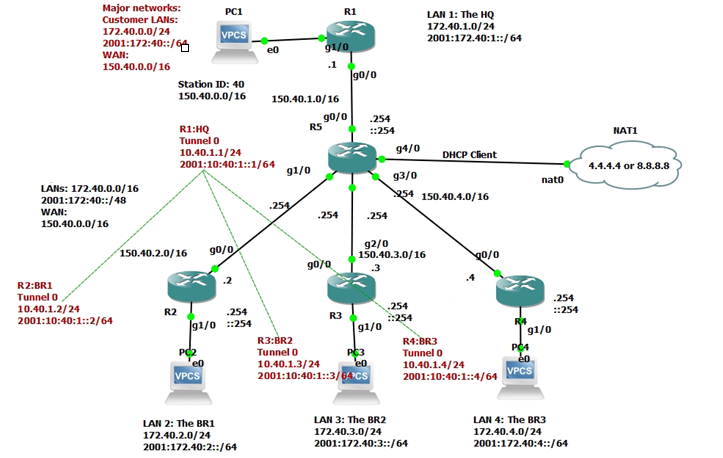
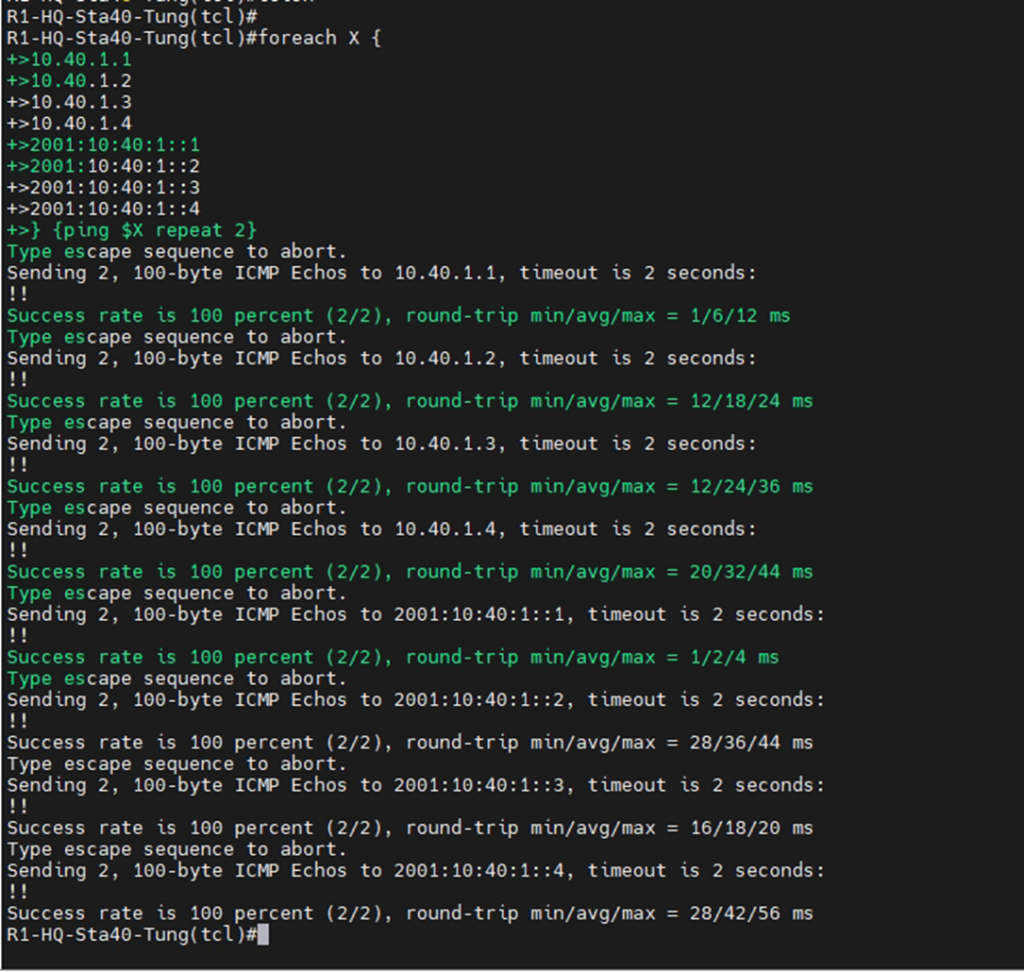
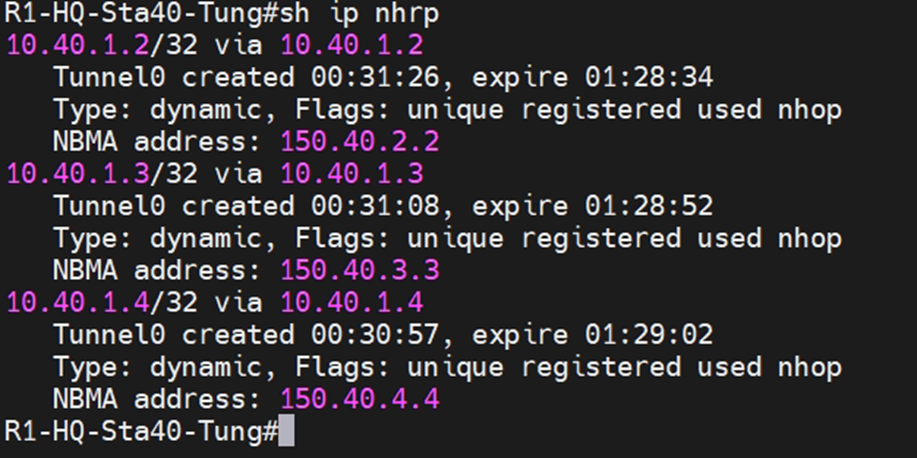
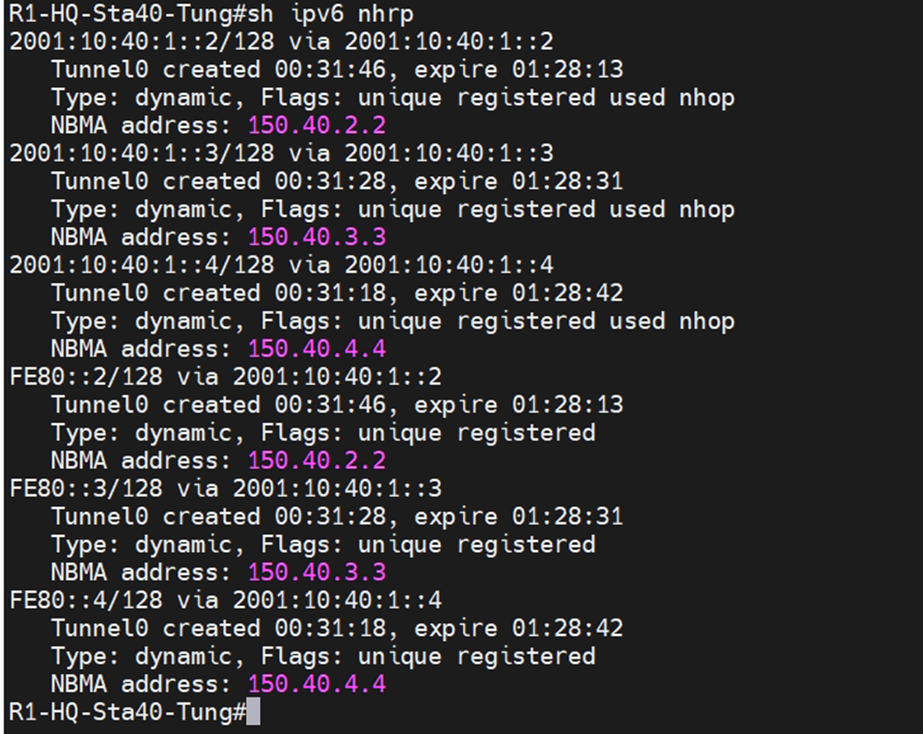
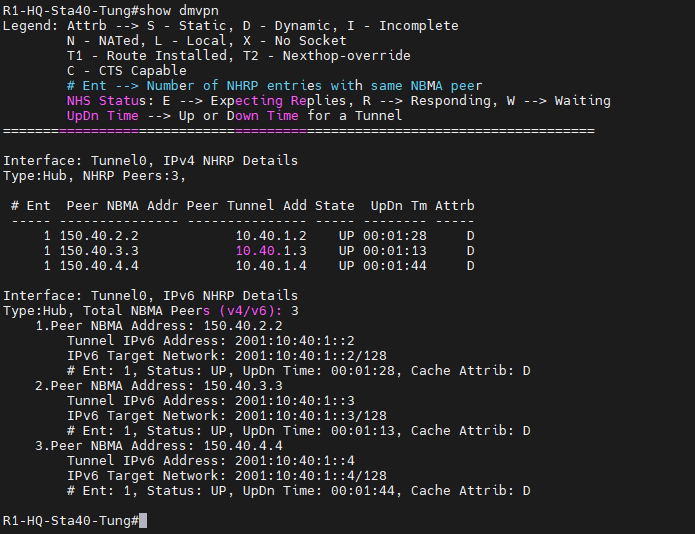
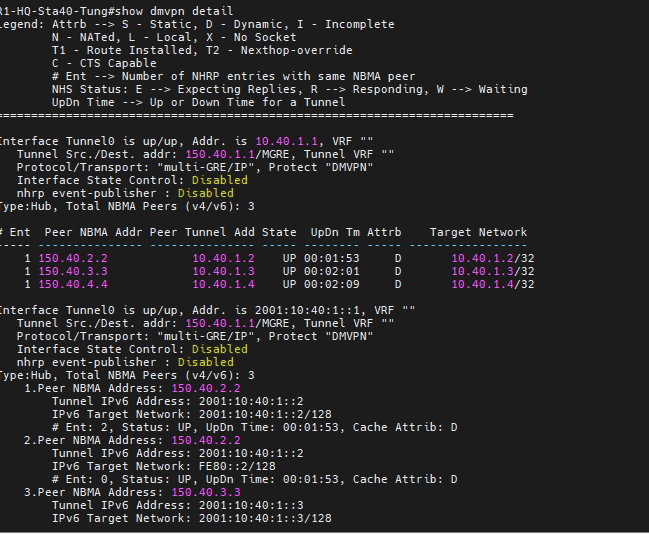
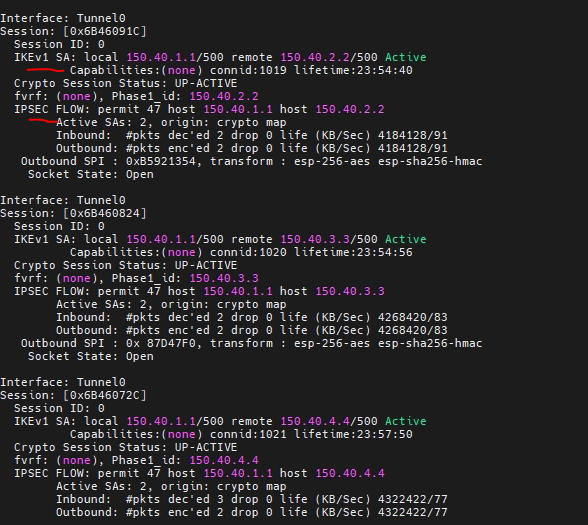
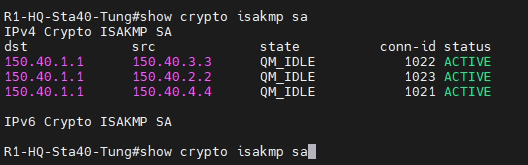
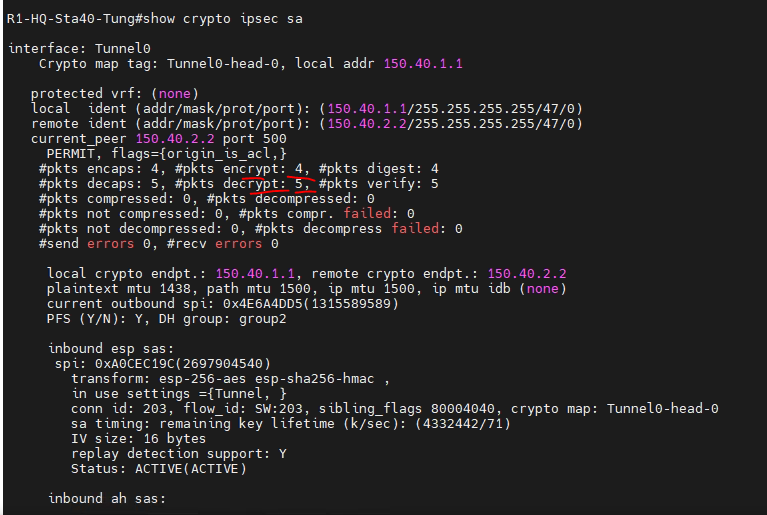
This is a topology for this lab.
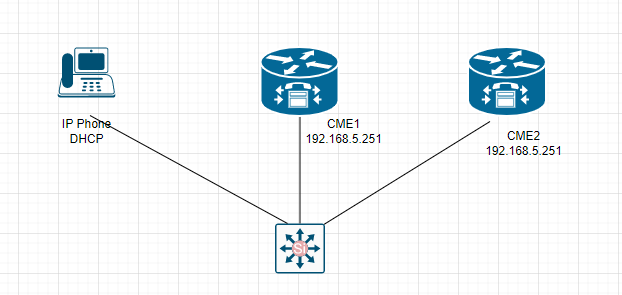
On Cisco CME R1 and R2:
+ On R1:
Configure secondary Cisco CME on the IP address 192.168.5.251 and register CIPC phone on Cisco CME R1 with DN is 1111
“ip source-address 192.168.5.250 port 2000 secondary 192.168.5.251 “

+ On R2:
Configure secondary Cisco CME on the IP address 192.168.5.250
“ip source-address 192.168.5.251 port 2000 secondary 192.168.5.250 “
telephony-service
max-ephones 2
max-dn 25
ip source-address 192.168.5.251 port 2000 secondary 192.168.5.250
system message TUNGLEVoIP
max-conferences 4 gain -6
web admin system name admin password Pa$$w0rd
dn-webedit
time-webedit
transfer-system full-consult
create cnf-files version-stamp Jan 01 2002 00:00:00
+ Next, configure CIPC softphone on Windows VM.
TFTP server 1: 192.168.5.210
TFTP server 2: 192.168.5.251

+ Shutdown R1 (192.168.5.250)

The phone has been switched to successfully register on CME R2.