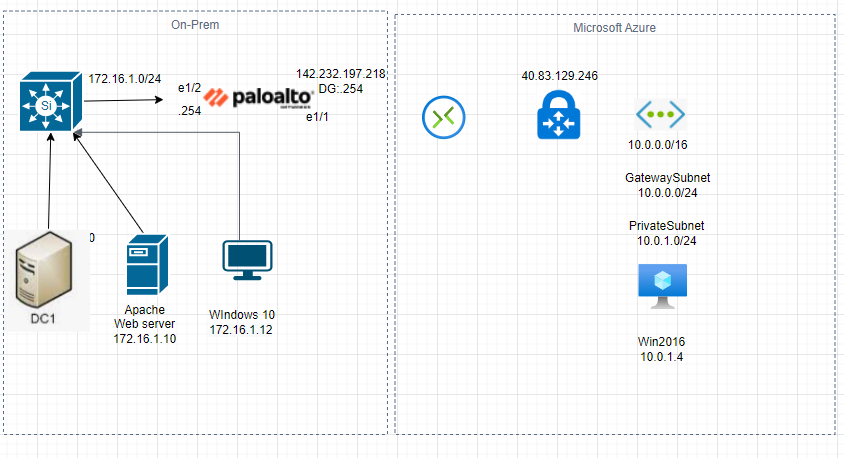
This is a diagram that I have used for the lab.
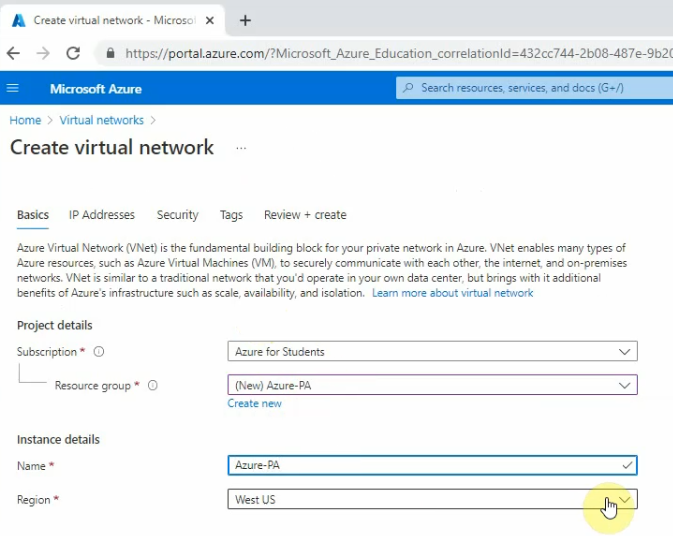
Create a new virtual network is Azure-PA.
Change default network to PrivateSubnet is 10.0.1.0.
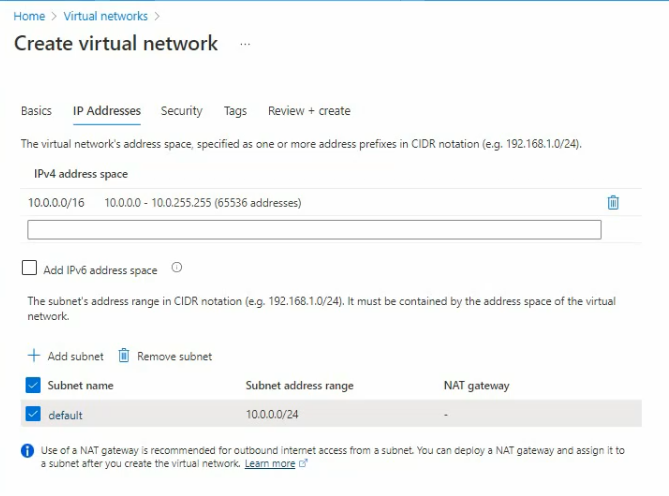
A subnet address range is 10.0.1.0/24
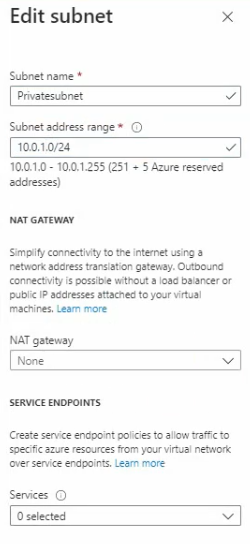
Click Create.
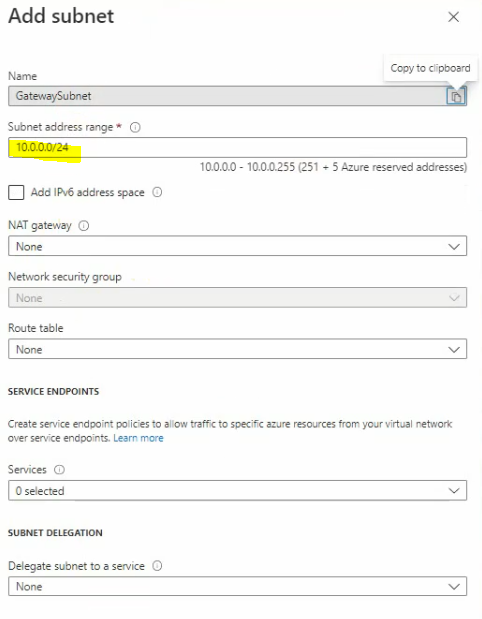
Create a new subnet.
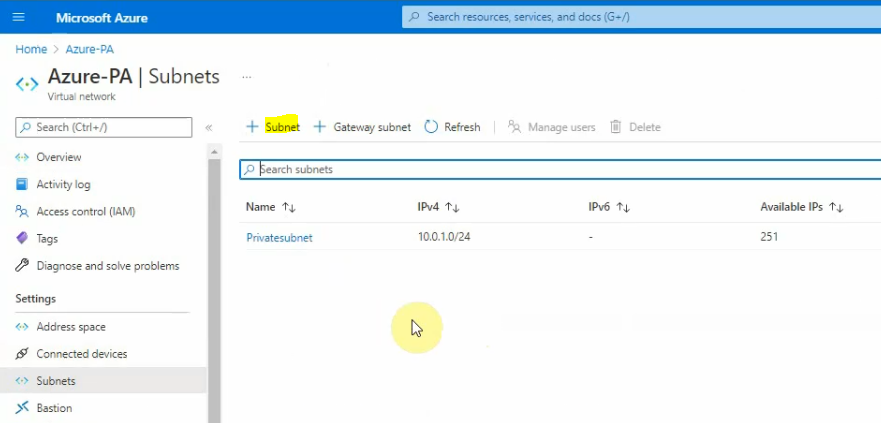
A subnet address range is 10.0.0.0/24
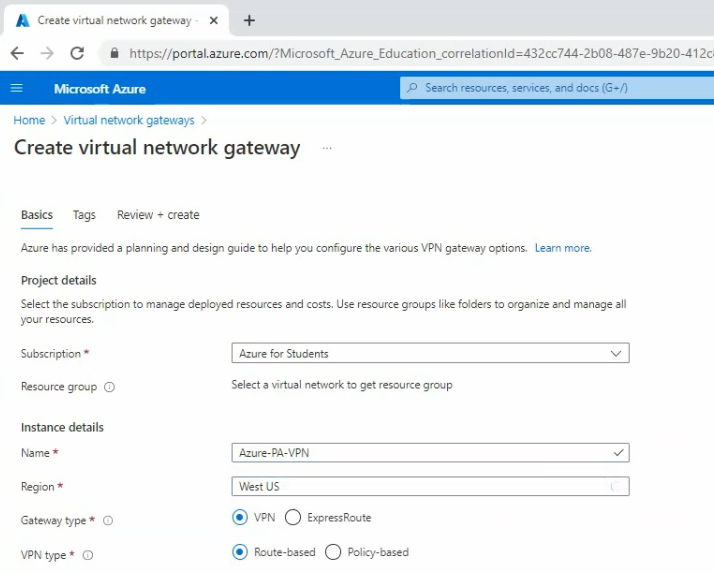
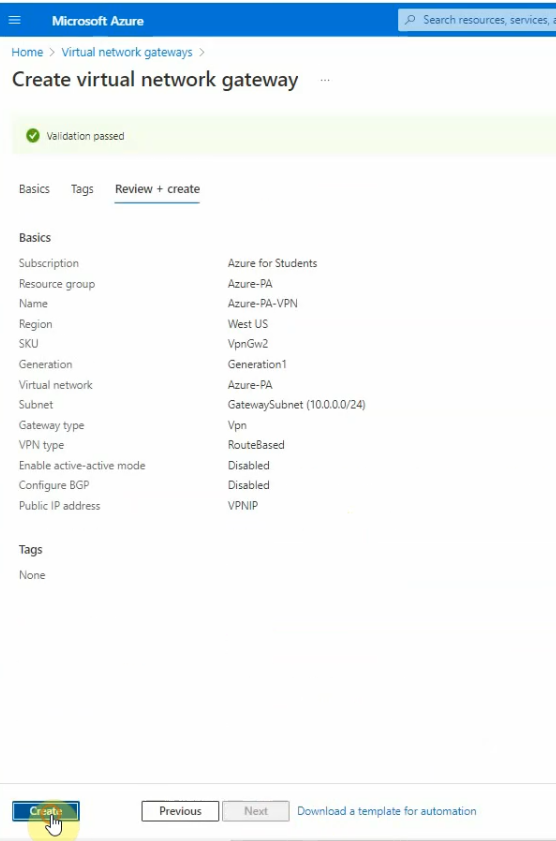
Go to “Virtual network gateway” to create a new virtual network gateway.
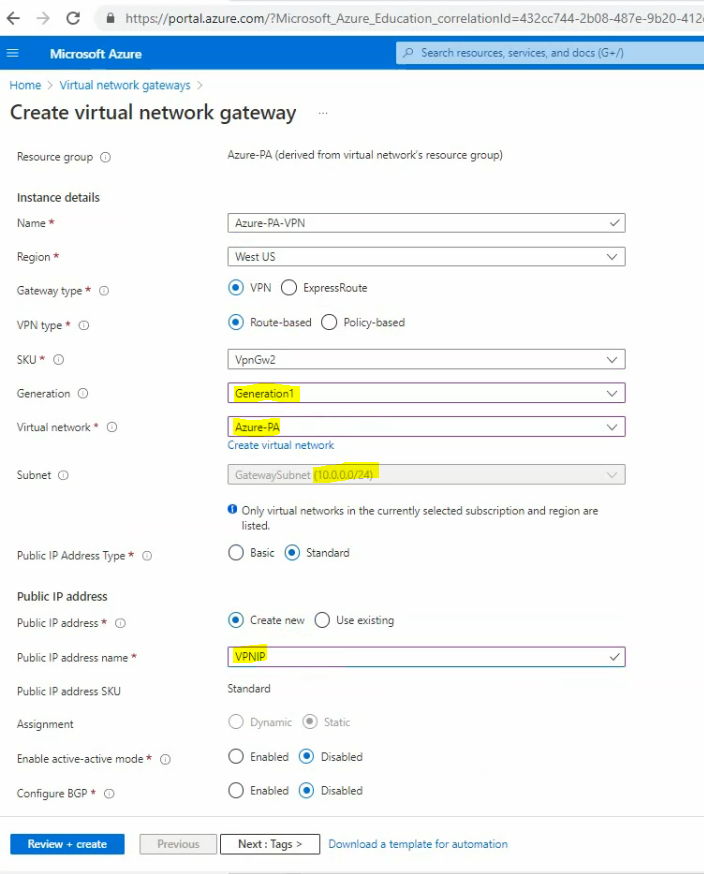
Virtual network: Azure-PA.
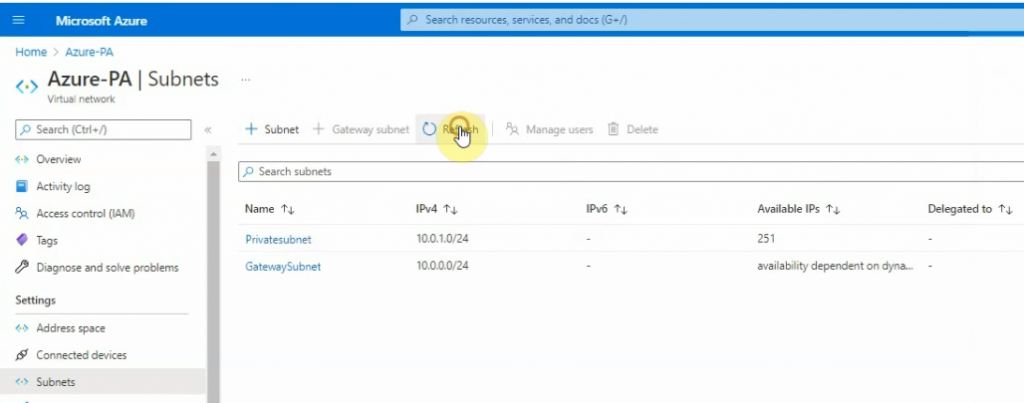
Subnet: Gatewaysubnet 10.0.0.0/24
Public IP address name: VPNIP
Click Create.
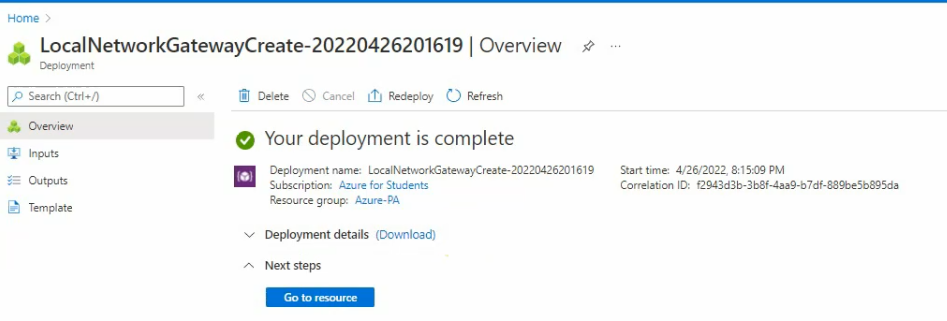
Wait around from 20 to 30 minutes to see if the Deployment is done.
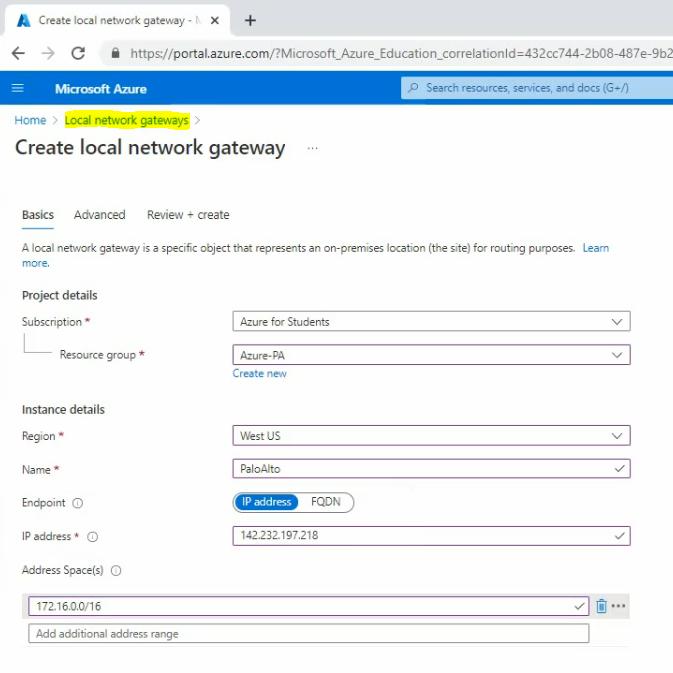
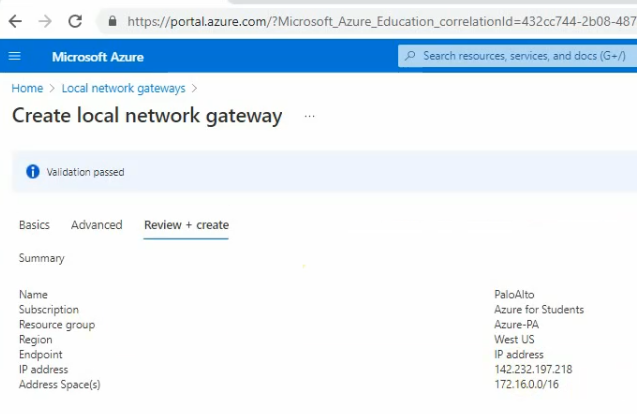
Go to “Local network gateway” and create a new local network gateway.
An IP address is a public IP address of the Palo Alto firewall.
Address space is Palo Alto’s LAN subnets.
Click create.
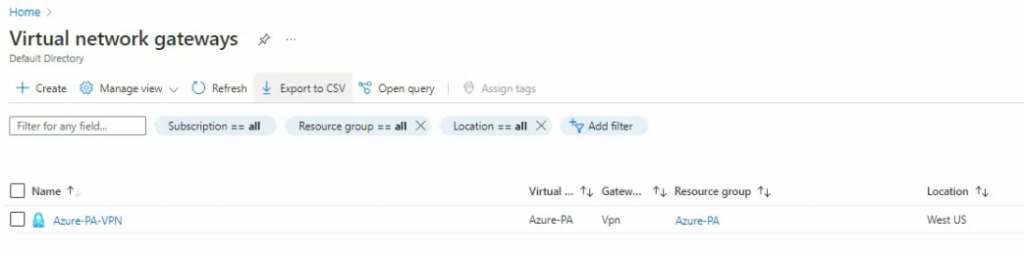
Go to “Virtual network gateways”, and select the virtual network gateways that we have created in the previous step.
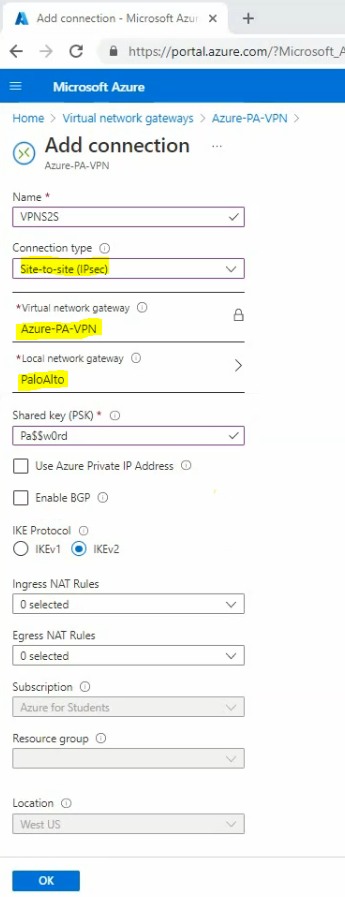
Go to “Connections” – Add.
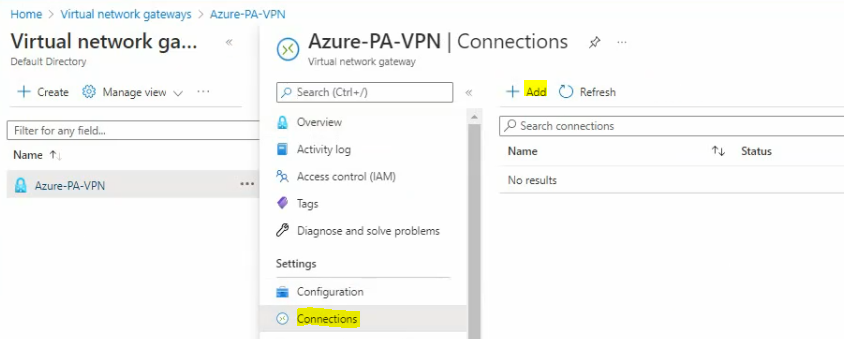
Enter a shared key (PSK) for VPN site-to-site.
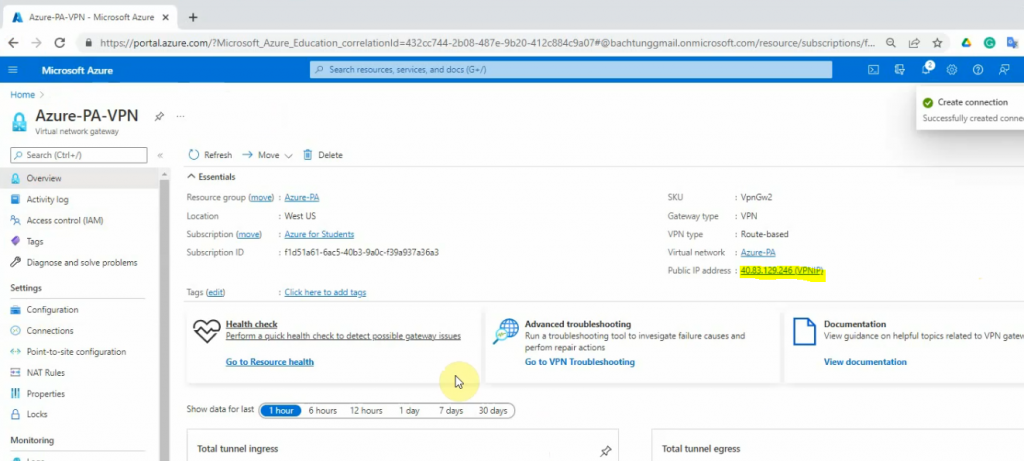
Take note of the IP address of Azure VPN.
On Palo Alto on-prem.
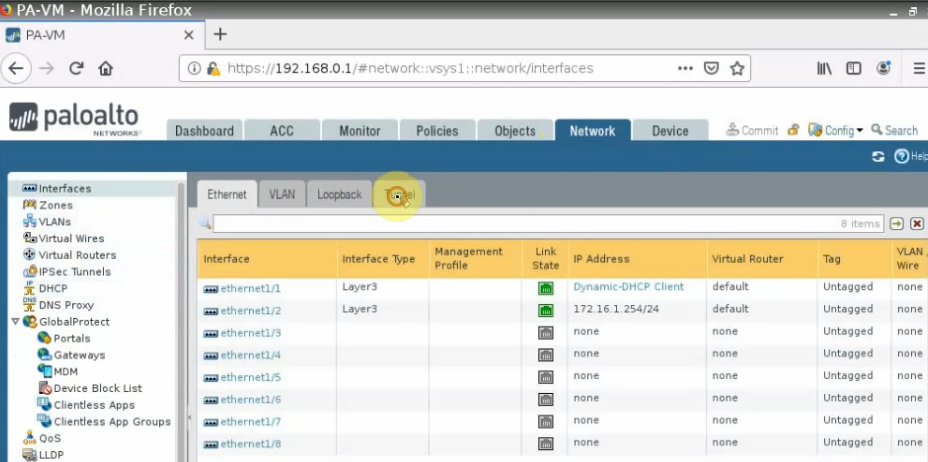
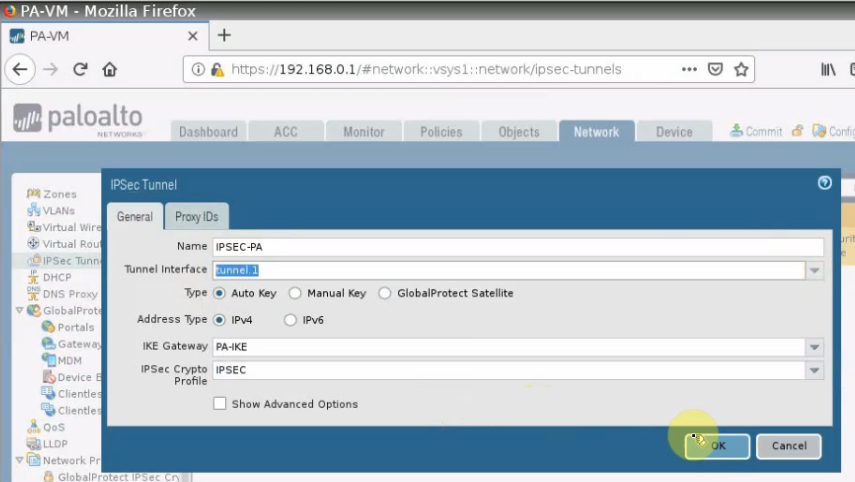
Interface tunnel1.
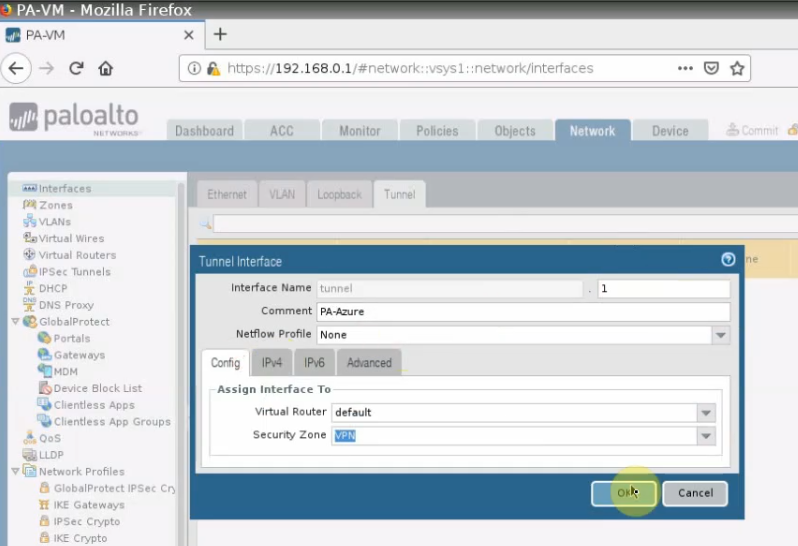
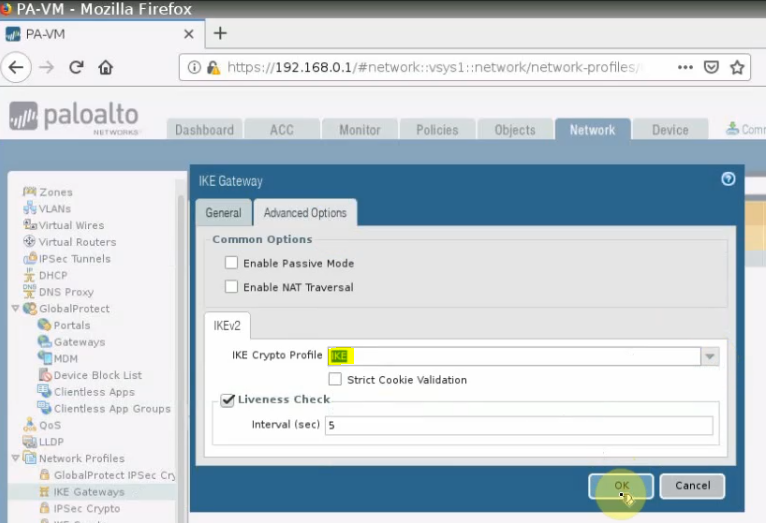
Create an IKE Crypto.
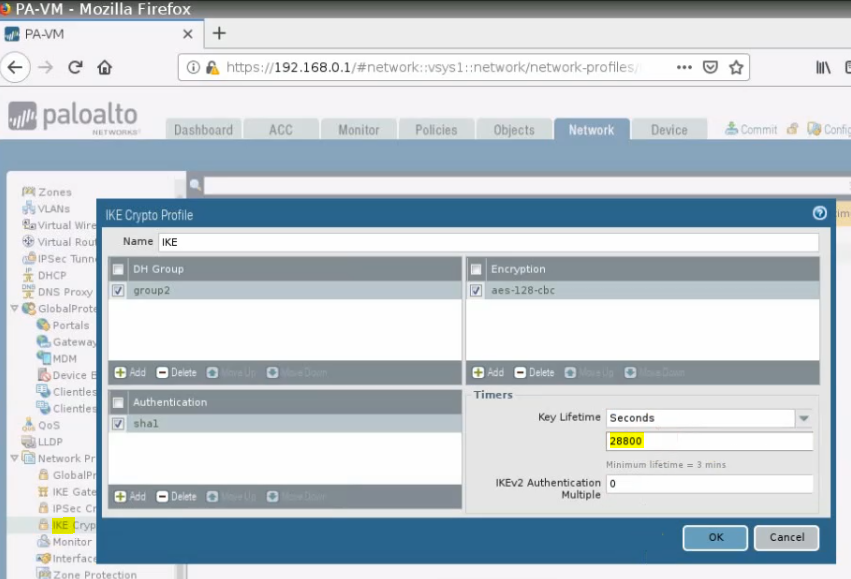
IPSEC Crypto.
According to Azure, we will use 27000 seconds for the key lifetime.
- IKEv2 Main Mode SA lifetime is fixed at 28,800 seconds on the Azure VPN gateways.
- QM SA Lifetimes are optional parameters. If none was specified, default values of 27,000 seconds (7.5 hrs) and 102400000 KBytes (102GB) are used.
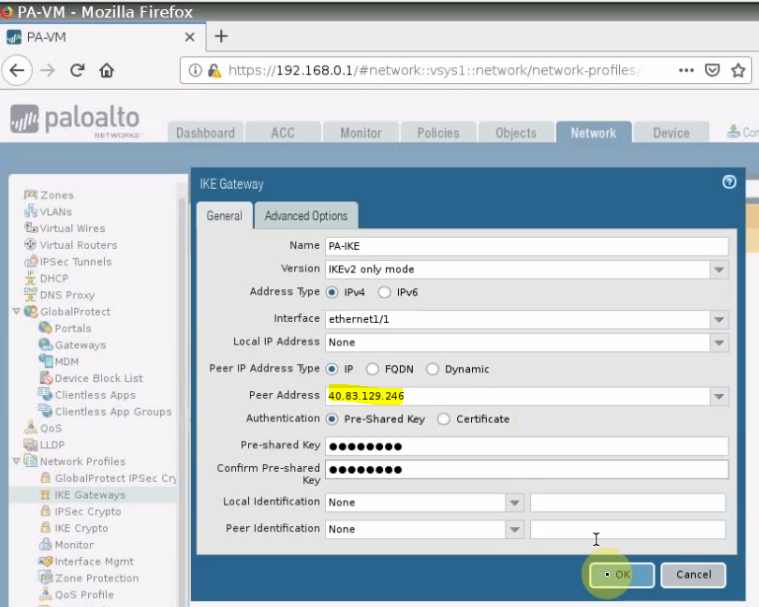
Create a new IKE Gateways.
The peer address is the Azure VPN gateway.
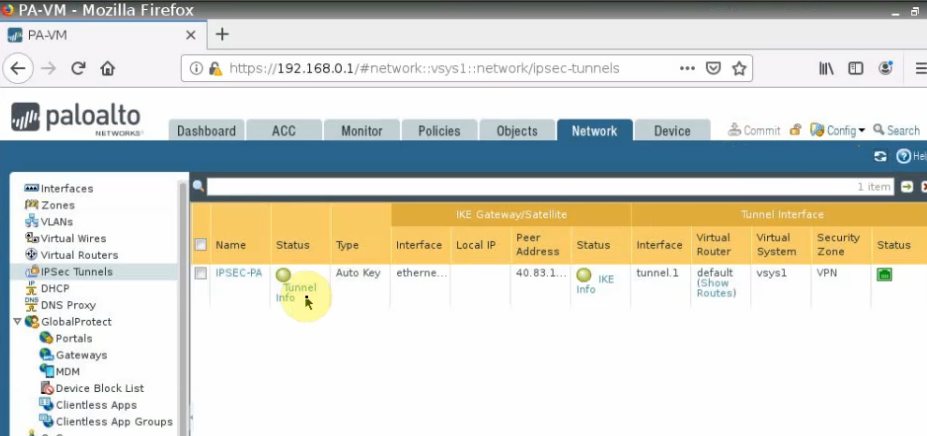
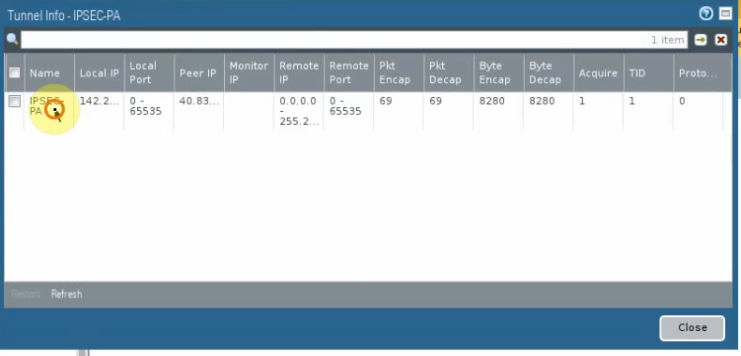
Create an IPSEC tunnel.
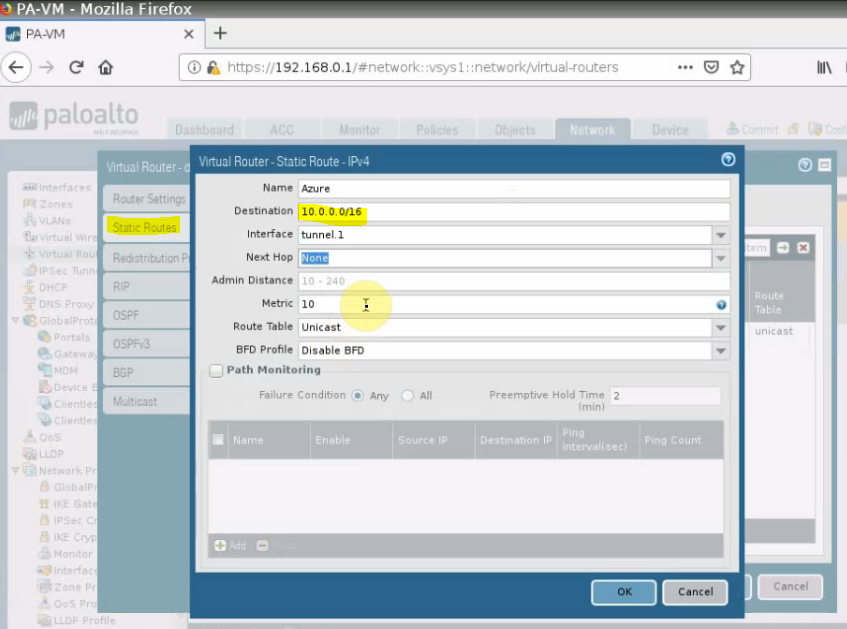
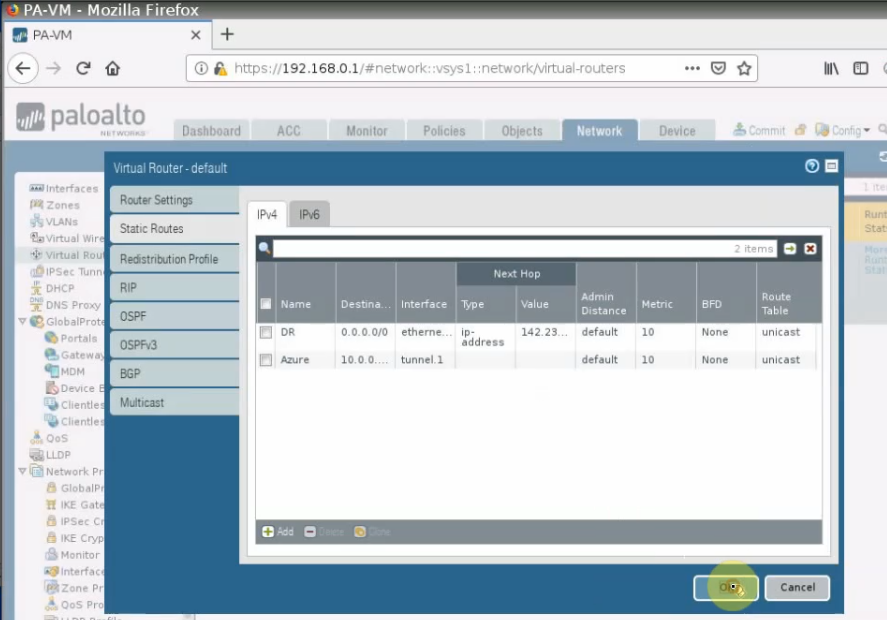
Create astatic routes to PrivateSubnet on Azure.
Create both access rules to allow traffic from PA LAN subnets to private subnet on Azure and vice versa.
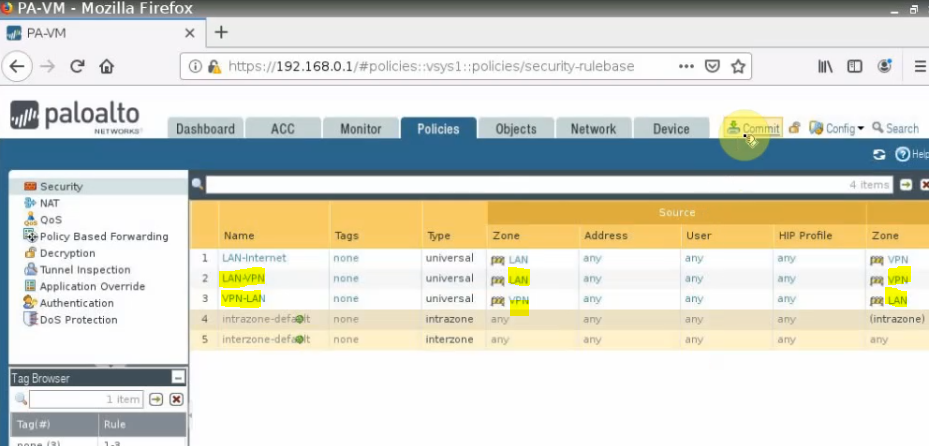
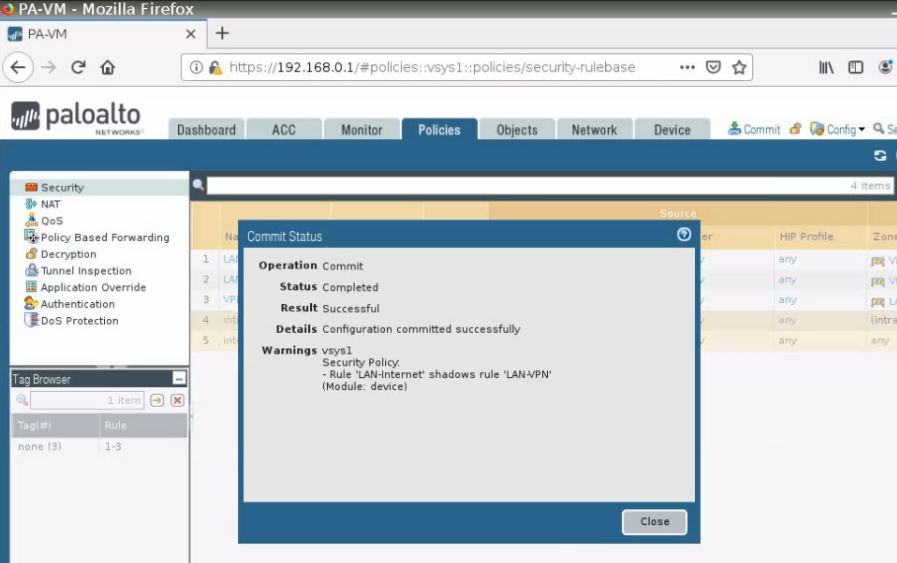
Click “Commit”.
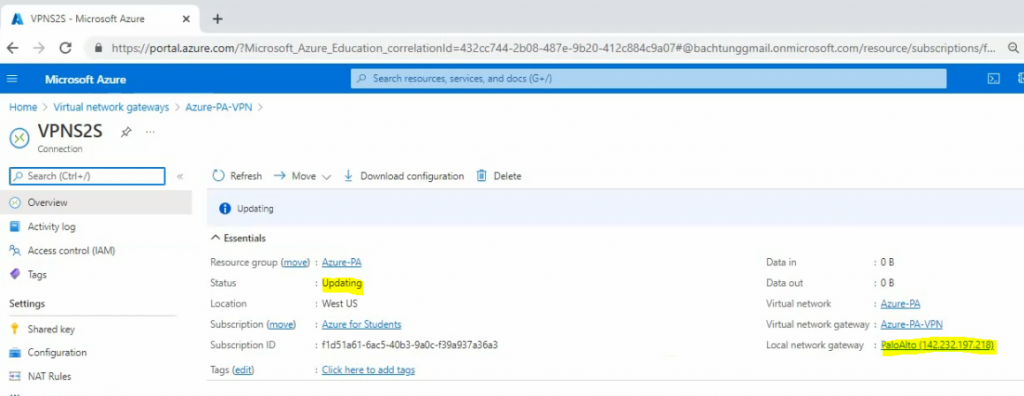
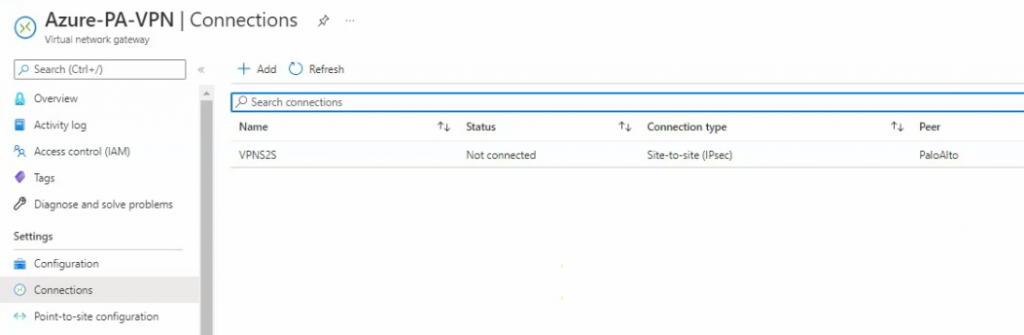
Back to Azure, the VPN site-to-site connection is still not connected.
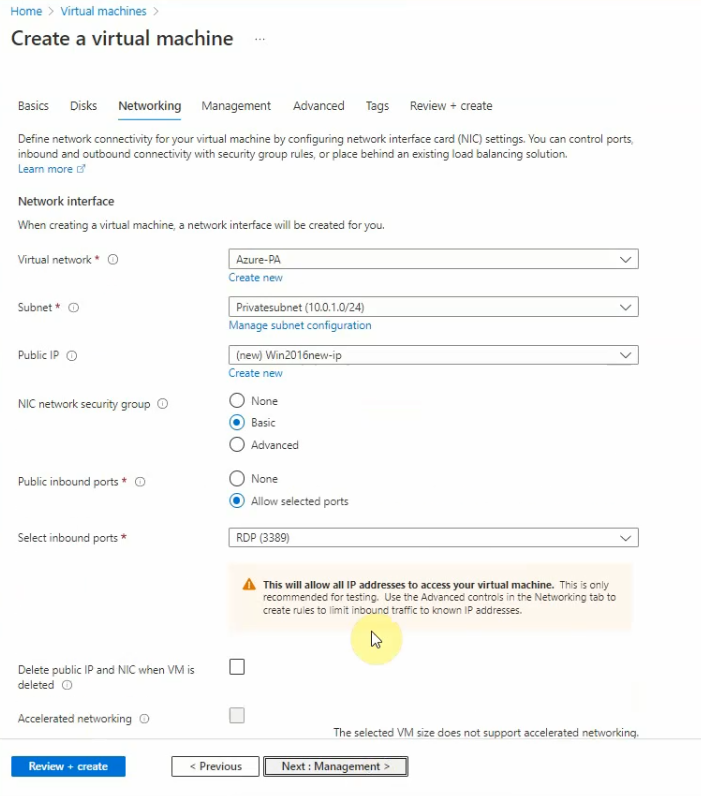
Create a new Windows 2016 virtual machine (Size is B1s).
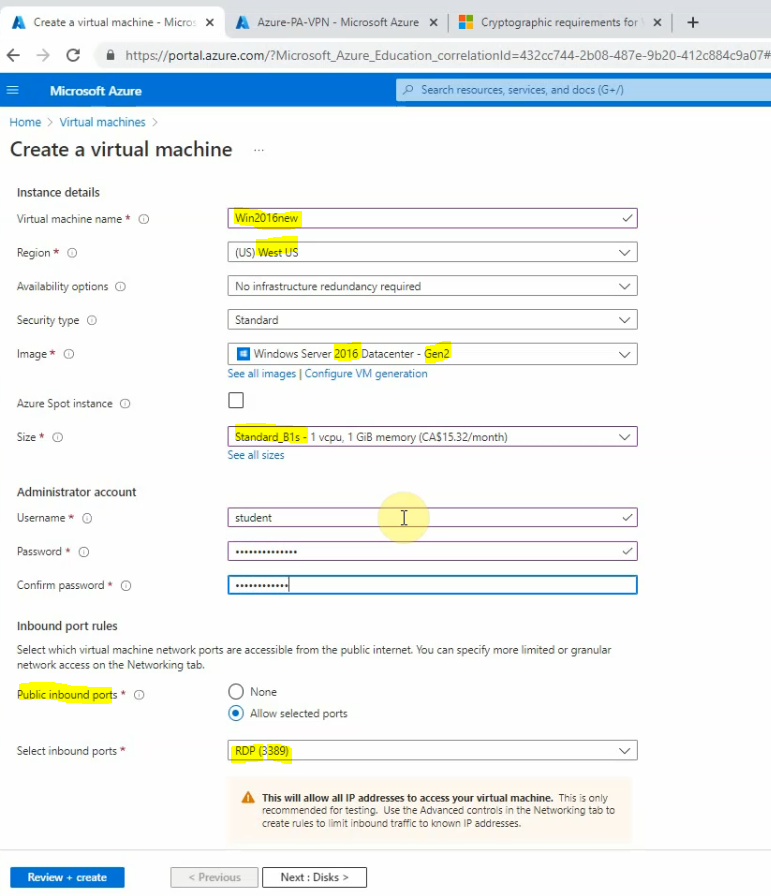
Get the Public IP address of the Windows 2016 virtual machine.
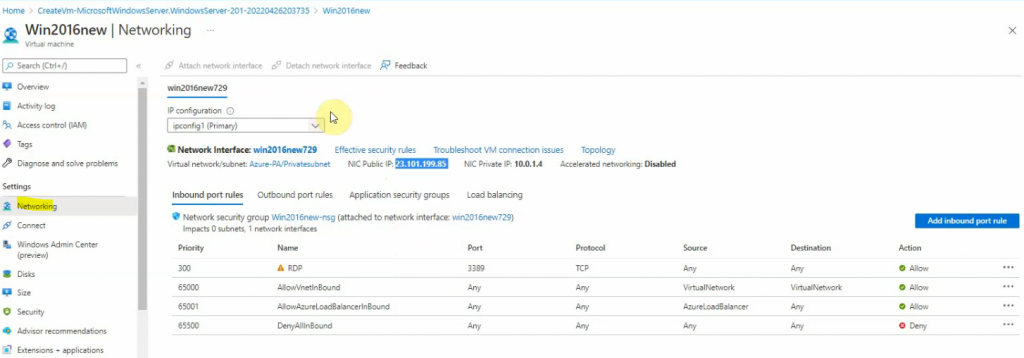
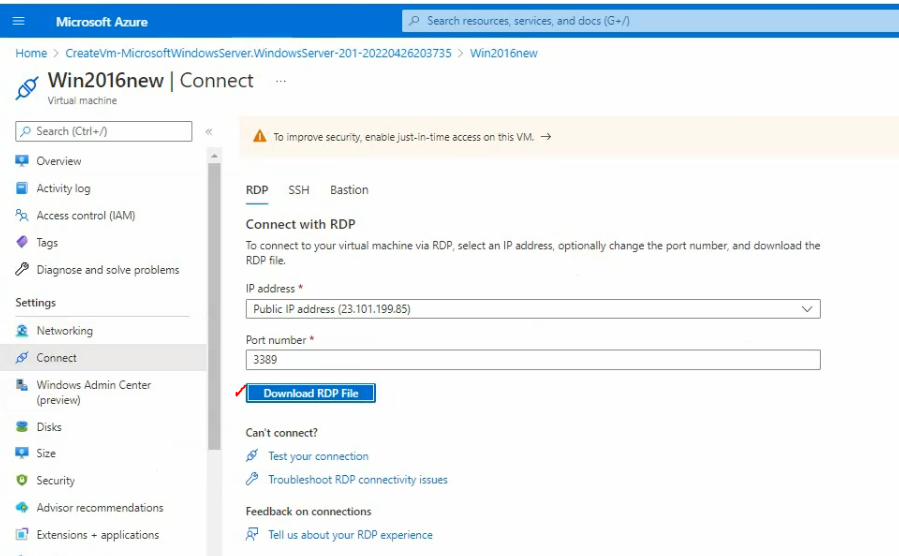
Download RDP file.
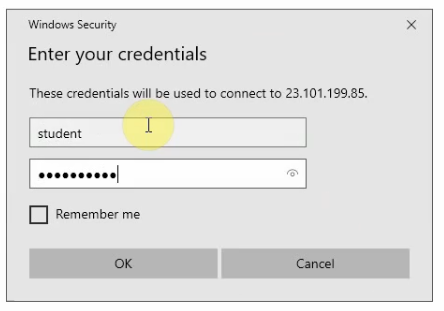
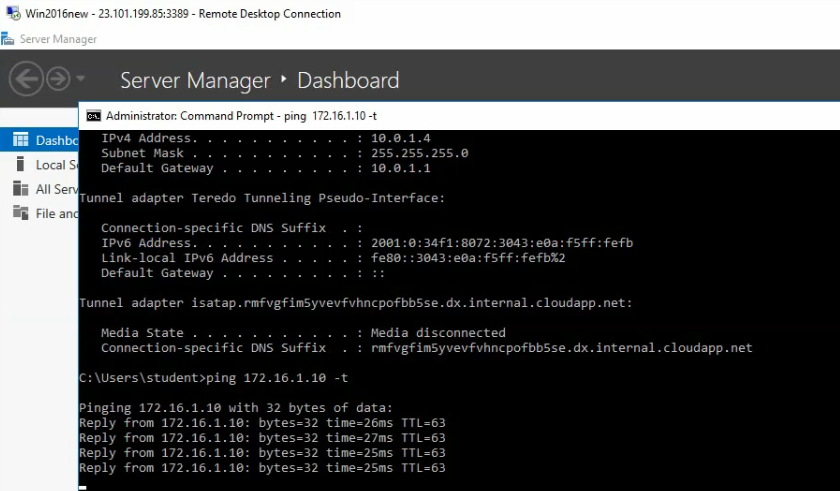
Back to VPN2S, we can see the VPN status connection is “Connected”.
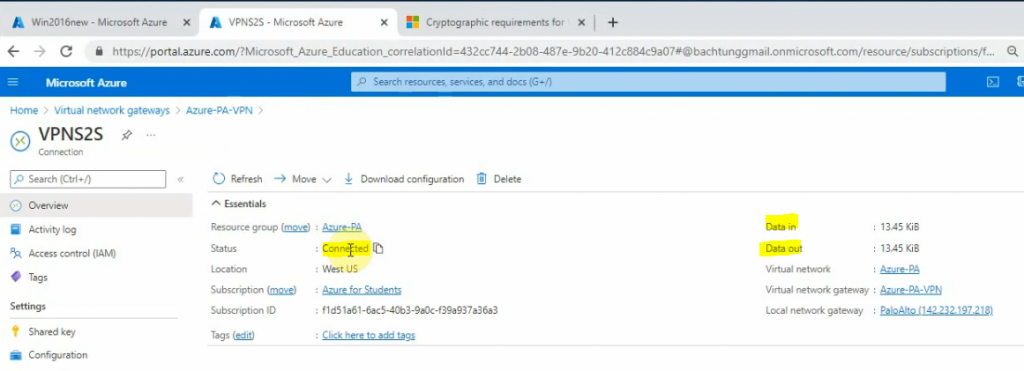
Microsoft Azure seems to not support many customer devices as Amazon AWS.
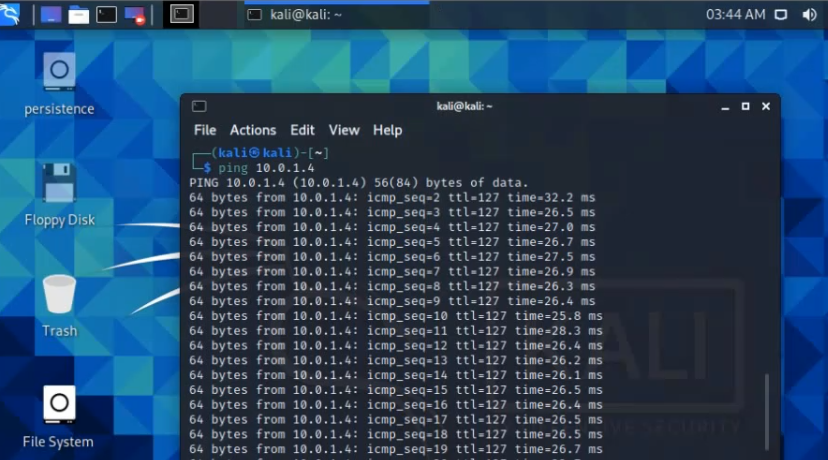
On Kali machine, pings Windows 2016 VM on Azure.
The IPSEC VPN site-to-site tunnel is up as well in Palo Alto.