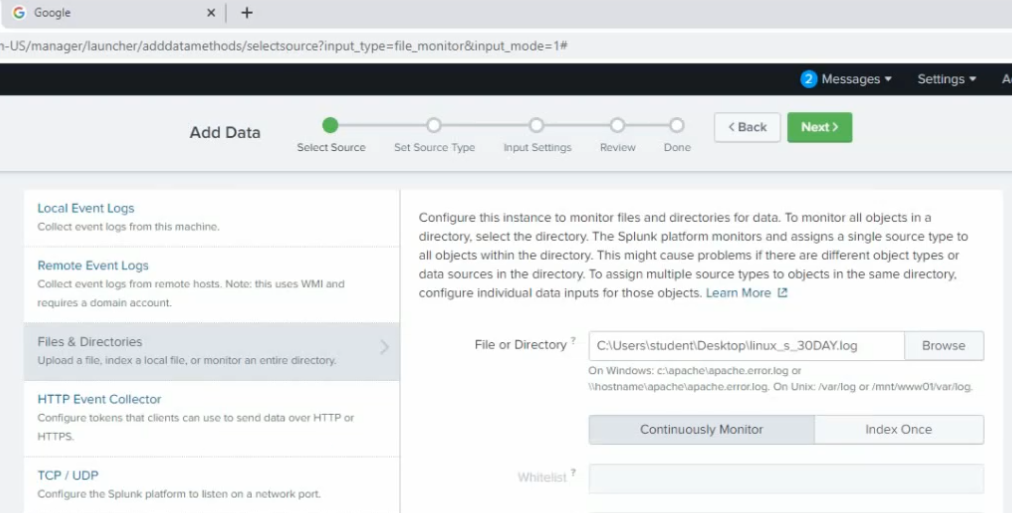
Splunk – Settings – Data Input – File Directories – New Local File and Directory – Browse to the Linux log file.
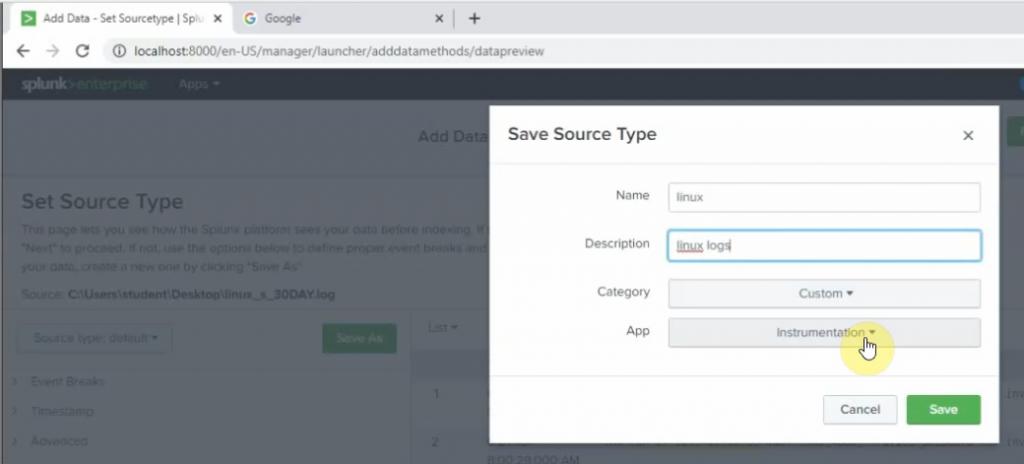
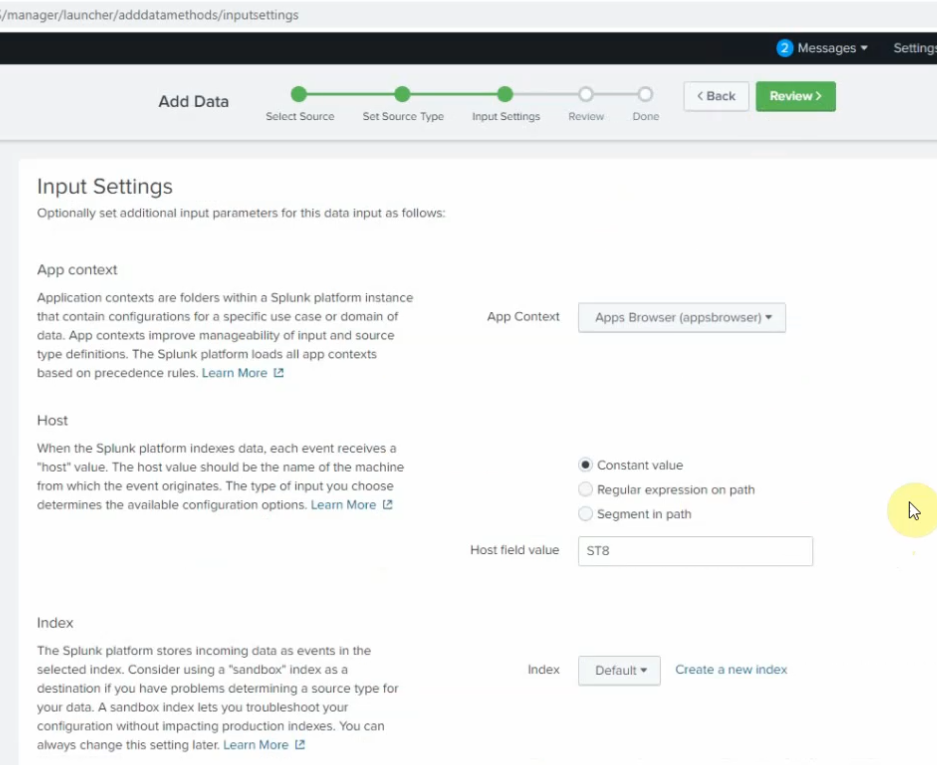
Save as log as linux.
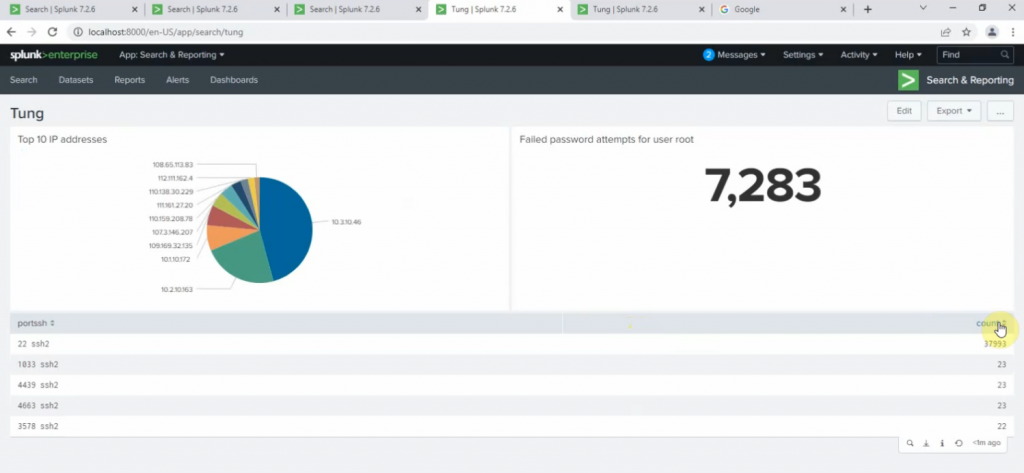
Count the number of Failed passwords for user root
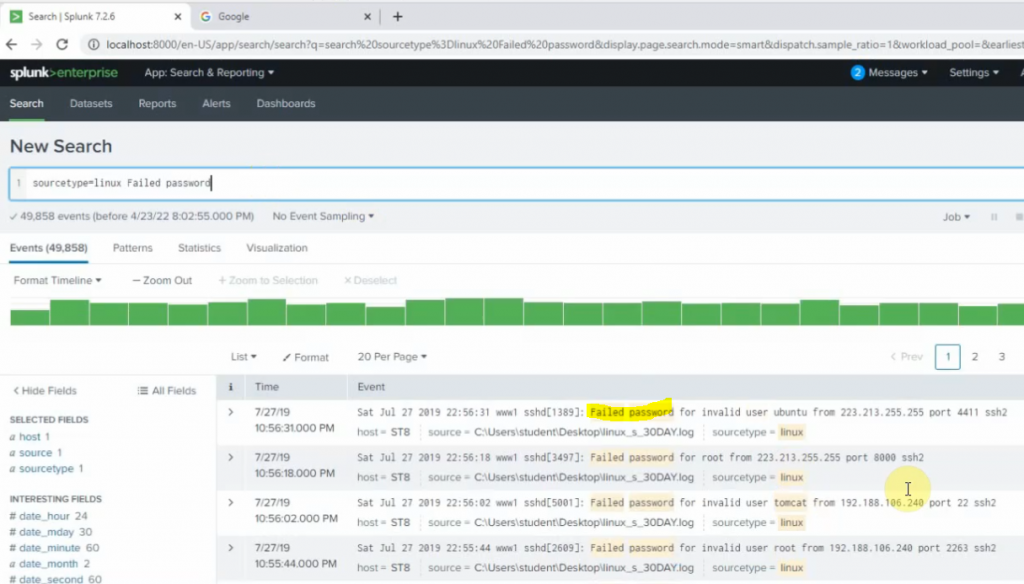
sourcetype="linux" Failed password root | stats count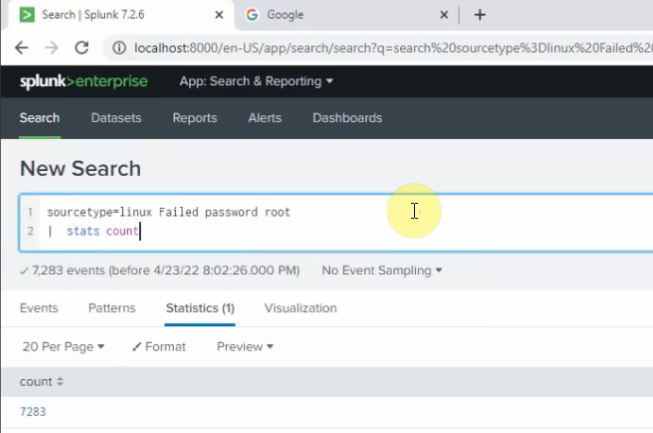
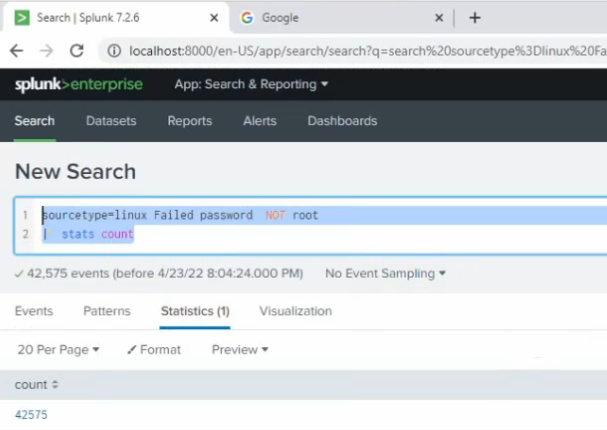
+ Count the number of Failed password except root.
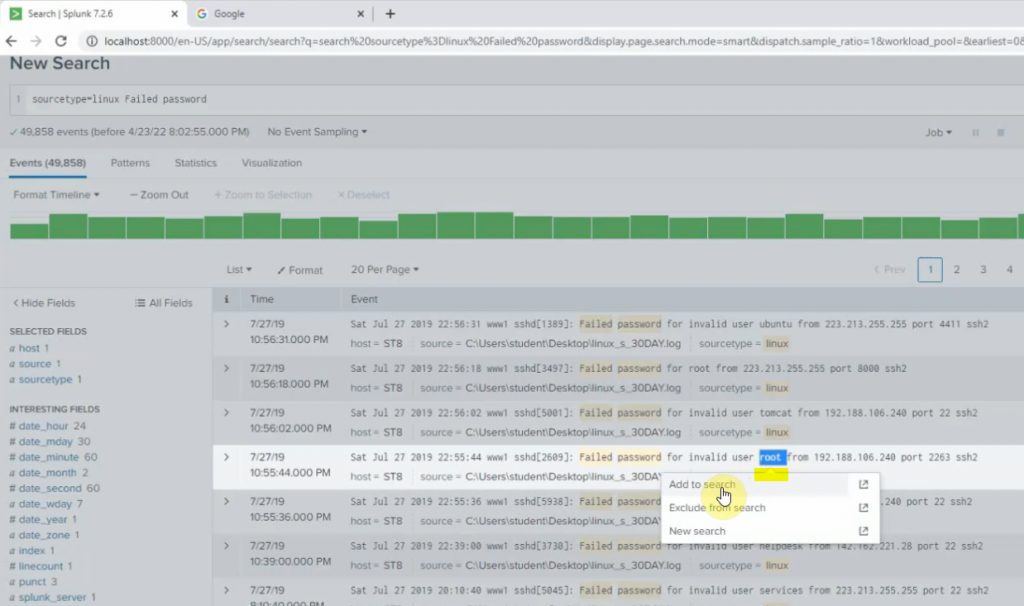
sourcetype="linux" Failed password NOT root | stats count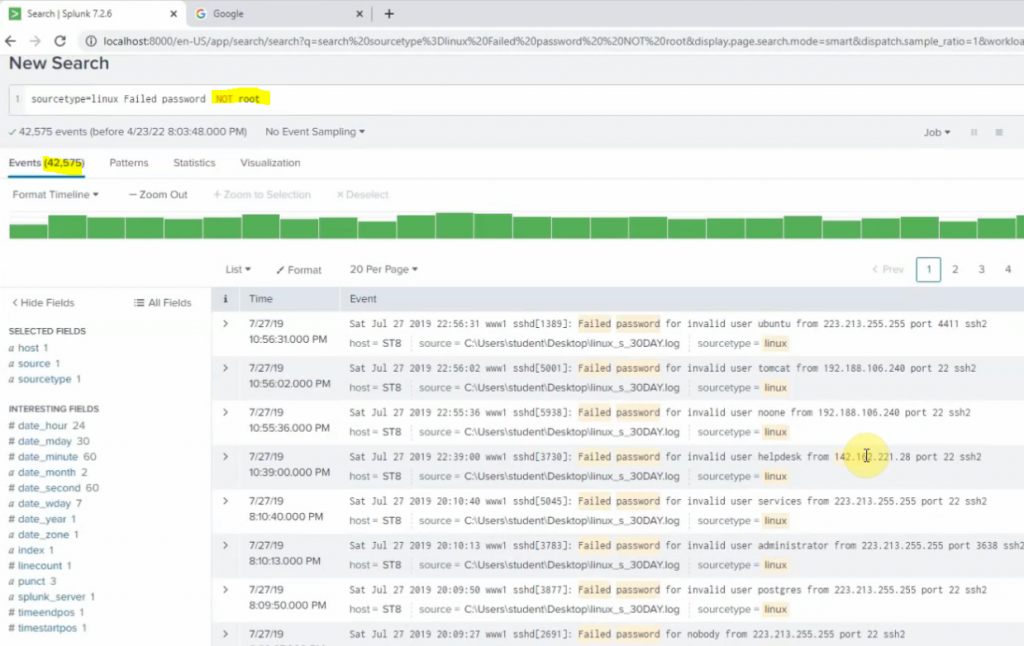
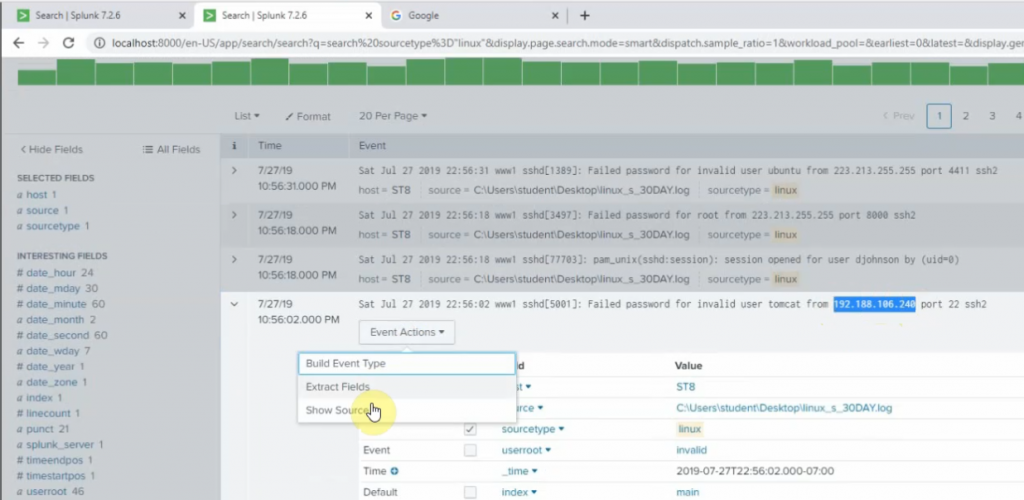
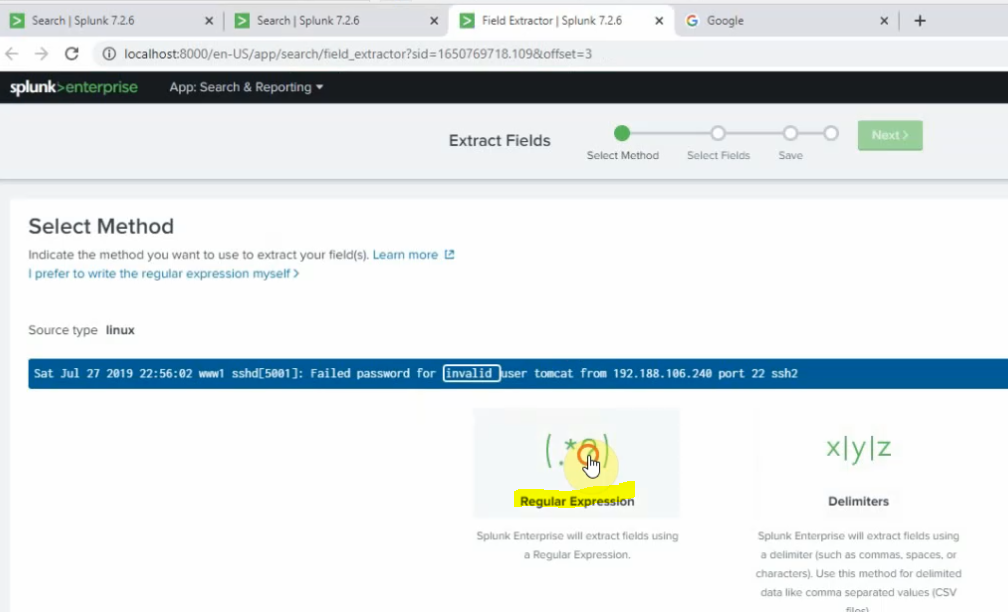
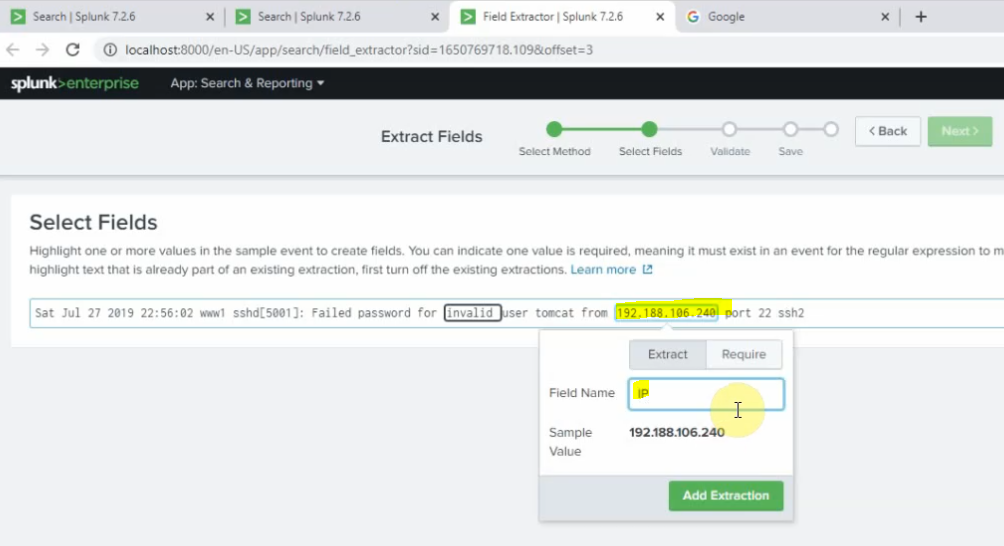
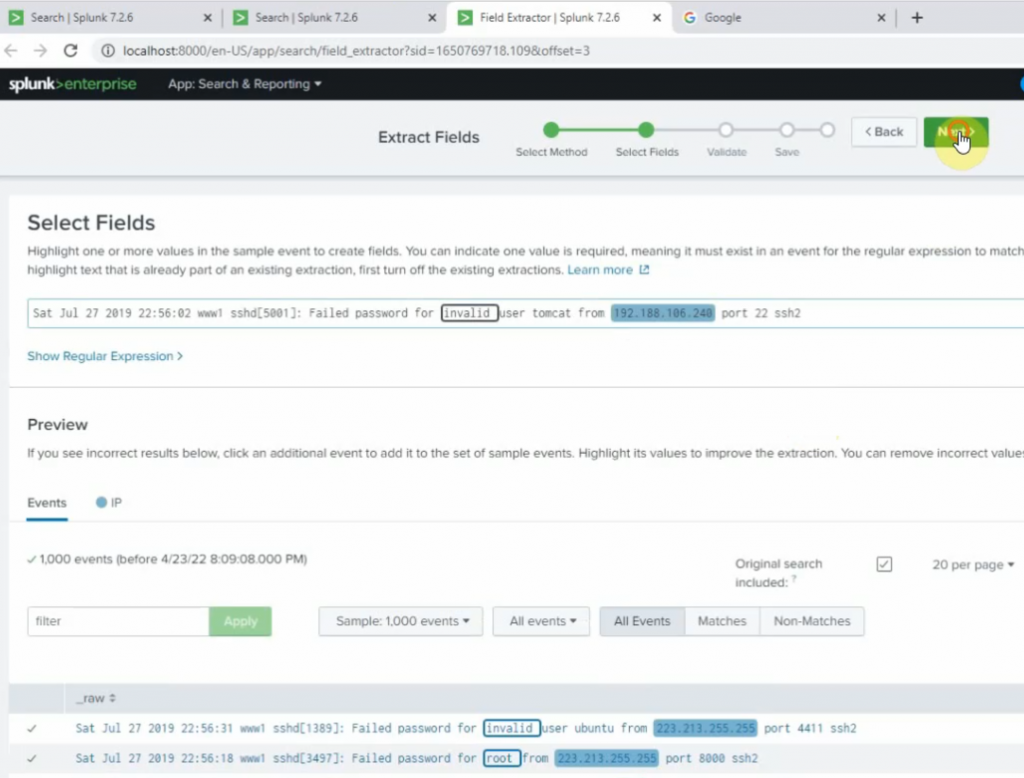
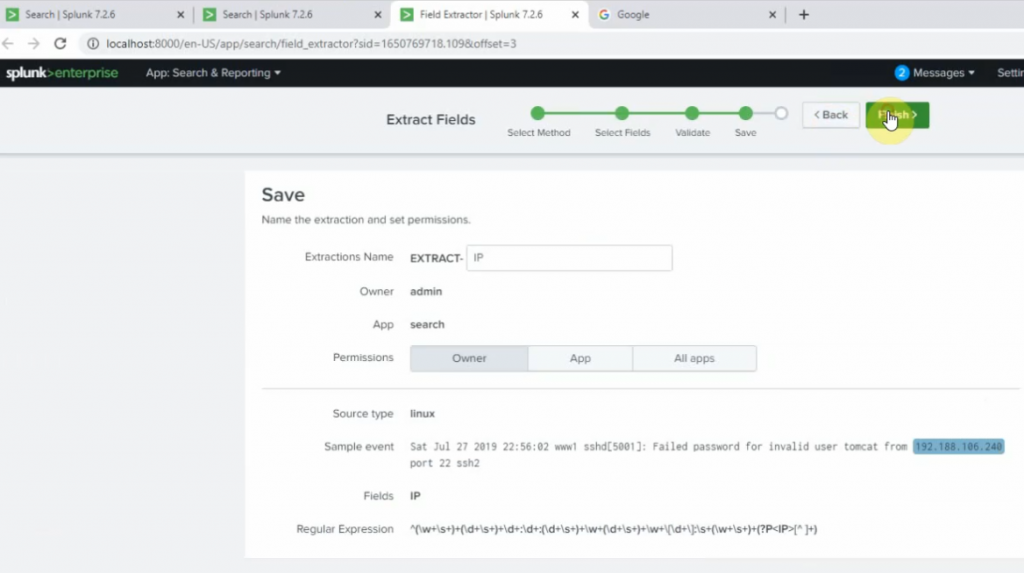
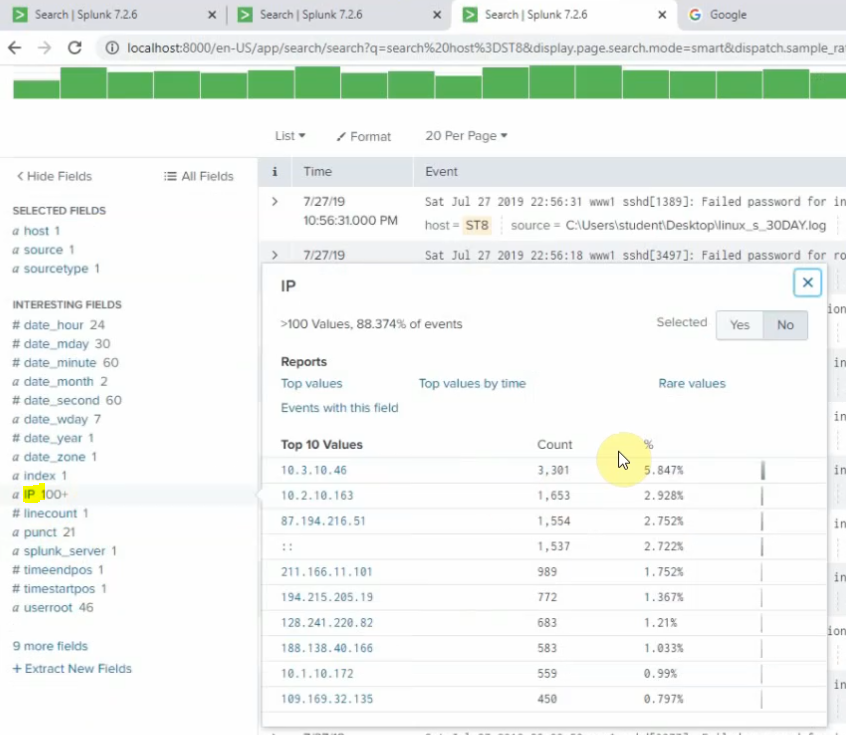
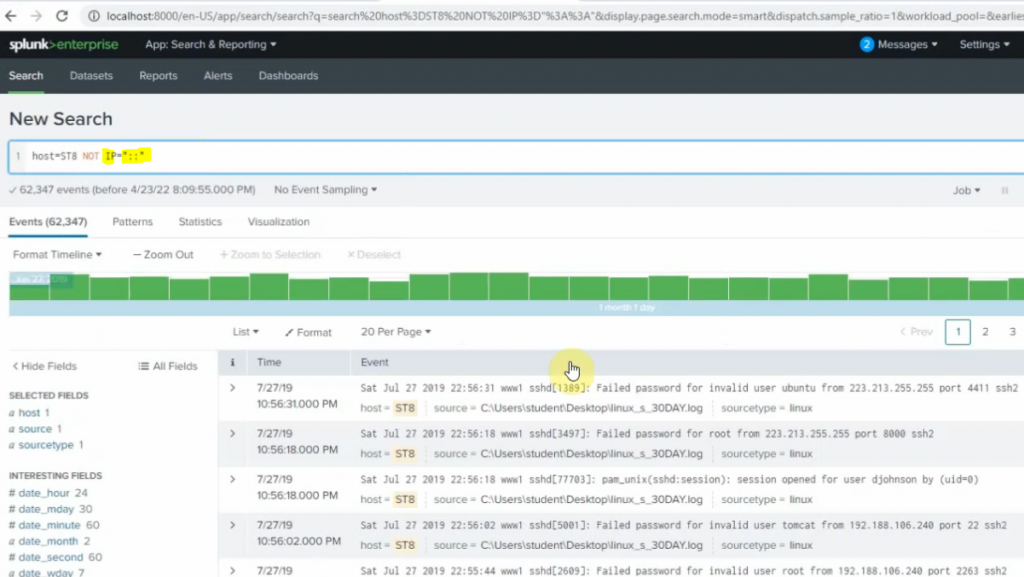
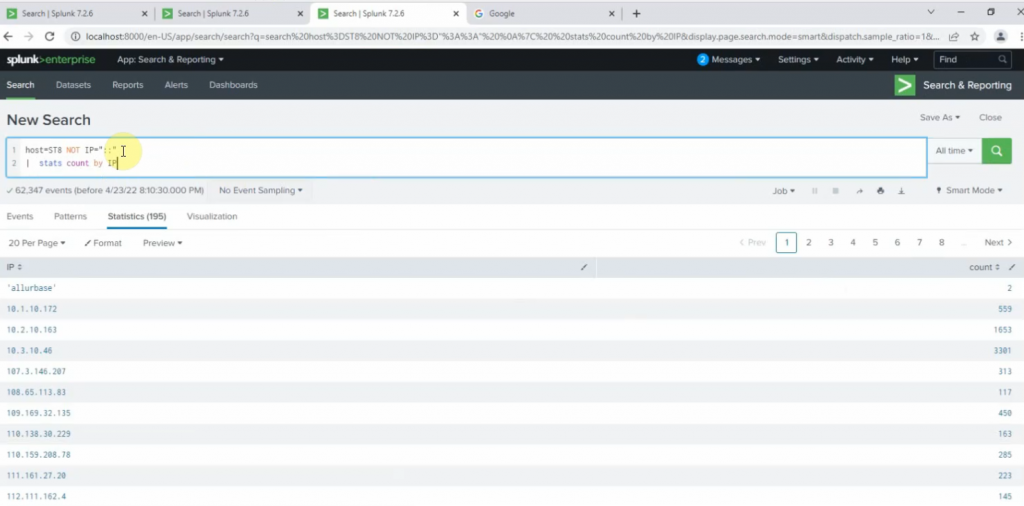
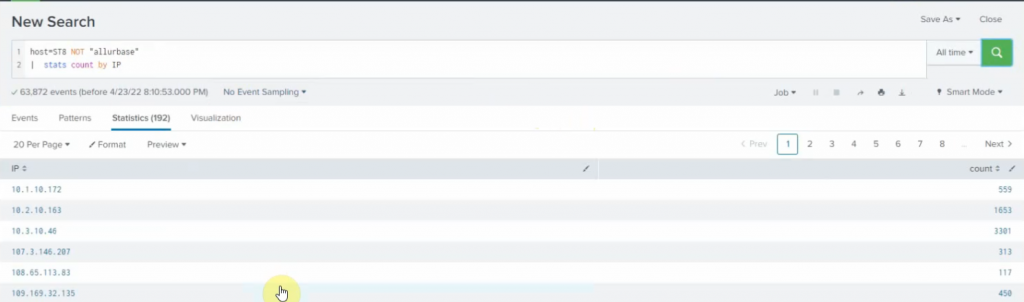
sourcetype=linuxlogs NOT 'allurbase' | stats count by IP | head 10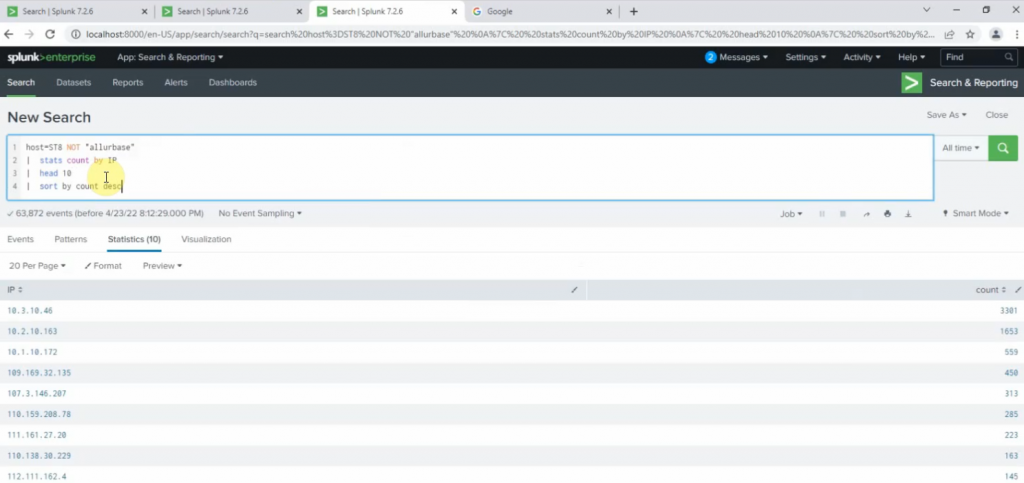
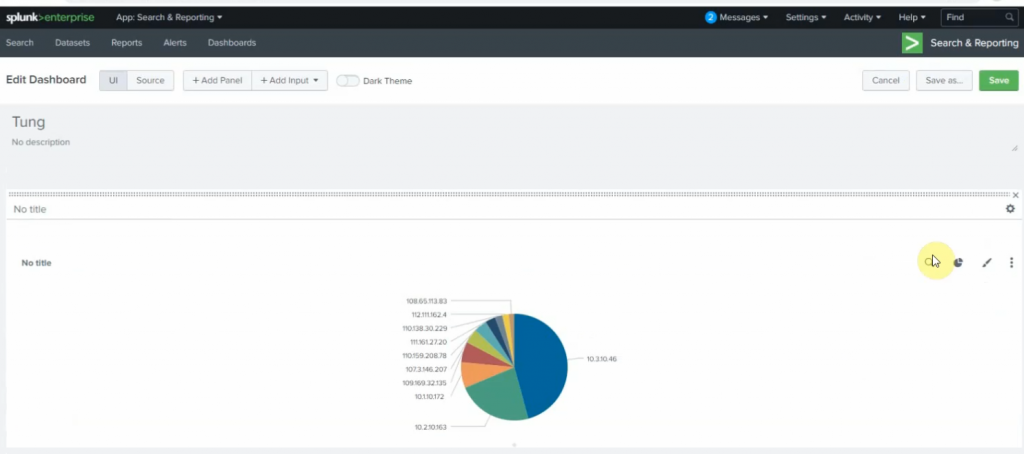
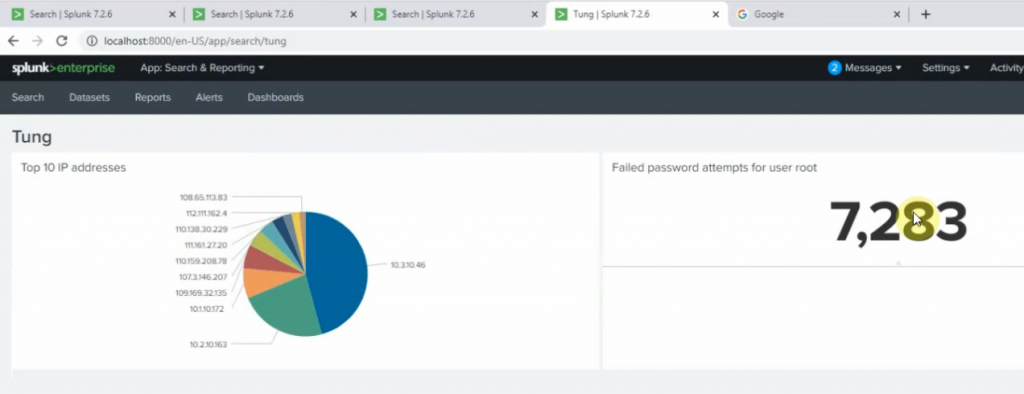
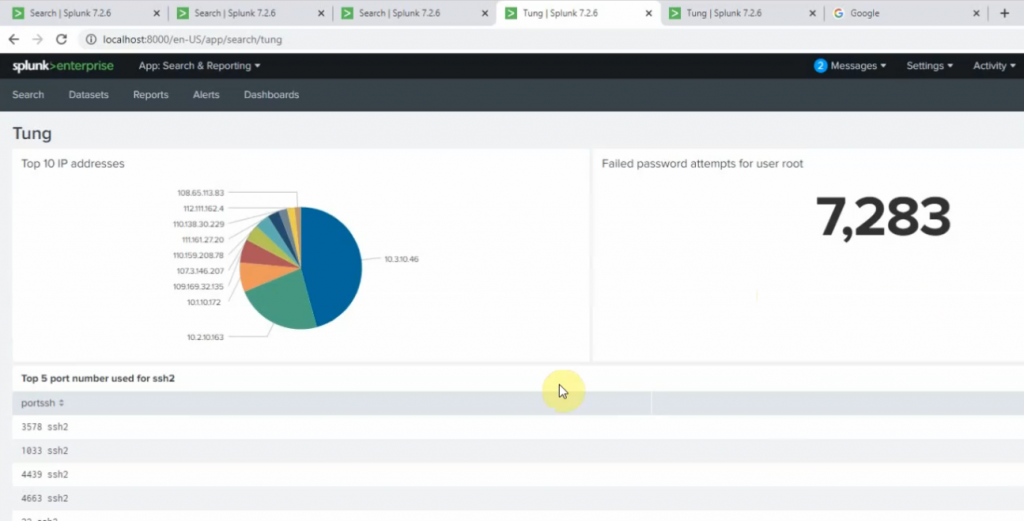
+ show top 5 port number used for ssh2.
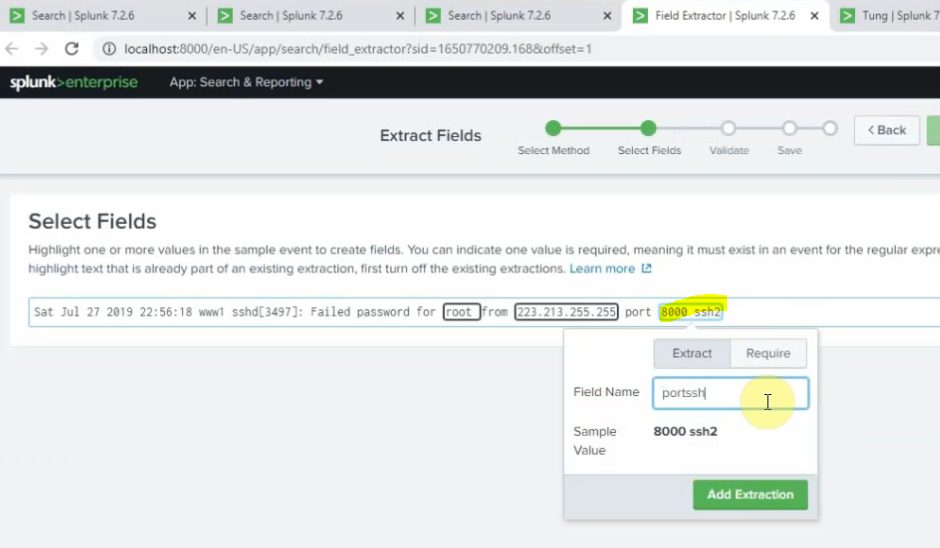
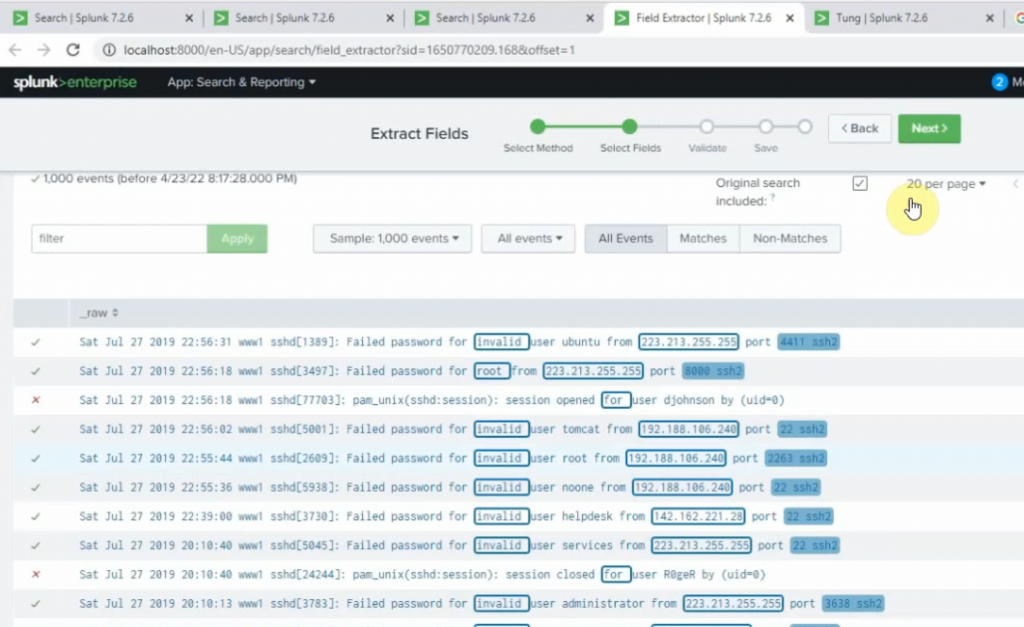
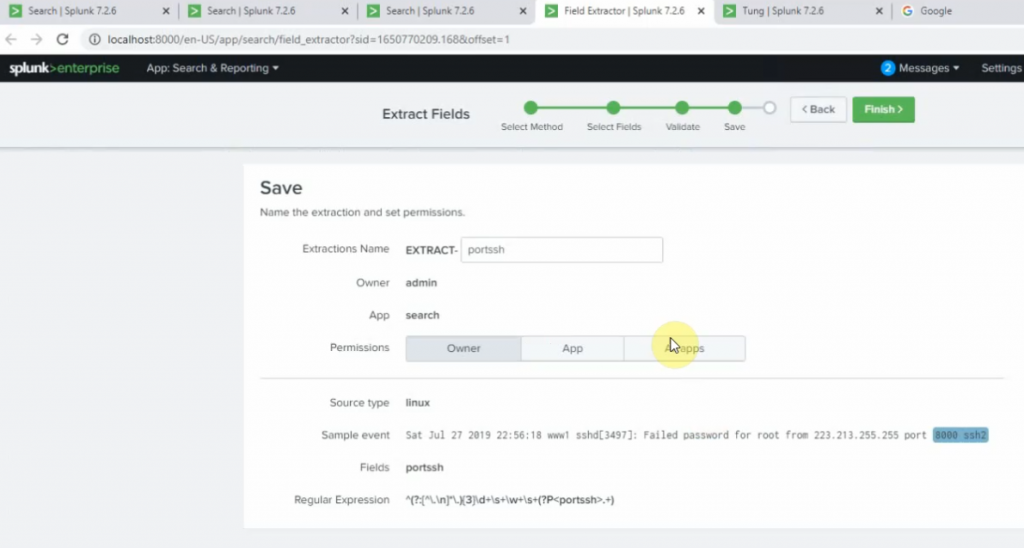
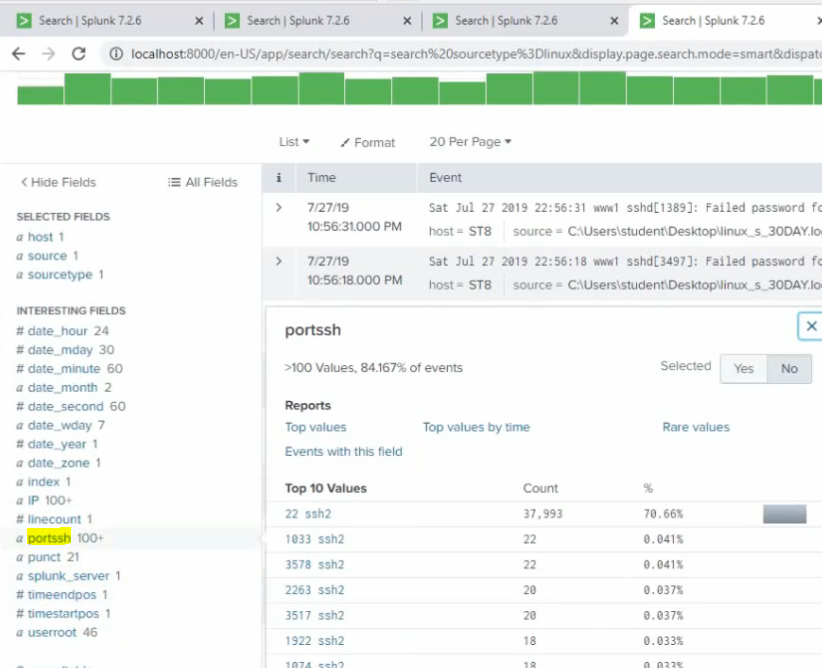
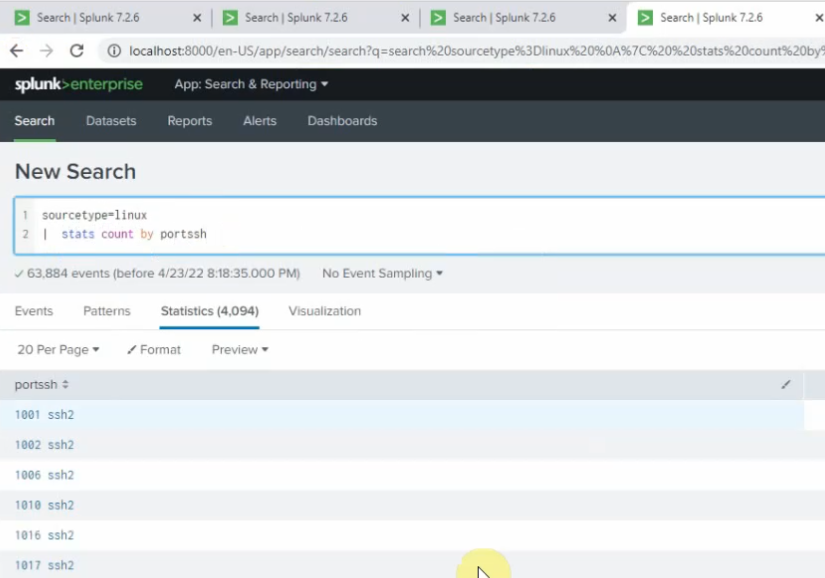
sourcetype="linux" | stats count by sshport | sort count by desc | head 5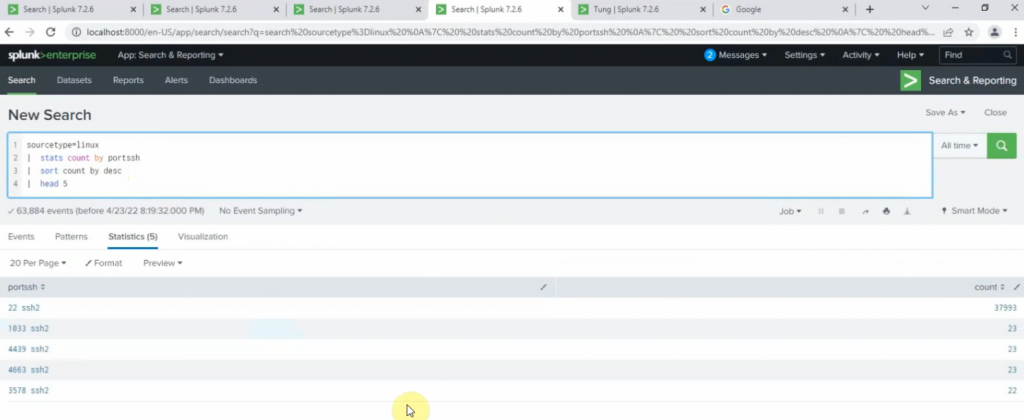
+ show top 5 port number used for ssh2
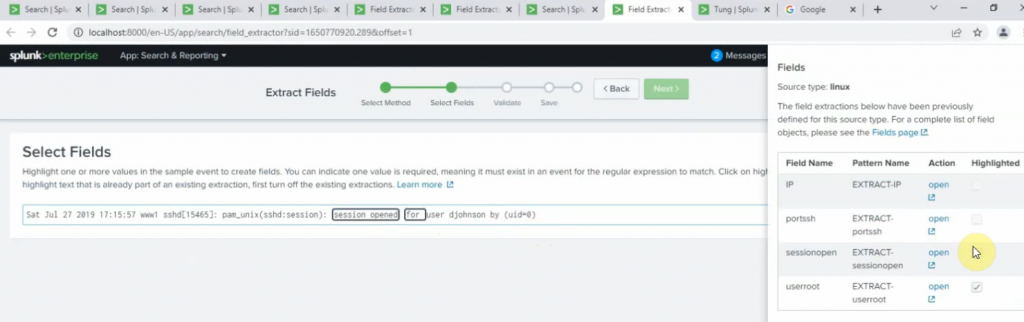
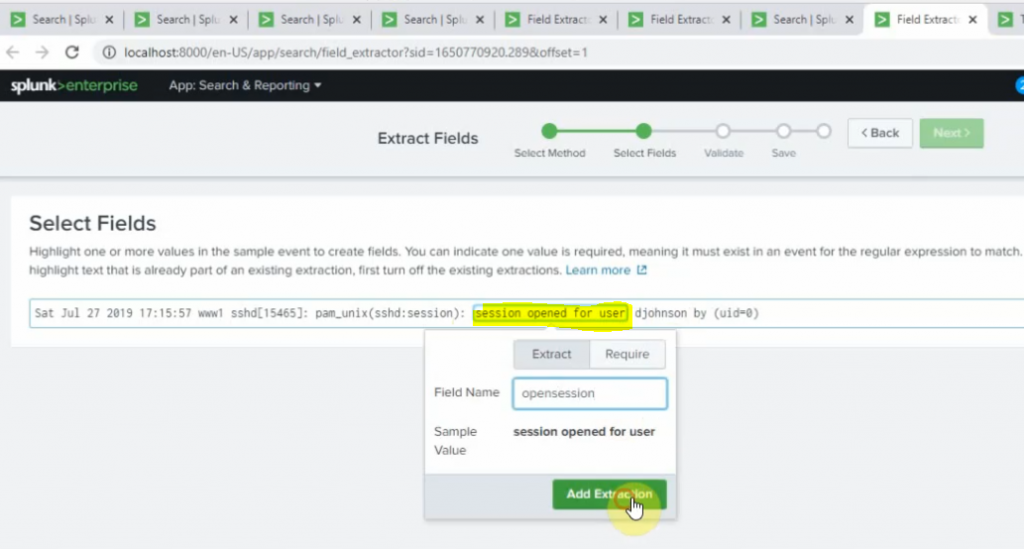
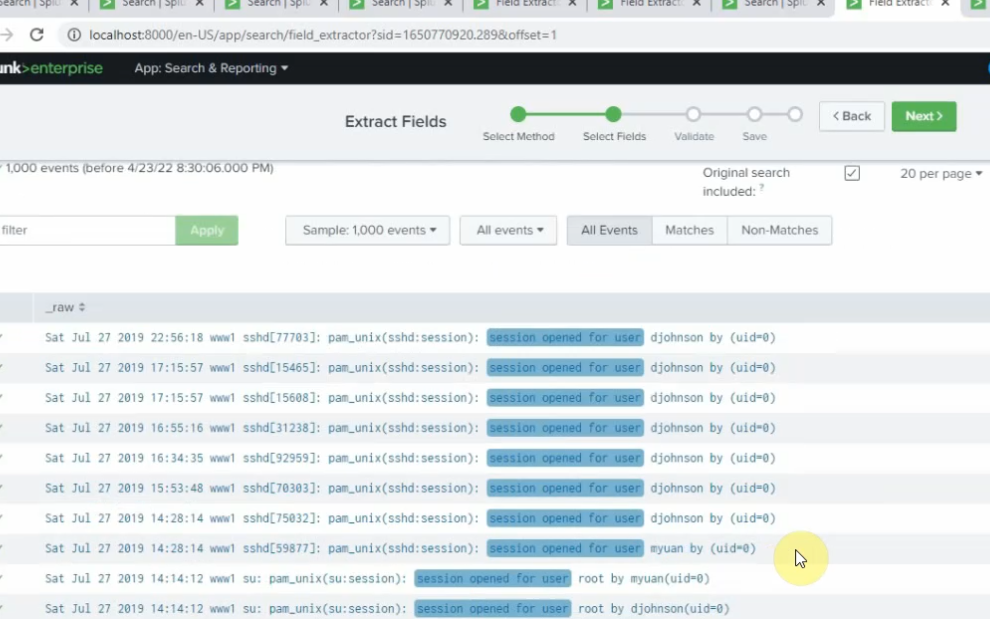
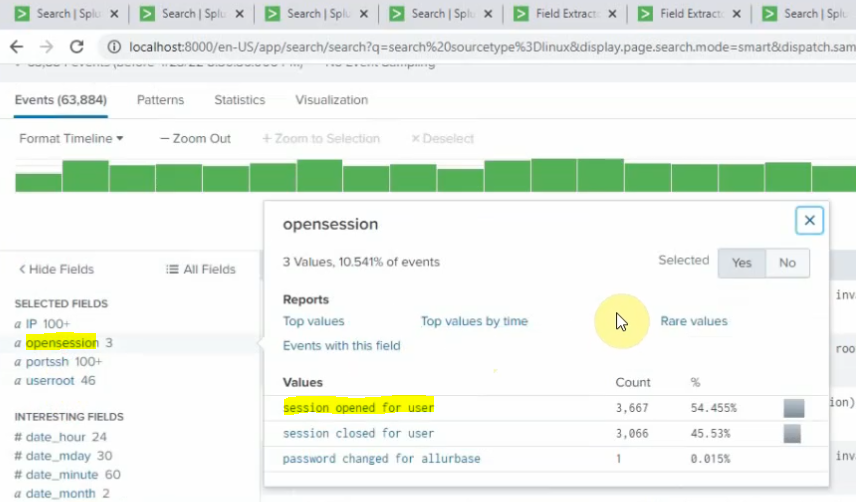
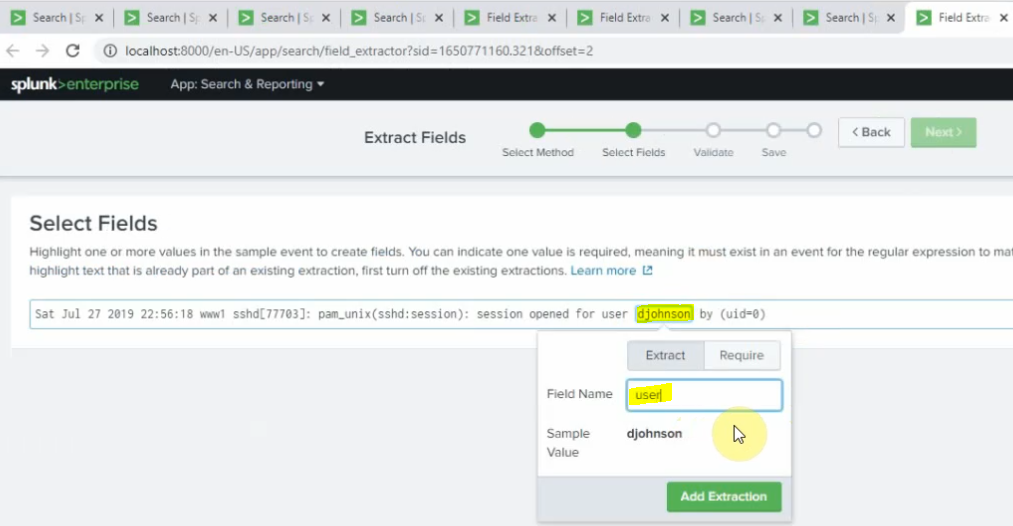
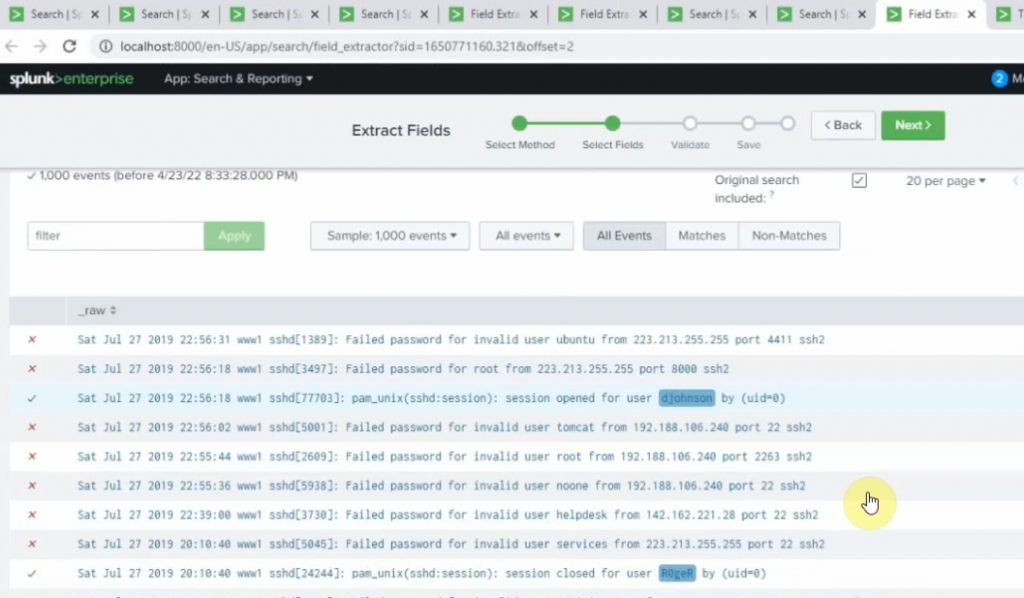
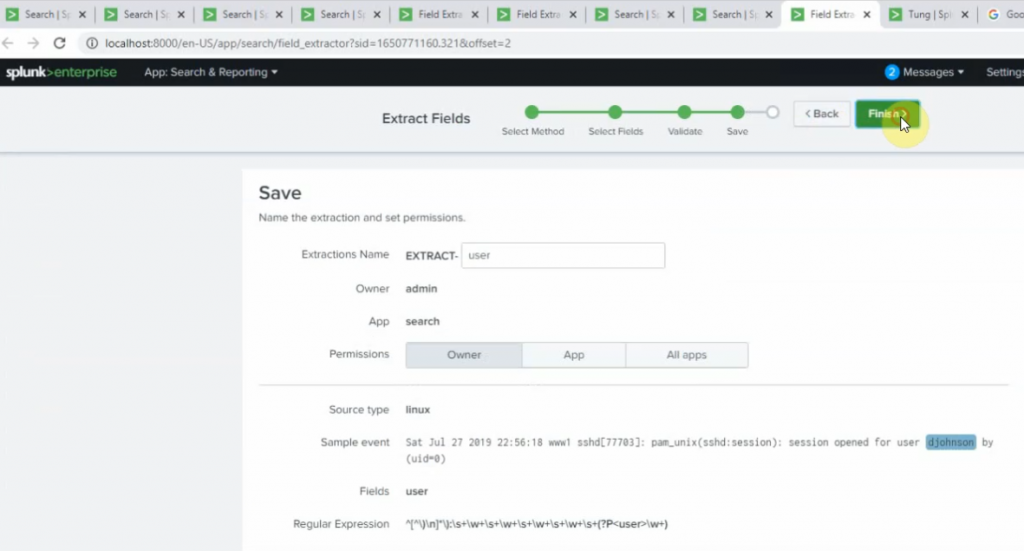
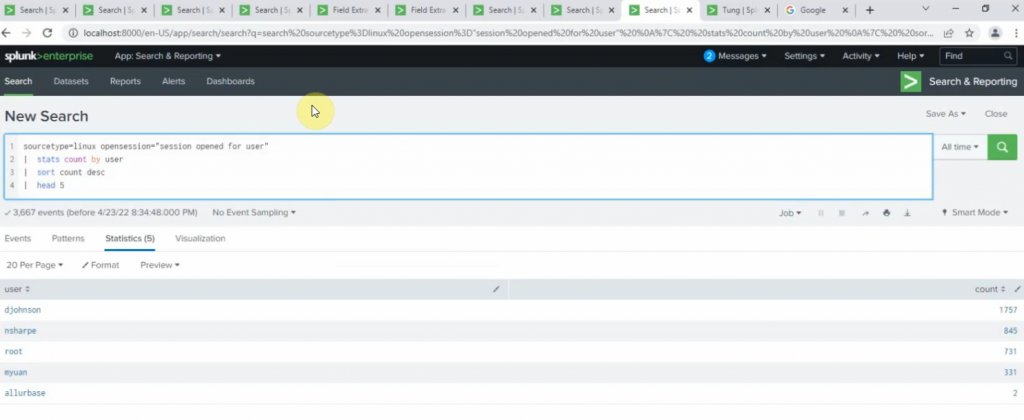
sourcetype="linux" session opened for user | stats count by user | sort count desc | head 5
Import Windows log file.
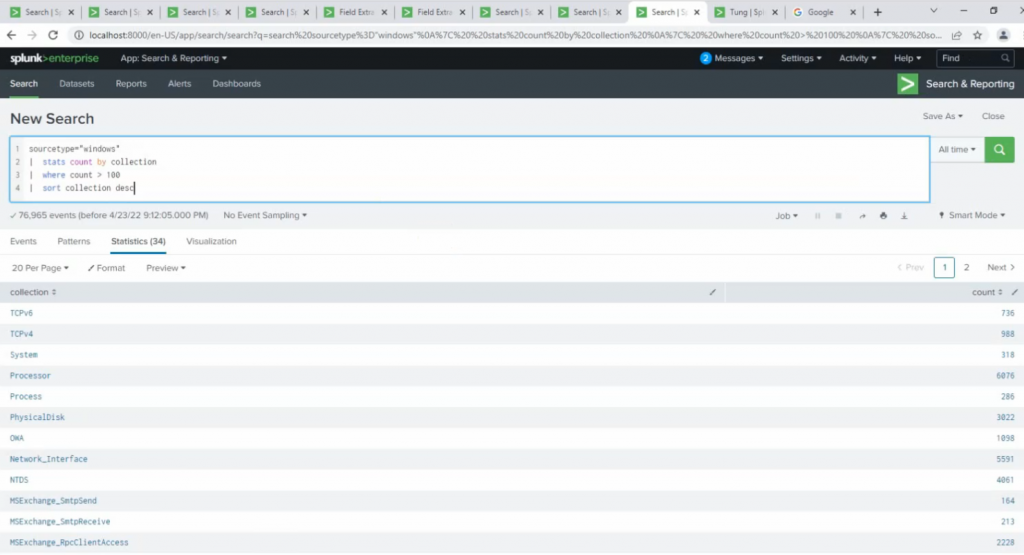
source=”windows_perfmon_logs.txt” | stats count by collection | where count>100 | sort collection desc
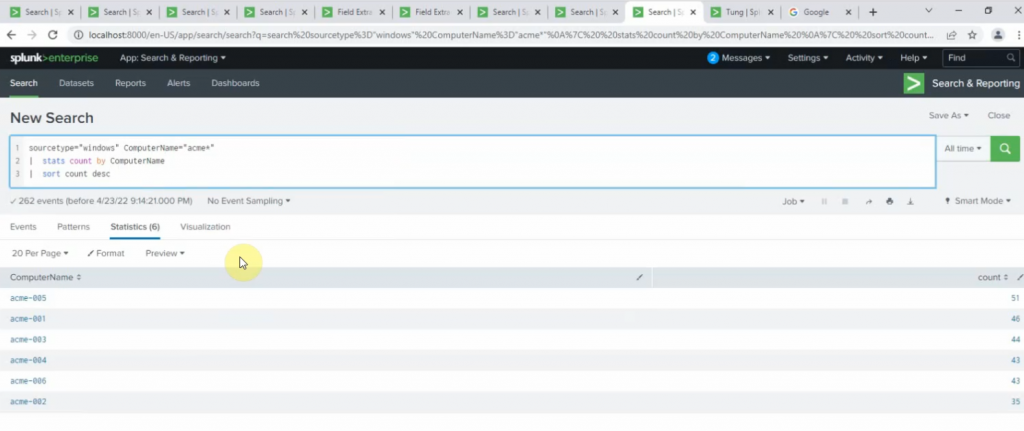
+ Count ComputerName start with acme and sort by desc.
source="windows_perfmon_logs.txt" ComputerName="acme*" | stats count by ComputerName | sort count desc