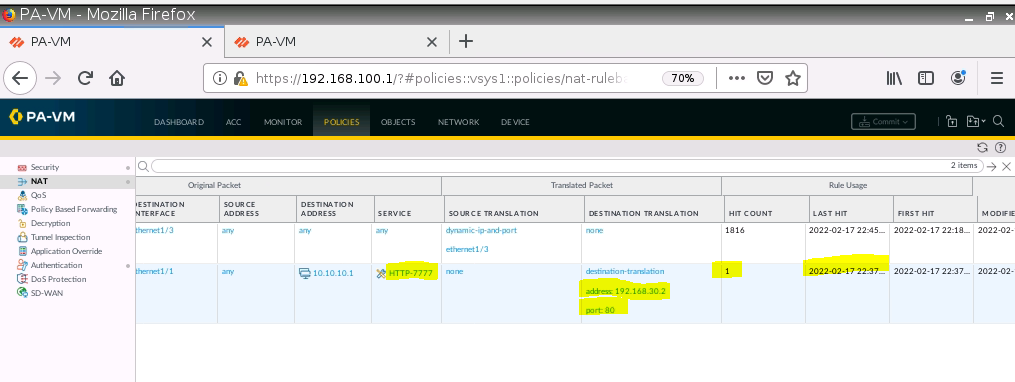
This is a topology that I have used in this lab.
+ Set up IPSEC site to site between both PAs.
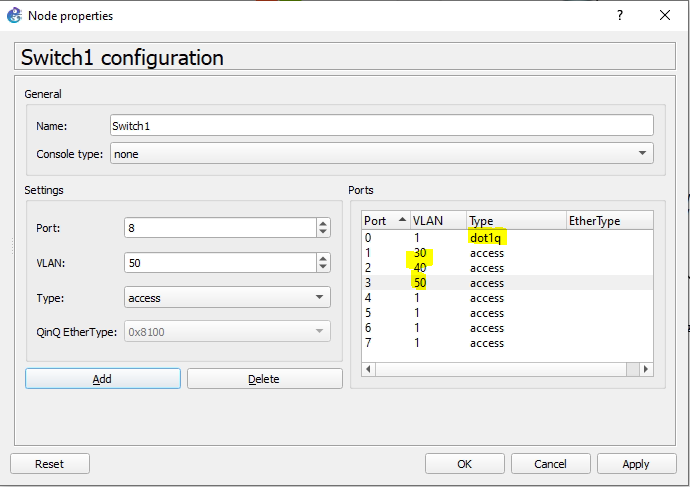
+ Configure Switch support multiple VLANs.
+ Configure DHCP service to multiple VLANs.
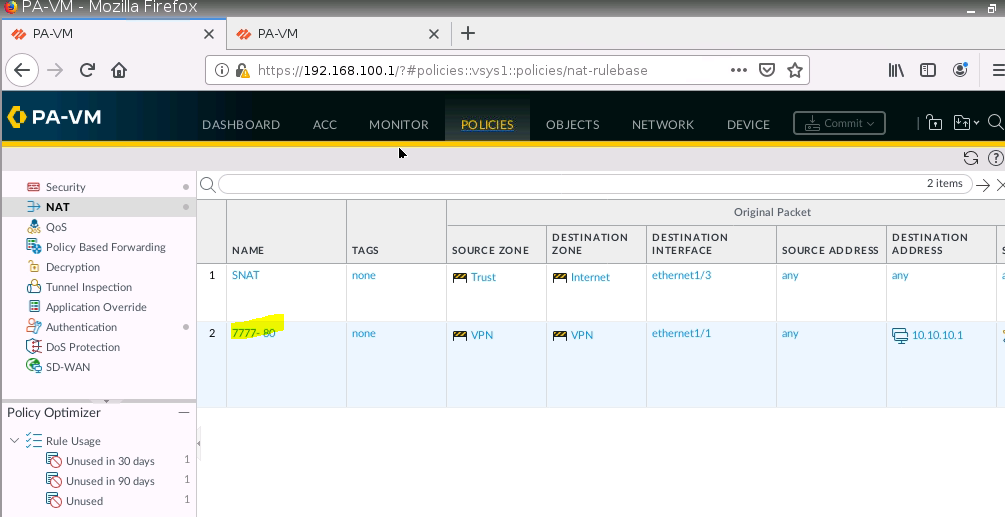
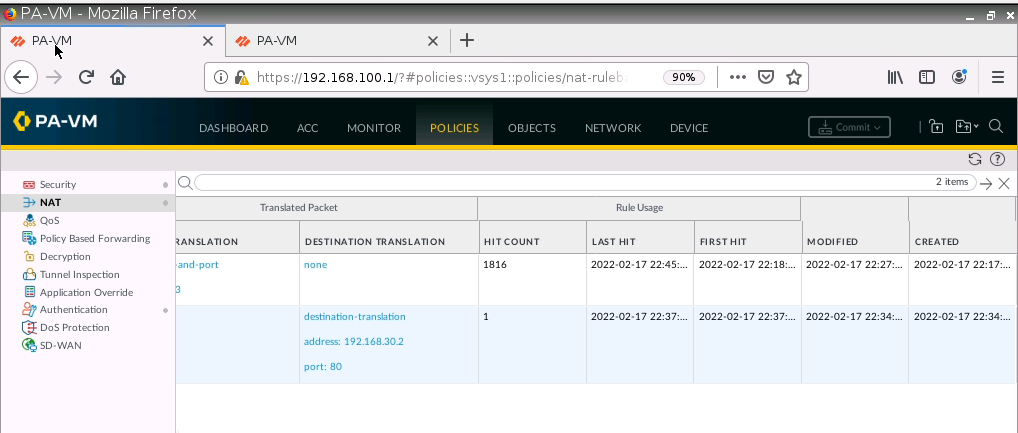
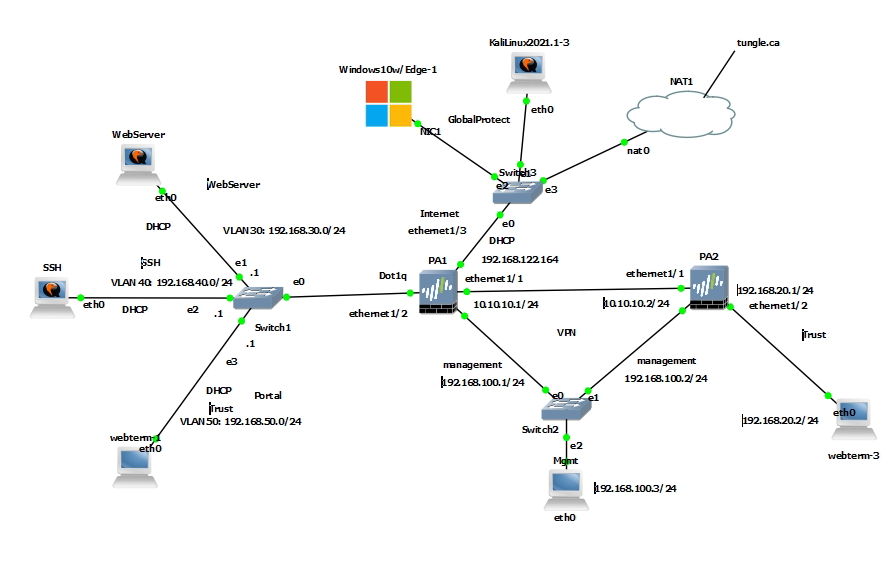
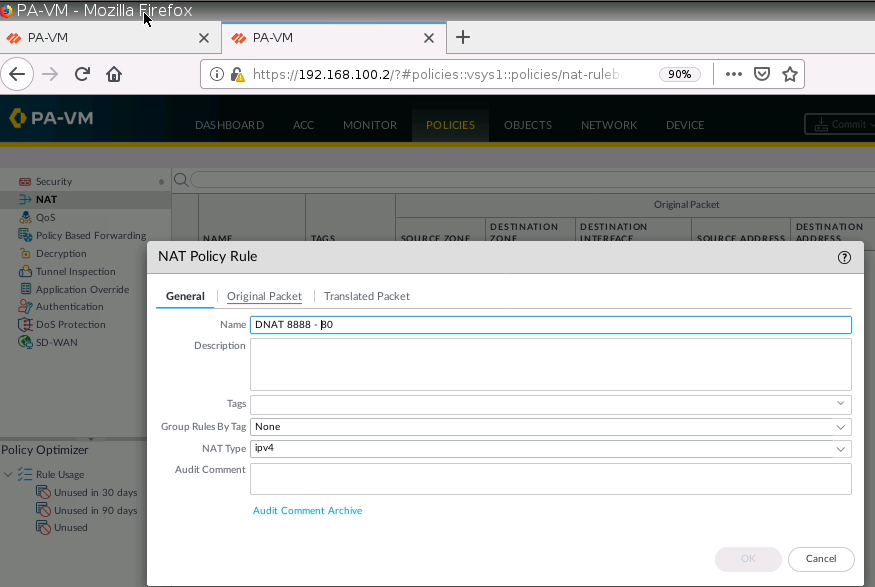
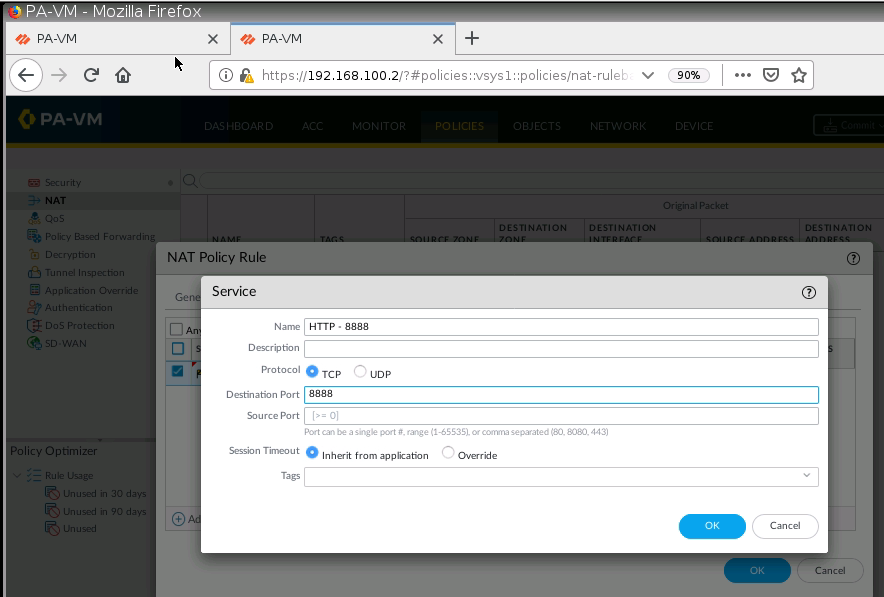
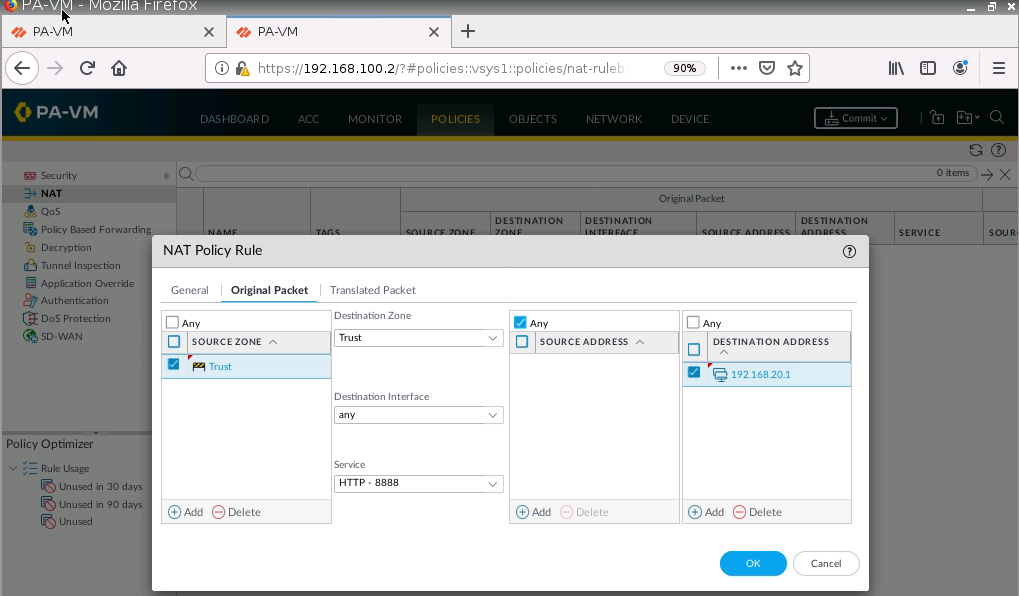
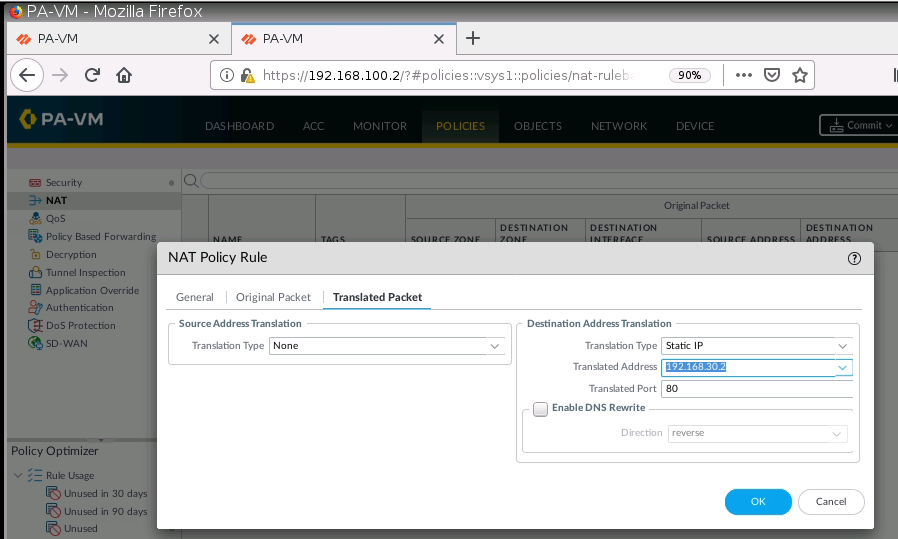
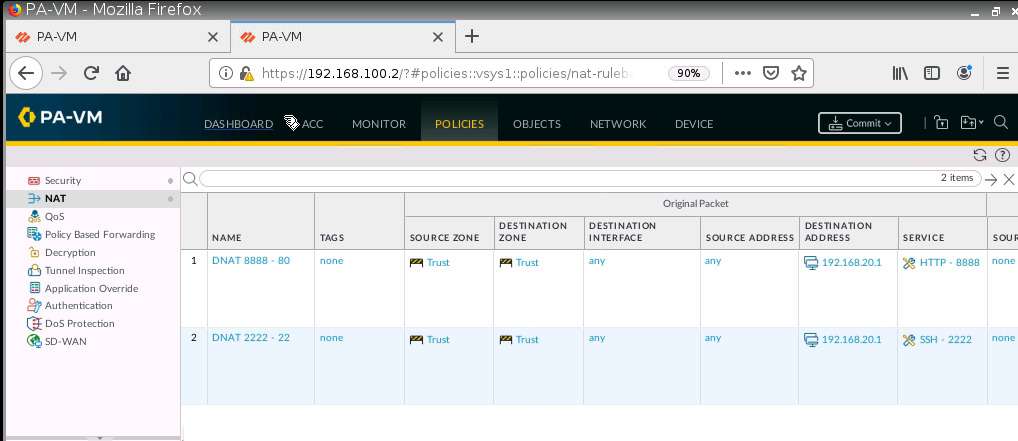
+ Configure DNAT on PA2 (192.168.20.1) to NAT to Webserver on Kali (192.168.30.2), then change to configure DNAT on PA2 (192.168.20.1:8888) to NAT to Webserver on Kali (192.168.30.2:80).
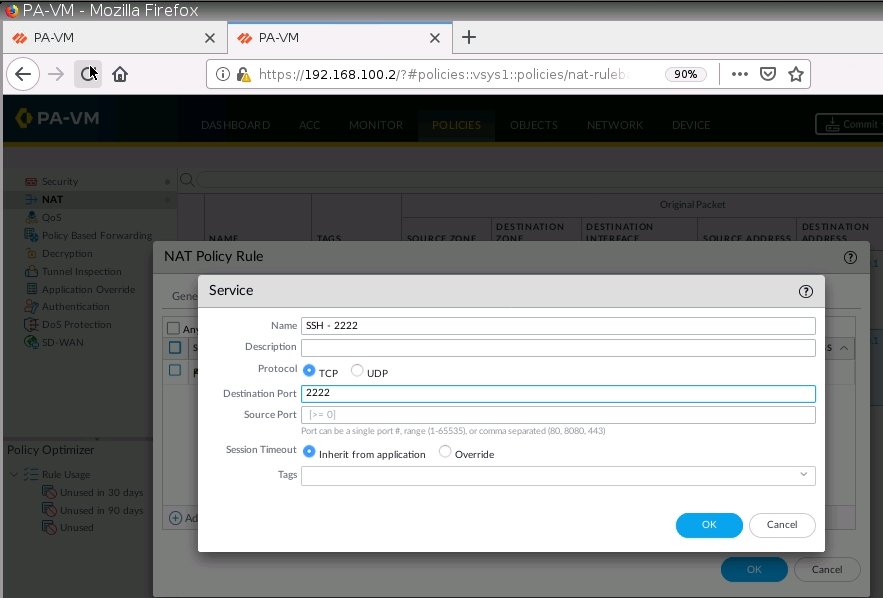
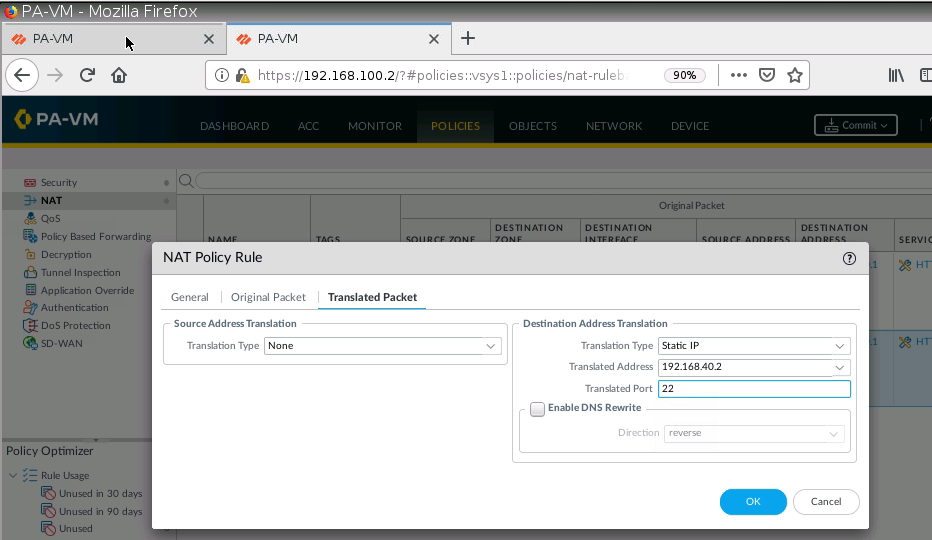
+ Configure DNAT on PA2 to SSH server on 192.168.40.2:22, and change (192.168.20.1:2222) to NAT to SSH server on Kali (192.168.40.2:22).
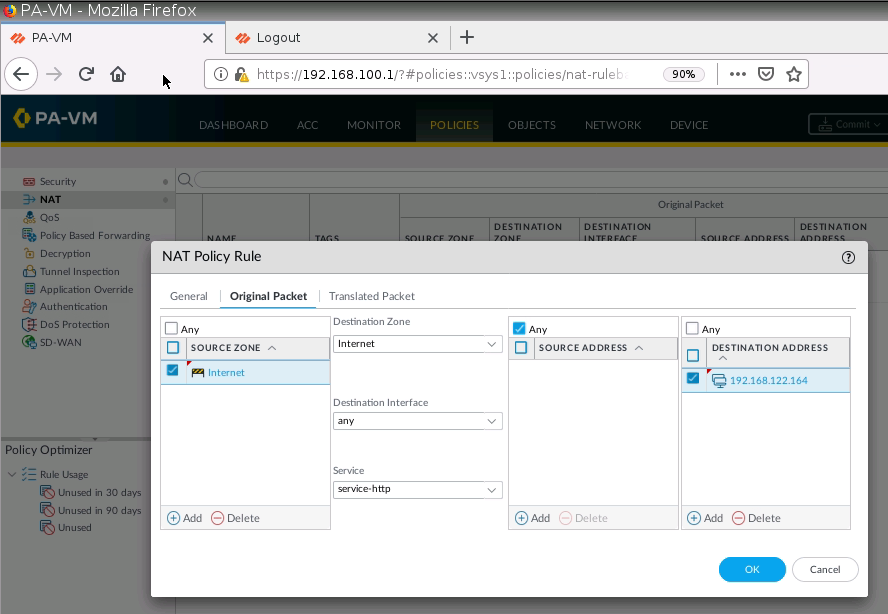
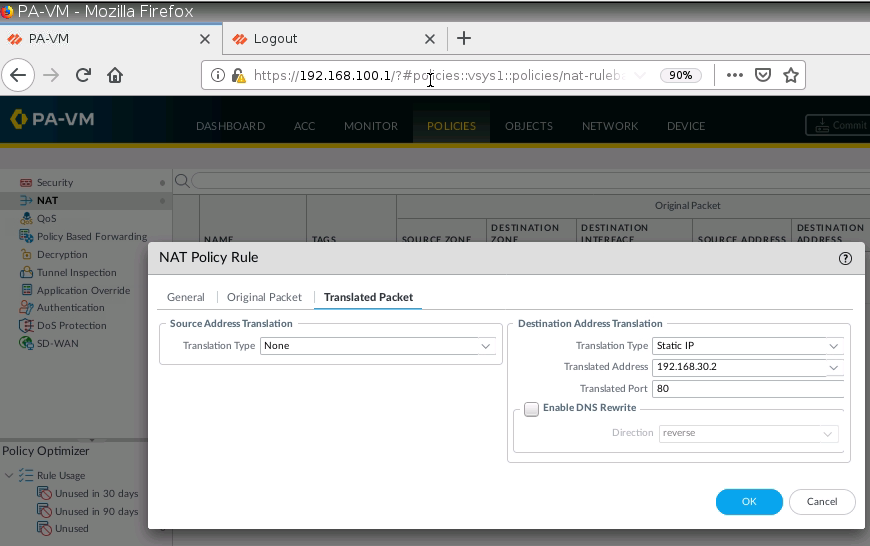
+ Configure DNAT to allow traffic from the Internet to the local Web server (DNAT).
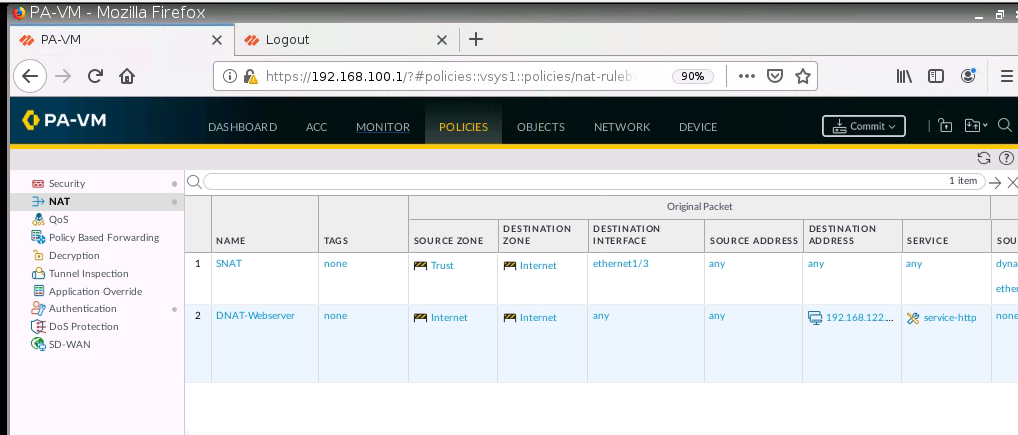
+ Configure SNAT to allow Trust on PA1 to access the Internet.
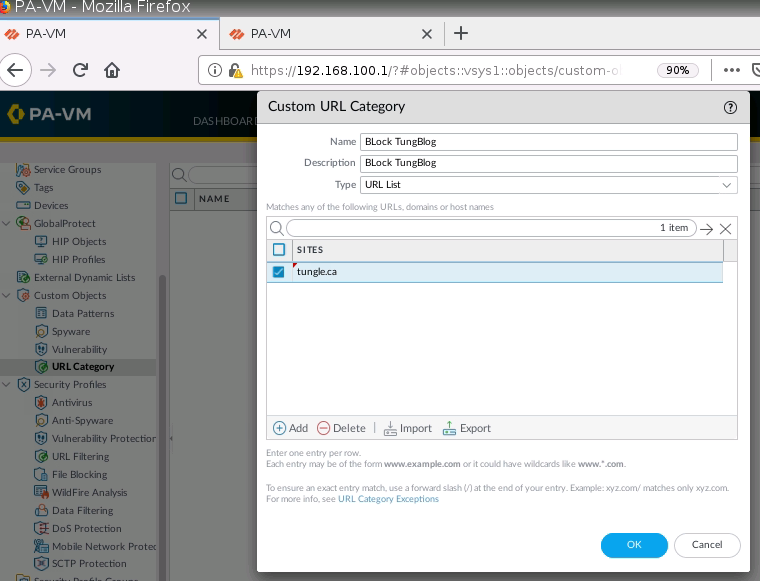
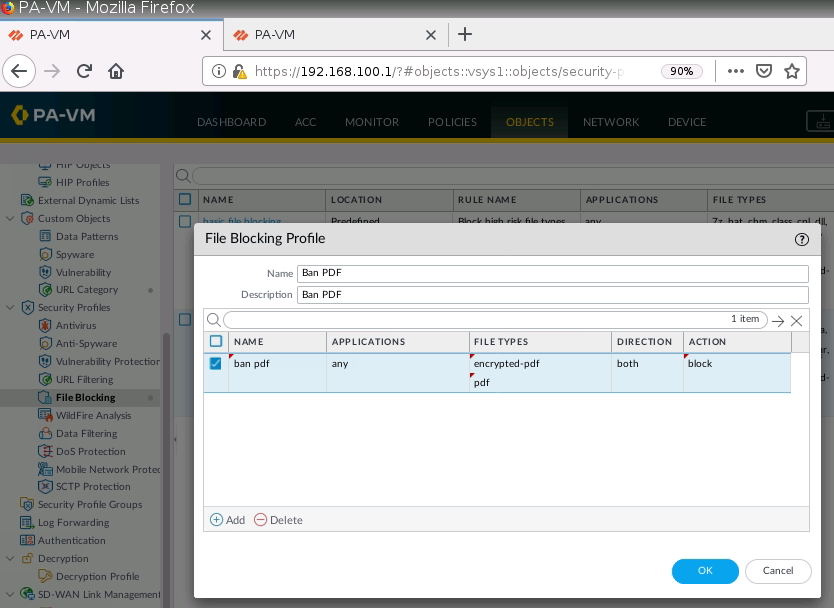
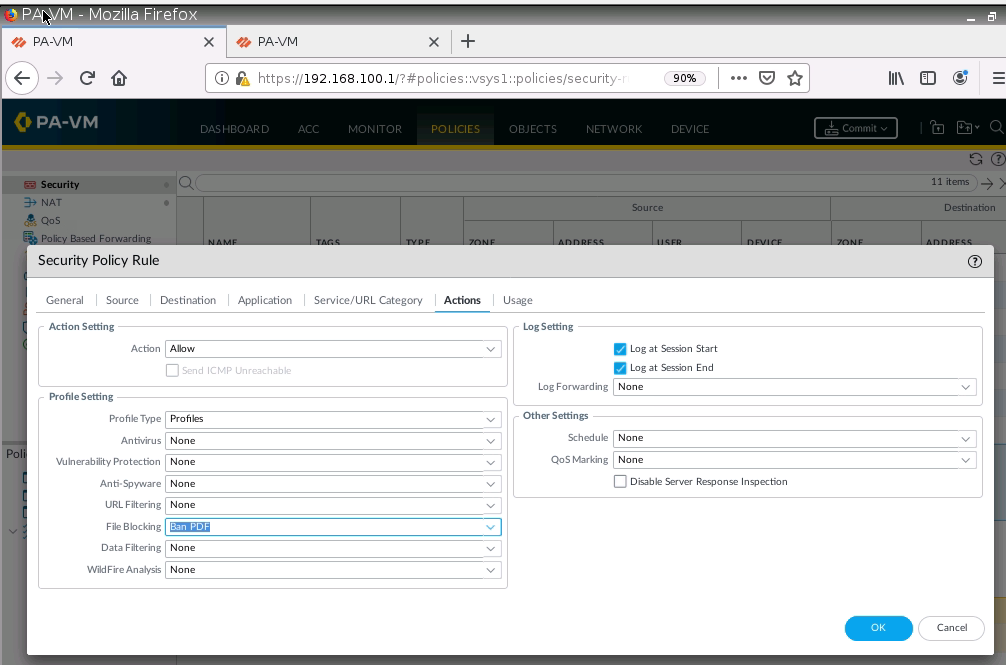
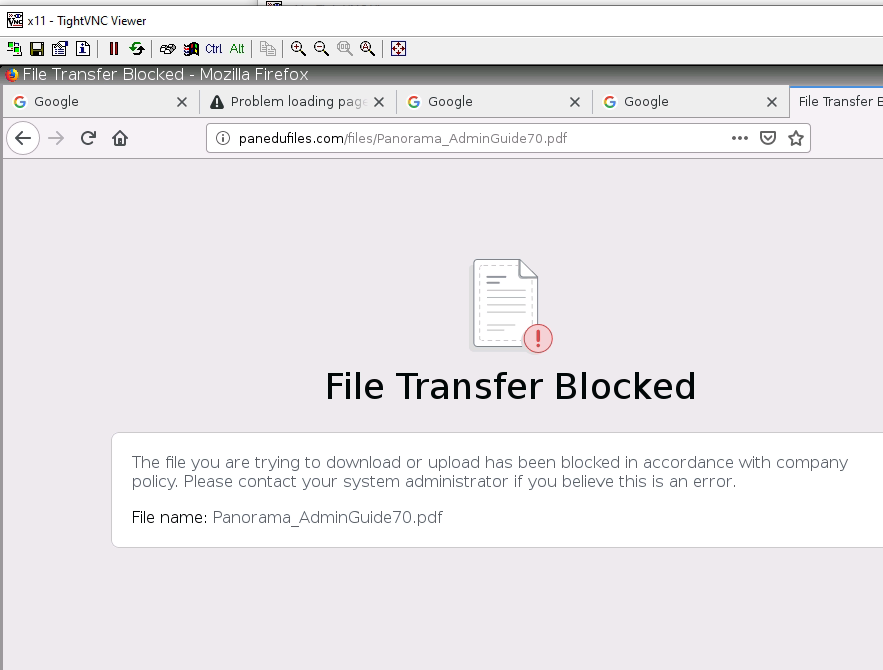
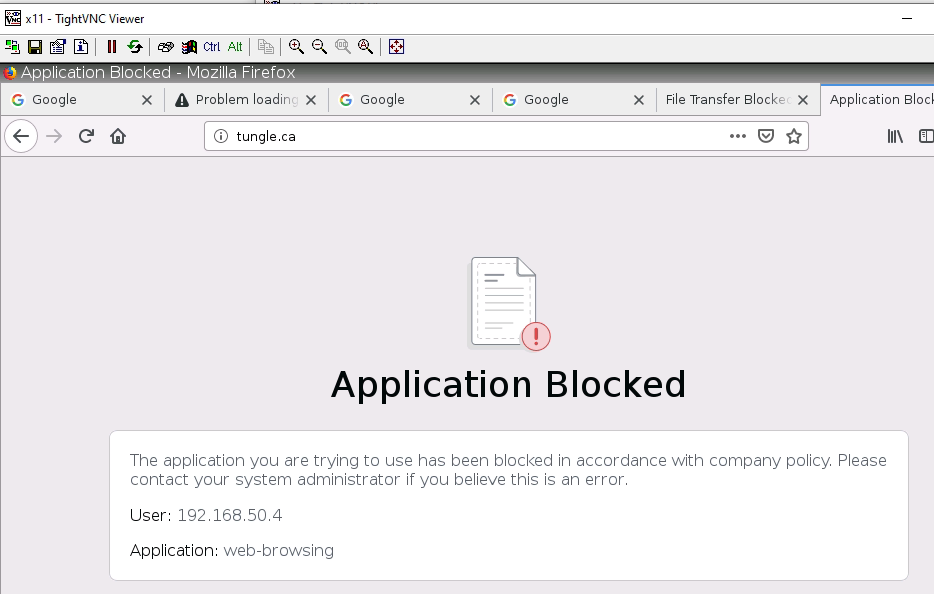
+ Ban on accessing pdf files, and block on accessing to tungle.ca domain (URF filtering).
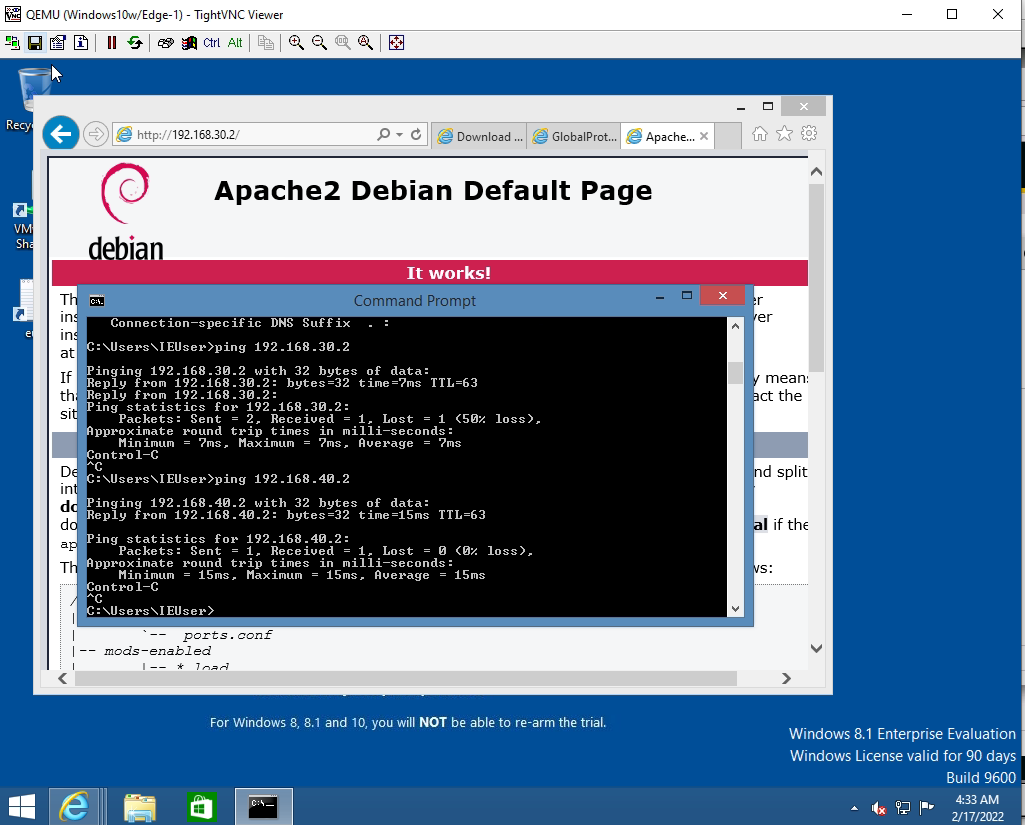
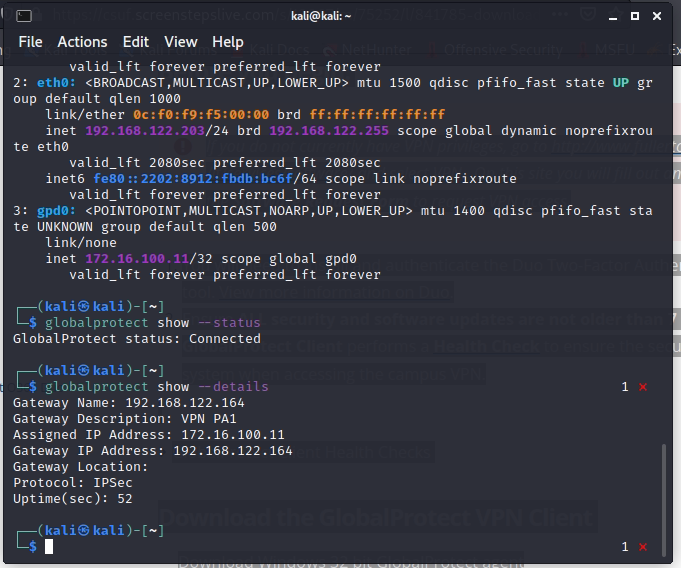
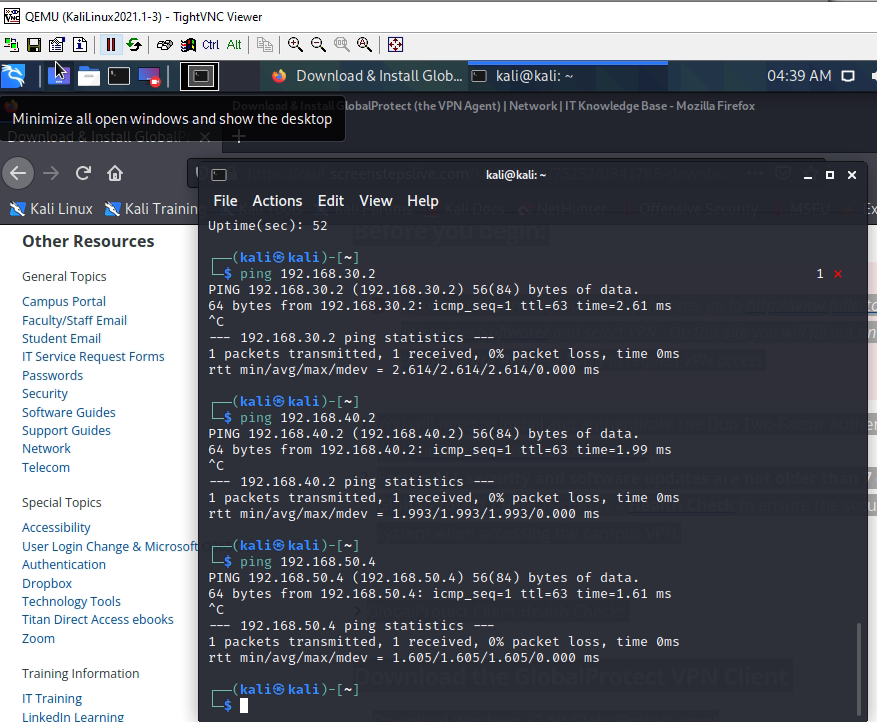
+ Set up Global Protect on Windows and Kali machines. Then, we are able to access the local network on the Global Protect VPN connection.
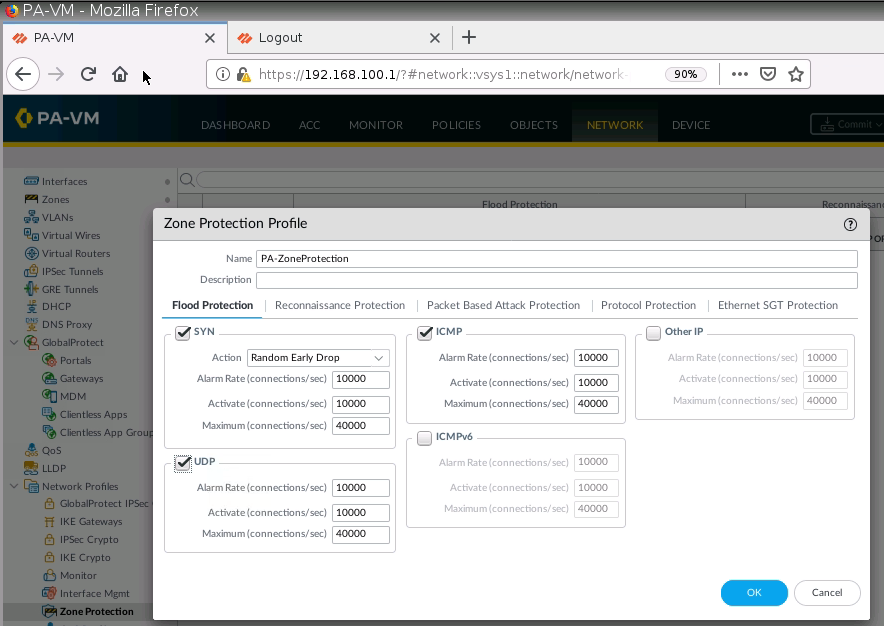
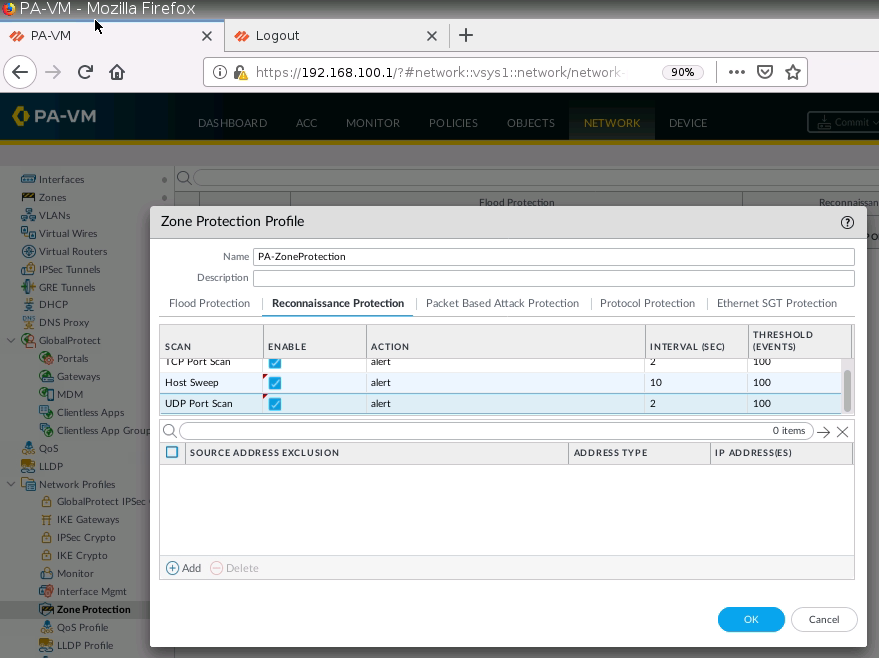
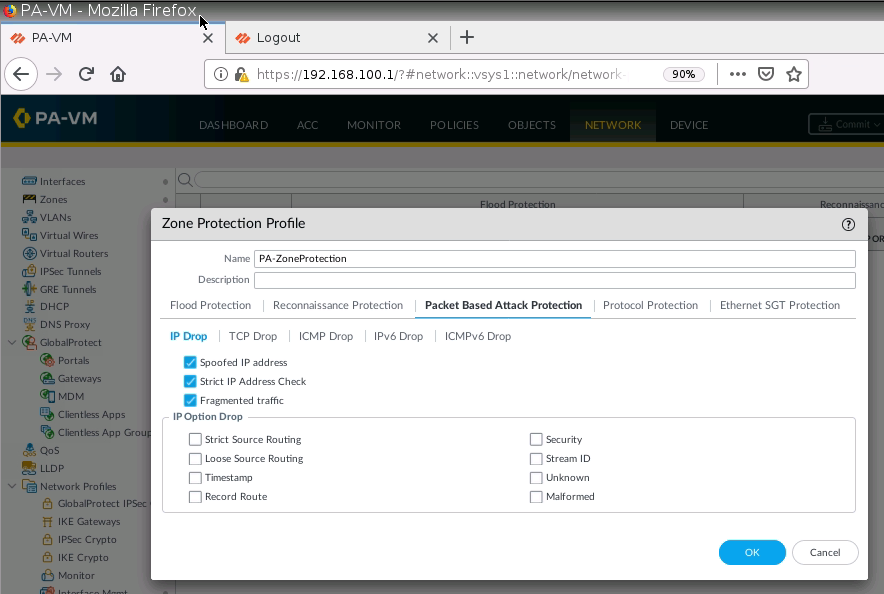
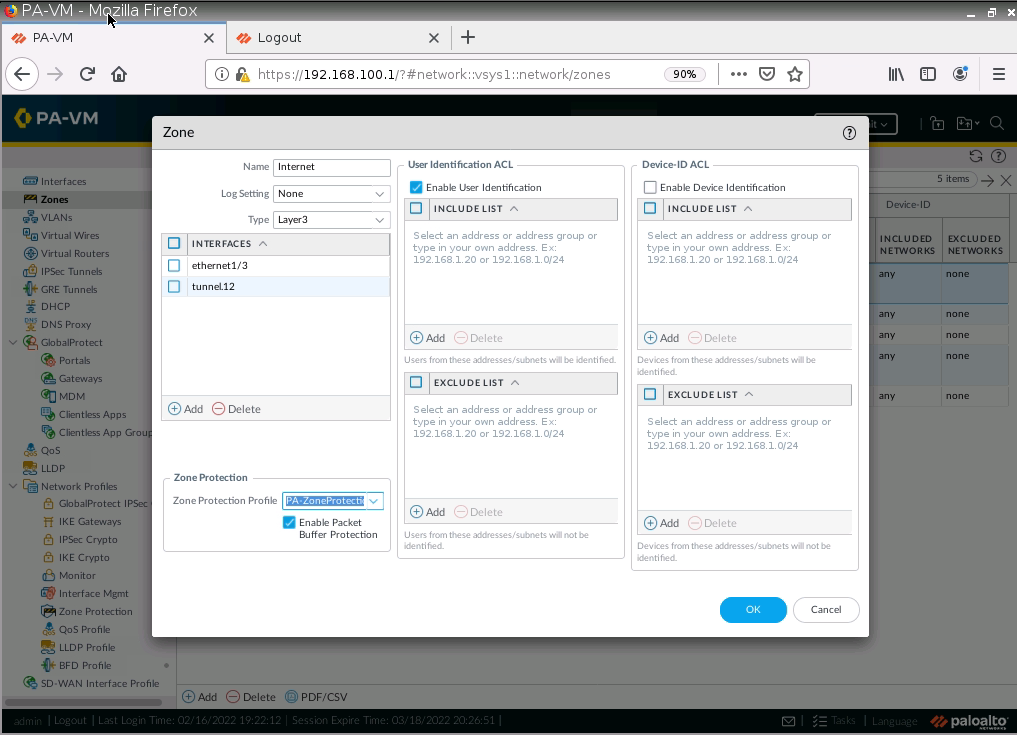
+ Enable Zone Protection on e1/3 to prevent DoS on this zone.
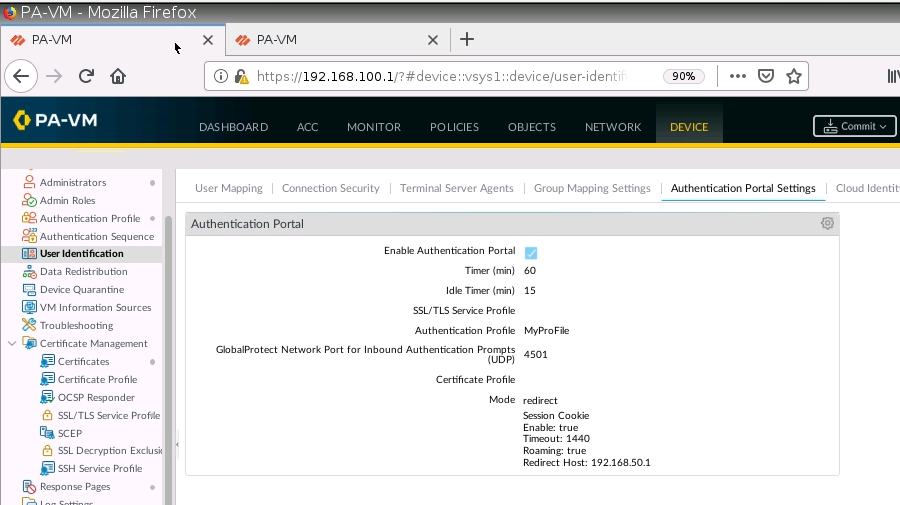
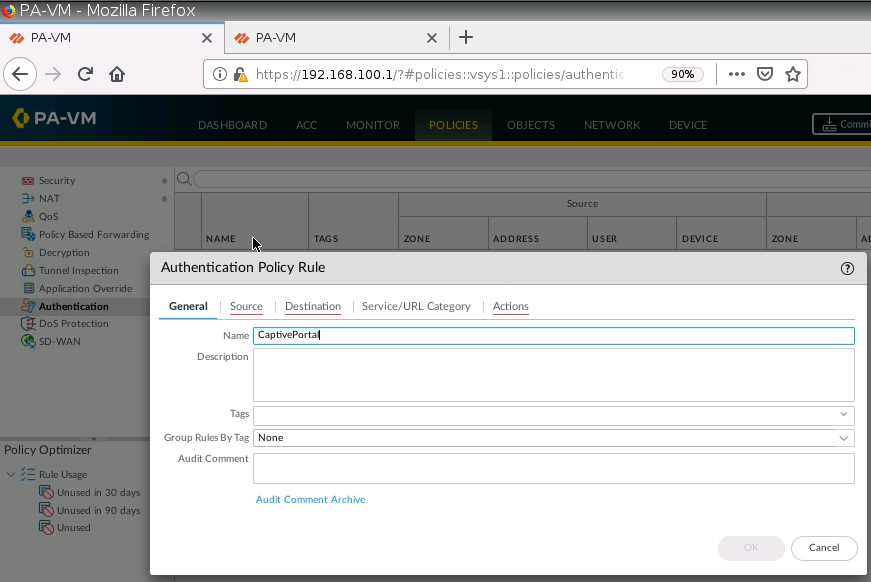
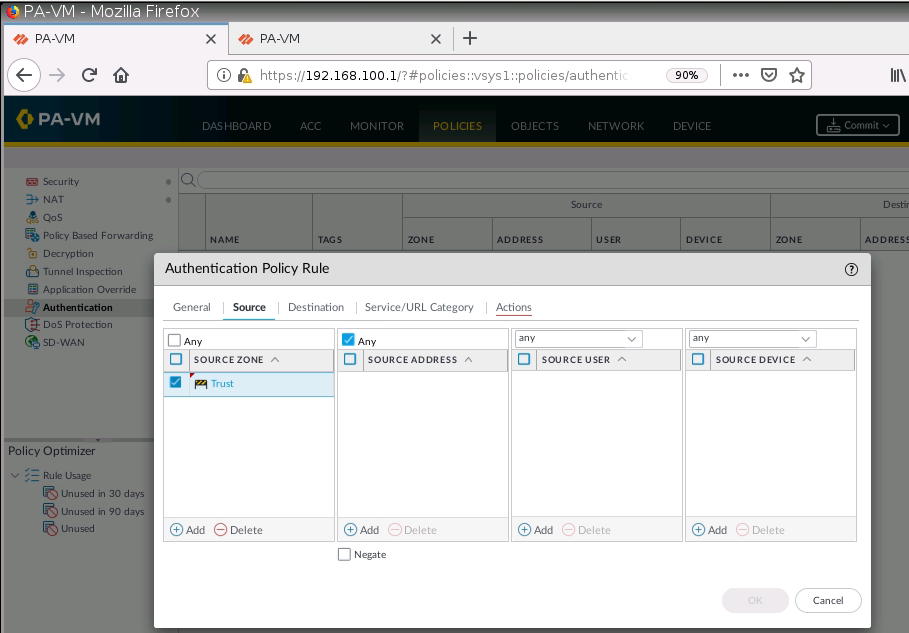
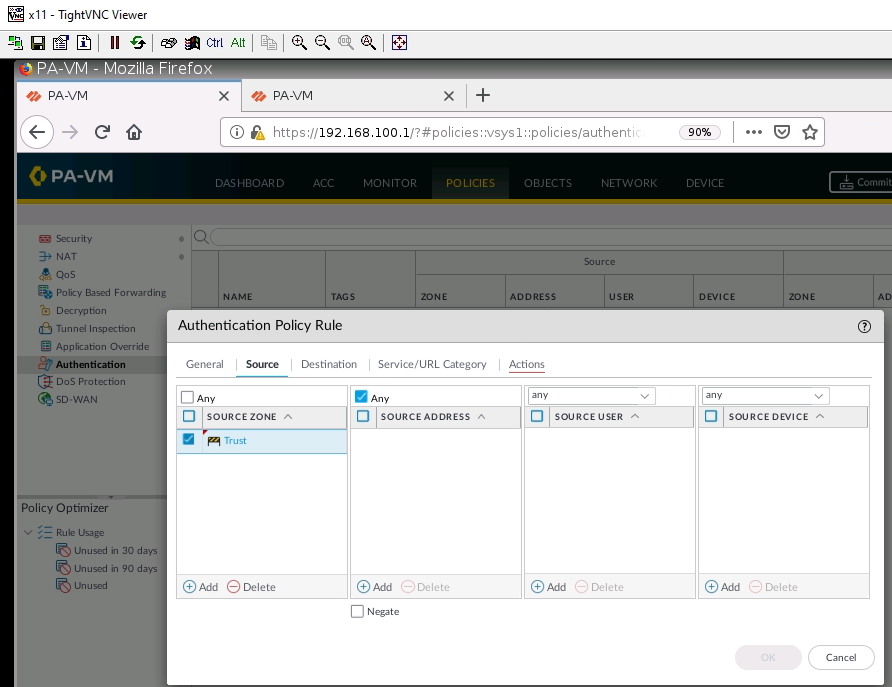
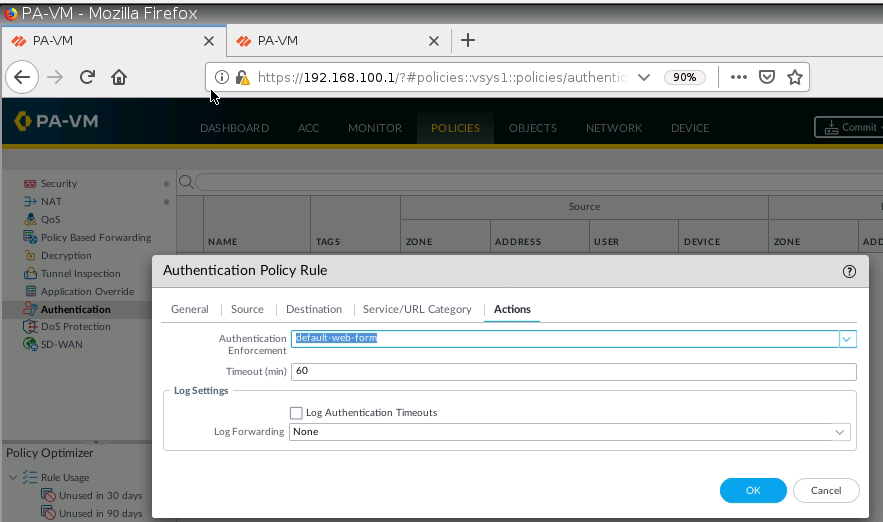
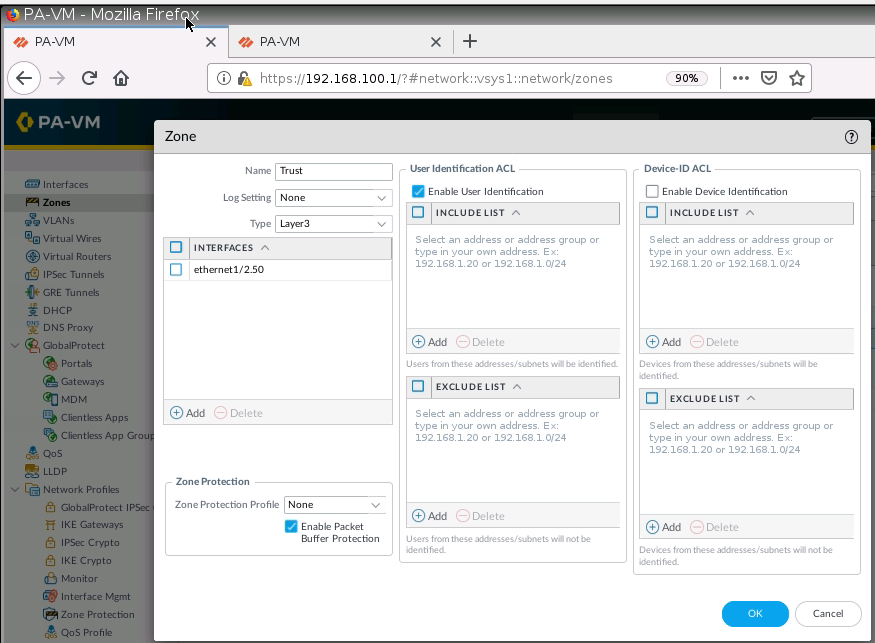
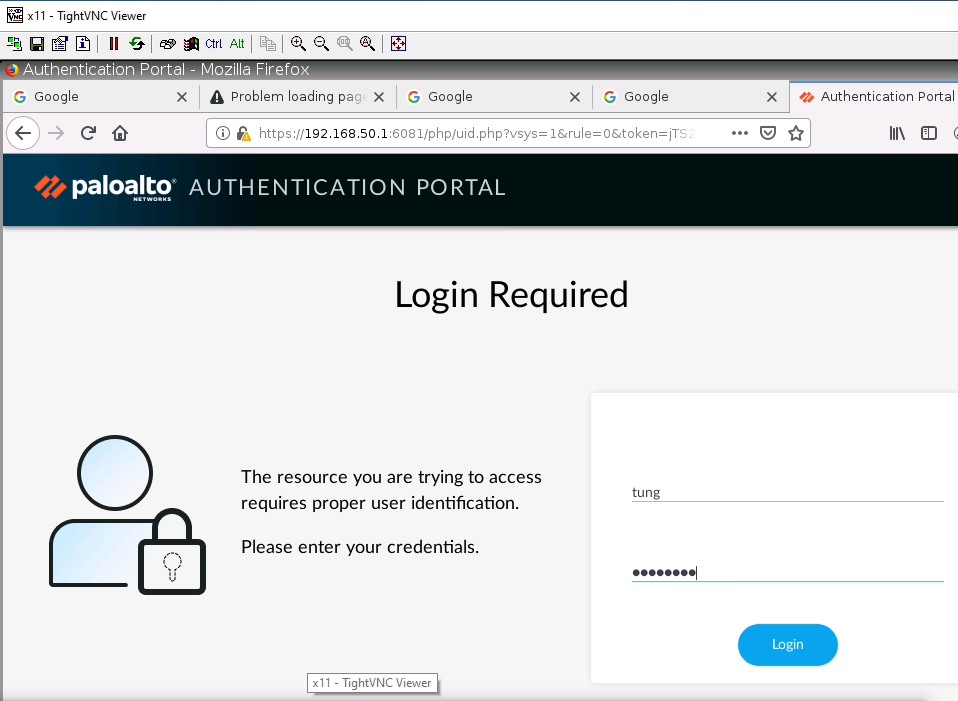
+ Set up Captive Portal on Trust interface on PA1.
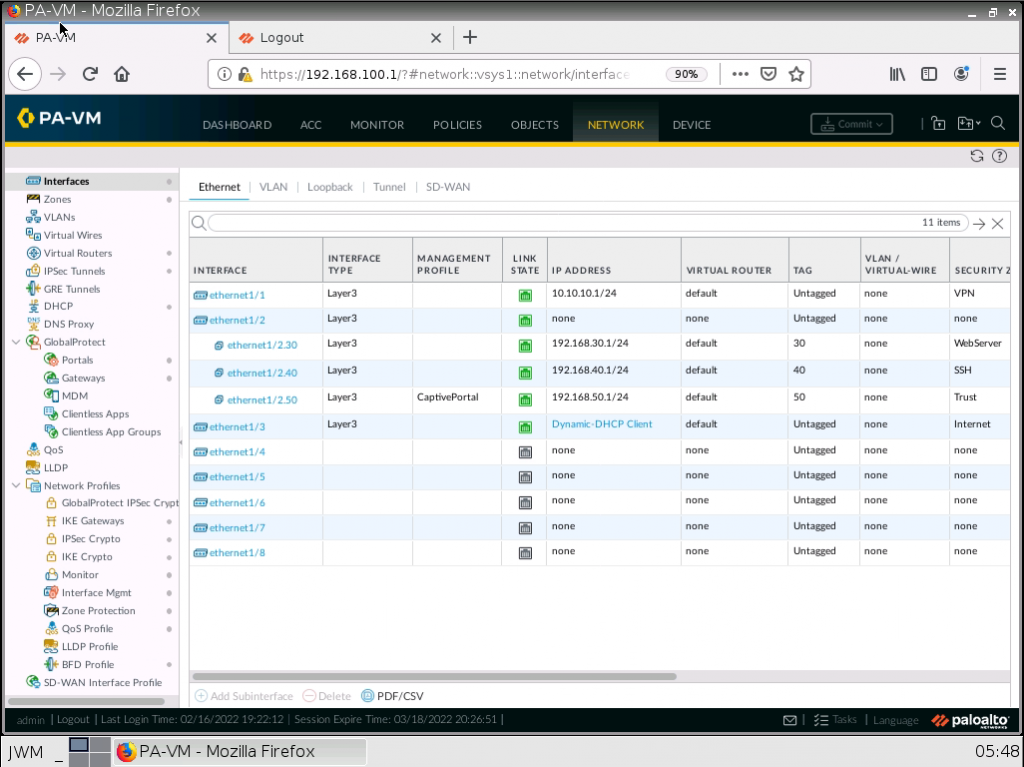
Configure the basic switch for support of multiple VLANs.
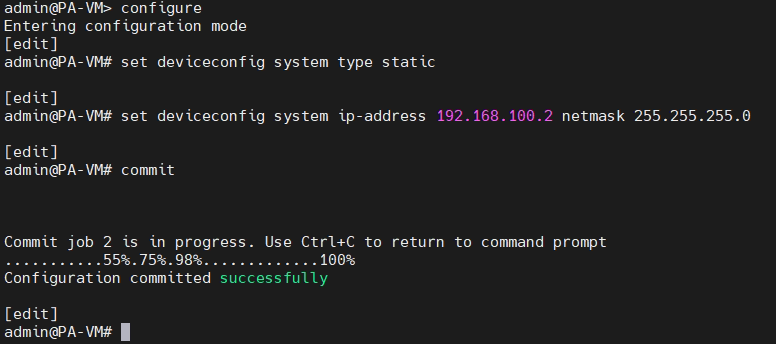
Configure PA1.
Configure DHCP.
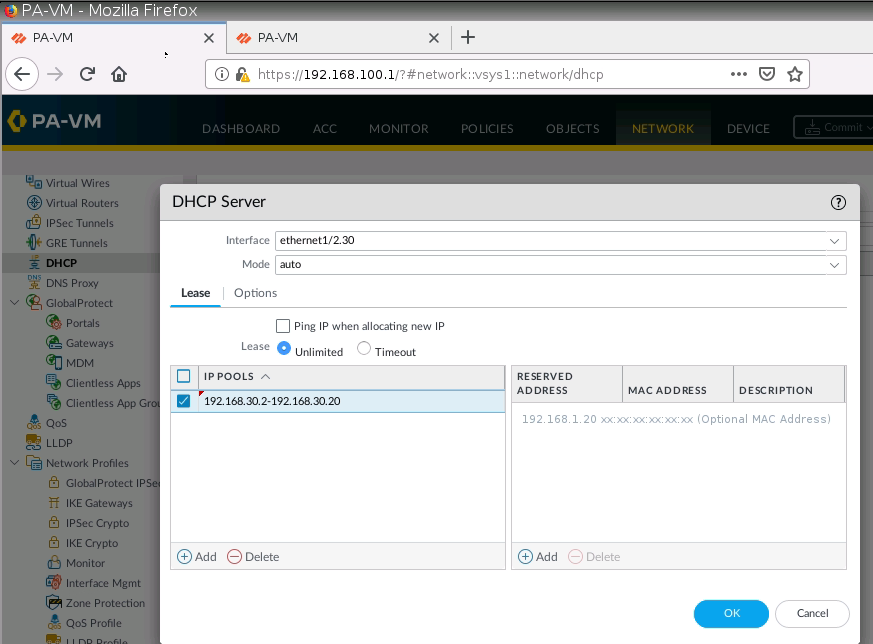
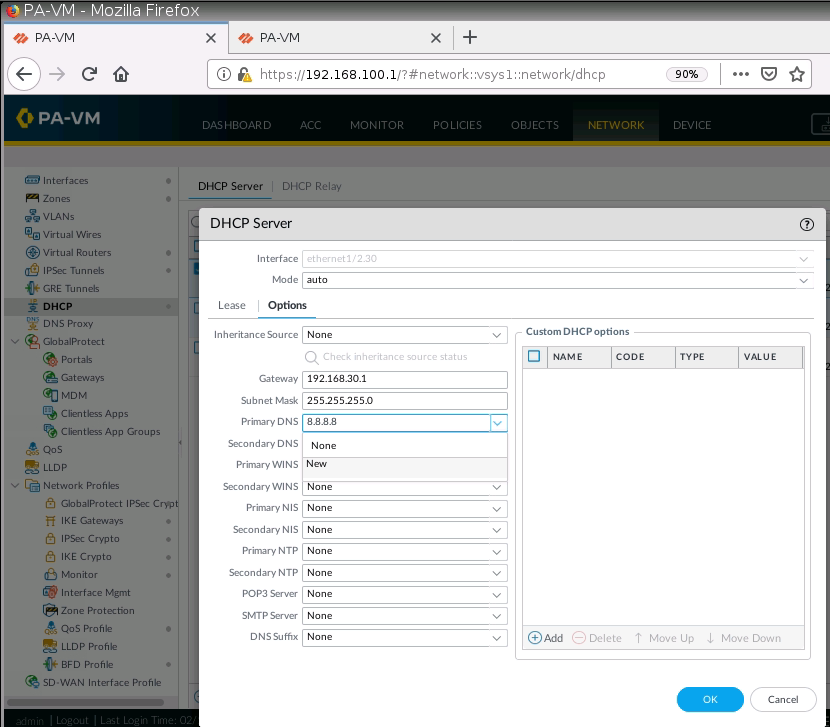
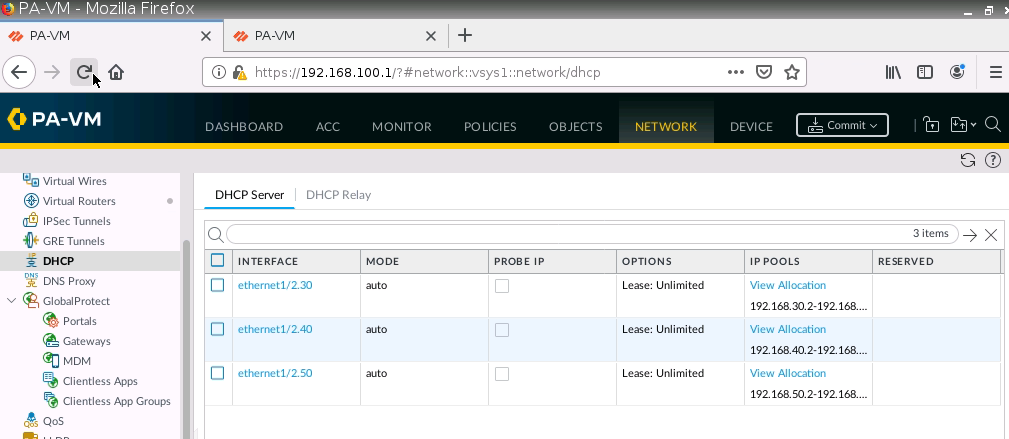
Check client on the local network has received IP address from DHCP Pool for VLAN30, VLAN40, and VLAN50.
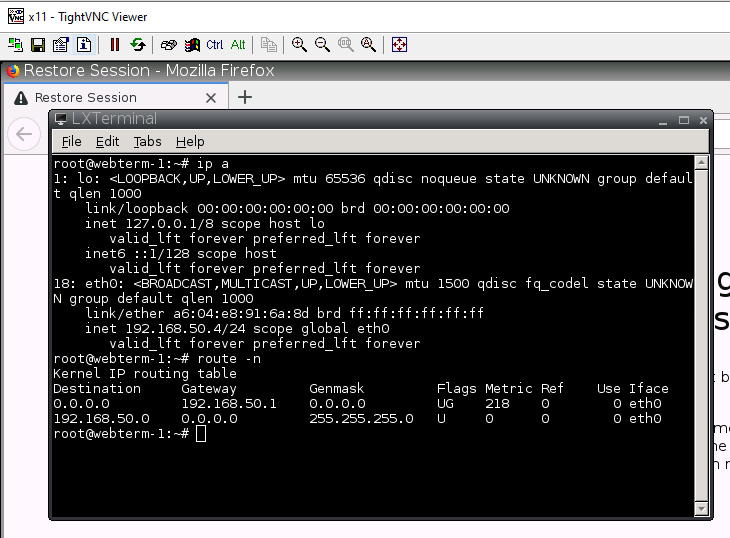
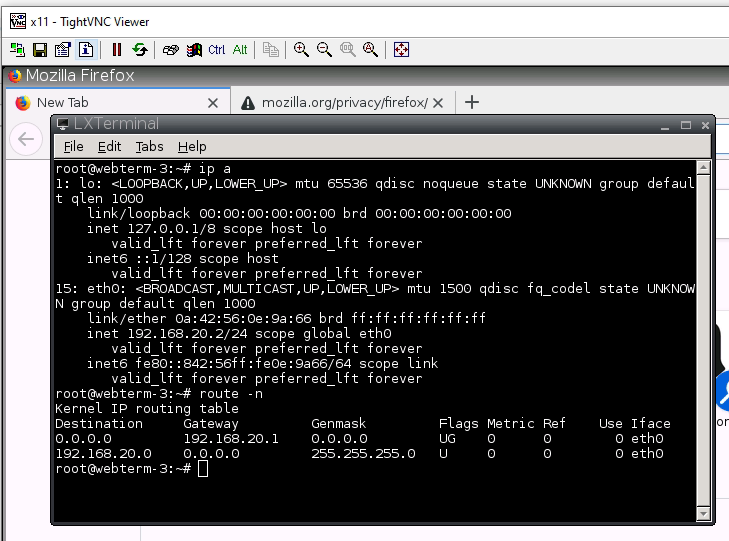
Webterm2 on PA2.
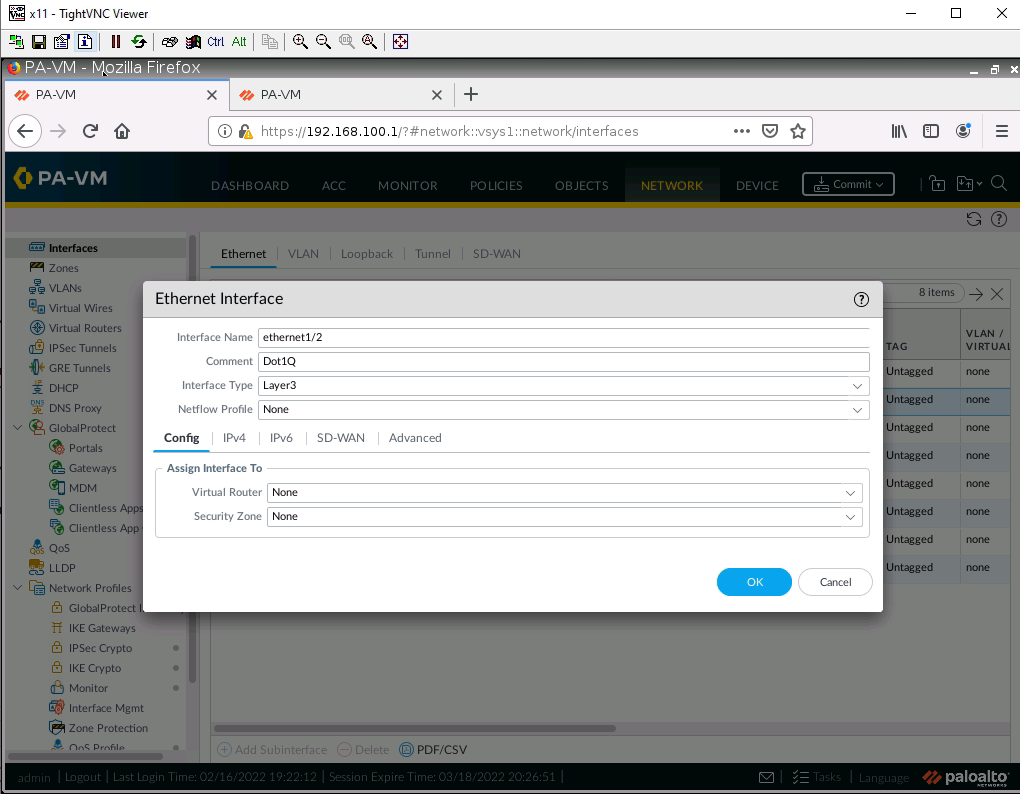
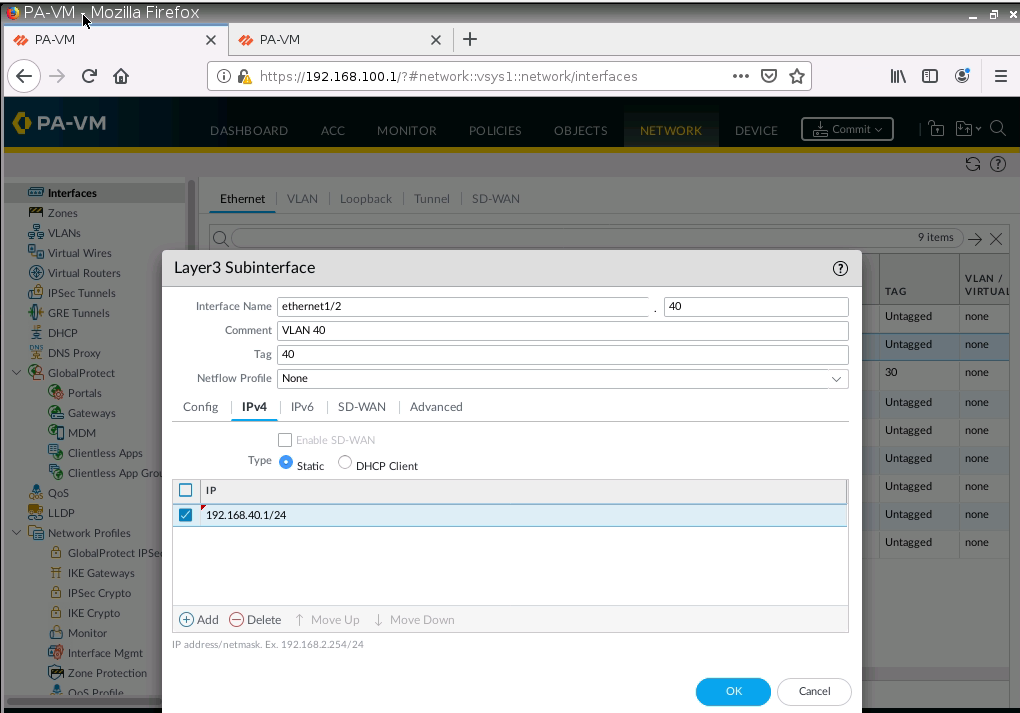
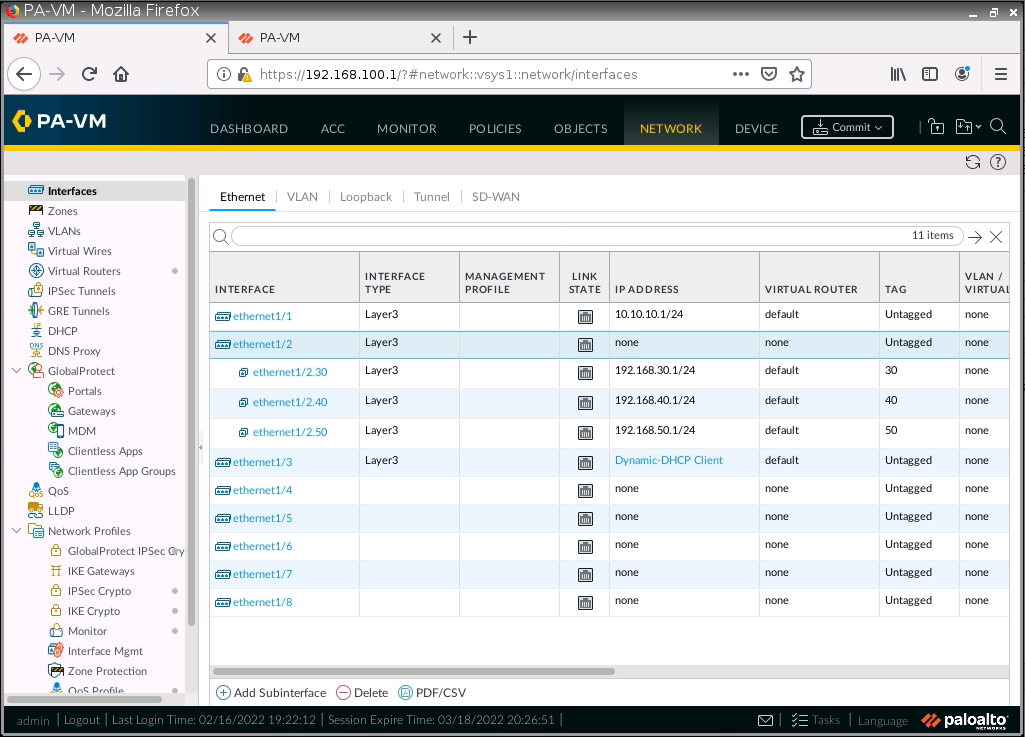
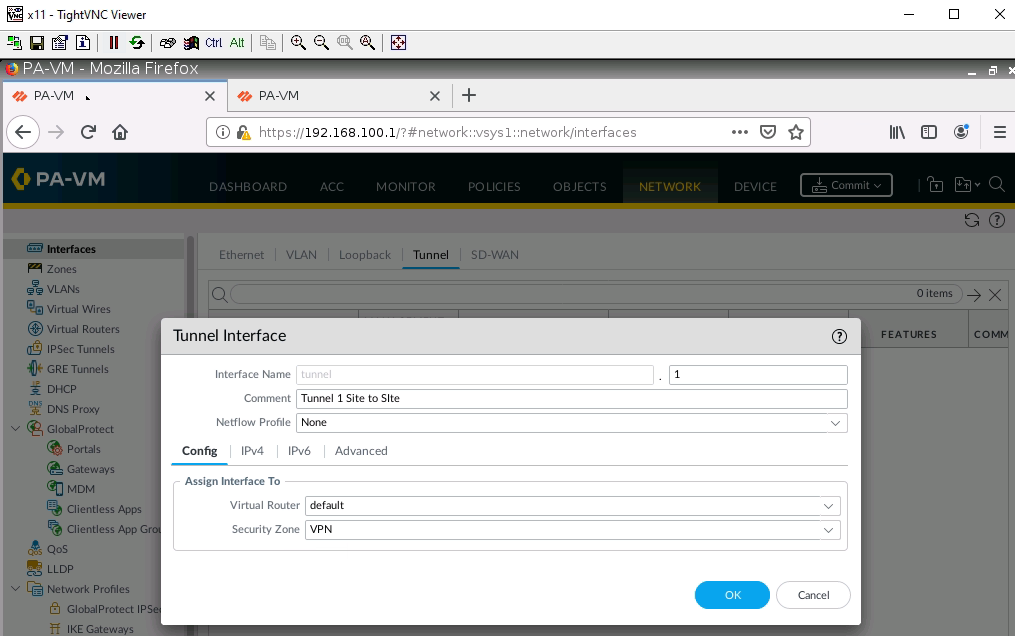
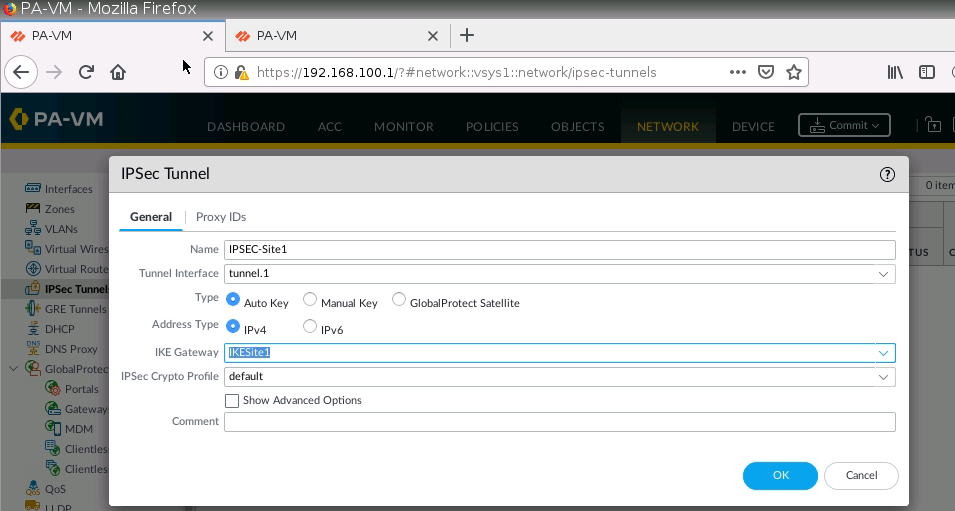
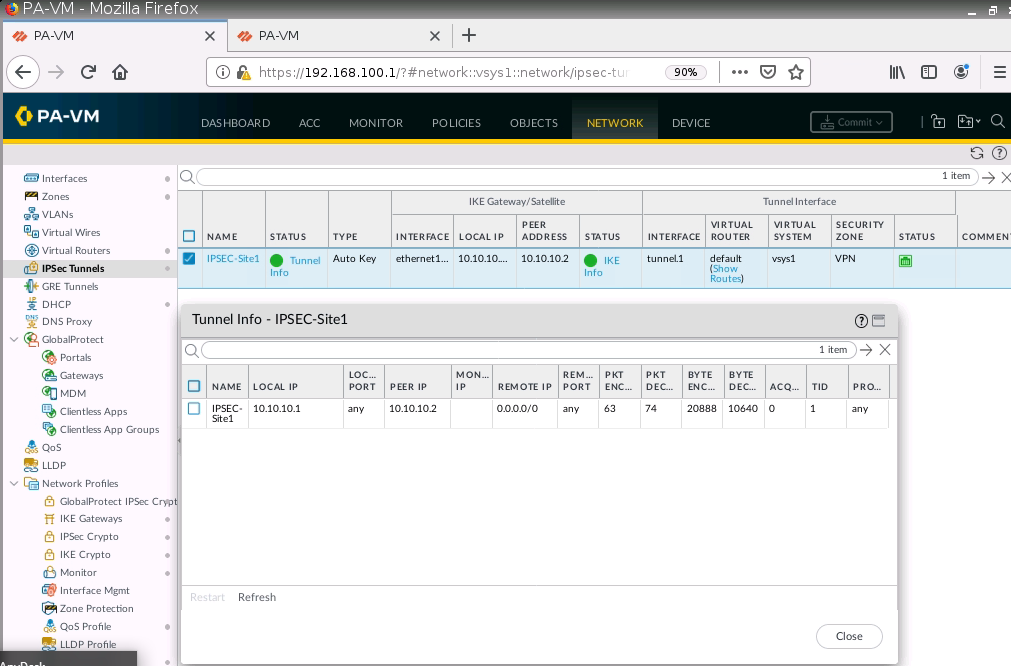
Configure tunnel 1 for IPSEC site to site from PA1 to PA2.
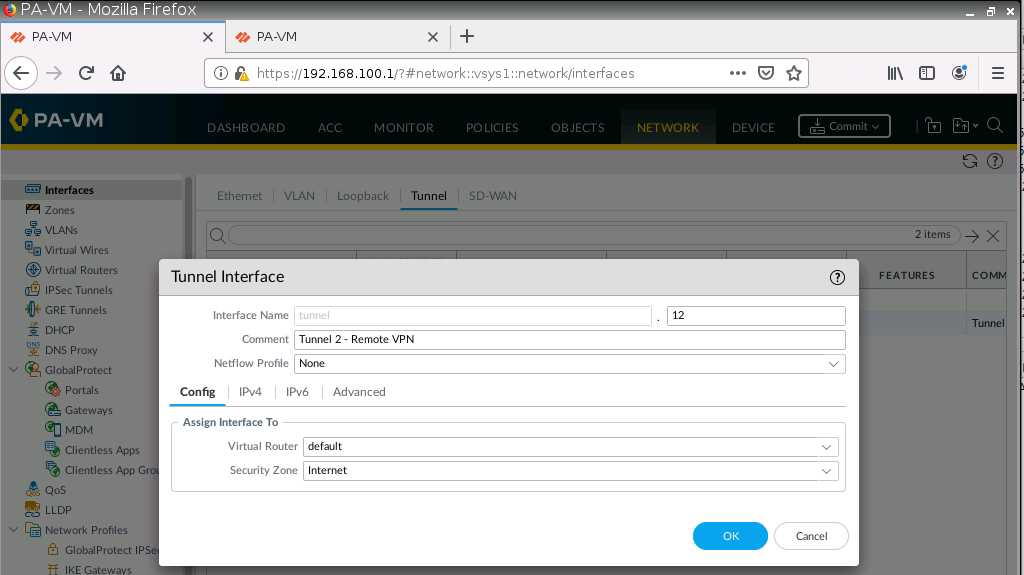
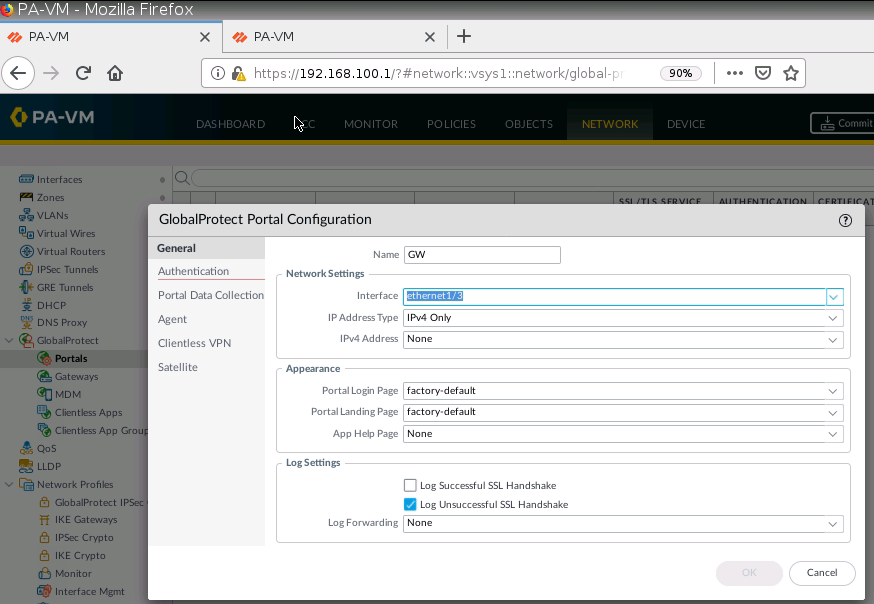
Configure tunnel 12 for Remote VPN via GlobalProtect.
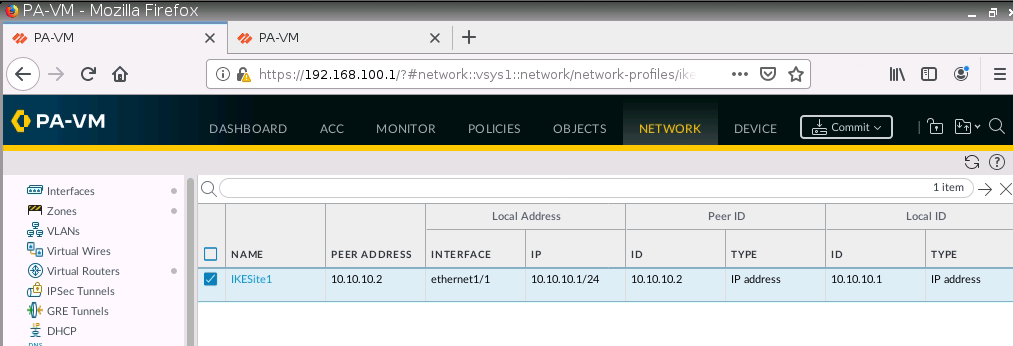
Setup IPSEC tunnel on PA1.
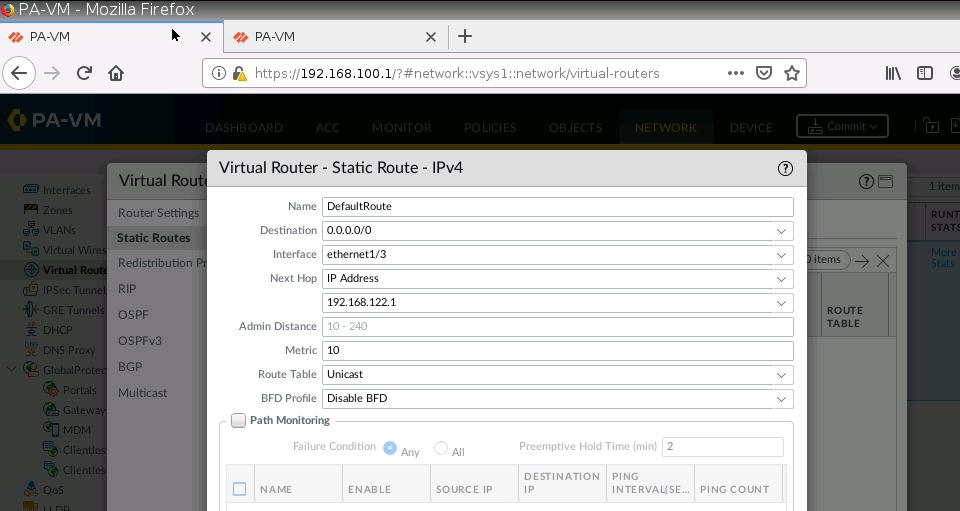
Configure default route to route traffic to the Internet.
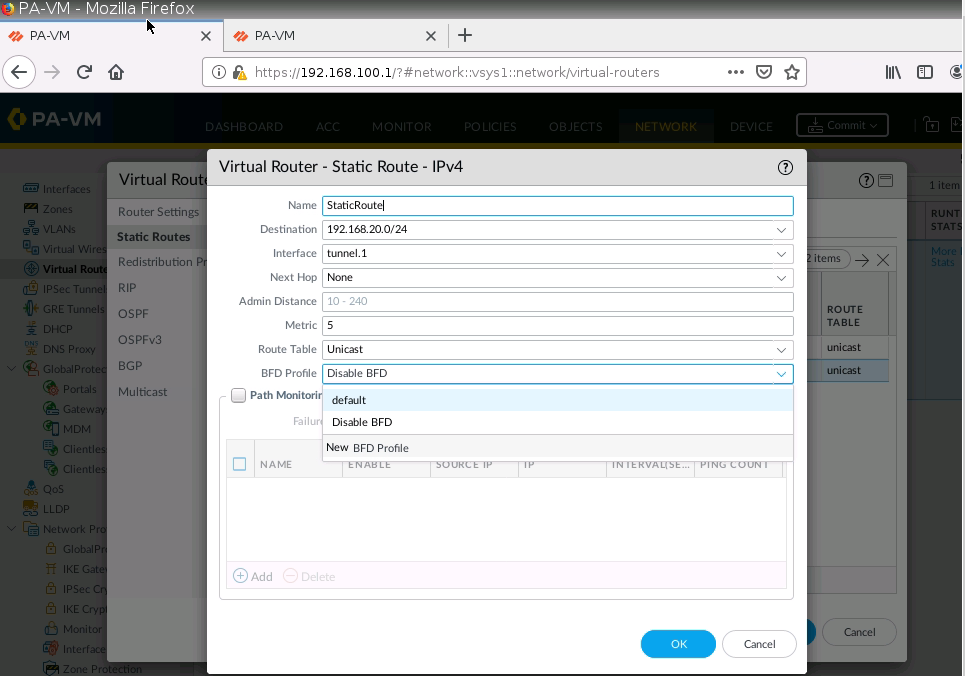
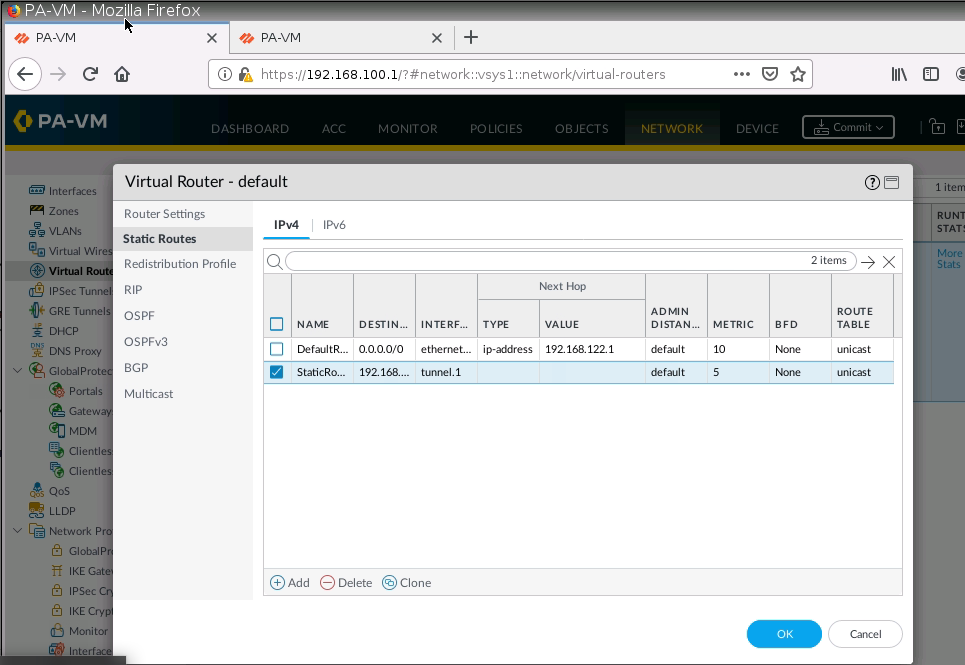
Configure another route to allow traffic from the local network on PA1 to access the local network on PA2.
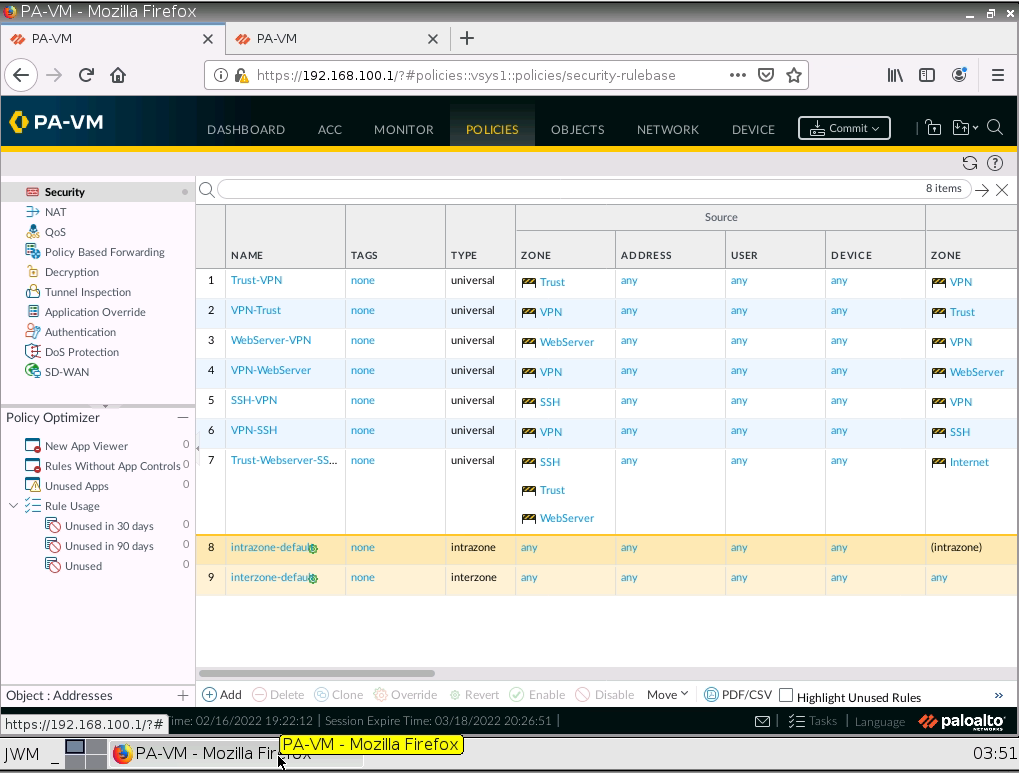
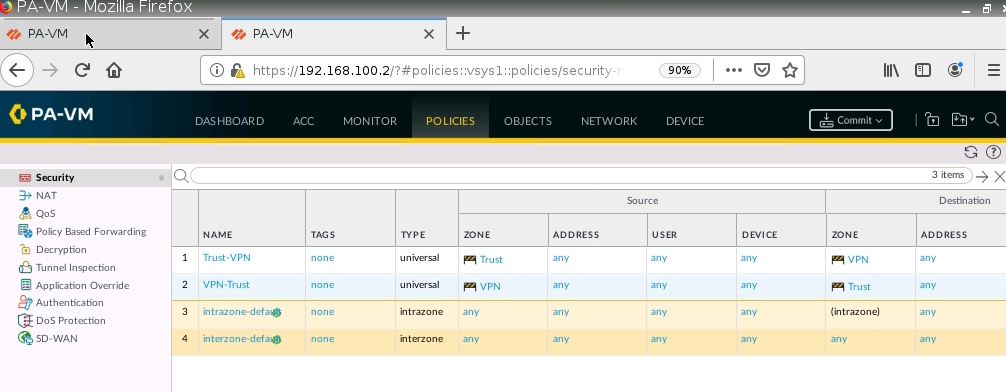
Configure access rules to allow traffic from the local network on PA1 to access the local network on PA2 and the Internet.
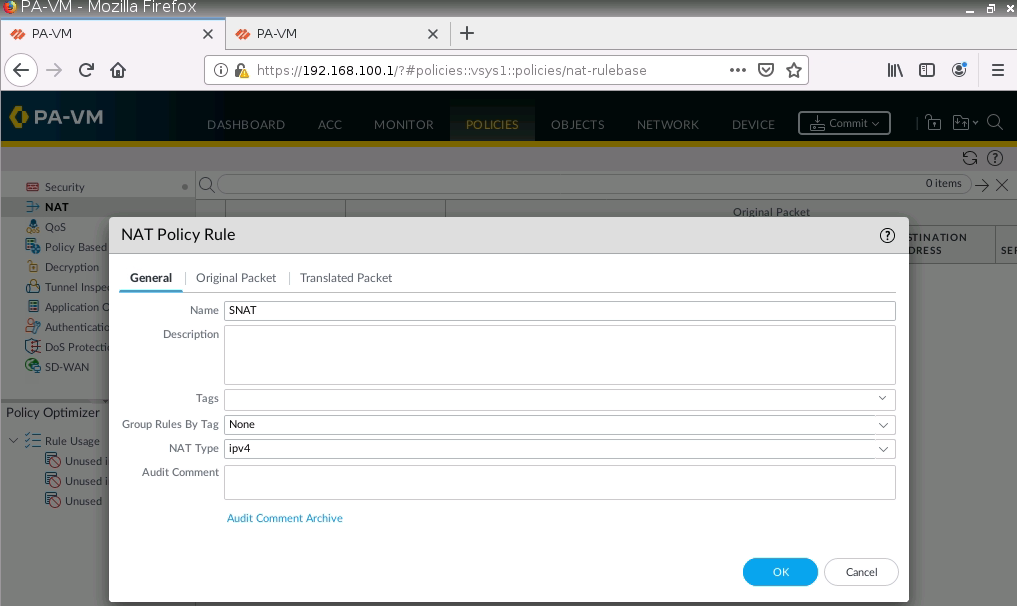
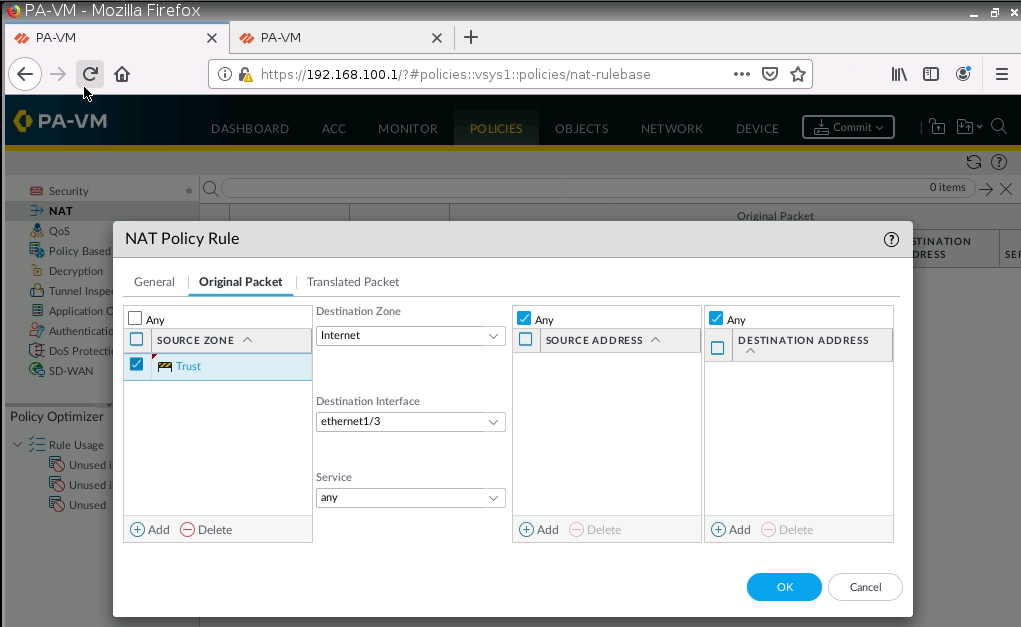
Configure SNAT to allow traffic from the Trust zone to the Internet.
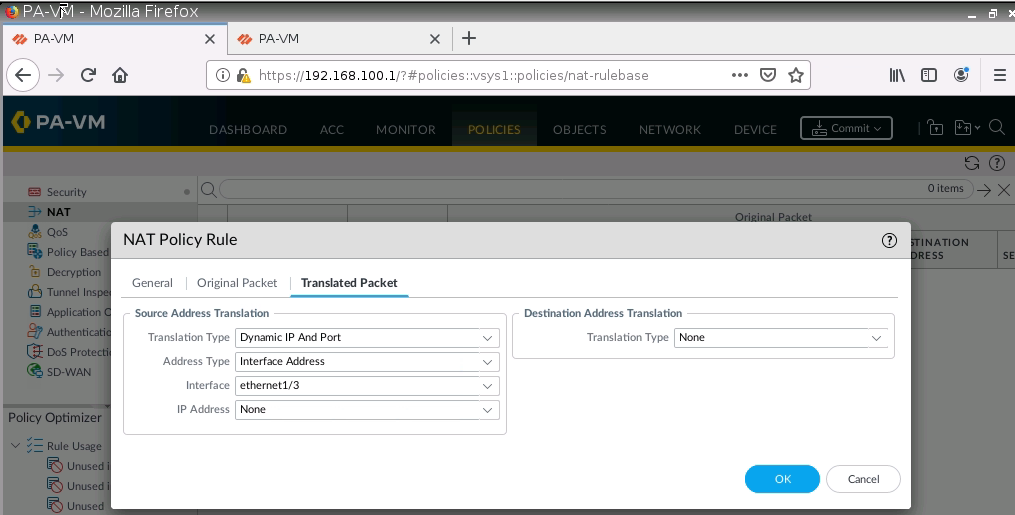
Setup IKETunnel on PA2.
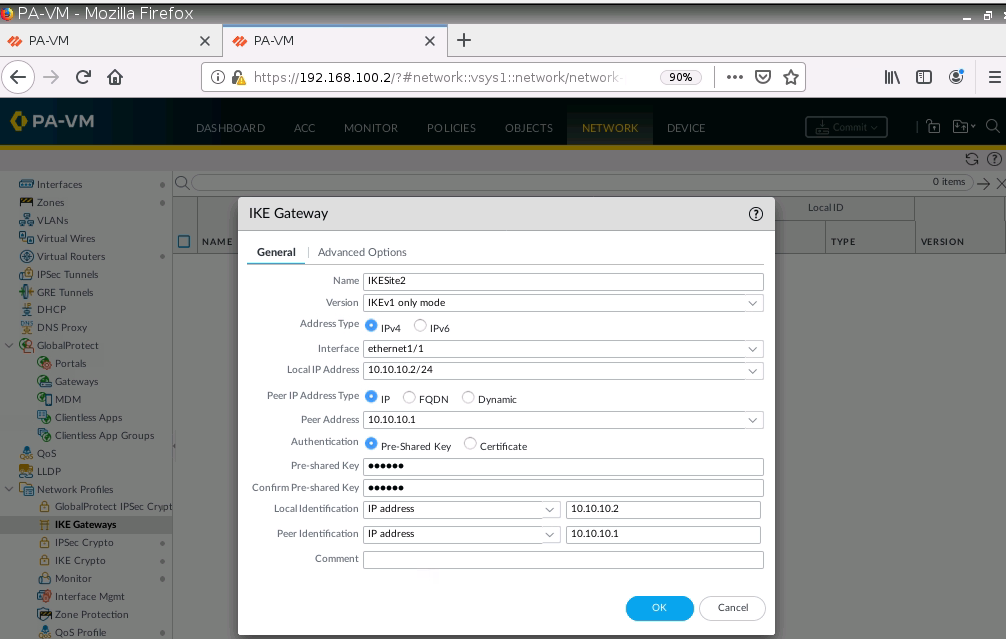
Set up IPSEC tunnel on PA2.
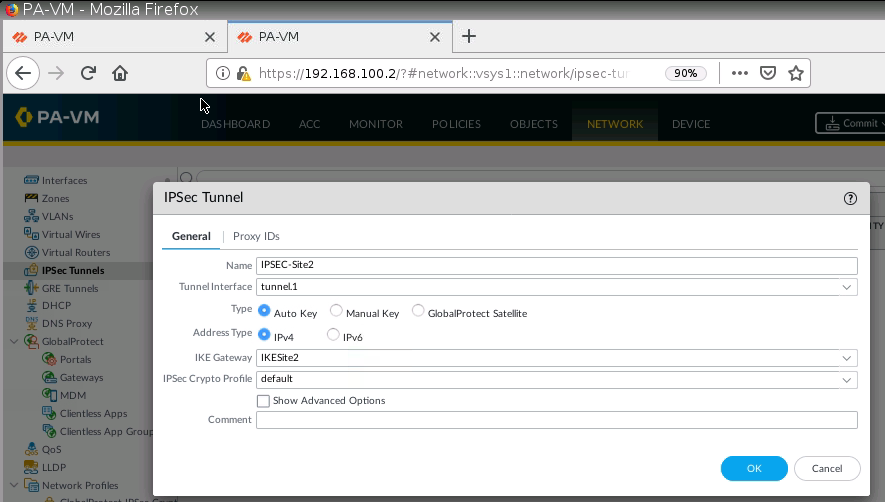
Configure default route from Local network on PA1 to the local network on PA1 via IPSEC tunnel 1.
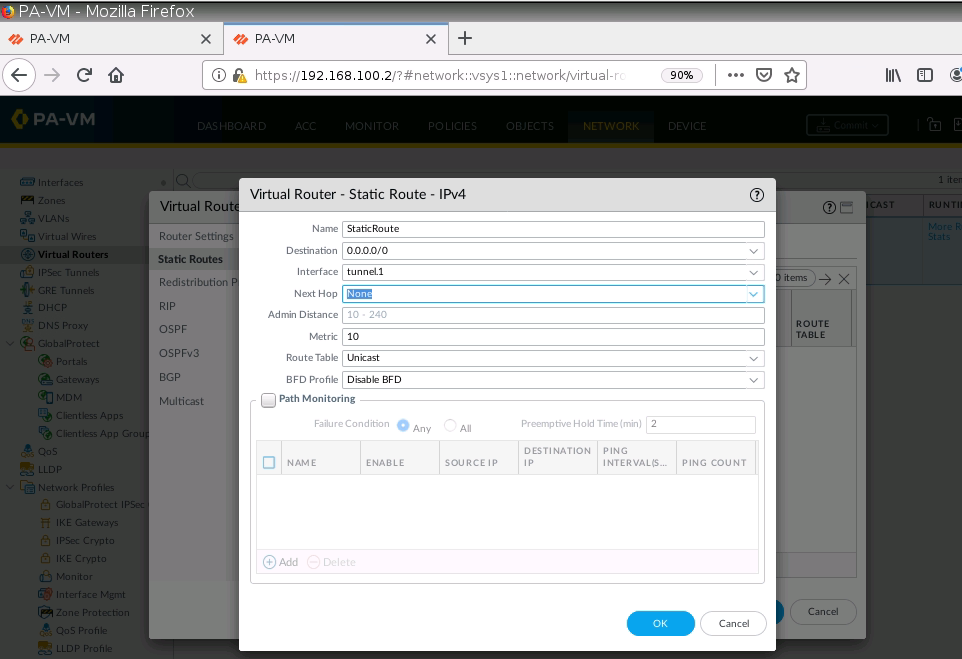
Create access rules to allow traffic from the local network on PA2 to the local network on PA1
Test IPSEC site to site.
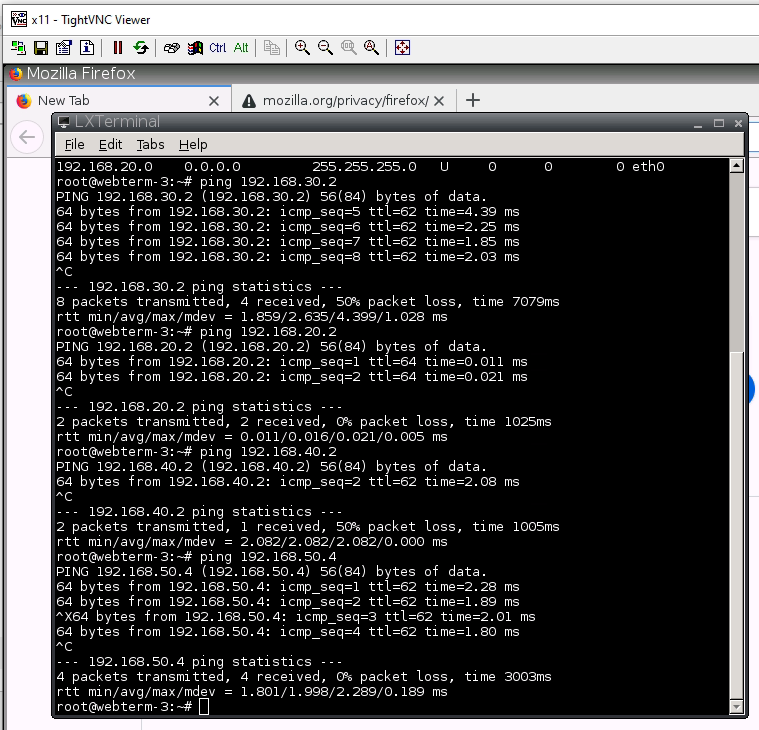
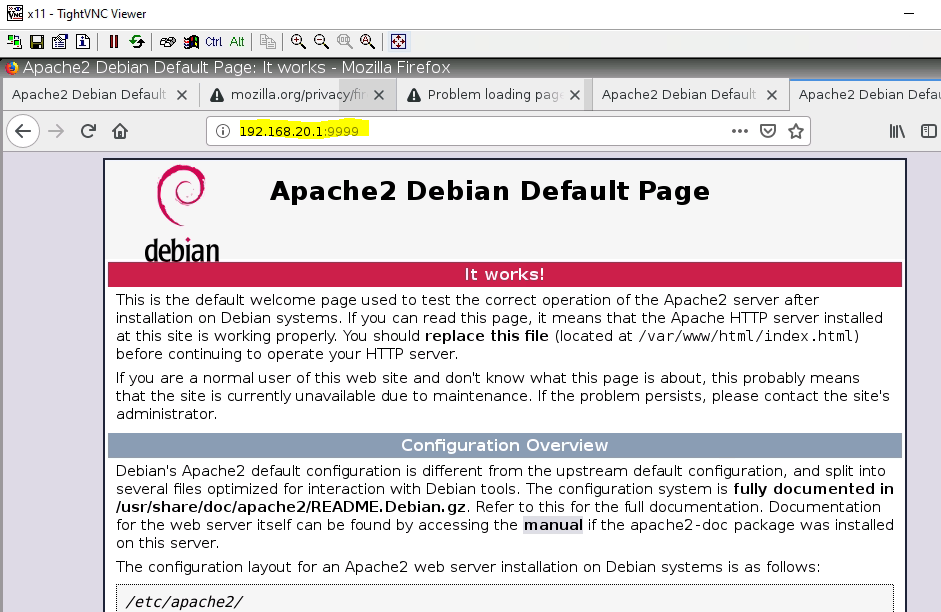
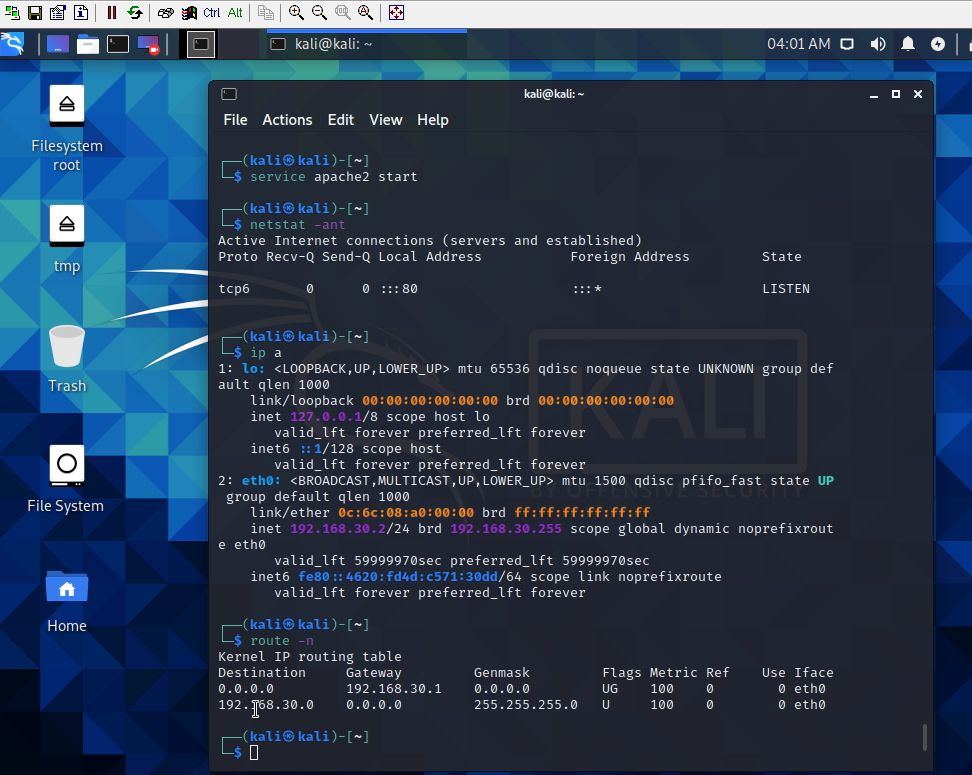
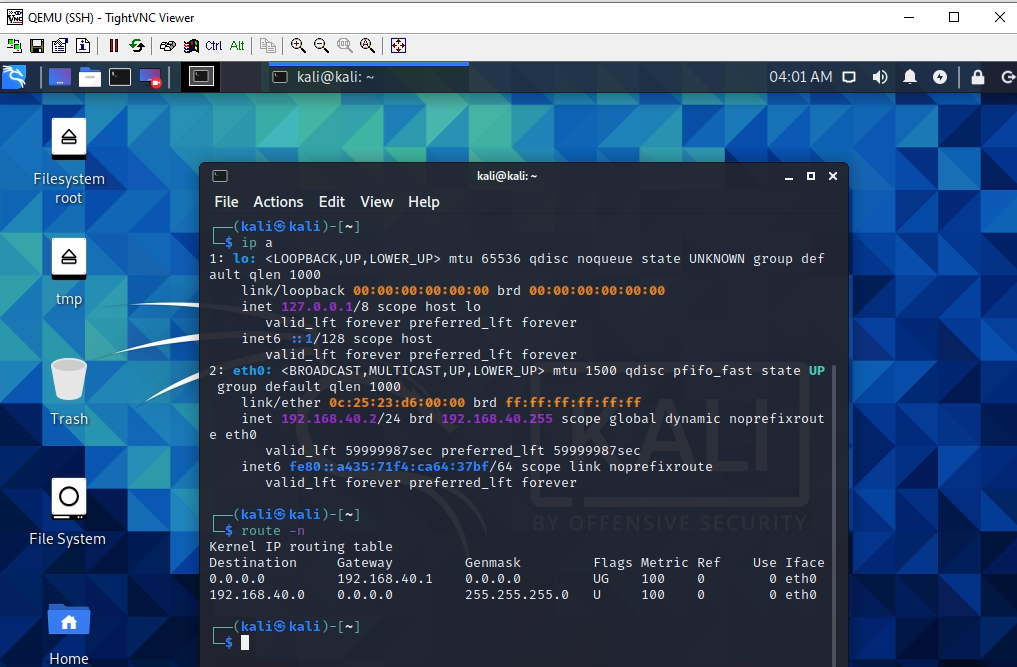
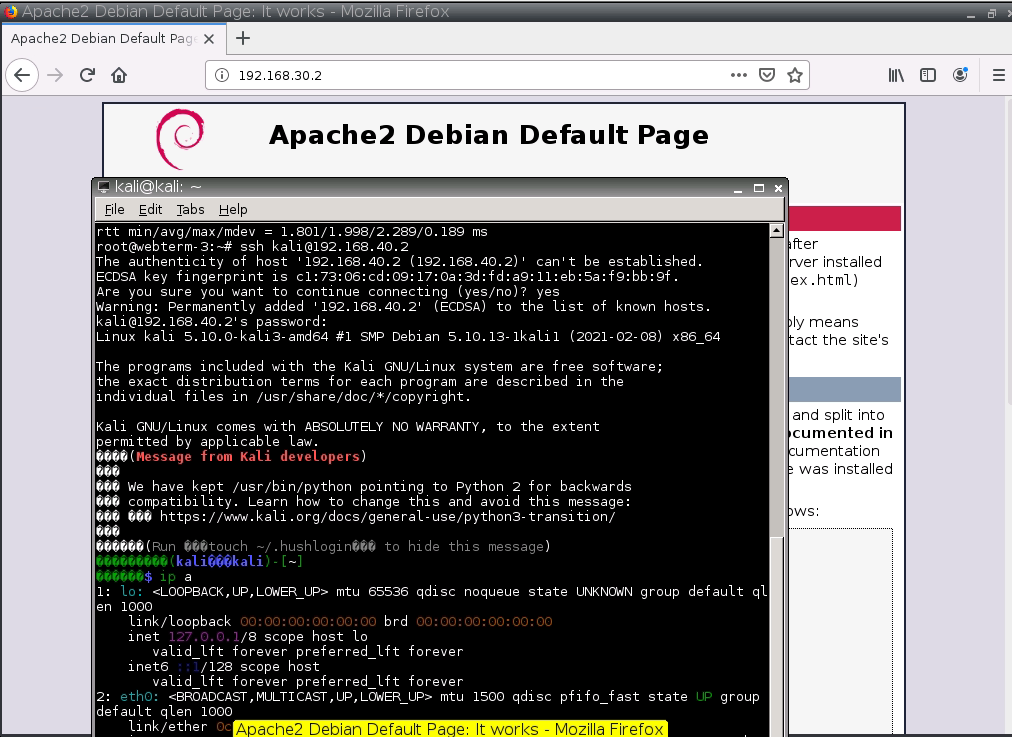
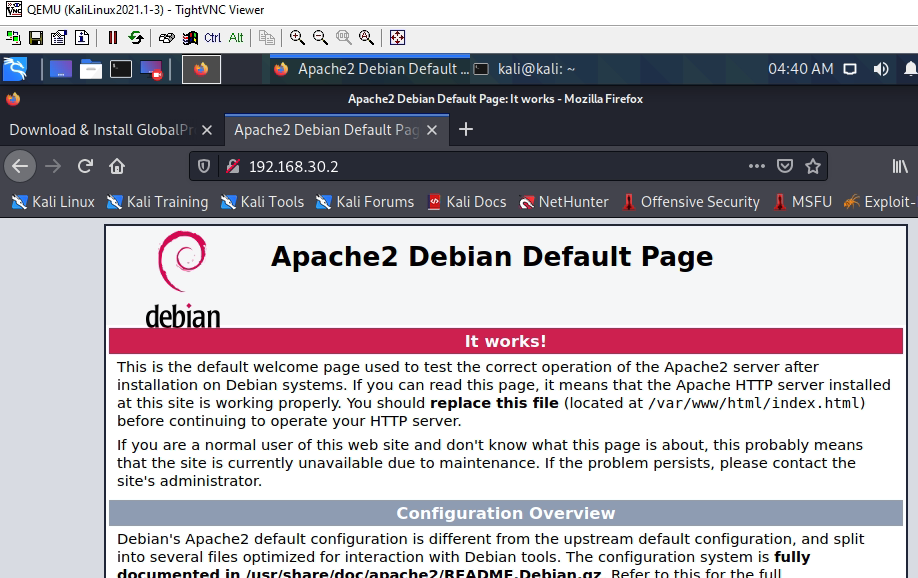
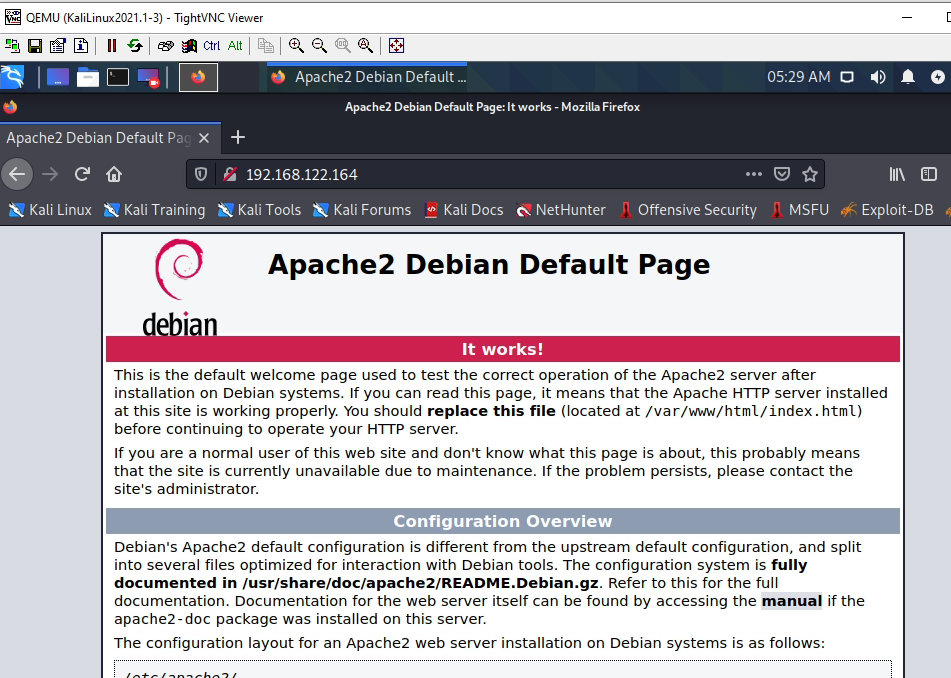
Access Apache website on VLAN 30 (service apache2 start).
The IPSEC tunnel is up.
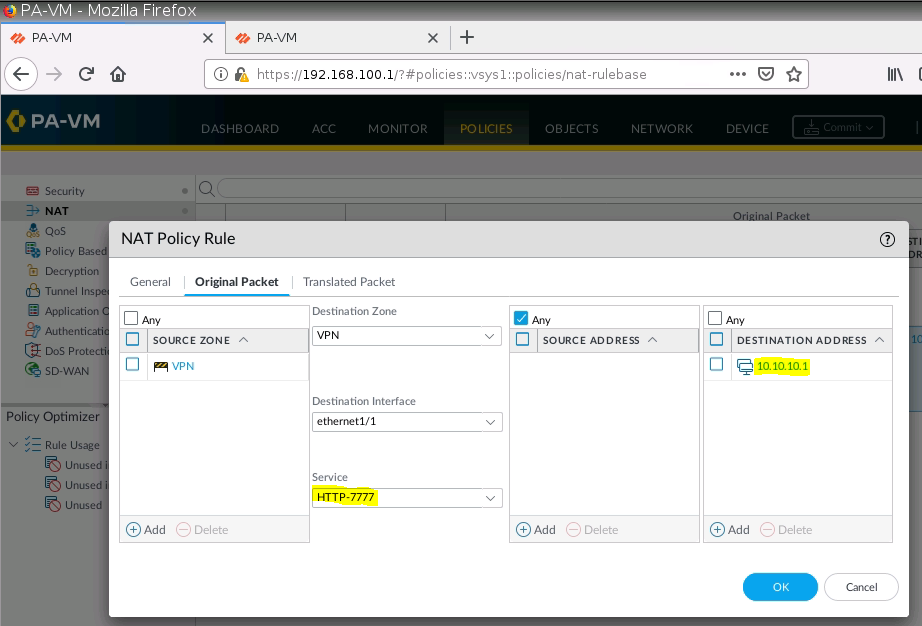
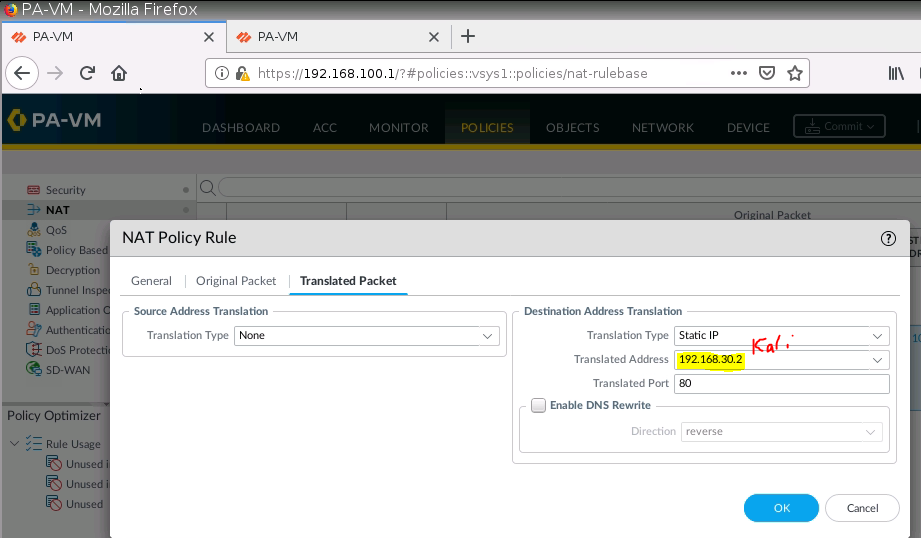
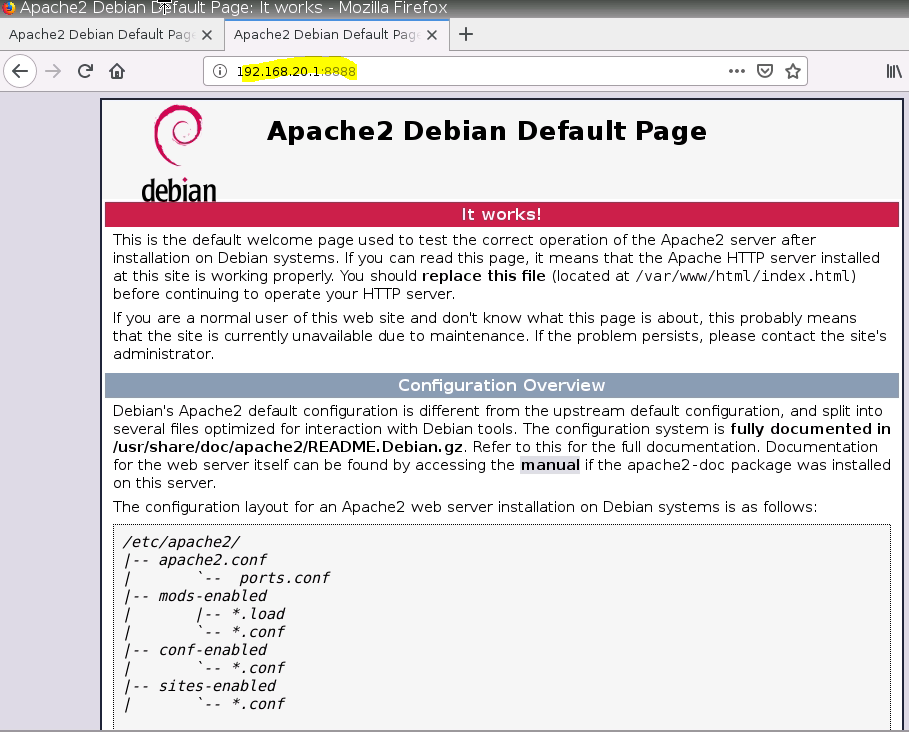
Configure DNAT on PA2 to allow port 8888 to be translated to port 80 on the Apache Web server.
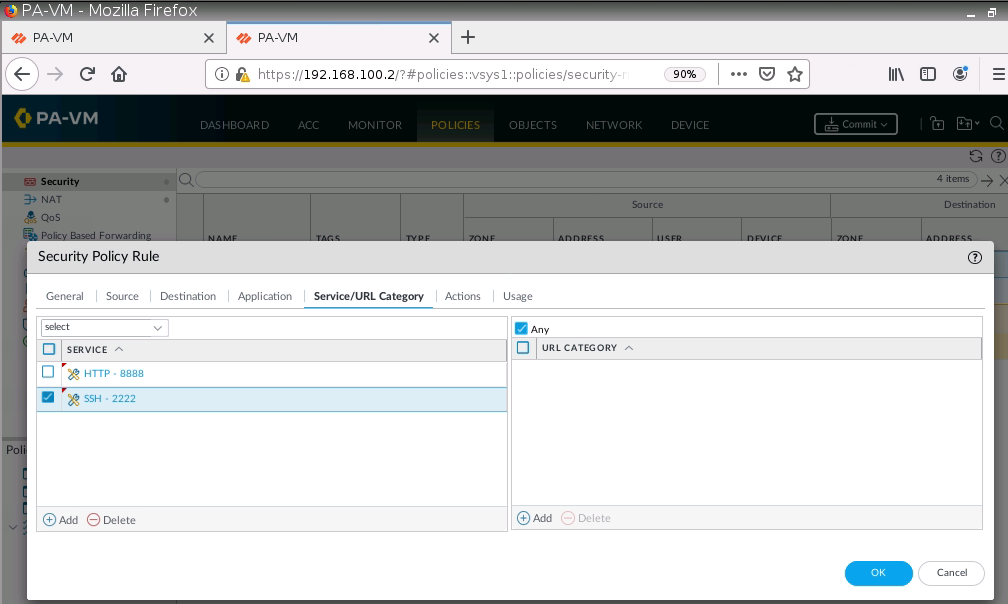
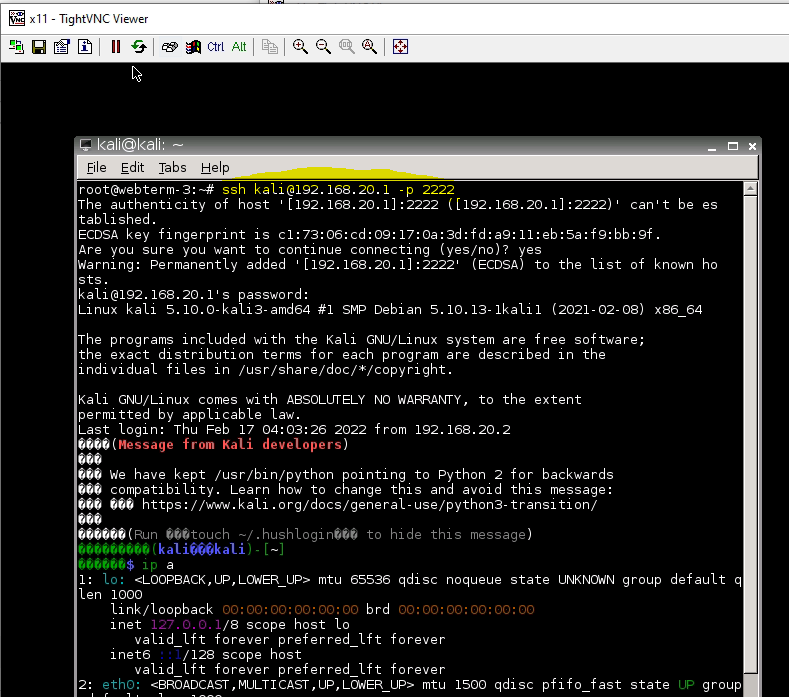
SSH 2222 to 22.
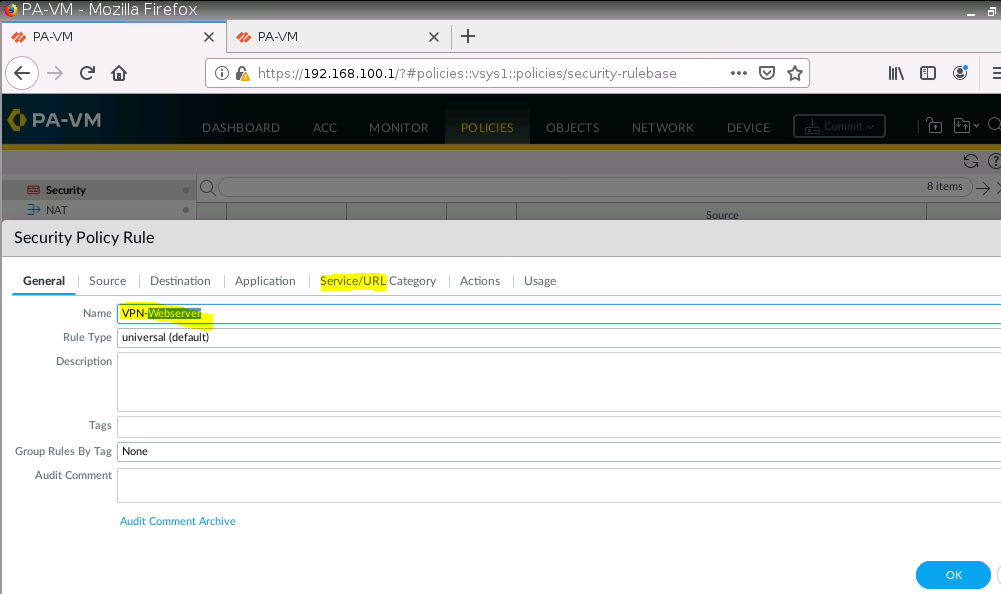
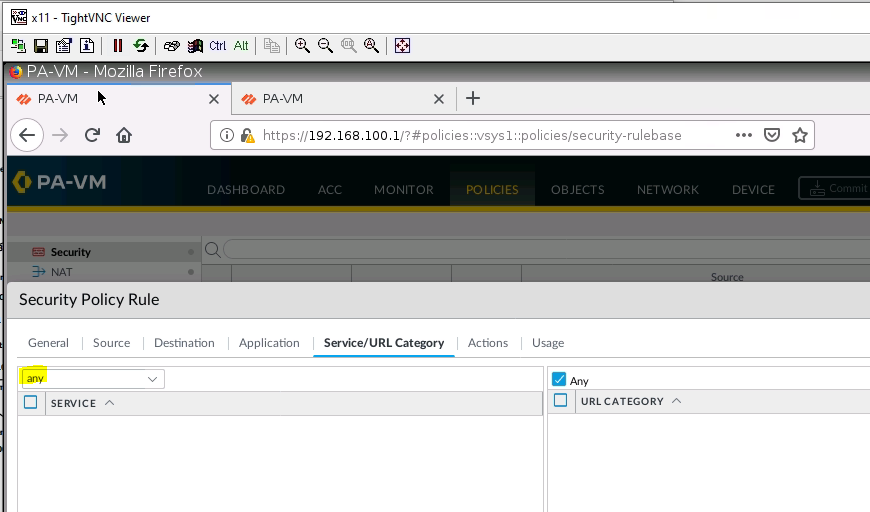
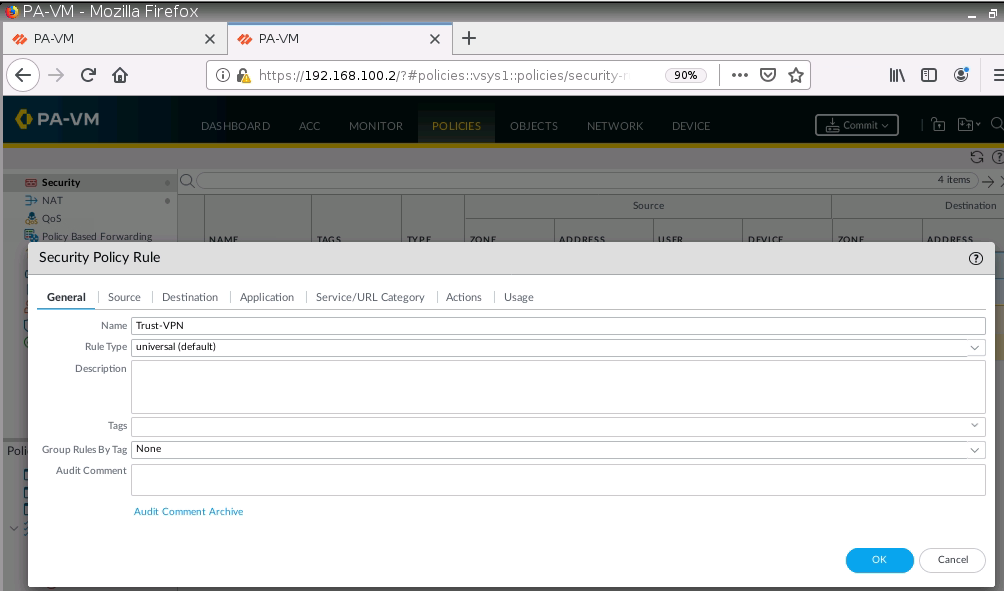
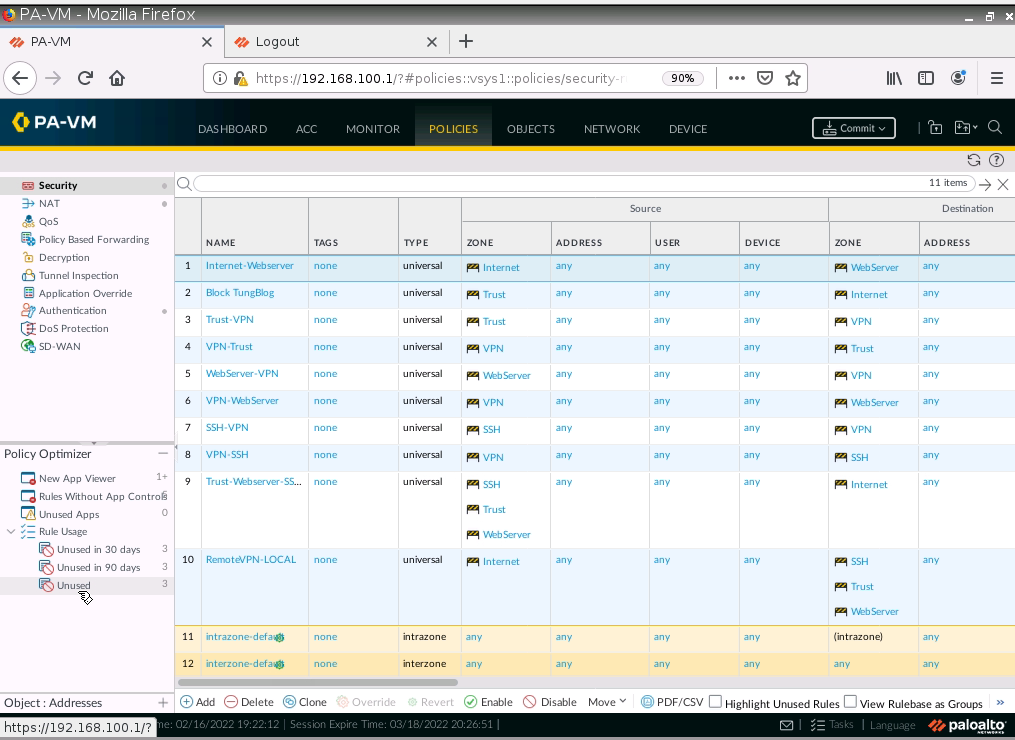
Create a Security Policy.
Access Apache2.
And SSH via 2222.
+ Set up GlobalProtect on PA1.
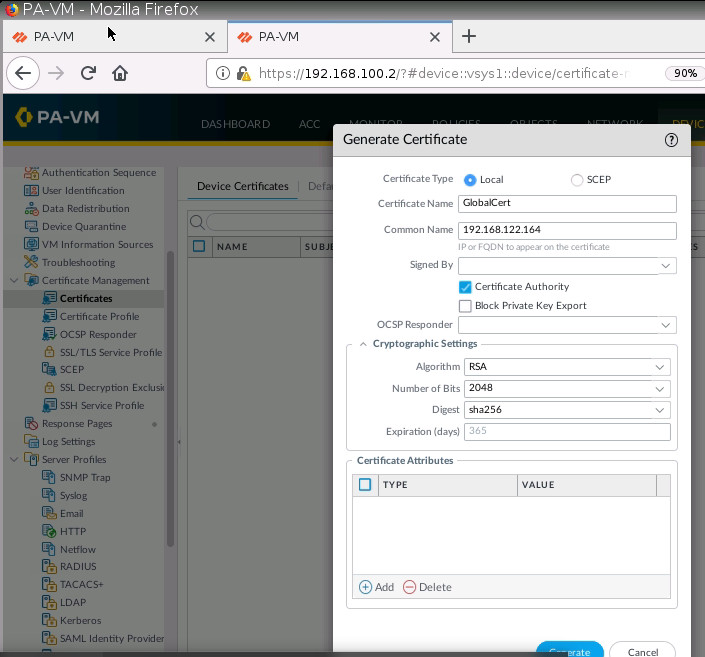
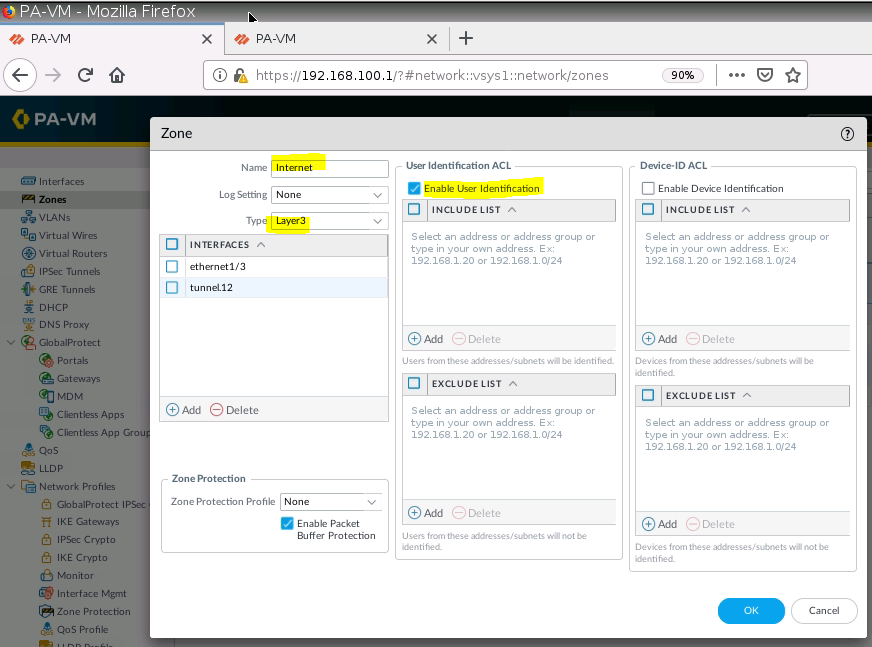
Enable User Authentication on Internet interface for GP.
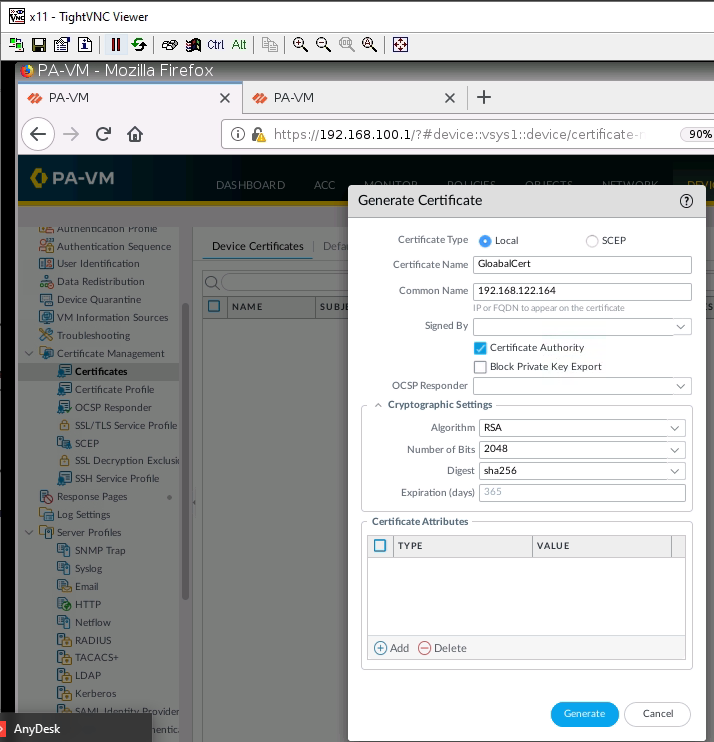
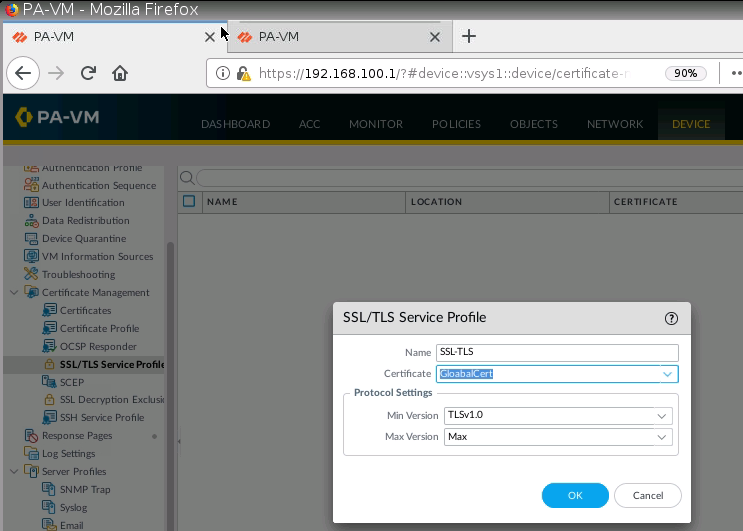
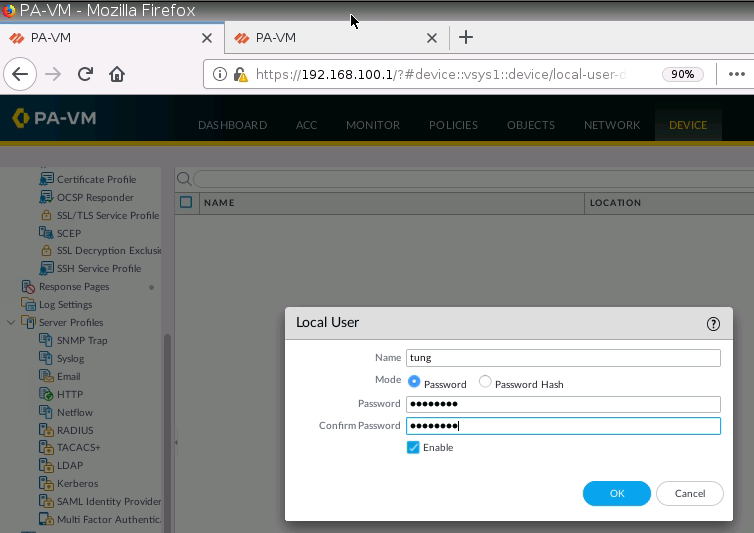
Create a new user/password.
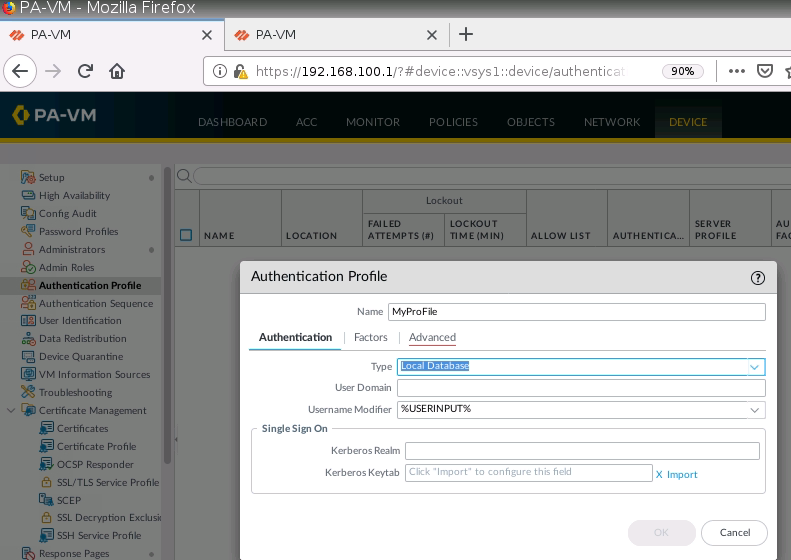
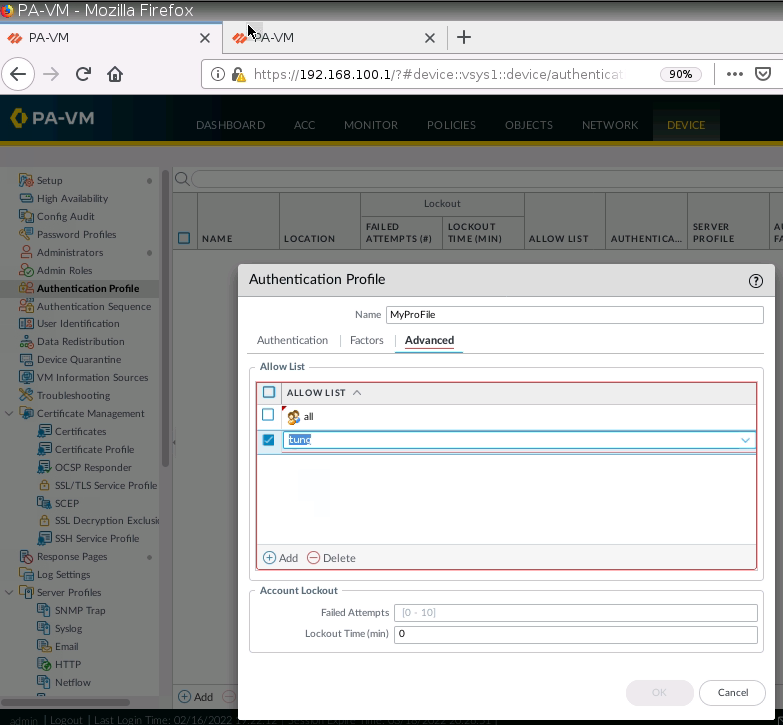
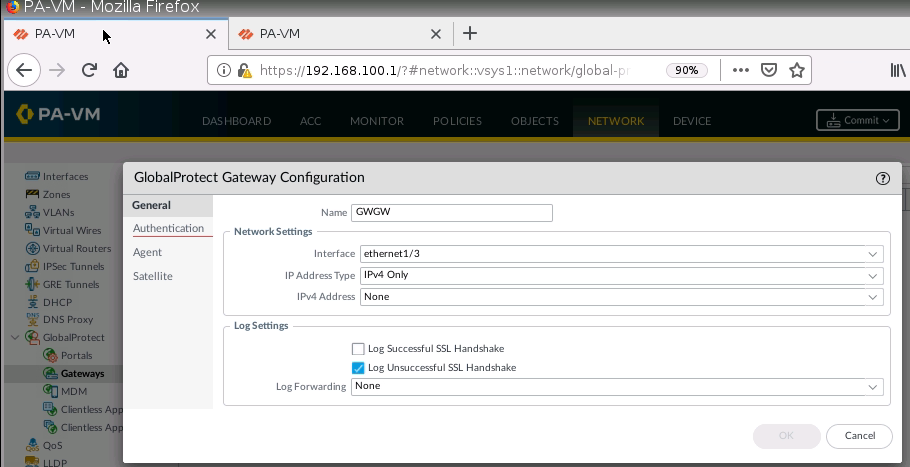
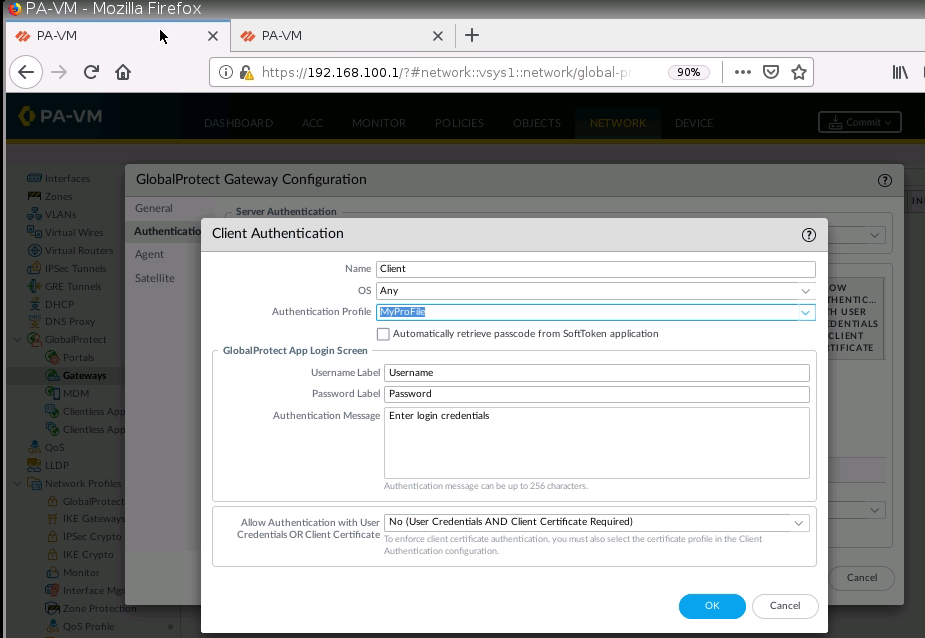
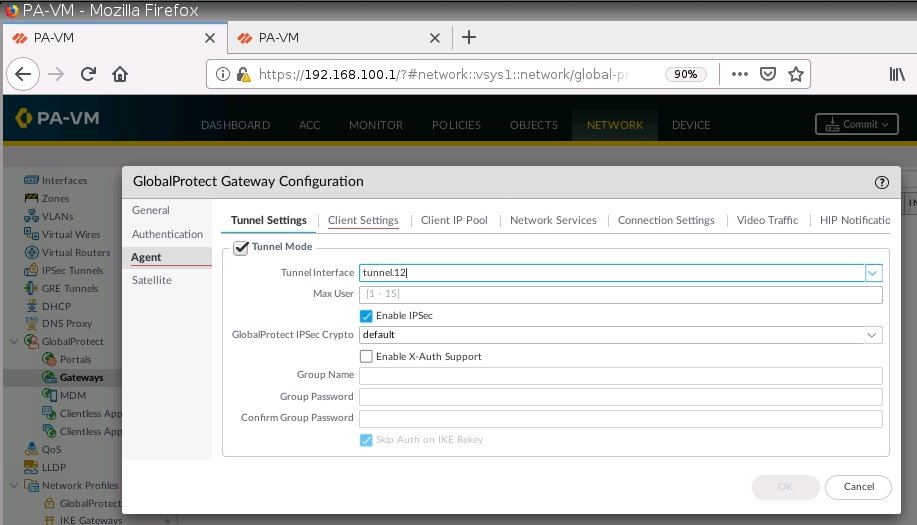
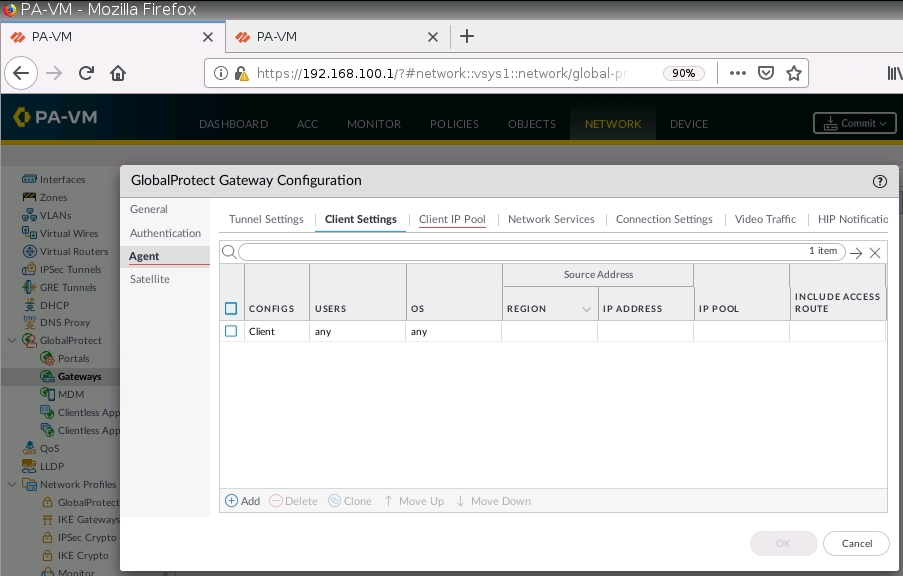
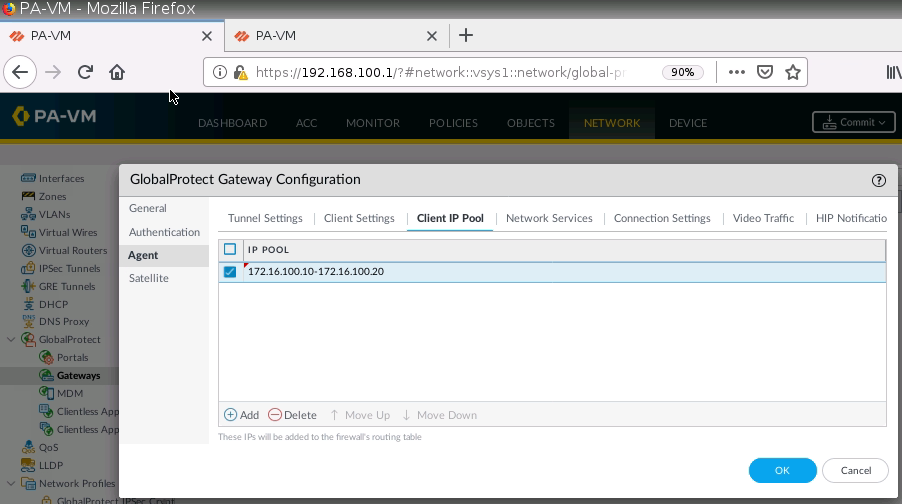
Set IP Pool for Global Protect VPN.
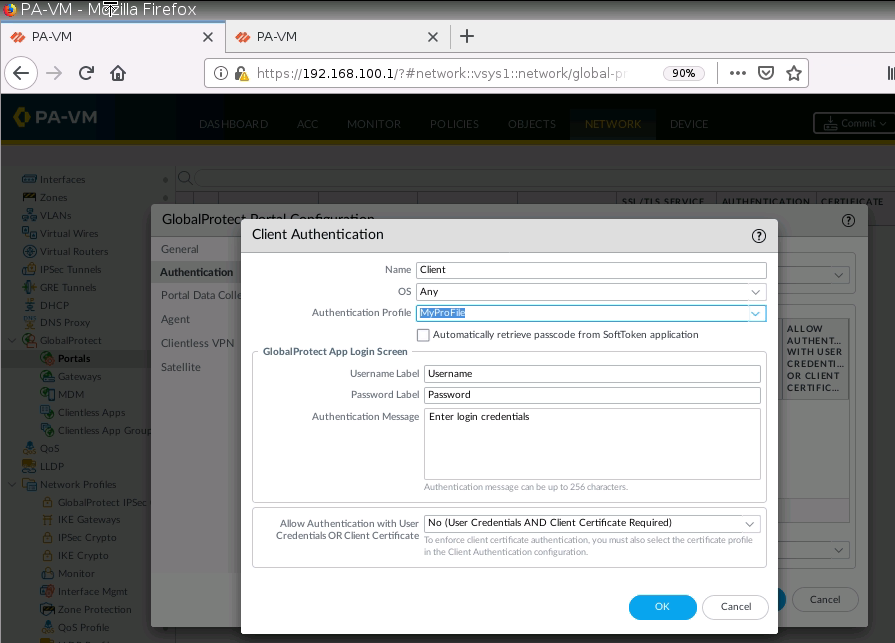
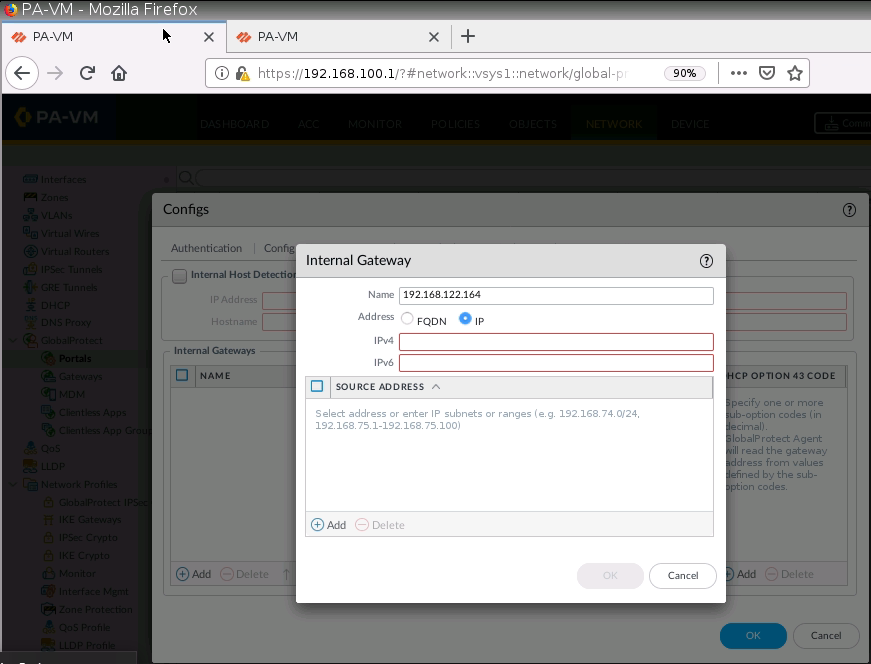
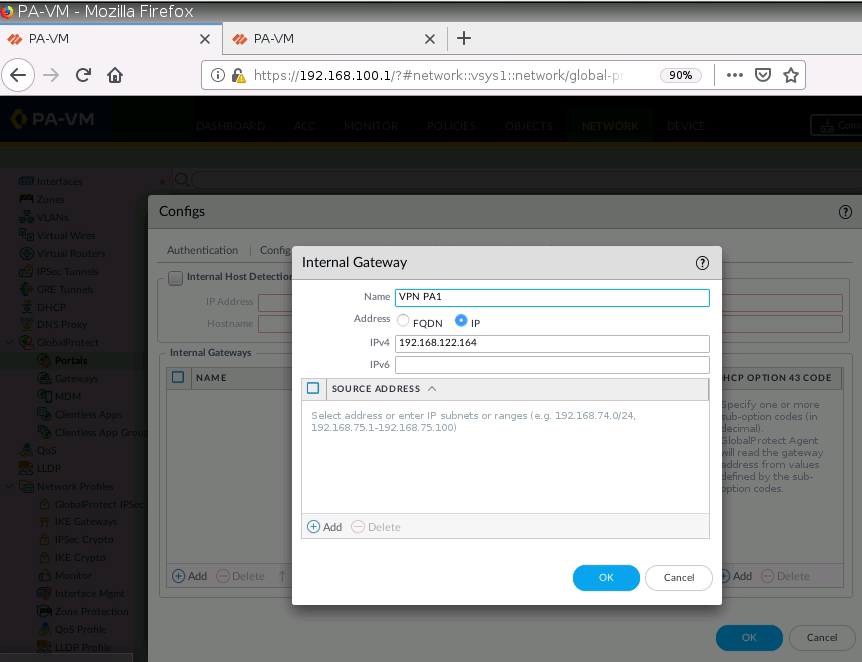
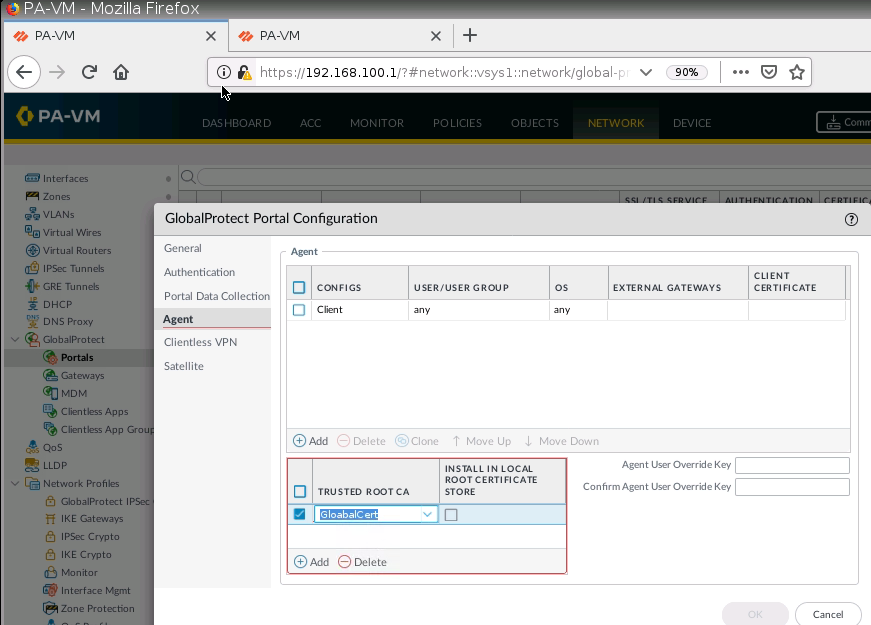
Create a new Security Rule to allow traffic from Global Protect to local networks.
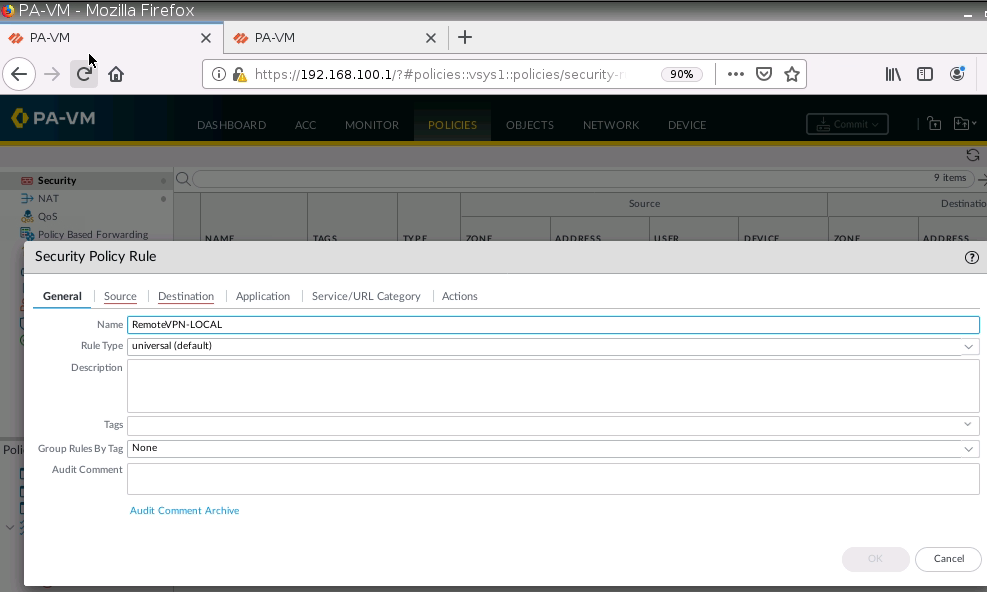
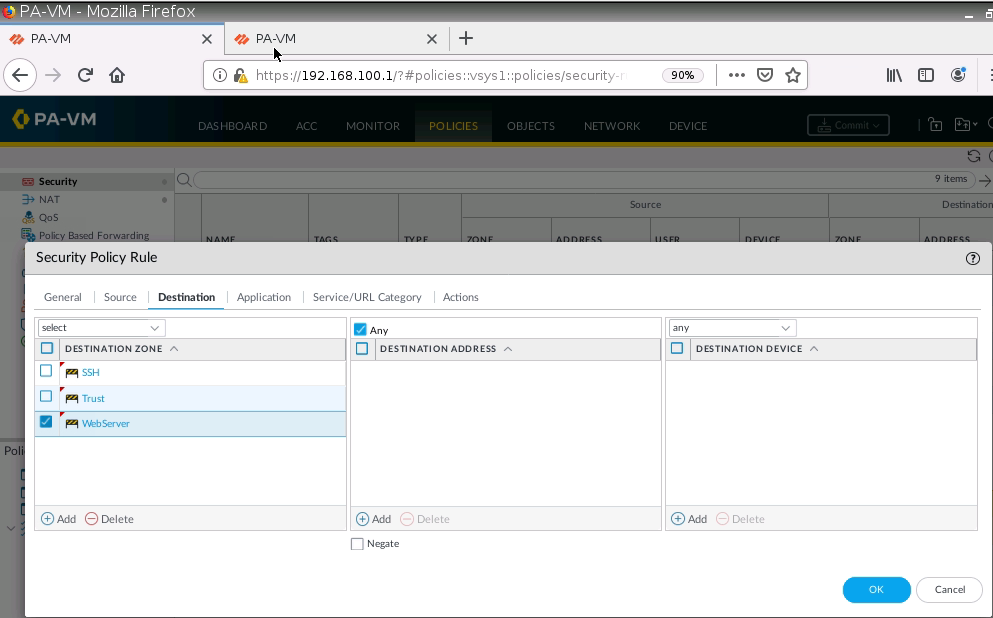
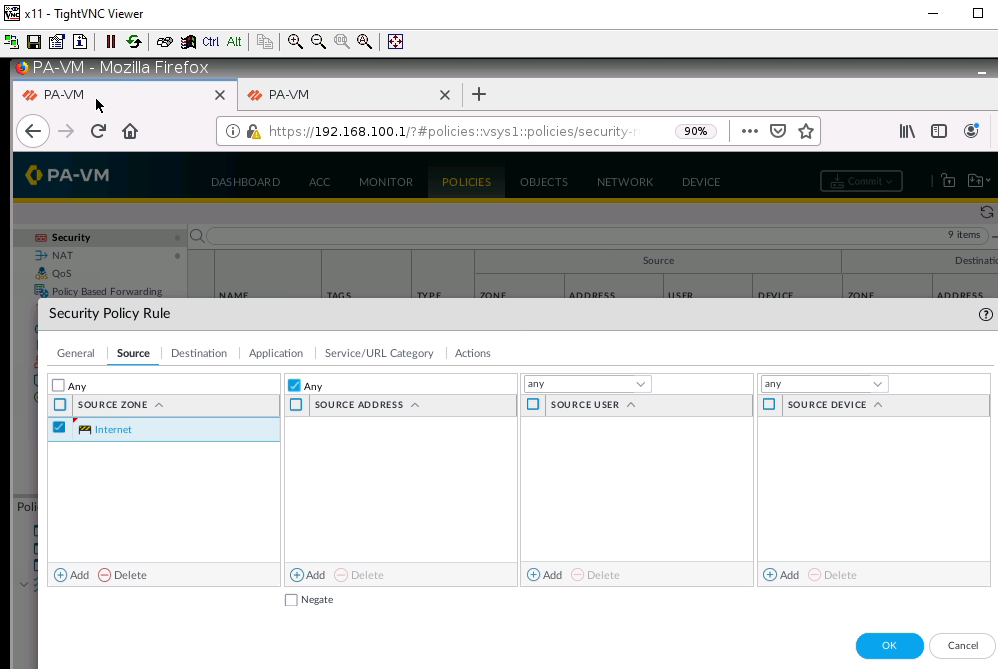
Access Global Protec VPN on Windows machine.
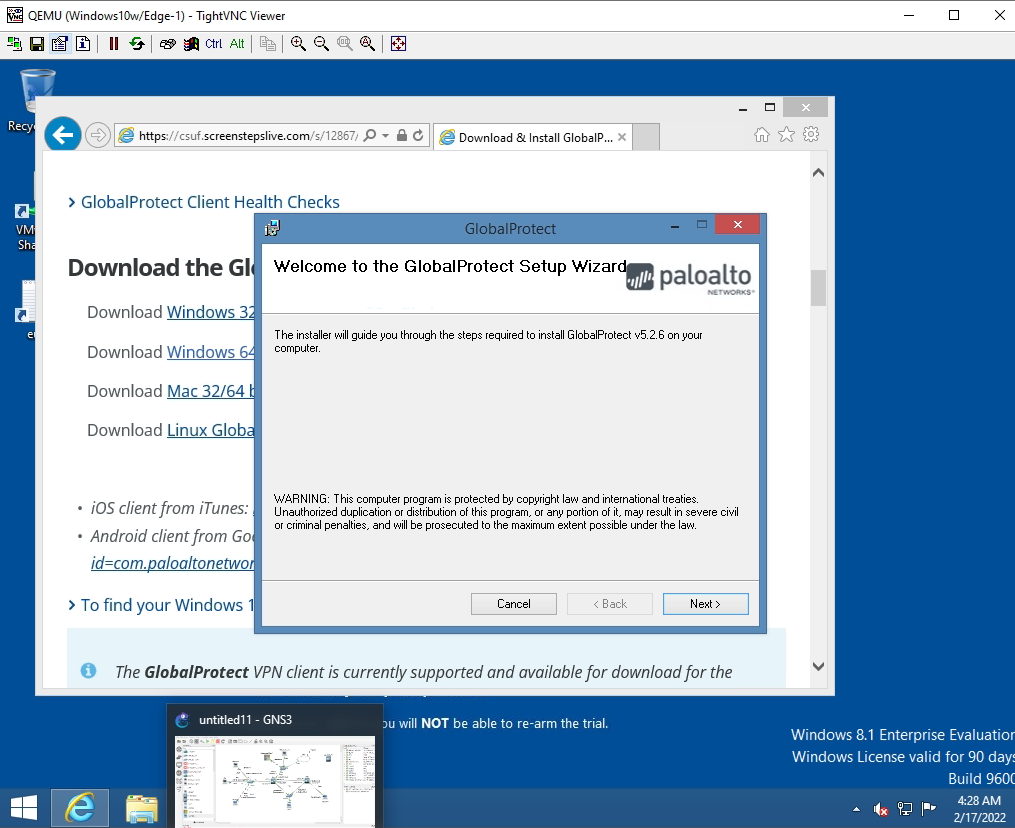

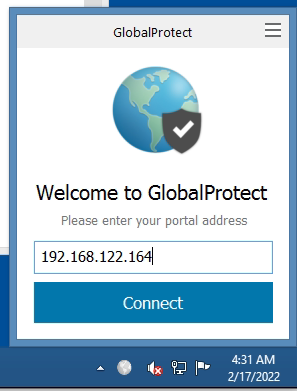
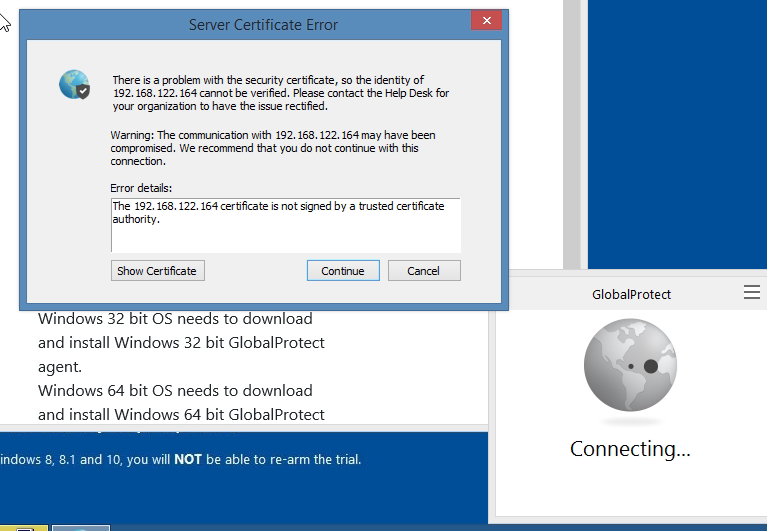
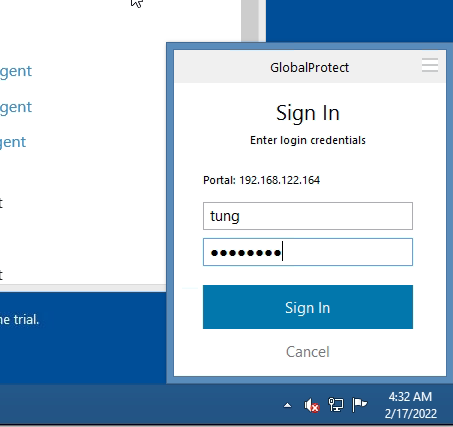
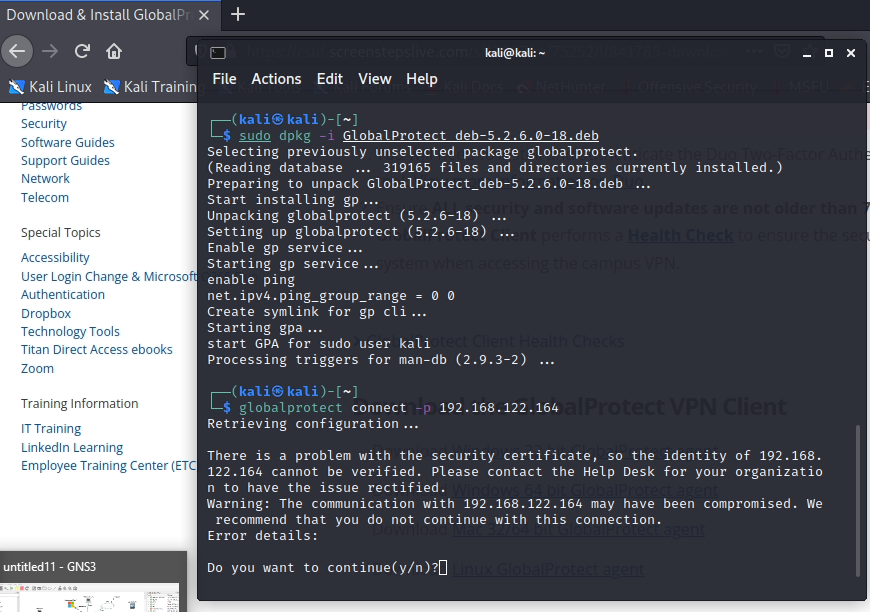
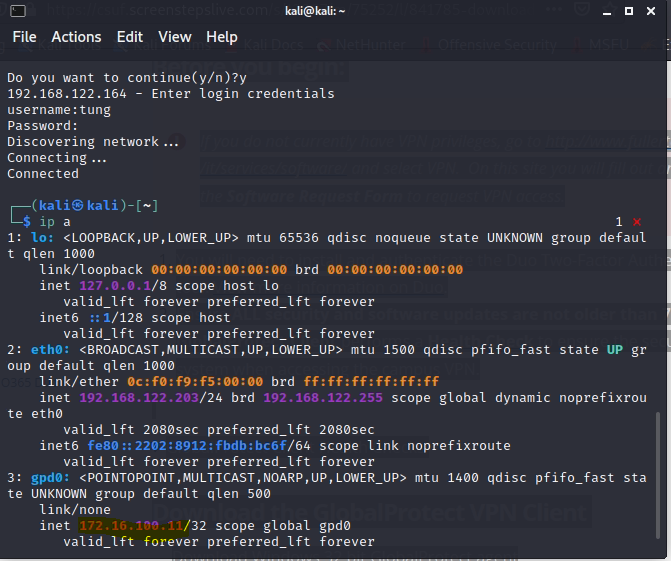
Set up GlobalProtect on Kali. Search to download Global Protect VPN on Google.
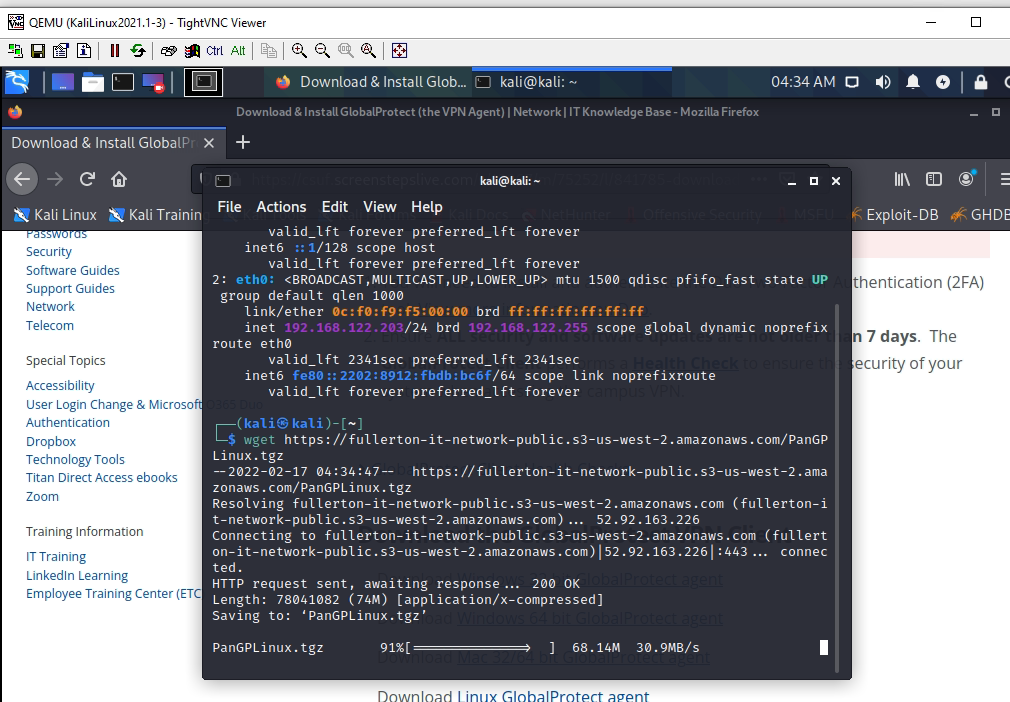
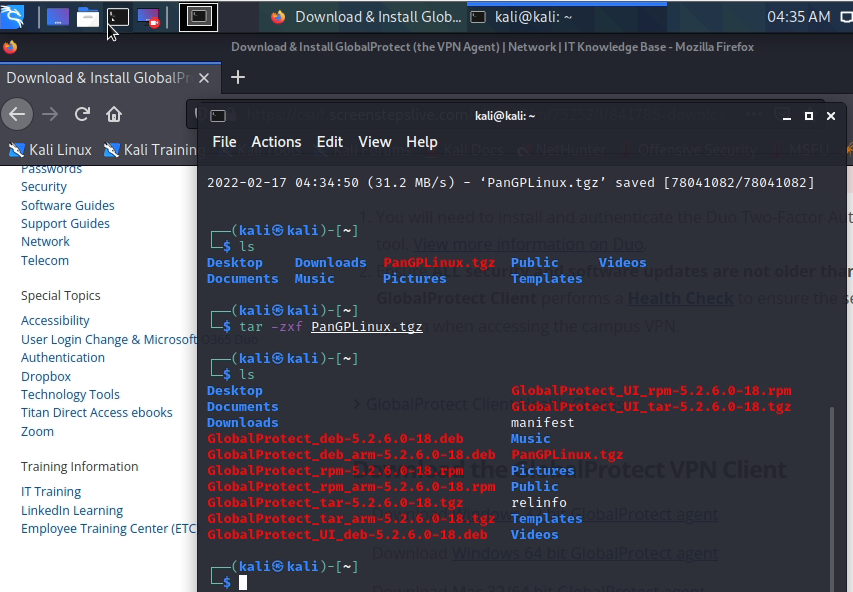
Creating a VPN tunnel via GlobalProtect.
+ Block TungBlog on PA1.
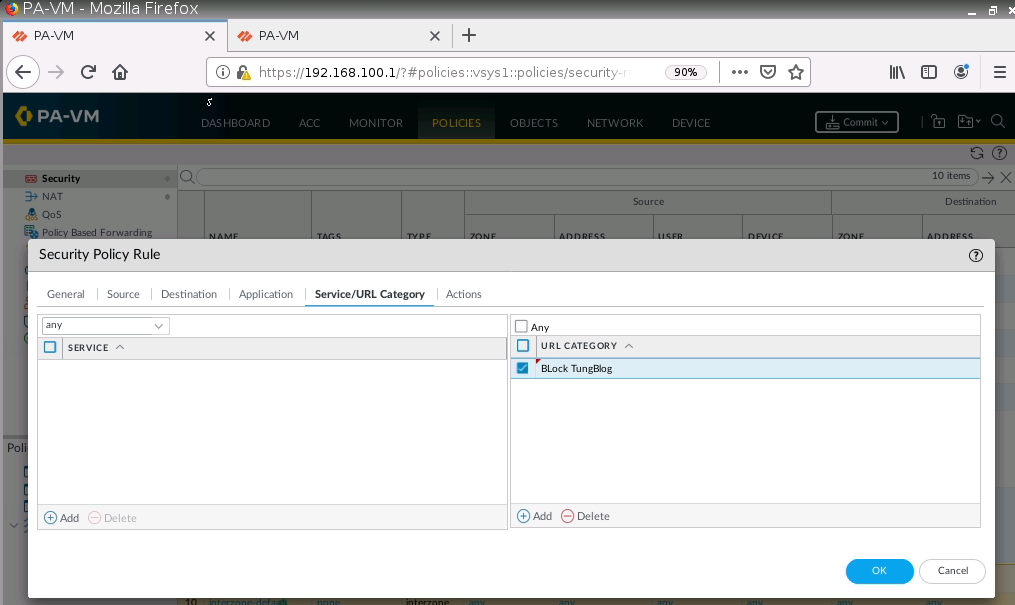
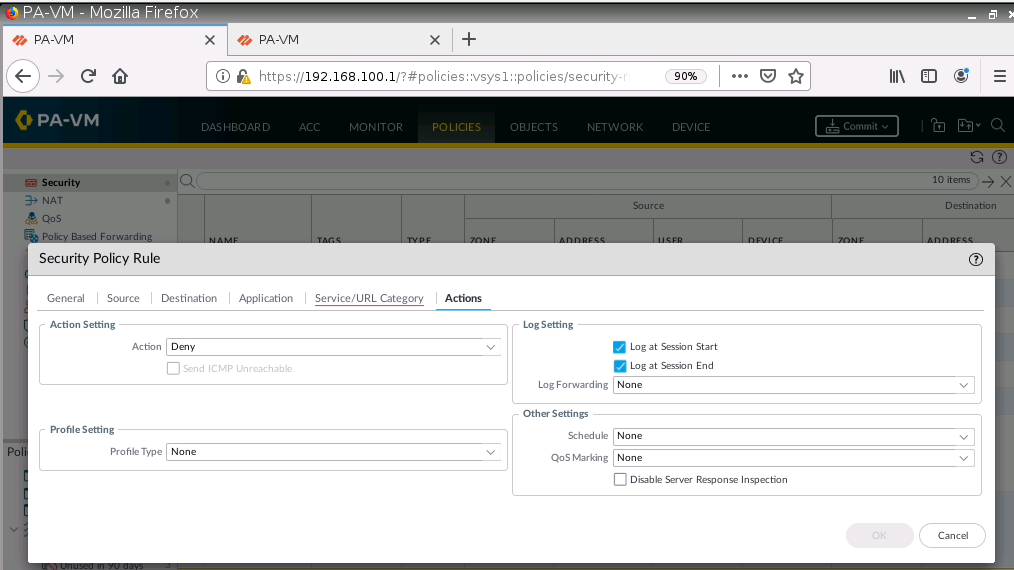
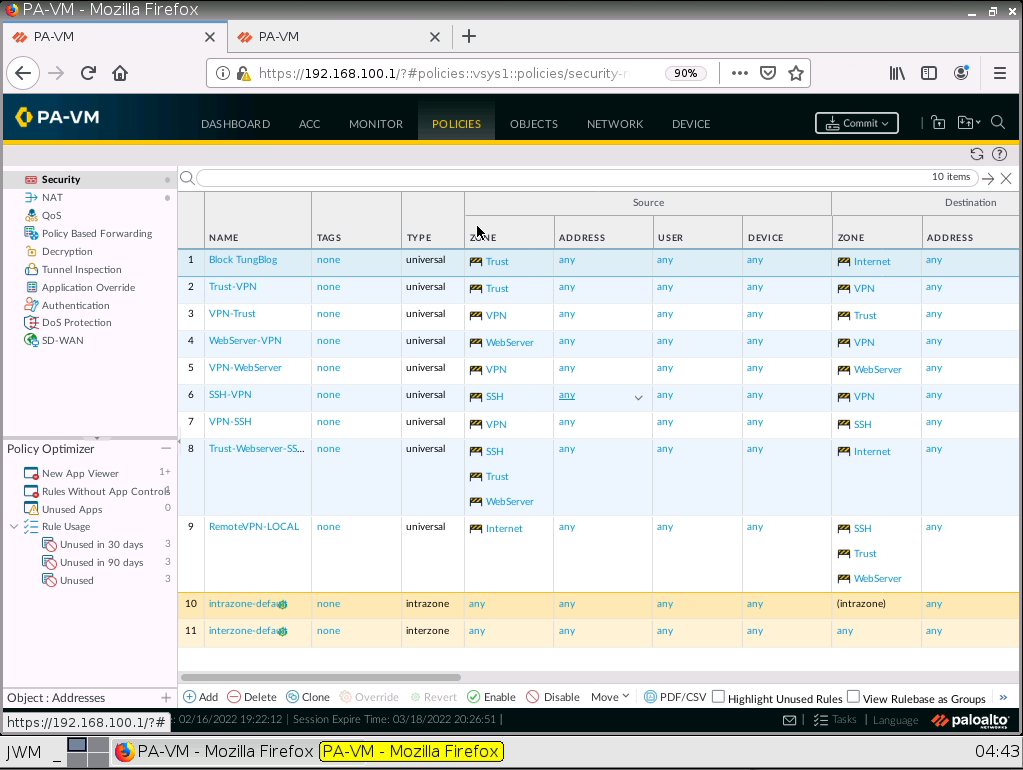
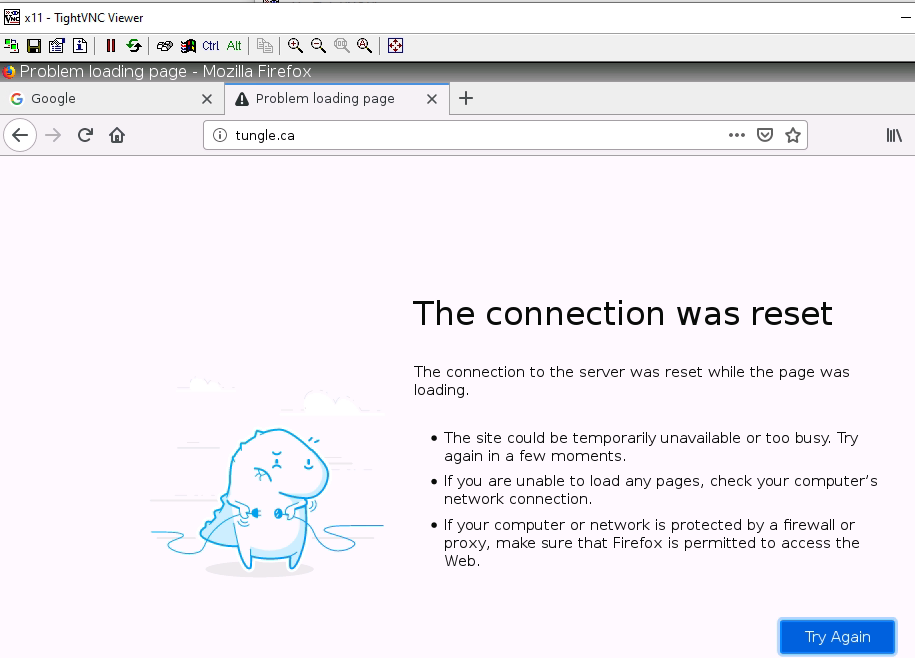
+ Setup Captive Portal on PA1.
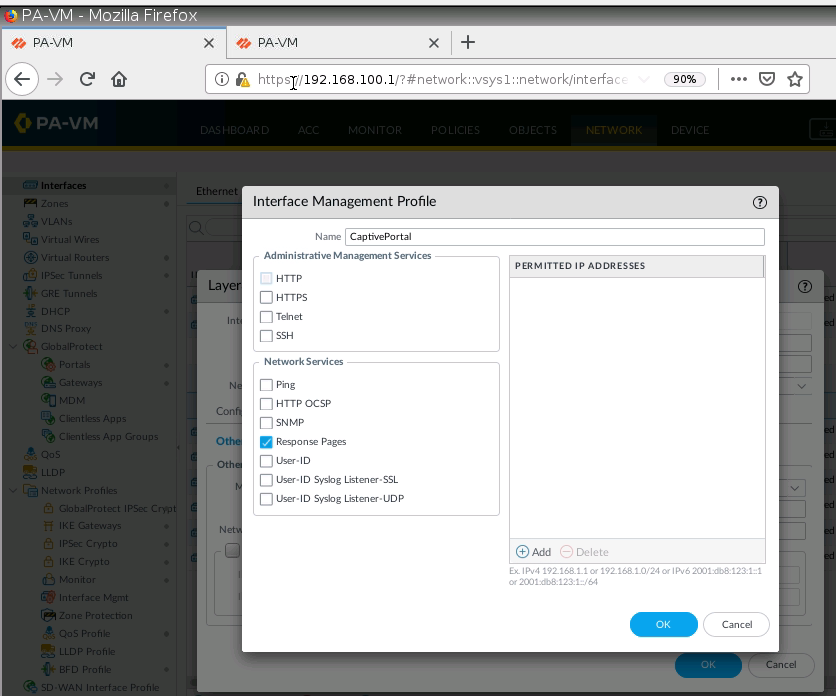
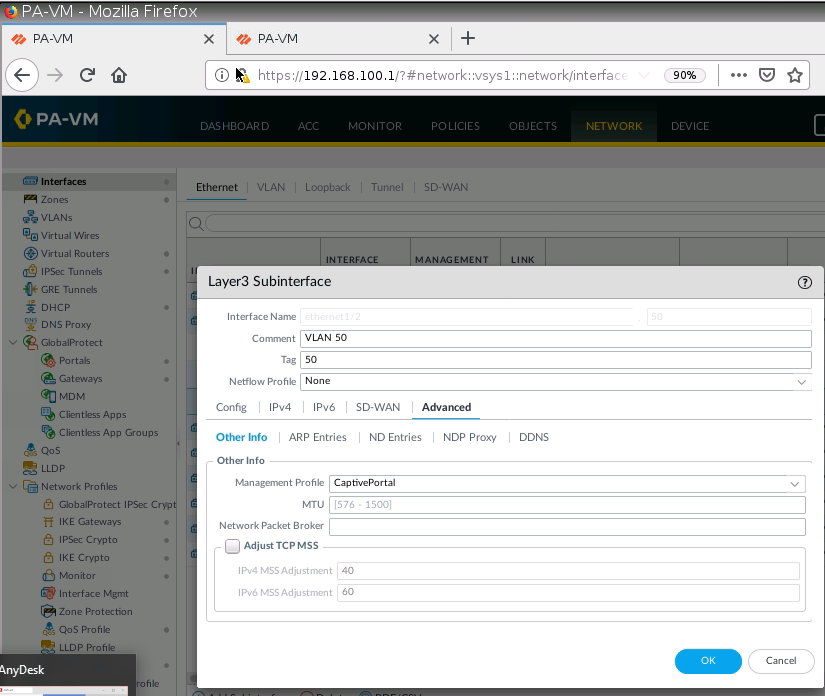
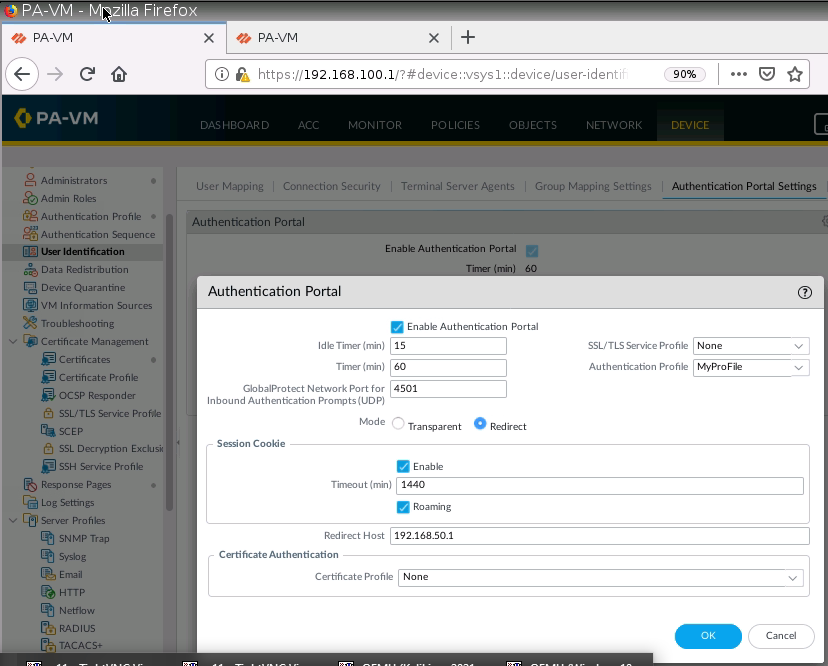
+ Ban PDF on PA1.
+ Configure DNAT on PA1.
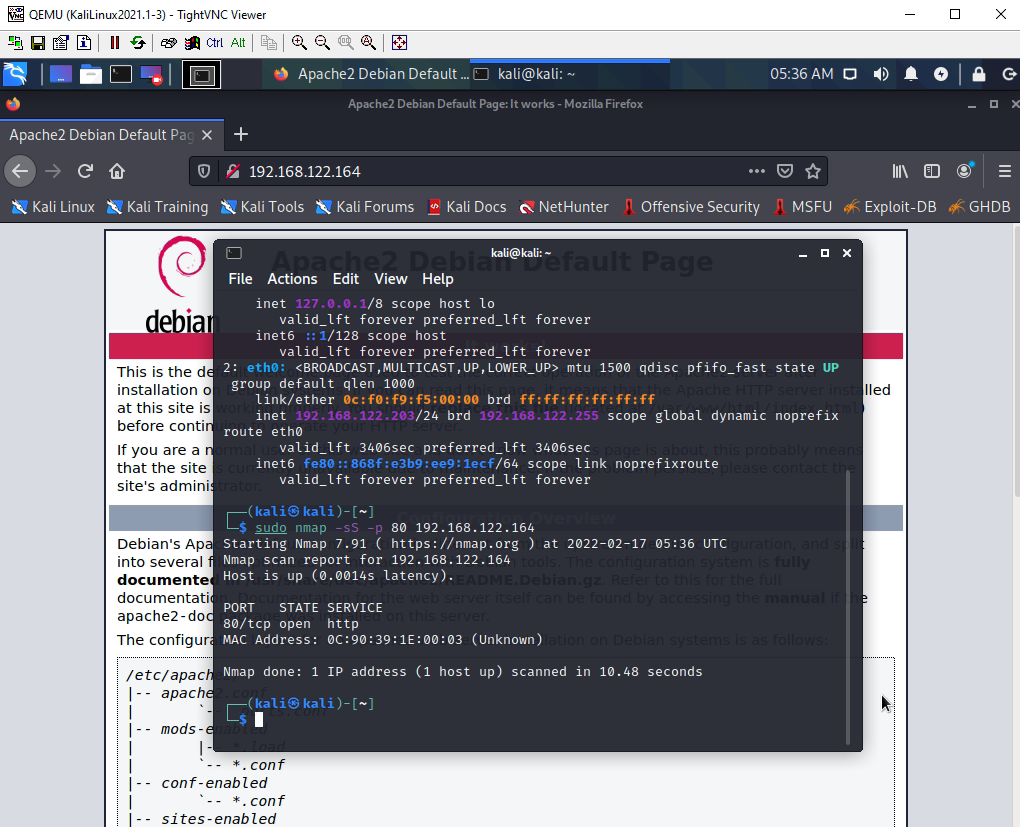
Scan ports by using Nmap tool.
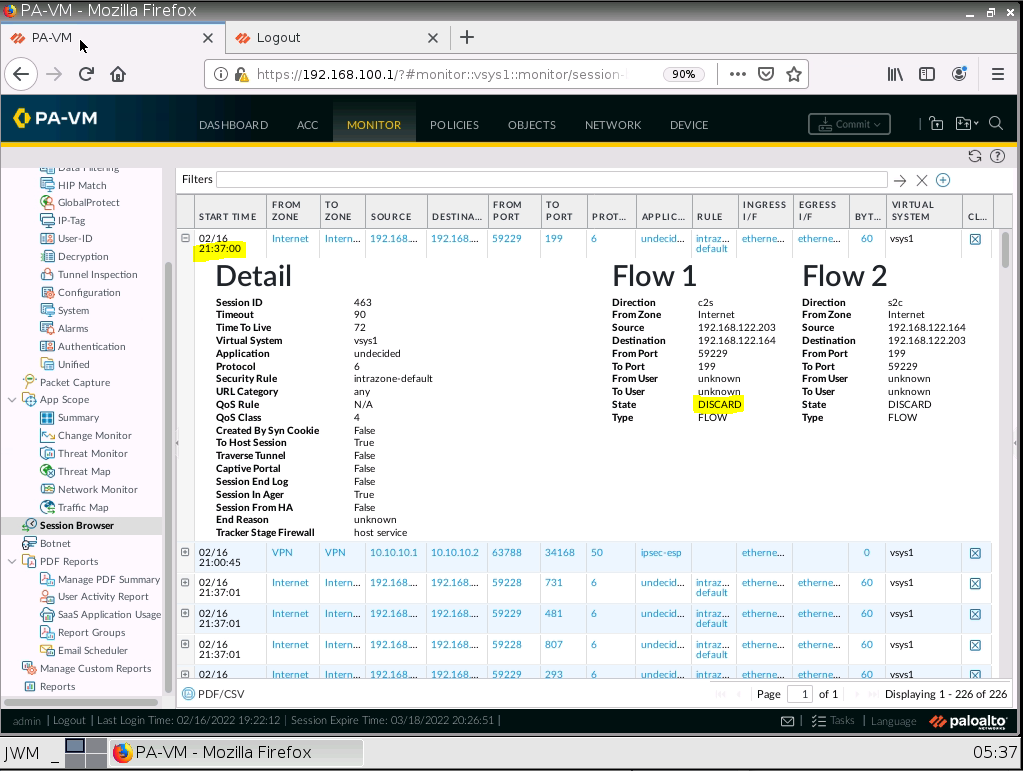
Scanned port traffic has been blocked by PA1.
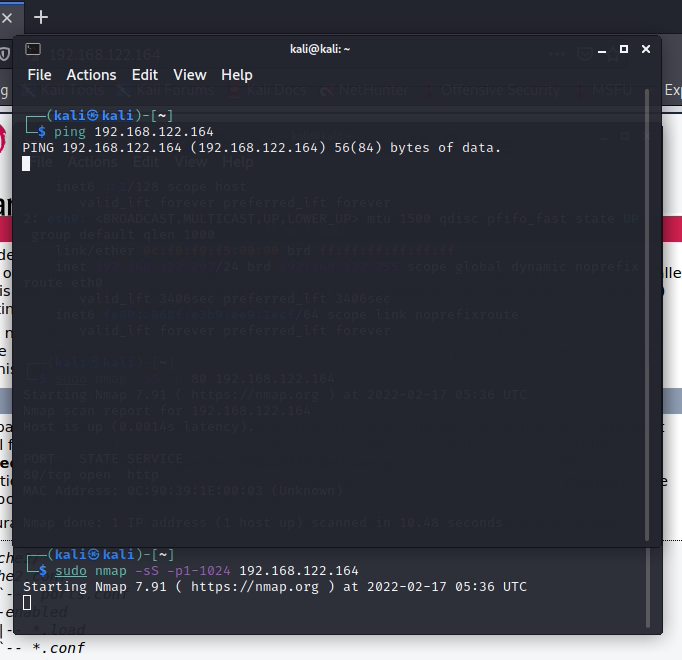
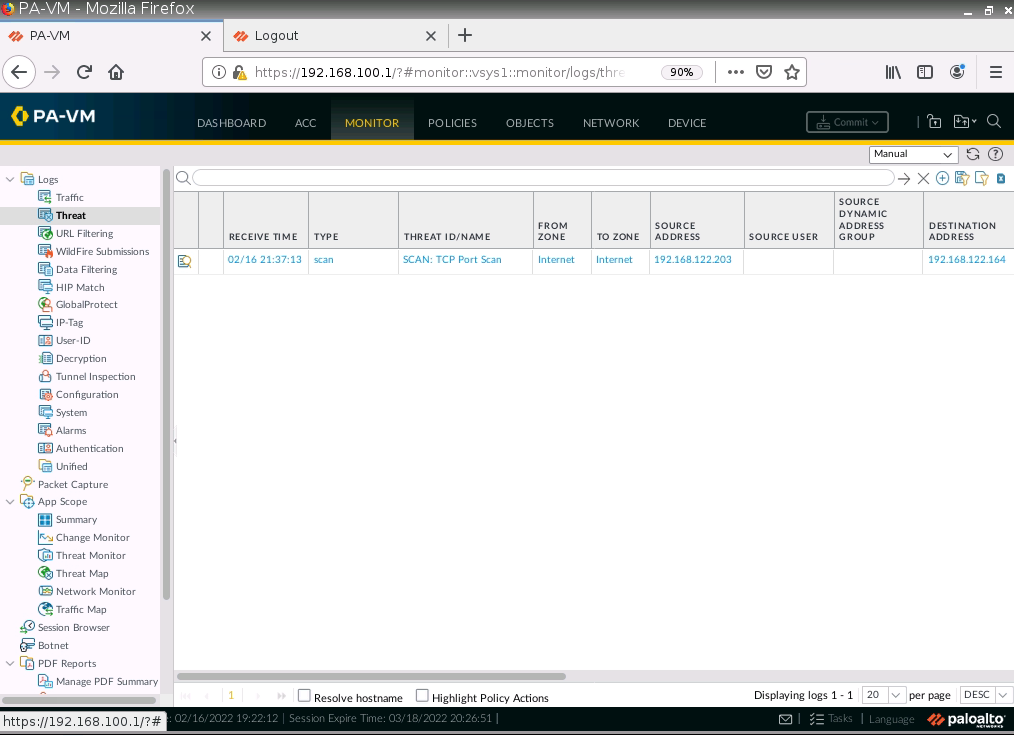
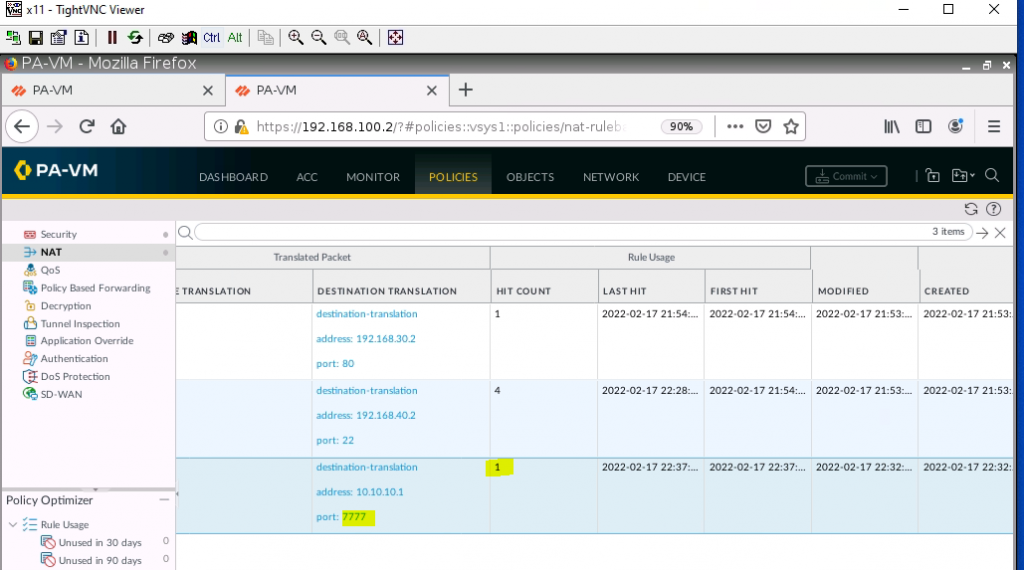
+ NAT port 9999 to port 7777 on 10.10.10.1 (PA1), then NAT again from port 7777 to 192.168.30.2:80 on Web Server.
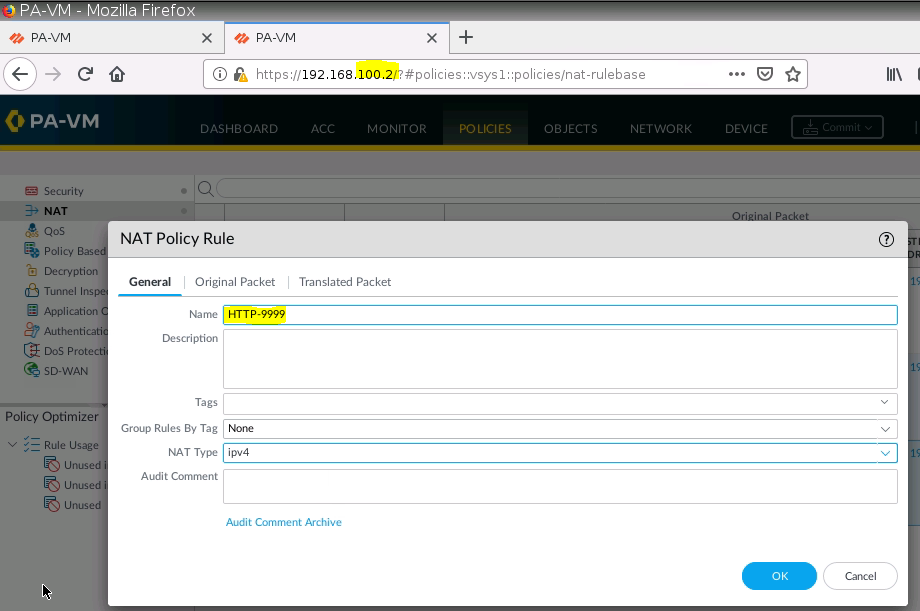
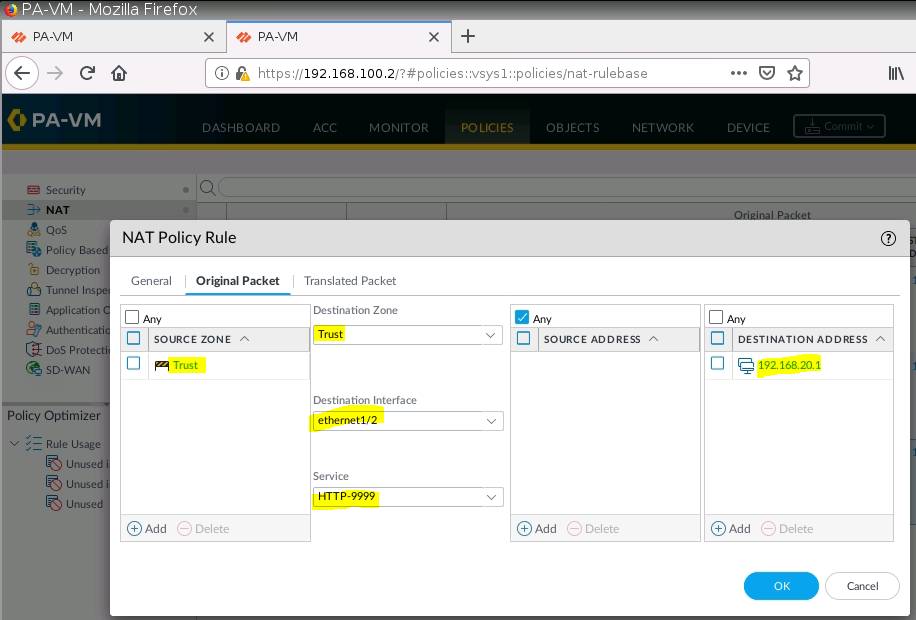
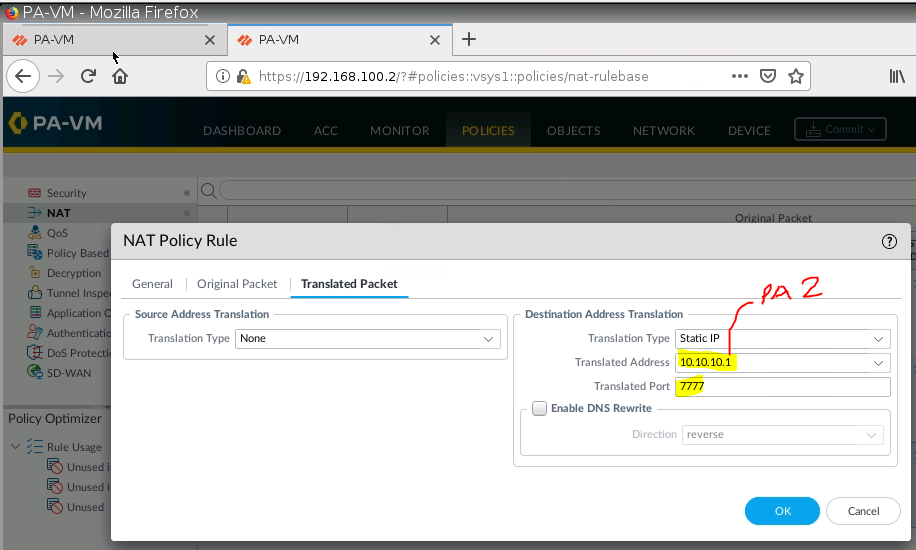
PA1: