Open PowerShell with administrator right to enable WinRM. Then type the following command, and press “Y” two times.
winrm quickconfig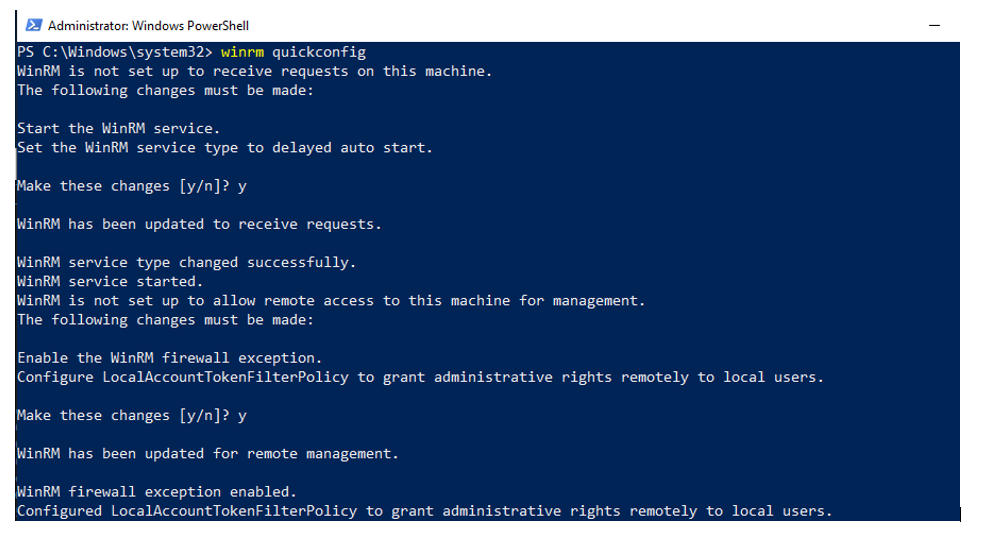
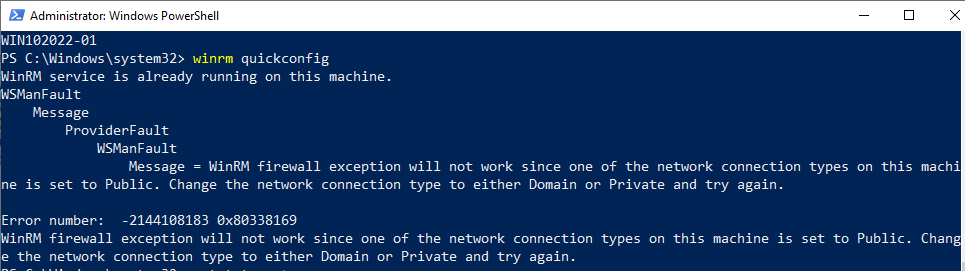
If your network connection type is Public, you will get an error below.
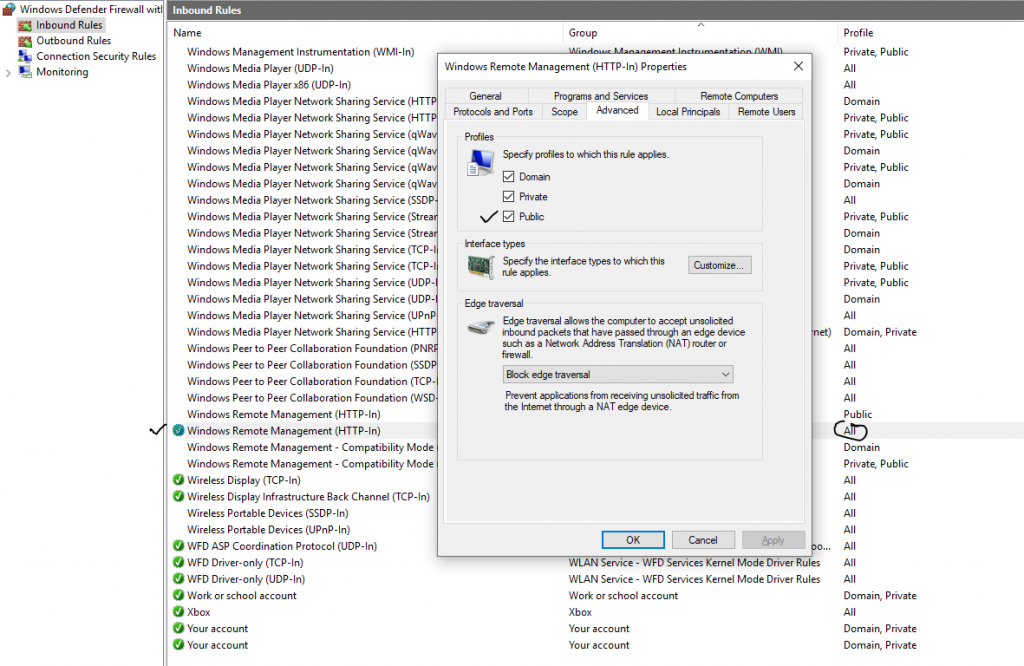
Go to Windows Firewall, and select “Public” on the Profiles setting to allow to connect via Public network.
Test the WinRM configuration by running the following command.
winrm identify -r:http://localhost:5985 -auth:noneIf the test is successful as in the screenshot below, your device is able to be managed via WMI.
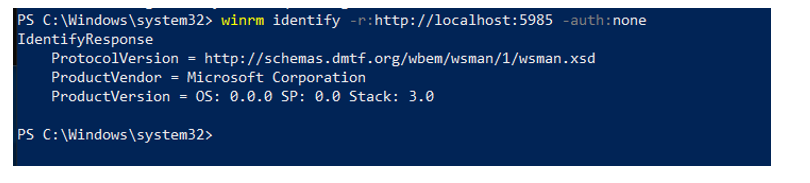
Check WinRM port is running.
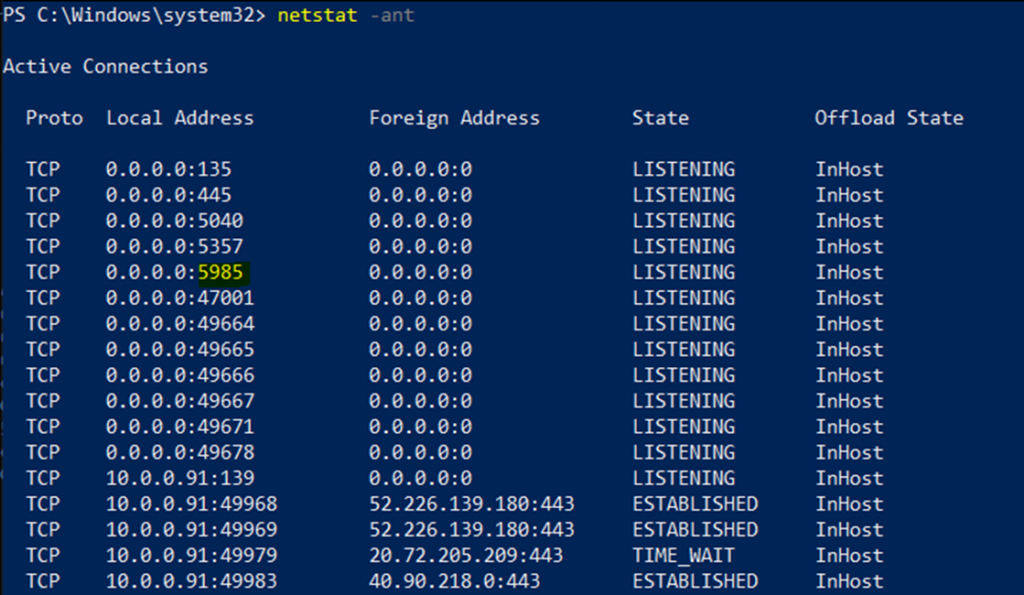
Remotely check WinRM port has listened on Windows machine.
Test-NetConnection WIN102022-01 -port 5985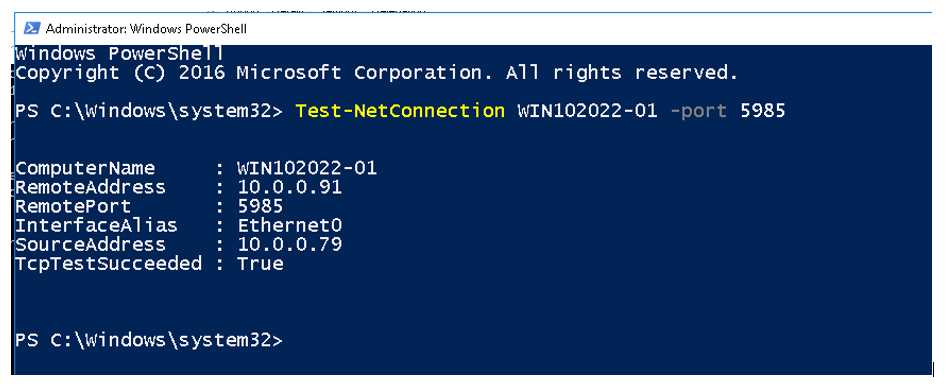
Enter WMI or WinRM credential for workgroup machine or Windows server.
PS C:\Windows\system32> $wmiuser, $wmisecret = (read-host 'Enter the WMIuser'), (Read-Host 'Enter the WMIsecret' -AsSecureString)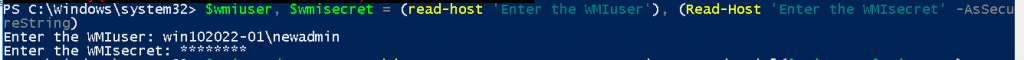
A newadmin user is member of local Administrators on Windows workgroup machine or Windows server.
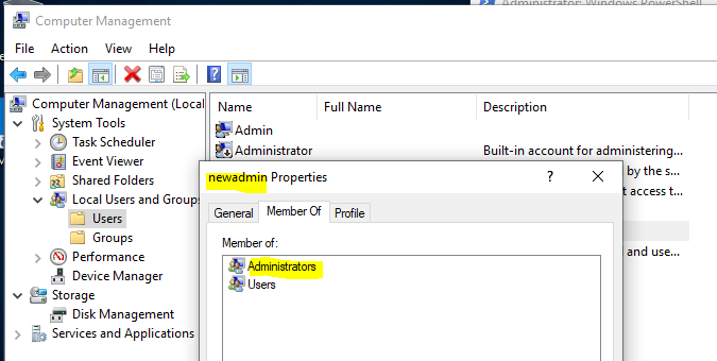
Create wmi_cred_new variable for WMI or WinRM credential.
$wmi_cred_new = New-Object System.Management.Automation.PSCredential($wmiuser, $wmisecret) 
Check hostname and ipconfig on a remote host via WinRM.
Invoke-Command -ComputerName WIN102022-01 -Credential $wmi_cred_new -ScriptBlock {hostname; ipconfig}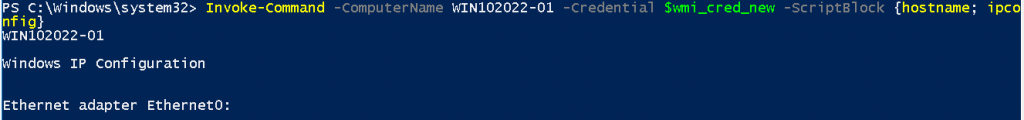
Check current OS Windows Patch.
Invoke-Command -ComputerName WIN102022-01 -FilePath C:\Shared\Get-CurrentPatchInfo.ps1 -Credential $wmi_cred_new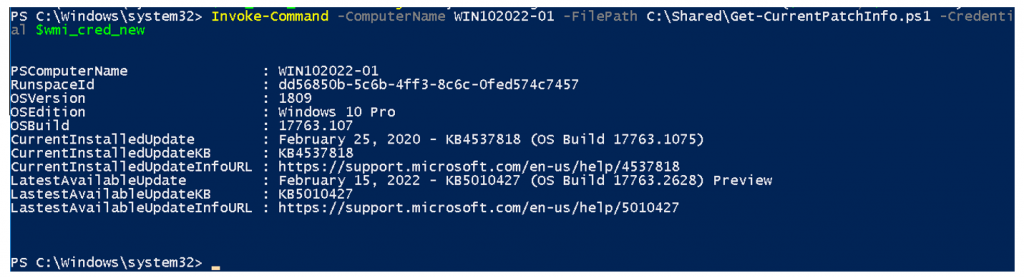
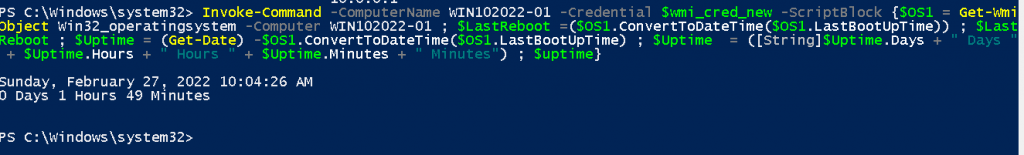
Get Lastreboot and uptime on Windows 10 workgroup machine.
Invoke-Command -ComputerName WIN102022-01 -Credential $wmi_cred_new -ScriptBlock {$OS1 = Get-WmiObject Win32_operatingsystem -Computer WIN102022-01 ; $LastReboot =($OS1.ConvertToDateTime($OS1.LastBootUpTime)) ; $LastReboot ; $Uptime = (Get-Date) -$OS1.ConvertToDateTime($OS1.LastBootUpTime) ; $Uptime = ([String]$Uptime.Days + " Days " + $Uptime.Hours + " Hours " + $Uptime.Minutes + " Minutes") ; $uptime}