Below is a lab topology to use to implement the OpenVPN solution on Debian 10.
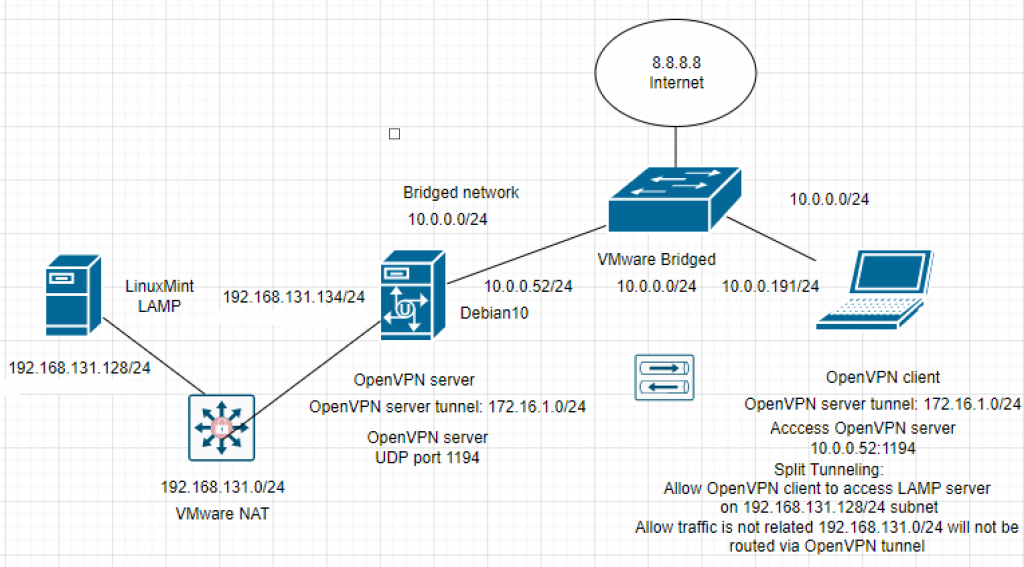
In this lab, we need to make sure clients on the Internet are able to create secure OpenVPN connections to the OpenVPN server. Also, the OpenVPN client is able to access inside the network beside the VPN tunnel (LAMP subnet: 192.168.131.0/24), and still access the Internet. Moreover, the Split tunneling feature should be used to make sure only traffic is related to accessing the LAMP subnet will be routed via the OpenVPN tunnel. All other traffic will use a public network adapter (Internet).
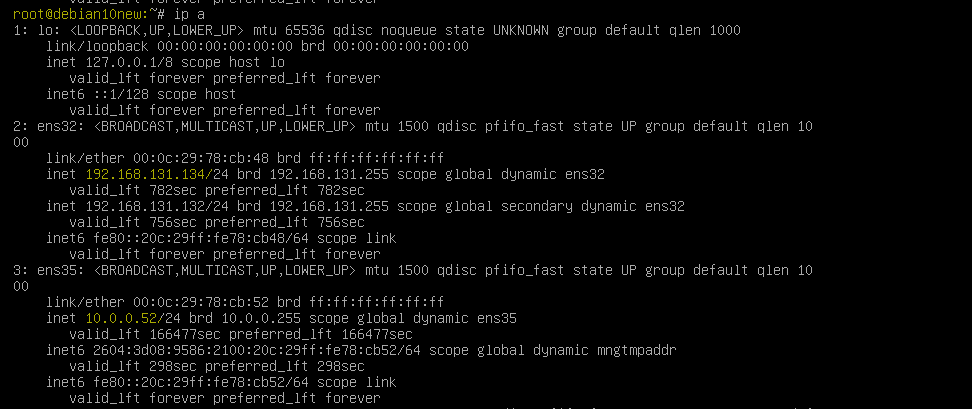
IP addresses of Debian OpenVPN server.
Access SSH from LinuxMint to easy to copy and paste commands.
Upgrade Debian’s machine.
apt-get update -y
apt-get upgrade -y+ Enable IP Forwarding
Edit the file /etc/sysctl.conf and add the line below at the end of the file.
net.ipv4.ip_forward = 1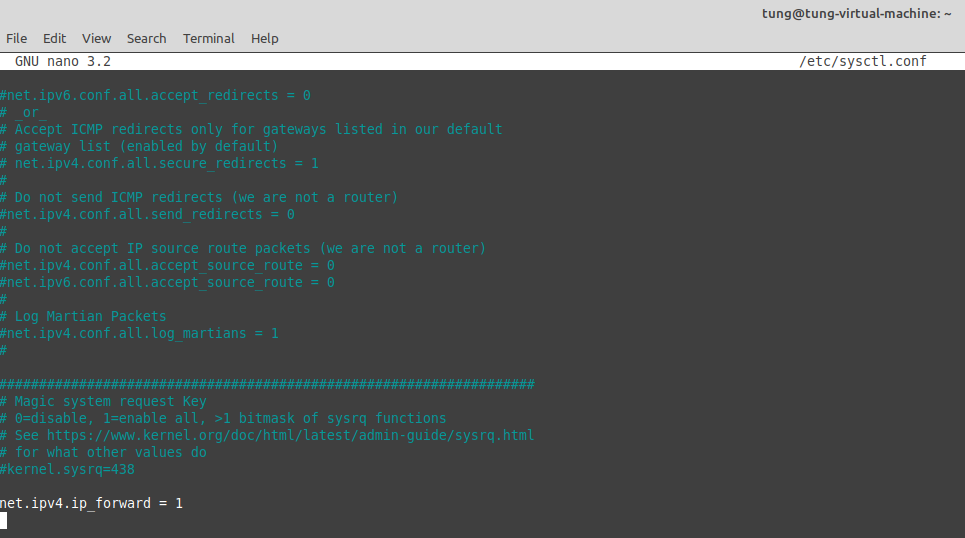
+ Enable proxy_arp for arp entry to appear on the OpenVPN server.
echo 1 > /proc/sys/net/ipv4/conf/all/proxy_arp+ Add a line below into /etc/sysctl.conf to make it permanent.
net.ipv4.conf.all.proxy_arp=1Run the following command to make the changes work.
sysctl -p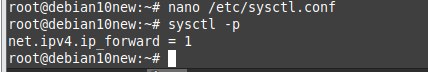
+ Install OpenVPN server.
apt-get install openvpn -y
Copy the easy-rsa directory from /usr/share directory to /etc/openvpn directory.for managing SSL certificates.
cp -r /usr/share/easy-rsa /etc/openvpn/+ Set up Certificate Authority (CA)
cd /etc/openvpn/easy-rsa
nano vars
#Add information below to the file.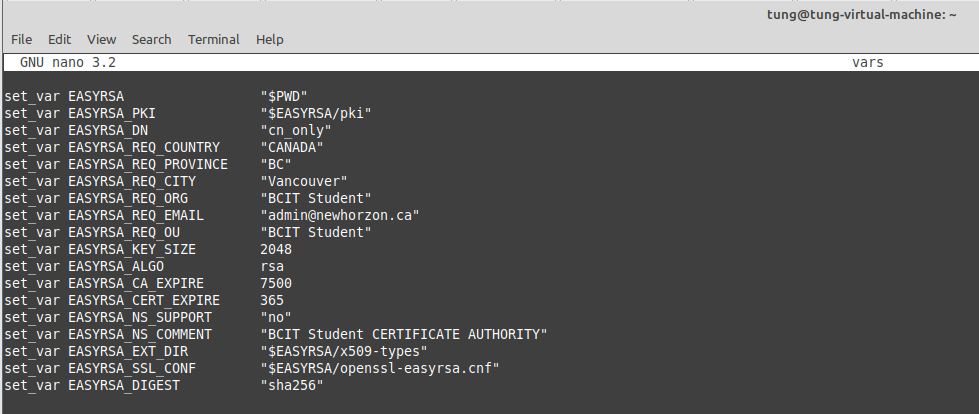
set_var EASYRSA "$PWD"
set_var EASYRSA_PKI "$EASYRSA/pki"
set_var EASYRSA_DN "cn_only"
set_var EASYRSA_REQ_COUNTRY "CANADA"
set_var EASYRSA_REQ_PROVINCE "BC"
set_var EASYRSA_REQ_CITY "Vancouver"
set_var EASYRSA_REQ_ORG "BCIT Student"
set_var EASYRSA_REQ_EMAIL "admin@newhorizon.ca"
set_var EASYRSA_REQ_OU "BCIT Student"
set_var EASYRSA_KEY_SIZE 2048
set_var EASYRSA_ALGO rsa
set_var EASYRSA_CA_EXPIRE 7500
set_var EASYRSA_CERT_EXPIRE 365
set_var EASYRSA_NS_SUPPORT "no"
set_var EASYRSA_NS_COMMENT "BCIT Student CERTIFICATE AUTHORITY"
set_var EASYRSA_EXT_DIR "$EASYRSA/x509-types"
set_var EASYRSA_SSL_CONF "$EASYRSA/openssl-easyrsa.cnf"
set_var EASYRSA_DIGEST "sha256"
Run the following command to initiate your own PKI.
./easyrsa init-pki
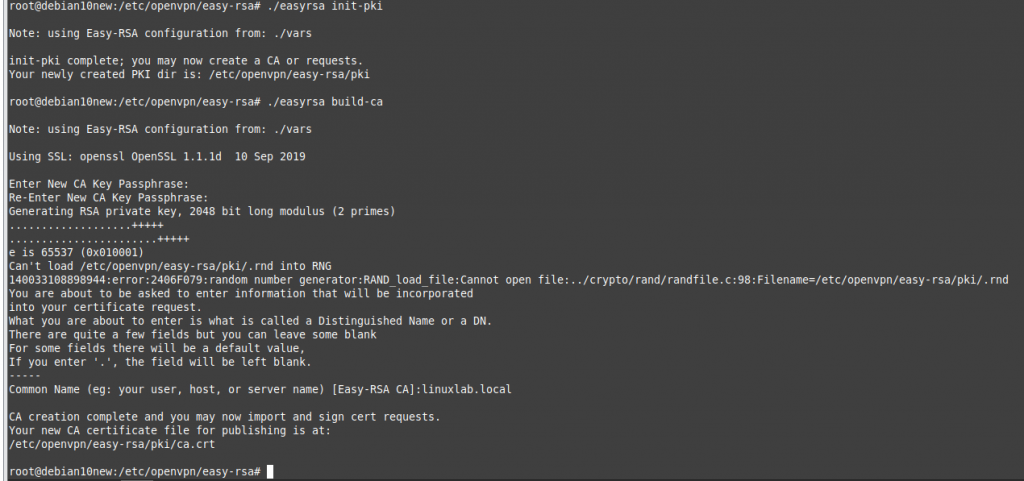
Build the CA certificates.
./easyrsa build-ca
+ Generate Server Certificate Files.
./easyrsa gen-req tung-server nopass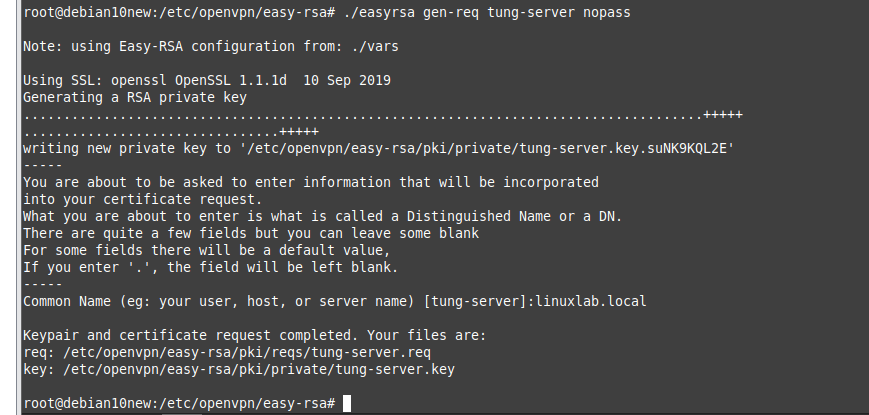
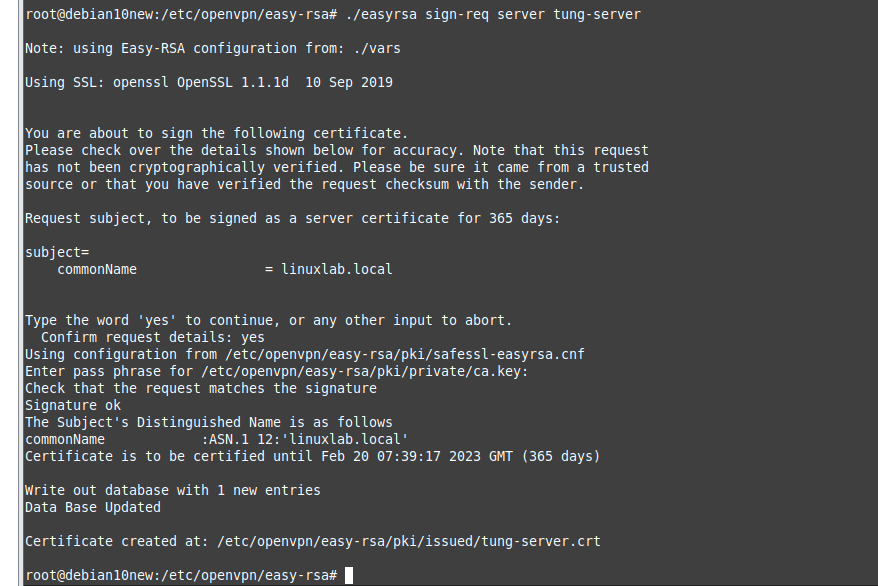
+ Sign the public key of the Server Using Root CA.
./easyrsa sign-req server tung-server
Verify cert.
openssl verify -CAfile pki/ca.crt pki/issued/tung-server.crt 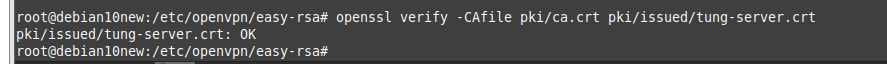
+ Create a strong Diffie-Hellman key to use for the key exchange
./easyrsa gen-dh
After creating all certificate files, copy them to the /etc/openvpn/server/ directory.
cp pki/ca.crt /etc/openvpn/server/
cp pki/dh.pem /etc/openvpn/server/
cp pki/private/tung-server.key /etc/openvpn/server/
cp pki/issued/tung-server.crt /etc/openvpn/server/+ Generate Client Certificate and Key File
./easyrsa gen-req client nopass
Next, sign the client key using your CA certificate.
./easyrsa sign-req client clientNext, copy all client certificate and key file to the /etc/openvpn/client/ directory
cp pki/ca.crt /etc/openvpn/client/
cp pki/issued/client.crt /etc/openvpn/client/
cp pki/private/client.key /etc/openvpn/client/
+ Configure OpenVPN Server
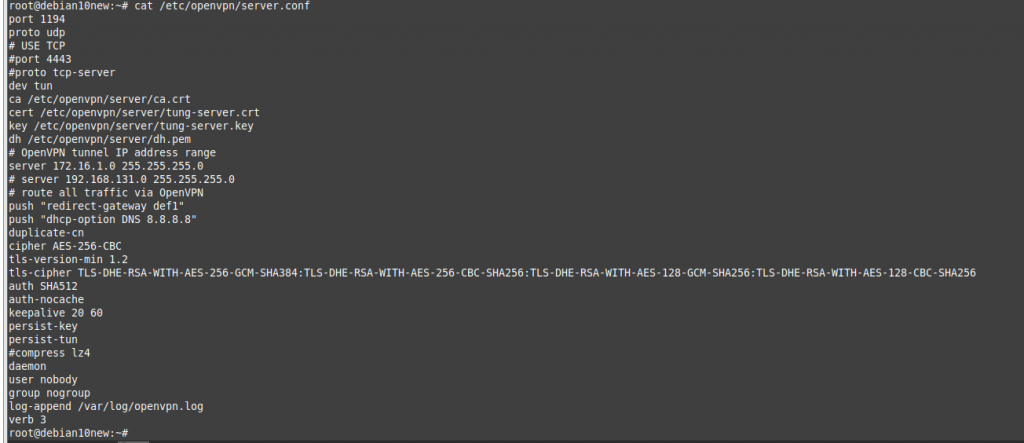
nano /etc/openvpn/server.conf
#---
root@debian10new:~# cat /etc/openvpn/server.conf
port 1194
proto udp
# USE TCP
#port 4443
#proto tcp-server
dev tun
ca /etc/openvpn/server/ca.crt
cert /etc/openvpn/server/tung-server.crt
key /etc/openvpn/server/tung-server.key
dh /etc/openvpn/server/dh.pem
# OpenVPN tunnel IP address range
server 172.16.1.0 255.255.255.0
# server 192.168.131.0 255.255.255.0
# route all traffic via OpenVPN
push "redirect-gateway def1"
push "dhcp-option DNS 8.8.8.8"
duplicate-cn
cipher AES-256-CBC
tls-version-min 1.2
tls-cipher TLS-DHE-RSA-WITH-AES-256-GCM-SHA384:TLS-DHE-RSA-WITH-AES-256-CBC-SHA256:TLS-DHE-RSA-WITH-AES-128-GCM-SHA256:TLS-DHE-RSA-WITH-AES-128-CBC-SHA256
auth SHA512
auth-nocache
keepalive 20 60
persist-key
persist-tun
#disable compress lz4 because of error on OpenVPN client
#compress lz4
daemon
user nobody
group nogroup
log-append /var/log/openvpn.log
verb 3
root@debian10new:~#
#---
+ Start OpenVPN service.
systemctl start openvpn@server
systemctl enable openvpn@server
systemctl status openvpn@server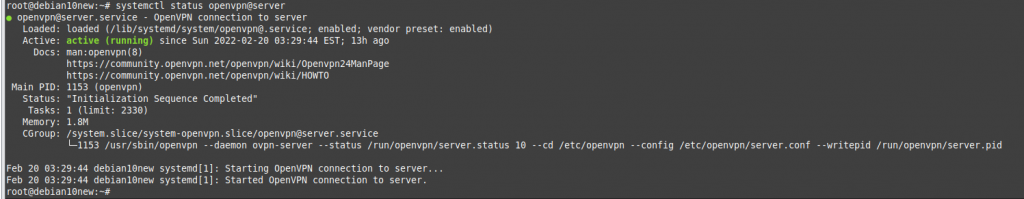
Show OpenVPN tunnel.
ip a show tun0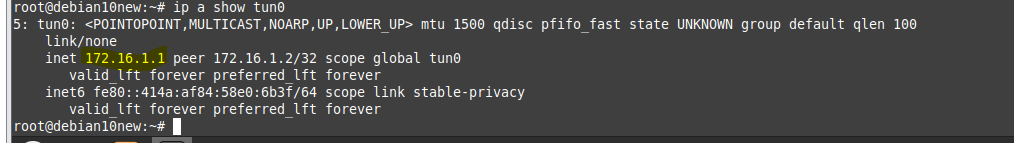
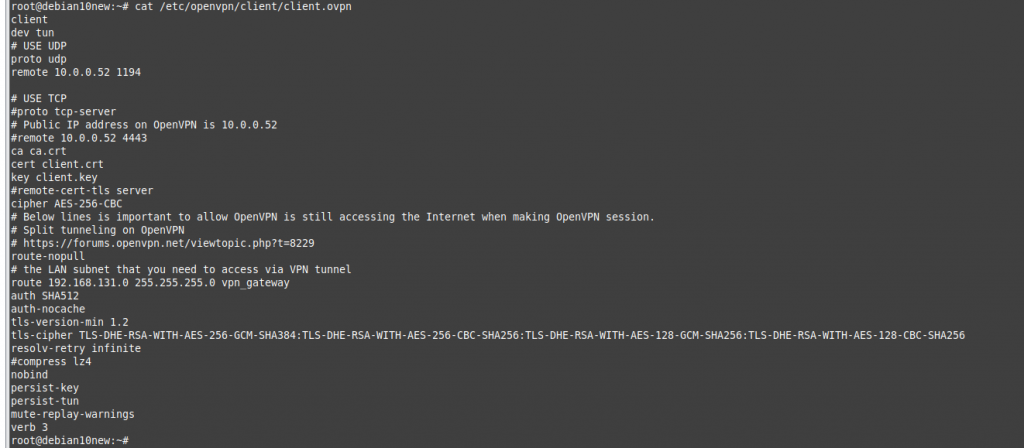
+ Generate client configuration.
nano /etc/openvpn/client/client.ovpn #--- client dev tun # USE UDP proto udp remote 10.0.0.52 1194 # USE TCP #proto tcp-server # Public IP address on OpenVPN is 10.0.0.52 #remote 10.0.0.52 4443 ca ca.crt cert client.crt key client.key #remote-cert-tls server cipher AES-256-CBC # Below lines is important to allow OpenVPN is still accessing the Internet when making OpenVPN session. # Split tunneling on OpenVPN # https://forums.openvpn.net/viewtopic.php?t=8229 route-nopull # the LAN subnet that you need to access via VPN tunnel route 192.168.131.0 255.255.255.0 vpn_gateway auth SHA512 auth-nocache tls-version-min 1.2 tls-cipher TLS-DHE-RSA-WITH-AES-256-GCM-SHA384:TLS-DHE-RSA-WITH-AES-256-CBC-SHA256:TLS-DHE-RSA-WITH-AES-128-GCM-SHA256:TLS-DHE-RSA-WITH-AES-128-CBC-SHA256 resolv-retry infinite #compress lz4 nobind persist-key persist-tun mute-replay-warnings verb 3 #---
+ Configure routing using UFW.
By default, the UFW firewall is not installed in Debian 10.
apt-get install ufw -yConfigure UFW to accept the forwarded packets.
nano /etc/default/ufw
# Change the following line:
DEFAULT_FORWARD_POLICY="ACCEPT"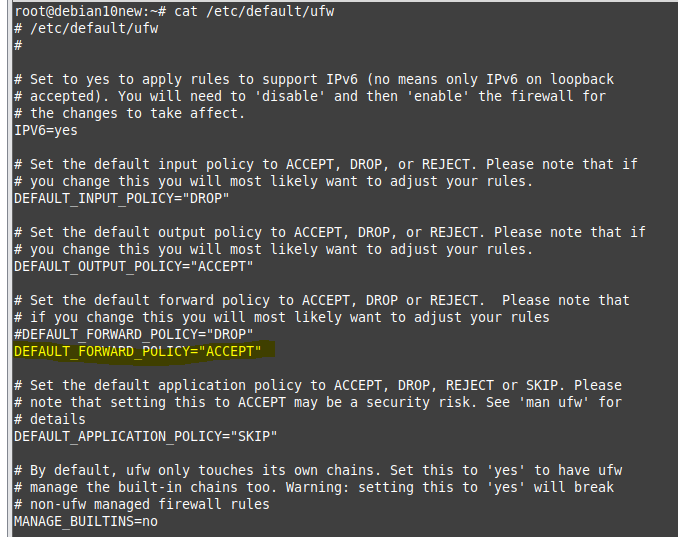
nano /etc/ufw/before.rules
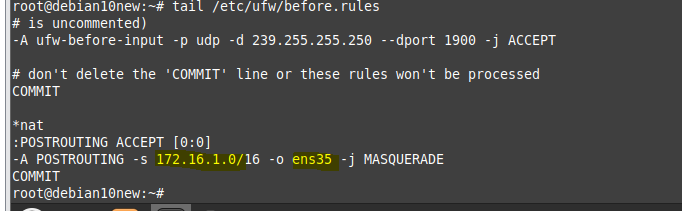
Note: Replace ens3 with the name of your public network interface in Debian OpenVPN server is ens35.
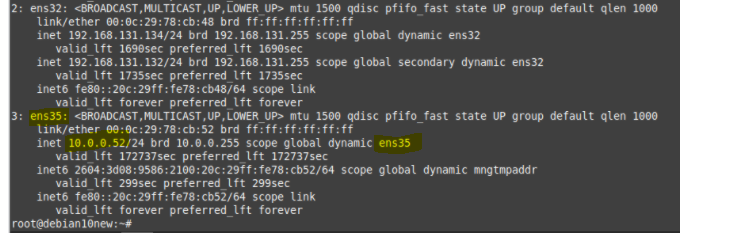
Allow the default OpenVPN port 1194 and OpenSSH. Then, reload the UFW firewall.
ufw allow 1194/udp
ufw allow OpenSSH
ufw disable
ufw enable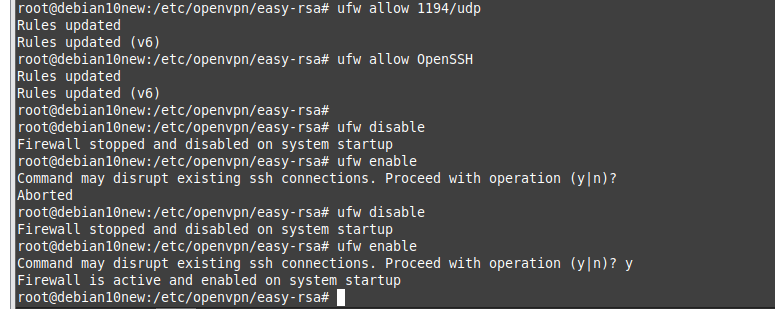
+ Connect OpenVPN from a client.
Install OpenVPN from the Kali machine.
apt-get install openvpn -y
On the client machine, run the command below to download all the client configuration files.
# public-vpn-server-ip: is 10.0.0.52 scp -r root@public-vpn-server-ip:/etc/openvpn/client .
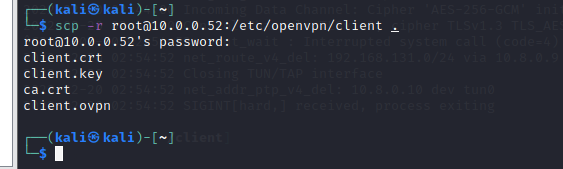
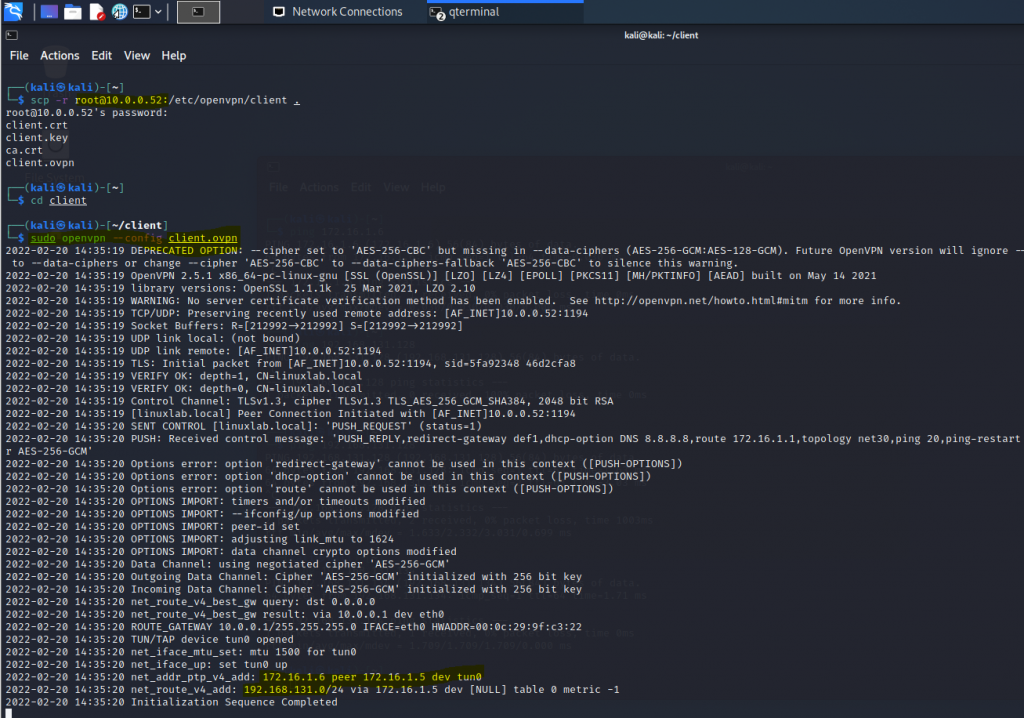
Check OpenVPN tunnel.
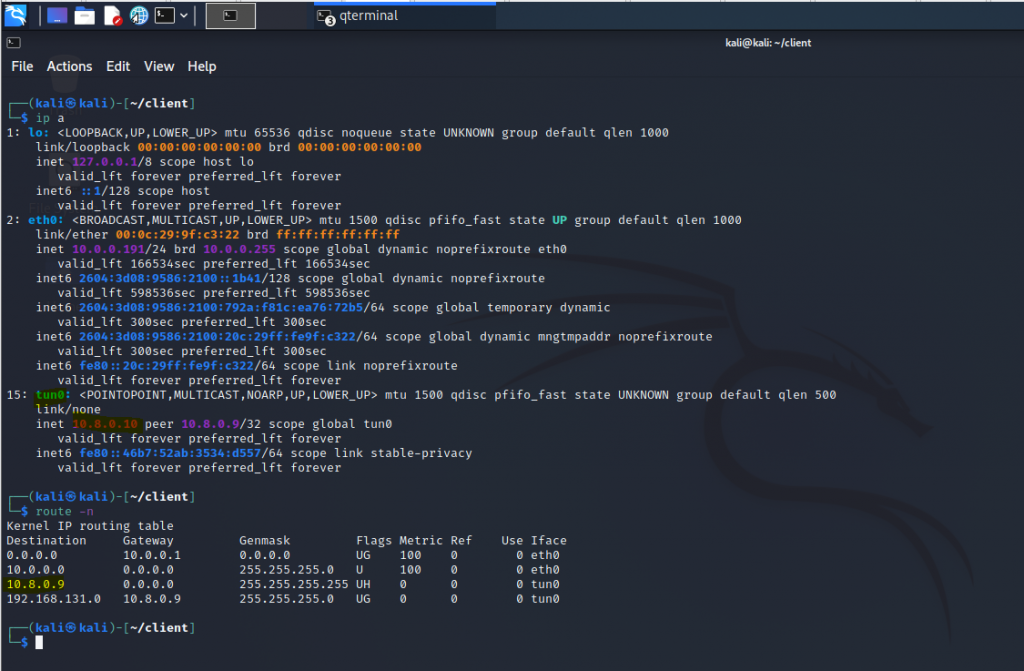
On OpenVPN client.
ping 8.8.8.8 (Internet)
ping 192.168.131.134 (OpenVPN gw tunnel)
ping 192.168.131.128 (LAMP server behind OpenVPN server)
We can see split tunneling is working well on OpenVPN.
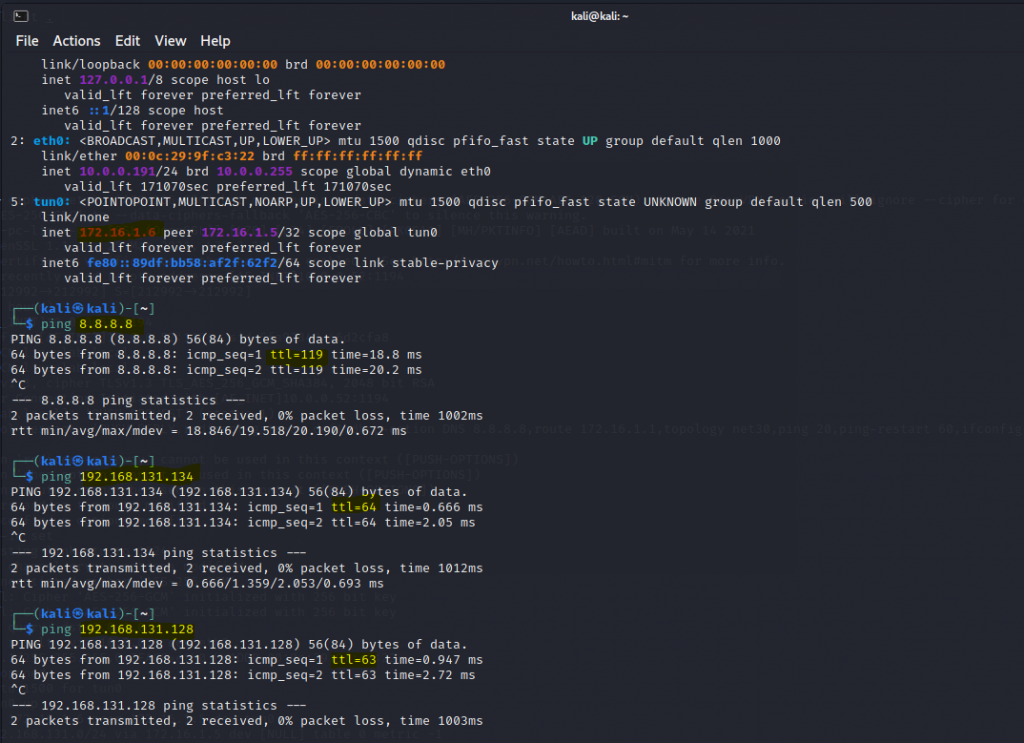
Access LAMP server.
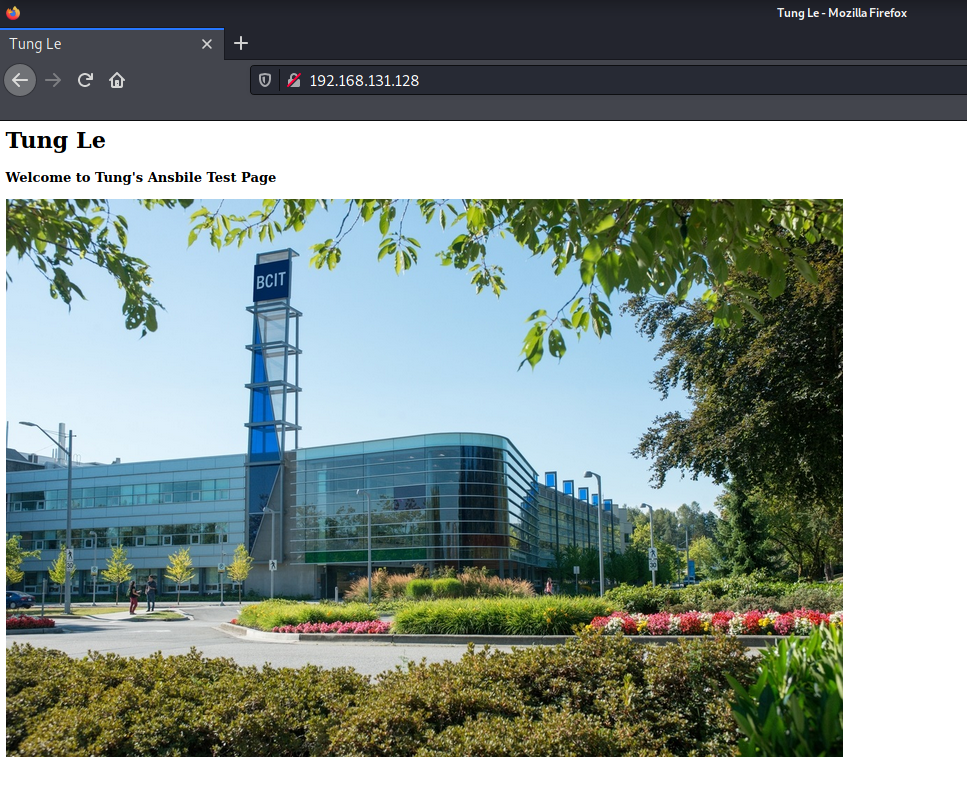
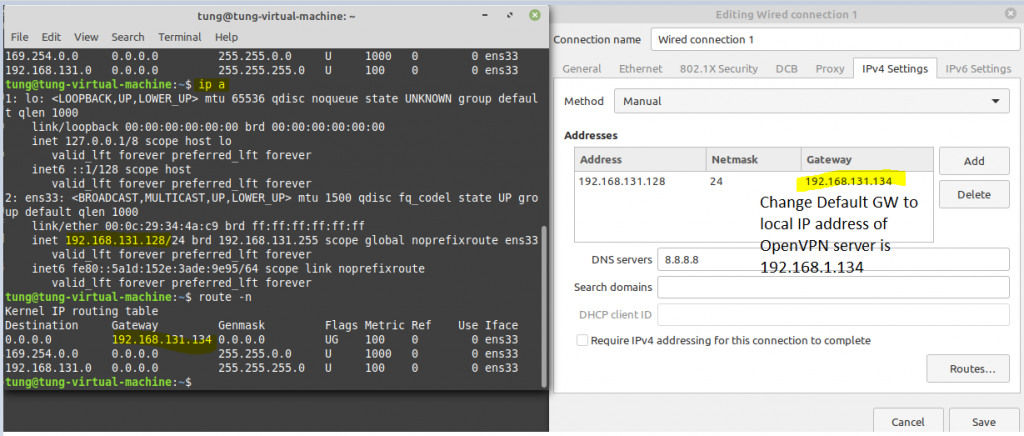
On Debian OpenVPN server.
Check routing table on OpenVPN server.
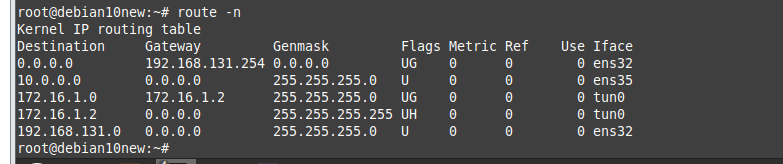
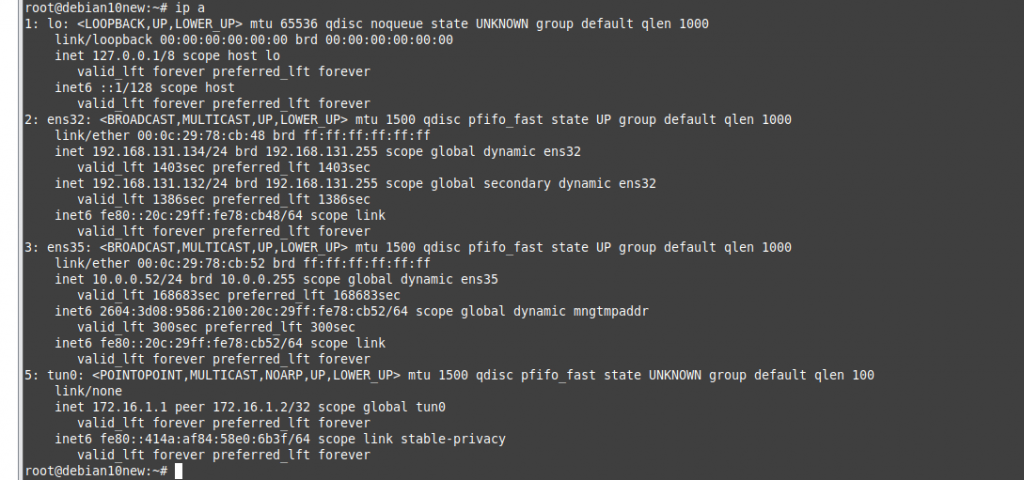
Check OpenVPN logs on the OpenVPN server.
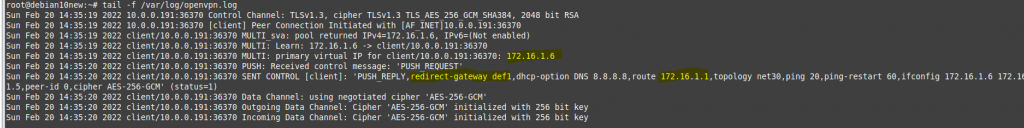
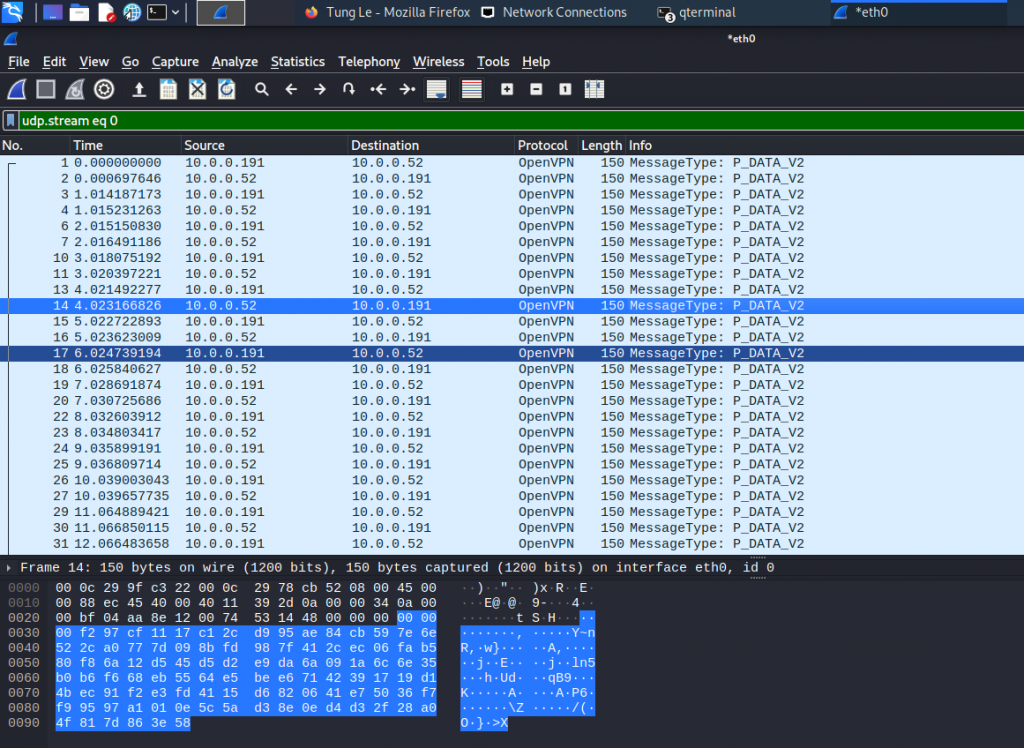
Monitor traffic on the OpenVPN server. OpenVPN traffic is using port 1194 UDP. OpenVPN traffic is encrypted using this tunnel.