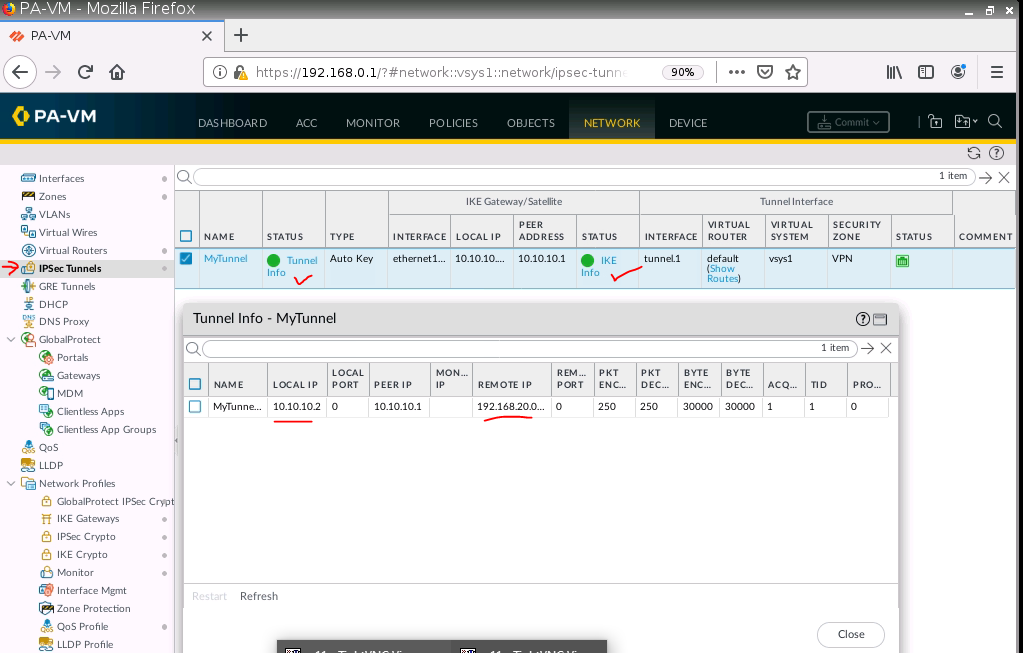
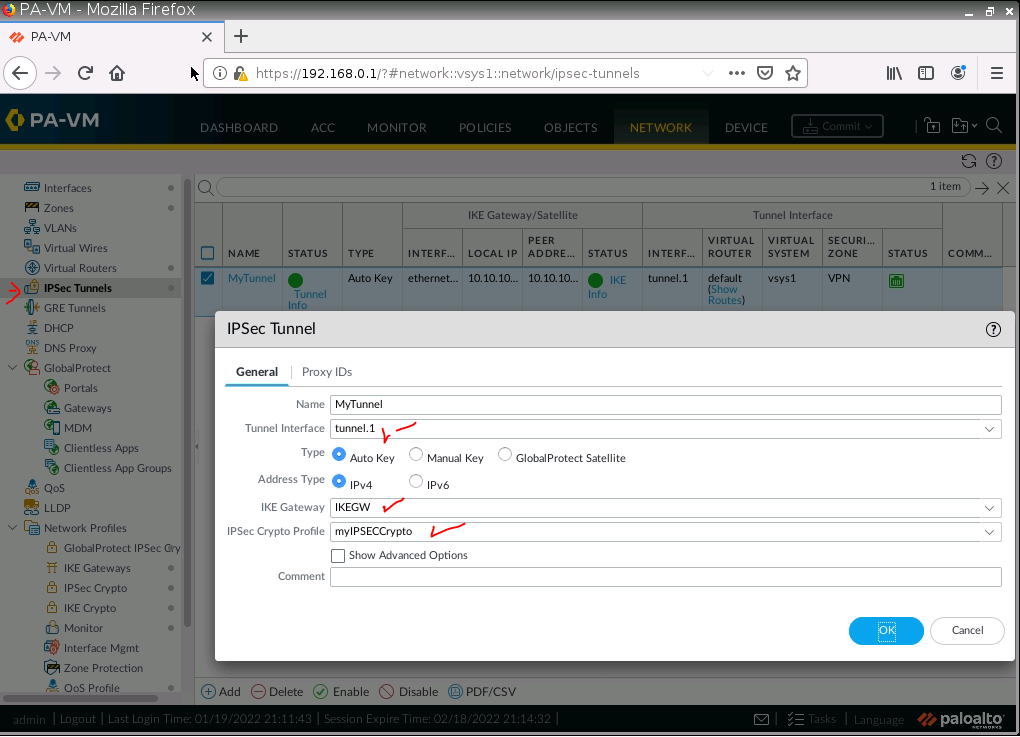
Configure IPSEC Tunnel.
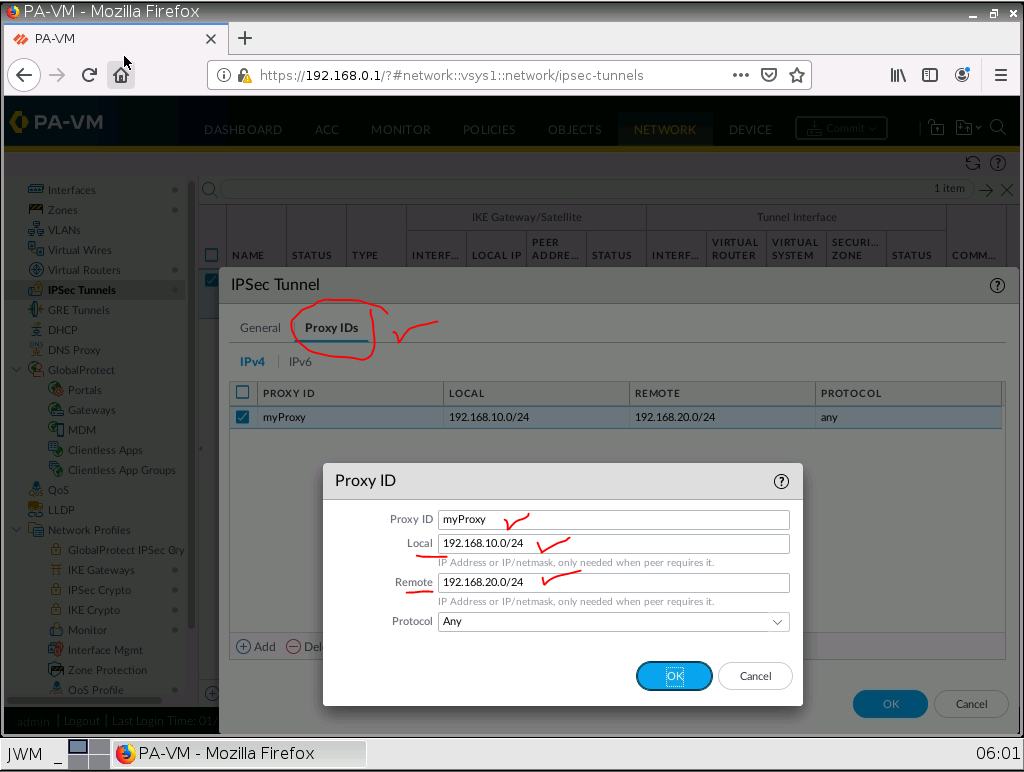
Configure Proxy ID.
Create both Security policies to allow traffic from the Trusted zone to the VPN zone and vice versa.
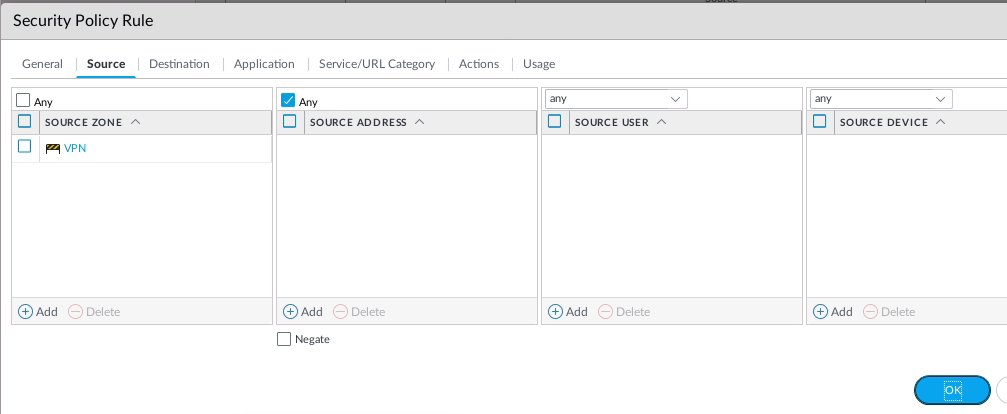
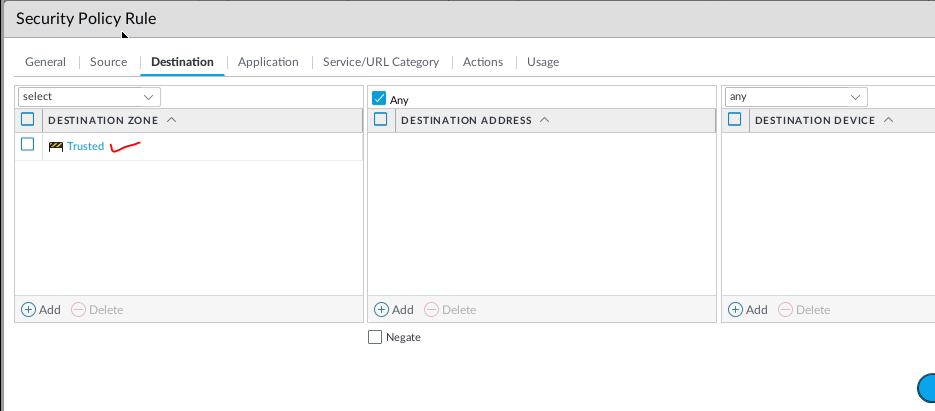
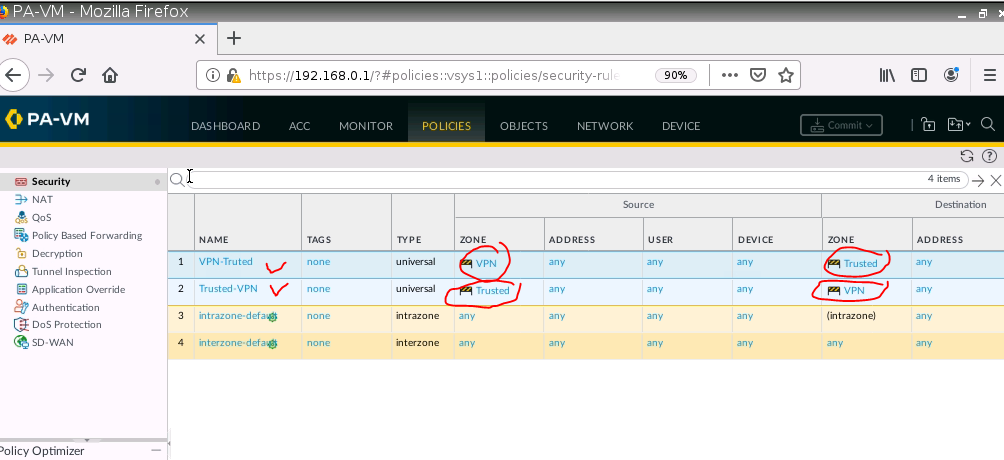
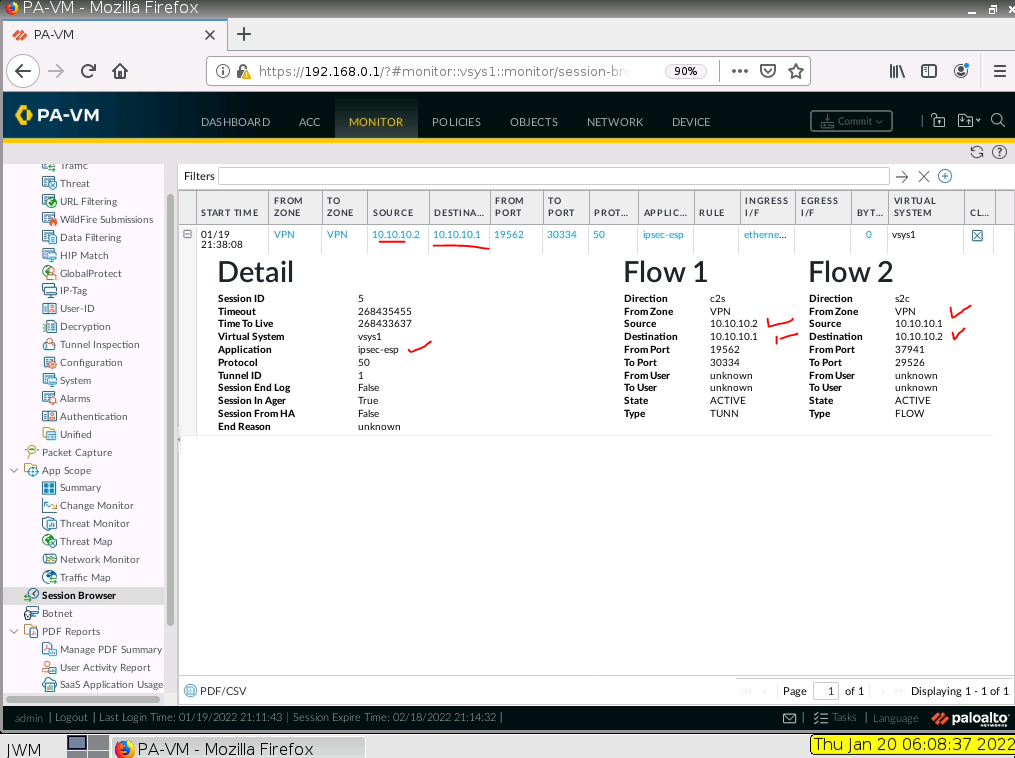
From Webterm2 (192.168.10.2) pings Webterm 3 (192.168.20.2).
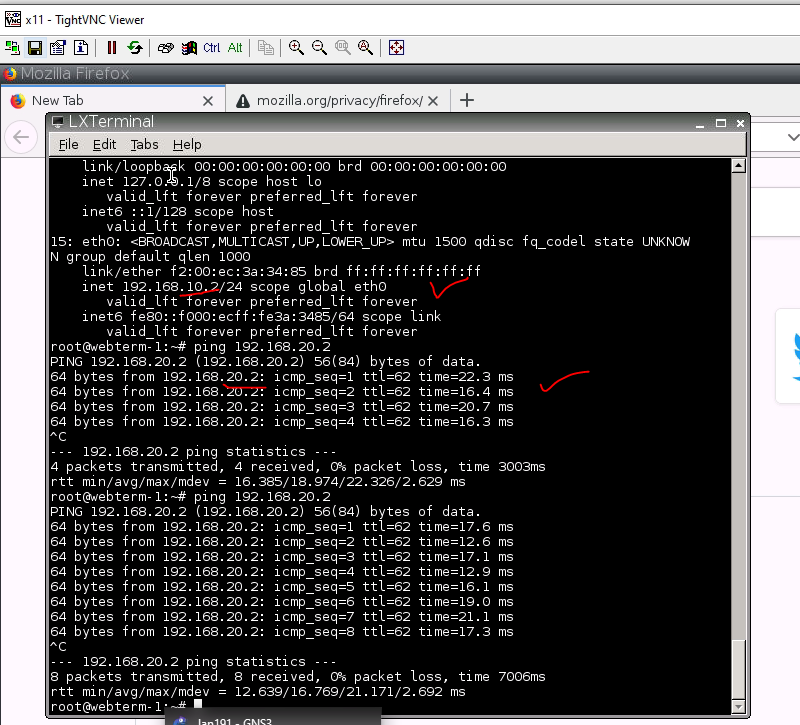
Check PA, the IPSEC tunnel is up.