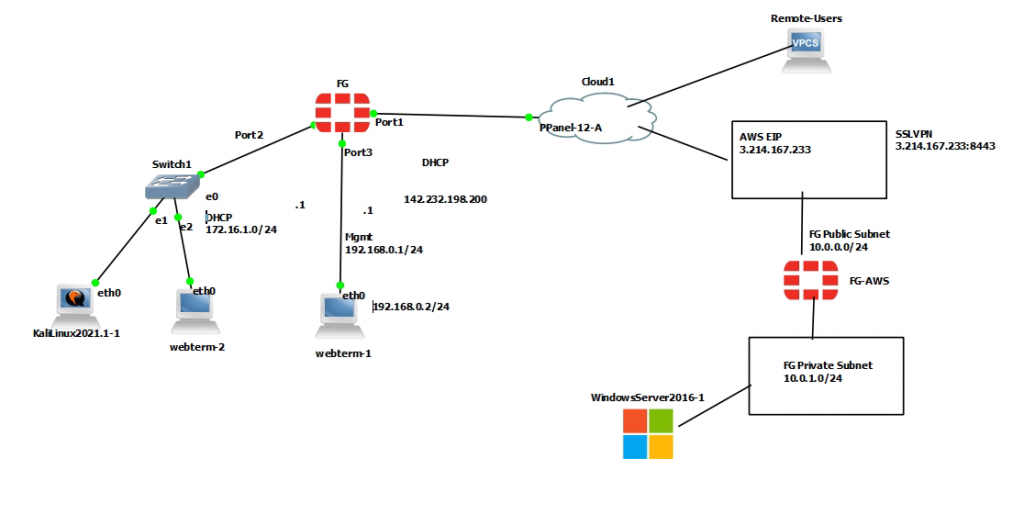
This is a topology that is used to deploy this lab.
+ Configure FortiGate on AWS.
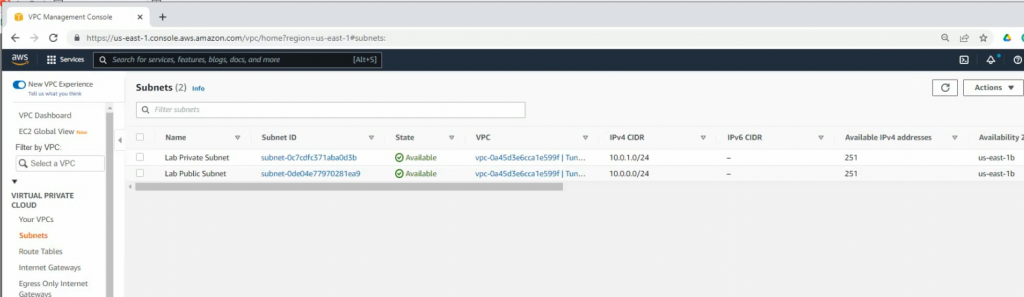
Create a new VPC with a CIDR network is 10.0.0.0/16. Then, create both Lab Public subnet and :ab Private subnet on AWS.
Create a new Internet gateway and attach to your VPC.
Create route tables.
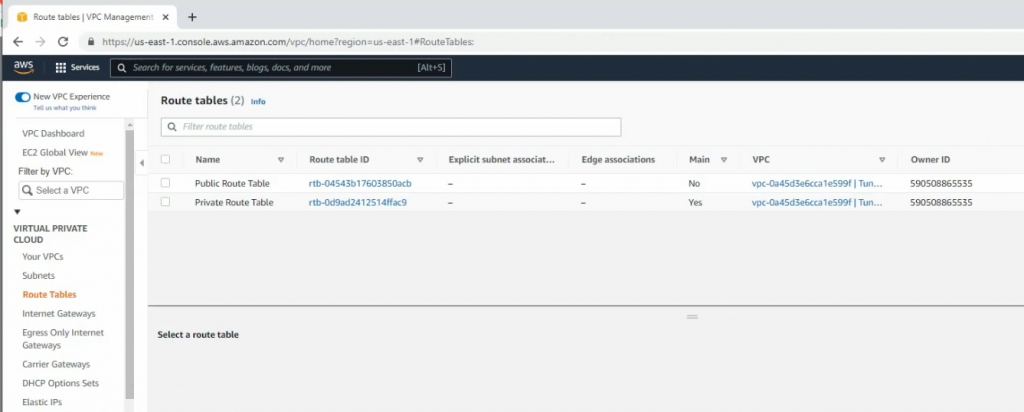
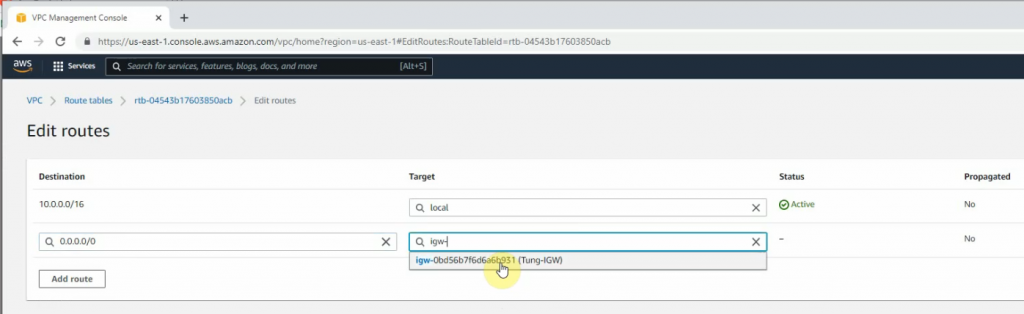
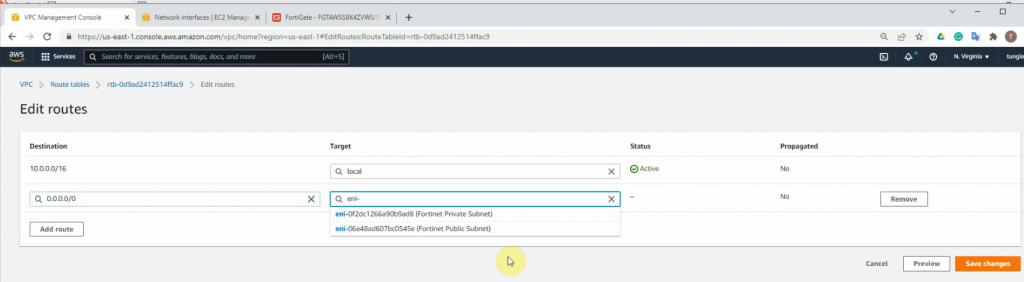
Add a new route to the public Route table.
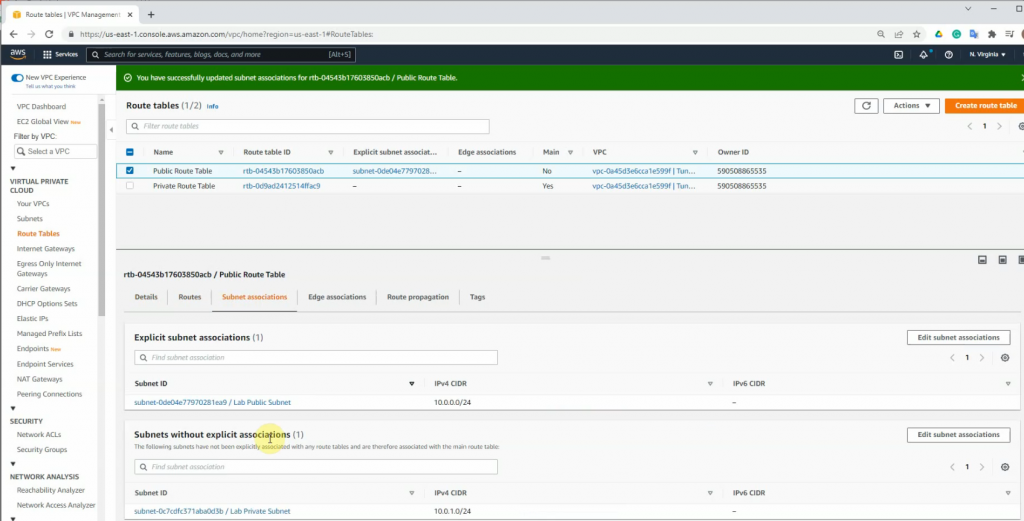
Associate the public subnet to the Public Route table.
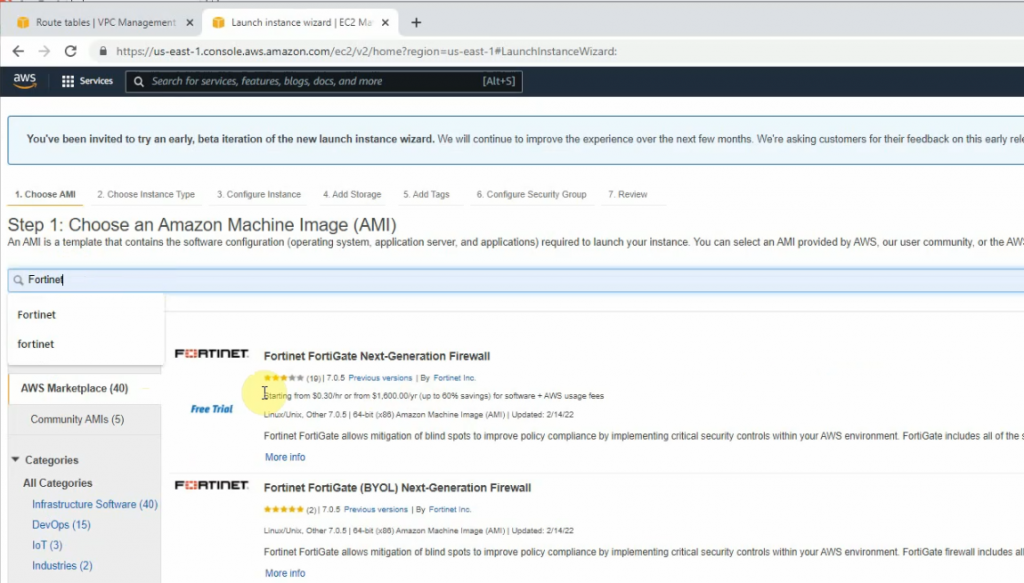
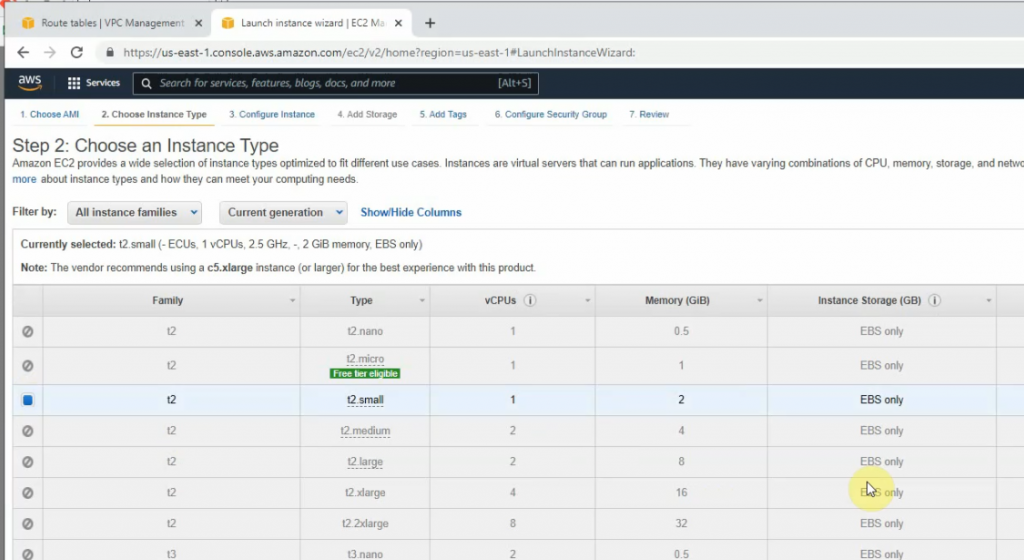
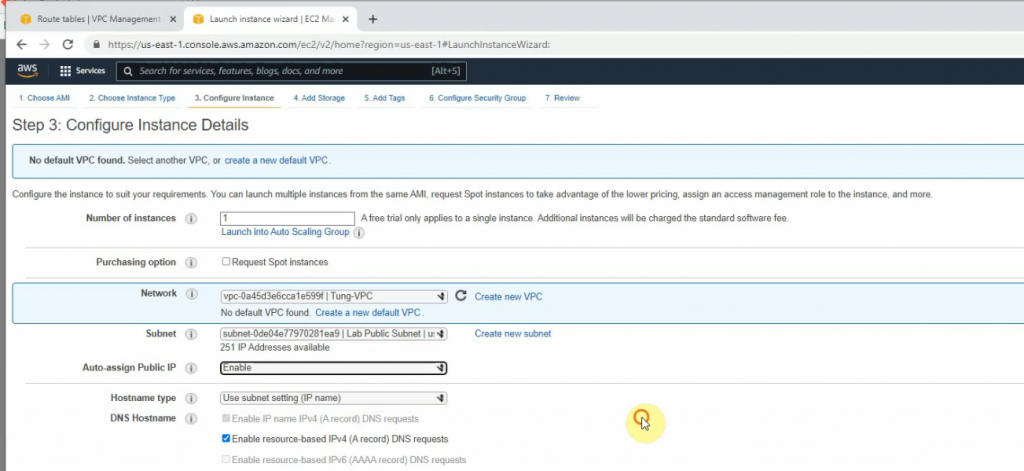
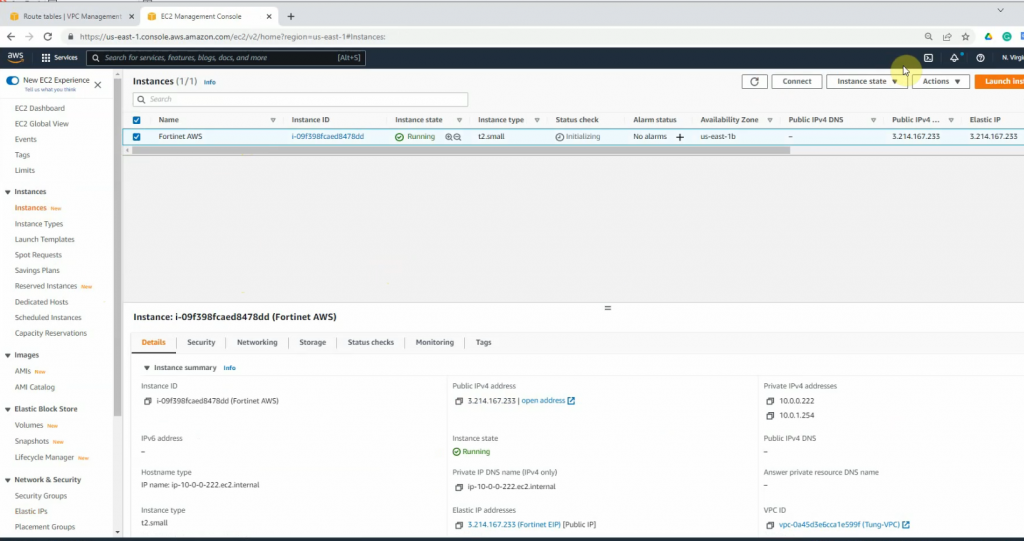
Go to EC2 and create a new FortiGate instance.
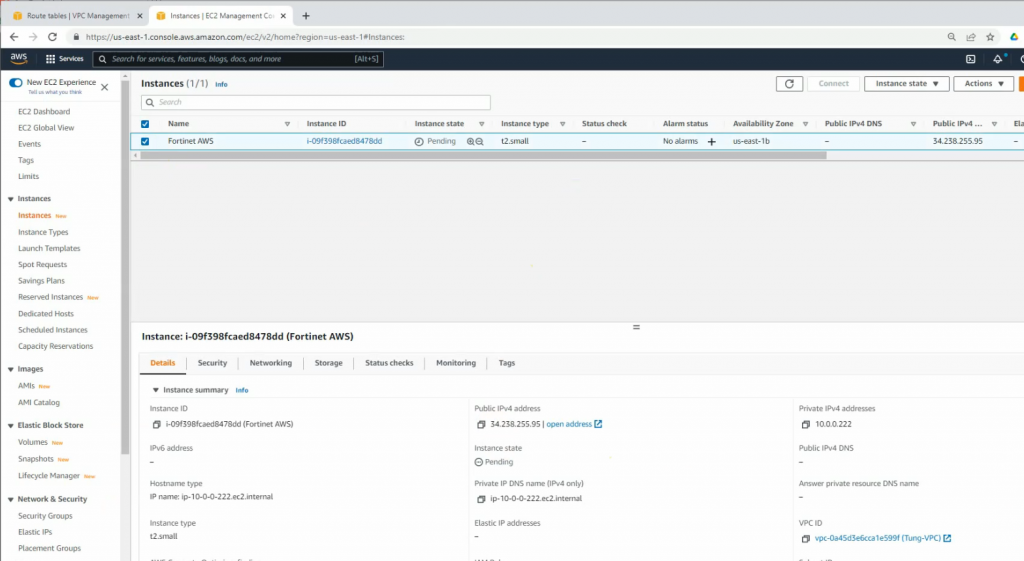
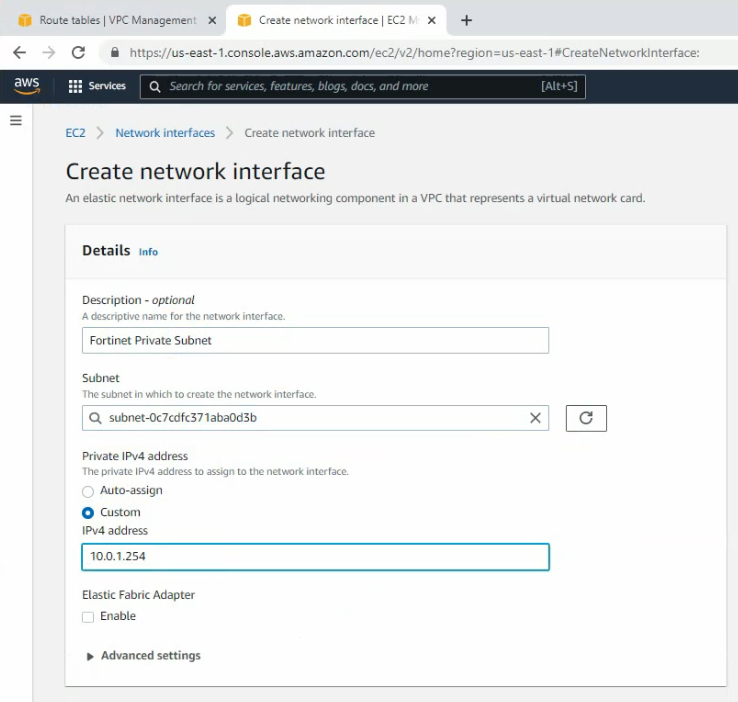
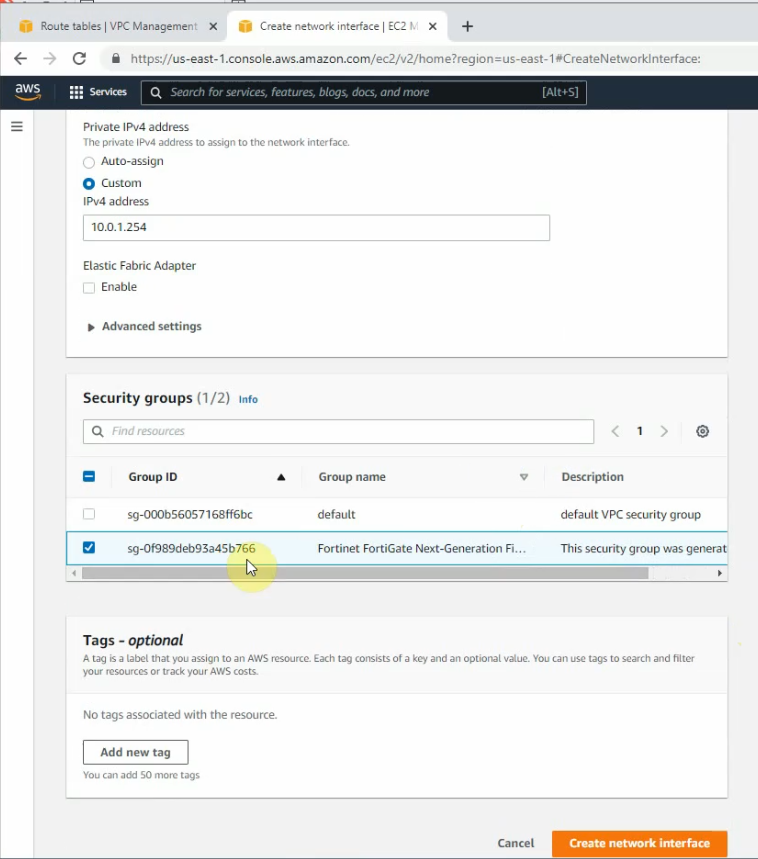
Create a new private interface for FortiGate.
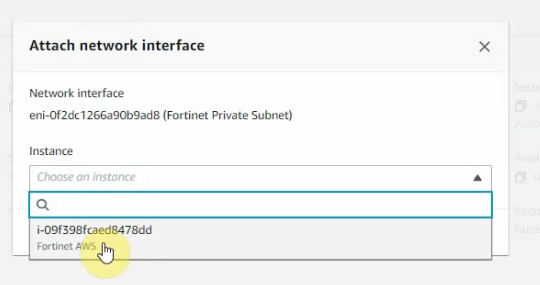
Attach the interface to FortiGate.
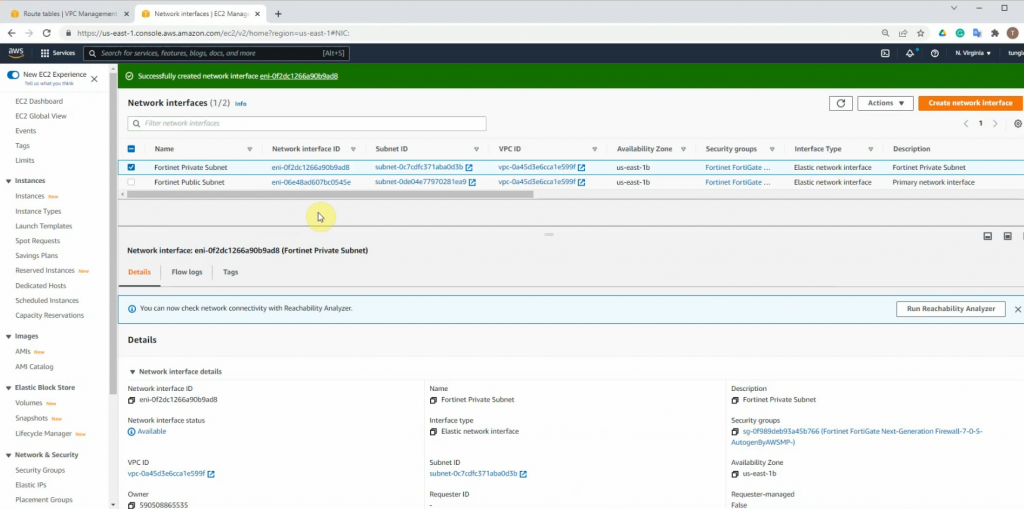
Disable “Source and destination check” on both Public and Private FortiGate interfaces.
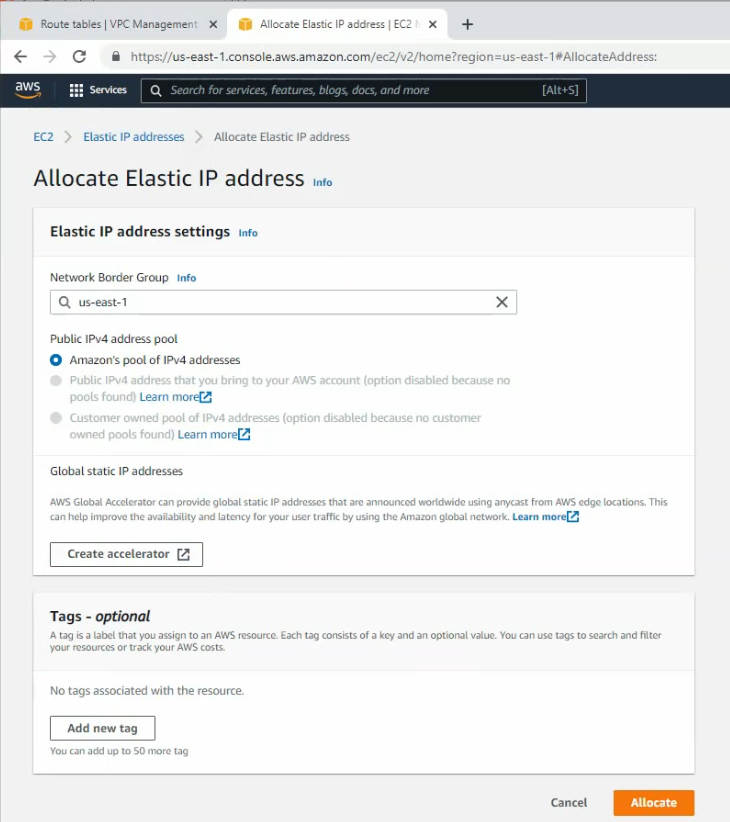
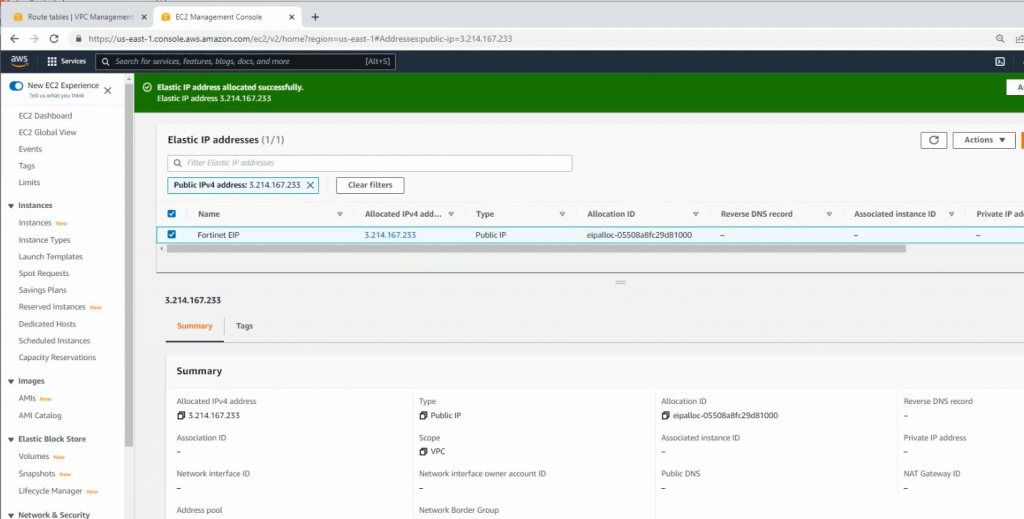
Create a new Elastic IP address and assign it to your FortiGate instance.
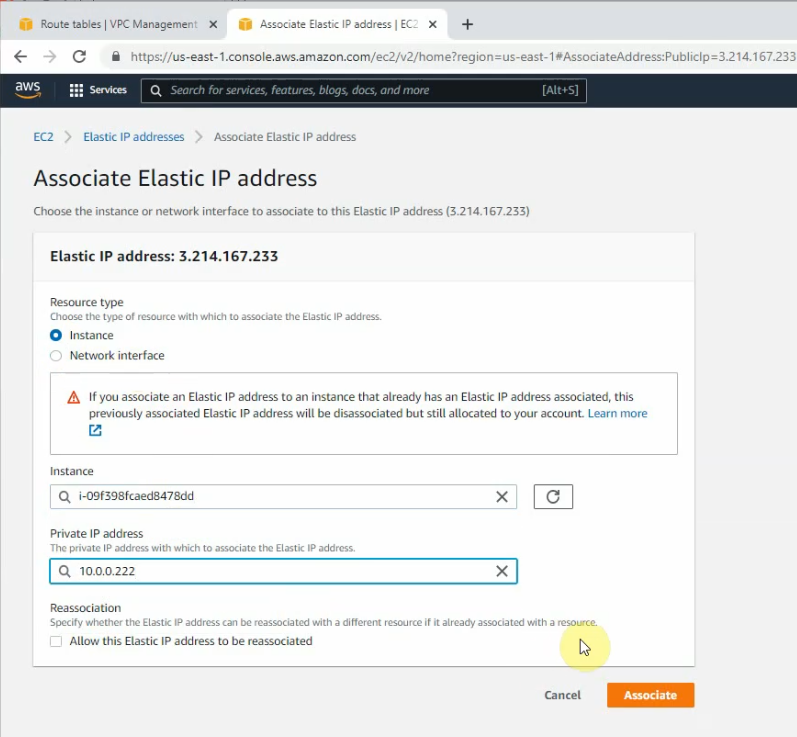
Assign the Elastic IP address to public FortiGate interface.
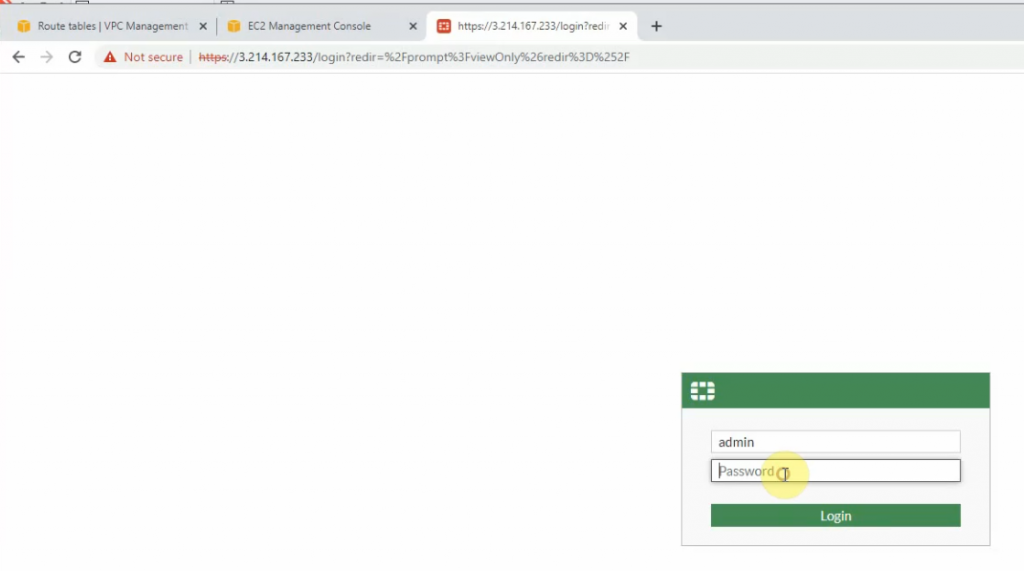
Access FortiGate management interface.
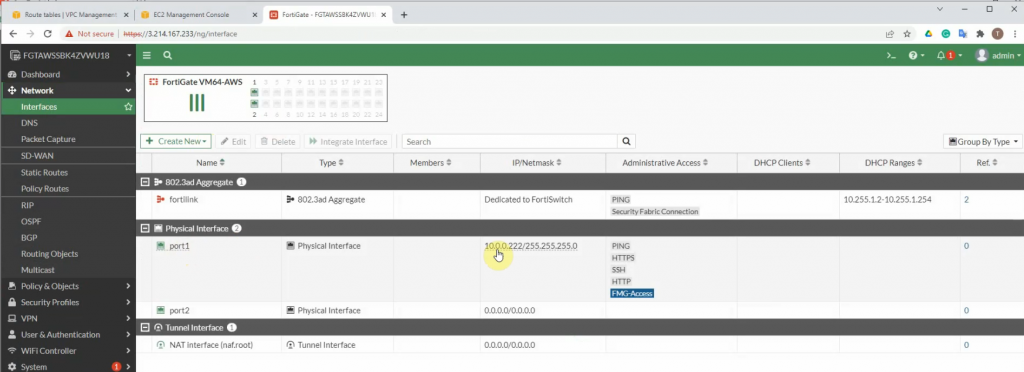
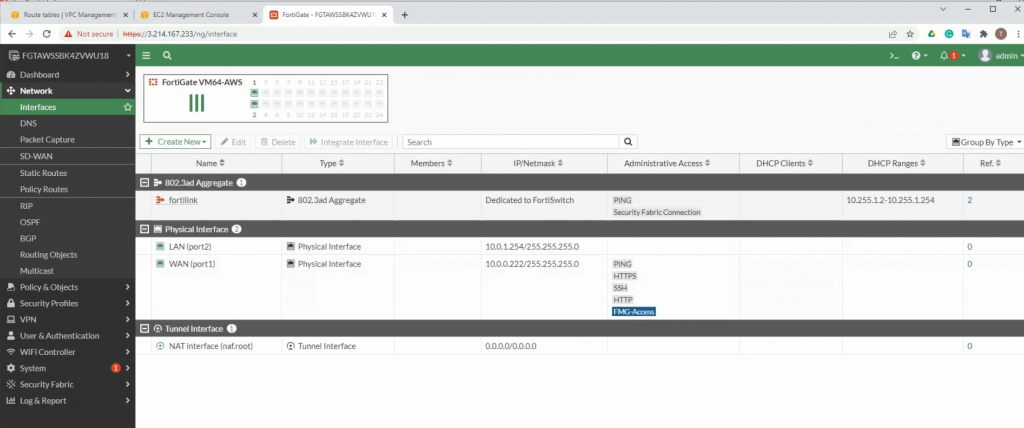
Add a new route on a Private Route table to the Private FortiGate interface.
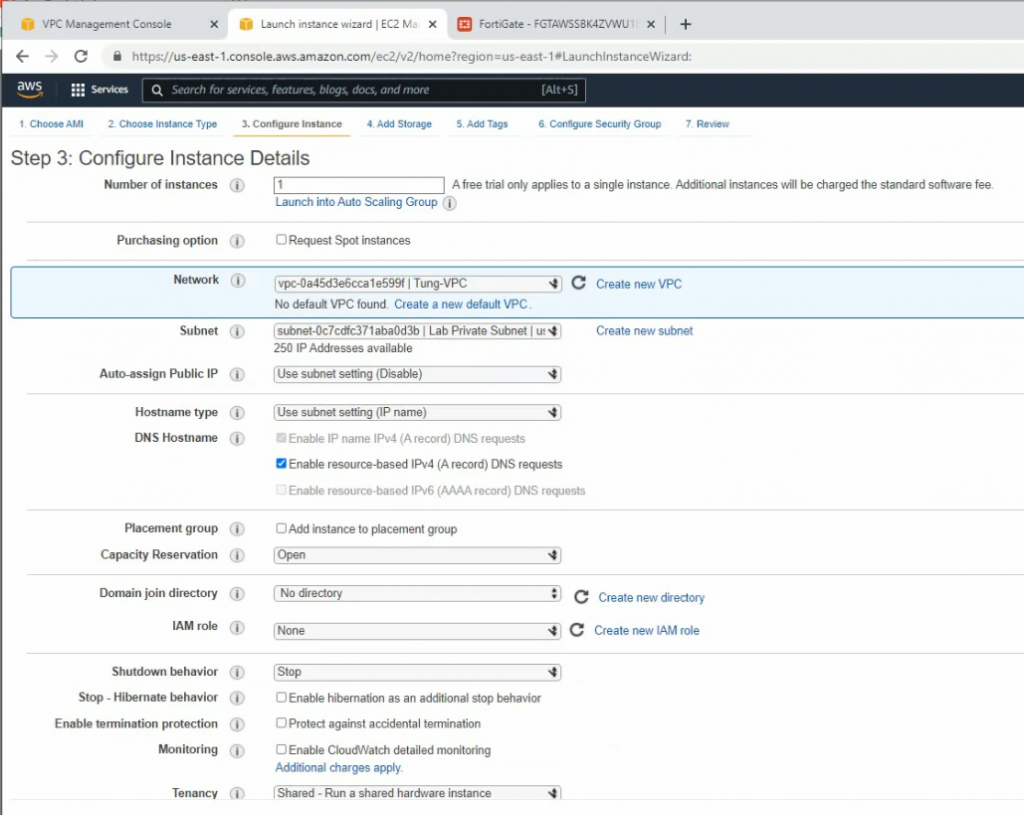
Create a new Windows instance on AWS.
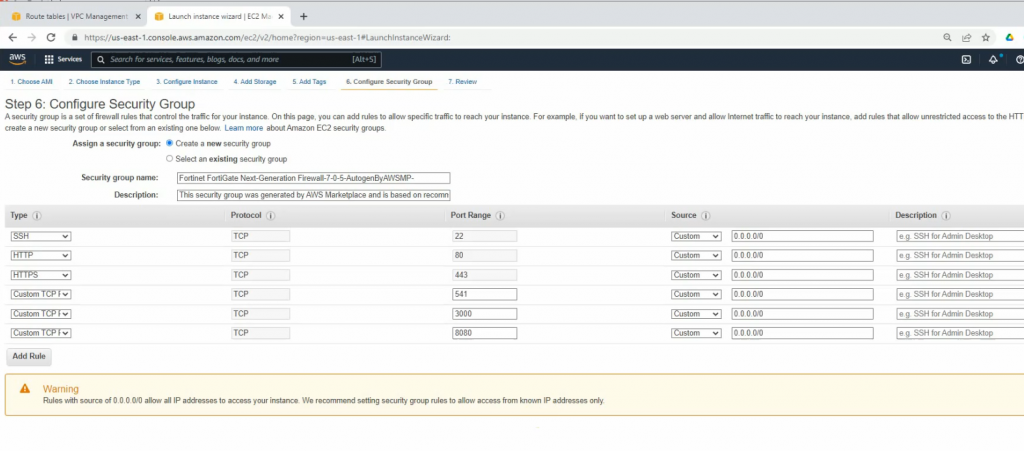
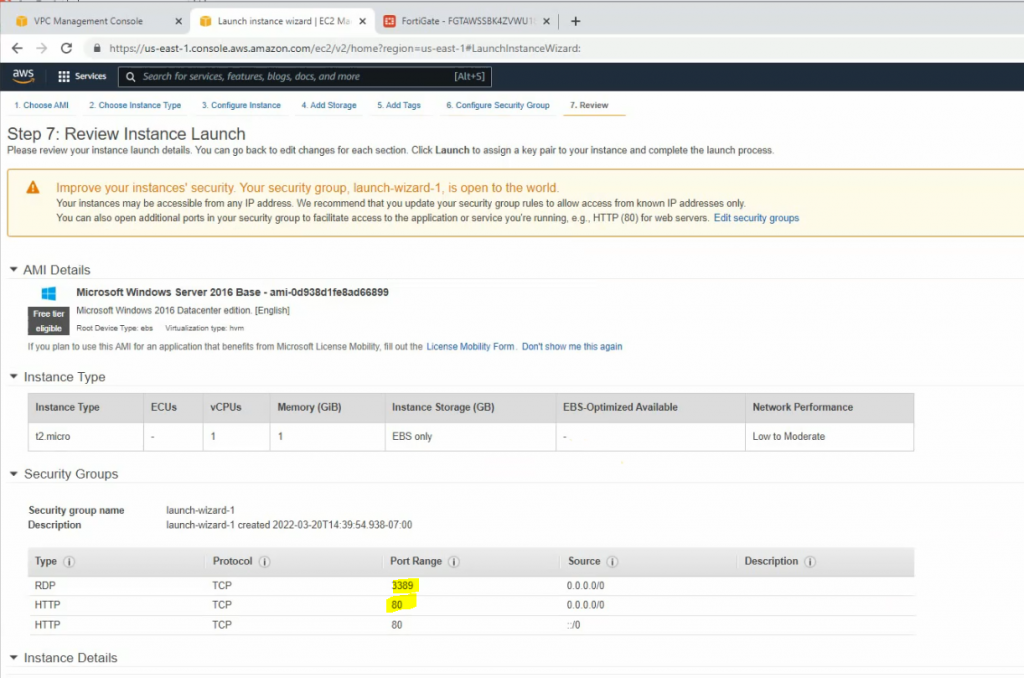
Security Group.
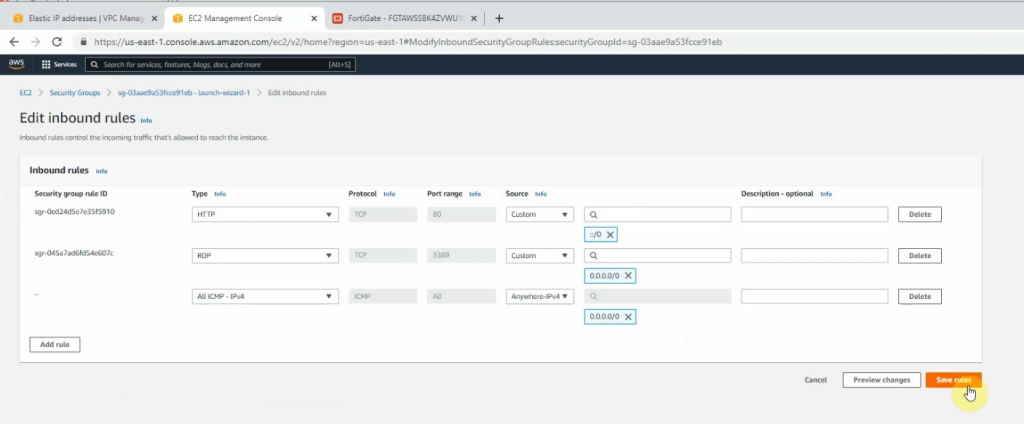
Modify Windows Security Group to allow ICMP traffic.
Configure VPN site to site.
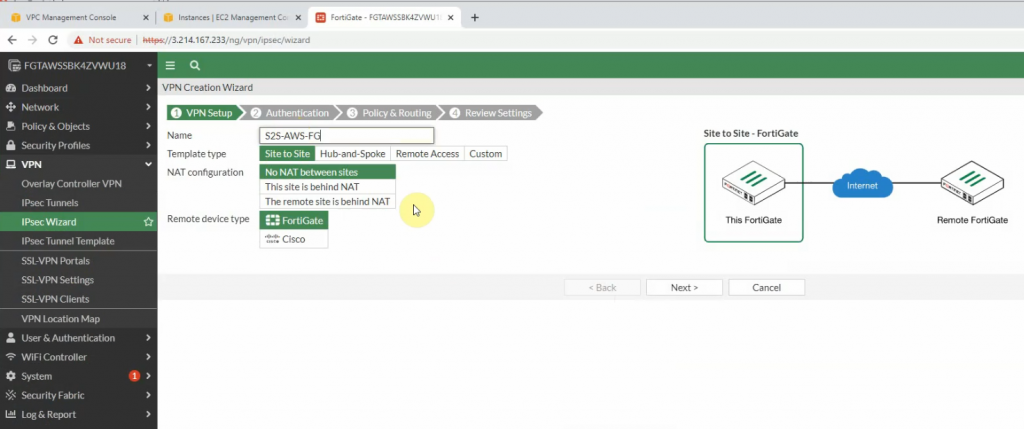
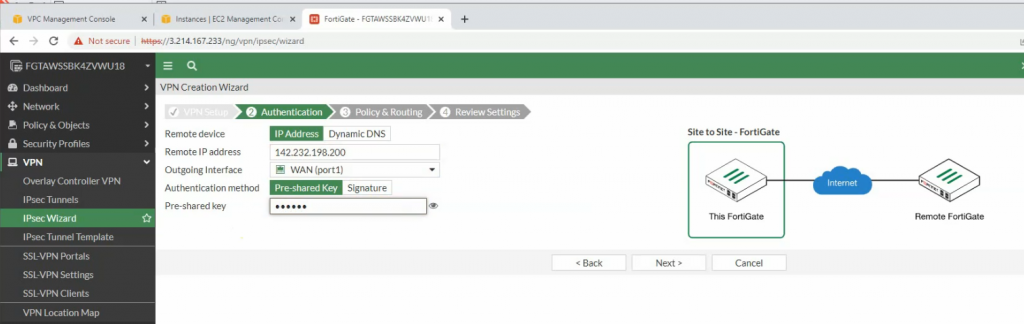
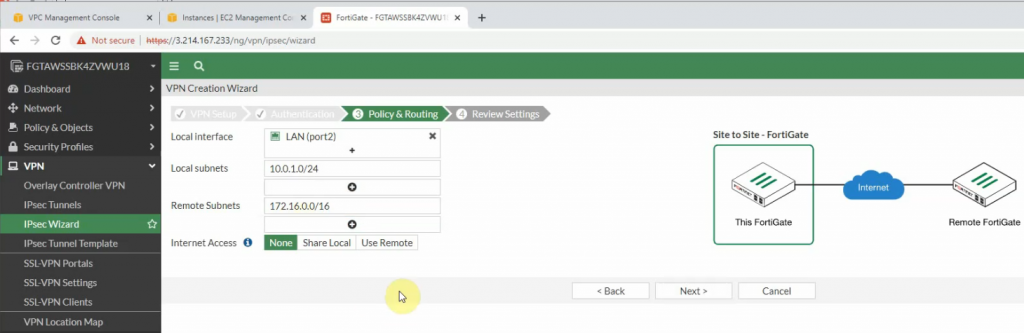
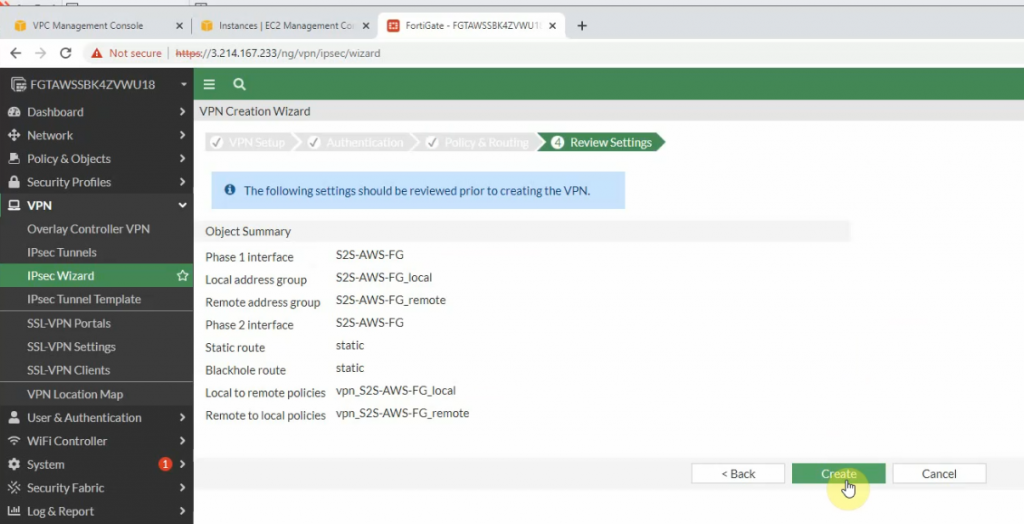
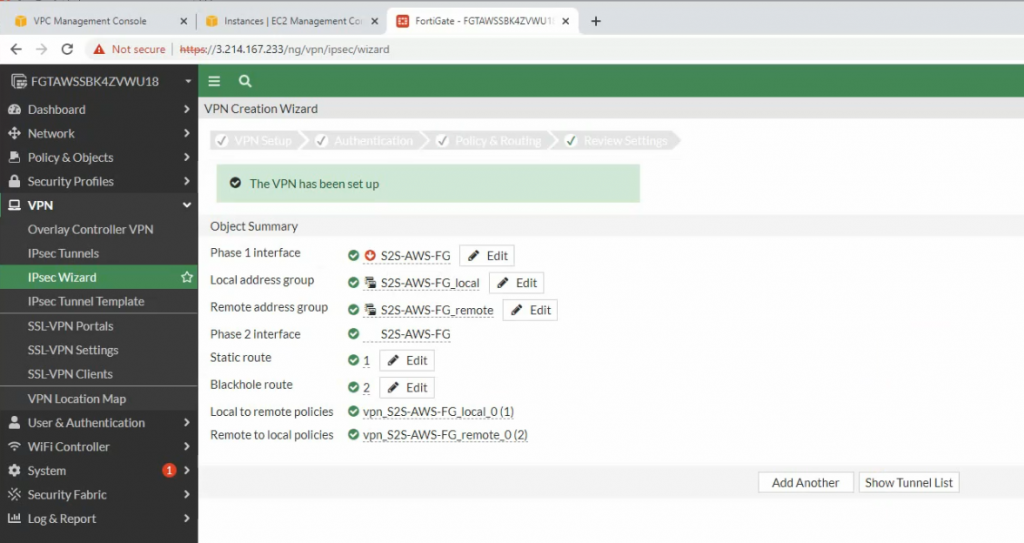
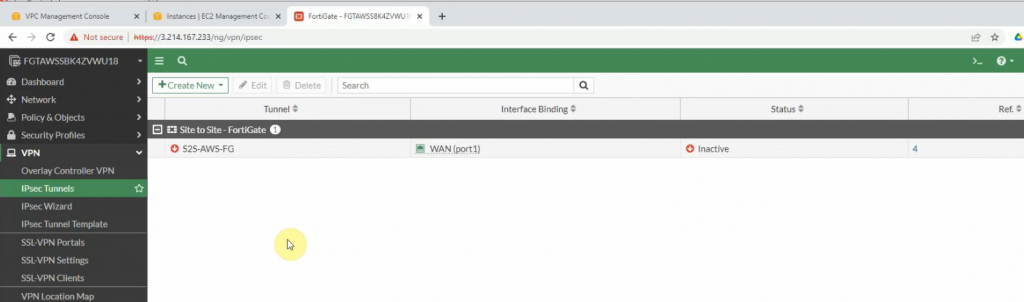
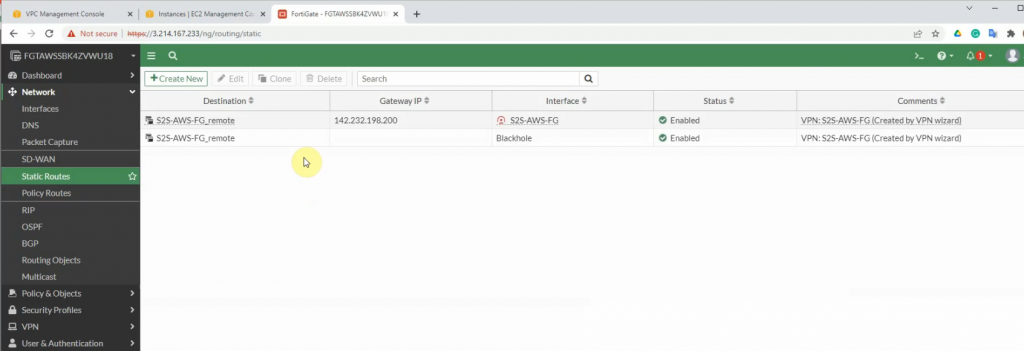
There are two routes that have been automatically created on FortiGate on the static routes setting.
+ Configure FortiGate on-prem.
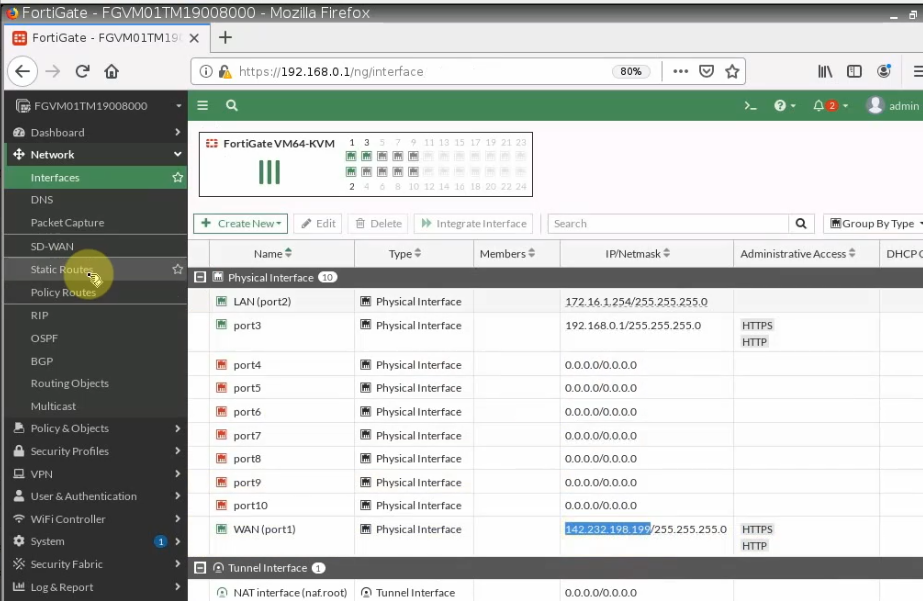
Configure a default route on FortiGate.
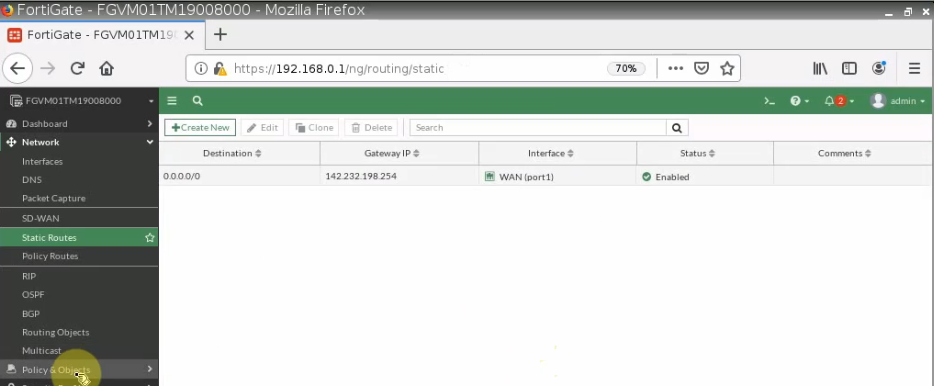
Configure VPN site to site between both FortiGate.
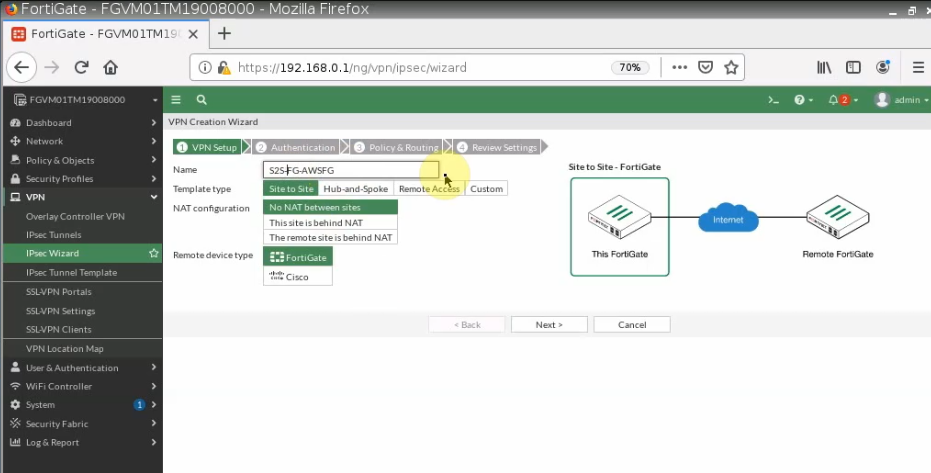
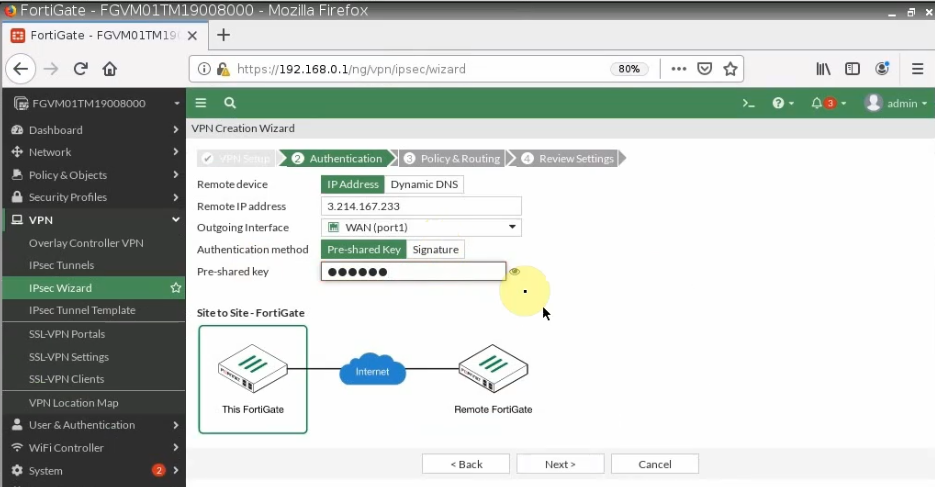
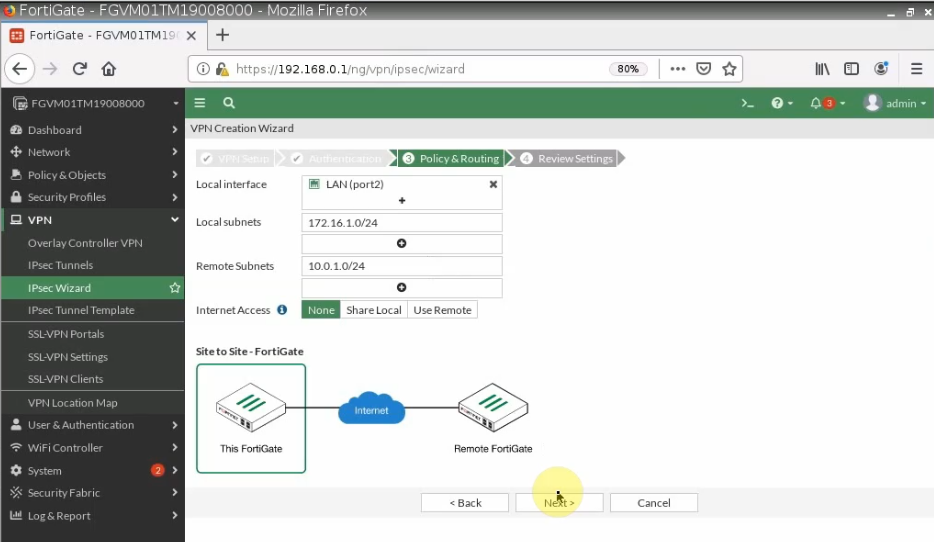
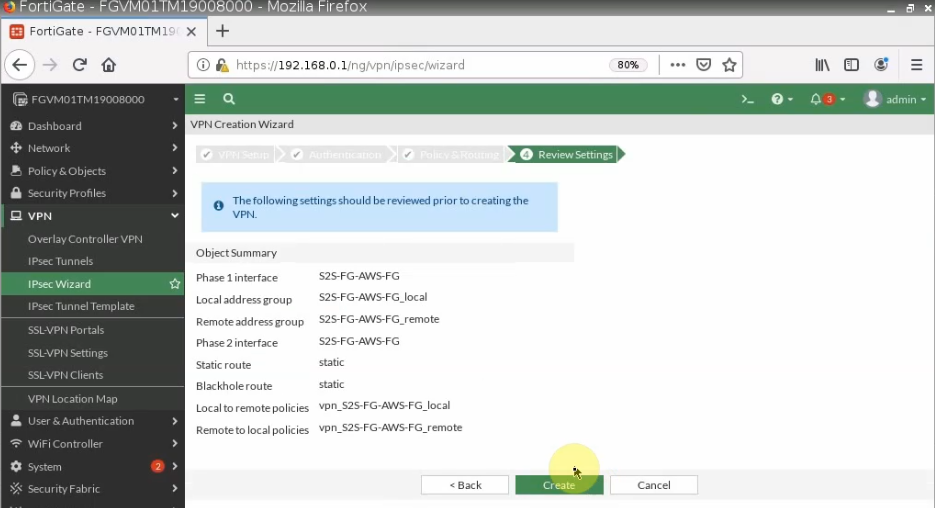
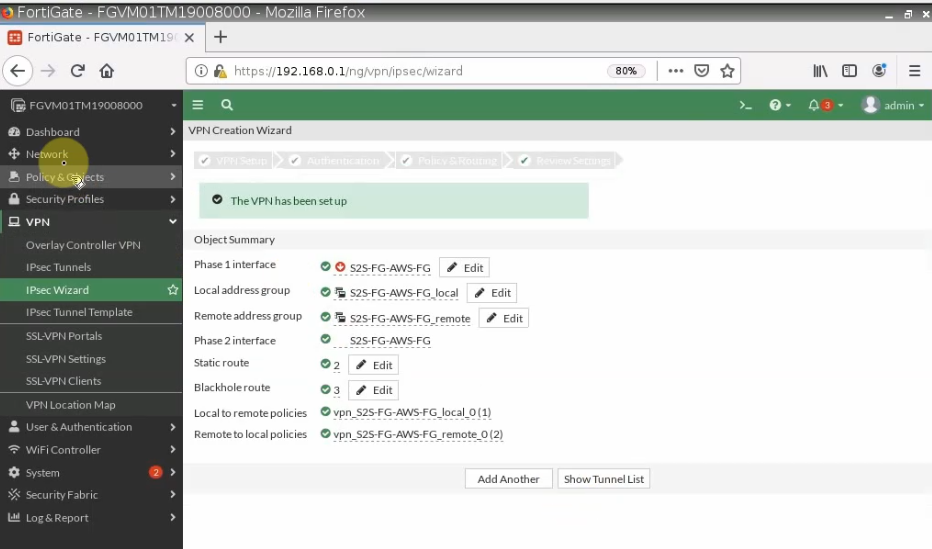
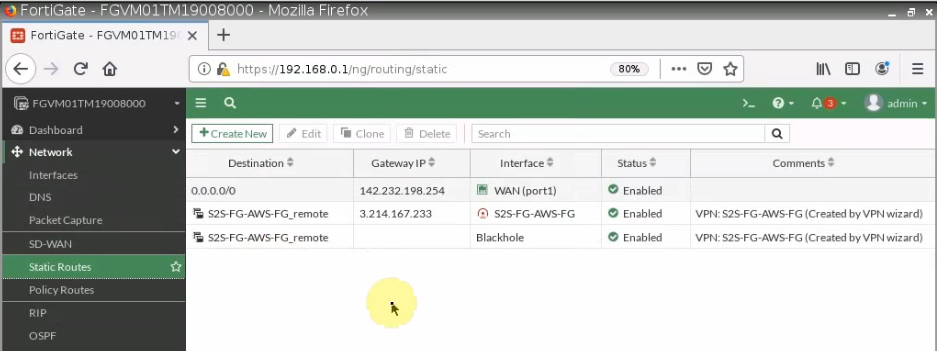
+ Pings a Windows instance on AWS from a machine on FortiGate on-prem. Remember to access RDP to the machine and disable Windows Firewall to allow ICMP traffic from on-prem to that machine.
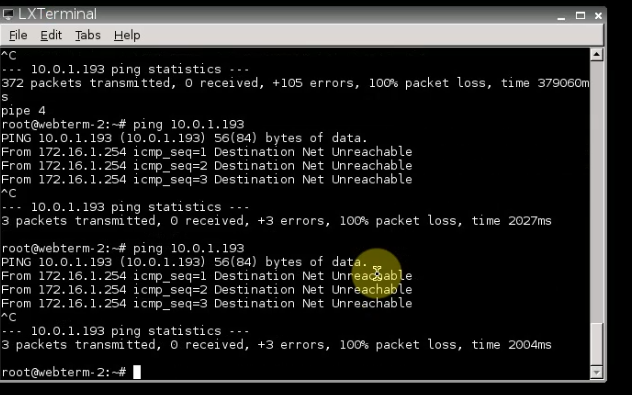
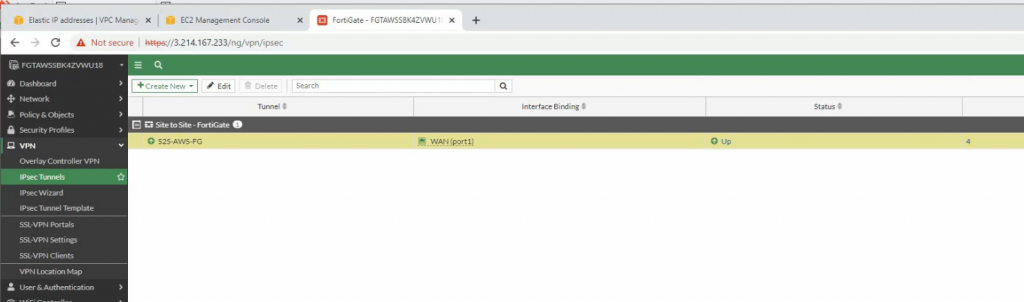
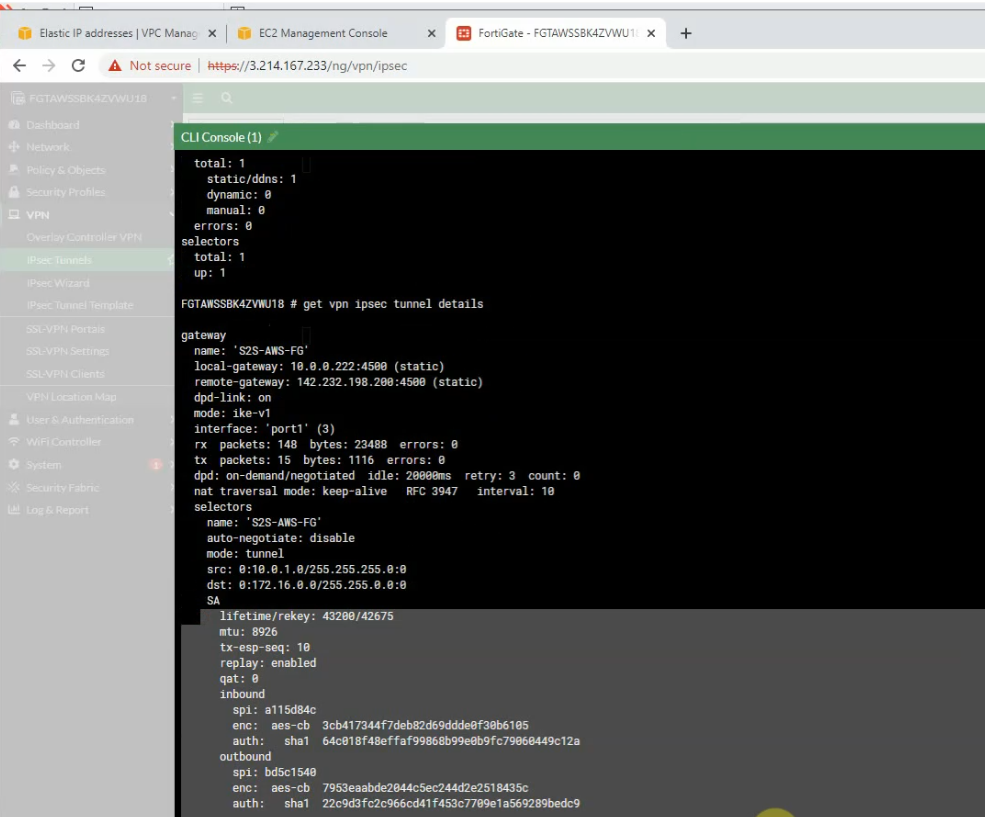
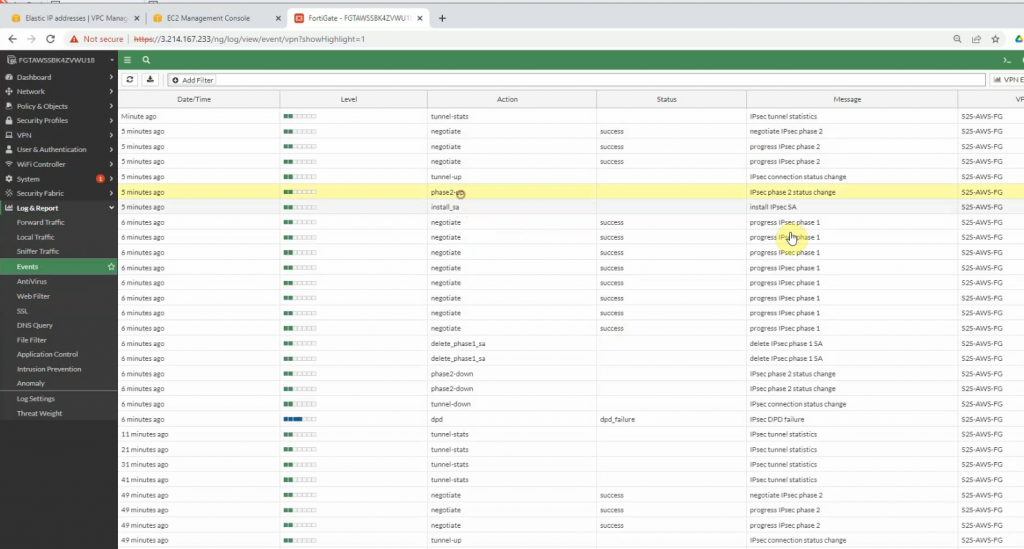
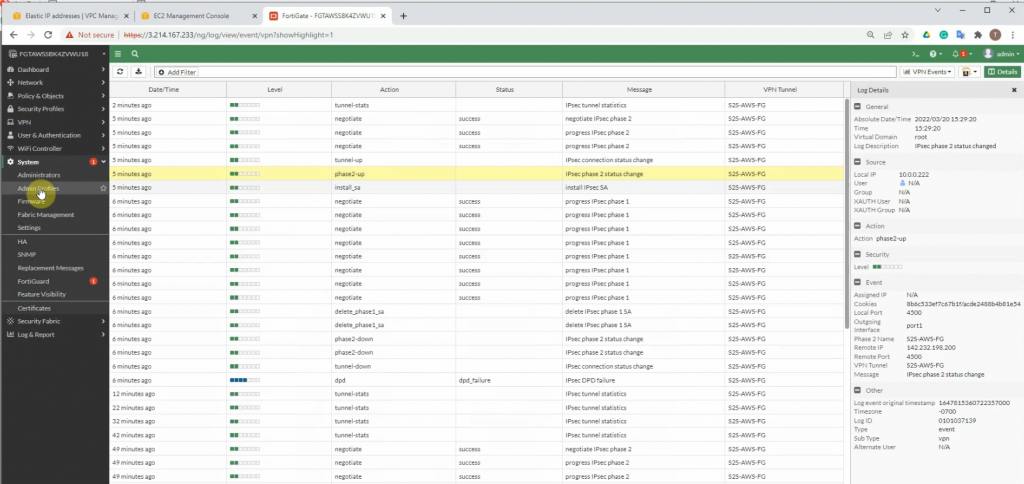
The IPSEC tunnel is up.
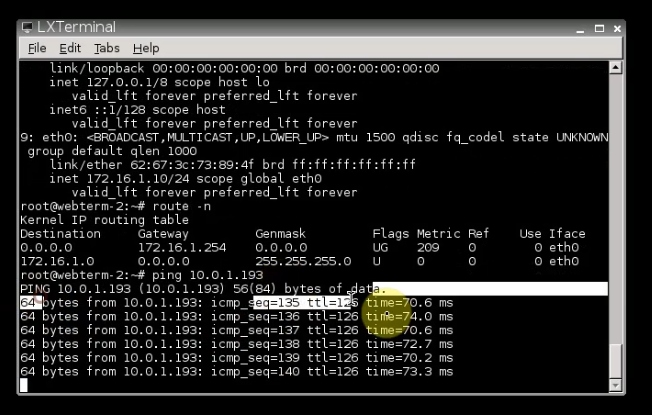
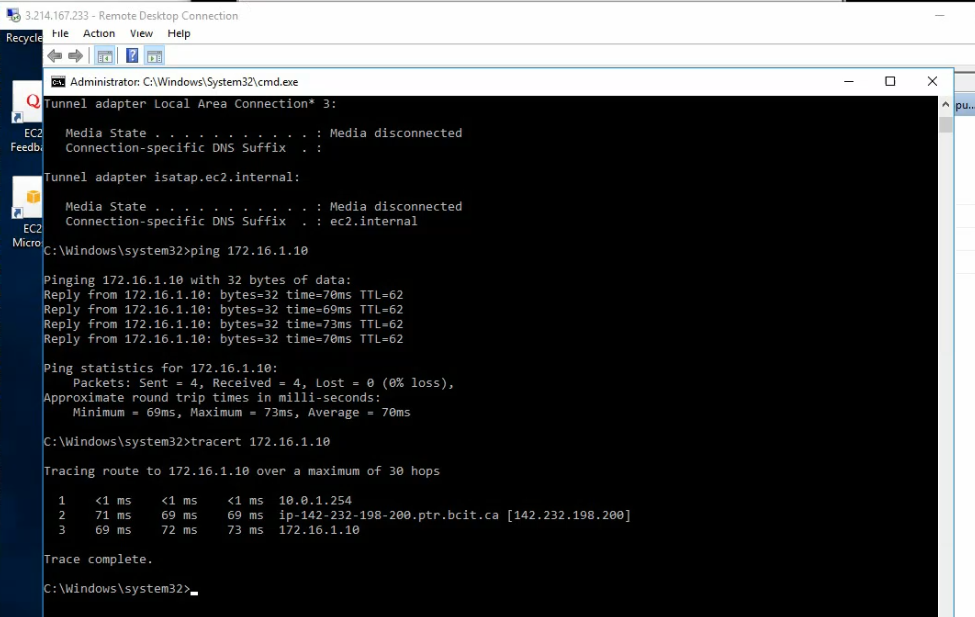
Pings from Windows instance on AWS to a computer on FortiGate LAN subnet on-prem.
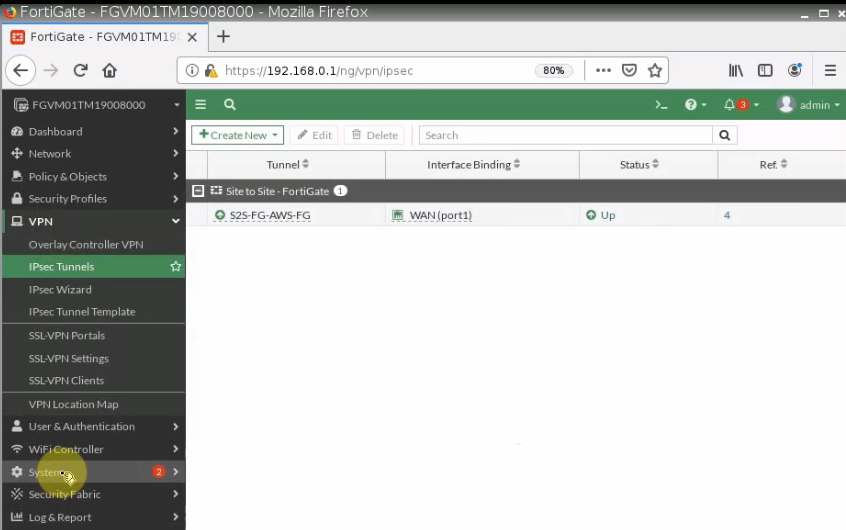
The IPSEC tunnel on-prem is up.
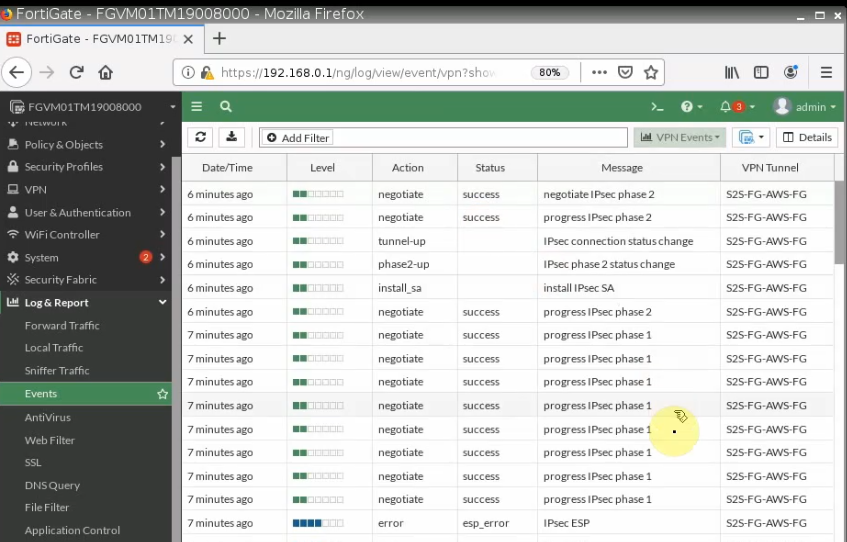
+ Configure SSLVPN portal on FortiGate on AWS.